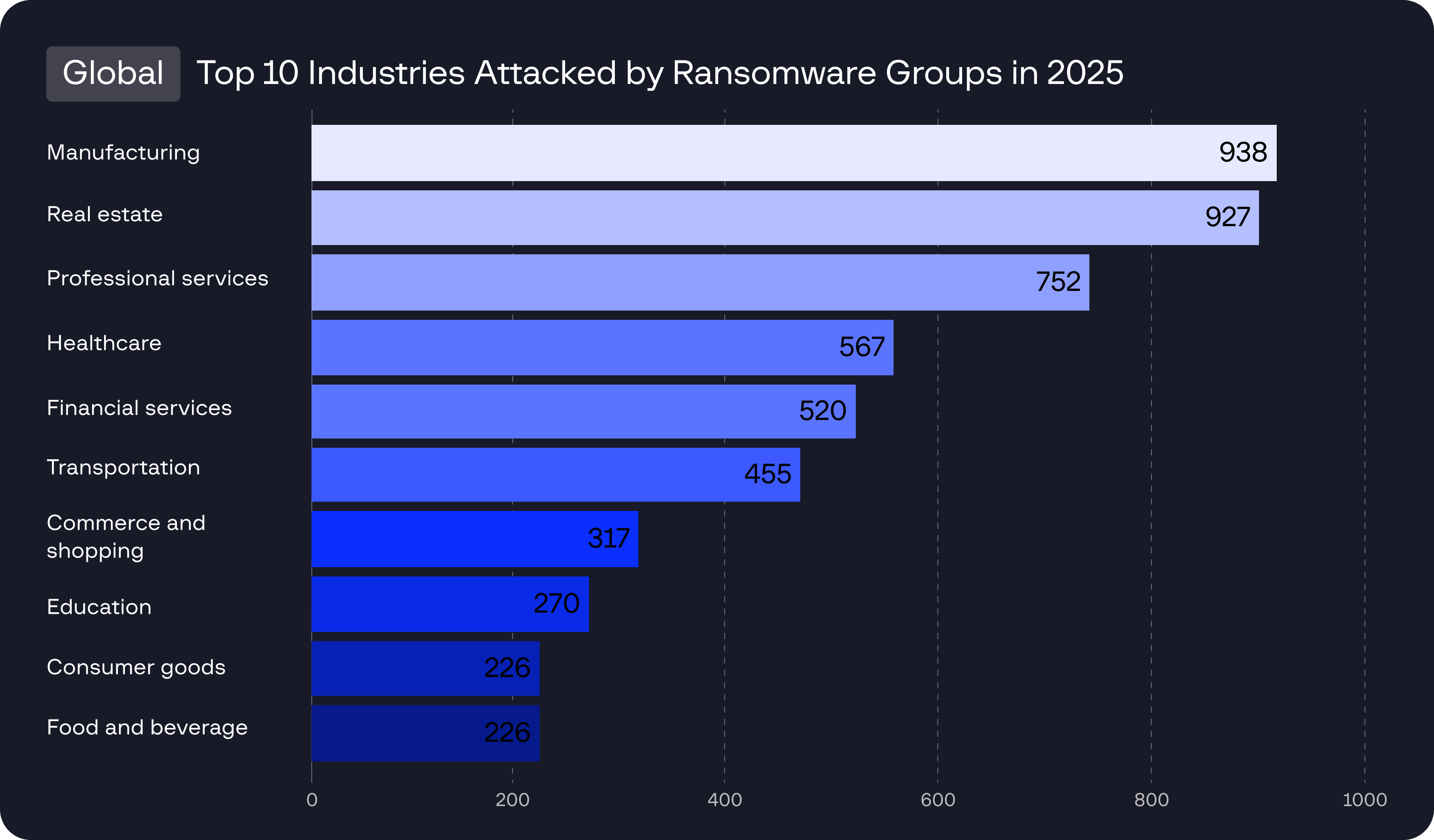
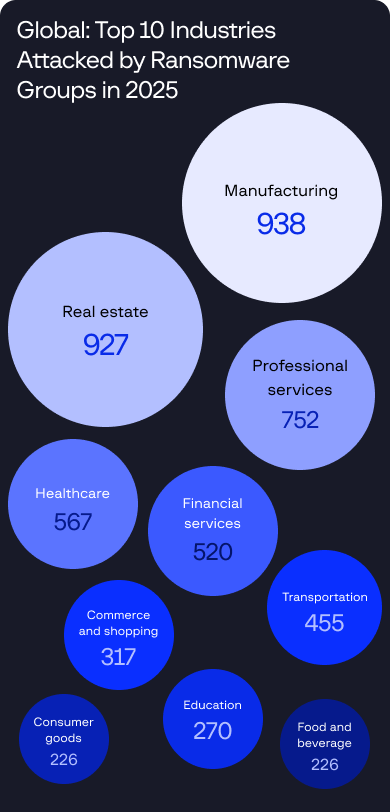
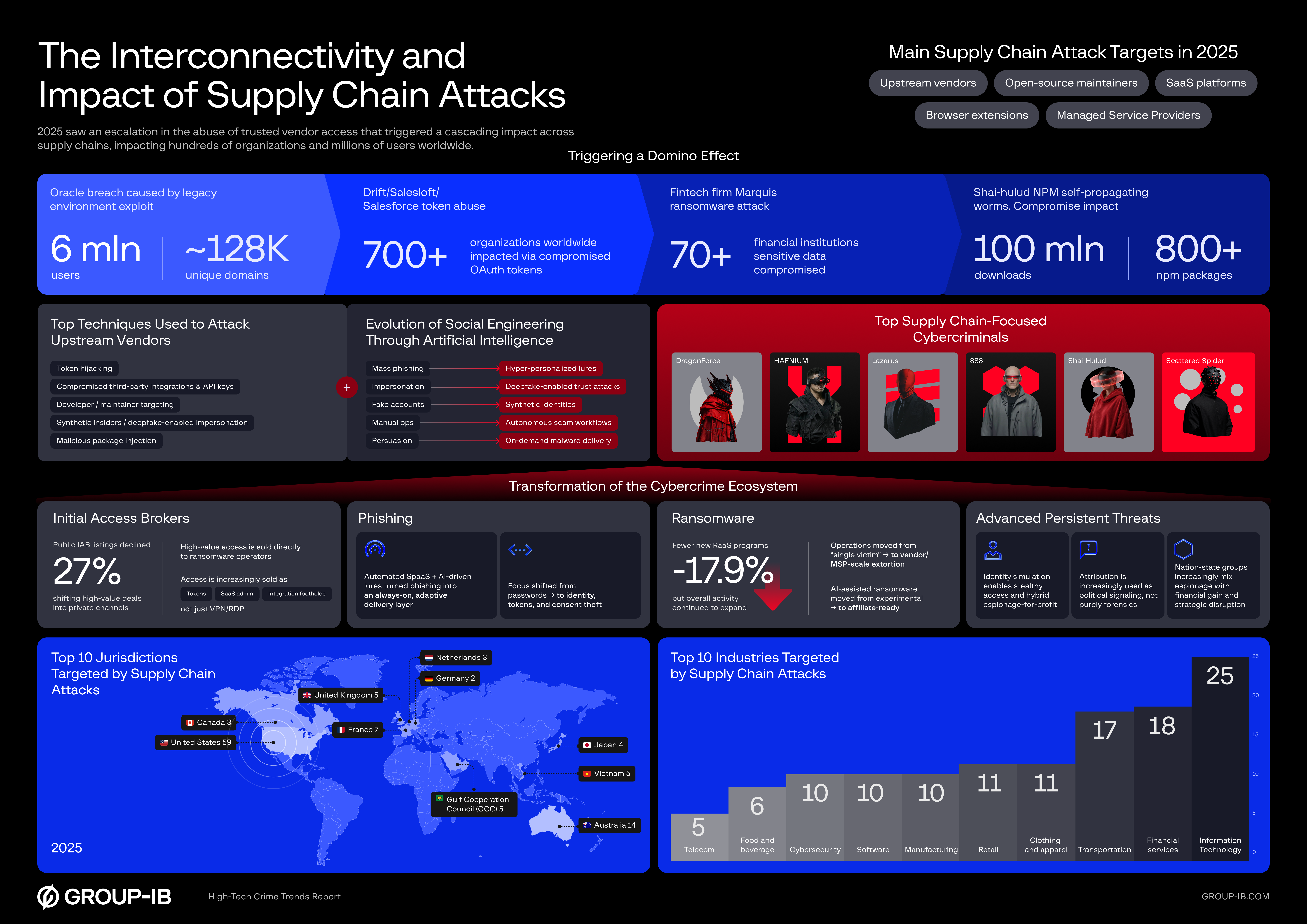
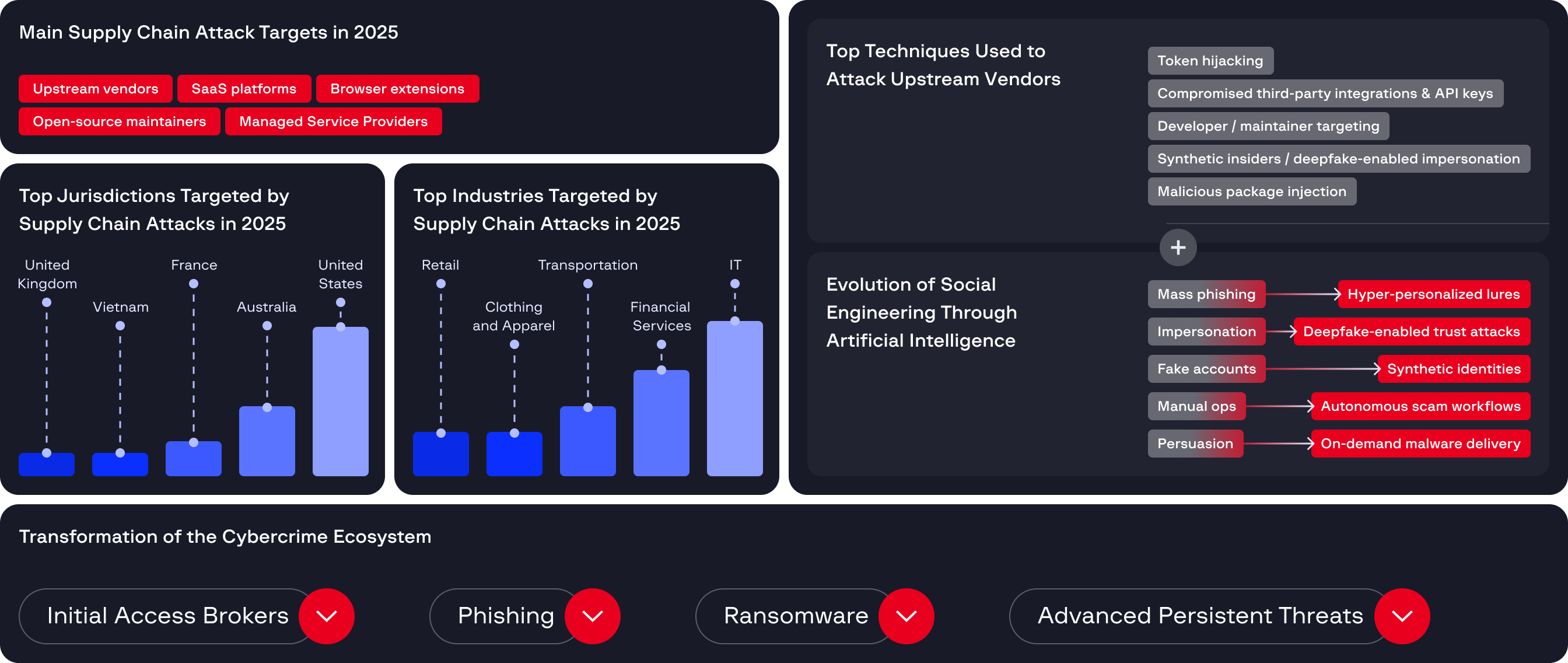
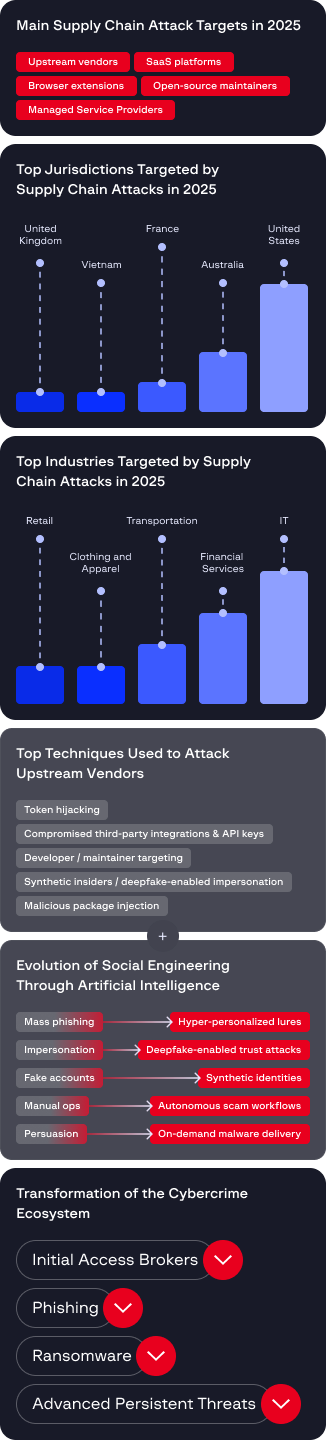
Cybercrime is no longer defined by isolated breaches. By compromising upstream vendors, SaaS platforms, open-source projects, and managed service providers, attackers inherit trusted access to hundreds of downstream organizations, transforming single intrusions into cascading, multi-victim incidents.
The High-Tech Crime Trends Report 2026 reveals how this shift has industrialized cybercrime, exposed the limits of perimeter-based defenses, and elevated identity and trust as the new primary attack surfaces.
verified, monitored, and secured continuously.

around supply chains
surface
are under sustained attack

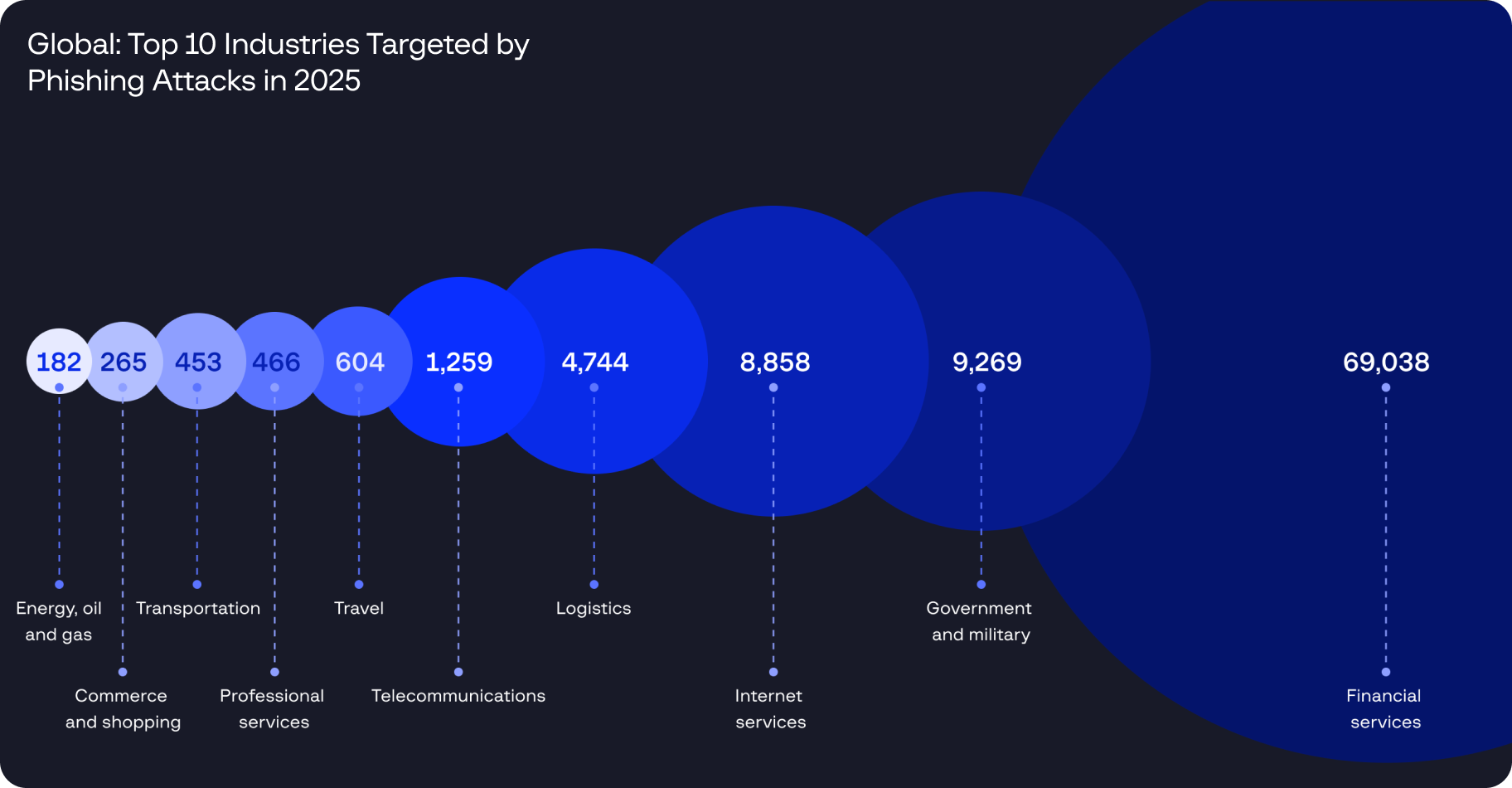
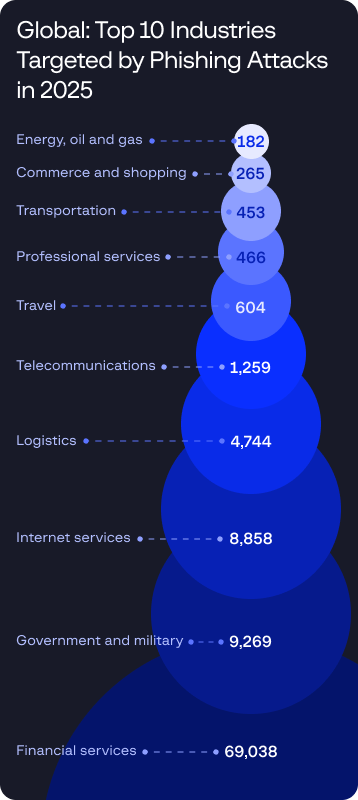
Supply chain compromises now enable attackers to infiltrate widely used software and services, evading traditional defenses while achieving scale from a single entry point. As these threats blend into normal operations and persist across interconnected ecosystems, organizations must assume supply chain risk is inevitable and prioritize visibility, verification, and resilience across their technology stack heading into 2026.




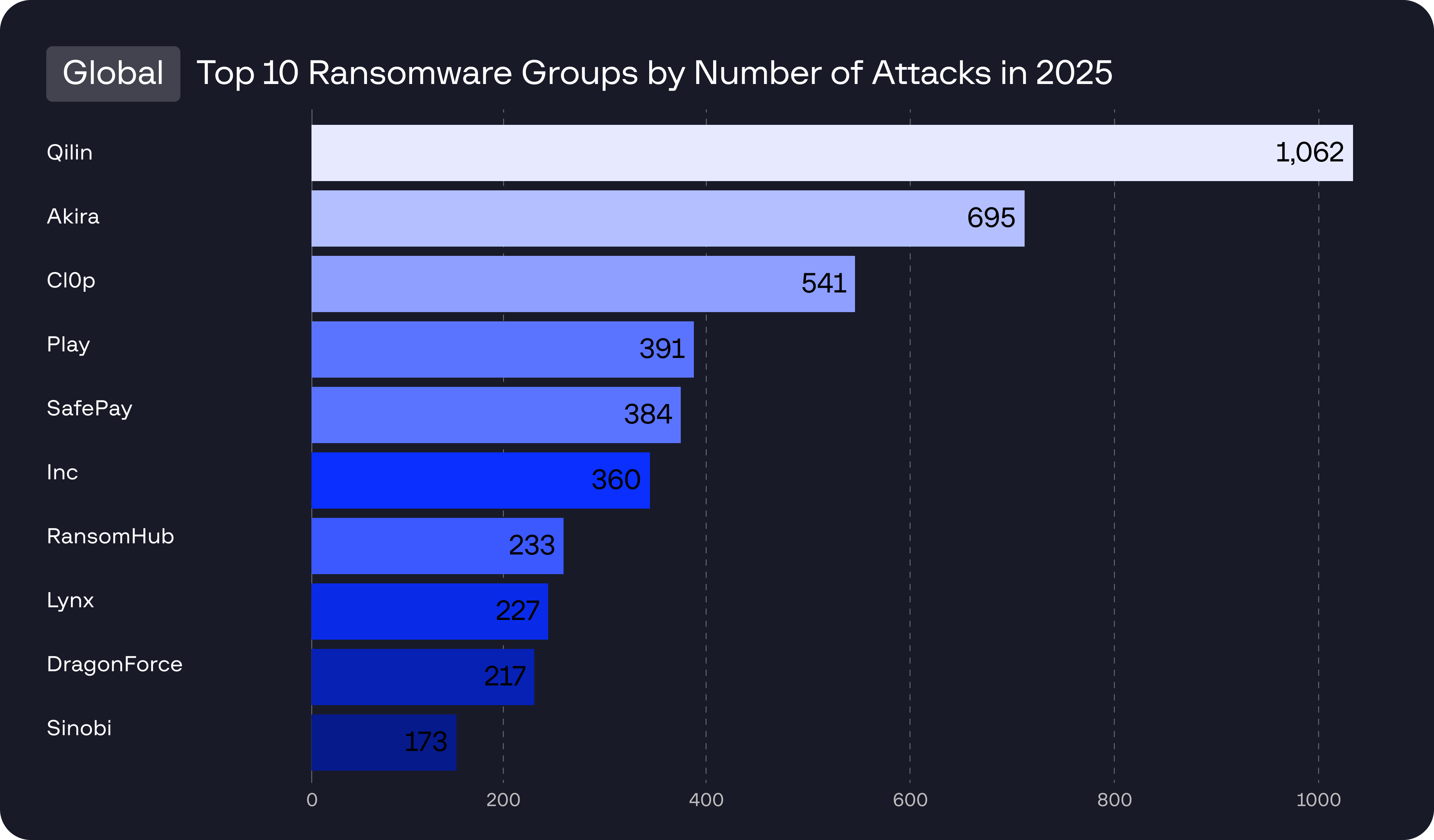
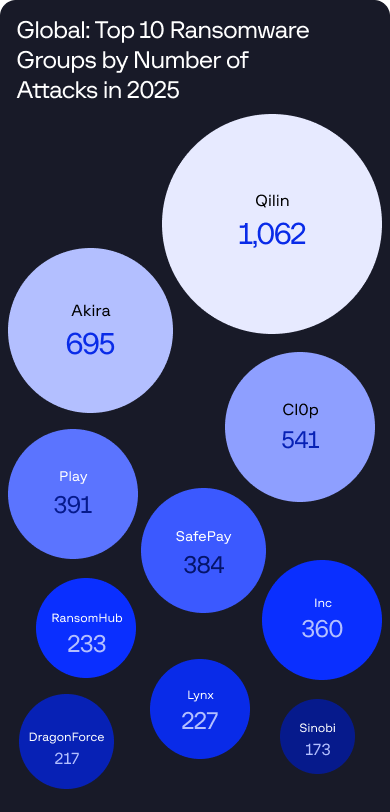
Supply chain compromises now enable attackers to fragmented ransomware-as-a-service groups and structured Initial Access Brokers began operating as integrated partners, while supply chain attacks through MSPs and SaaS platforms enabled scalable, low-friction intrusions.



In several incidents, a single stolen OAuth token enabled access to interconnected tenants, third-party services, and CI/CD pipelines – driving large-scale data exfiltration and lateral movement. Attackers increasingly targeted high-trust integrations, turning identity compromise into a force multiplier for systemic breaches.