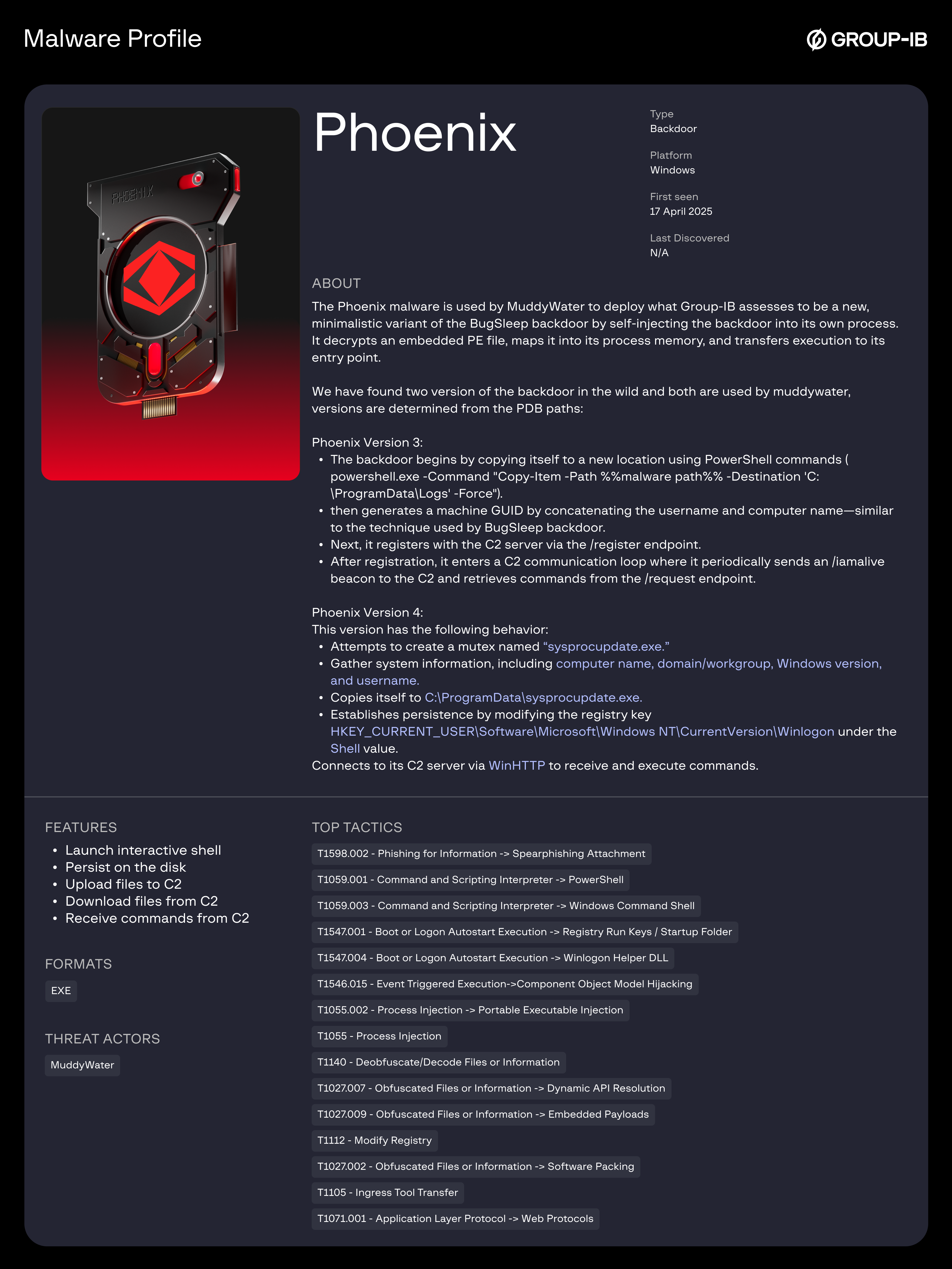
Introduction
Group-IB Threat Intelligence uncovered a sophisticated phishing campaign orchestrated by the Advanced Persistent Threat (APT) MuddyWater, targeting international organizations worldwide to gather foreign intelligence.
MuddyWater accessed the compromised mailbox through NordVPN(a legitimate service abused by the threat actor), and used it to send phishing emails that appeared to be authentic correspondence. By exploiting the trust and authority associated with such communications, the campaign significantly increased its chances of deceiving recipients into opening the malicious attachments.
The phishing emails contain Microsoft Word documents that prompted recipients (victims) to enable macros in order to view the content. As soon as macros were activated, the Microsoft Word documents executed malicious Visual Basic for Application (VBA) code, ultimately leading to the deployment of version 4 of the Phoenix backdoor on the victim’s system.
Group-IB attributes this campaign to the Iran-linked threat actor MuddyWater with high confidence, based on the tools, techniques, and procedures (TTPs) observed. The incident underscores how state-backed Threat Actors continue to exploit trusted channels of communication to evade defenses and infiltrate high-value targets.
Key Takeaways
- Muddywater is targeting international organizations in an espionage campaign.
- The use of version 4 of the Phoenix backdoor malware in this campaign, featuring a different persistence technique.
- A new Remote Monitoring and Management (RMM) tool and custom browser credential stealer were potentially used in this campaign.
Attribution Assessment
Group-IB attributes this campaign to MuddyWater with high confidence based on the following indicators observed during the course of our investigation and analysis:
- The dropped malware families, Fakeupdate injector and Phoenix Backdoor, are custom malware previously observed exclusively in Muddywater operations.
- The malicious macro embedded in the document shares similar logic and matches code with macros used in past MuddyWater campaigns (hash: 40dead1e1d83107698ff96bce9ea52236803b15b63fb0002e0b55af71a9b5e05).
- The command-and-control (C2) server hosts a custom browser credential stealer that employs the same string decoding techniques observed in other MuddyWater-linked malware.
- The same C2 infrastructure also contains PDQ RMM tools, which have been previously used by MuddyWater for remote access and persistence.
- The targeting patterns align with MuddyWater’s historical victimology, specifically its focus on the Middle East region.
Group-IB Threat Intelligence Portal: MuddyWater
Group-IB customers can access our Threat Intelligence portal for more information about MuddyWater and Phoenix malware profiles.
From Malicious Email to System Compromise
MuddyWater launched the operation by sending malicious email using a compromised account. Based on the email header, MuddyWater accessed the compromised account through NordVPN, and used it to send phishing emails to multiple targets worldwide.
The phishing emails contained a malicious Microsoft Word attachment. When opened, the document displayed blurred content and instructed the recipient to “enable content” to view the text. Once macros were enabled, the embedded VBA code executed functioning as a dropper that decoded and wrote a loader to disk before executing it.
The loader was identified as FakeUpdate, which is an injector-style loader that decrypts an embedded second-stage payload using Advanced Encryption Standard (AES) and injects it into its own process. The decrypted second-stage payload was identified as Phoenix backdoor version 4. Written to disk under the name sysProcUpdate, Phoenix v4 registered the infected host with the attacker’s command-and-control (C2) infrastructure, initiating continuous beaconing, and polling for commands, and in doing so enabling remote control, data collection, and further post-exploitation activities.
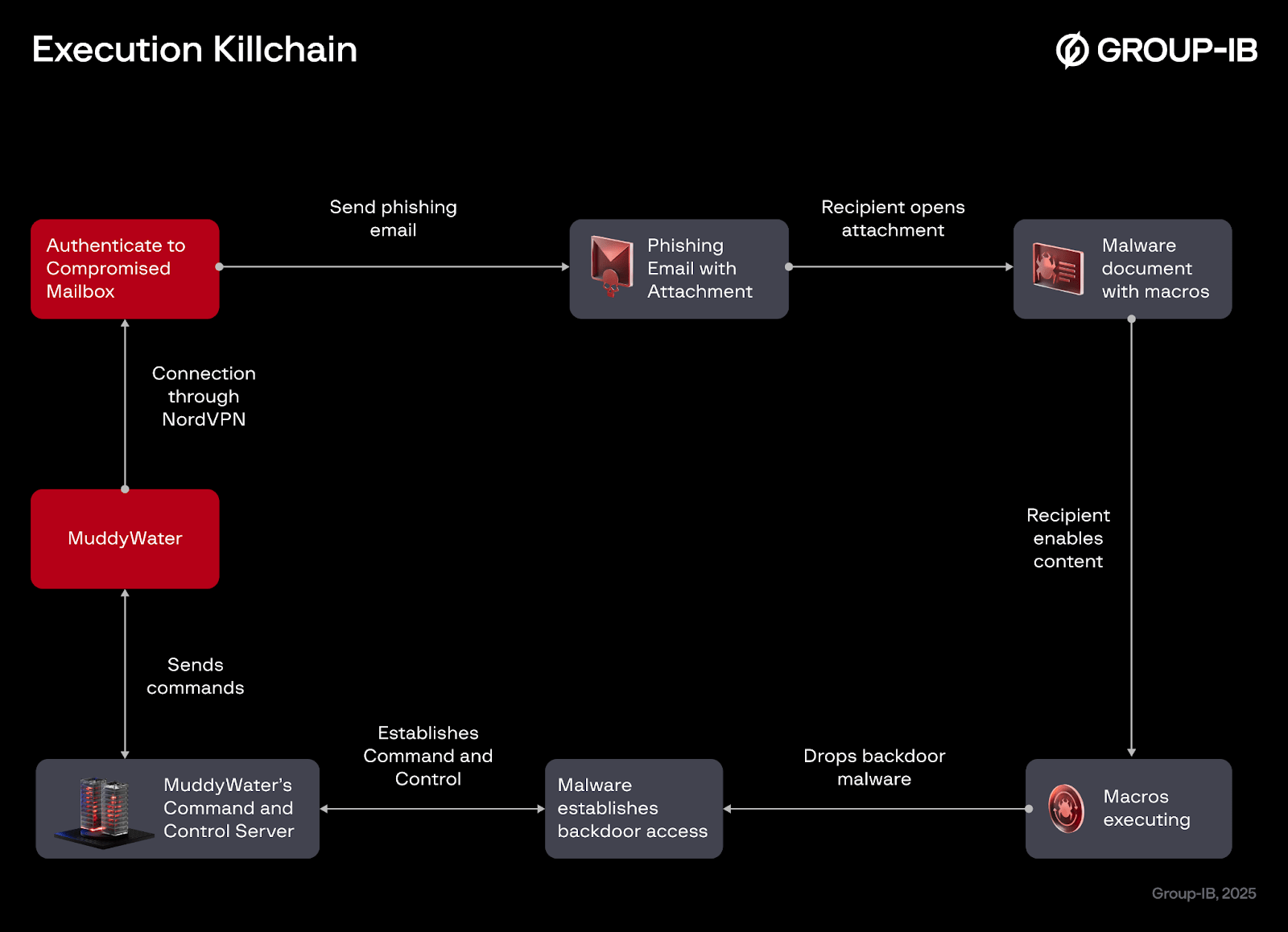
Figure 1. An overview of the execution killchain.
Targeting Analysis and Campaign Insights
An examination of the recipients from the phishing emails observed by Group-IB reveals several key insights :
Notable targeting patterns
- Inclusion of Personal Email Accounts: The mix of official (.gov) and personal emails (Yahoo, Gmail, and Hotmail) indicates that MuddyWater possesses detailed knowledge of its targets.
- Targeting of International Organizations: The campaign’s focus extended to influential global organizations engaged in international cooperation and humanitarian missions, highlighting the actor’s broader geopolitical motivations.
Target Types Classification
The diagram below provides a breakdown of the different target categories identified in this espionage campaign, based on Group-IB’s analysis of the phishing email recipients.
Several targeted recipients are part of well-known global institutions that focus on international cooperation and humanitarian work. This supports the group’s larger geopolitical goals and the purposeful nature of its targeting.
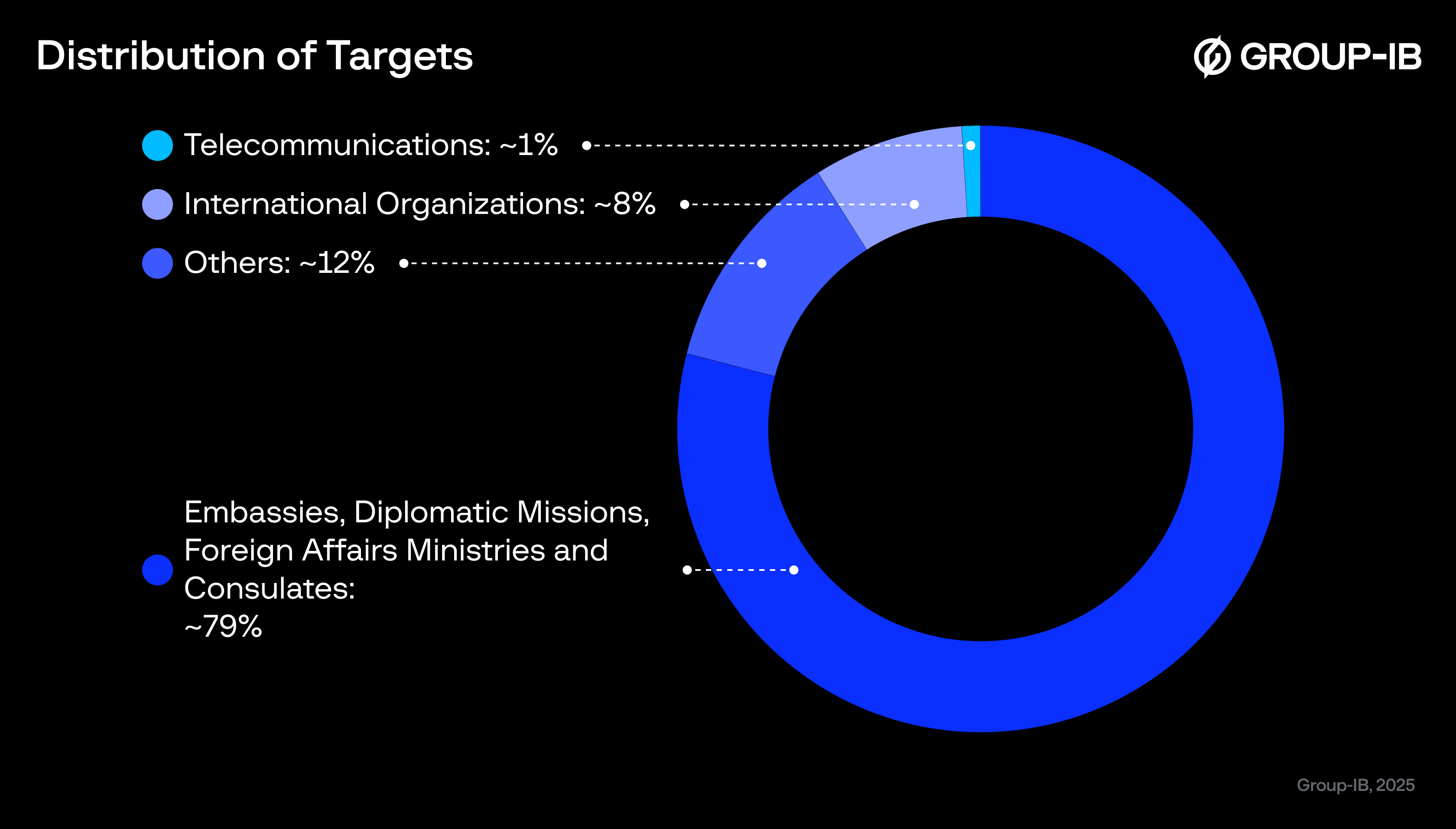
Figure 2. A diagram highlighting the types of targets observed during this MuddyWater campaign.
Samples Connections and Campaign Overlaps
During extended analysis of artifacts associated with this campaign, Group-IB Threat Intelligence identified additional malicious documents that share technical and infrastructure overlaps with the current operation. These findings suggest continued activity by MuddyWater, potentially involving related or concurrent campaigns.
We identified another malicious document that impersonates a government-organization seminar addressing ongoing geopolitical tensions in the region and mirrors themes seen elsewhere in this campaign. The file contains identical macro code, delivers the same payload, and communicates with the same command-and-control (C2) domain as other samples (screenai[.]online). Given these overlaps — including matching last-editor metadata and edit timestamps — we assess this document as part of the same espionage campaign. Although the exact distribution method remains unconfirmed, phishing via a compromised email account is the most likely vector.
Additionally, we identified another document which targeted the energy sector in the Middle East and North Africa. This file also deployed the FakeUpdate malware injector to deliver Phoenix backdoor version 4, communicating with the same C2 infrastructure (screenai[.]online) used in this Espionage Campaign. The attack was conducted in the same time frame as the campaign mentioned in this blog, However, due to differing target profiles, with this sample focusing on energy-sector entities rather than diplomatic or international organizations, we assess it to be a separate but concurrent MuddyWater operation reusing the same C2 domain.
Malware Analysis
Malicious Mail attachment
When macros are enabled and executed, the malicious document macros retrieves an embedded dropped file and writes C:\Users\Public\Documents\ManagerProc.log ,then executes that file.
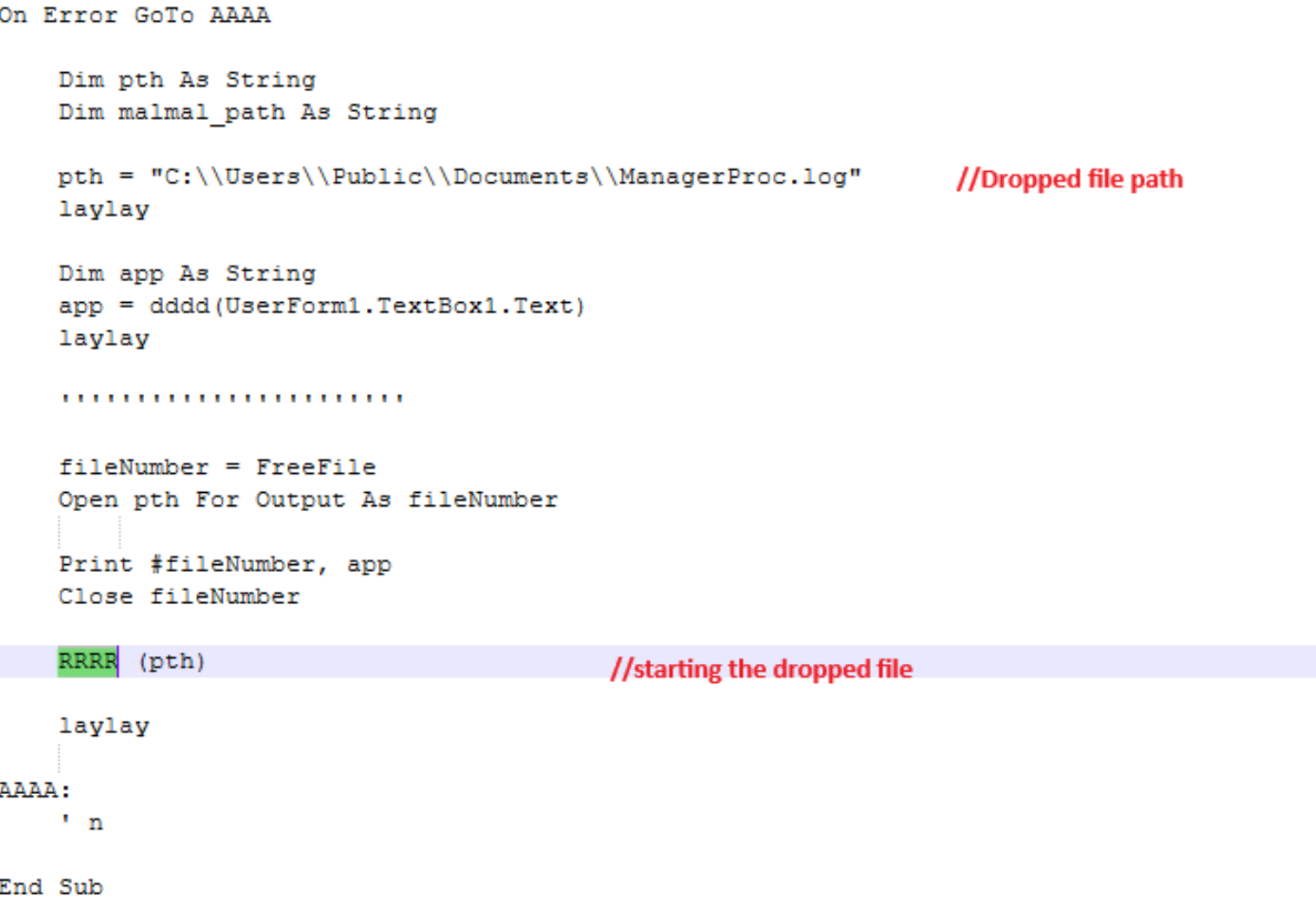
Figure 3. A screenshot of the executed macro, as soon as the recipient enables it.
Dropped Backdoor
The dropped file acts as an injector tracked by Group-IB as FakeUpdate. It decrypts an embedded second-stage payload and injects it into its own process. The injected component is a backdoor which is version 4 of the Phoenix backdoor used by MuddyWater, which performs the following actions:
- Attempts to create a mutex named sysprocupdate.exe
- Gather system information, including computer name, domain/workgroup, Windows version, and username.
- Copies itself to C:\ProgramData\sysprocupdate.exe
- Achieves persistence by modifying the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon and altering the Shell value.
- Connects to its C2 server via WinHTTP to receive and execute commands.
Command Mapping
| Command | Description |
| 65 | Sleep |
| 68 | Upload file |
| 85 | Download file |
| 67 | Start Shell |
| 83 | Update sleep interval time |
COM-Based Persistence and Overlapping Artifact
This version 4 of the Phoenix backdoor used in this attack has an embedded Portable Executable (PE) file that was not dropped or executed during normal operation. Upon extracting and reverse-engineering this file, Group-IB’s Threat Intelligence determined that it is Component Object Model (COM) Dynamic Link Library (DLL) designed to establish persistence by launching the file C:\\Users\\Public\\Downloads\\Mononoke.exe.
A similar DLL (coreglobconfig.dll) was previously observed in the CannonRat malware, which has also been linked to MuddyWater.
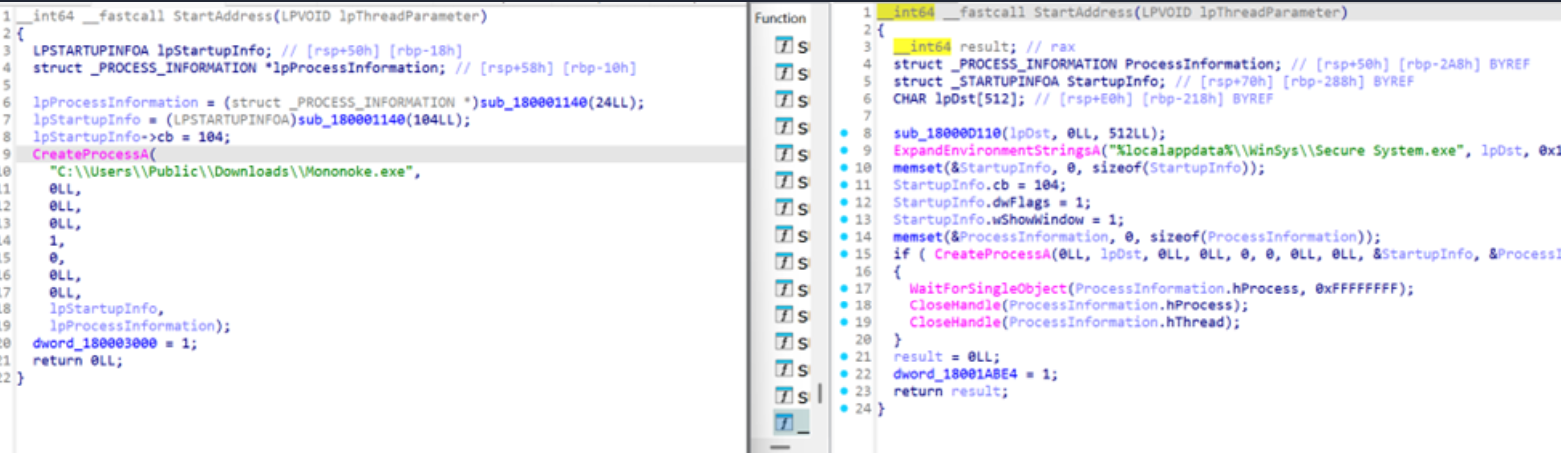
Figure 4. Comparison between coreglobconfig used by CannonRat and embedded DLL inside this backdoor.
During the hunt for the file path C:\Users\Public\Downloads\Mononoke.exe, Group-IB Threat Intelligence recovered another two samples whose Program Database (PDB) path points to
C:\Users\win10\Desktop\phoenixV4\phoenixV3\phoenixV2\x64\Debug\phoenix.pdb (hashes: 6de859a27ccc784689e8748cef536e32780e498a, bed6506f8f5281888f89781cf6fbc750545292fc). Both samples were identified as Phoenix backdoor version 4, and the artifacts indicate that this version of the backdoor includes an additional persistence mechanism via a Component Object Model (COM) object, and not just the Winlogon registry modification observed in this campaign.
The Mononoke.exe backdoor and its associated DLL were delivered through a malicious document employing the same lure and theme seen in a recent MuddyWater operation documented by Group-IB Threat Intelligence. This overlap suggests that the developer likely neglected to remove this DLL artifact from the malware used in this campaign.
Figure 5. The document dropped the Mononoke.exe, which uses the same theme used in a recent attack.
Infrastructure Analysis
The value of x-originating-ip in the email header is a NordVPN exit node located in France. The x-originating-ip header reveals the original IP address of the client or device that first submitted the email to the mail server. According to IPinfo this IP is located in France:
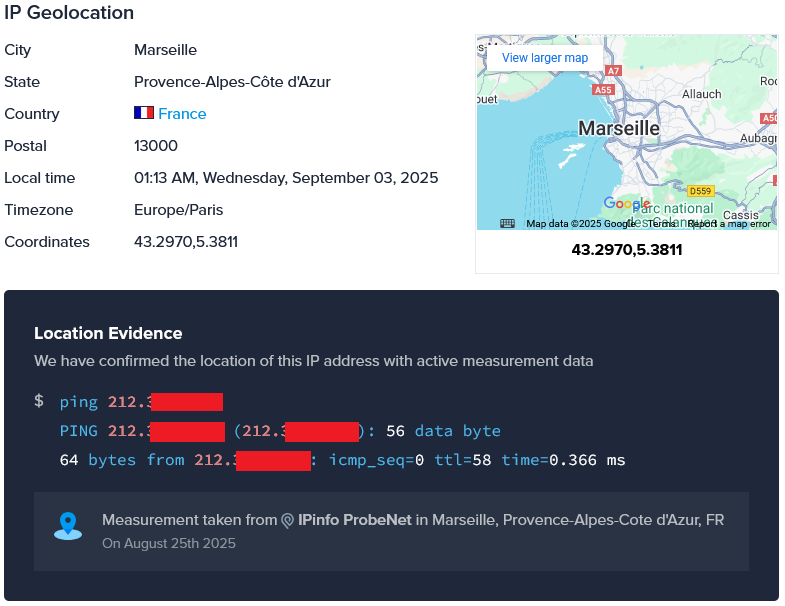
Figure 6. NordVPN exit node IP information.
Based on this analysis, we can record the fact that MuddyWater uses NordVPN and possibly other similar VPN services in their operations.
The malware samples contained a hardcoded C2 domain screenai[.]online which remained active only for several days after the launch of the phishing campaign. Although available information on this domain is limited, Group-IB Threat Intelligence was able to establish several key details.
The domain screenai[.]online was registered via NameCheap on 17 August 2025 at 16:41:01 hours (UTC) (2025-08-17T16:41:01.00Z), with an expiration date of 17 August 2026 16:41:01 hours (2026-08-17T16:41:01.00Z). The DNS servers were set to CloudFlare as shown in the WHOIS records.
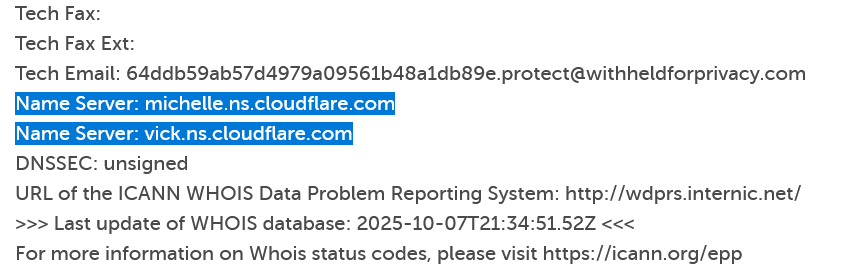
Figure 7. C2 name servers in WHOIS info.
This can be confirmed by looking at the resolved IP addresses that belong to CloudFlare as shown in the image below:
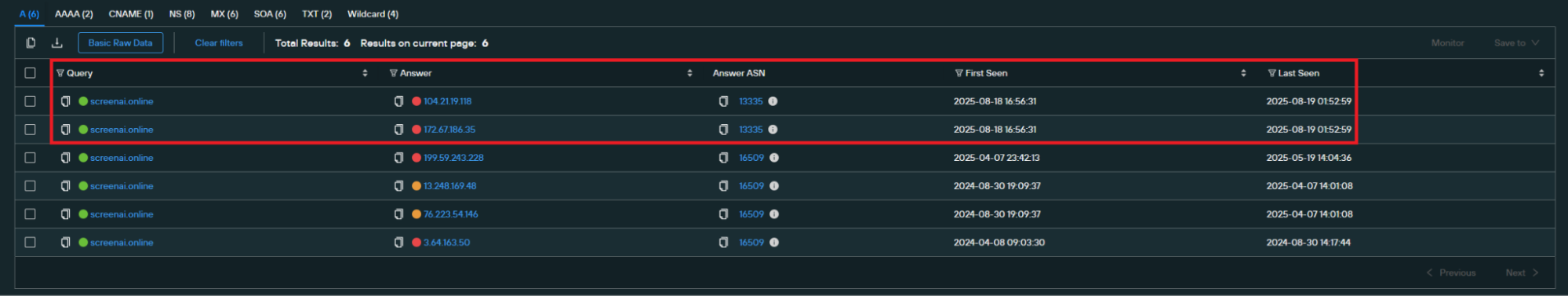
Figure 8. C2 passive DNS history.
At this stage, further analysis would not be possible unless we obtain the real IP address. However, we were able to uncover it through the Secure Sockets Layer (SSL) certificate, which showed that the real IP of the server was 159[.]198[.]36[.]115 which is registered under NameCheap’s Autonomous System Number (ASN), this aligns with the domain registration information.
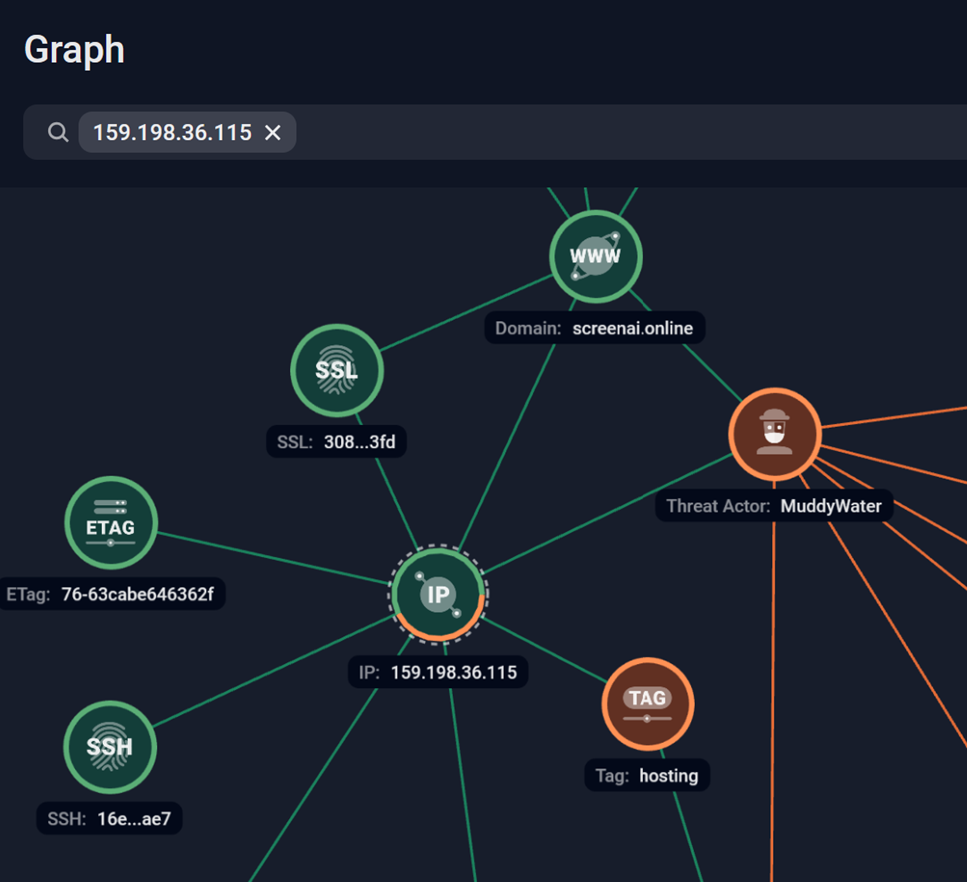
Figure 9. Analysis of the MuddyWater’s C2 domain using Group-IB’s Graph solution.
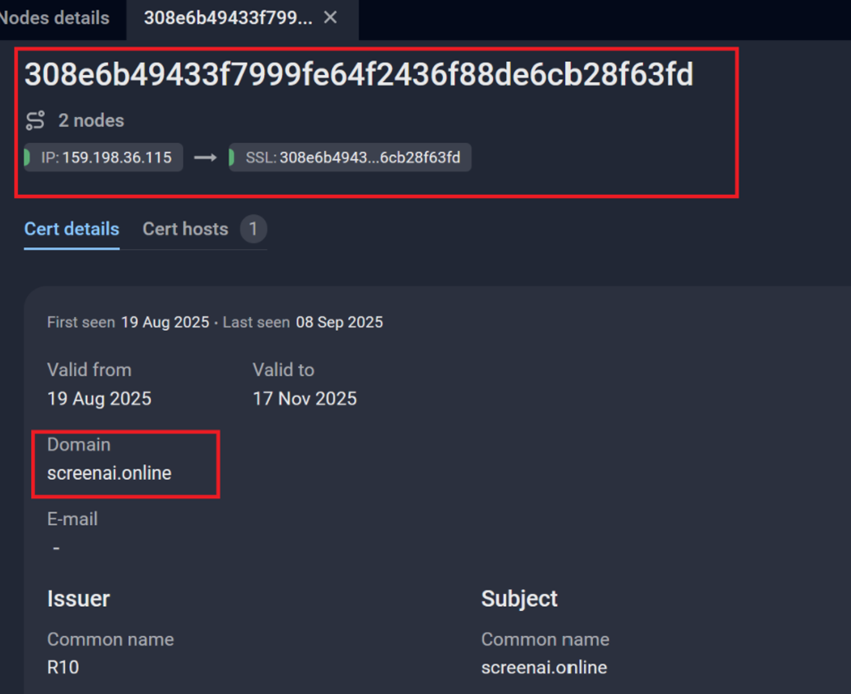
Figure 10. A screenshot of the SSL certificate used by C2 via Group-IB’s Threat Intelligence platform.
Analyzing the banners associated with the real IP address reveals several findings:
- The threat actor deployed the server and server-side C2 component on 19 August 2025, and took it down on 24 August 2025, indicating an active attack window of about five days.
- The C2 component initially ran on Uvicorn, until MuddyWater replaced it with Apache on 24 August 2025 which had been responding with a “503 service unavailable” message.
- The web page displayed the title “ScreenAI | Your On-Screen Content Genius“
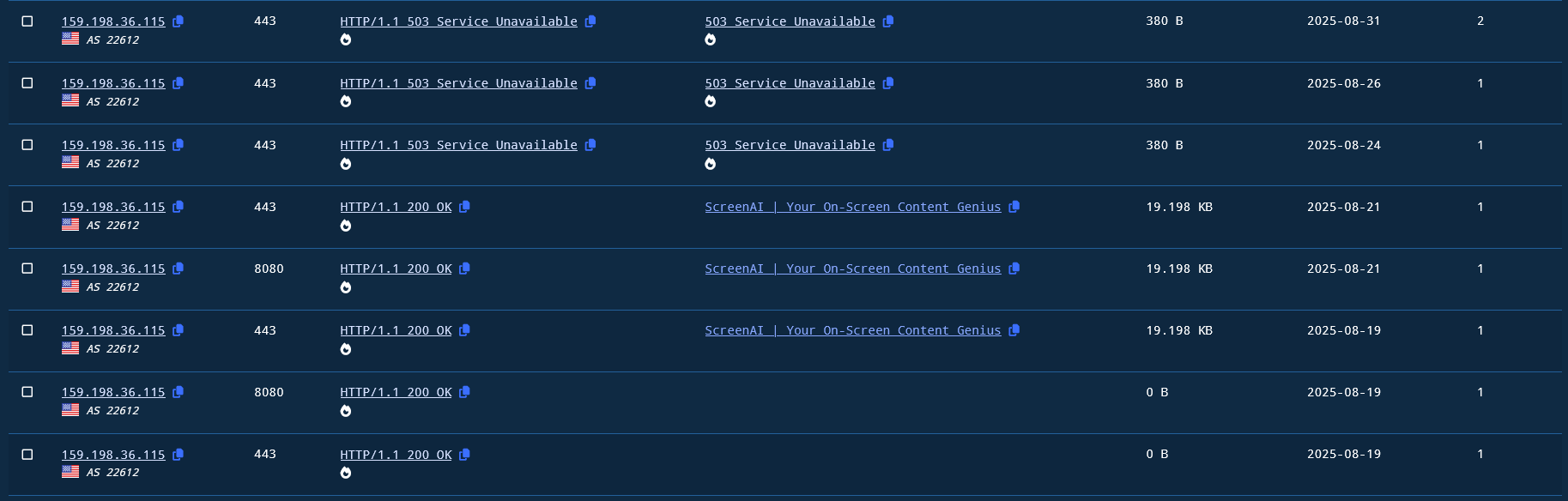
Figure 11. A screenshot of the real IP address of the C2 server.
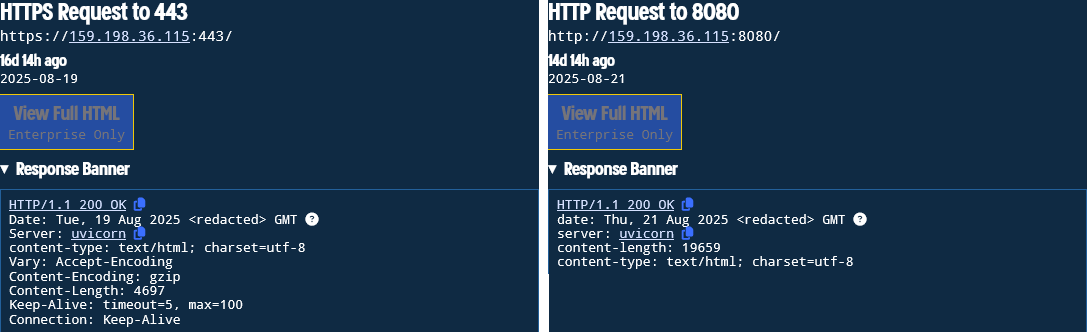
Figure 12. A screenshot of the C2 server’s real IP address and installed application on port 443 and port 8080.
Given the short attack timeframe and the fact that disabling the C2 server renders the deployed backdoors inactive, we assess that MuddyWater has probably followed up with additional tools or malware on infected hosts to maintain access and continue intelligence gathering, this assessment is supported by the open directory observed on that IP which has several RMM and post exploitation tools.
The open directory was exposed using a Python simple HTTP server (SimpleHTTP/0.6 Python/3.10.12). It is noteworthy that no similar servers were identified

Figure 13. Screenshot of the open directory exposed on the C2 server.
Custom Malware and new Remote Monitoring and Management Tool:
During investigation of the infrastructure tied to this campaign, specifically 159[.]198[.]36[.]115, Group-IB Threat Intelligence identified a custom tool and several remote monitoring and management (RMM) utilities hosted on the attacker C2 server. These components appear to have been used for remote access and credential harvesting on compromised hosts. We believe that those tools and utilities were potentially used in this campaign by Muddywater.
The artifacts observed on the C2 include a custom browser credential stealer and two RMM utilities:
- Chromium_Stealer: Custom browser credential stealer hosted at
hxxp://159.198.36[.]115:4444/chromium_stealer_user.exe, disguised as a calculator application.
- Action1: RMM tool identified on the C2, used for remote management and command execution.
- PDQ RMM: Additional RMM utility found on the same C2 server, previously observed in MuddyWater operations.
Chromium_Stealer — technical summary
Host URL: hxxp://159.198.36[.]115:4444/chromium_stealer_user.exe
Disguise: Appears as a calculator-like user App to reduce suspicion.
Primary goal: Harvest credentials stored by browsers and write the harvested data to a local staging file.
Observed behavior:
- Enumerates browsers profile directories to locate the Local State file and profile databases.
- Extracts the os_crypt.encrypted_key from Local State and uses OS crypto APIs to unwrap the master key.
- Terminates active browser processes mostly to remove file locks on profile databases.
- Opens Login Data files to extract stored login credentials.
- Decrypts credentials using the recovered master key and writes the results to a local staging file at
C:\Users\Public\Downloads\cobe-notes.txt(credentials are written in encrypted form).
- Restores the browser by restarting it from its last state to minimize user suspicion.
Affected browsers:
- Google Chrome
- Opera
- Brave
- Microsoft Edge
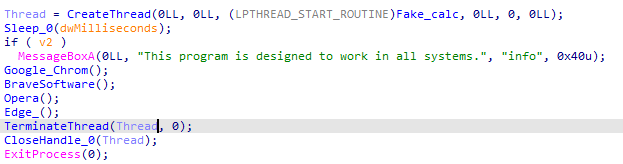
Figure 14. Entry point of the Chromium stealer.
Conclusion
MuddyWater remains a persistent Iran-aligned threat actor engaged in long-term espionage and infiltration campaigns targeting high-value governmental, and international organizations across the Middle East, with expanding operations observed in Europe, Africa, and North America.
This campaign highlights MuddyWater’s evolving tradecraft and operational maturity. The group leveraged a compromised mailbox to exploit trusted communication channels, a highly effective social engineering vector that bypassed conventional security defenses. By deploying updated malware variants such as the Phoenix v4 backdoor, the FakeUpdate injector, and custom credential-stealing tools alongside legitimate RMM utilities like PDQ and Action1, MuddyWater demonstrated an enhanced ability to integrate custom code with commercial tools for improved stealth and persistence.
Given MuddyWater’s sustained focus on governmental targets especially amid the ongoing geo-political tension in the region, Group-IB expects similar campaigns will continue to emerge, leveraging newly compromised accounts and evolving payloads. MuddyWater’s consistent pattern of reusing and modifying its custom malware families underscores a long-term strategic intelligence objective rather than pursuit of short-term gain.
Recommendations
Organizations, particularly those operating within government and critical infrastructure sectors,
can strengthen their defenses against MuddyWater and similar state-aligned actors by
implementing the following measures:
- Strengthen Threat Intelligence and Monitoring
- Subscribe to trusted Threat Intelligence feeds to receive up-to-date Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs) related to MuddyWater.
- Conduct continuous threat hunt for indicators associated with Phoenix, FakeUpdate, and related infrastructure
(e.g., screenai[.]online, sysprocupdate.exe). - Integrate YARA rules and Endpoint Detection and Response (EDR) detections for known MuddyWater malware families.
- Enhance Email and Phishing Defenses
- Deploy sandboxing and attachment scanning for Office documents, flagging those with embedded macros or suspicious VBA code.
- Conduct regular phishing simulations and awareness training for personnel, emphasizing “enable content” macro lures.
- Implement Endpoint and Access Controls
- Disable Office macros by default through Group Policy and allow execution only from signed or trusted sources.
- Deploy and tune EDR/XDR solutions to detect PowerShell misuse, process injection, and abnormal auto registry modifications.
- Enforce Multi-Factor Authentication (MFA) across all accounts to prevent unauthorized mailbox access.
- Strengthen Network and Infrastructure Security
- Monitor outbound traffic for unusual beaconing or repeated HTTP(S) requests matching known MuddyWater C2 patterns and domains.
- Restrict, log, and monitor the use of remote monitoring and management tools (RMMs) such as Action1, PDQ, and ScreenConnect, and only allow the RMM tools needed for the organization.
- Build Long-Term Strategic Defense
- Maintain comprehensive asset visibility and enforce least-privilege principles for all critical systems.
- Deploy behavioral-based anomaly detection for account logins and email patterns from unexpected regions or VPNs.
- Periodically review and update incident response and crisis playbooks to address phishing-based intrusions and credential-compromise scenarios.
DISCLAIMER. All technical information, including malware analysis, indicators of compromise and infrastructure details provided in this publication, is shared solely for defensive cybersecurity and research purposes. Group-IB does not endorse or permit any unauthorized or offensive use of the information contained herein. The data and conclusions represent Group-IB’s analytical assessment based on available evidence and are intended to help organizations detect, prevent, and respond to cyber threats.
Group-IB expressly disclaims liability for any misuse of the information provided. Organizations and readers are encouraged to apply this intelligence responsibly and in compliance with all applicable laws and regulations.
Frequently Asked Questions
What is the MuddyWater Espionage Campaign?
This is a cyber-espionage operation conducted by MuddyWater, an Iran-linked Advanced Persistent Threat (APT) group. During this campaign were sent phishing emails containing Phoenix backdoor malware to over 100 governmental targets worldwide.
When did this campaign begin?
The operation began on 19 August 2025, with evidence indicating that MuddyWater accessed and used an email account through a NordVPN connection to distribute phishing emails.
How were victims targeted?
Victims received phishing emails that appeared to come from legitimate sources. The attached Microsoft Word documents urged recipients to “enable content.” Once enabled, malicious VBA macros executed code that installed the Phoenix v4 backdoor, giving attackers persistent access to the victim’s system.
What malware families were used in the attack?
The primary malware families identified include:
- Phoenix Backdoor (Version 4) — used for persistence, command execution, and data exfiltration.
- FakeUpdate Injector — used to deploy the Phoenix backdoor.
- Chromium_Stealer — a custom credential stealer disguised as a calculator app.
- Remote Monitoring and Management (RMM) Tools — PDQ RMM and Action1, used for remote control and persistence.
How does the Phoenix Backdoor work?
Version 4 of the Phoenix backdoor works by:
- Creating a mutex (sysprocupdate.exe) for process uniqueness.
- Gathering host and system information.
- Copying itself to C:\ProgramData\sysprocupdate.exe.
- Establishing persistence via Windows Registry modification.
- Communicating with its Command-and-Control (C2) server over WinHTTP, receiving and executing attacker commands.
What is the significance of the C2 domain “screenai[.]online”?
The domain screenai[.]online served as the core command-and-control hub for the operation, registered on 17 August 2025 via NameCheap and hosted on 159[.]198[.]36[.]115 behind Cloudflare infrastructure. It remained active for approximately five days, indicating a short and tightly controlled attack window.
How did Group-IB attribute the campaign to MuddyWater?
Attribution was made with high confidence based on shared malware code and macros previously observed in MuddyWater campaigns, consistent targeting patterns focused on governmental entities, and the presence of MuddyWater’s known tools, including FakeUpdate, Phoenix, and PDQ RMM.
What is MuddyWater’s background and motivation?
MuddyWater (also known by aliases such as Seedworm, TA450, Boggy Serpens, and Earth Vetala) has operated since 2017 and is reportedly linked to Iran’s Ministry of Intelligence and Security (MOIS); its primary objectives include long-term espionage and intelligence gathering, tactical disruption of geopolitical adversaries, and maintaining sustained access to strategic sectors such as government, energy, and telecommunications.
Indicators of Compromise (IOCs)
| Backdoor | mononoke.exe | 668dd5b6fb06fe30a98dd59dd802258b45394ccd7cd610f0aaab43d801bf1a1e |
| Backdoor | mononoke.exe | 5ec5a2adaa82a983fcc42ed9f720f4e894652bd7bd1f366826a16ac98bb91839 |
| Backdoor | sysProcUpdate | 1883db6de22d98ed00f8719b11de5bf1d02fc206b89fedd6dd0df0e8d40c4c56 |
| Backdoor | sysProcUpdate | 3ac8283916547c50501eed8e7c3a77f0ae8b009c7b72275be8726a5b6ae255e3 |
| Backdoor | sysProcUpdate | 76fa8dca768b64aefedd85f7d0a33c2693b94bdb55f40ced7830561e48e39c75 |
| Backdoor | sysProcUpdate | 3d6f69cc0330b302ddf4701bbc956b8fca683d1c1b3146768dcbce4a1a3932ca |
| C2 Domain | Creation date 2025-08-17 | screenai[.]online |
| C2 IP | real IP address behind CloudFlare | 159[.]198[.]36[.]115 |