Background
The individual at the center of the takedown was one of the most prolific data leak actors operating globally.
His campaigns began in 2020, with initial targets in Thailand, where he focused on exfiltrating sensitive customer data from corporations and demanding hush-money payments. If refused, victims faced a PR nightmare: they alerted regulators, journalists, or customers directly to the breach. These weren’t empty threats; they were part of a sophisticated extortion strategy designed to weaponize reputation.
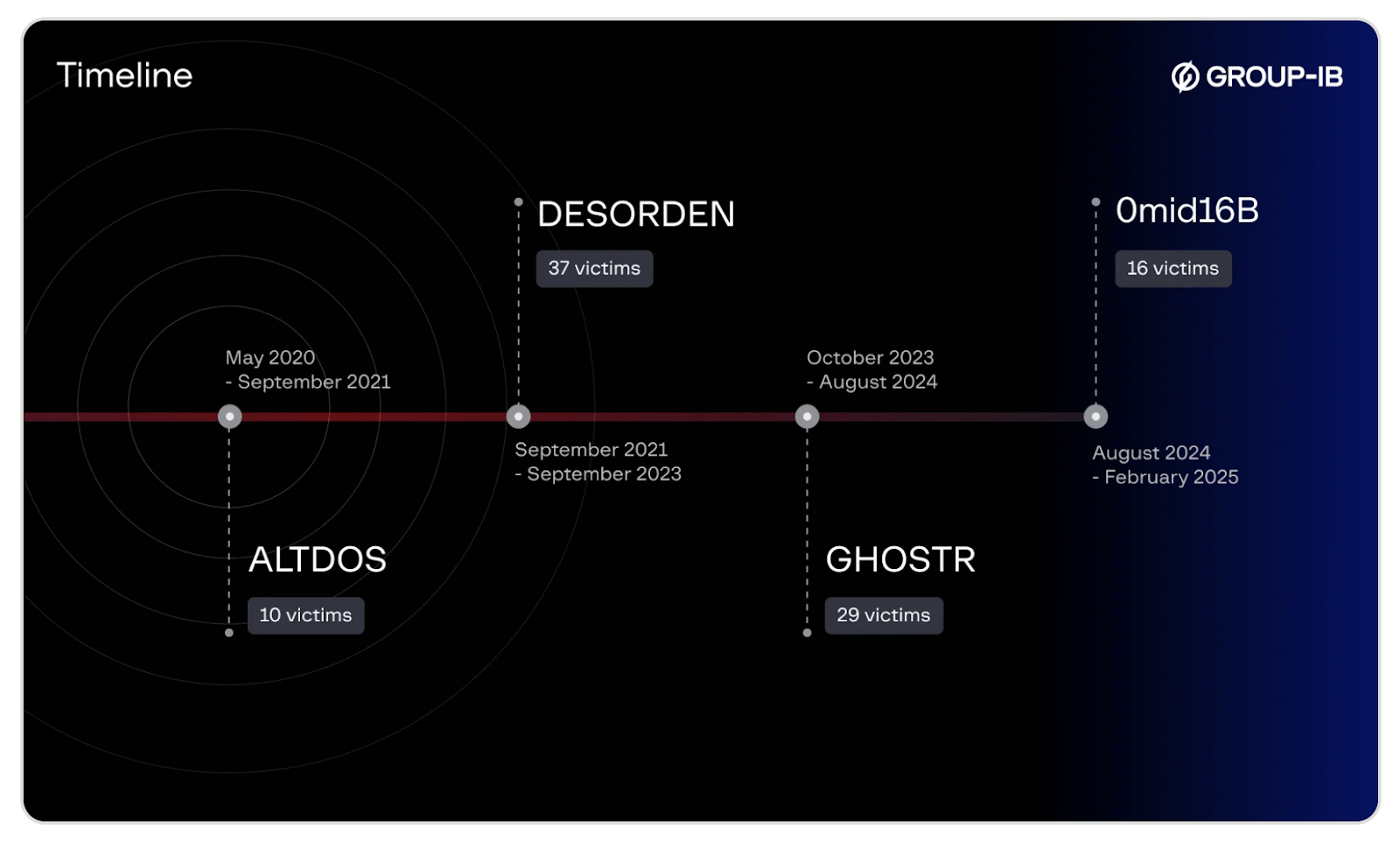
Over time, his targeting expanded across the Asia-Pacific region, reaching organizations in Singapore, Malaysia, Indonesia, India, and beyond. By 2024, he was also breaching companies in the United Kingdom, the United States, Canada, and the Middle East, under the aliases GHOSTR and 0mid16B.
His victims spanned diverse industries like healthcare, finance, logistics, technology, e-commerce, retail, insurance, property, and recruitment. The actor’s adaptability, evolving aliases, and direct psychological pressure tactics made him uniquely disruptive in the cybercriminal ecosystem.
Behind the Scenes
His first move was small and a little clumsy. In April 2021, he appeared on CryptBB as mystic251, posting a single thread about a database from a “popular furniture retail chain in Singapore.” The forum, which was heavy on hacking talk, barely reacted. The lack of reaction seems to have shaped his next step.
He pivoted to RaidForums under the handle altdos, and the difference was immediate. The same kind of post drew numerous replies, giving him an audience and a market. It’s a neat tell from the early phase where he was still learning how and where breached data sells.
Storyline
In late 2020, Group-IB’s Threat Intelligence and High-Tech Crime Investigation teams began investigating a series of database breaches targeting organizations in Thailand and Singapore. The threat actor behind these incidents operated under the alias ALTDOS. Over time, the persona rotated through multiple aliases and drew notable media attention.
Group-IB investigators analyzed dark-web activity to identify actors specializing in data breaches, who targeted victims in Asia, particularly Thailand, and used Matrix for communication. Threat Intelligence data showed that between 2022 and 2023, DESORDEN was the only known actor matching that profile, strengthening the link between his operations and his preferred communication channel.
The First Traces
The first confirmed breach under ALTDOS involved a property investment firm in Thailand. DataBreaches.net reported on 10 December 2020 that ALTDOS emailed the company’s executives on 5 December, demanding 170 BTC, worth over US$3 million at the time, to keep the stolen data private. When the firm refused, ALTDOS released the compromised information publicly, setting the pattern for later incidents. Our subsequent review indicates this actor also had earlier, unreported victims before December 2020.
Investigators discovered unauthorized RDP access tied to a vulnerable server. Analysis revealed the use of SQL injection and tools, such as sqlmap, resulting in the exfiltration of internal databases containing personal records, contracts, and contact information.
To attack victims, the cybercriminal exploited vulnerable Remote Desktop Protocol (RDP) servers to gain unauthorized access to sensitive data. The cybercriminal then installed a beacon of a cracked version of the CobaltStrike to control compromised servers. Based on Group-IB’s findings, the cybercriminal did not perform significant lateral movement, and exfiltrated data to their rented cloud servers for further blackmailing of a company.
He would then a beacon of a cracked version of the Cobalt Strike pentesting toolkit to control compromised servers.
Group-IB said it did not observe the actor performing significant lateral movement, focusing on quickly exfiltrating data to rented cloud servers.
The actor stuck to a familiar playbook and focused on firms across the ASEAN region. Over time, the approach evolved. Complete data sets began appearing on dark-web forums like CryptBB and RaidForums, a public dump meant to warn future targets about the cost of refusal. The next step was monetization at scale, with the same stolen databases offered for sale to broaden reach and maximize profit.
By 2021, the alias DESORDEN emerged on dark web leak forums, touting access to high-value databases and offering samples to attract buyers.
The investigation was complicated by the actor’s repeated changes in nickname and tradecraft. Group-IB identified that from 2020 through February 2025, the individual operated under several aliases, including ALTDOS, DESORDEN, GHOSTR, and 0mid16B.
As DESORDEN gained popularity on criminal forums, the actor’s footprint expanded beyond Thailand to Singapore, Malaysia, and Indonesia. What followed was a methodical sequence of attacks: breach, exfiltrate, extort, and if the company didn’t pay, sell the data or spark reputational damage through public exposure.
The Turn of the Tide
Group-IB reports that between 2023 and 2024, GHOSTR, apart from DESORDEN, was the only other actor using Matrix for contact while targeting Thai victims in data breaches.
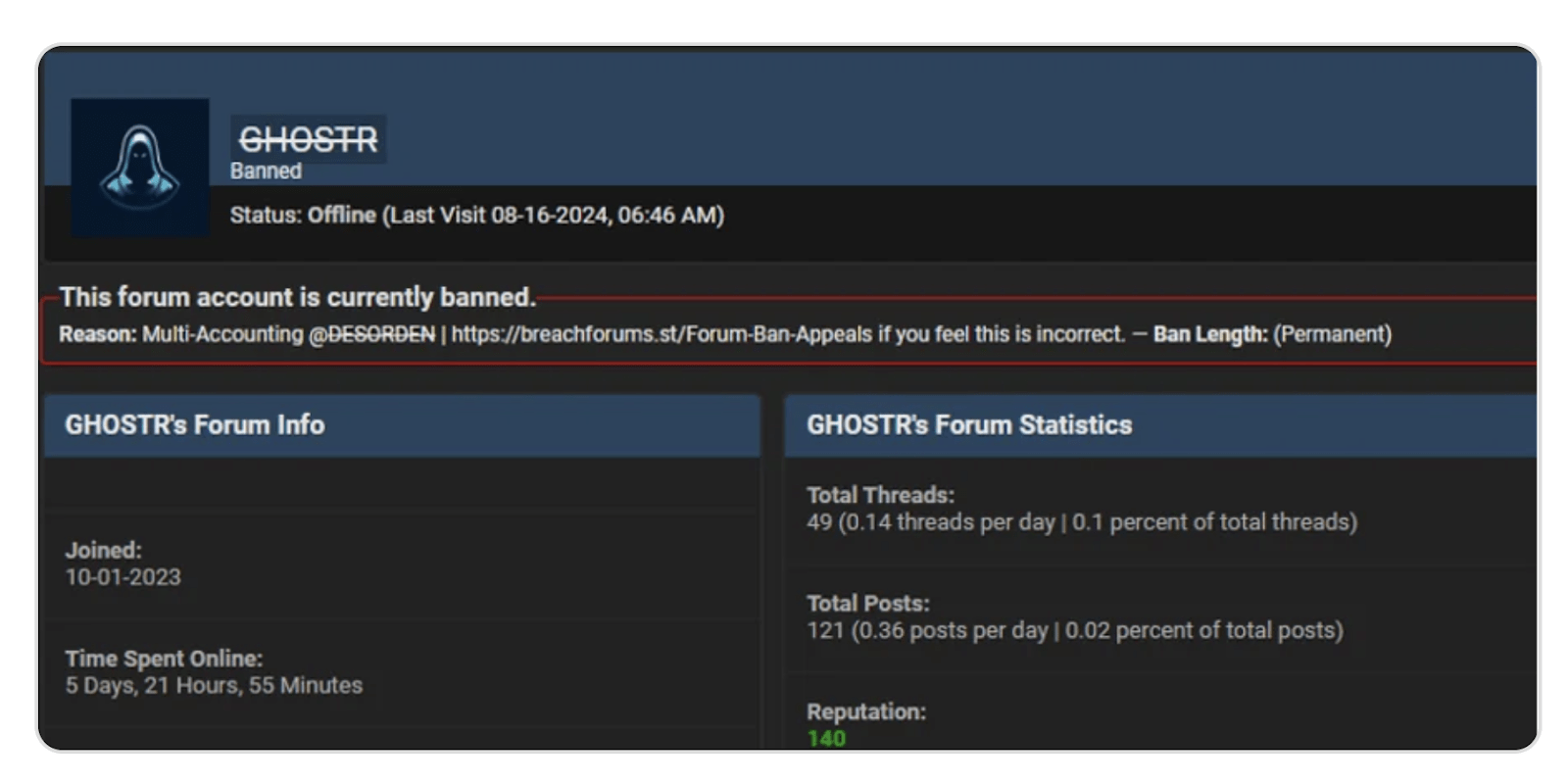
The actor was banned from a central forum in mid-2023 for scamming buyers, and again in 2024 for multi-accounting, prompting another alias shift. But the trail was already lit.
Later Targets and Global Expansion
From 2024 onward, the threat actor expanded operations into the United Kingdom, the United States, Canada, and the Middle East. Government agencies were not spared; some were attacked, and sensitive internal records were leaked or weaponized to embarrass public institutions.
Despite lacking custom malware, the threat actor remained dangerous due to its precision and persistence. Attacks required minimal lateral movement; once a system was breached, they exfiltrated straight to cloud servers rented under false identities. The scale of leaks reached 13TB, covering millions of personal records.
And Justice for All
The correlation of technical indicators, dark web monitoring, and behavioral analysis allowed Group-IB to provide the necessary intelligence to the Royal Thai Police and the Singapore Police Force.
Account-activity logs further supported these links, and repeated database overlaps confirmed a single operator. Identical writing patterns, a consistent breach methodology, and an exclusive reliance on Matrix for communication clearly identified the actor as the only one targeting Thai data assets at this scale.
A raid was launched on the suspect’s premises in Thailand. Law enforcement seized electronic devices and luxury goods purchased using illicit proceeds. The arrest marked the end of a multi-year campaign of psychological and digital coercion.
The Royal Thai Police stated that the cybercriminal admitted to focusing on large private companies and steering clear of government agencies, saying he did not want the public to be affected.
What ALTDOS Takedown Taught Us About Fighting Data Breach at Scale
ALTDOS Takedown reminded us that intimidation can be just as potent as encryption, and that fear, when orchestrated carefully, is a weapon in itself.
The attacker built a career out of reputational extortion, turning every breach into a public spectacle and every refusal to pay into a headline. But he slipped. Recycled infrastructure, reused leak formats, and signature behavioral patterns gave investigators just enough to work with.
What we uncovered through ALTDOS Takedown, how extortion was scaled and how digital identities were masked, now serves as a blueprint for stopping the next generation of cyber extortion.
Most importantly, it shows that only coordinated action between private intelligence and international law enforcement can physically dismantle threat actors operating across borders. And as always, Group-IB will be there, uncovering the cracks, connecting the dots, and dismantling cybercrime one takedown at a time.