Introduction
ShadowSyndicate is a malicious activity cluster that unites a wide set of campaigns based on infrastructure overlaps. Despite the huge number of servers involved, the threat actor relies on OpenSSH and usually uses one SSH key for all of them. But each pair of SSH keys is unique, so the presence of the public key on the server is usually associated with a specific person or group that has access to it. Because ShadowSyndicate’s SSH fingerprints are known to be used with a large number of servers, it allows researchers to spot the links and analyze such clusters. ShadowSyndicate’s infrastructure is always connected to various malware families and has links to different ransomware groups or affiliate programs.
After initial discovery by Group-IB in 2023, the threat actor continued to orchestrate their infrastructure using the same SSH fingerprint on multiple servers. Recently, Intrinsec researchers have discovered a new SSH fingerprint attributing it to ShadowSyndicate.
The presence of similar attack frameworks, malware and connections to multiple Ransomware-as-a-Service (RaaS) brands – almost everything in the adversary’s behavior strongly aligns with previously observed campaigns. Moreover, attackers even continued to rely on a highly similar set of the hosting providers.
As ShadowSyndicate’s modus operandi started to seem clear and predictable, Group-IB researchers have discovered a new, unreported trend in their behavior: the threat actor tends to reuse previously employed infrastructure, sometimes rotating various SSH keys across their servers. If such technique is performed correctly, the infrastructure is transferred subsequently, much like in a legitimate scenario, when a server goes to a new user. This transition leaves some room for reasonable doubt in the connection between the “old” and “new” owner. But if something goes wrong and the presence of these keys overlaps, it reveals the link. And ShadowSyndicate has made a few OPSEC inaccuracies that allowed Group-IB to spot and prove such connections.
This blog is aimed at sharing some insights about such undocumented developments in ShadowSyndicate behavior, provide analysis of infrastructure related to newly discovered SSH fingerprints and highlight new malicious clusters related to that infrastructure. It is based on data from Group-IB telemetry, public sandboxes and other open sources.
Yet, there still is a need to establish ShadowSyndicate’s true status. According to Group-IB intelligence, evidence leads to two main theories explaining a wide set of tools and methods. Either the threat actor may be an Initial Access Broker (IAB) or they may provide bulletproof hosting services to cybercriminals.
We would like to thank the Intrinsec team for their efforts and contributions to the research of ShadowSyndicate. Their data was one of the reasons the current analysis was initiated.
Key Discoveries
- Confirmed 2 additional SSH fingerprints used by ShadowSyndicate.
- ShadowSyndicate continues using the same SSH fingerprints on multiple servers.
- New technique discovered: ShadowSyndicate tends to transfer servers between their SSH clusters.
- At least 20 servers were used as C2 for different frameworks.
- ShadowSyndicate continues to be associated with toolkits including Cobalt Strike, MetaSploit, Havoc, Mythic, Sliver, AsyncRAT, MeshAgent and Brute Ratel.
- ShadowSyndicate’s infrastructure can be associated with various groups and affiliates of ransomware programs.
- Analyzed part of the ShadowSyndicate cluster can be attributed to Cl0p, ALPHV/BlackCat, Black Basta, Ryuk and Malsmoke activities.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
Group-IB Threat Intelligence Portal: ShadowSyndicate
Group-IB customers can access our Threat Intelligence portal for more information about ShadowSyndicate.
Threat Actor Profile
When the Keys Match
First seen in 2022, the infamous SSH fingerprint 1ca4cbac895fc3bd12417b77fc6ed31d became a gold mine for the research because of its connections to a variety of malicious servers. Back then, it formed the malicious activity cluster which would be known later as ShadowSyndicate. Group-IB researched those activities and published an initial blog titled “Dusting for fingerprints: ShadowSyndicate, a new RaaS player?” in 2023. Later, in 2025, the Intrinsec researchers reported another SSH fingerprint 081d96a941fa72747b5cfca5e6b2f1b9 having similar behaviors to the one initially discovered. The abovementioned infrastructure formed the basis of the dataset reviewed during current analysis.
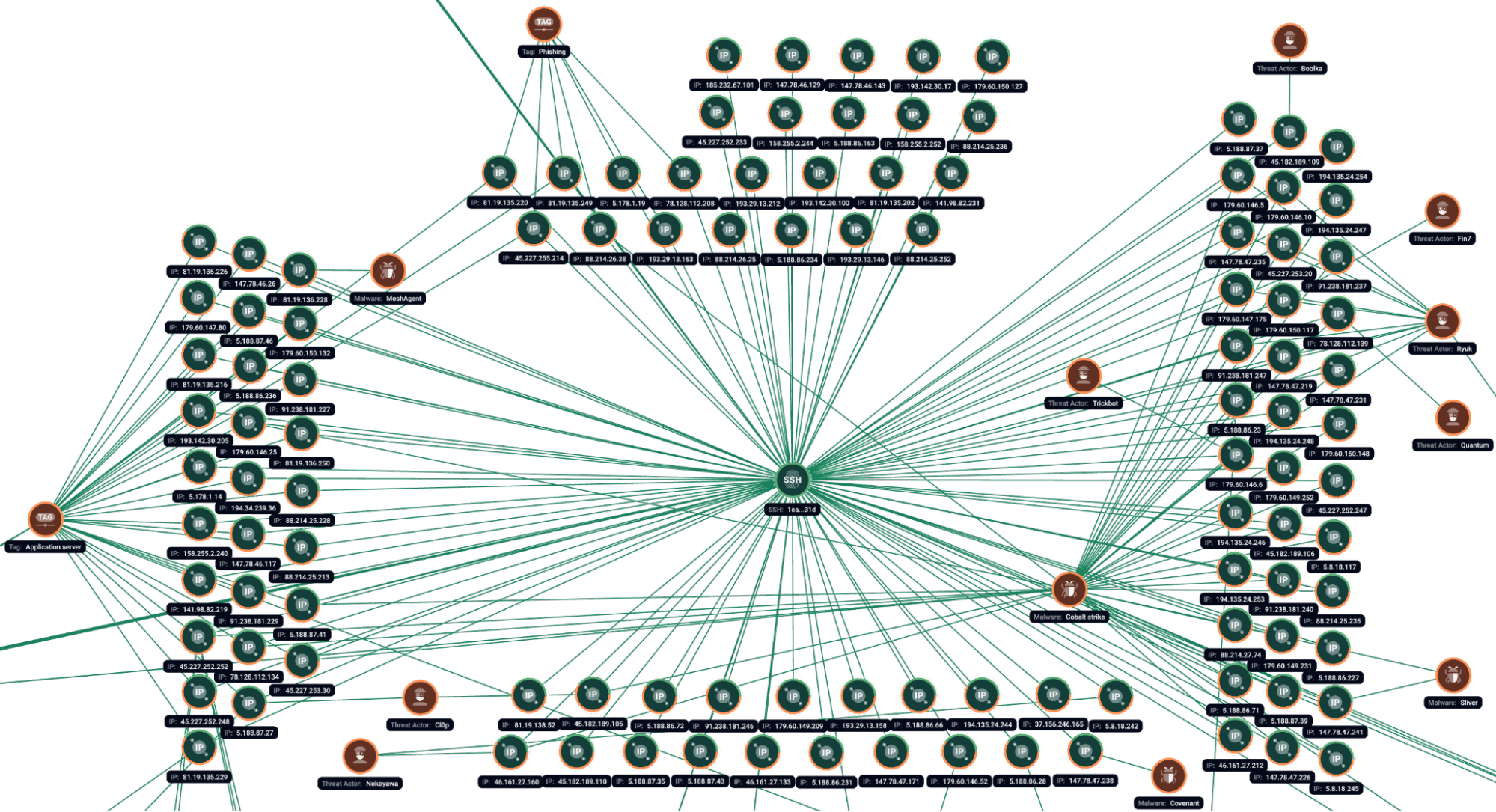
Figure 1.1. Group-IB Graph analysis of the network infrastructure related to the SSH fingerprint 1ca4cbac895fc3bd12417b77fc6ed31d.
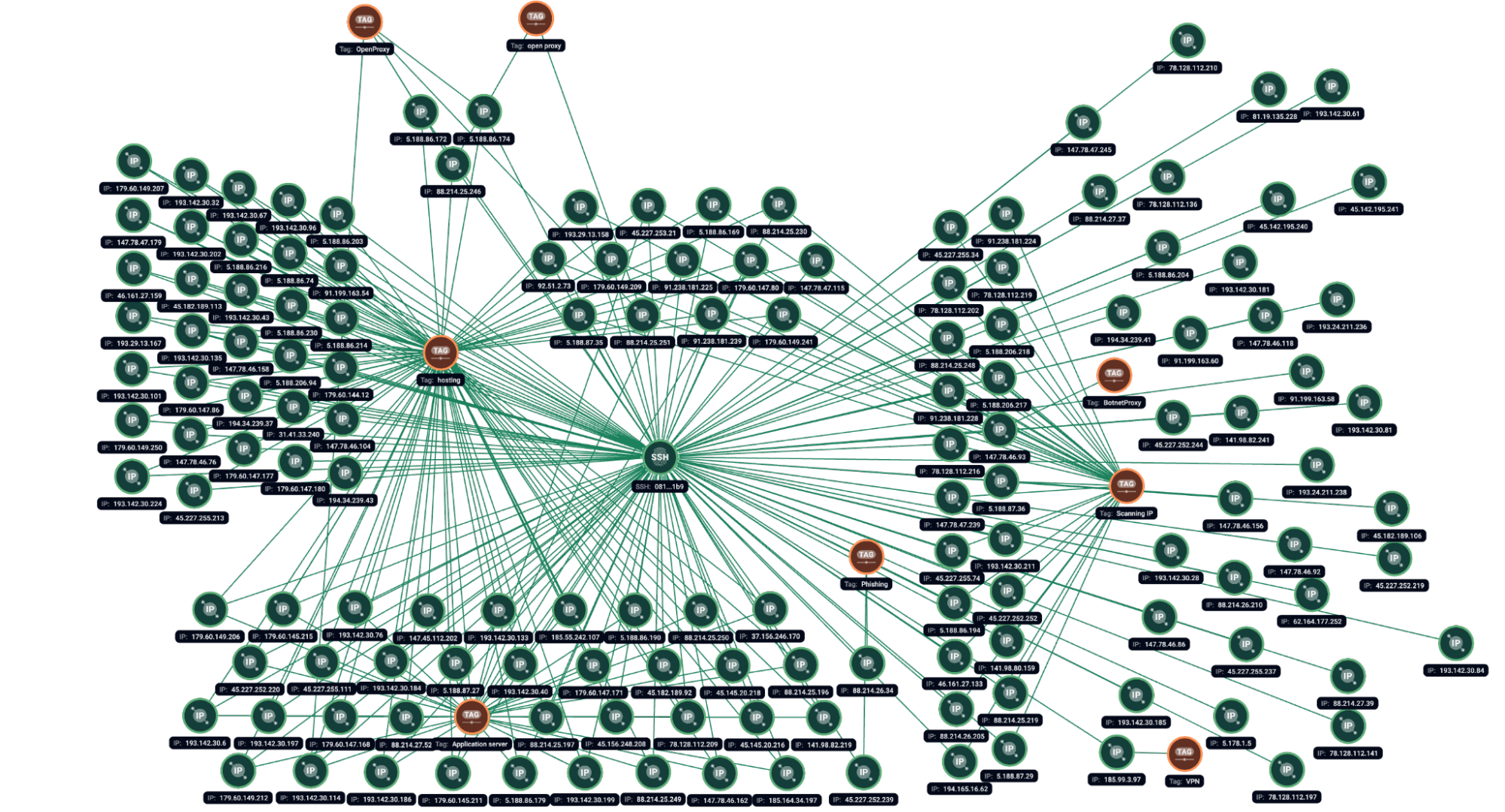
Figure 1.2. Group-IB Graph analysis of the network infrastructure related to the SSH fingerprint 081d96a941fa72747b5cfca5e6b2f1b9.
Based on new research, Group-IB has identified several additional SSH fingerprints that were reused across multiple servers. Suspicions were raised by the fact that most of these fingerprints were seen either shortly prior or not longer after ones provenly belonging to ShadowSyndicate. Among such occurrences, we have found examples of their simultaneous presence on part of known servers, which became evidence for further attribution to ShadowSyndicate clusters and reason for deeper analysis. This is a technique that was not previously reported to be employed by ShadowSyndicate.
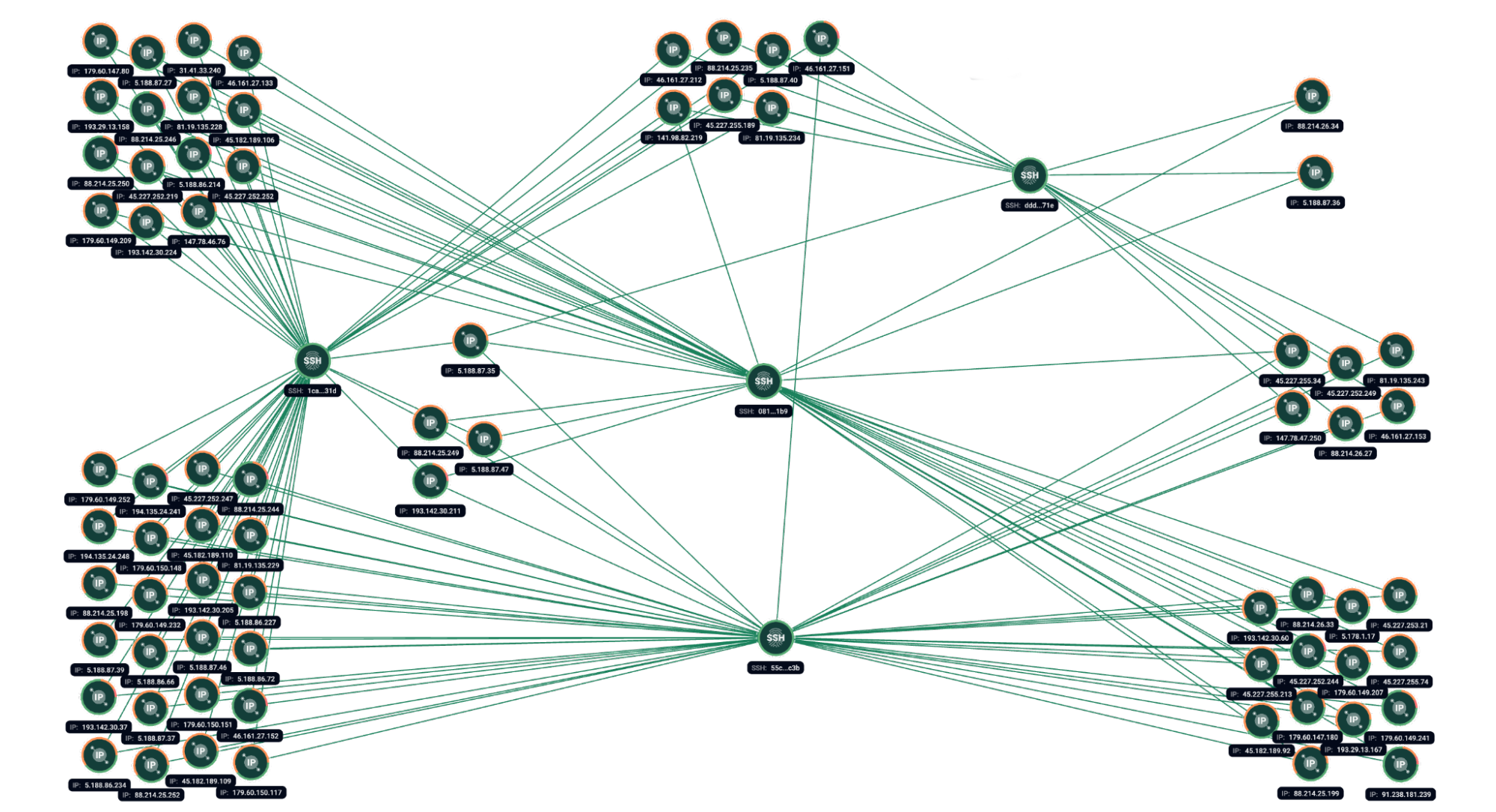
Figure 2. Group-IB Graph analysis of the network infrastructure sharing common SSH fingerprints (optimized).
Each of the discovered SSH fingerprints formed clusters of servers similar to the ones observed before. Further analysis of the related IP addresses has revealed connections to various threat actors and traces of different attack frameworks and malware. Some servers were also detected in past known attacks.
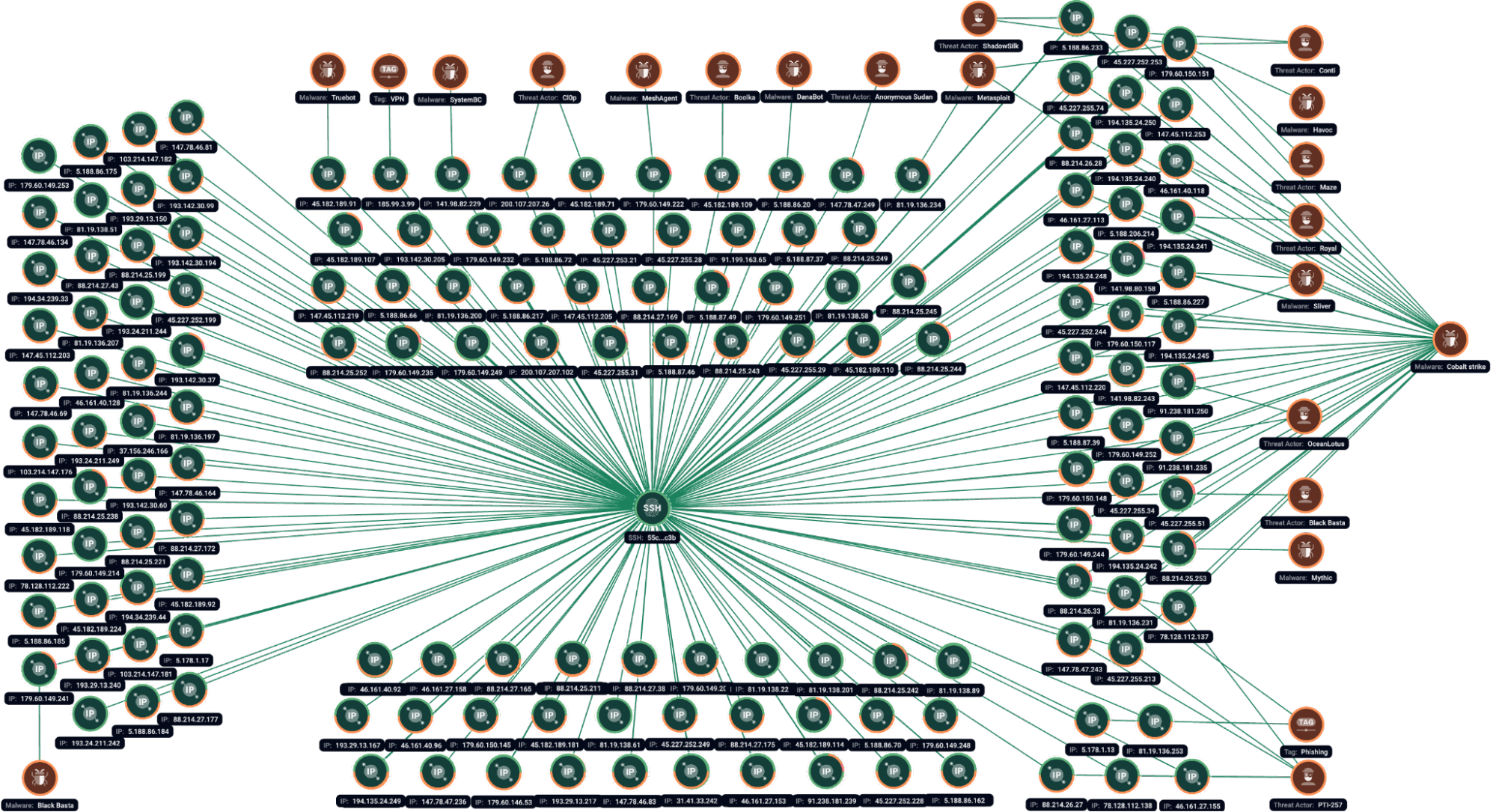
Figure 3.1. Group-IB Graph analysis of the network infrastructure related to the SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
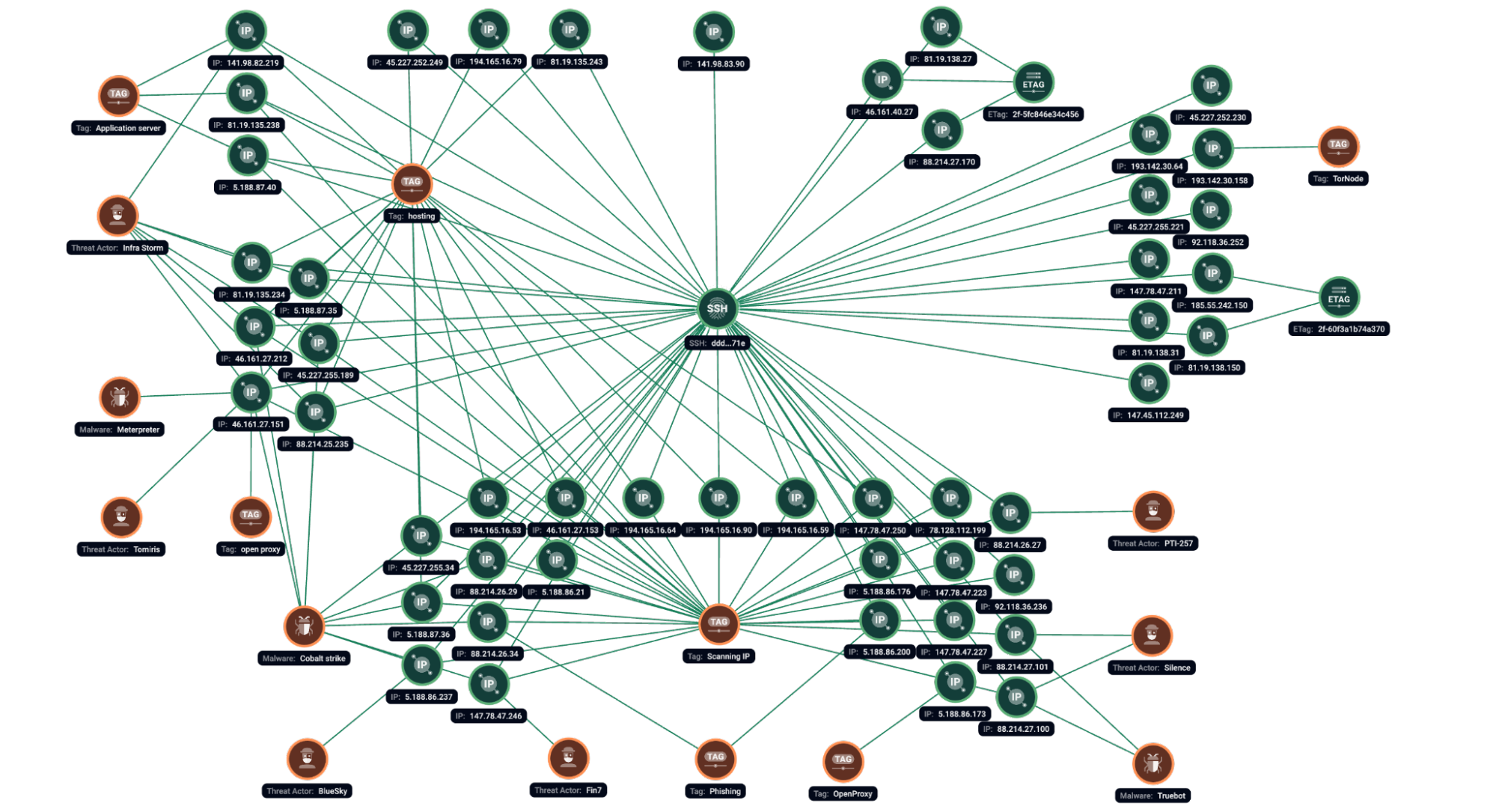
Figure 3.2. Group-IB Graph analysis of the network infrastructure related to the SSH fingerprint ddd9ca54c1309cde578062cba965571e.
In addition to familiar toolsets – Cobalt Strike, Metasploit, Havoc and Brute Ratel – other tools and malware used by the attackers include similar open source instruments like Mythic and Sliver (more on these below).
The further part of this research will mostly focus on analysis of clusters related to the two newly confirmed fingerprints:
- SSH ddd9ca54c1309cde578062cba965571e
- SSH 55c658703c07d6344e325ea26cf96c3b
Tools Identified
Analysis of the discovered infrastructure has shown signs of the following tools associated with the attacker. While most of the tools and attributions described in this chapter may be repetitions of previously discovered ones, it is key to highlight the consistency of ShadowSyndicate’s nature, and a necessity to understand a wider picture because these pieces may lead to a complete breakdown of the threat actor or exploration of new clusters, like it was in the Boolka research.
Cobalt Strike
Cobalt Strike is a known commercial red-team framework with post-exploitation modules frequently used by legitimate red teams and widely abused by threat actors. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has found traces of Cobalt Strike on 194.165.16[.]64 server at the same time with SSH fingerprint ddd9ca54c1309cde578062cba965571e.
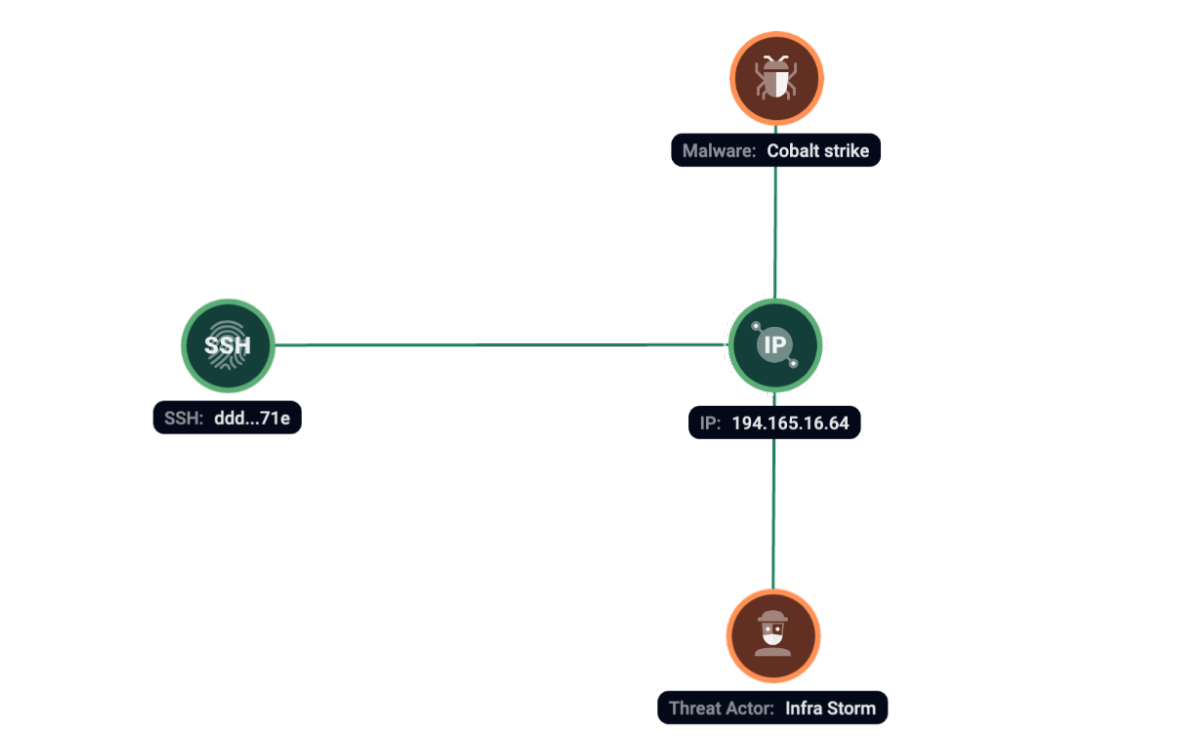
Figure 4. Group-IB Graph analysis of the network infrastructure related to Cobalt Strike.
Cobalt Strike was also seen on the following servers:
| IP address |
| 194.165.16[.]64 |
| 194.135.24[.]245 |
| 194.165.16[.]95 |
| 147.78.47[.]221 |
| 141.98.82[.]243 |
| 194.135.24[.]240 |
| 194.135.24[.]250 |
| 194.165.16[.]57 |
| 45.227.252[.]253 |
| 46.161.40[.]118 |
| 194.165.16[.]59 |
| 88.214.26[.]33 |
| 88.214.26[.]31 |
| 147.45.112[.]220 |
| 147.78.47[.]246 |
MetaSploit
MetaSploit is an open-source exploitation framework with exploit modules and payloads. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has found traces of MetaSploit on 147.45.112[.]220 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
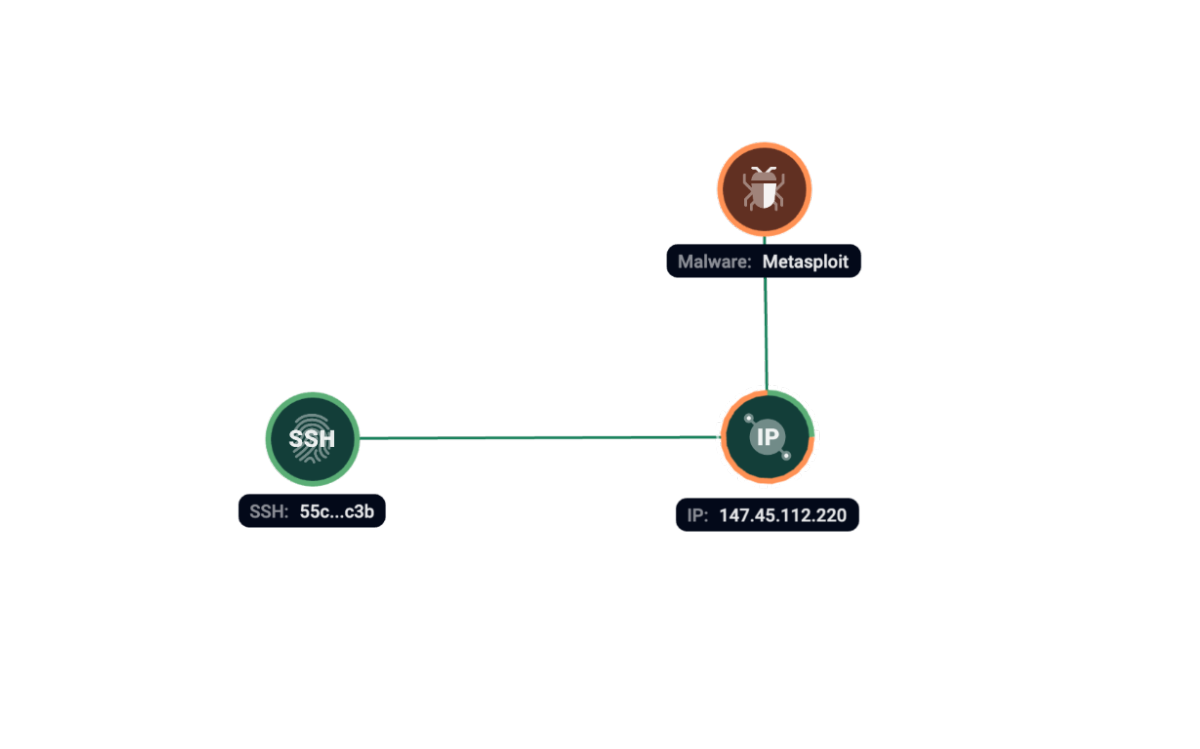
Figure 5. Group-IB Graph analysis of the network infrastructure related to MetaSploit.
MetaSploit was also seen on the following servers:
| IP address |
| 147.45.112[.]220 |
| 46.161.27[.]151 |
Havoc
Havoc is an open-source post-exploitation C2 framework available on GitHub. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has found traces of Havoc on server 78.128.112[.]209 at the same time with SSH fingerprint 081d96a941fa72747b5cfca5e6b2f1b9.
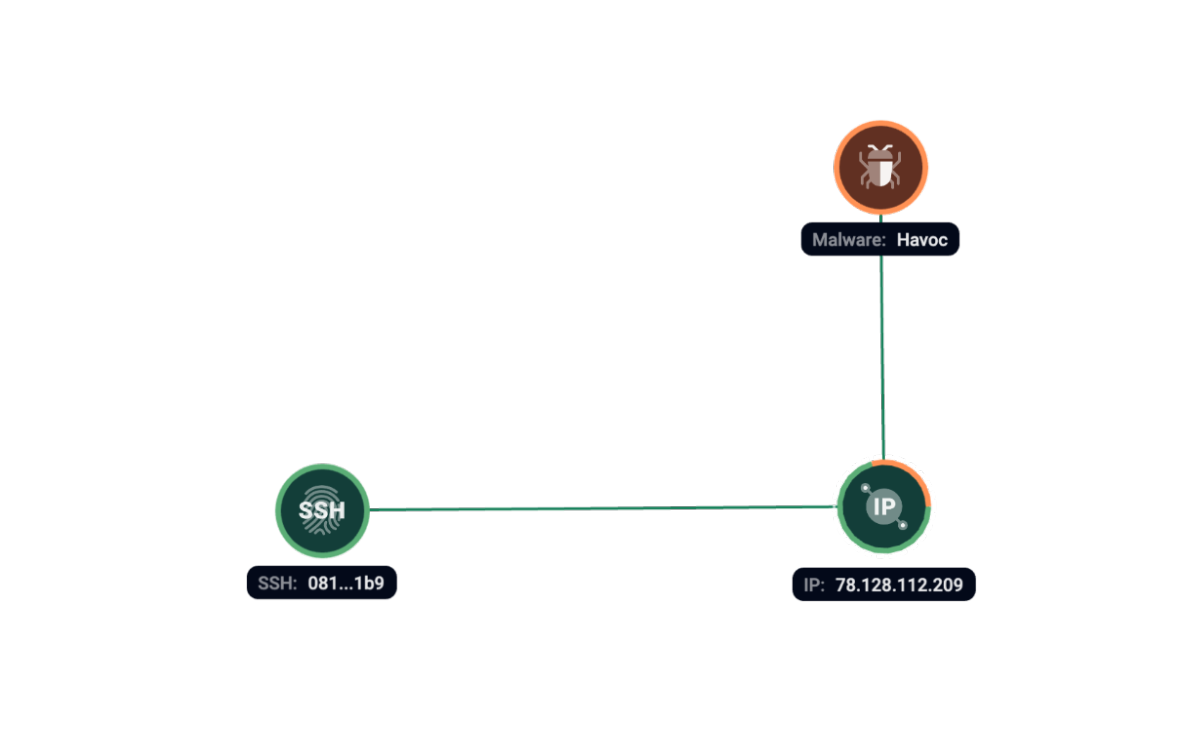
Figure 6. Group-IB Graph analysis of the network infrastructure related to Havoc.
Havoc was seen on the following server:
| IP address |
| 78.128.112[.]209
|
Mythic
Mythic is an open source cross-platform post-exploitation framework for red teaming. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has found traces of Mythic on 88.214.25[.]253 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
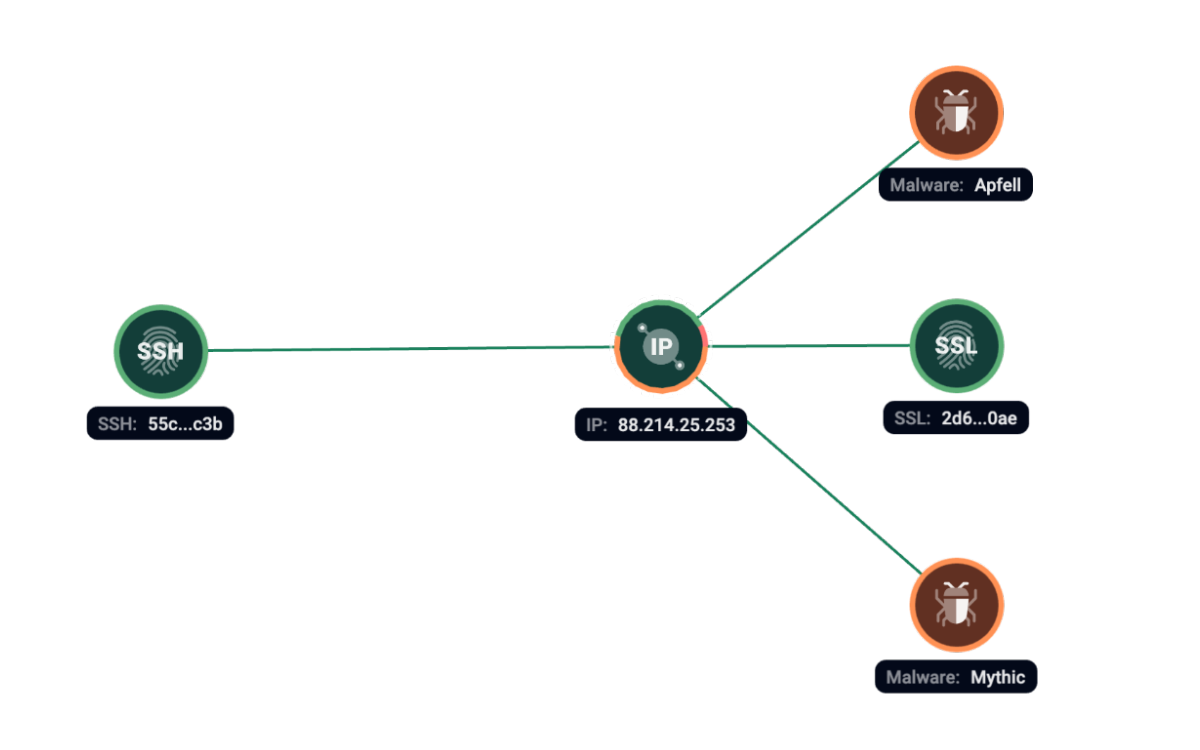
Figure 7. Group-IB Graph analysis of the network infrastructure related to Mythic.
Mythic was seen on the following server:
| IP address |
| 88.214.25[.]253 |
Sliver
Sliver is an open-source penetration testing tool written in Go language. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has detected a Silver certificate on 194.135.24[.]245 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
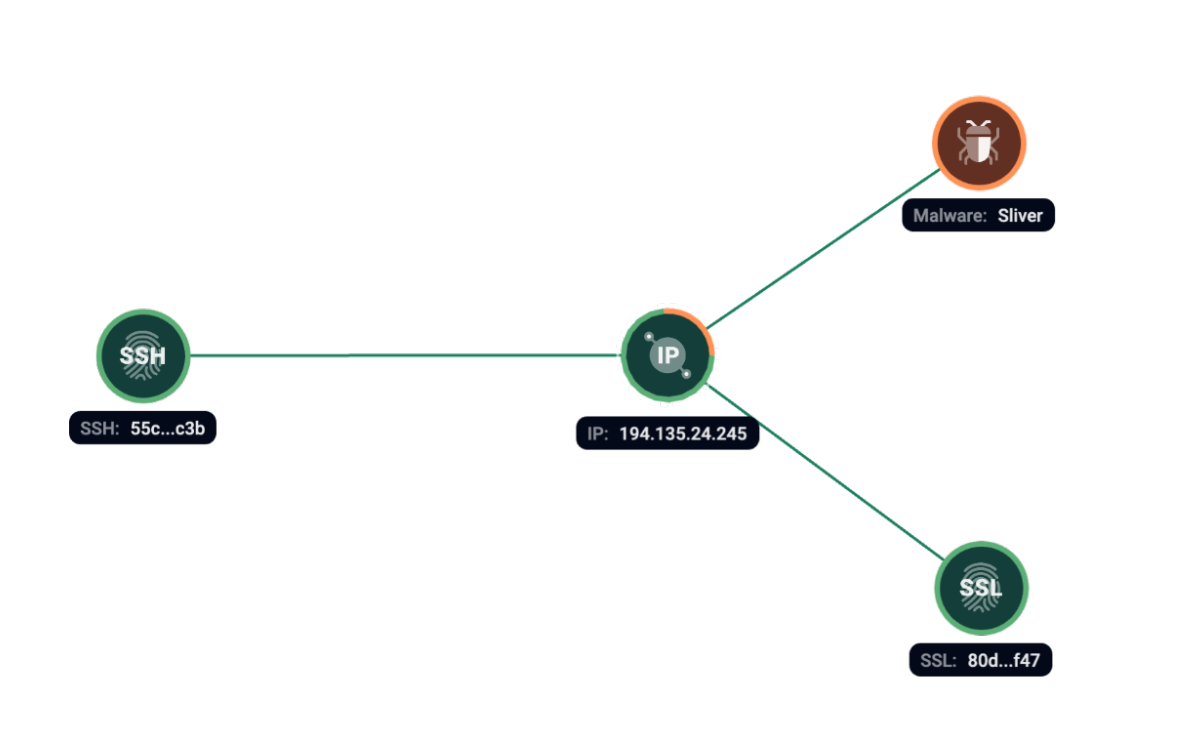
Figure 8. Group-IB Graph analysis of the network infrastructure related to Sliver.
Sliver was seen on the following server:
| IP address |
| 194.135.24[.]245 |
AsyncRAT
AsyncRAT is an open-source RAT available on GitHub. Group-IB customers can find more information on our platform.
We have observed AsyncRAT samples (SHA1 543c114c1a399697a1bf2a194e2e62db4f64d9c8 and SHA1 df77f2ca72c82673334b4127fd881de4dc09abe2) uploaded to VirusTotal and contacting with 5.188.87[.]37 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
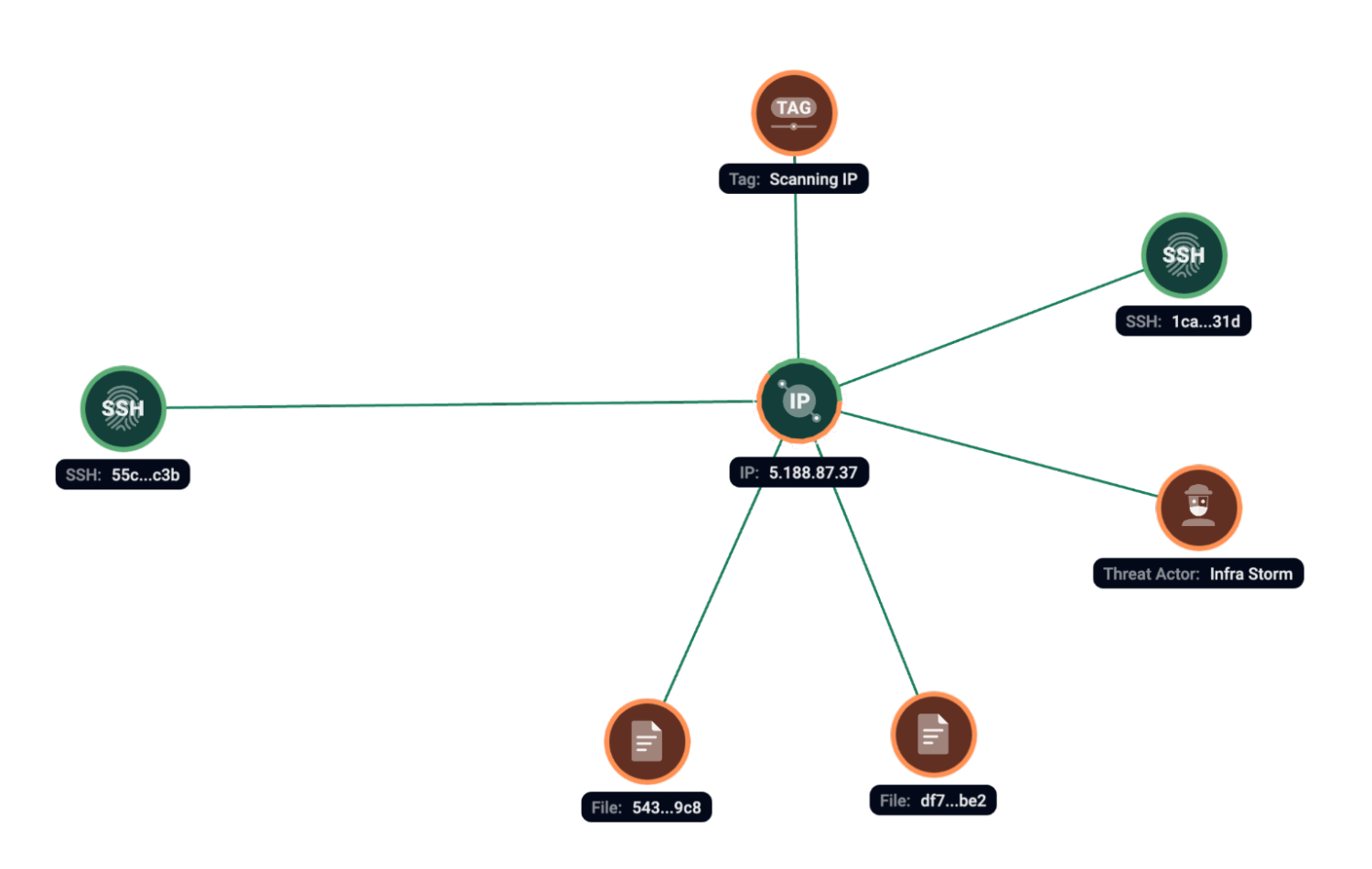
Figure 9. Group-IB Graph analysis of the network infrastructure related to AsyncRAT.
Based on our research Sliver was seen on the following server:
| IP address |
| 5.188.87[.]37 |
MeshAgent
MeshAgent is the software that runs on remote devices and connects to the MeshCentral server to allow for remote device management. This agent is compiled for Windows, many different Linux distributions, macOS and FreeBSD. Group-IB customers can find more information on our platform.
MeshAgent has been observed on 179.60.149[.]222 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
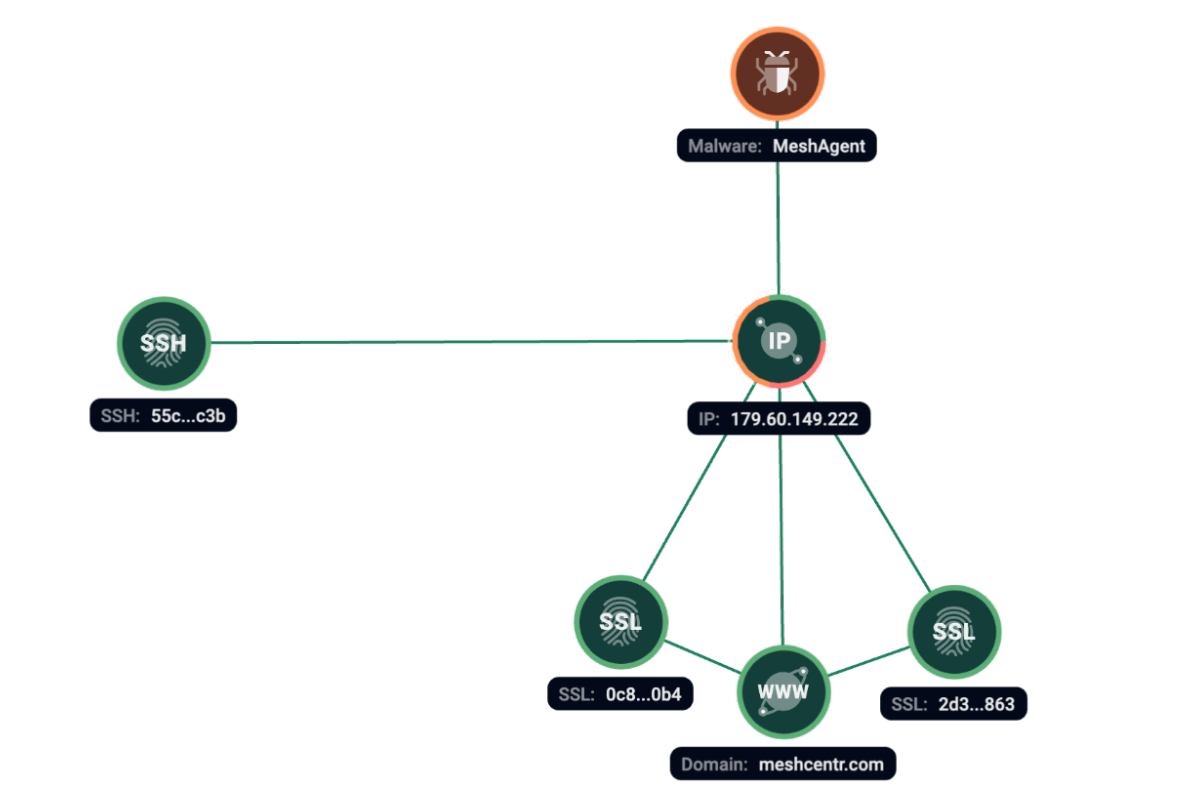
Figure 10. Group-IB Graph analysis of the network infrastructure related to MeshAgent.
MeshAgent was seen on the following server:
| IP address |
| 179.60.149[.]222 |
Brute Ratel
Brute Ratel C4 is a commercial red-teaming framework with advanced evasion techniques. Group-IB customers can find more information on our platform.
Group-IB Threat Intelligence has found traces of Brute Ratel – SSL Certificate – on server 193.24.211[.]238 one day prior SSH fingerprint 081d96a941fa72747b5cfca5e6b2f1b9. Due to the absence of simultaneous presence, but visible within a short enough period to reasonably be considered a margin in the scan results, we recommend treating this particular connection with low confidence.
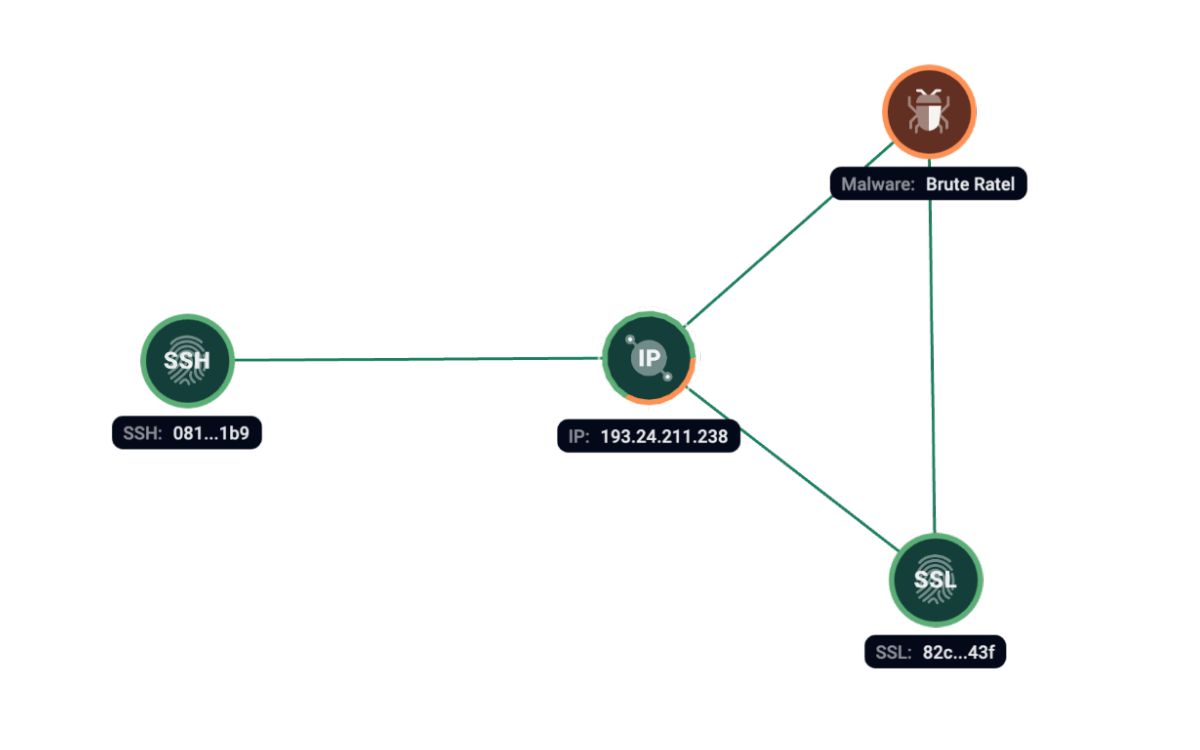
Figure 11. Group-IB Graph analysis of the network infrastructure related to Brute Ratel.
Brute Ratel was seen on the following server:
| IP address |
| 193.24.211[.]238 |
Connections to Other Threat Clusters
Besides indications of various tools and malware families running on, or connecting to ShadowSyndicate infrastructure, Group-IB researchers have also observed samples belonging to various ransomware affiliate programs.
Cl0p/Truebot
Cl0p – is the cybercrime group, which used Cl0p ransomware for attacks. Clop ransomware was discovered in February 2019. In 2023, Truebot was also detected in Cl0p’s attacks. Group-IB customers can find more information on our platform.
According to Group-IB telemetry, we have seen server 200.107.207[.]26, at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b, used by Cl0p in their campaigns with moderate to high confidence.
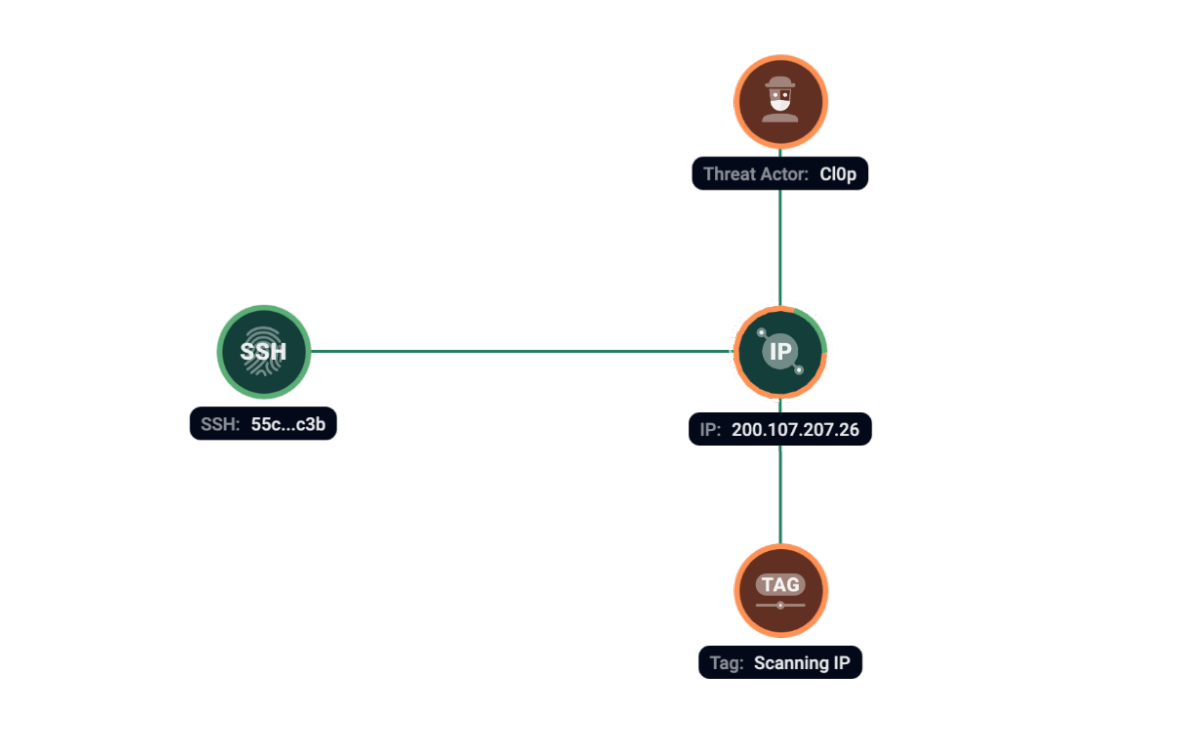
Figure 12. Group-IB Graph analysis of the network infrastructure related to Cl0p/Truebot.
Cl0p/Truebot was seen on following servers:
| IP address |
| 200.107.207[.]26 |
| 45.182.189[.]71 |
ALPHV/BlackCat
ALPHV (also known as BlackCat) is a ransomware operator group discovered in December 2021. ALPHV ransomware is written in Rust and uses AES or ChaCha to encrypt the victim’s data. Group-IB customers can find more information on our platform.
According to our telemetry, we have seen server 194.165.16[.]64; at the same time with SSH fingerprints ddd9ca54c1309cde578062cba965571e, 55c658703c07d6344e325ea26cf96c3b and 1ca4cbac895fc3bd12417b77fc6ed31d; used by ALPHV/BlackCat in their campaigns with moderate to high confidence.
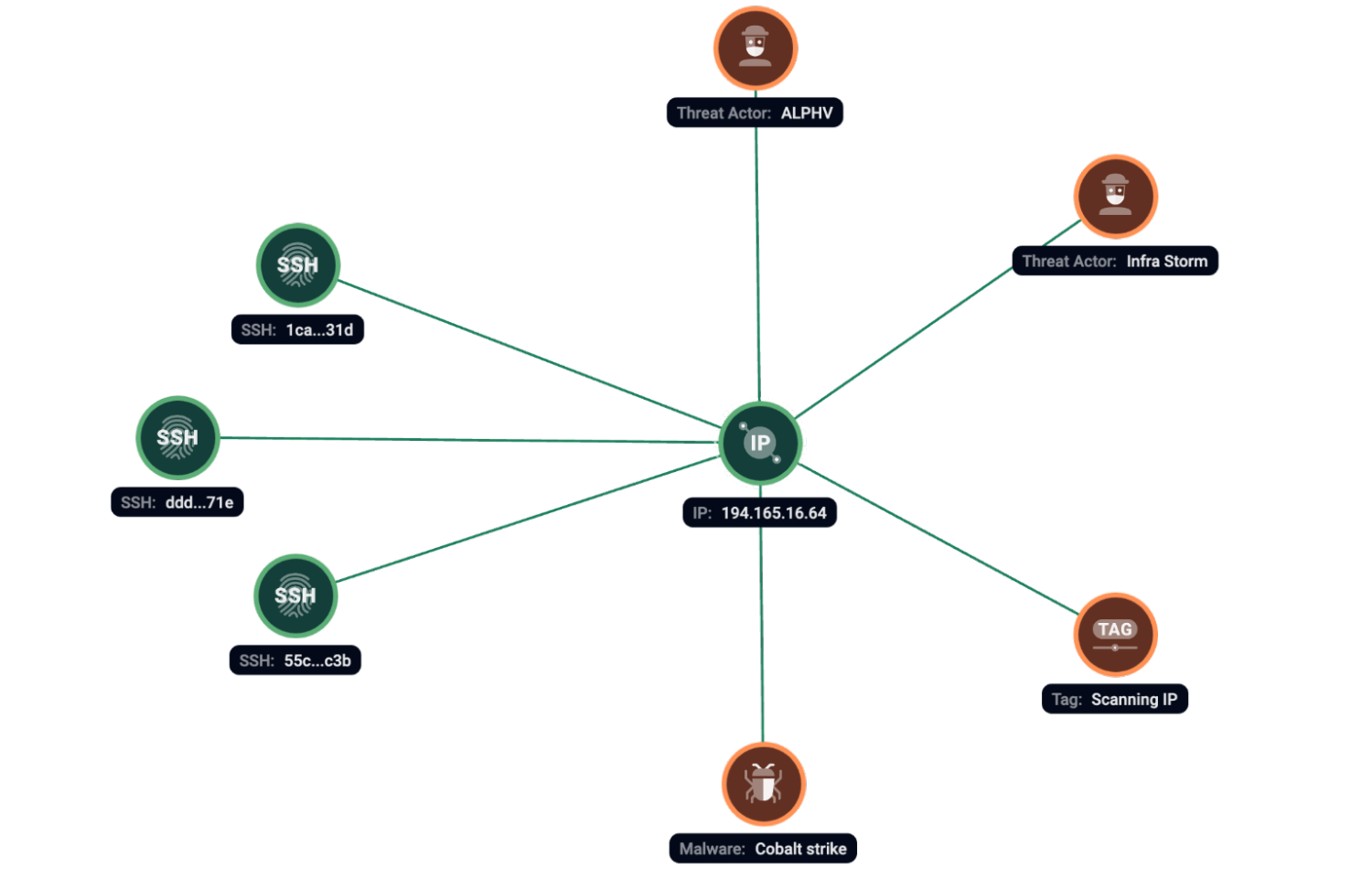
Figure 13. Group-IB Graph analysis of the network infrastructure related to ALPHV/BlackCat.
Based on research, the following server have links to ALPHV/BlackCat:
| IP address |
| 194.165.16[.]64 |
Ryuk
Ryuk is a ransomware, first appeared in August 2018 and used in targeted attacks against various organizations worldwide, it encrypts PC, storage and data centers in each infected company. Cybercrime group doesn’t have affiliate program on underground forums. Also they don’t have a Data Leak Site where they publish information about victims and compromised data, like other groups do. Group-IB customers can find more information on our platform.
According to Group-IB telemetry, we have seen server 194.165.16[.]64, at the same time with SSH fingerprint ddd9ca54c1309cde578062cba965571e, used by Ryuk in their campaigns with moderate to high confidence.
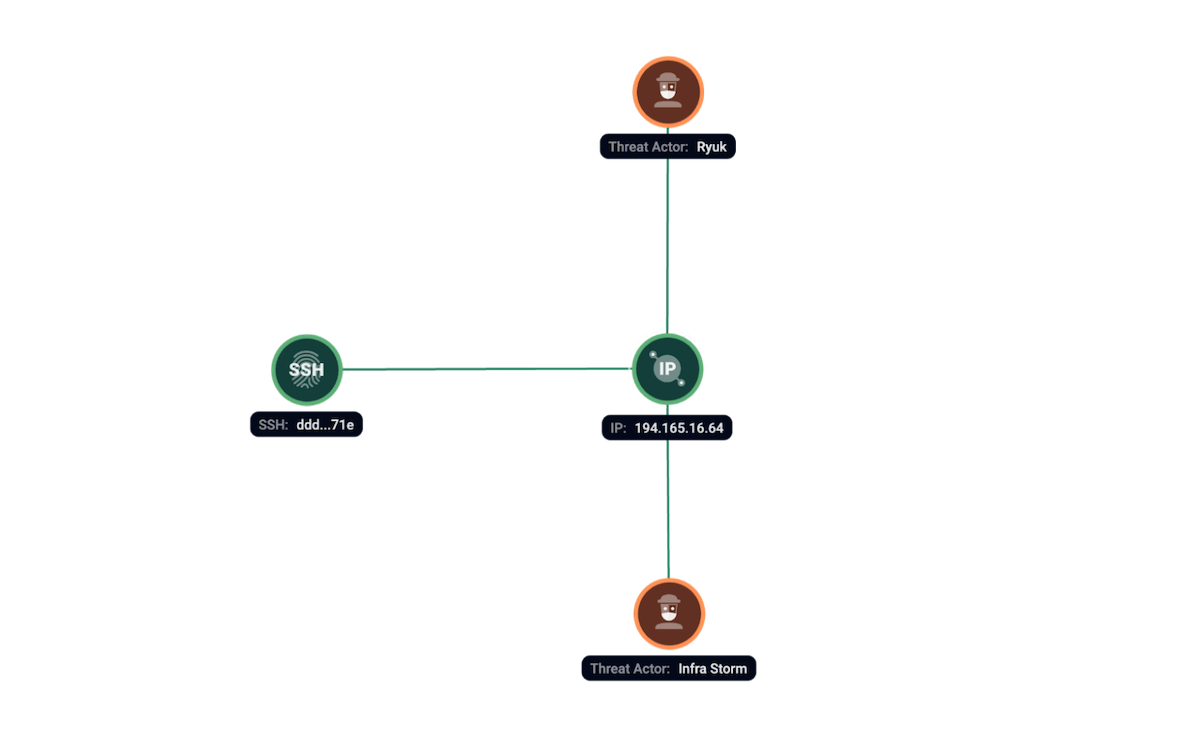
Figure 14. Group-IB Graph analysis of the network infrastructure related to Ryuk.
Based on our research, the following servers have links to Ryuk:
| IP address |
| 194.165.16[.]64 |
| 147.78.47[.]178 |
| 46.161.40[.]118 |
| 141.98.82[.]243 |
| 194.165.16[.]95 |
Malsmoke
MalSmoke is a threat actor that has been active since December 2019. We believe that the current TA is responsible for the BatLoader campaign described in that report prepared by VMware researchers. Group-IB customers can find more information on our platform.
According to Group-IB telemetry, we have seen server 194.135.24[.]245, at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b, used by Malsmoke in their campaigns with moderate to high confidence.
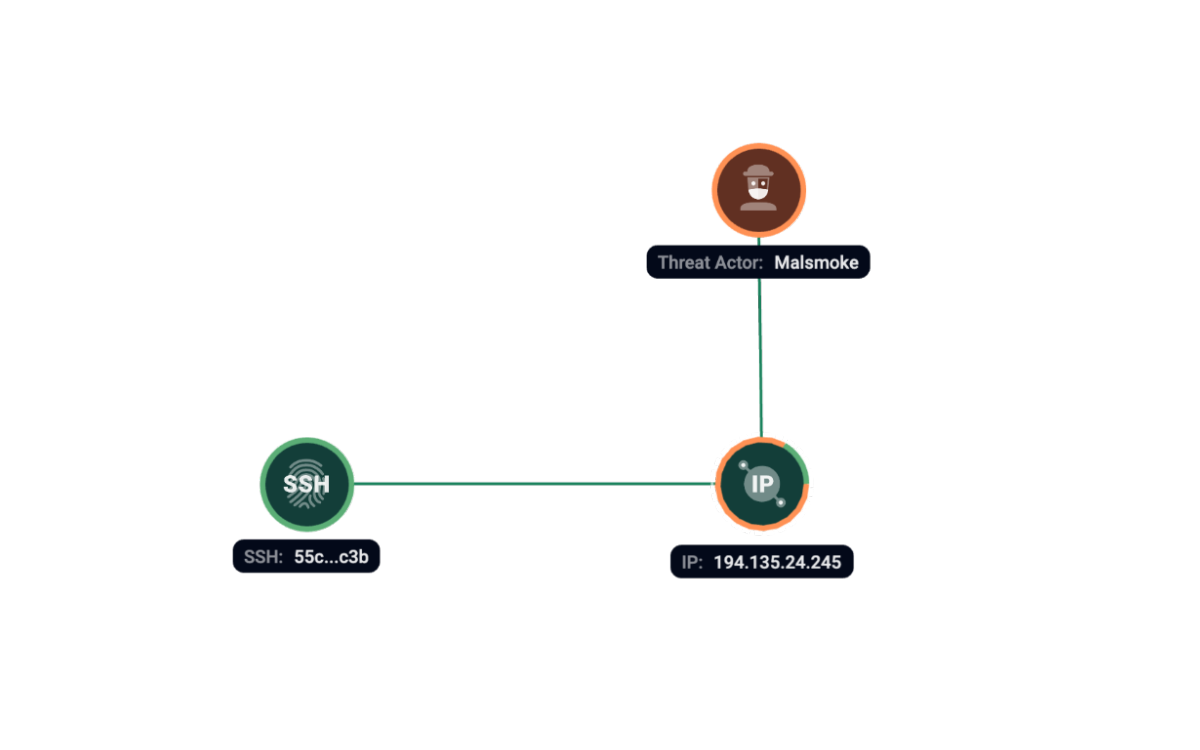
Figure 15. Group-IB Graph analysis of the network infrastructure related to Malsmoke.
Based on our research following servers have links to Malsmoke:
| IP address |
| 194.135.24[.]245 |
| 194.135.24[.]250 |
Black Basta
Black Basta is a ransomware operator group discovered in April 2022. Black Basta is a private operation and not a Ransomware-as-a-Service (RaaS). Group-IB customers can find more information on our platform.
We have seen Black Basta connection with 88.214.25[.]253 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b. According to the Bridewell blog, the domain fortiveme[.]net with A-record 88.214.25[.]253 was created shortly prior to the publication of the same name company victim of Black Basta on their Data Leak Site. However, that attribution should be treated with a low level of confidence because we do not know if that infrastructure was actually used in the attack.
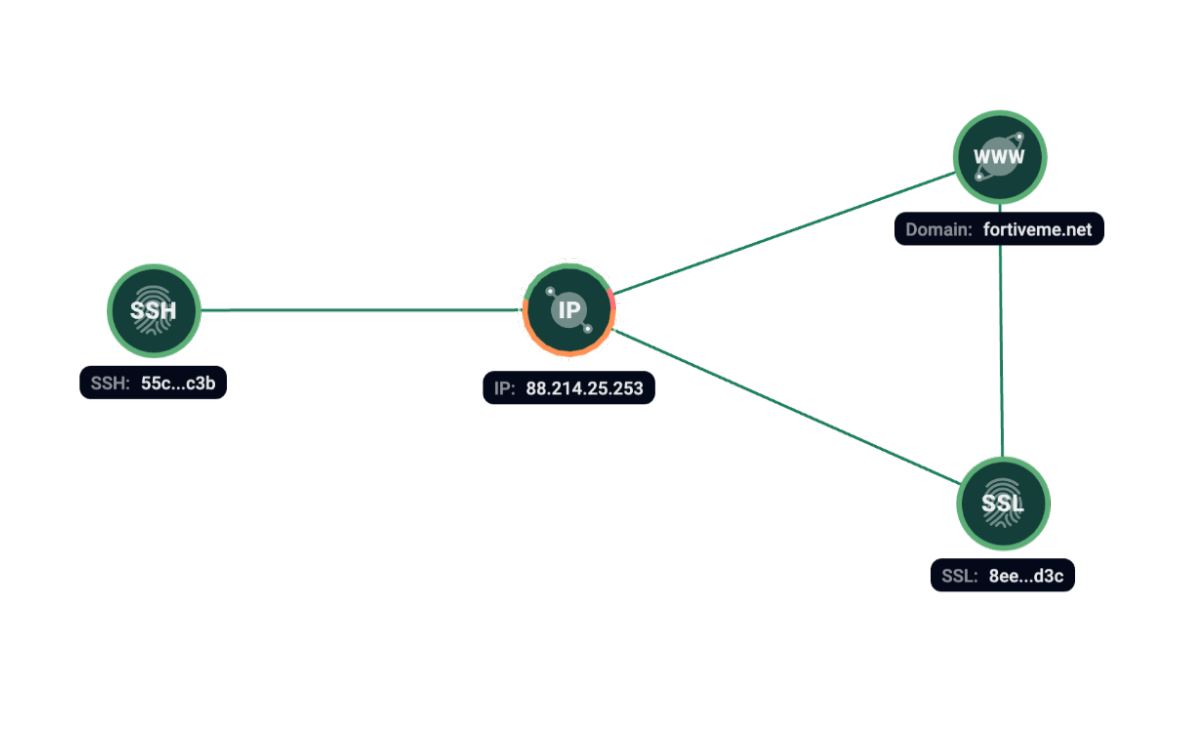
Figure 16. Group-IB Graph analysis of the network infrastructure related to Black Basta.
Additionally, we have found part of the servers (including one above) present in a Black Basta chat leak in messages dated within the presence of the confirmed ShadowSyndicate’s SSH fingerprints on the corresponding servers.
Based on our research, the following servers have links to Black Basta:
| IP address |
| 88.214.25[.]253 |
| 46.161.27[.]151 |
| 81.19.136[.]234 |
| 88.214.25[.]245 |
| 88.214.25[.]244 |
| 179.60.149[.]235 |
| 179.60.149[.]241 |
| 45.182.189[.]114 |
Others
Notably, despite being actively spotted during previous research on ShadowSyndicate infrastructure, the following groups were not seen as a part of currently analyzed clusters: LockBit, Cicada3301, Quantum, Nokoyawa, Cactus and Play.
Consistent Hosting Preference
As the majority of ShadowSyndicate analysis is devoted to network infrastructure, it is impossible to ignore preferential hosting patterns that appear with each discovered SSH fingerprint. Now, servers used by ShadowSyndicate do not have the same owner, nor do they share the same network name, and they originate from different territories. So, why does this matter?
The Intrinsec team in their ShadowSyndicate research has noticed an interesting trend of how new servers may align ASNs with previously discovered ones. Group-IB researchers have also made a correlation for new data, and that alignment is applicable to all the clusters created by ShadowSyndicate, leaving all doubts aside.
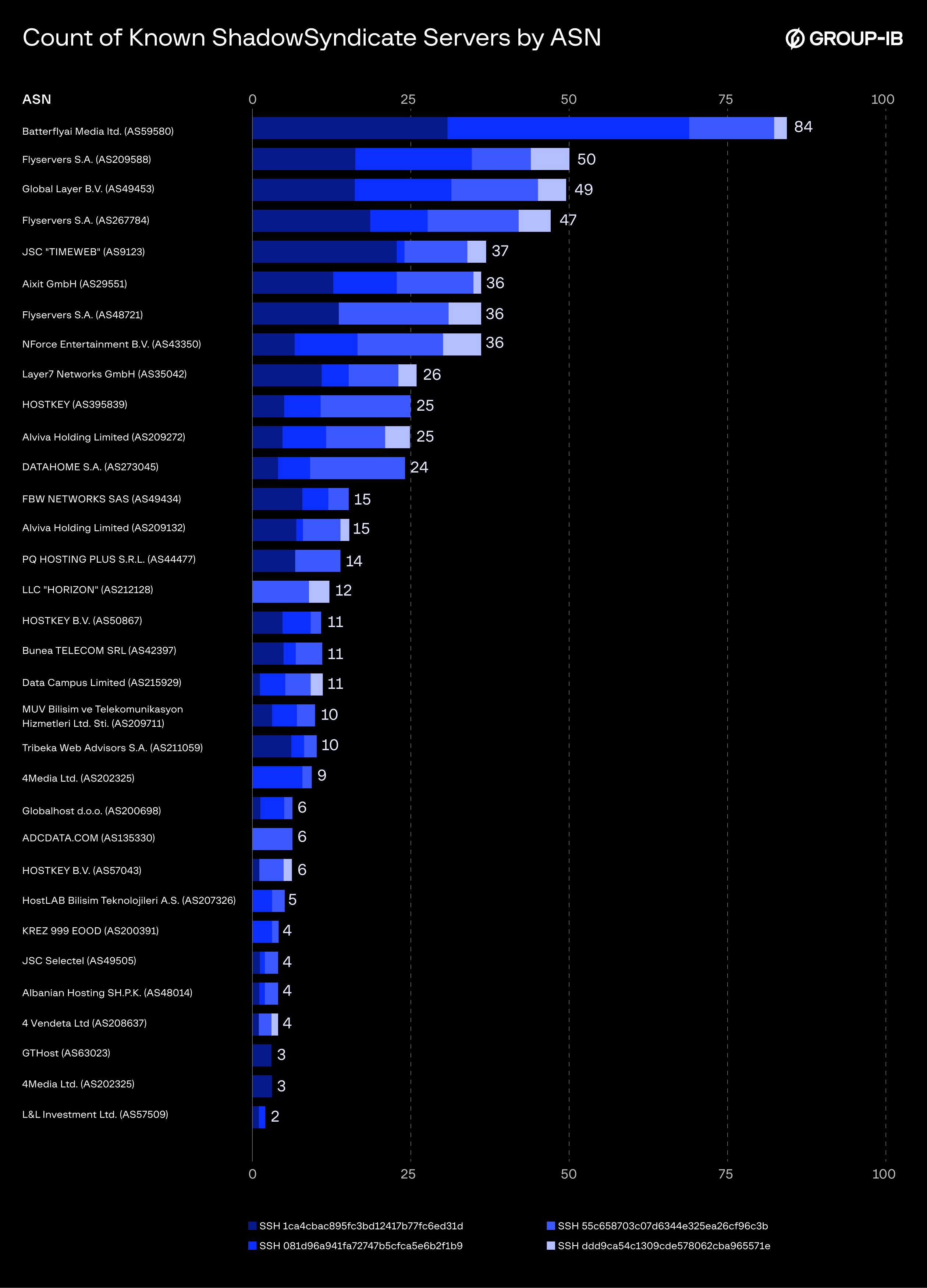
Figure 17. Distribution of known ShadowSyndicate servers related to different SSH fingerprints and their ASNs.
Although it’s not possible to concretely explain the reason behind ASN preferences, it can be surmised that the threat actor feels comfortable working with these providers. This observed consistency creates predictable patterns that can be useful for infrastructure correlation, attribution, and proactive detection.
Conclusion
A clear set of infrastructure management techniques employed by ShadowSyndicate has evolved. In addition to their distinctive method of orchestrating large clusters using a single SSH key, Group-IB researchers have discovered a new tendency to rotate the use of multiple ones. Such behavior may indicate either sophistication of the cluster’s structure or changes in processes requiring implementation of access control or segregation of duties.
Appearance of new network clusters aligns with the threat actor’s preferences to a familiar set of hosting providers. Created infrastructure is utilized for similar malicious activities, including hosting C2 servers for various attack frameworks and participating in attacks attributed to various ransomware groups. Therefore, it can be assumed that the general purpose of ShadowSyndicate activities has likely remained consistent.
While it’s still not possible yet to fully confirm the exact nature of ShadowSyndicate, Group-IB’s current intelligence primarily points to the following options: either they operate as an Initial Access Broker (IAB) or offer bulletproof hosting (BPH) provider services.
Recommendations
Based on Group-IB research experience of ShadowSyndicate, possible attack scenarios can be assessed based on the techniques associated with the discovered toolset. For this reason, we’ve built up the following list enhancing security measures in your organizations with basic recommendations. However, depending on the complexity of the attack, its type and impact, the recommendations for prevention/mitigation will vary and are often tailored specifically for an event.
- Incorporate IOCs from this report into your Threat Intelligence platform.
- Monitor all the activity related to the IP addresses belonging to frequently used autonomous systems highlighted in this blog.
- Look out for:
- Repeated MFA failures / high volume of repeated login attempts.
- Rapid login attempts with valid credentials.
- Unusual login attempt source location.
- Mismatch in location of login attempt and device receiving 2FA/MFA request prompts.
Frequently Asked Questions (FAQ)
What is an SSH key or fingerprint?
An SSH key is a secure, cryptographic method of logging onto servers without using a password. It comprises a pair: a public key which resides on the server and a private key which sits on your computer. When both keys match, you’re let in. SSH fingerprints referred to in this blog on the other hand, are the unique identifiers of an SSH key. An SSH fingerprint is derived from a hash of the SSH key and is used to identify said key, but it is not the actual key itself and cannot be used to login to servers.
What is an Initial Access Broker?
An Initial Access Broker (IAB) is a type of cybercriminal that performs the initial penetration attack on companies or services and then sells the stolen credentials or access information on the black market or to other criminal groups.
What is Bulletproof Hosting?
Bulletproof Hosting (BPH) is a type of hosting service that is often run by and used by cybercriminal groups. Servers operated by a BPH provider would allow a range of criminal activity such as malware hosting, phishing websites and C2 servers. They act as a shield from legal entities, ignoring takedown requests and do not cooperate with law enforcement actions.
What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service, or RaaS, is a “subscription-based” cybercrime in which ransomware creators lease or sell their malware to affiliates who then use it to execute attacks. You can read more about it on the Group-IB Knowledge Hub.
Indicators of Compromise (IOCs)
Network IOCs
| IP | SSH fingerprint | First seen | Last seen |
| 147.78.46[.]29 | 55c658703c07d6344e325ea26cf96c3b | 26 Jan 2026 | 26 Jan 2026 |
| 147.78.46[.]30 | 55c658703c07d6344e325ea26cf96c3b | 26 Jan 2026 | 26 Jan 2026 |
| 147.78.46[.]31 | 55c658703c07d6344e325ea26cf96c3b | 26 Jan 2026 | 26 Jan 2026 |
| 179.60.146[.]241 | 55c658703c07d6344e325ea26cf96c3b | 29 Dec 2025 | 27 Jan 2026 |
| 62.164.177[.]252 | 55c658703c07d6344e325ea26cf96c3b | 29 Dec 2025 | 10 Jan 2026 |
| 62.164.177[.]243 | 55c658703c07d6344e325ea26cf96c3b | 28 Dec 2025 | 10 Jan 2026 |
| 62.164.177[.]240 | 55c658703c07d6344e325ea26cf96c3b | 27 Dec 2025 | 23 Jan 2026 |
| 45.13.212[.]243 | 55c658703c07d6344e325ea26cf96c3b | 24 Dec 2025 | 6 Jan 2026 |
| 193.142.30[.]49 | 55c658703c07d6344e325ea26cf96c3b | 14 Dec 2025 | 19 Jan 2026 |
| 147.45.112[.]198 | 55c658703c07d6344e325ea26cf96c3b | 06 Dec 2025 | 20 Jan 2026 |
| 45.227.255[.]31 | 55c658703c07d6344e325ea26cf96c3b | 9 Oct 2025 | 18 Nov 2025 |
| 45.227.252[.]199 | 55c658703c07d6344e325ea26cf96c3b | 05 Sep 2025 | 23 Jan 2026 |
| 193.24.211[.]249 | 55c658703c07d6344e325ea26cf96c3b | 01 Sep 2025 | 26 Nov 2025 |
| 5.188.87[.]46 | 55c658703c07d6344e325ea26cf96c3b | 18 Aug 2025 | 26 Jan 2026 |
| 88.214.27[.]43 | 55c658703c07d6344e325ea26cf96c3b | 11 Aug 2025 | 25 Oct 2025 |
| 200.107.207[.]102 | 55c658703c07d6344e325ea26cf96c3b | 6 Aug 2025 | 30 Oct 2025 |
| 147.45.112[.]219 | 55c658703c07d6344e325ea26cf96c3b | 2 Aug 2025 | 17 Jan 2026 |
| 193.142.30[.]37 | 55c658703c07d6344e325ea26cf96c3b | 20 Jul 2025 | 11 Oct 2025 |
| 147.78.46[.]69 | 55c658703c07d6344e325ea26cf96c3b | 9 Jul 2025 | 01 Sep 2025 |
| 194.34.239[.]44 | 55c658703c07d6344e325ea26cf96c3b | 8 Jul 2025 | 25 Jan 2026 |
| 88.214.27[.]172 | 55c658703c07d6344e325ea26cf96c3b | 8 Jul 2025 | 24 Jan 2026 |
| 193.142.30[.]99 | 55c658703c07d6344e325ea26cf96c3b | 07 Jul 2025 | 20 Sep 2025 |
| 103.214.147[.]182 | 55c658703c07d6344e325ea26cf96c3b | 05 Jul 2025 | 19 Sep 2025 |
| 91.199.163[.]65 | 55c658703c07d6344e325ea26cf96c3b | 25 Jun 2025 | 4 Sep 2025 |
| 193.24.211[.]242 | 55c658703c07d6344e325ea26cf96c3b | 20 Jun 2025 | 20 Jun 2025 |
| 193.24.211[.]244 | 55c658703c07d6344e325ea26cf96c3b | 18 Jun 2025 | 25 June 2025 |
| 91.199.163[.]59 | 55c658703c07d6344e325ea26cf96c3b | 17 Jun 2025 | 09 Sep 2025 |
| 194.34.239[.]33 | 55c658703c07d6344e325ea26cf96c3b | 14 Jun 2025 | 25 Jan 2026 |
| 45.227.255[.]28 | 55c658703c07d6344e325ea26cf96c3b | 11 June 2025 | 07 Aug 2025 |
| 5.188.86[.]185 | 55c658703c07d6344e325ea26cf96c3b | 19 May 2025 | 26 Jan 2026 |
| 147.45.112[.]203 | 55c658703c07d6344e325ea26cf96c3b | 16 May 2025 | 12 Nov 2025 |
| 147.78.46[.]164 | 55c658703c07d6344e325ea26cf96c3b | 11 May 2025 | 26 Jan 2026 |
| 5.188.86[.]66 | 55c658703c07d6344e325ea26cf96c3b | 11 May 2025 | 11 May 2025 |
| 5.188.87[.]49 | 55c658703c07d6344e325ea26cf96c3b | 11 May 2025 | 1 Jun 2025 |
| 5.188.87[.]35 | 55c658703c07d6344e325ea26cf96c3b | 10 May 2025 | 25 May 2025 |
| 5.188.87[.]39 | 55c658703c07d6344e325ea26cf96c3b | 10 May 2025 | 02 Jun 2025 |
| 103.214.147[.]181 | 55c658703c07d6344e325ea26cf96c3b | 6 May 2025 | 30 Dec 2025 |
| 5.188.86[.]162 | 55c658703c07d6344e325ea26cf96c3b | 6 May 2025 | 3 Jun 2025 |
| 5.188.86[.]70 | 55c658703c07d6344e325ea26cf96c3b | 6 May 2025 | 6 May 2025 |
| 5.188.86[.]72 | 55c658703c07d6344e325ea26cf96c3b | 6 May 2025 | 6 May 2025 |
| 147.78.46[.]134 | 55c658703c07d6344e325ea26cf96c3b | 05 May 2025 | 26 Jan 2026 |
| 78.128.112[.]222 | 55c658703c07d6344e325ea26cf96c3b | 02 May 2025 | 13 Jan 2026 |
| 88.214.25[.]198 | 55c658703c07d6344e325ea26cf96c3b | 25 Apr 2025 | 08 May 2025 |
| 193.142.30[.]175 | 55c658703c07d6344e325ea26cf96c3b | 16 Apr 2025 | 16 Apr 2025 |
| 147.45.112[.]205 | 55c658703c07d6344e325ea26cf96c3b | 12 Apr 2025 | 20 Jan 2026 |
| 5.178.1[.]17 | 55c658703c07d6344e325ea26cf96c3b | 29 Mar 2025 | 23 Aug 2025 |
| 200.107.207[.]26 | 55c658703c07d6344e325ea26cf96c3b | 24 Mar 2025 | 31 Aug 2025 |
| 88.214.25[.]221 | 55c658703c07d6344e325ea26cf96c3b | 23 Mar 2025 | 9 Jan 2026 |
| 103.214.147[.]177 | 55c658703c07d6344e325ea26cf96c3b | 20 Mar 2025 | 09 Apr 2025 |
| 103.214.147[.]187 | 55c658703c07d6344e325ea26cf96c3b | 20 Mar 2025 | 20 Mar 2025 |
| 147.45.112[.]220 | 55c658703c07d6344e325ea26cf96c3b | 09 Mar 2025 | 09 Mar 2025 |
| 45.227.255[.]34 | ddd9ca54c1309cde578062cba965571e | 09 Mar 2025 | 09 Mar 2025 |
| 45.182.189[.]181 | 55c658703c07d6344e325ea26cf96c3b | 06 Mar 2025 | 17 Apr 2025 |
| 37.156.246[.]166 | 55c658703c07d6344e325ea26cf96c3b | 04 Mar 2025 | 20 Aug 2025 |
| 5.188.86[.]187 | 55c658703c07d6344e325ea26cf96c3b | 03 Mar 2025 | 03 Mar 2025 |
| 88.214.27[.]170 | ddd9ca54c1309cde578062cba965571e | 01 Mar 2025 | 25 Jan 2026 |
| 103.214.147[.]178 | 55c658703c07d6344e325ea26cf96c3b | 25 Feb 2025 | 09 Apr 2025 |
| 103.214.147[.]176 | 55c658703c07d6344e325ea26cf96c3b | 21 Feb 2025 | 25 Jan 2026 |
| 185.55.242[.]150 | ddd9ca54c1309cde578062cba965571e | 16 Feb 2025 | 15 Jan 2026 |
| 31.41.33[.]242 | 55c658703c07d6344e325ea26cf96c3b | 08 Feb 2025 | 26 Jul 2025 |
| 46.161.27[.]113 | 55c658703c07d6344e325ea26cf96c3b | 06 Feb 2025 | 02 Aug 2025 |
| 147.45.112[.]253 | 55c658703c07d6344e325ea26cf96c3b | 29 Jan 2025 | 28 Feb 2025 |
| 185.99.3[.]99 | 55c658703c07d6344e325ea26cf96c3b | 29 Jan 2025 | 26 Jul 2025 |
| 193.142.30[.]205 | 55c658703c07d6344e325ea26cf96c3b | 29 Jan 2025 | 22 Jan 2026 |
| 31.41.33[.]241 | 55c658703c07d6344e325ea26cf96c3b | 28 Jan 2025 | 24 Jul 2025 |
| 5.188.86[.]184 | 55c658703c07d6344e325ea26cf96c3b | 24 Jan 2025 | 18 Mar 2025 |
| 5.188.86[.]173 | ddd9ca54c1309cde578062cba965571e | 30 Dec 2024 | 14 Jan 2025 |
| 5.188.86[.]175 | 55c658703c07d6344e325ea26cf96c3b | 30 Dec 2024 | 14 Jan 2025 |
| 45.182.189[.]194 | 55c658703c07d6344e325ea26cf96c3b | 27 Dec 2024 | 13 May 2025 |
| 81.19.135[.]229 | 55c658703c07d6344e325ea26cf96c3b | 27 Dec 2024 | 05 Jan 2025 |
| 147.78.46[.]81 | 55c658703c07d6344e325ea26cf96c3b | 23 Dec 2024 | 26 Jan 2026 |
| 5.188.86[.]176 | ddd9ca54c1309cde578062cba965571e | 22 Dec 2024 | 14 Jan 2025 |
| 91.238.181[.]235 | 55c658703c07d6344e325ea26cf96c3b | 22 Dec 2024 | 24 Jan 2025 |
| 88.214.25[.]199 | 55c658703c07d6344e325ea26cf96c3b | 18 Dec 2024 | 27 Jan 2025 |
| 46.161.27[.]155 | 55c658703c07d6344e325ea26cf96c3b | 16 Dec 2024 | 07 Mar 2025 |
| 46.161.27[.]158 | 55c658703c07d6344e325ea26cf96c3b | 09 Dec 2024 | 29 Jan 2025 |
| 81.19.138[.]201 | 55c658703c07d6344e325ea26cf96c3b | 06 Dec 2024 | 10 Feb 2025 |
| 5.178.1[.]13 | 55c658703c07d6344e325ea26cf96c3b | 27 Nov 2024 | 27 Nov 2024 |
| 81.19.135[.]212 | 55c658703c07d6344e325ea26cf96c3b | 15 Nov 2024 | 15 Nov 2024 |
| 194.165.16[.]54 | 55c658703c07d6344e325ea26cf96c3b | 14 Nov 2024 | 06 Jul 2025 |
| 45.227.255[.]29 | 55c658703c07d6344e325ea26cf96c3b | 13 Nov 2024 | 18 Aug 2025 |
| 45.145.20[.]211 | 55c658703c07d6344e325ea26cf96c3b | 03 Nov 2024 | 05 Mar 2025 |
| 45.182.189[.]224 | 55c658703c07d6344e325ea26cf96c3b | 02 Nov 2024 | 24 Jul 2025 |
| 81.19.136[.]200 | 55c658703c07d6344e325ea26cf96c3b | 26 Oct 2024 | 14 Jan 2025 |
| 193.29.13[.]150 | 55c658703c07d6344e325ea26cf96c3b | 18 Oct 2024 | 21 Jan 2026 |
| 45.227.252[.]228 | 55c658703c07d6344e325ea26cf96c3b | 18 Oct 2024 | 18 Oct 2024 |
| 45.227.252[.]230 | ddd9ca54c1309cde578062cba965571e | 18 Oct 2024 | 18 Oct 2024 |
| 5.188.206[.]214 | 55c658703c07d6344e325ea26cf96c3b | 18 Oct 2024 | 01 Feb 2025 |
| 81.19.136[.]197 | 55c658703c07d6344e325ea26cf96c3b | 17 Oct 2024 | 05 Feb 2025 |
| 147.45.112[.]249 | ddd9ca54c1309cde578062cba965571e | 16 Oct 2024 | 16 Oct 2024 |
| 141.98.82[.]219 | ddd9ca54c1309cde578062cba965571e | 12 Oct 2024 | 30 Oct 2024 |
| 193.142.30[.]194 | 55c658703c07d6344e325ea26cf96c3b | 07 Oct 2024 | 18 Dec 2025 |
| 179.60.149[.]207 | 55c658703c07d6344e325ea26cf96c3b | 04 Oct 2024 | 12 Nov 2024 |
| 141.98.83[.]90 | ddd9ca54c1309cde578062cba965571e | 01 Oct 2024 | 24 Oct 2024 |
| 194.165.16[.]53 | ddd9ca54c1309cde578062cba965571e | 01 Oct 2024 | 31 Oct 2024 |
| 88.214.25[.]235 | ddd9ca54c1309cde578062cba965571e | 29 Sep 2024 | 30 Oct 2024 |
| 88.214.25[.]211 | 55c658703c07d6344e325ea26cf96c3b | 27 Sep 2024 | 17 Dec 2024 |
| 5.188.87[.]47 | 55c658703c07d6344e325ea26cf96c3b | 22 Sep 2024 | 26 Nov 2024 |
| 147.78.46[.]83 | 55c658703c07d6344e325ea26cf96c3b | 19 Sep 2024 | 13 Nov 2024 |
| 147.78.47[.]236 | 55c658703c07d6344e325ea26cf96c3b | 16 Sep 2024 | 06 Feb 2025 |
| 185.232.67[.]13 | 55c658703c07d6344e325ea26cf96c3b | 15 Sep 2024 | 06 Feb 2025 |
| 185.232.67[.]15 | 55c658703c07d6344e325ea26cf96c3b | 15 Sep 2024 | 24 Feb 2025 |
| 37.156.246[.]168 | 55c658703c07d6344e325ea26cf96c3b | 15 Sep 2024 | 07 Jun 2025 |
| 147.78.47[.]243 | 55c658703c07d6344e325ea26cf96c3b | 12 Sep 2024 | 09 Mar 2025 |
| 193.29.13[.]240 | 55c658703c07d6344e325ea26cf96c3b | 11 Sep 2024 | 18 Jan 2026 |
| 81.19.136[.]231 | 55c658703c07d6344e325ea26cf96c3b | 09 Sep 2024 | 02 Nov 2024 |
| 81.19.136[.]253 | 55c658703c07d6344e325ea26cf96c3b | 09 Sep 2024 | 13 Feb 2025 |
| 194.165.16[.]90 | ddd9ca54c1309cde578062cba965571e | 04 Sep 2024 | 20 Nov 2024 |
| 194.165.16[.]59 | ddd9ca54c1309cde578062cba965571e | 02 Sep 2024 | 20 Nov 2024 |
| 81.19.138[.]89 | 55c658703c07d6344e325ea26cf96c3b | 29 Aug 2024 | 28 Sep 2024 |
| 179.60.149[.]252 | 55c658703c07d6344e325ea26cf96c3b | 27 Aug 2024 | 14 Sep 2024 |
| 81.19.136[.]207 | 55c658703c07d6344e325ea26cf96c3b | 16 Aug 2024 | 01 Oct 2024 |
| 88.214.27[.]169 | 55c658703c07d6344e325ea26cf96c3b | 03 Aug 2024 | 19 Dec 2025 |
| 88.214.27[.]179 | 55c658703c07d6344e325ea26cf96c3b | 22 Jul 2024 | 25 Nov 2024 |
| 81.19.138[.]61 | 55c658703c07d6344e325ea26cf96c3b | 06 Jul 2024 | 22 Dec 2024 |
| 78.128.112[.]199 | ddd9ca54c1309cde578062cba965571e | 03 Jul 2024 | 25 Jan 2026 |
| 193.142.30[.]158 | ddd9ca54c1309cde578062cba965571e | 02 Jul 2024 | 06 Feb 2025 |
| 88.214.27[.]165 | 55c658703c07d6344e325ea26cf96c3b | 18 Jun 2024 | 18 Jun 2024 |
| 88.214.25[.]238 | 55c658703c07d6344e325ea26cf96c3b | 14 Jun 2024 | 14 Jun 2024 |
| 179.60.149[.]249 | 55c658703c07d6344e325ea26cf96c3b | 10 Jun 2024 | 17 Nov 2024 |
| 88.214.27[.]177 | 55c658703c07d6344e325ea26cf96c3b | 05 Jun 2024 | 29 Oct 2024 |
| 88.214.27[.]175 | 55c658703c07d6344e325ea26cf96c3b | 02 Jun 2024 | 09 Dec 2024 |
| 179.60.149[.]222 | 55c658703c07d6344e325ea26cf96c3b | 14 May 2024 | 15 Oct 2024 |
| 179.60.149[.]223 | 55c658703c07d6344e325ea26cf96c3b | 14 May 2024 | 07 Oct 2024 |
| 81.19.138[.]92 | 55c658703c07d6344e325ea26cf96c3b | 04 May 2024 | 21 Jul 2024 |
| 88.214.26[.]27 | 55c658703c07d6344e325ea26cf96c3b | 03 May 2024 | 07 Oct 2024 |
| 88.214.25[.]243 | 55c658703c07d6344e325ea26cf96c3b | 01 May 2024 | 13 Oct 2024 |
| 179.60.150[.]117 | 55c658703c07d6344e325ea26cf96c3b | 27 Apr 2024 | 22 Oct 2024 |
| 5.188.86[.]234 | 55c658703c07d6344e325ea26cf96c3b | 27 Apr 2024 | 02 Jun 2024 |
| 78.128.112[.]137 | 55c658703c07d6344e325ea26cf96c3b | 27 Apr 2024 | 21 Oct 2024 |
| 78.128.112[.]138 | 55c658703c07d6344e325ea26cf96c3b | 27 Apr 2024 | 19 Oct 2024 |
| 88.214.26[.]28 | 55c658703c07d6344e325ea26cf96c3b | 27 Apr 2024 | 23 Oct 2024 |
| 193.142.30[.]235 | 55c658703c07d6344e325ea26cf96c3b | 12 Apr 2024 | 12 Apr 2024 |
| 179.60.149[.]214 | 55c658703c07d6344e325ea26cf96c3b | 06 Apr 2024 | 06 Apr 2024 |
| 45.227.252[.]226 | 55c658703c07d6344e325ea26cf96c3b | 06 Apr 2024 | 22 Aug 2025 |
| 5.188.86[.]20 | 55c658703c07d6344e325ea26cf96c3b | 16 Mar 2024 | 06 Sep 2024 |
| 88.214.26[.]27 | ddd9ca54c1309cde578062cba965571e | 12 Mar 2024 | 12 Mar 2024 |
| 179.60.147[.]180 | 55c658703c07d6344e325ea26cf96c3b | 11 Mar 2024 | 04 Apr 2024 |
| 88.214.27[.]38 | 55c658703c07d6344e325ea26cf96c3b | 16 Feb 2024 | 31 Mar 2024 |
| 81.19.138[.]58 | 55c658703c07d6344e325ea26cf96c3b | 11 Feb 2024 | 18 Sep 2024 |
| 5.188.86[.]21 | ddd9ca54c1309cde578062cba965571e | 10 Feb 2024 | 16 Jul 2025 |
| 5.188.86[.]217 | 55c658703c07d6344e325ea26cf96c3b | 10 Feb 2024 | 26 Apr 2025 |
| 81.19.138[.]22 | 55c658703c07d6344e325ea26cf96c3b | 08 Feb 2024 | 24 Mar 2024 |
| 81.19.138[.]27 | ddd9ca54c1309cde578062cba965571e | 08 Feb 2024 | 26 Jan 2025 |
| 45.182.189[.]107 | 55c658703c07d6344e325ea26cf96c3b | 06 Feb 2024 | 08 Sep 2025 |
| 179.60.149[.]245 | 55c658703c07d6344e325ea26cf96c3b | 02 Feb 2024 | 16 Feb 2024 |
| 179.60.149[.]251 | 55c658703c07d6344e325ea26cf96c3b | 02 Feb 2024 | 06 Apr 2024 |
| 179.60.149[.]253 | 55c658703c07d6344e325ea26cf96c3b | 02 Feb 2024 | 16 Feb 2024 |
| 141.98.82[.]229 | 55c658703c07d6344e325ea26cf96c3b | 01 Feb 2024 | 15 Mar 2024 |
| 88.214.25[.]249 | 55c658703c07d6344e325ea26cf96c3b | 30 Jan 2024 | 16 Feb 2024 |
| 81.19.136[.]234 | 55c658703c07d6344e325ea26cf96c3b | 27 Jan 2024 | 28 Feb 2024 |
| 46.161.27[.]151 | 55c658703c07d6344e325ea26cf96c3b | 23 Jan 2024 | 08 May 2024 |
| 88.214.25[.]252 | 55c658703c07d6344e325ea26cf96c3b | 20 Jan 2024 | 20 Jan 2024 |
| 81.19.138[.]150 | ddd9ca54c1309cde578062cba965571e | 17 Jan 2024 | 07 Feb 2025 |
| 147.78.47[.]178 | 55c658703c07d6344e325ea26cf96c3b | 22 Dec 2023 | 21 Oct 2024 |
| 81.19.138[.]59 | 55c658703c07d6344e325ea26cf96c3b | 22 Nov 2023 | 09 Oct 2024 |
| 5.188.87[.]59 | 55c658703c07d6344e325ea26cf96c3b | 08 Nov 2023 | 08 Nov 2023 |
| 91.238.181[.]239 | 55c658703c07d6344e325ea26cf96c3b | 06 Nov 2023 | 06 Nov 2023 |
| 88.214.25[.]245 | 55c658703c07d6344e325ea26cf96c3b | 05 Nov 2023 | 12 Mar 2024 |
| 179.60.149[.]232 | 55c658703c07d6344e325ea26cf96c3b | 01 Nov 2023 | 06 Nov 2023 |
| 81.19.138[.]91 | 55c658703c07d6344e325ea26cf96c3b | 01 Nov 2023 | 03 Feb 2025 |
| 81.19.138[.]51 | 55c658703c07d6344e325ea26cf96c3b | 31 Oct 2023 | 31 Oct 2023 |
| 193.29.13[.]217 | 55c658703c07d6344e325ea26cf96c3b | 26 Oct 2023 | 29 Mar 2024 |
| 81.19.135[.]234 | ddd9ca54c1309cde578062cba965571e | 25 Oct 2023 | 25 Oct 2023 |
| 193.29.13[.]167 | 55c658703c07d6344e325ea26cf96c3b | 22 Oct 2023 | 10 Nov 2023 |
| 81.19.138[.]31 | ddd9ca54c1309cde578062cba965571e | 17 Oct 2023 | 01 Nov 2023 |
| 88.214.25[.]253 | 55c658703c07d6344e325ea26cf96c3b | 17 Oct 2023 | 22 Jan 2024 |
| 141.98.80[.]158 | 55c658703c07d6344e325ea26cf96c3b | 22 Sep 2023 | 22 Sep 2023 |
| 179.60.149[.]244 | 55c658703c07d6344e325ea26cf96c3b | 22 Sep 2023 | 09 Feb 2025 |
| 45.227.252[.]244 | 55c658703c07d6344e325ea26cf96c3b | 22 Sep 2023 | 22 Sep 2023 |
| 91.238.181[.]250 | 55c658703c07d6344e325ea26cf96c3b | 22 Sep 2023 | 23 Sep 2023 |
| 88.214.26[.]31 | 55c658703c07d6344e325ea26cf96c3b | 21 Sep 2023 | 23 Sep 2023 |
| 92.118.36[.]203 | 55c658703c07d6344e325ea26cf96c3b | 21 Sep 2023 | 23 Sep 2023 |
| 88.214.25[.]242 | 55c658703c07d6344e325ea26cf96c3b | 20 Sep 2023 | 23 Oct 2024 |
| 88.214.25[.]244 | 55c658703c07d6344e325ea26cf96c3b | 20 Sep 2023 | 23 Jan 2024 |
| 88.214.26[.]33 | 55c658703c07d6344e325ea26cf96c3b | 20 Sep 2023 | 14 Oct 2023 |
| 46.161.27[.]152 | 55c658703c07d6344e325ea26cf96c3b | 19 Sep 2023 | 24 Sep 2023 |
| 5.188.87[.]37 | 55c658703c07d6344e325ea26cf96c3b | 03 Aug 2023 | 08 May 2025 |
| 45.182.189[.]110 | 55c658703c07d6344e325ea26cf96c3b | 28 Jul 2023 | 28 Jul 2023 |
| 45.182.189[.]109 | 55c658703c07d6344e325ea26cf96c3b | 18 Jul 2023 | 02 Nov 2023 |
| 46.161.40[.]27 | ddd9ca54c1309cde578062cba965571e | 07 Jul 2023 | 18 Dec 2023 |
| 5.188.87[.]40 | ddd9ca54c1309cde578062cba965571e | 06 Jul 2023 | 07 Nov 2023 |
| 88.214.26[.]34 | ddd9ca54c1309cde578062cba965571e | 09 Jun 2023 | 29 Oct 2023 |
| 147.78.47[.]223 | ddd9ca54c1309cde578062cba965571e | 08 Jun 2023 | 08 Jun 2023 |
| 147.78.47[.]249 | 55c658703c07d6344e325ea26cf96c3b | 08 Jun 2023 | 08 Jun 2023 |
| 179.60.150[.]145 | 55c658703c07d6344e325ea26cf96c3b | 08 Jun 2023 | 08 Jun 2023 |
| 45.182.189[.]92 | 55c658703c07d6344e325ea26cf96c3b | 08 Jun 2023 | 08 Jun 2023 |
| 179.60.149[.]235 | 55c658703c07d6344e325ea26cf96c3b | 07 Jun 2023 | 07 Nov 2023 |
| 193.142.30[.]211 | 55c658703c07d6344e325ea26cf96c3b | 06 Jun 2023 | 08 Jun 2023 |
| 5.188.87[.]35 | ddd9ca54c1309cde578062cba965571e | 06 Jun 2023 | 30 May 2024 |
| 5.188.87[.]36 | ddd9ca54c1309cde578062cba965571e | 06 Jun 2023 | 06 Jun 2023 |
| 147.78.47[.]227 | ddd9ca54c1309cde578062cba965571e | 01 Jun 2023 | 08 Nov 2023 |
| 179.60.150[.]148 | 55c658703c07d6344e325ea26cf96c3b | 28 May 2023 | 28 Jun 2023 |
| 45.227.255[.]34 | 55c658703c07d6344e325ea26cf96c3b | 27 May 2023 | 13 Oct 2023 |
| 179.60.149[.]241 | 55c658703c07d6344e325ea26cf96c3b | 25 May 2023 | 09 Apr 2024 |
| 179.60.149[.]248 | 55c658703c07d6344e325ea26cf96c3b | 25 May 2023 | 04 Jun 2023 |
| 45.182.189[.]71 | 55c658703c07d6344e325ea26cf96c3b | 22 May 2023 | 22 May 2023 |
| 46.161.40[.]92 | 55c658703c07d6344e325ea26cf96c3b | 19 May 2023 | 19 May 2023 |
| 45.182.189[.]91 | 55c658703c07d6344e325ea26cf96c3b | 18 May 2023 | 26 May 2023 |
| 5.188.86[.]200 | ddd9ca54c1309cde578062cba965571e | 17 May 2023 | 05 Jul 2023 |
| 5.188.86[.]237 | ddd9ca54c1309cde578062cba965571e | 17 May 2023 | 08 Jul 2023 |
| 81.19.136[.]244 | 55c658703c07d6344e325ea26cf96c3b | 17 May 2023 | 14 Sep 2023 |
| 46.161.27[.]153 | 55c658703c07d6344e325ea26cf96c3b | 11 May 2023 | 18 May 2023 |
| 46.161.40[.]96 | 55c658703c07d6344e325ea26cf96c3b | 11 May 2023 | 07 Nov 2023 |
| 45.182.189[.]120 | 55c658703c07d6344e325ea26cf96c3b | 09 May 2023 | 17 May 2023 |
| 81.19.135[.]238 | ddd9ca54c1309cde578062cba965571e | 09 May 2023 | 13 Jun 2023 |
| 81.19.135[.]243 | 55c658703c07d6344e325ea26cf96c3b | 09 May 2023 | 07 Jul 2023 |
| 194.165.16[.]94 | 55c658703c07d6344e325ea26cf96c3b | 28 Apr 2023 | 17 May 2023 |
| 45.182.189[.]118 | 55c658703c07d6344e325ea26cf96c3b | 26 Apr 2023 | 09 Jun 2024 |
| 45.182.189[.]103 | 55c658703c07d6344e325ea26cf96c3b | 18 Apr 2023 | 23 Apr 2023 |
| 92.118.36[.]252 | ddd9ca54c1309cde578062cba965571e | 13 Apr 2023 | 13 Apr 2023 |
| 194.165.16[.]59 | 55c658703c07d6344e325ea26cf96c3b | 05 Apr 2023 | 20 May 2023 |
| 194.165.16[.]92 | 55c658703c07d6344e325ea26cf96c3b | 05 Apr 2023 | 29 Apr 2023 |
| 92.118.36[.]236 | ddd9ca54c1309cde578062cba965571e | 04 Apr 2023 | 10 Apr 2023 |
| 45.182.189[.]114 | 55c658703c07d6344e325ea26cf96c3b | 01 Apr 2023 | 03 Nov 2023 |
| 194.165.16[.]81 | 55c658703c07d6344e325ea26cf96c3b | 31 Mar 2023 | 03 Apr 2023 |
| 194.165.16[.]82 | 55c658703c07d6344e325ea26cf96c3b | 31 Mar 2023 | 02 Apr 2023 |
| 45.227.255[.]74 | 55c658703c07d6344e325ea26cf96c3b | 16 Mar 2023 | 31 Jul 2025 |
| 194.165.16[.]55 | 55c658703c07d6344e325ea26cf96c3b | 14 Mar 2023 | 14 Mar 2023 |
| 194.135.24[.]241 | 55c658703c07d6344e325ea26cf96c3b | 11 Mar 2023 | 16 Apr 2023 |
| 194.165.16[.]80 | 55c658703c07d6344e325ea26cf96c3b | 09 Mar 2023 | 01 Apr 2023 |
| 45.227.255[.]189 | ddd9ca54c1309cde578062cba965571e | 26 Feb 2023 | 05 Mar 2023 |
| 193.142.30[.]64 | ddd9ca54c1309cde578062cba965571e | 17 Feb 2023 | 17 Feb 2023 |
| 194.165.16[.]93 | 55c658703c07d6344e325ea26cf96c3b | 16 Feb 2023 | 02 May 2023 |
| 179.60.150[.]151 | 55c658703c07d6344e325ea26cf96c3b | 06 Feb 2023 | 02 Jun 2023 |
| 194.135.24[.]249 | 55c658703c07d6344e325ea26cf96c3b | 06 Feb 2023 | 06 Feb 2023 |
| 46.161.40[.]118 | 55c658703c07d6344e325ea26cf96c3b | 06 Feb 2023 | 06 Dec 2023 |
| 194.165.16[.]56 | 55c658703c07d6344e325ea26cf96c3b | 03 Feb 2023 | 03 Feb 2023 |
| 45.227.252[.]249 | ddd9ca54c1309cde578062cba965571e | 01 Feb 2023 | 01 Feb 2023 |
| 193.142.30[.]60 | 55c658703c07d6344e325ea26cf96c3b | 24 Jan 2023 | 24 Jan 2023 |
| 46.161.40[.]128 | 55c658703c07d6344e325ea26cf96c3b | 20 Jan 2023 | 20 Jun 2023 |
| 45.227.252[.]247 | 55c658703c07d6344e325ea26cf96c3b | 19 Dec 2022 | 11 Jan 2023 |
| 147.78.47[.]246 | ddd9ca54c1309cde578062cba965571e | 15 Dec 2022 | 17 Feb 2023 |
| 194.135.24[.]248 | 55c658703c07d6344e325ea26cf96c3b | 14 Dec 2022 | 09 Mar 2023 |
| 45.227.255[.]221 | ddd9ca54c1309cde578062cba965571e | 14 Dec 2022 | 14 Dec 2022 |
| 88.214.26[.]29 | ddd9ca54c1309cde578062cba965571e | 14 Dec 2022 | 19 Nov 2024 |
| 88.214.27[.]101 | ddd9ca54c1309cde578062cba965571e | 10 Dec 2022 | 12 Dec 2022 |
| 147.78.47[.]250 | ddd9ca54c1309cde578062cba965571e | 09 Dec 2022 | 06 Mar 2025 |
| 88.214.27[.]100 | ddd9ca54c1309cde578062cba965571e | 09 Dec 2022 | 09 Dec 2022 |
| 194.165.16[.]58 | 55c658703c07d6344e325ea26cf96c3b | 02 Dec 2022 | 07 Feb 2023 |
| 194.165.16[.]79 | ddd9ca54c1309cde578062cba965571e | 02 Dec 2022 | 08 Jun 2023 |
| 194.165.16[.]53 | 55c658703c07d6344e325ea26cf96c3b | 01 Dec 2022 | 19 May 2023 |
| 45.227.252[.]253 | 55c658703c07d6344e325ea26cf96c3b | 29 Nov 2022 | 22 Dec 2022 |
| 194.165.16[.]57 | 55c658703c07d6344e325ea26cf96c3b | 28 Nov 2022 | 27 Feb 2023 |
| 194.135.24[.]242 | 55c658703c07d6344e325ea26cf96c3b | 26 Nov 2022 | 21 Dec 2022 |
| 194.135.24[.]250 | 55c658703c07d6344e325ea26cf96c3b | 26 Nov 2022 | 21 Dec 2022 |
| 141.98.82[.]243 | 55c658703c07d6344e325ea26cf96c3b | 23 Nov 2022 | 09 Dec 2022 |
| 194.135.24[.]240 | 55c658703c07d6344e325ea26cf96c3b | 23 Nov 2022 | 17 Apr 2023 |
| 45.227.252[.]249 | 55c658703c07d6344e325ea26cf96c3b | 16 Nov 2022 | 01 Dec 2022 |
| 46.161.27[.]151 | ddd9ca54c1309cde578062cba965571e | 11 Nov 2022 | 01 Dec 2022 |
| 194.165.16[.]90 | 55c658703c07d6344e325ea26cf96c3b | 03 Nov 2022 | 27 Apr 2023 |
| 147.78.47[.]221 | 55c658703c07d6344e325ea26cf96c3b | 27 Oct 2022 | 10 Dec 2022 |
| 194.165.16[.]64 | 55c658703c07d6344e325ea26cf96c3b | 26 Oct 2022 | 27 Nov 2022 |
| 194.165.16[.]91 | 55c658703c07d6344e325ea26cf96c3b | 26 Oct 2022 | 29 Apr 2023 |
| 179.60.146[.]53 | 55c658703c07d6344e325ea26cf96c3b | 07 Oct 2022 | 07 Oct 2022 |
| 45.227.253[.]21 | 55c658703c07d6344e325ea26cf96c3b | 07 Oct 2022 | 07 Oct 2022 |
| 5.188.86[.]233 | 55c658703c07d6344e325ea26cf96c3b | 06 Oct 2022 | 08 Oct 2022 |
| 45.227.255[.]213 | 55c658703c07d6344e325ea26cf96c3b | 04 Oct 2022 | 04 Oct 2022 |
| 45.227.255[.]51 | 55c658703c07d6344e325ea26cf96c3b | 02 Oct 2022 | 03 Oct 2022 |
| 147.78.47[.]211 | ddd9ca54c1309cde578062cba965571e | 26 Sep 2022 | 03 Oct 2022 |
| 194.135.24[.]245 | 55c658703c07d6344e325ea26cf96c3b | 23 Sep 2022 | 20 Dec 2022 |
| 46.161.27[.]153 | ddd9ca54c1309cde578062cba965571e | 22 Sep 2022 | 22 Sep 2022 |
| 194.165.16[.]64 | ddd9ca54c1309cde578062cba965571e | 12 Sep 2022 | 03 Oct 2022 |
| 194.165.16[.]95 | 55c658703c07d6344e325ea26cf96c3b | 12 Sep 2022 | 25 Feb 2023 |
| 46.161.27[.]212 | ddd9ca54c1309cde578062cba965571e | 01 Sep 2022 | 25 Oct 2022 |
| 147.78.47[.]250 | 55c658703c07d6344e325ea26cf96c3b | 31 Aug 2022 | 06 Sep 2022 |
| 81.19.135[.]243 | ddd9ca54c1309cde578062cba965571e | 19 Jul 2022 | 28 Jul 2022 |
| 5.188.86[.]227 | 55c658703c07d6344e325ea26cf96c3b | 07 Jul 2022 | 21 Jul 2022 |
DISCLAIMER: All technical information, including malware analysis, indicators of compromise and infrastructure details provided in this publication, is shared solely for defensive cybersecurity and research purposes. Group-IB does not endorse or permit any unauthorized or offensive use of the information contained herein. The data and conclusions represent Group-IB’s analytical assessment based on available evidence and are intended to help organizations detect, prevent, and respond to cyber threats.
Group-IB expressly disclaims liability for any misuse of the information provided. Organizations and readers are encouraged to apply this intelligence responsibly and in compliance with all applicable laws and regulations.
This blog may reference legitimate third-party services, tools, and others, solely to illustrate cases where threat actors have abused or misused these platforms.