Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.

Move away from traditional sandboxes. Access more than 2 million malware reports dissected by Group-IB’s Malware Detonation Platform and gain unparalleled insights into how malware behaves and evolves and how it threatens your organization
Group-IB’s Threat Intelligence team scours thousands of malware samples every day to detect emerging threats. The samples are analyzed using our advanced Malware Detonation Platform as part of Group-IB Managed XDR, which provides a complete view of the threat journey, from initial infection to the final payload
Our database containing over 2 million reports of public malware samples is available for free, helping you automate malware analysis and focus on higher-priority tasks. Each report includes detailed process trees, indicators of compromise, network activity dumps, and in-depth behavioral analysis.
Whether you're a SOC analyst, threat hunter, reverse engineer, or malware researcher, Group-IB’s database delivers actionable insights that will help you strengthen your defenses. Browse millions of reports and enhance your security posture.

Watching malware operate in real time hones your technical skills far better than just reading about how someone else reverse-engineered it.

New malware strains emerge all the time, making it challenging for security teams to stay up-to-date and defend against evolving threats.

Many platforms have unintuitive interfaces, which slows down security teams and increases the likelihood of overlooking critical insights.
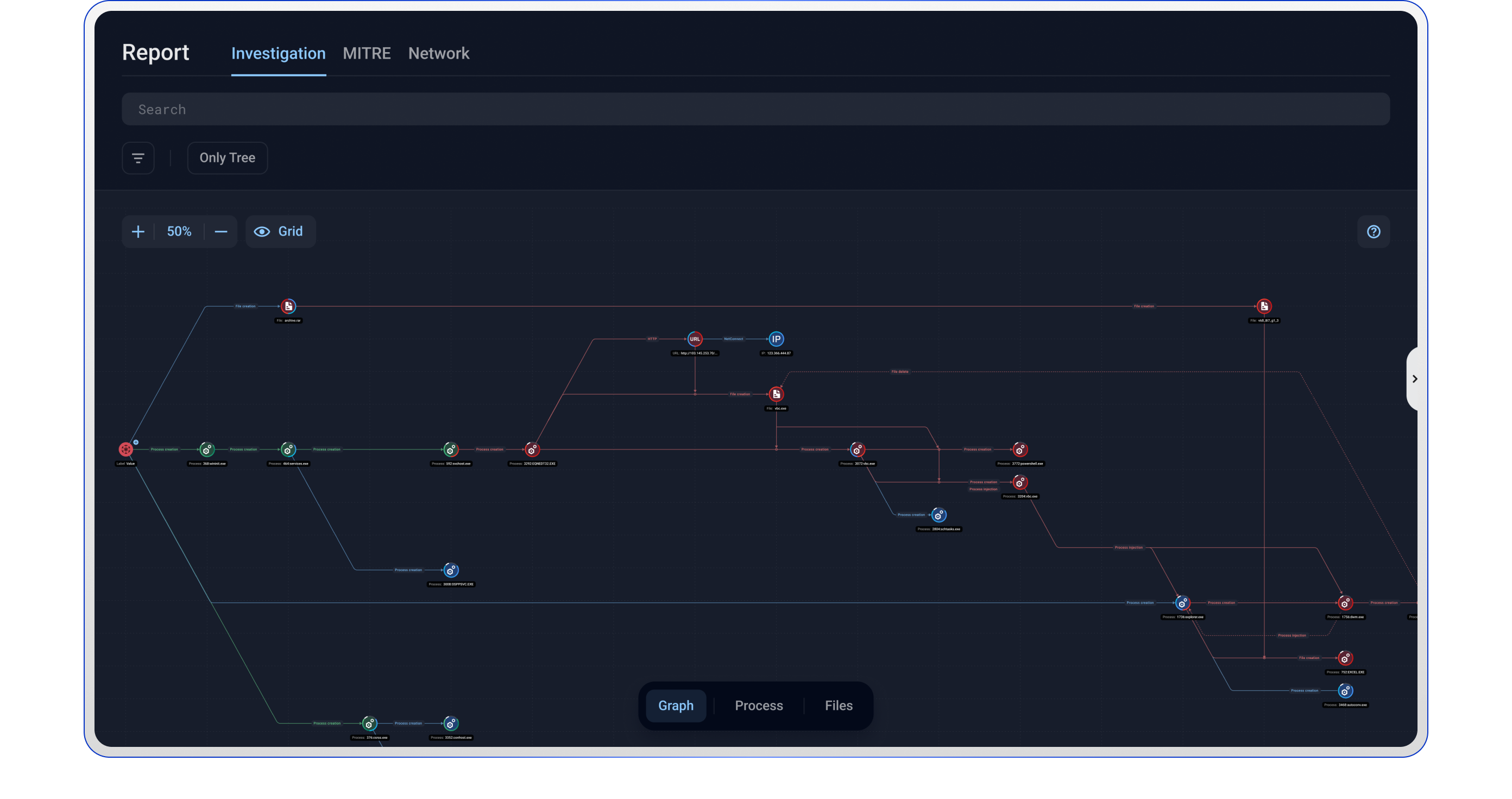
Group-IB’s Malware Detonation Platform does much more than merely identify good and bad files. It reveals how attacks unfold in real time and pinpoints which processes are executed, which files are created or modified, and what network connections are established. Malware Detonation Platform doesn’t just detect malware — it deceives attackers and encourages them to proceed with their attack, which reveals their full intentions and shows what could have happened if the threat wasn’t stopped.
Malware Detonation Platform offers in-depth behavioral analysis, beyond mere file classification
Each malware report includes an animated visualization of the attack process, helping you explore the malware’s behavior in detail
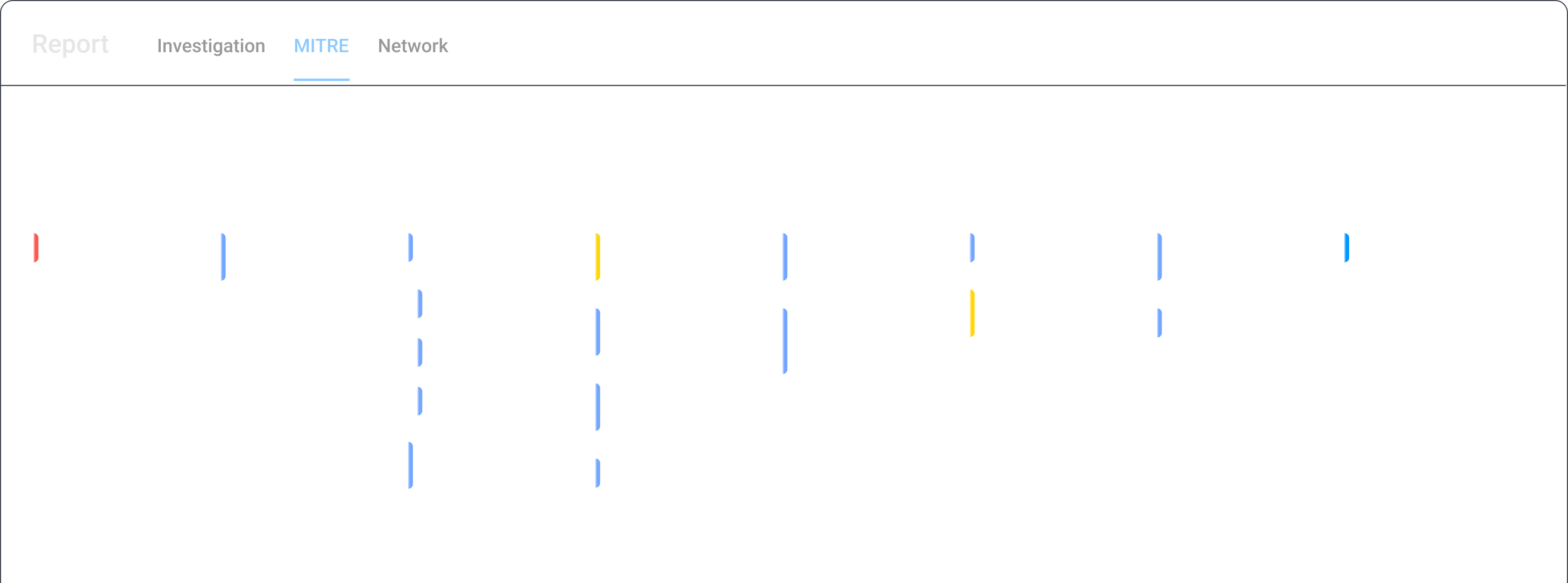
Every detected threat is mapped to the MITRE ATT&CK® framework
and aligns malware behavior with the tactics and techniques used by
the adversaries

Look up malware by name, hash, string, or file type

Search by behavior, verdict, and specifications

Compare historical and current threats using domains, IP addresses, or MITRE ATT&CK® technique IDs

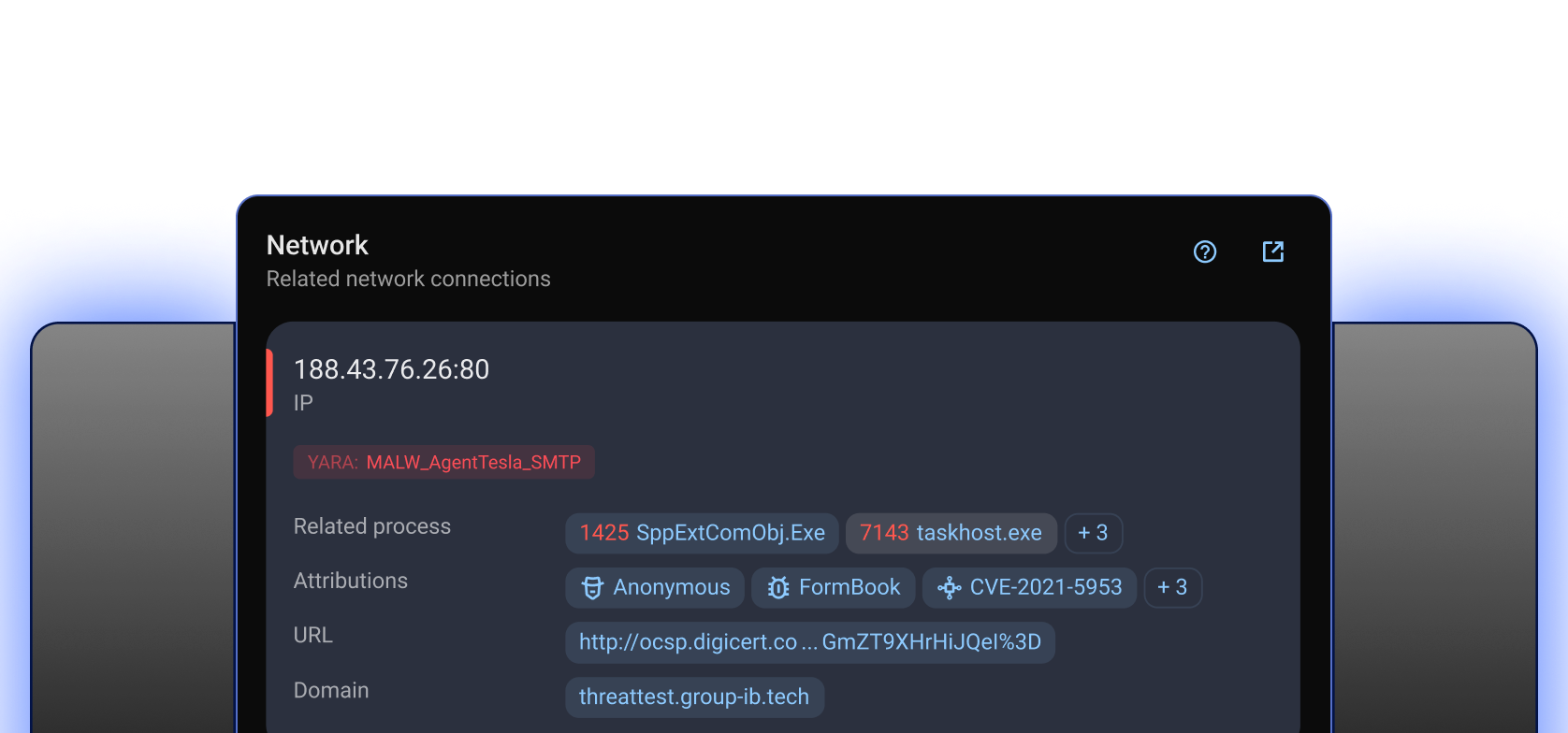

Discover how this spyware logs keystrokes and steals sensitive information
Find out how this stealer exfiltrates user data to its C&C server
Learn how this ransomware encrypts files and demands cryptocurrency in exchange for decryption
See how this remote administration tool is used to steal data and execute commands
Read about how this backdoor executes remote commands and exfiltrates data