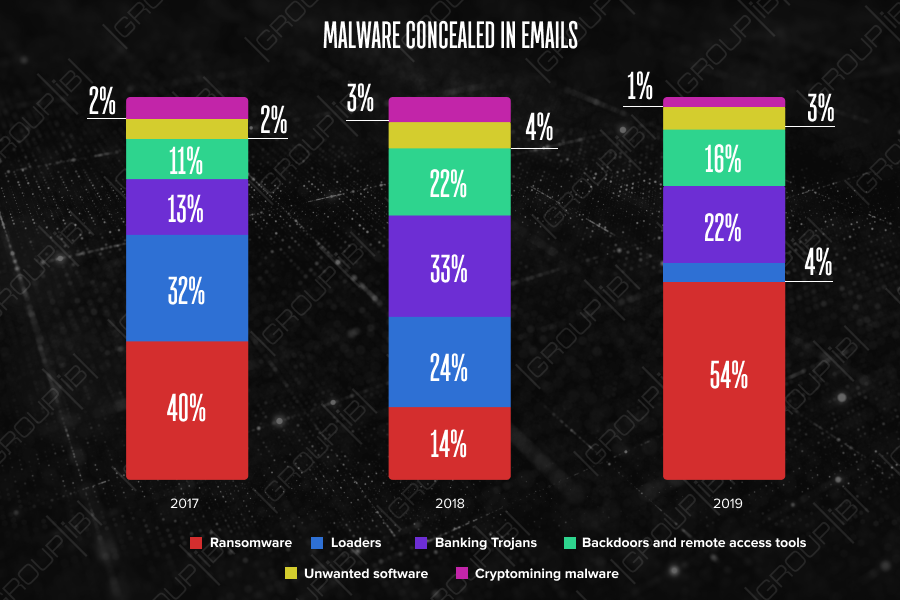
Group-IB, a Singapore-based cybersecurity company: ransomware accounted for over a half of all malicious mailings in H1 2019, detected and analyzed by Group-IB’s Computer Emergency Response Team (CERT-GIB), with Troldesh being the most popular tool among cybercriminals. To bypass antivirus systems, hackers send out malicious emails in non-working hours with delayed activation. More than 80% of all malicious files were disguised as .zip and .rar archive files.
Dangerous email
CERT-GIB’s report is based on data collected and analyzed by the Managed Extended Detection and Response (MXDR) as part of operations to prevent and detect threats distributed online in H1 2019 in more than 60 countries. The report’s findings reveal that email remains the main method of delivering ransomware, banking Trojans, and backdoors. The second half of 2018 saw a drop in the number of malicious programs downloaded via browsers reaching its minimum at less than 5%, while in the first half of 2019 only every 19th download was initiated via means other than email.
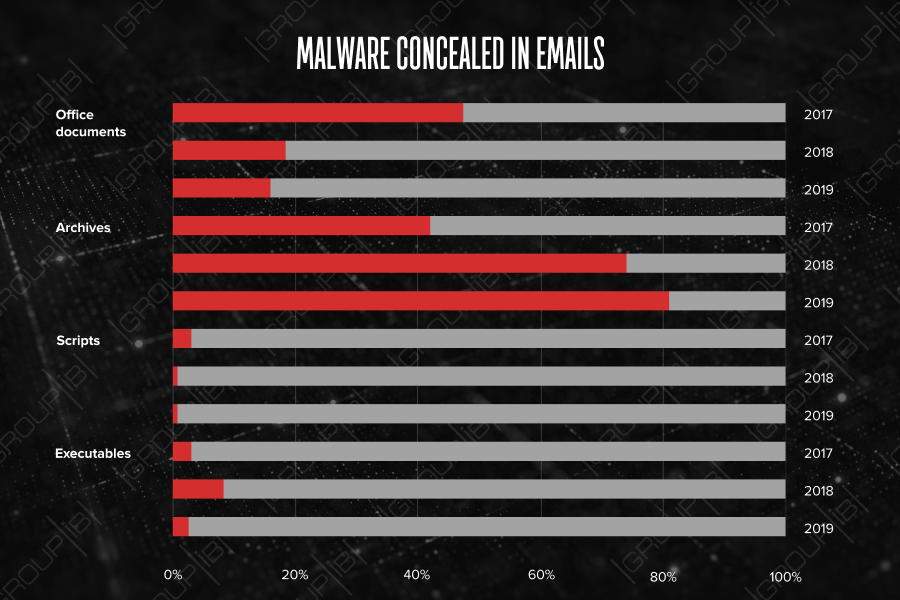
The first half of 2019 saw a 10-fold increase in the number of password-protected objects, such as documents and archive files, being used to deliver malware. In 2017, password-protected archives accounted for only 0.08% of all malicious objects. In 2018, their number grew to 3.6%, while in H1 2019 saw an unusual rise of up to 27.8%.
Another trend was disguising malware in emails. To bypass corporate security systems, cybercriminals are increasingly often archiving their malicious attachments. Over the first six months in 2019, more than 80% of all malicious objects, detected by CERT-GIB, were delivered in archive files, mainly in .zip (32%) and .rar (25%) formats. Threat actors included the passwords for accessing the contents in the subject of the email, the name of the archive, or in their subsequent correspondence with the victim.
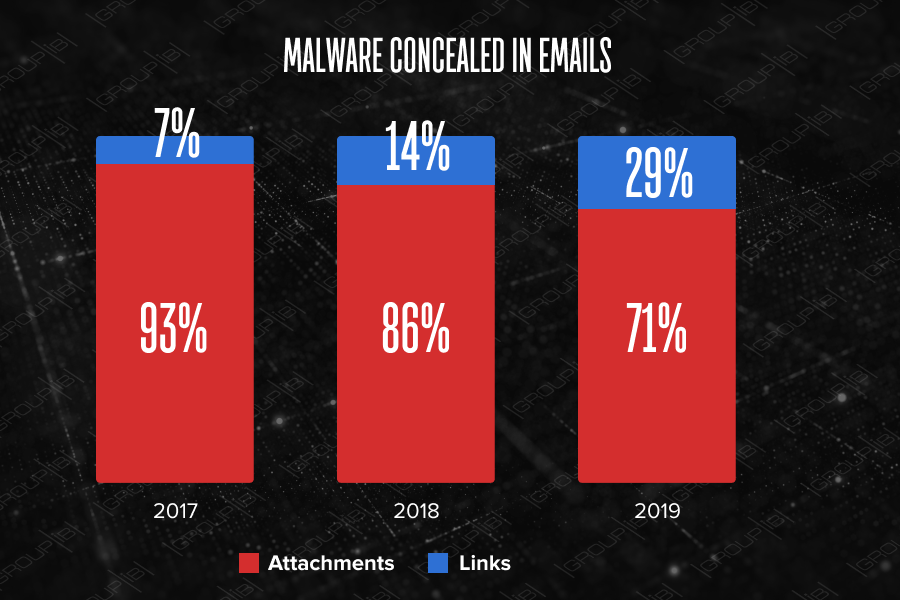
Instead of traditional attachments, cybercriminals more often put links in emails, which when clicked download malicious attachments. Links account for 29%, while attachments—for 71%. Half as much malware was distributed through links in 2018.
Another technique used by cybercriminals to bypass antivirus systems is a targeted attack, in which malicious email are delivered outside regular working hours. When scanned by antivirus software, malicious links in such emails are inactive and labelled as legitimate, thus ending up in victims’ email boxes. Cybercriminals activate these malicious links during business hours, thereby increasing the likelihood of infecting computers.
Modern cybercriminals have all necessary tools to make sure that the malicious objects they send out are not detected by popular antivirus software. It is worth noting that schemes with password-protected or attached archives, and delayed activation etc. are detected promptly and effectively only if companies use advanced early threat detection and prevention systems. Thanks to behavioral analysis, such systems make it possible to detect previously unknown malware samples.

Head of Group-IB’s Computer Emergency Response Team (CERT-GIB)
Financial departments at high risk
Cybercriminals use social engineering techniques to convince users to click on malicious links or extract archives. In most cases, attackers use accounting and financial topics to attract email recipients’ attention. This year the most popular names for malicious files used in malicious mailings worldwide have been «Payment», «Scan», «Invoice», «Voice Message», «New Order» etc. As can be seen from these filenames, accounting and financial vocabulary prevails. If analyzing a typical mass mailing, it can be seen that the use of accounting and financial topics increases the likelihood of infecting users from financial department, which obviously has greater value for cybercriminals.
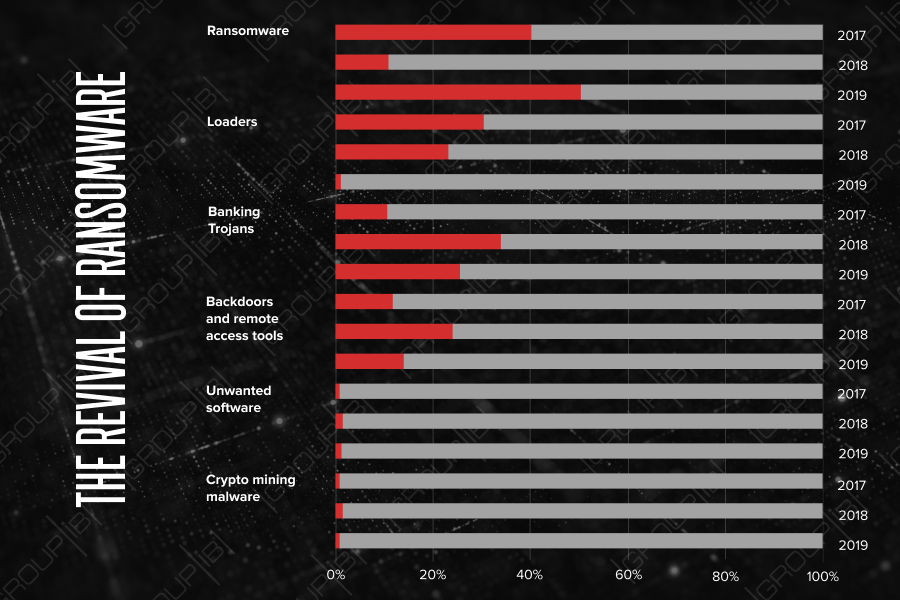
The revival of ransomware
In 2018, the major vector for financial losses was via bank Trojans and backdoors, whereas the first half of 2019 showed a rapid increase in ransomware usage. Ransomware activity has spiked up to first place amongst threats and grown by 54%, according to CERT-GIB data. Currently, three of the most widespread tools used in attacks tracked by Group-IB’s Computer Emergency Response Team have been Troldesh (53%), RTM (17%) and Pony Formgrabber (6%).
The most widely spread is Troldesh, a ransomware, which Group-IB has been tracking for several years. The main functionality of the malware is to encrypt data on the computer and make ransom demands. Troldesh is actively sold and rented out, but it is constantly in demand as it is frequently updated with new functionality. The most recent Troldesh campaigns show that it now does not just encrypt files, but also can mine cryptocurrency and generate phony traffic on websites to increase revenue from ad-fraud.
In second place is the banking Trojan RTM, which was developed by the similarly named hacker group. RTM first appeared in 2016 and attracted attention as its C&C was a LiveJournal (Russian social networking service) page. Analysis revealed that that RTM is aimed at stealing funds through the remote banking services of Russian financial institutions. As the RTM group has used a range of methods for distribution, tracking them has fluctuated over time. From mid-2018, it was identified as being spread from a network of fake accounting sites, later during the reviewed period, the group was identified in other attacks on companies in the financial sector and their business customers. Since the start of 2019, the number of malicious mailings involving the use of RTM malware has continued at high frequency.
The third malware type is Pony Formgrabber designed to steal victim passwords from over 100 applications, including browsers, E-mail clients, messengers, FTP and VPN clients. Some versions of it are capable of hidden download and installation of other malware onto infected computers.