Group-IB, a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime, announced today that it has contributed to “Operation Synergia II”, an INTERPOL-led global operation aimed at combating the surge of phishing, ransomware and information stealer attacks. 95 countries participated in the operation that took down 22,000 malicious servers. In total, 41 individuals were arrested by a multinational coalition of law enforcement agencies, with 65 other suspects still under investigation. As part of the operation, Group-IB’s analysts identified over 2,500 IP addresses linked to 5,000 phishing websites, and more than 1,300 IP addresses tied to various malware activities spanning 84 countries.
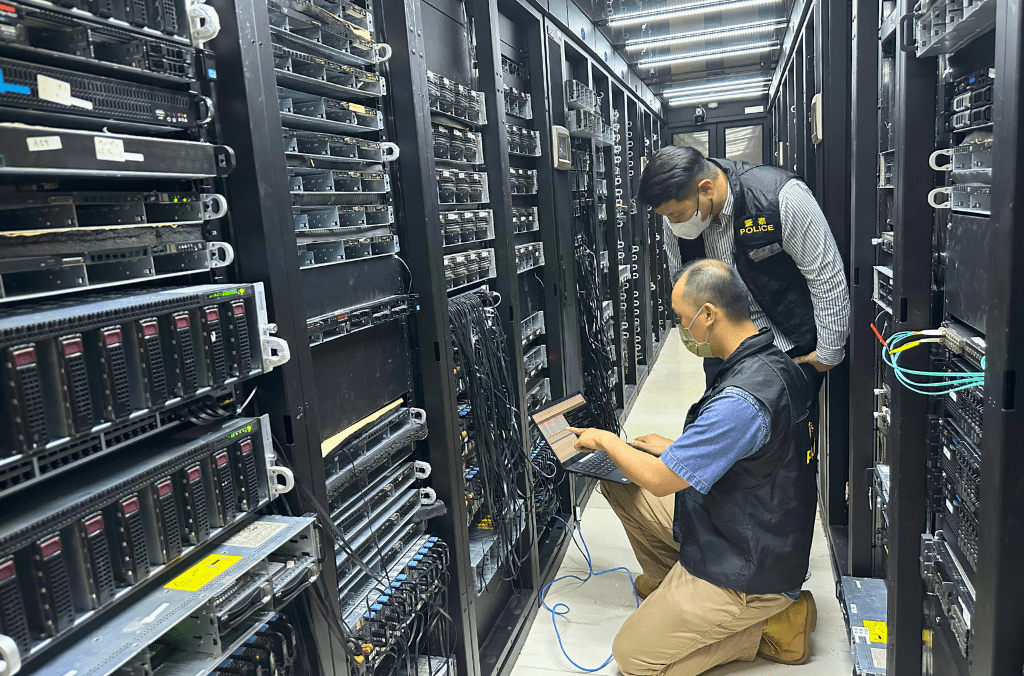
Members of the Hong Kong Police Force raided the premises of the suspects and took more than 1,037 servers linked to malicious services offline. Image credit: INTERPOL and the Hong Kong Police Force
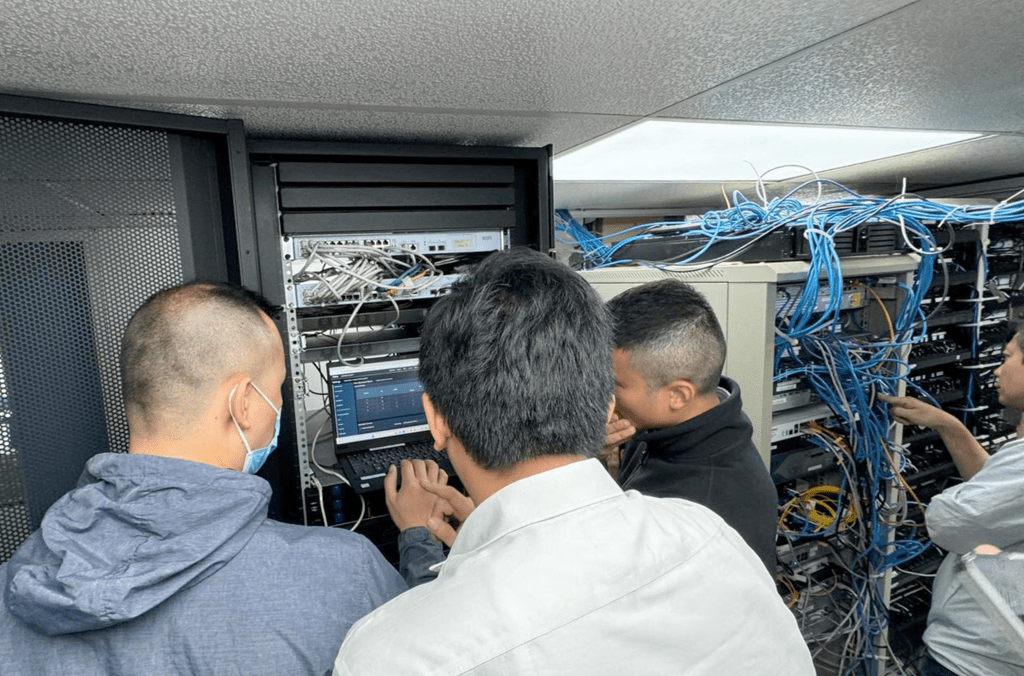
Conducted from 1 April until 31 August 2024, Operation Synergia II was a joint effort from INTERPOL, private sector partners, and law enforcement agencies from 95 INTERPOL member countries, aimed at disrupting phishing, ransomware, and information stealer cybercriminals and syndicates. Leveraging Group-IB’s expertise in tracking illegal cyber activities to identify thousands of malicious servers, INTERPOL shared this information with participating law enforcement agencies, who conducted preliminary investigations leading to a series of coordinated actions, including house searches, disruption of malicious cyber activities, and lawful seizures of servers and electronic devices.

Local law enforcement and INTERPOL coordination meeting in Africa for Operation Synergia II. Image credit: INTERPOL
Of the approximately 30,000 suspicious IP addresses identified under the operation, more than 22,000 were taken down and 59 servers were seized. Additionally, 43 electronic devices, including laptops, mobile phones and hard disks were seized.
The following countries participated in the operation:
- Hong Kong (China) – Police supported the operation by taking offline more than 1,037 servers linked to malicious services.
- Mongolia – Investigations included 21 house searches, the seizure of a server and the identification of 93 individuals with links to illegal cyber activities.
- Macau (China) – Police took 291 servers offline.
- Madagascar – Authorities identified 11 individuals with links to malicious servers and seized 11 electronic devices for further investigation.
- Estonia – Police seized more than 80GB of server data and authorities are now working with INTERPOL to conduct further analysis of data linked to phishing and banking malware.
“The global nature of cybercrime requires a global response which is evident by the support member countries provided to Operation Synergia II. Together, we’ve not only dismantled malicious infrastructure, but also prevented hundreds of thousands of potential victims from falling prey to cybercrime. INTERPOL is proud to bring together a diverse team of member countries to fight this ever-evolving threat and make our world a safer place.”

INTERPOL’s Director of the Cybercrime Directorate
“We are proud to have contributed to Operation Synergia II by supporting INTERPOL and law enforcement agencies from member countries in the disruption of malicious infrastructure and preventing cybercrimes. As an INTERPOL Gateway Partner, we firmly believe that closer collaboration between the public and private sector will not only tackle cybercrime in all its guises more effectively, but also safeguard the information and data of our clients and that of the society globally.”

CEO of Group-IB
Operation Synergia II is the second edition of Operation Synergia that ran from September to November 2023, in which Group-IB’s Threat Intelligence and High-Tech Crime Investigation teams identified more than 500 IP addresses hosting phishing sites and more than 1,900 IP addresses used by ransomware, Trojan and other malware operators. The identified malicious resources were found to be hosted in more than 50 countries, including Australia, Canada, Hong Kong, Singapore, and others. The malicious infrastructure used by the threat actors was distributed across 200+ web hosting providers around the world.