
Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.



Key features of Group-IB’s threat intelligence solution
Group-IB Threat Intelligence Platform delivers the full value of digital threat intelligence, strengthening every component of your security with strategic, operational, and tactical insights
Understand threat trends and anticipate specific cyber attacks with thorough knowledge of your threat landscape. Group-IB Threat Intelligence Platform provides precise, tailored, and reliable cyber threat intelligence for data-driven strategic decisions.
Strengthen defenses with detailed insight into attacker behaviors and infrastructure. Group-IB Threat Intelligence Platform delivers the most comprehensive insight into past, present, and future attacks targeting your organization, industry, partners, and clients.
Identify cyberattacks faster and reduce incident response time with full visibility into every attack stage. Group-IB Threat Intelligence Platform equips your teams with the best possible insight into the methods used by adversaries.

with tailored on-demand, and regular monthly and quarterly threat reports written by threat intelligence analysts specifically for the board and executives

with actionable threat intelligence before expanding into a new region/business line, and get industry-specific threats before digital transformation

of cyber security by avoiding unnecessary purchases and postponing upgrades by maximizing the efficacy of your existing security infrastructure

and adapt instantly, use the insights to block malicious network and endpoint activity the moment it is first observed anywhere in the world

before they are exploited by arming your Red Team with detailed knowledge of threat actor’s tools, tactics and processes

and improve team efficiency by enriching your SIEM, SOAR, EDR and vulnerability management platforms with out-of-the-box API integrations supporting TAXII and STIX

for your technology stack with automated alerts that inform you the moment vulnerabilities are discovered or exploited by threat actors targeting your industry

and focus on legitimately risky events with a database of indicators of compromise for cybercriminals in your threat landscape

and quickly remove attackers from your network with knowledge of the cyber kill chain used by threat actors in the MITRE ATT&CK matrix format
Paste sites
Code repositories
Exploit repositories
Social media discussions
URL sharing services
C&C server analysis
Darkweb markets
Darkweb forums
Instant Messengers data (Telegram, Discord)
Phishing and malware kits
Compromised data-checkers
Detonation platform
Malware emulators
Malware configuration files extraction
Public sandboxes
ISP-level sensors
Honeypot network
IP scanners
Web crawlers
Malware reverse engineers
Undercover dark web agents
DFIR and audit services
Law enforcement operations
Regional specialists
Embedded managed service teams
CVE list
Exploit repositories
Dark web discussions
Threat campaigns mapping
This specialized offering enables you to submit requests to our seasoned threat intelligence researchers, skilled in analyzing and interpreting complex threat landscapes.
Threat Intelligence is a scope of data (or database) collected from various sources, processed and analyzed to provide a deep insight into adversary behavior, their motives, and attack tactics. Threat intelligence solutions empower security teams to make faster and data-driven cybersecurity decisions and switch from reactive to proactive approach to fighting against threat actors.
Group-IB Threat Intelligence Platform provides unparalleled insight into threat actors and optimizes the performance of every component of your security with strategic, operational, and tactical intelligence.
Threat intelligence comes in strategic, tactical, and operational forms, each providing unique foresight. Integrated threat intelligence enhances detection and fortifies protections from dangers across an organization through real-time visibility and predictive insights.
A threat intelligence platform (TIP), also known as a cyber threat intelligence platform, is a technology solution that gathers, combines, and organizes threat intelligence from various sources.
Threat intelligence solutions empower effective and precise threat identification, investigation, and response by providing a security team with information about threats in an easily digestible format.
Solutions of this class automate data collection and management, allowing threat intelligence analysts to focus on analyzing and researching cybersecurity threats. Additionally, threat intelligence platforms facilitate the communication of digital threat intelligence information to security specialists.
A cyber threat intelligence platform provides organizations with insights into potential security threats by gathering data and transforming it into useful intel. Threat intel platforms also include security assessments, monitoring, and offering threat response support. Intelligence platforms work through the following process:
Threat intel platforms collect threat data from various threat intelligence sources, including open-source sources. They also look for cybersecurity indicators from dark web monitoring, malware sandboxes, threat intelligence sharing, and the vendor’s own research.
They then store large amounts of raw threat data in the platform’s database for analysis and correlation.
The raw data undergoes a normalization process to uniformly structure it and filter out irrelevant items, preparing it for analysis.
The platform deploys machine learning and artificial intelligence to identify patterns and relationships in the normalized threat data.
By correlating and enriching analyzed data, the platform generates threat information through organized insights, tactical reports, and strategic assessments.
Threat intelligence platforms also disseminates the generated threat intelligence to connected security tools, systems, and users via automated feeds and interactive dashboards or interfaces.
The intelligence enables proactive security postures by feeding threat detection, alerting systems to known risks, empowering investigations, and driving security control improvements.
A threat intel platform provides an automated, proactive approach to obtaining threat data from various sources and turning it into actionable intelligence. It enables real-time monitoring of emerging threats through alerts and reports and helps improve an organization’s security posture. Use our industry-leading cyber threat intelligence platform to gain an upper hand against cybercriminals.
Cyber threat intelligence teams help organizations stay a step ahead of attackers by understanding tactics, visualizing emerging risks, and tracking threat indicators in real-time. With timely alerts and actionable insights gained from a cyber threat intelligence platform, organizations block or isolate preemptively before impacting critical systems and data.
Threat intelligence data isn’t simply information. Organizations use accurate and timely threat intel as a blueprint for their mitigation efforts. A cyber threat intelligence platform provides relevant updates, allowing organizations to anticipate and respond to imminent trouble. Threat intelligence solutions offer value in the following ways:
Giving context: Through threat intelligence tools or software, a platform takes raw security data and gives it context. Platforms integrating threat intelligence from multiple sources provide insight into malicious infrastructure, techniques, and threat indicators linked to each alert. This contextualization allows analysts to prioritize issues based on a complete understanding of inherent risks
Automation: Threat intelligence platforms use automation to achieve faster threat detection and response by automatically collecting threat data from various sources around the clock. They then structure and correlate this information to identify relationships and patterns that cybercriminals use. Use our Managed XDR solution for automated threat intel feeds, monitoring and analysis, and detection in real-time.
Real-time monitoring: Timely response is key in managing and responding to cyber threats. Threat intelligence tools facilitate real-time monitoring and detection of threats through analytics capabilities. They scan networks and continuously analyze all incoming data to surface anomalies and detect emerging threats. A security operations center generates alerts upon detecting potential security incidents, which empowers organizations to reduce security risks and data exposure.
To get started simply fill in the form on this page. Our threat intelligence team will guide you through the proof of concept process and show you how to get the most value out of your Threat Intelligence solution.
Group-IB Threat Intelligence Platform is a cloud service and can be enabled instantly. Our onboarding team will help configure the threat intelligence solution to meet your specific requirements and support integration with third-party services.
Our threat intelligence platform is modular and flexible, allowing you to gather the intelligence you need how and when you need it. We believe that intelligence should be accessed and do not charge per user, integration or API call.
Group-IB’s threat intel platform utilizes Threat Hunting Rules, enabling intelligence to be filtered and refined to meet your exact needs. Our team will set these up when the threat intelligence solution is first enabled and will work with you to continuously refine them. Your team can also add/remove/modify any rule to customize the intelligence to your exact needs.
With numerous successful deployments worldwide, we can provide case studies to help you build a business case for digital threat intelligence. Reach out to our team of experts to learn how Group-IB has improved security and provided ROI for organizations in any sector.
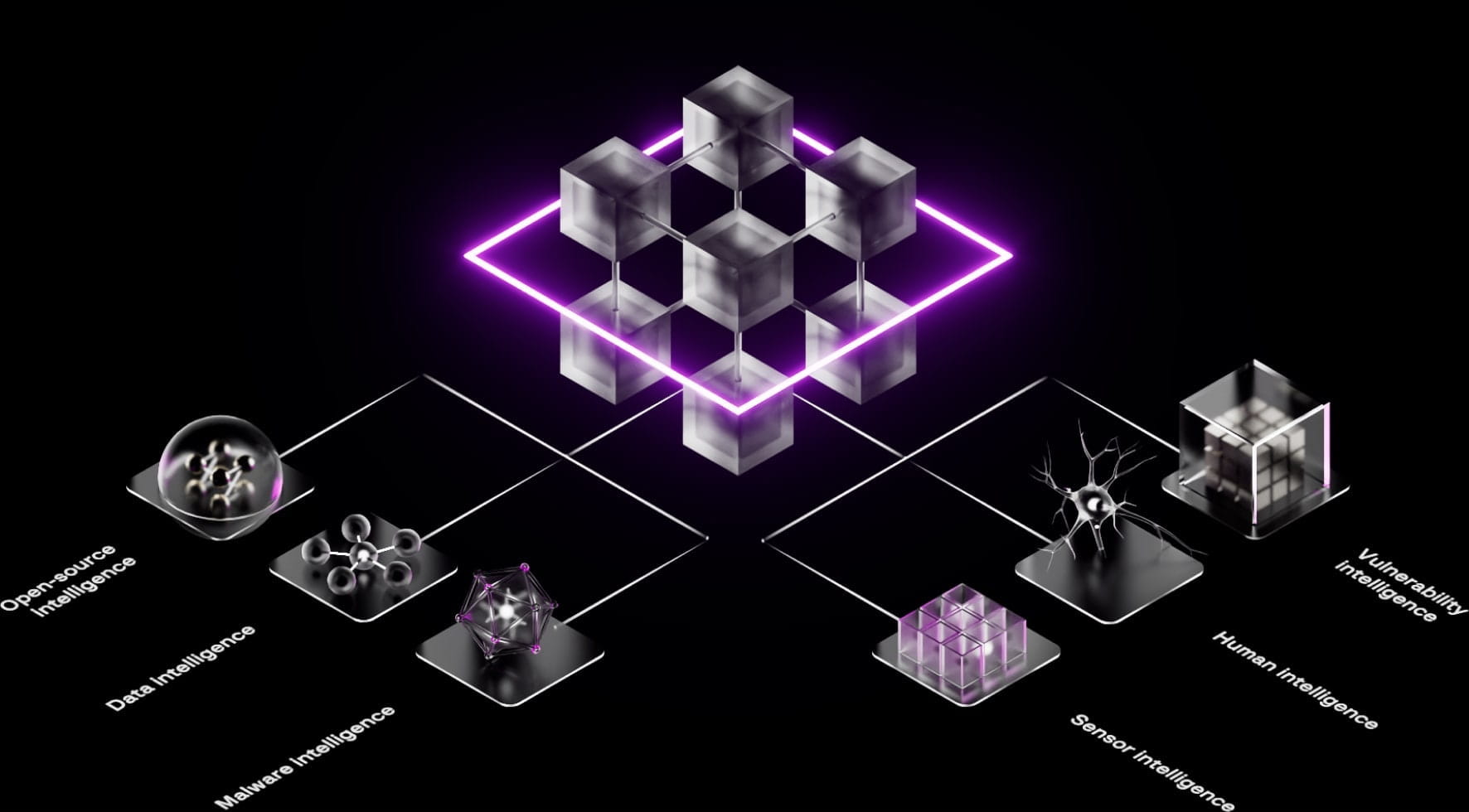
Our Threat Intelligence is powered by the Unified Risk Platform, which collects, correlates, and applies intelligence that is gathered from every function of Group-IB. This provides us with a uniquely diverse set of sources:
Malware intelligence
Data intelligence
Human intelligence
Sensor intelligence
Vulnerability intelligence
Open-source intelligence
When considering the ideal cyber threat intelligence platform for your organization, consider the features offered. This includes the variety of sources, integrated data aggregation and correlation capabilities, functionality for real-time monitoring and machine-readable reports, ease of integration with existing security operations, and opportunities for customization.
At Group IB, we stay at the cutting edge of threat intelligence technology by continually adding new intelligence sources, analytics techniques, and security integrations.