What does this blog cover?
As organizations race to scale multi-cloud environments, the gap between “speed of deployment” and “security” is widening. In this post, we discuss why traditional tools and point-in-time compliance checks are failing to stop breaches, how CI/CD pipelines have become the new attack frontier, and why a shift to Group-IB’s newly-launched real-time, threat-aware CSPM is an effective way to reclaim control in modern, multi-cloud environments.
In order to help businesses robustly manage their cloud and interconnected risk surface, CSPM is designed as part of Group-IB’s Unified Risk Platform (URP), an integrated ecosystem built to protect your internal infrastructure, the network perimeter, cloud environments, and beyond.
Introduction
Cloud adoption in today’s reality: Need for speed (and need for security)
Every modern business is chasing speed, scale, automation, new ways of innovation to keep up with operating in the competitive digital world. And cloud delivers all of it: without “top dollar infrastructure costs” and with always-on operations at competitive speed.
But while productivity compounds in the cloud, security does not. The hastily businesses move to the cloud, the easier it becomes to make mistakes that attackers can exploit.
Cloud and API ecosystems are code by default, meaning they are machine-readable and therefore, exploitable. 96.8% of organizations have cloud misconfigurations, often introduced silently through routine deployments.
Additionally, a common misperception is that when companies migrate to the cloud, security is an inherited feature. But cloud providers secure the infrastructure, not your configurations. They don’t patch your workloads, monitor your access routes, detect threats or escalated permissions, or maintain your compliance posture. This leaves teams struggling to map static regulatory frameworks to dynamic environments, where a single code change can instantly violate policies.
This ignored yet critical detail creates another major gap: reduced time and dependence on security checks. It’s why misconfigurations are now the leading cause of cloud breaches.
Add multi-cloud environments into the mix (AWS, Azure, GCP, Alibaba, etc), and thousands of potential exposure points are created. Each cloud has its own identity model, controls, permissions, storage rules, logs, and APIs. As these environments interconnect, they create dynamic systems where cloud visibility and risk detection become difficult, let alone prioritizing patching.
Often, businesses place their faith in traditional tools, saying, “we bought a SIEM, so we’re covered,” or “our third-party platform handles cloud security.”
But SIEMs read logs, detect events, and native platforms only see within their own environment: AWS sees AWS. Azure sees Azure. GCP sees GCP. Without unified visibility across all clouds, blind spots remain and proliferate.
To secure the cloud at the speed it operates, organizations need:
- real-time misconfiguration detection
- unified multi-cloud visibility
- threat-aware prioritization
- continuous (not point-in-time) compliance
This is where Cloud Security Posture Management (CSPM) becomes indispensable.
What are the major security challenges in modern cloud?
Most cloud exposures aren’t the result of a hack. They’re the result of misconfigurations and the absence of real-time exposure awareness and continuous posture monitoring that can detect active threats before they become incidents.
Here’s a recent example that reinforces this point.
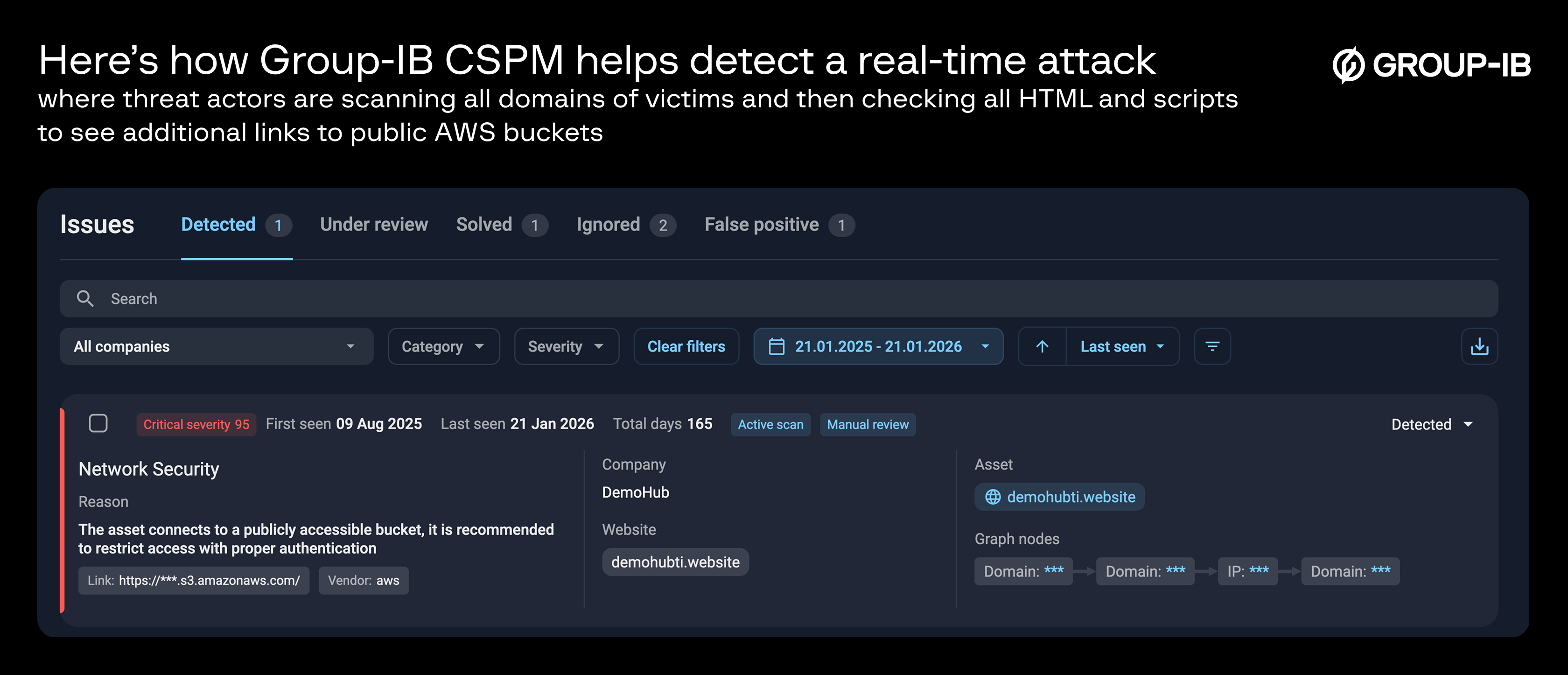
In mid-2024, the Snowflake breach affected 160 client cloud environments, which were configured and accessed, exposing sensitive customer data such as call records, personal information, and other confidential information across multiple enterprises.
While the data was later secured, even minutes-long exposures can cause breaches and open risks, in a time when automated scanners constantly crawl the web. And instances like these don’t live in isolation; they’re common, but can be contained in real-time with a CSPM tool that would’ve flagged the misconfiguration of public ACL immediately, issued an alert, and allowed security teams to remediate it.
A wider range of cloud risks is created due to overlooked configurations like exposed storage buckets, undefined IAM roles, database services, misconfigured network controls, and insecure interfaces. Let’s look at other ways where an insecure cloud is leaving your organization exposed and vulnerable.
Limited understanding of what’s exposed and where
Most organizations today are resorting to more than one cloud provider (for reasons like avoiding dependence on a single vendor, team preferences, or different business units choosing different tools). This means they must now manage not just one platform, but an ecosystem of multi-cloud, multi-frameworks, multi-accounts, identities, and more.
These environments create both existing and new unseen exposures, often exploited by attackers to steal sensitive files, upload malicious code or payloads, or escalate privileges and move laterally across the infrastructure. And while visibility into misconfigurations isn’t enough, context is needed to avoid getting lost in raw lists that cause trails of alerts. Teams must know which misconfigurations are actually exploitable (is this misconfiguration reachable from the internet? Is it exploitable in an attack path?).
Exploits often transcend cloud and services; visibility and remediation need to as well. Organizations need cross-cloud visibility and intelligence to understand the full scope of risks and the severity of each, to focus on threats versus false alarms.
Group-IB CSPM enables automated protection powered by our proprietary Threat Intelligence. Together, it ensures that your cloud posture isn’t just monitored, but is continuously evaluated against real attacker activity, allowing teams to overcome critical gaps promptly.
Compliance vs continuous compliance
Compliance teams, auditors, and even security leaders often assume that establishing compliance once and then running periodic checks will make their cloud secure enough.
But the work doesn’t end there…
Checking for deviations, mapping systems to evolving regulations and frameworks (CIS benchmarks, NIST, ISO, GDPR) is a manual, labor-intensive task requiring weeks.
This check-by-check process might make you compliant at a point in time, but not in the present, as threats keep emerging.
Here’s a real scenario that explains how:
“We just passed our cloud compliance audit, so we’re 100% secure now.”
— a healthcare organization verified.
Three weeks later, they faced a critical exposure in one of their production workloads. Open storage buckets and undefined permissions that could have led to a breach were discovered, despite them being fully compliant with the frameworks they were assessed against.
Where’s the gap? They relied on a SIEM tool for monitoring, but never enabled real-time exposure monitoring with a modern CSPM solution. Several encryption-at-rest settings were not enforced, causing unknown “non-compliance” with their own internal policies.
Once CSPM platforms are activated – built-in visibility, continuous checks, automated alerts- the compliance conversation changes entirely.
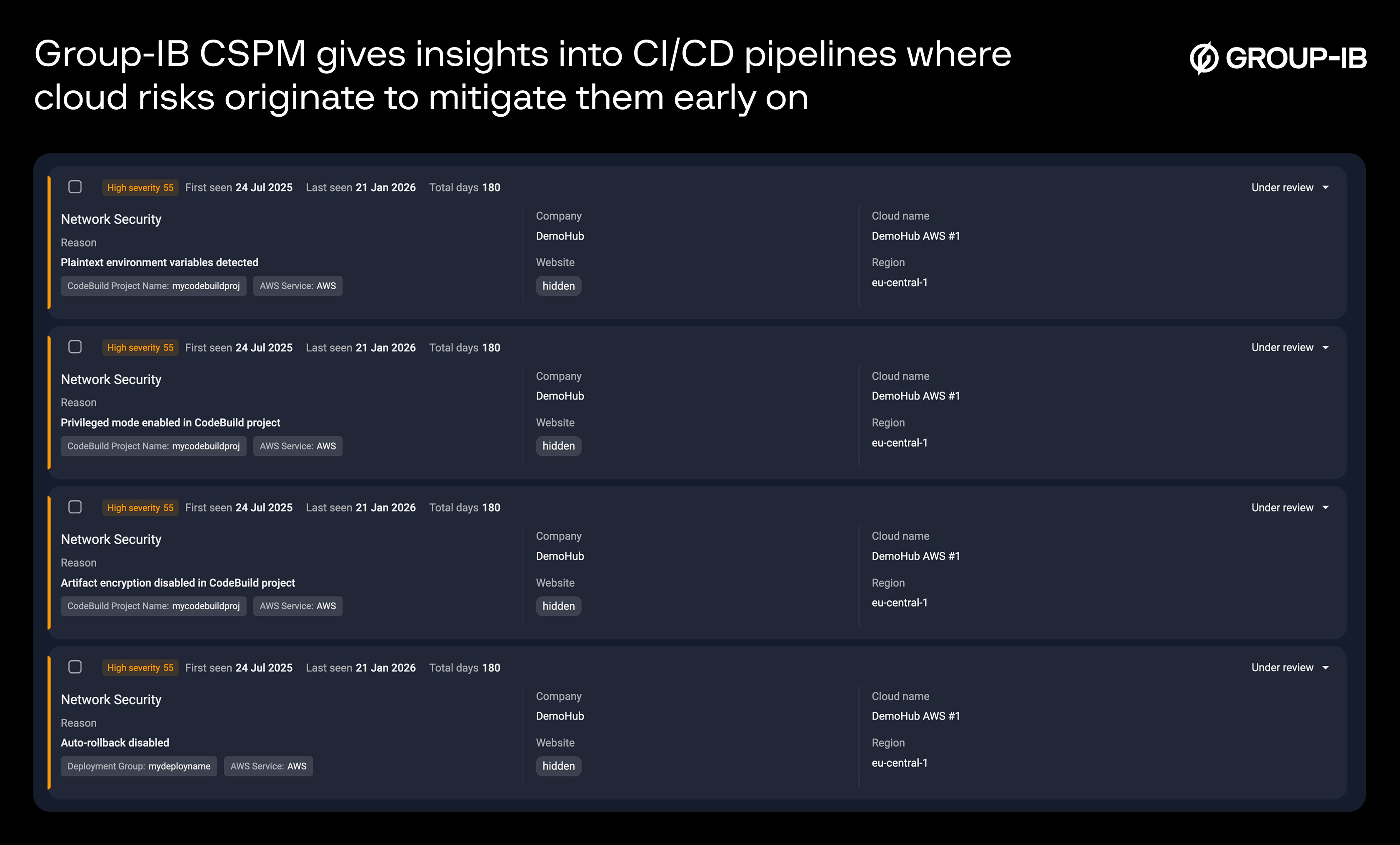
Risks begin in the build pipeline, not only in post-launch
Most cloud risks begin with exploited build systems, not the post-launch environment. CI/CD (Continuous Integration / Continuous Deployment) pipelines act as the DevOps team’s builder and deployer of cloud — compiling code, reducing error-prone changes, running tests, building containers, and deploying updates into cloud environments.
But if misconfigured, CI/CD pipelines can give adversaries a direct route into the post-launch environment.
Because CI/CD is an integral part of the cloud development lifecycle, from building to testing to deployment, these systems become high-value targets. This makes pipeline security absolutely critical; thus, the need for “shifting cloud security left.” It means teams need to integrate security checks earlier in the CI/CD pipeline to catch misconfigurations before they reach post-launch. While most CSPM tools don’t perform CI/CD security checks (usually offered only in CNAPP platforms).
Group-IB CSPM, however, does provide this feature to help teams secure the cloud by design. With CSPM + CI/CD security in one platform, it helps secure the cloud proactively across build, deploy, and runtime stages.
Most misconfigurations are noise; real risks need real-time prioritization
Teams receive hundreds of misconfiguration warnings, but 90% are low-impact or false positives. The lack of context around these alerts makes prioritization difficult. If this does not sound painful, imagine teams staring at 3,000 alerts across three clouds — wondering which ones actually expose workloads or violate critical policies.
To top that, remediation must be real-time as adversaries are already weaponizing automation to find vulnerabilities across your clouds.
So, in addition to having multi-cloud visibility, security teams need prioritization based on real-world exposure data and attackers’ active tactics.
With Group-IB CSPM, businesses gain real-world exposure validation of cloud assets through Group-IB Attack Surface Management and live threat intelligence, giving them the threat context needed to correlate misconfigurations with attacker infrastructure, making sure that critical fires in your cloud are put out first.
Different clouds, disconnected tooling
Cloud teams use multiple tools, each tied to their own environment. In multi-cloud structures, this means teams have multiple dashboards, non-aligned risk definitions and scoring systems, creating not just ambiguity, but more tools to handle, and no correlations.
This puts teams back to square one: remediating manually, and often wasting hours fixing the same escalated issue across different dashboards.
Most organizations count on native platforms and telemetry, or even Attack Surface Management (ASM), Threat Intelligence (TI), and SIEM tools, to prioritize what matters most across every cloud they operate in. But they don’t automatically correlate with external exposure, threat activity, or logs captured in other clouds.
This is why workflow alignment is required. Group-IB CSPM supports it by allowing teams to push findings into existing tools or pull data via API so risk remediation stays non-ambiguous, centralized, and aligned across all cloud environments.
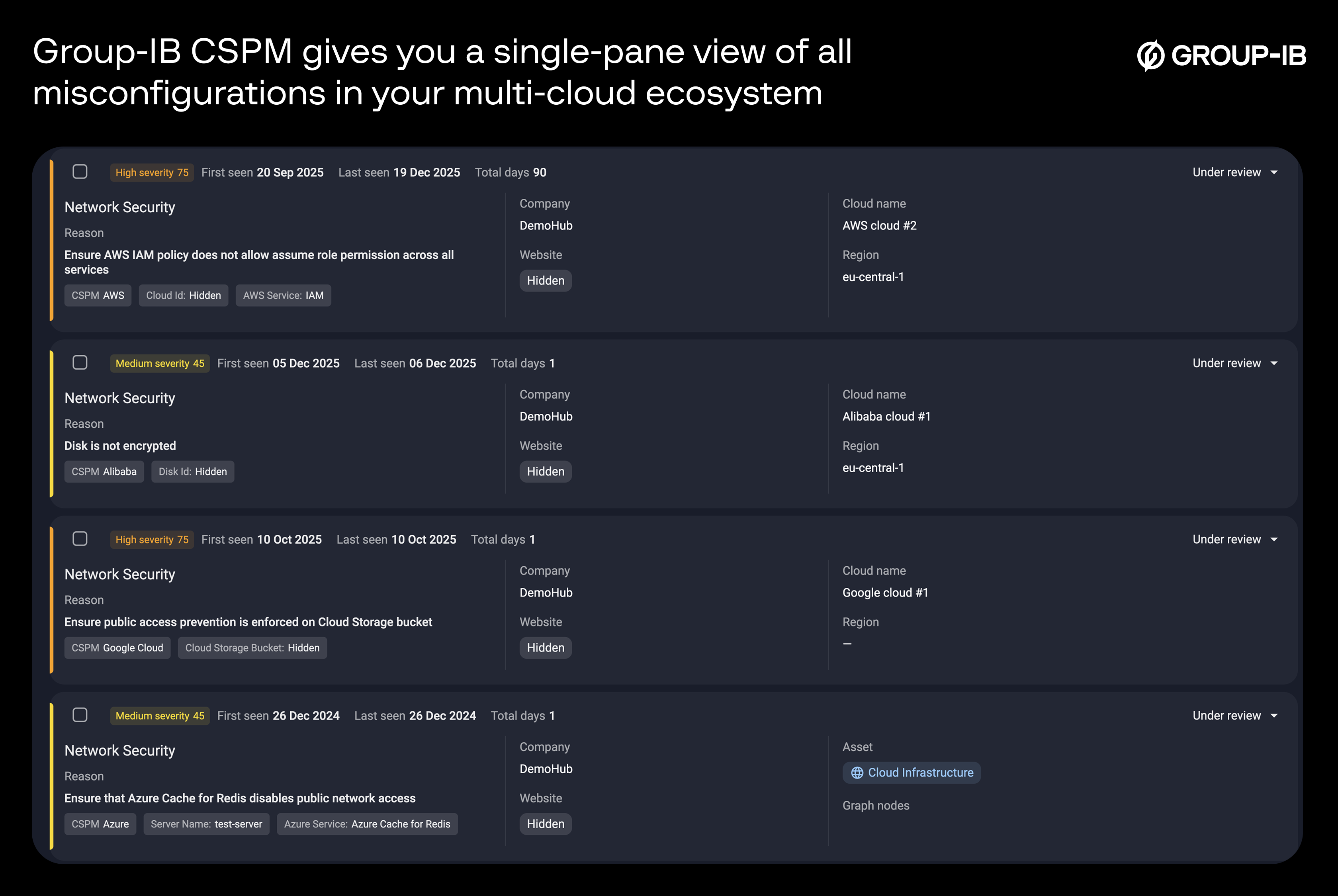
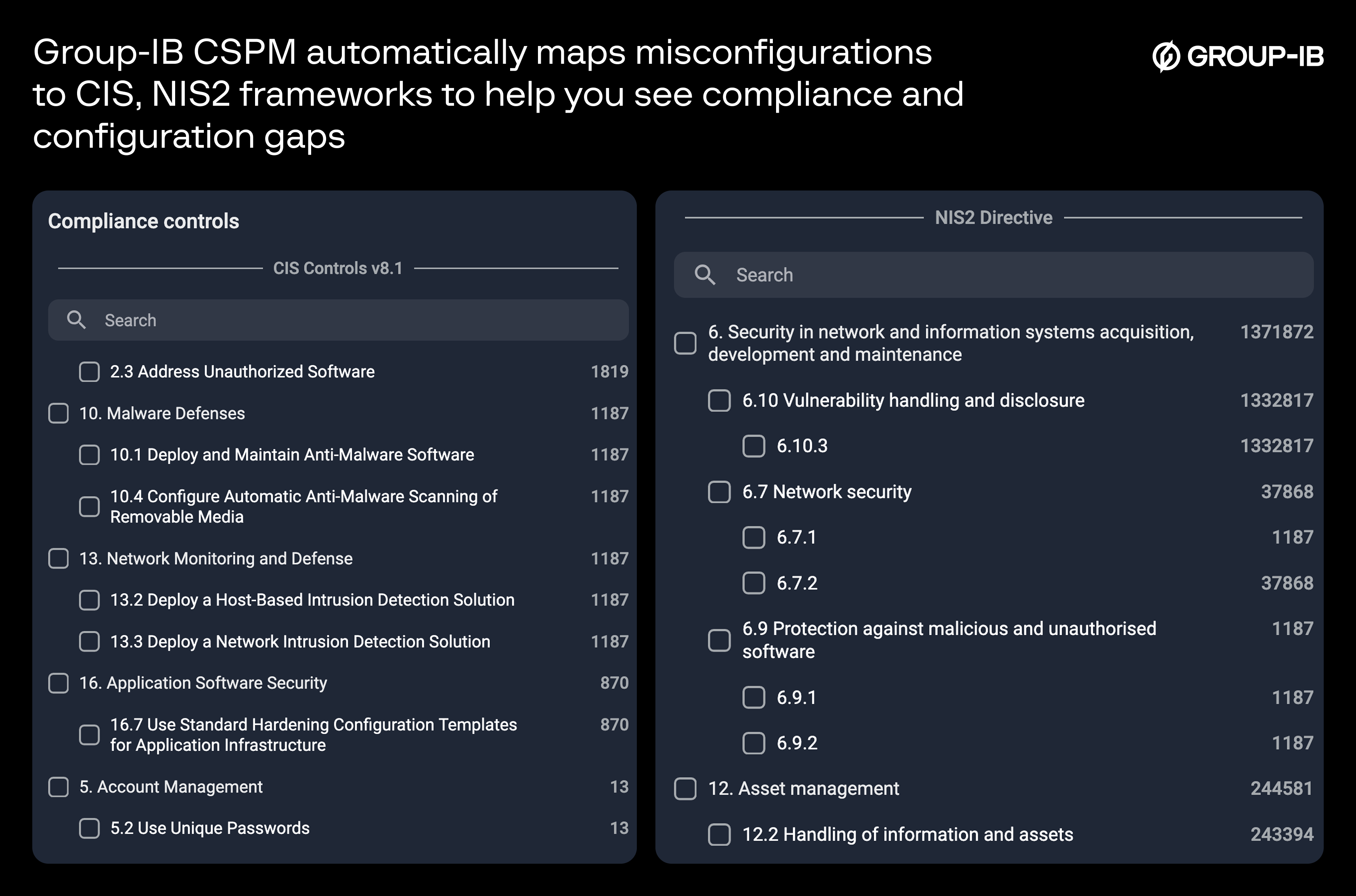
Prioritize misconfigurations that matter: Group-IB Cloud Security Posture Management (CSPM)
Cloud adoption continues to grow, but not all implementations succeed. Organizations need to match scale with localized control. The industry collectively identified the challenge and presented an answer through Cloud Security Posture Management (CSPM) solutions.
However, most CSPMs address misconfigurations without understanding the full context of risk. Group-IB Cloud Security Posture Management (CSPM) is built to tackle cloud challenges holistically; beginning with secure cloud-by-design (very few CSPMs integrate CI/CD misconfiguration checks), offering cross-cloud coverage, built-in compliance, and threat-aware risk scoring, delivering a far more accurate view of cloud risk.
Group-IB’s solution provides the inside-out view of posture across cloud assets, combining Group-IB Attack Surface Management (ASM) and Threat Intelligence (TI) for an outside-in view of internet-facing exposures. Together, they enrich visibility and risk prioritization. By blending inside-out posture with outside-in exposure intelligence, the platform closes the gap between internal compliance posture and external attack surface threats.
Group-IB CSPM connects directly to public cloud environments like AWS, Google Cloud Platform (GCP), and Microsoft Azure via API keys (no agents required). This allows it to automatically discover cloud assets, detect misconfigurations, and run compliance checks against major frameworks (CIS and NIST). The integration is fully SaaS-based, meaning setup is up and running in minutes, without any operational disruption.
Multi-cloud security is a messy undertaking. Group-IB streamlines it like no other: Built for a multi-cloud-first world, CSPM maps risks across all clouds and gives a single, unified point of view of what matters most.
Adding to that, CSPM gives an opportunity to move beyond reactive and manual detection to automated protection powered by Group-IB’s Threat Intelligence, turning misconfiguration alerts into real-world, threat-aware prioritization.
Automated compliance checks save your team weeks of grunt work: It’s the ability to continuously map posture to frameworks, which offers huge relief for compliance and security teams alike. These automated compliance checks are complemented by exportable reports, helping with compliance and reporting use cases.
Not just findings, remediation is part of the package: Group-IB CSPM provides an open API, allowing customers to integrate findings and posture data into their existing security controls, such as SIEM or SOAR platforms. So, real-time deviation alerts are integrated into ticketing systems.
Group-IB Cloud Security Posture Management (CSPM)
Frictionless architecture. Powerful integrations. Real-time clarity on risks that matter.
Most CSPM tools identify misconfigurations, but lack the capabilities to further detail these exposure warnings into real-world attack paths. Group-IB CSPM bridges the gap between noise and action. It combines configuration analysis with threat intelligence and attacker visibility, allowing teams to focus on what is actively exploitable and how, not just what is misconfigured. Here are two common, real-life cloud risks that modern businesses face: data exposure and cloud ransomware without malware. Group-IB Cloud Security Posture Management helps businesses mitigate these threats, along with a wide range of other cloud security and compliance challenges. To explore the full range of supported use cases and capabilities, visit the Group-IB CSPM solution page.
Use Case 1: Cloud leaks through misconfigured storage
Cloud data leaks today often don’t look like a “hack” at all; they look like exposure. A single missing guardrail or an overly permissive access rule can quietly turn an S3 bucket into an internet-facing data source, making sensitive files readable from the outside without triggering any “break-in” alerts. And because attackers typically favor the simplest, most repeatable paths to data exfiltration, misconfigured cloud storage is an especially attractive target.
Group-IB CSPM is built to catch exactly these “easy-to-miss, high-impact” gaps. It continuously checks the configuration patterns that most often lead to public exposure, and verifies that S3 Block Public Access guardrails are actually enabled to override accidental policies and ACLs. The result is a fast, clear signal: which buckets are externally reachable, why, and what needs to change to close the leak before it becomes an incident.
Use Case 2: Cloud ransomware without the use of malware
Cloud ransomware doesn’t always require malware. With stolen cloud credentials, attackers can use native management APIs to enumerate storage, exfiltrate high-value data, and then turn recovery into a crisis by mass-deleting objects, overwriting them, or forcing encryption workflows that deny the owner access (sometimes while also changing access controls to slow down incident response). Because these activities often look like normal administrative behavior, the most effective defense is preventative guardrails.
Group-IB CSPM continuously verifies guardrails and quickly surfaces the risky gaps: whether critical datasets have immutability protection, whether encryption is enforced under customer-managed keys (so you retain cryptographic control), and if identity permissions create easy paths to destructive write actions, large-scale data exfiltration, or privilege escalation. The result is actionable: identify which data stores are ransomware-resilient and which ones are one leaked credential away from irreversible loss.
These use cases show how configuration gaps can quickly escalate into real risks. To see your cloud misconfigurations and the risks they open before attackers do, request a Group-IB Cloud Posture Management (CSPM) demo or talk to our experts today.