
Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.


Protect critical attack surfaces in your infrastructure, proactively hunt for adversaries, and respond in real time.

Get complete visibility over your security operations, including endpoints, servers, cloud workloads, emails, and networks

Maintain business process continuity and increase the value of existing security investments with a product that offers native integrations and a rapid full deployment

Automate routine tasks to free up resources and let ML algorithms make sense of enormous bodies of data so SOC personnel can respond to the threats that need to be addressed

Leverage proprietary technologies and global expertise to identify the sophisticated threats that would otherwise go undetected

Work with leading analysts in a shared environment. Expand your security team with managed detection, hunting, and response

Integrate siloed data sources throughout your environment to increase the value of each product while creating a security program that is greater than the sum of its parts

An independent evaluation from Forrester analyzed how Managed XDR impacts a customer’s revenue and savings, estimating a significant ROI for the business.
Built for enterprise SOC teams, Group-IB Managed XDR platform combines advanced technology with 24/7 expert oversight to help you stay ahead of evolving threats.
Graph
To start POC, simply request a demo by completing a form above. In most cases, you will need just to provide a number of end devices in your IT environment to clarify the scope, and POC is ready to start.
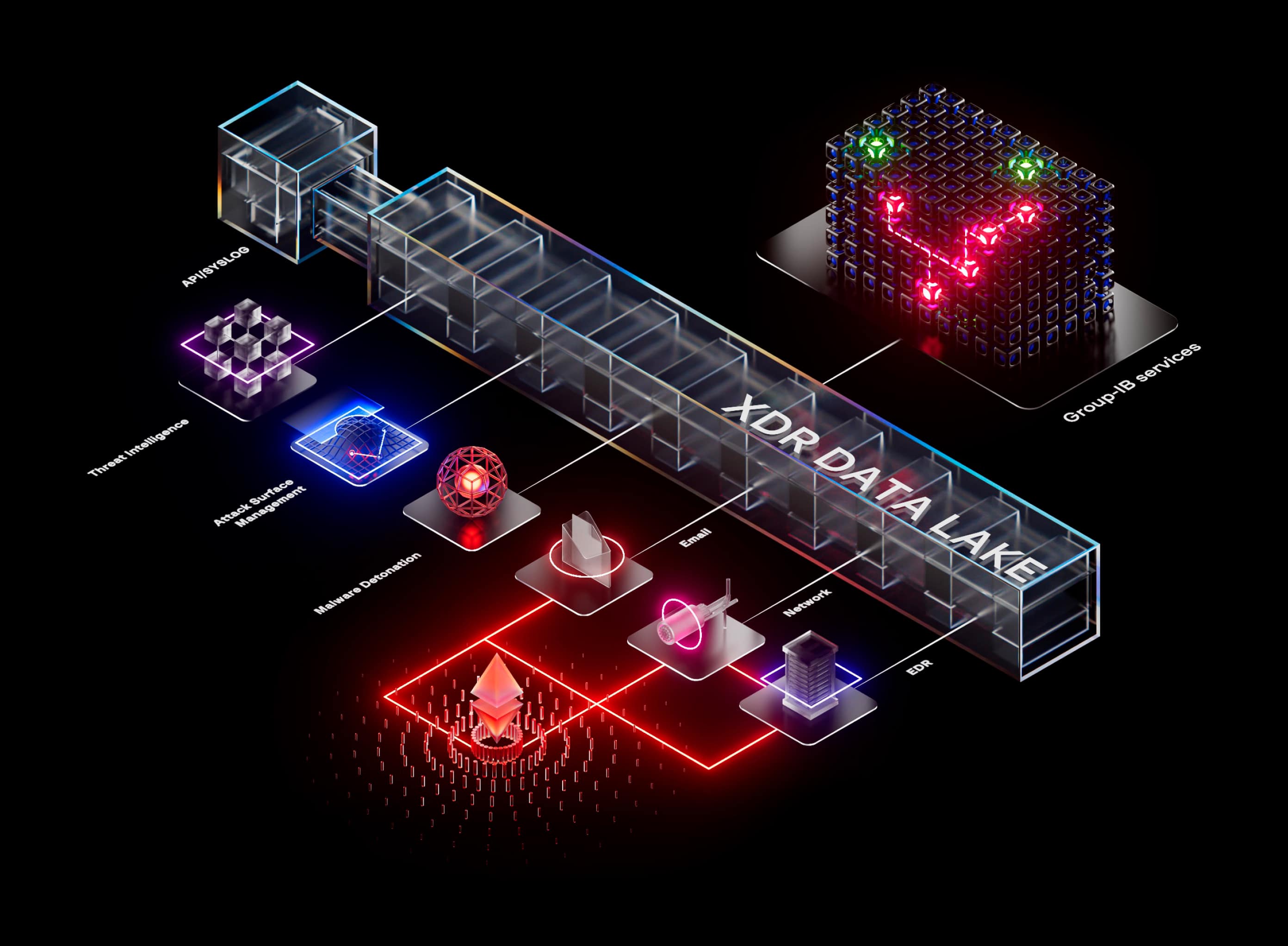
Extended Detection and Response (XDR) is a class of information security systems produced to proactively detect and respond to threats. XDR can help to optimize the threat hunting process and to accelerate the incident response process. Extended Detection and Response functions are available in automatic mode and work on different infrastructure levels.
Group-IB Managed XDR provides organizations with advanced detection and response capabilities with access to threat hunting and remediation through a single interface. The solution uses a combination of several best-in-class technologies and human-led expertise:
Group-IB’s provides managed XDR services with round-the-clock support in case of an incident, alert triage, and managed threat hunting activities.
Group-IB also offers a range of audit services, including penetration testing and red teaming, and DFIR services, including incident response and eDiscovery.
Group-IB continuously updates the intelligence used by Managed XDR to identify threats in real-time. Machine learning engines and analysts work to update and refine TTPs, IoCs, malware profiles and more with the latest insights as they are discovered.
The features and capabilities of Managed XDR are also regularly updated, approximately once a month Group-IB releases product updates with the enhancements and new features.
Yes, organizations that do not have the expertise or headcount to perform threat hunting can utilize Group-IB Managed XDR platform. Supported by highly-trained analysts, they help attribute threats, understand company-specific TTPs, and make recommendations for improving security posture.
The Managed XDR unified dashboard gathers telemetry from all sources, correlates alerts, and identifies threats using its machine learning engine. Security teams can easily test hypotheses and search for threats with intuitive search queries.
Yes, Managed XDR is routinely used for incident response. Customers, managed service providers, and Group-IB’s own teams use the solution to identify, respond and remediate threats. Organizations that do not have the expertise or headcount to perform incident response can utilize Group-IB’s managed service offering.
When hunting for threats Managed XDR automatically links detected TTPs, IoCs, and malware with threat actors, and provides insight into how they conduct attacks. These insights help teams attribute threats and identify false-positives.
Yes, Group-IB provides a range of out-of-the-box integrations with popular solutions such as SIEM. Flexible APIs are also available, enabling Managed XDR to integrate with any 3rd party tool, including custom-built dashboards.