Group-IB, a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime, announced today the launch of its new, free tool: Malware Reports. This innovative platform offers access to a continuously updated database of publicly available malware reports, allowing security professionals to gain critical insights into how malware behaves, evolves, and threatens organizations worldwide.
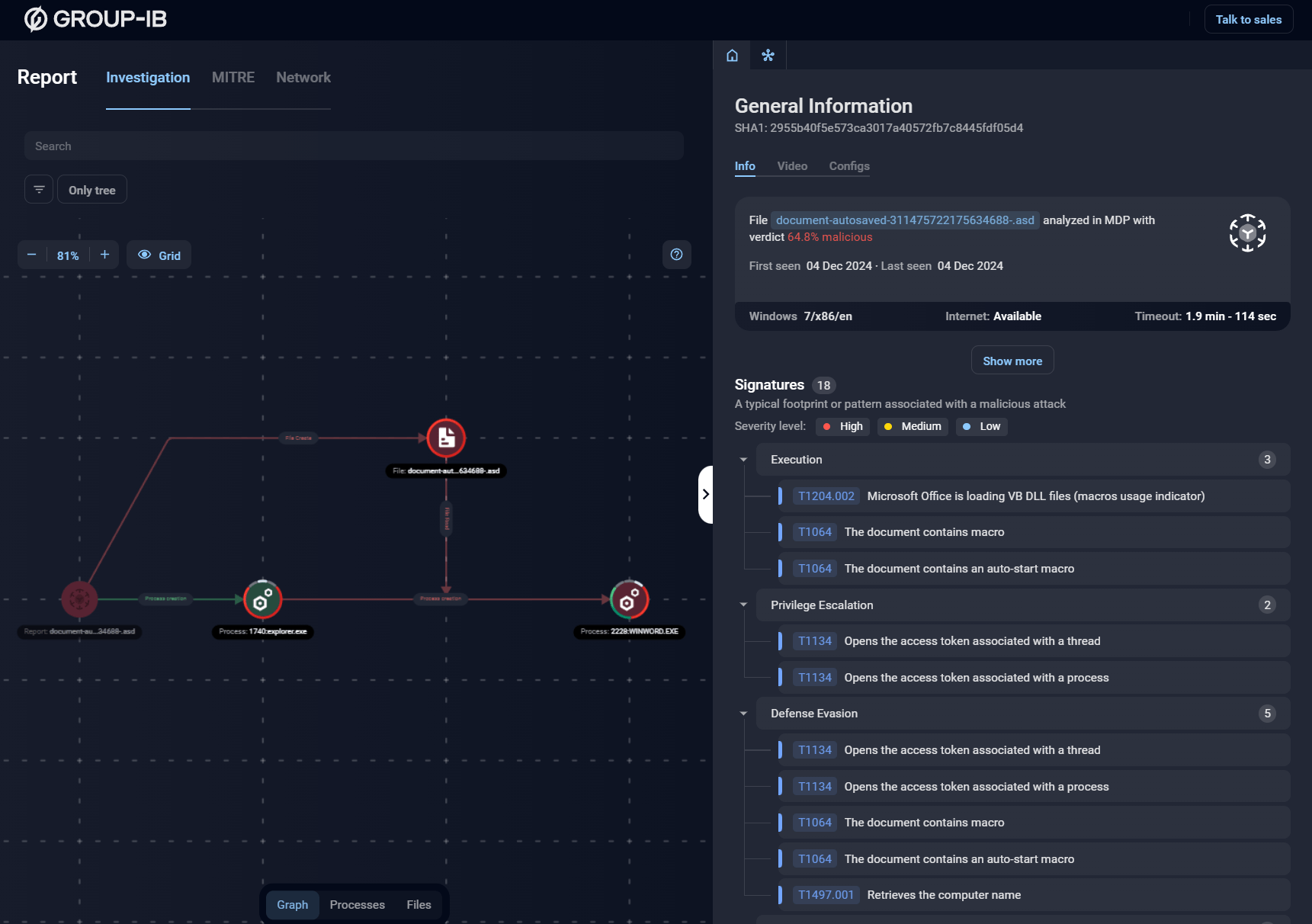
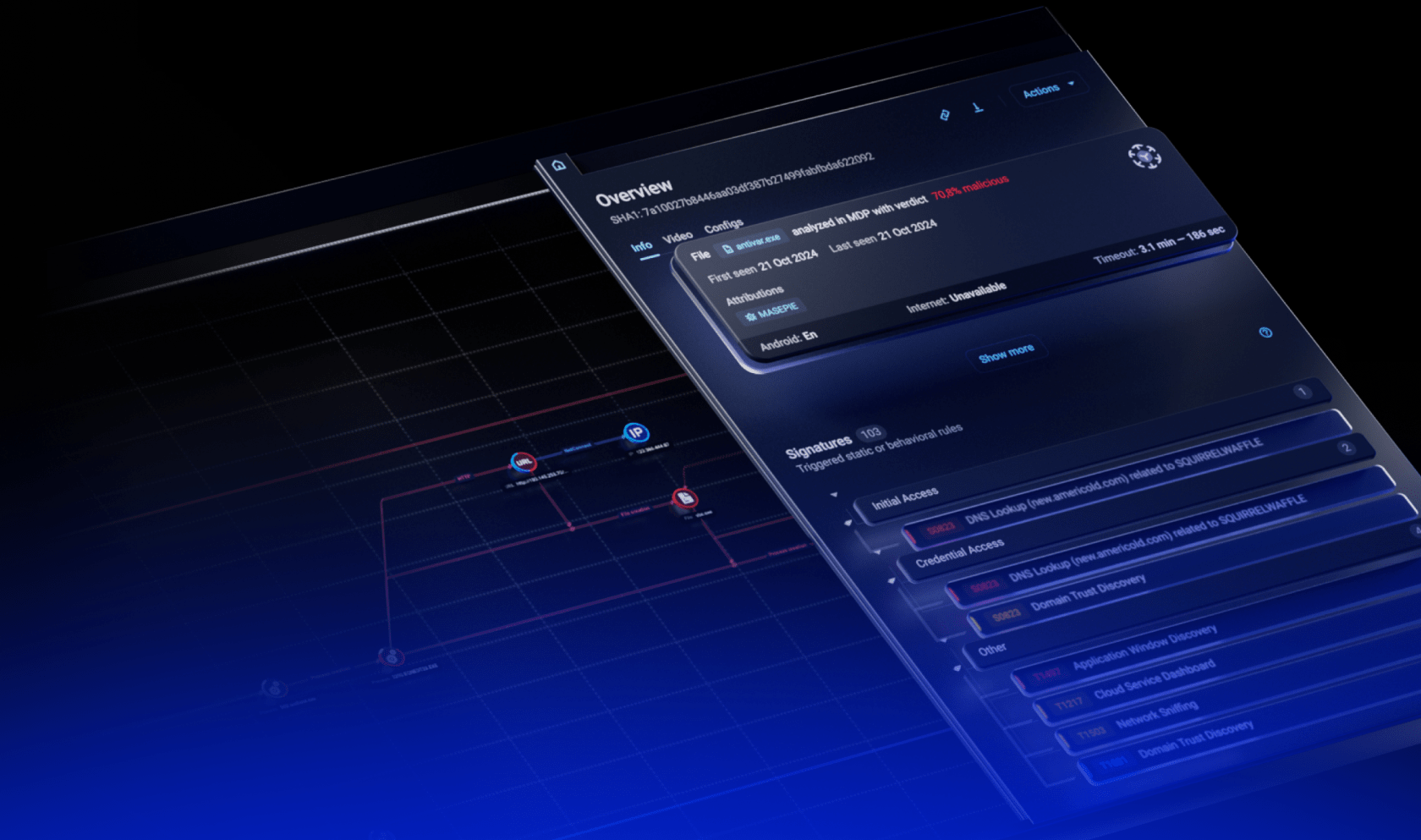
A screenshot of Group-IB’s new and free Malware Reports tool.
Leveraging the power of Group-IB’s Malware Detonation Platform, the Malware Reports tool is designed to help security teams automate malware analysis and focus on higher-priority tasks. With comprehensive reports that include in-depth behavioral analysis and techniques mapped to the MITRE ATT&CK framework, detailed process trees, indicators of compromise (IOCs), and network activity dumps, this resource provides a robust, easily accessible repository of intelligence for professionals at all levels.
“We understand that knowledge sharing is the foundation of effective cybersecurity. With our free Malware Reports tool, our goal is to equip professionals with the critical insights they need to understand how malware operates and stay one step ahead of adversaries. We are excited to announce the launch of our new and free Malware Reports tool, which provides access to a selection of our in-depth malware behavior analysis reports, generated by our advanced sandbox – Malware Detonation Platform. By making this powerful resource available, we aim to help the cybersecurity community enhance their defense strategies and protect against ever-evolving threats.”

CEO of Group-IB
Key Features of Malware Reports:
- Comprehensive Database: Access over continuously updated and detailed malware reports, dissected by Group-IB’s Malware Detonation Platform (advanced sandbox), to understand the intricacies of malware behavior.
- Behavioral Analysis: Each report provides in-depth behavioral analysis, going beyond simple file classification to reveal how malware behaves in different environments.
- Interactive Reports: Explore malware behavior through animated visualizations, offering a step-by-step breakdown of attack processes.
- MITRE ATT&CK® Framework: Every detected threat is mapped to the MITRE ATT&CK® framework, aligning malware behaviors with adversary tactics and techniques.
- Advanced Search and Filters: Search by file properties such as name, hash, or file type, and apply advanced filters to find malware by behavior, verdict, or specific characteristics.
- Historical Analysis: Compare current and historical threats using domains, IP addresses, or MITRE ATT&CK® technique IDs to identify patterns and strengthen defenses.
- Actionable Insights: View detailed insights to boost your knowledge, create Sigma and YARA rules, conduct threat hunting and attribution, and share reports with your team for improved coordination.
Group-IB’s free Malware Malware reports tool can greatly benefit a variety of professionals, including SOC analysts, threat hunters, reverse engineers, and malware researchers. SOC analysts can use the reports to enhance their ability to detect and respond to threats, while threat hunters can conduct in-depth research and proactively identify emerging threats before they impact the organization. Reverse engineers can analyze malware behavior through advanced visualizations to further their technical expertise. Malware researchers, on the other hand, can access continuously updated reports to track malware evolution and improve their threat intelligence.
To access the tool, please visit www.group-ib.com/tools/malware-reports.