Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.

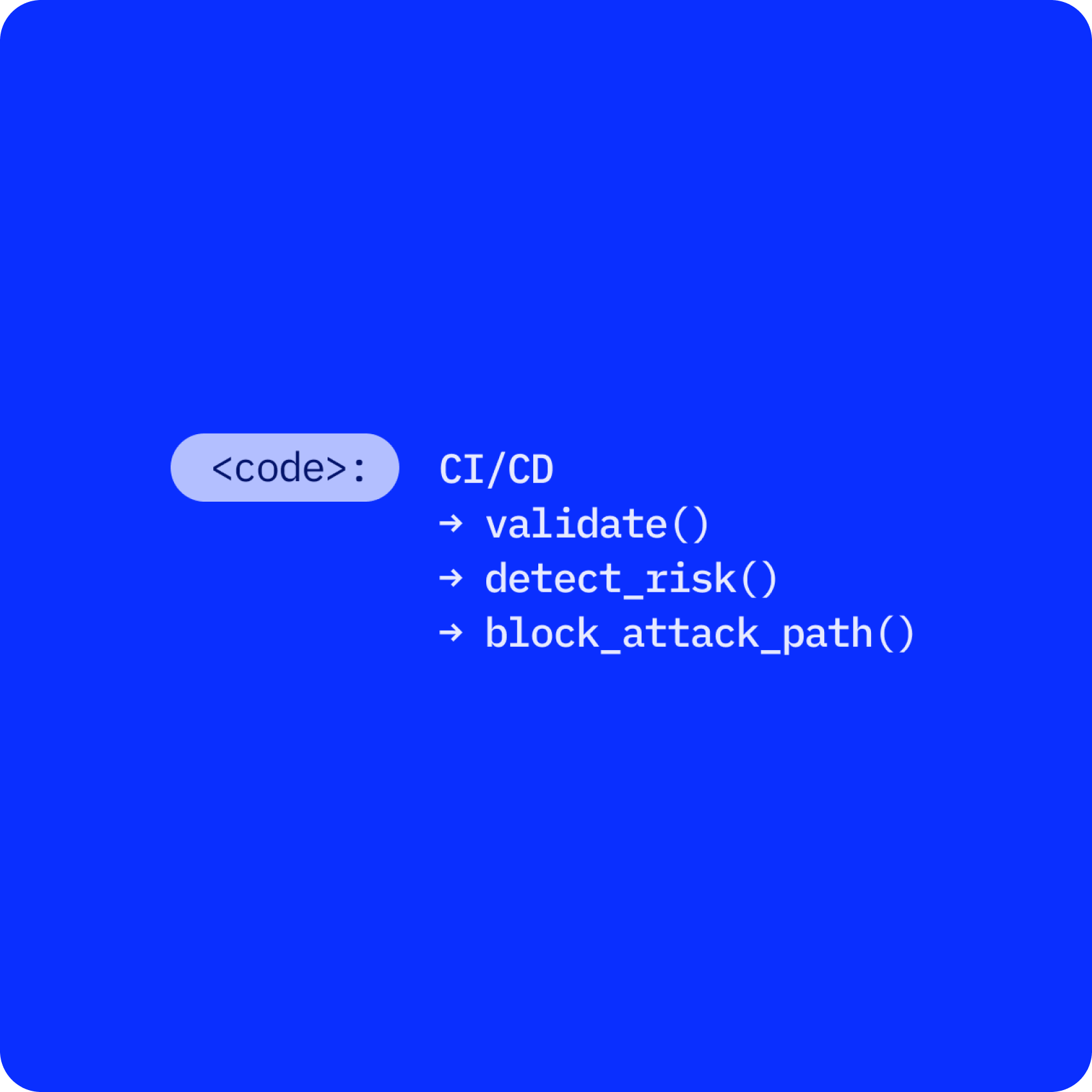
For organizations, the cloud brings speed and scale; for adversaries, it
opens new attack paths. Without CSPM, security teams struggle to:














Yes. You don’t need separate licenses—ASM and Threat Intelligence are embedded.
AWS, Microsoft Azure, Google Cloud Platform (GCP), and Alibaba Cloud.
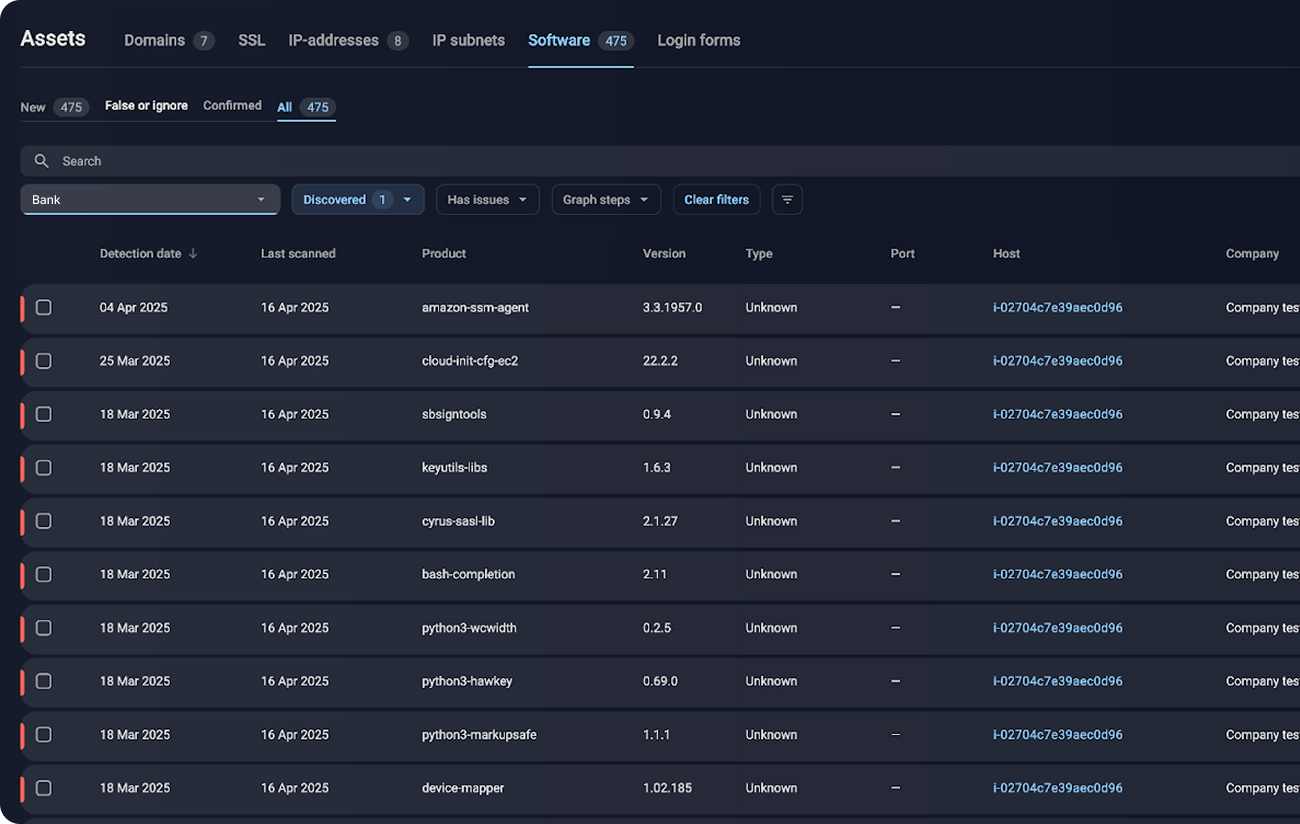
Yes. The solution connects via API and requires no agents or invasive deployment.
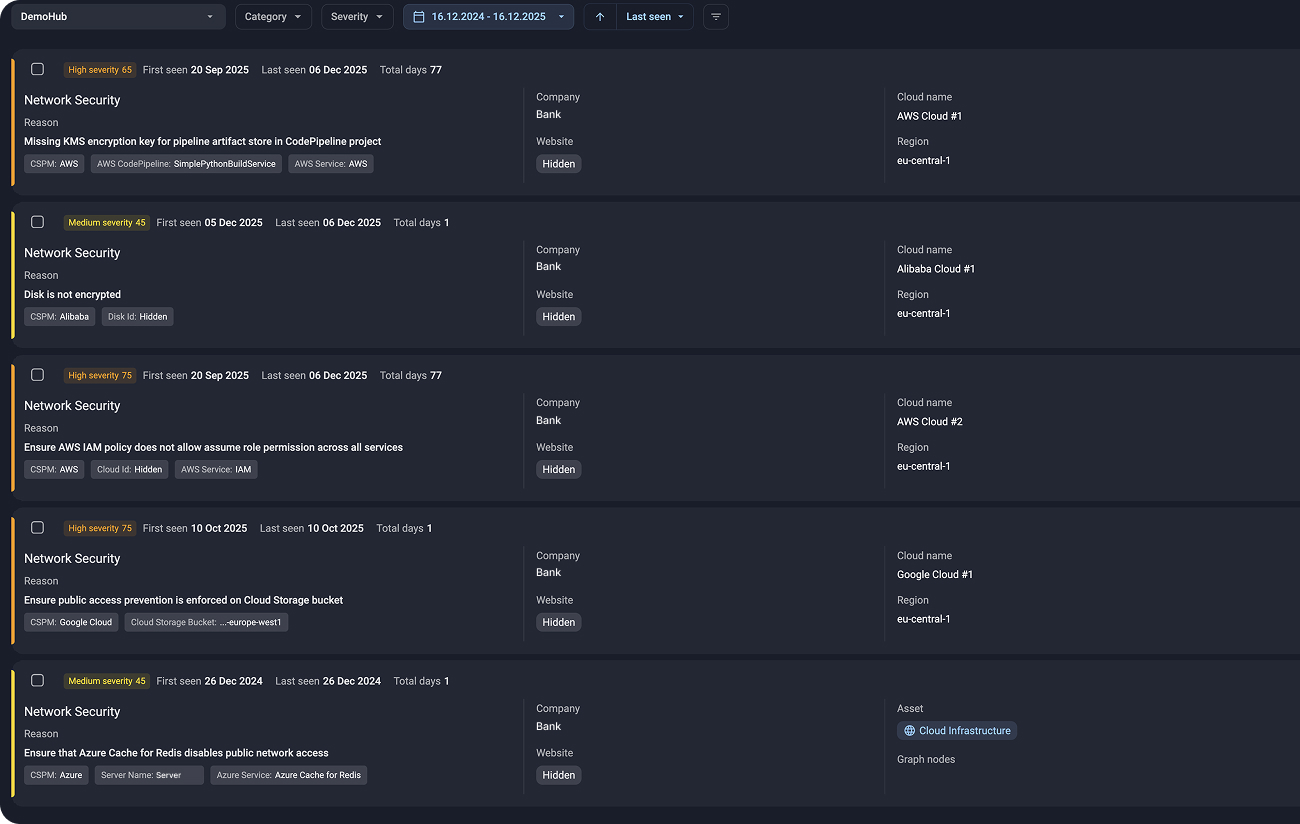
Yes. Group-IB CSPM integrates with our Attack Surface Management solution to show you which misconfigurations are publicly exposed.
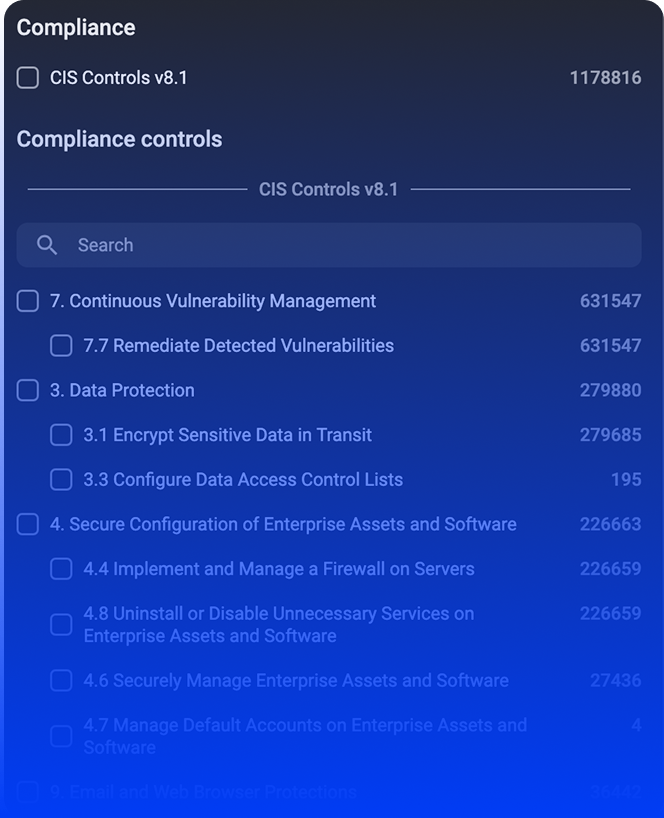
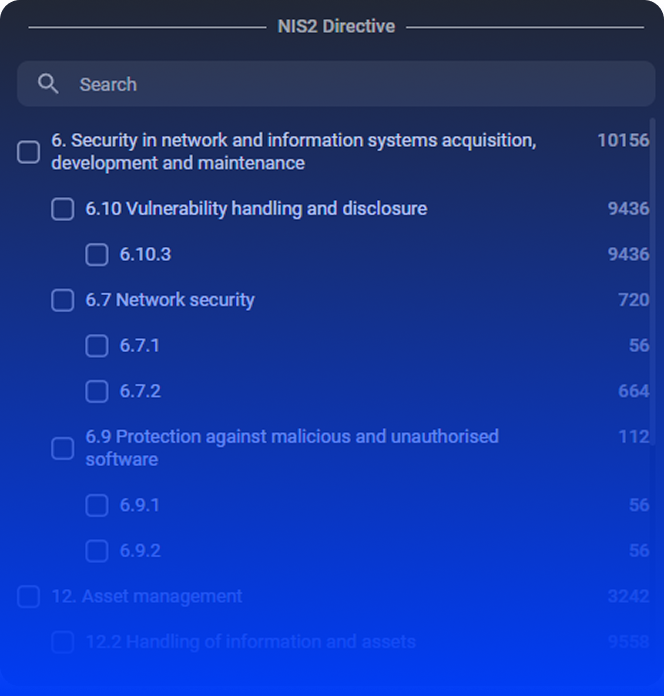
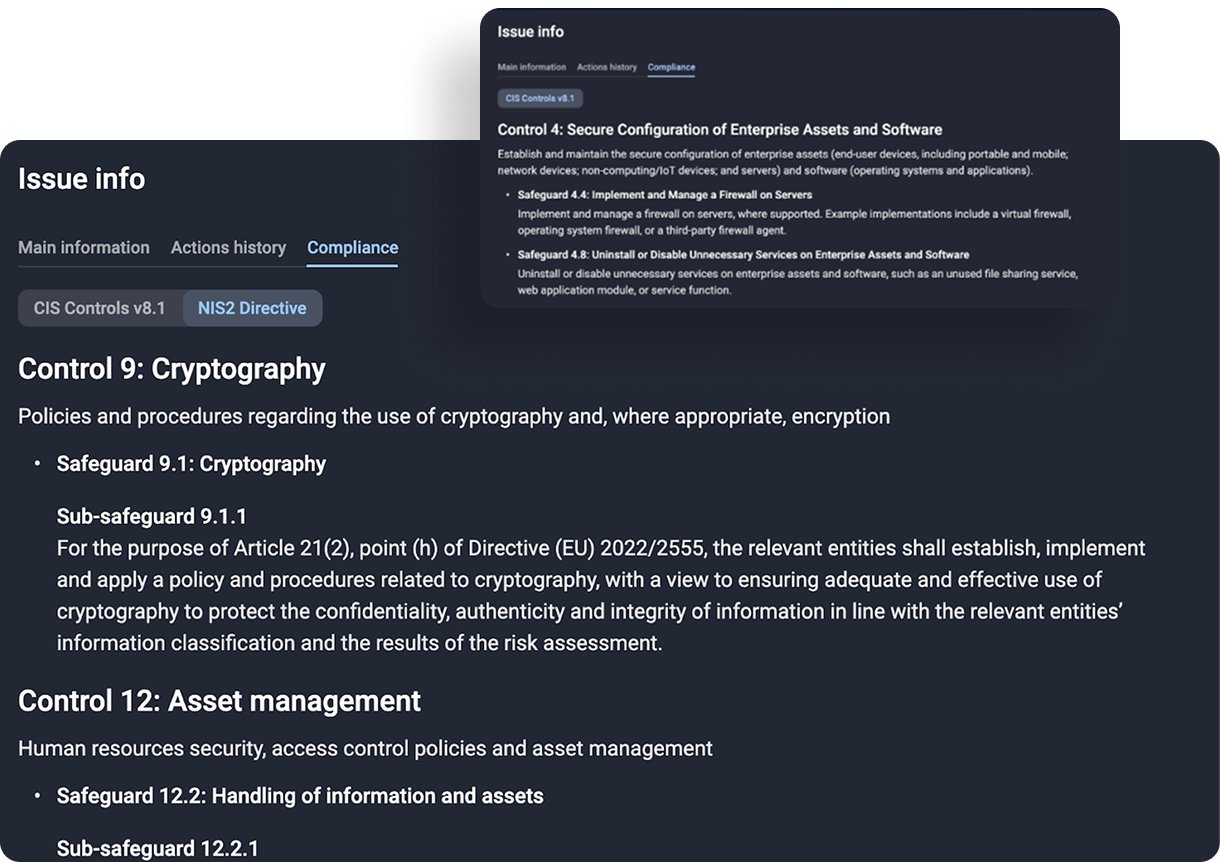
Yes. CIS and NIST benchmarks are supported out of the box.
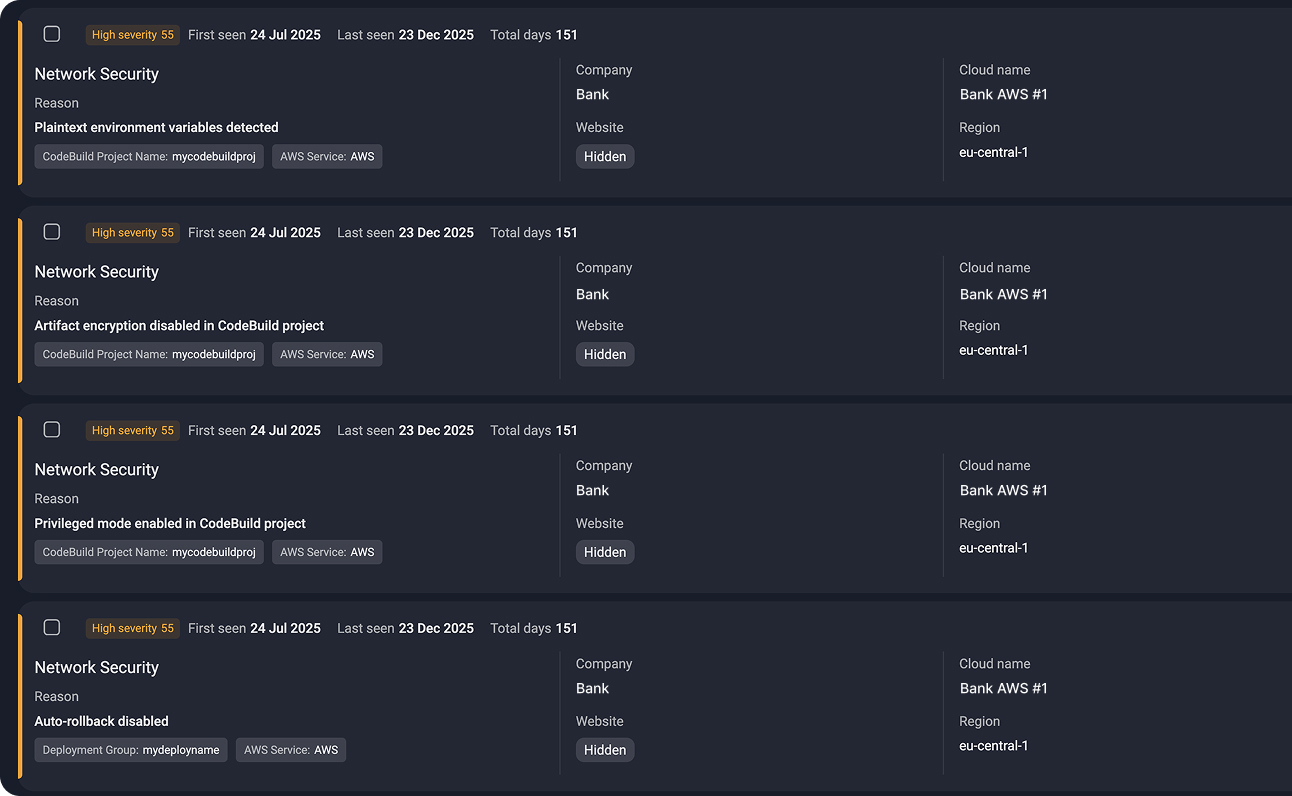
Group-IB combines posture findings with external visibility and threat intelligence, helping you focus on misconfigurations that are exploitable — not just technically incorrect.