Introduction
Phishing remains one of the most significant cyberattack entry points worldwide. According to Group-IB’s High-Tech Crime Trends Report 2025, phishing activity grew by 22% year-on-year — highlighting how heavily attackers still rely on social-engineering to gain initial access. Meanwhile, the FBI’s IC3 recorded 193,407 phishing and spoofing complaints in 2024, the year’s top cyber-crime category, contributing to $16.6 billion in reported losses.
Methods of phishing continue to evolve as attackers adapt their techniques to avoid being caught by detection systems. Some modify their infrastructure on the fly, relying on legitimate services and real-time data scraping to remain unnoticed. Yet even as these tactics grow more sophisticated, there are still reliable ways to tell a malicious email or URL from a benign one.
This post is the latest entry in Group-IB’s Email Protection Spotlight series, which highlights real-world phishing, explains adversary tactics, and shows how Business Email Protection uses advanced detection and global threat intelligence to stop threats before they can impact your business.
Case study
Since late August 2025, Group-IB has observed a rise in DocuSign impersonation cases. Attacks increasingly rely on trusted business tools, and the familiar look and customization of such services make these emails easier to overlook during a busy workday.
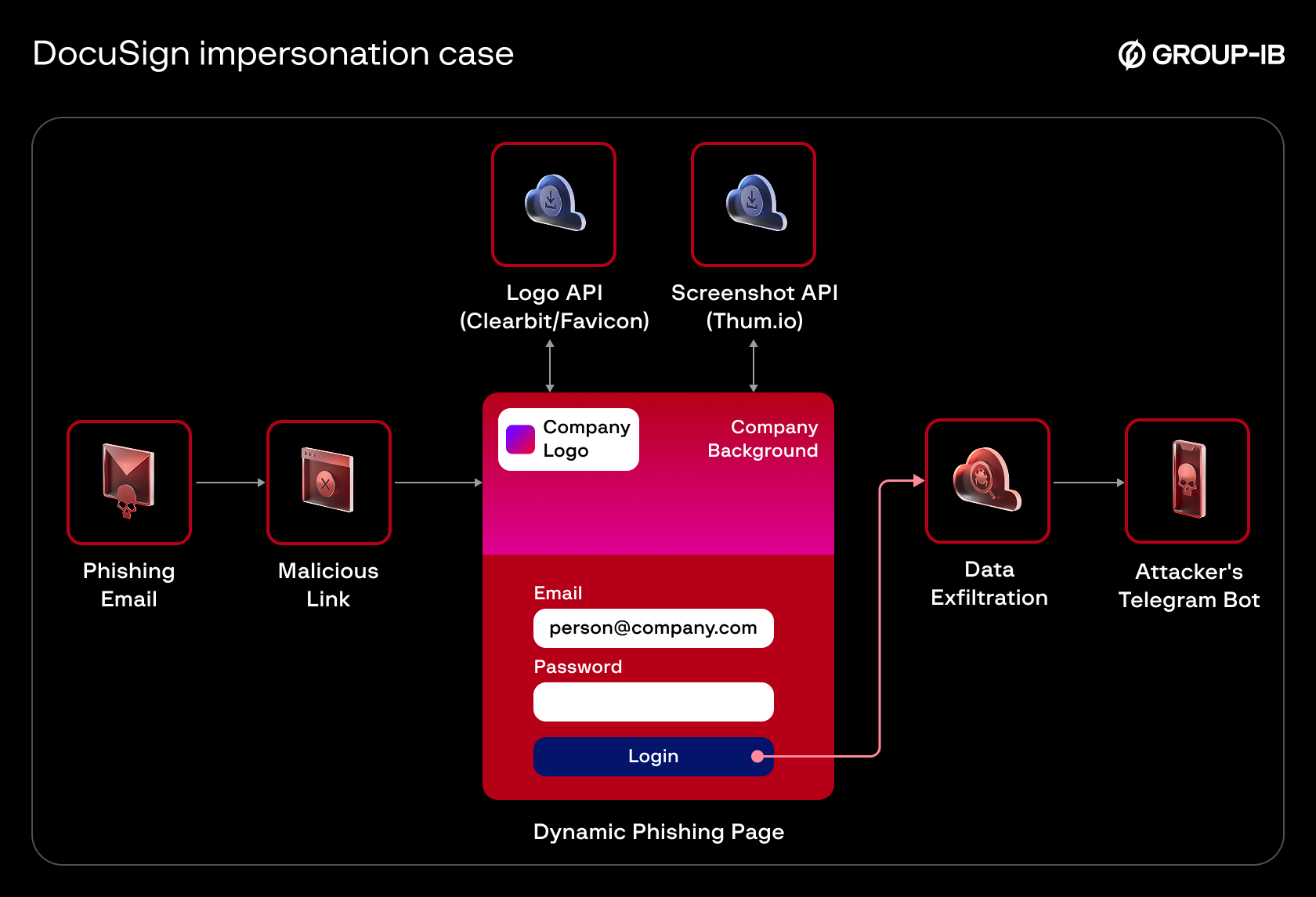
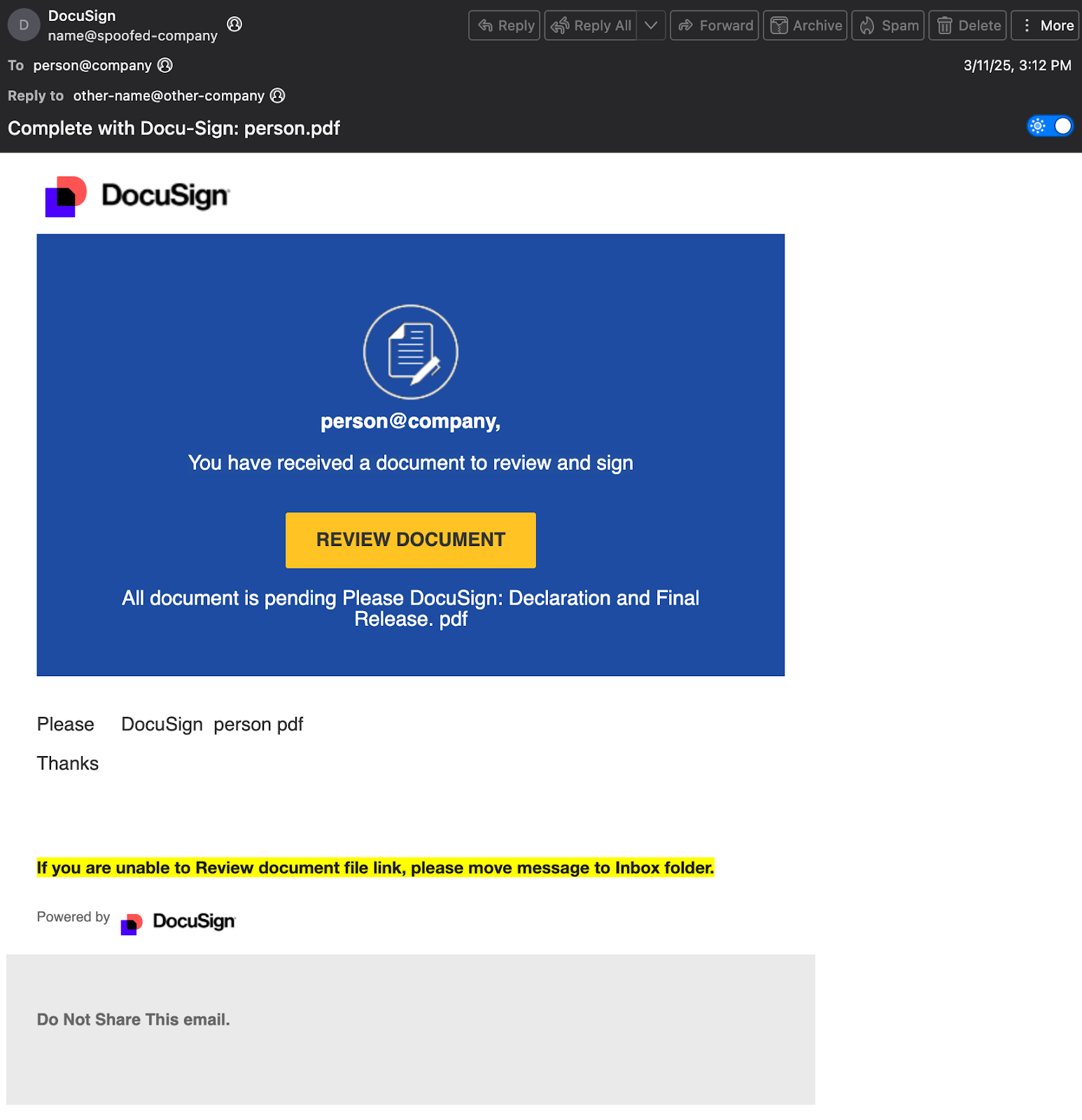
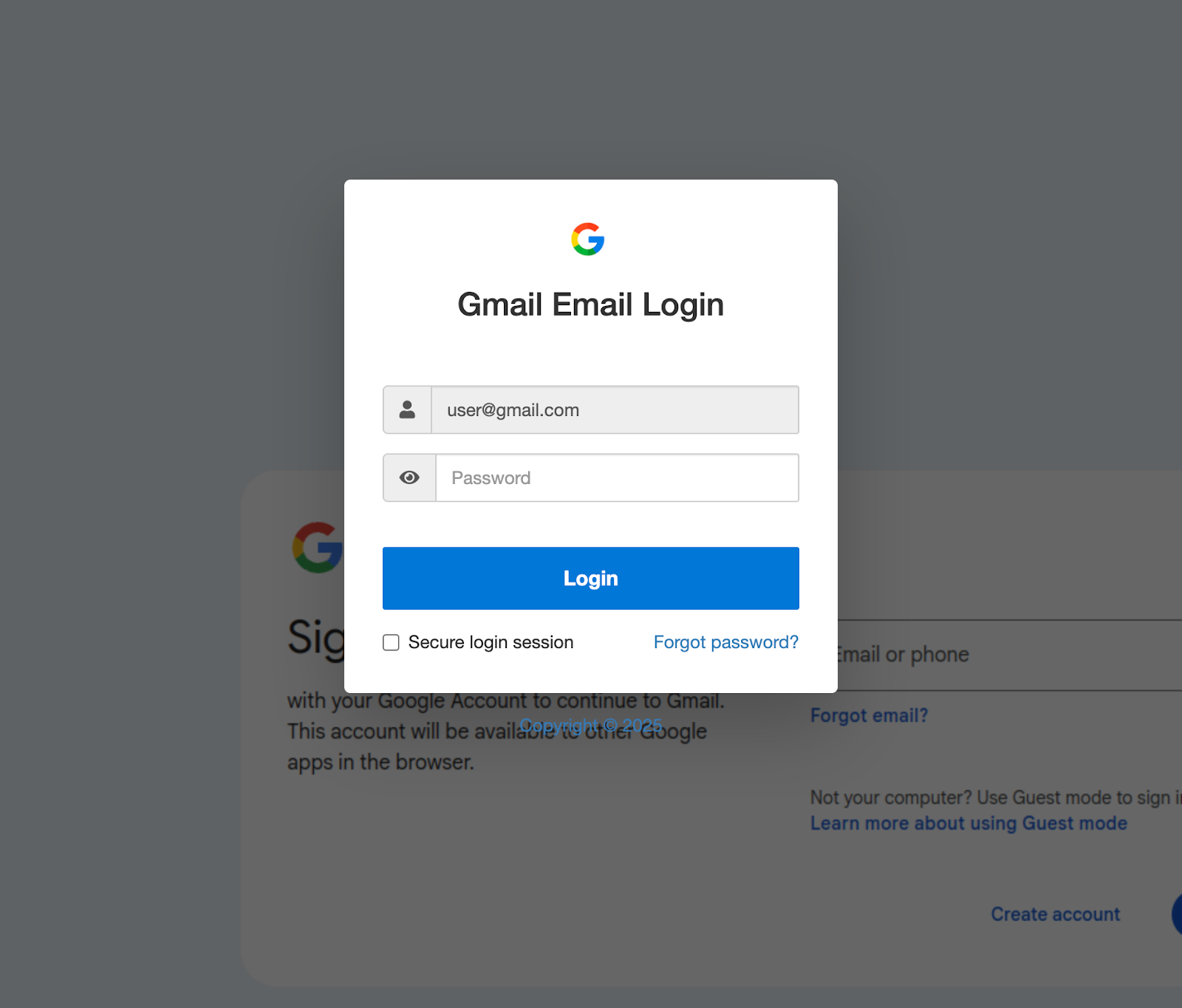
In this wave, the email claims there is a new document to review and closely follows the legitimate DocuSign design. The sender is spoofed — sometimes mimicking the recipient’s own domain — and the message addresses the user by their login name before directing them to a credential-harvesting page built with LogoKit, a phishing framework known for dynamically loading branding elements to create highly convincing login portals. As the site loads, it builds its appearance, allowing attackers to imitate the target organization with minimal effort.
More information about attacks that use DocuSign impersonation, related IOCs and phishing indicators, can be found in the Group-IB Threat Intelligence platform.
Email сharacteristics and tactics
The email is a polished DocuSign imitation sent from a spoofed organization, with the Reply-To header frequently mismatching the sender — often redirecting to an unrelated company or a generic Gmail account. The message refers to the recipient by their login name. The “Review document” button leads to a URL hosted on an IPFS gateway or AWS S3, and the target’s email address is passed in the URL. That link ultimately loads a phishing page built using LogoKit.
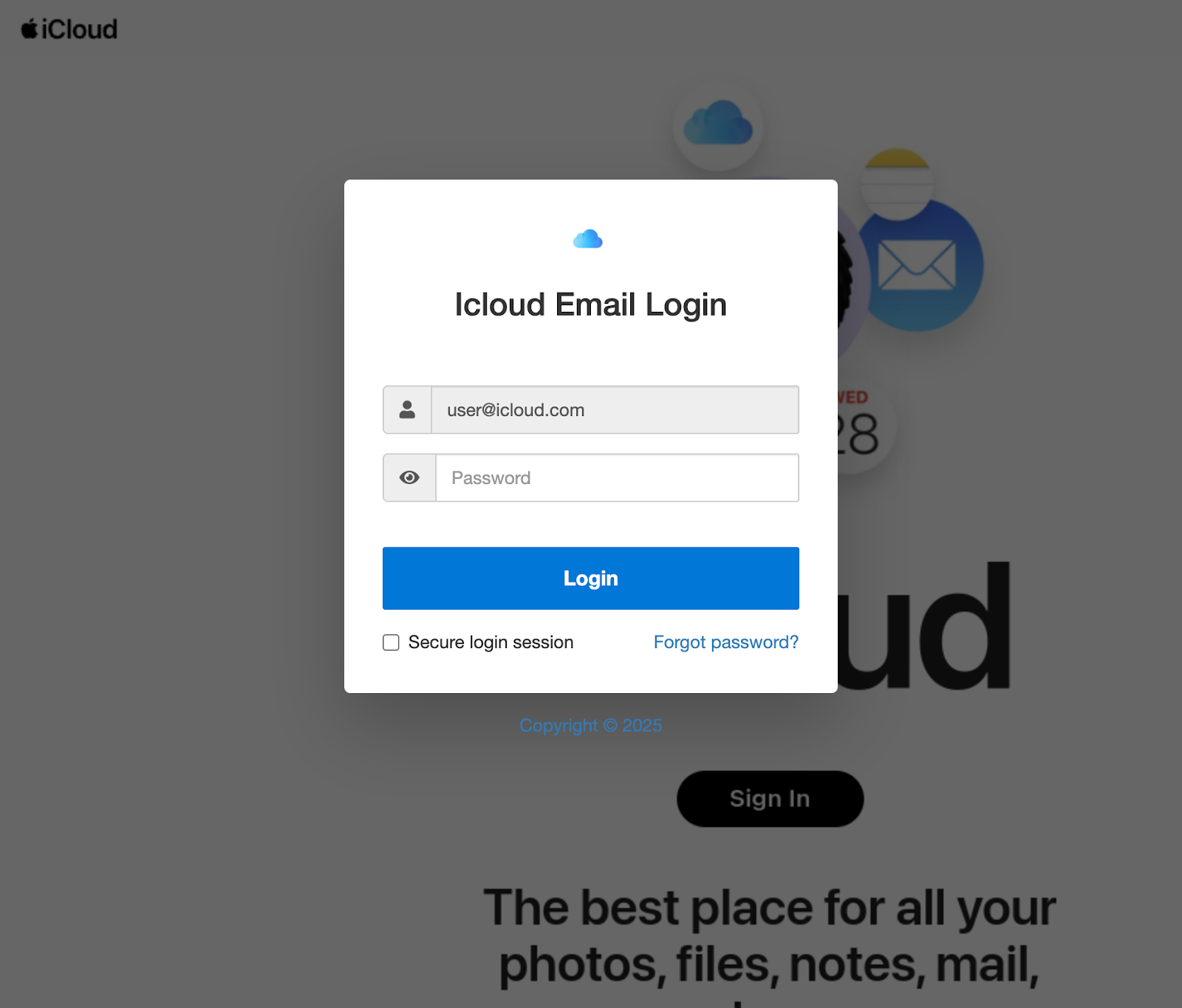
Once the target clicks the link, the webpage dynamically builds itself around the victim’s organization. Using the domain value passed through the URL, the page fetches a background screenshot of the target website via the thum.io service and retrieves the favicon using Clearbit or Google’s favicon service. After loading these visual elements, the site transitions into a customized login screen designed to mimic the target’s own login portal, making the credential-harvesting attempt appear authentic.
Signs of malicious activity
Immediately, the email shows an SPF fail due to sender spoofing, and several other indicators commonly seen in phishing attempts:
- Reply-To points to an unrelated organization or a public email provider
- The target email is forwarded as a part of the URL
- The URLs direct to an IPFS gateway or AWS S3 bucket, where the credential-harvesting page is hosted
All these indicators — a forged sender, infrastructure unrelated to DocuSign, and hosting typical for phishing pages, none of which fit a legitimate business environment — clearly show the intent to harvest user credentials and mark this as a phishing attempt.
Indicators of compromise
IPs:
- 107.174.142[.]90
- 198.23.160[.]148
- 172.245.25[.]171
- 213.210.58[.]119
- 80.97.160[.]191
- 213.209.157[.]59
Email subject:
- Complete with DocuSign: .*
Detection with Business Email Protection
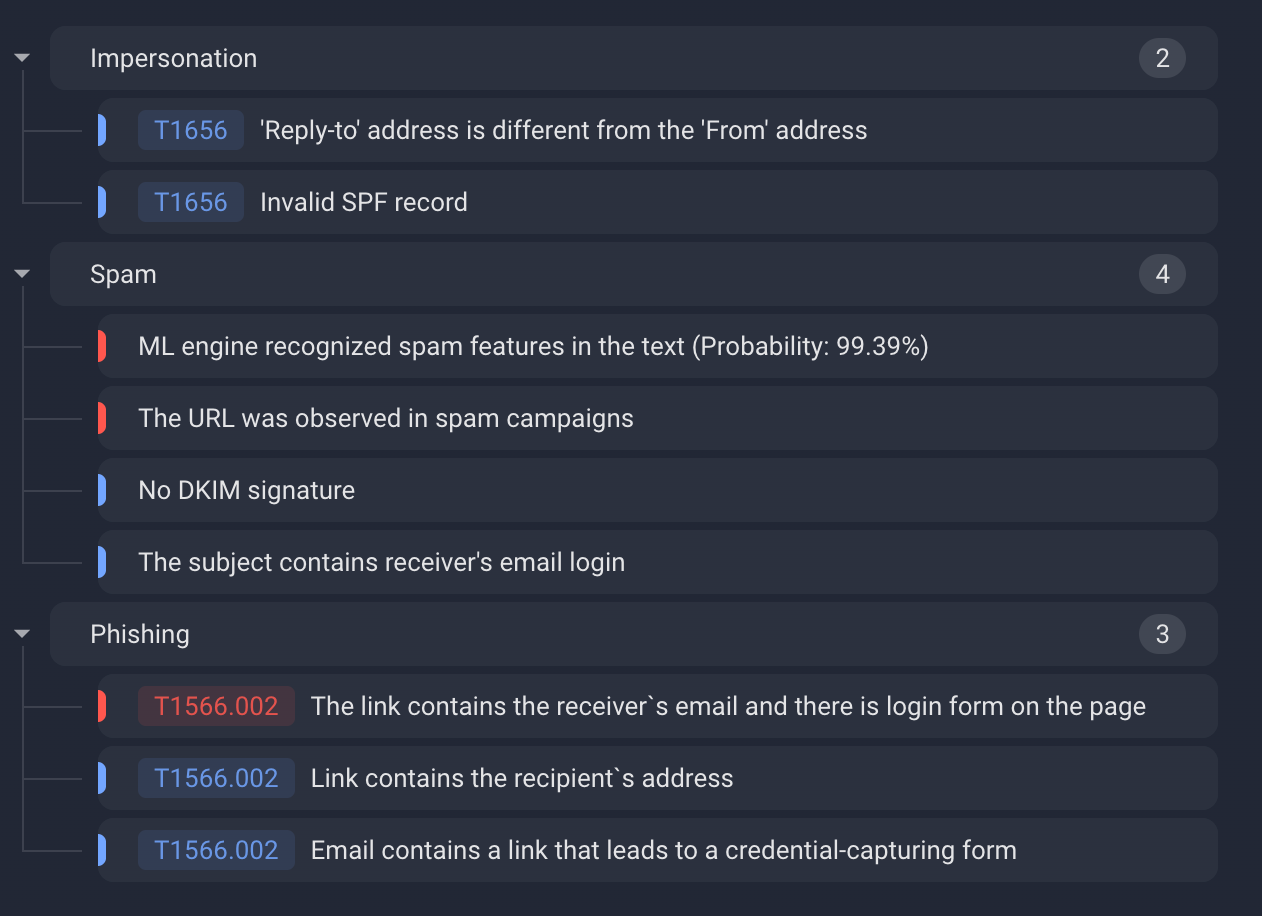
Group-IB’s Business Email Protection platform detects and blocks this DocuSign-impersonation wave by correlating signals across multiple detection layers. The system analyzes sender behavior, message content, embedded URLs, and metadata to uncover the hidden indicators that expose this campaign.
Our multi-layer detection approach includes:
- Sender and infrastructure analysis: BEP detects the mismatch between the Reply-To and From headers,a failed SPF check and a lack of a DKIM signature — all indicators of spoofed sender identity.
- Content and linguistic signals: Machine-learning models recognize spam-like features in the email content with high confidence, and the subject line contains the recipient’s login, a tactic commonly used to personalize phishing messages.
- URL and behavior analysis: The embedded link includes the recipient’s email address, has been previously seen in spam campaigns, and points to pages hosted on IPFS or AWS S3 with the victim’s email appended to the url — a known pattern of dynamic credential-harvesting pages.
This combined signal correlation allows BEP to identify and block the attack even when it closely imitates legitimate DocuSign notifications.
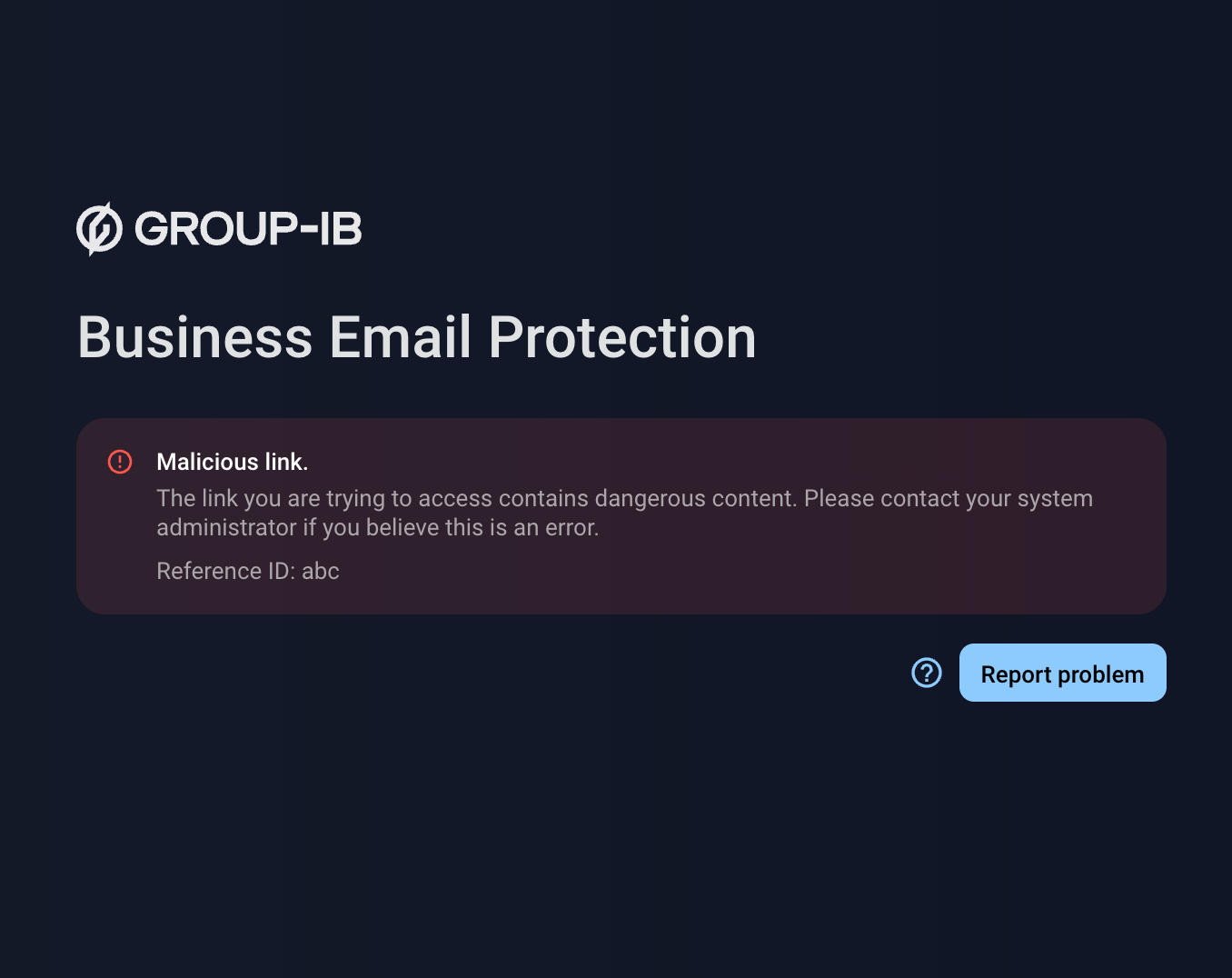
Even if an attacker hides behind a highly reputable email context, remote all the possible phishing indicators and “disarms” the URL during delivery, when the user clicks the malicious link, Group-IB’s Time-of-Click analysis evaluates the page in its live state, extracting all indicators — hosting details, parameters, and any dynamic content. If the page loads a credential-harvesting form or triggers malicious behavior, BEP blocks access immediately and displays a warning page, stopping the attack even at its final stage.
Conclusion
This DocuSign impersonation wave demonstrates how modern phishing campaigns combine trusted brands and real-time page morphing to evade traditional defenses. By analyzing sender anomalies, content signals, URL behavior, and the dynamic state of the phishing page itself, Group-IB’s Business Email Protection effectively identifies and blocks the attack at every stage — from delivery to the final click.
Comprehensive, multi-layer detection and Time-of-Click protection ensure that even highly customized, adaptive phishing attempts are stopped before they can compromise user credentials or impact the organization.
Group-IB’s Business Email Protection team continuously monitors emerging supply chain threats, analyzes adversary techniques targeting developer ecosystems, and updates detection models to protect our customers against evolving email-based attacks on critical infrastructure.