Background
In September 2024, Group-IB supported Operation Kaerb, an international action coordinated by Europol and Ameripol with European and Latin American partners, which dismantled iServer. This phishing-as-a-service platform has been active since 2019.
Investigators attribute approximately 1.2 million targeted devices and about 483,000 victims worldwide to iServer; coordinated raids led to 17 arrests across Argentina, Chile, Colombia, Ecuador, Peru, and Spain, and the platform’s domain was seized. With the context established, we turn to the operational impact of the takedown.
Impact
— Disrupted a mature PhaaS supply chain used to unlock and resell stolen devices.
— Eliminated an industrialized workflow that validated credentials/OTPs in real time and returned confirmed data to operators.
— Produced evidence packages enabling prosecutions and takedowns beyond the initial arrests.
— Reduced near‑term smishing/credential‑harvesting activity against cloud‑based mobile services in Spanish‑ and Portuguese‑speaking markets.
Storyline
Group-IB’s investigation revealed that iServer operates as a platform where the owner/developer sells access to “unlockers,” who, in turn, offer phone-unlocking services to criminals using stolen, locked devices.
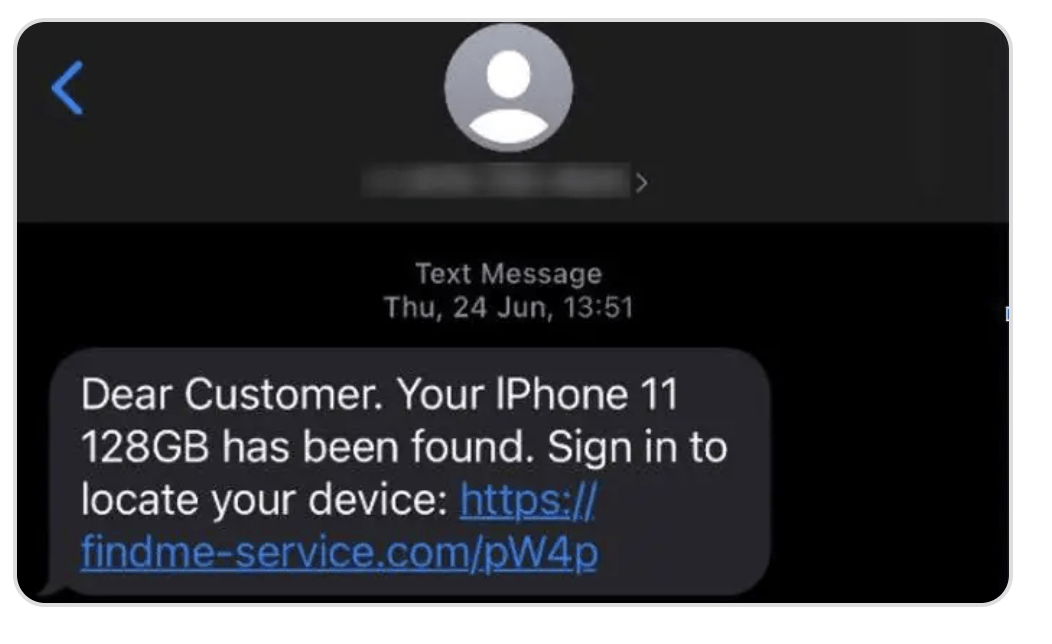
Unlockers first collected device context such as IMEI, language, owner details, and contact information, often from Lost Mode screens or the victim’s cloud account, then selected an attack scenario inside iServer.
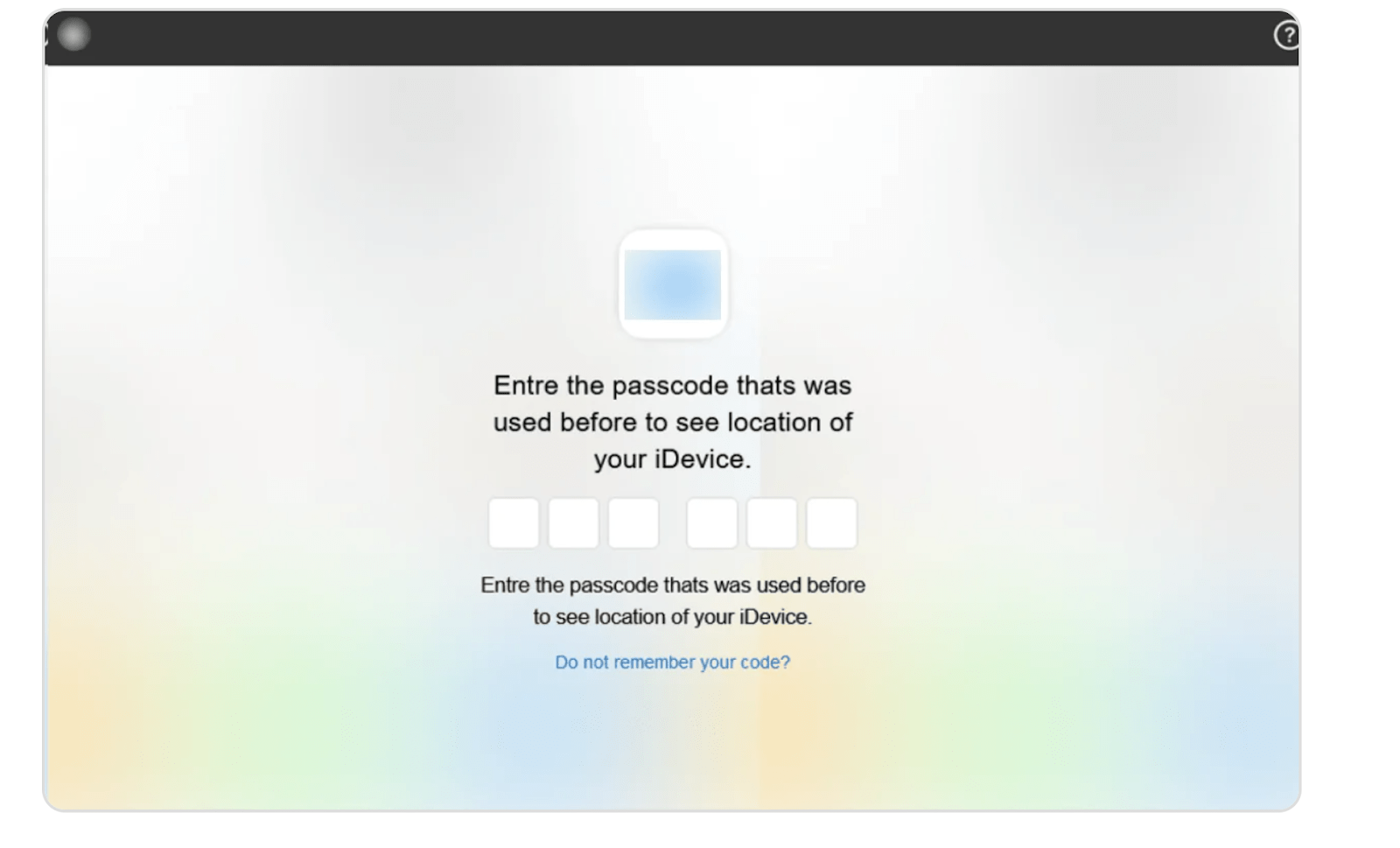
The platform generated brand-mimicking phishing pages hosted on iServer-provided or operator-controlled domains. Targets received SMS links, which were passed through a redirector that filtered visitors and prompted them for credentials, and, when necessary, one-time codes.
Submissions were validated in real-time and returned via the iServer interface, enabling device unlock and resale. This model was observed primarily across Spanish- and Portuguese-language operations in Latin America, with spillover to Europe and North America.
Group-IB mapped the infrastructure, operator roles, and workflow dependencies, creating a clear, evidentiary picture that enabled coordinated enforcement, as described below.
Screenshot of iServer’s phishing page disguised as a popular cloud-based mobile service website.
And Justice For All…
Using the shared intelligence, Europol, Ameripol, and national agencies executed synchronized raids, apprehended the platform administrator, seized backend assets and domains, and took iServer offline as an operational service. With the takedown complete, the case also offers practical lessons for defenders.
What Kaerb Taught Us About Fighting Phishing at Scale
Operation Kaerb reminded us that even the most polished cybercriminal operations leave cracks, and all it takes is the right eyes to find them. iServer built a business around digital fraud, offering a service that made phishing campaigns easy, fast, and dangerously scalable.
But it wasn’t bulletproof. Small mistakes in how domains were set up, the reuse of infrastructure, and sloppy operational habits provided investigators with the threads they needed to unravel the entire operation.
Phishing today is not the work of a single attacker behind a keyboard; it’s a service that anyone can rent. And with that comes new risks for banks, telecom providers, and the millions of people who trust their phones with their personal information.
What we learned from Kaerb, how the infrastructure worked, how it spread, and how it was monetized will help us stay one step ahead of whoever tries to build the next version.
And as always, Group-IB remains focused on helping dismantle the systems that fuel cybercrime, one platform, one takedown at a time.