Introduction
Building unbeatable defenses against ever-evolving cyber threats often puts organizations in a tough spot. Today, most organizations rely on a vast portfolio of cybersecurity tools implemented across different layers to address diverse needs—ranging from firewalls (FWs) and cloud infrastructures with built-in and third-party security solutions to email protection, endpoint detection, and response (EDR) platforms, and threat intelligence feeds—both public and private.
However, end-to-end protection cannot be built on fragmented defenses. Yet many security teams and leaders adopt tools without considering integration from the outset. What is the aftermath?
- Discarding solutions or overlaying them without a defense-in-depth strategy
- Added complexities and cost co-efficient of incompatible solutions
- Revisiting integrations as an answer to such inconsistencies and problems arising from misconfigurations
- Not just working on integrations but introducing scalability and automation to future-proof their security architecture
- Benefit/Risk analysis of using prebuilt cybersecurity integrations versus developing custom API/SDK solutions
With so much to consider when approaching integrations, some pushback is inevitable. Don’t worry—this is the first blog in our series on cybersecurity integrations, where we’ll tackle key challenges and provide strategic insights for cybersecurity integrations. In this post, we’re addressing one of the most critical issues: misconfigurations—how they arise (explained through scenarios), the impact, and how to prevent them.
Connections enabling cybersecurity: Do you need an integrated approach?
Threat actors increasingly leverage automation, AI, and cross-platform vulnerabilities to execute multi-vector attacks. Conventional technologies and security strategies may no longer be sufficient against these evolving threats. What’s needed is the power of technologies working together for full-cycle risk management—making integration the most critical enabler.
Integrations are key to automating redundant security processes, streamlining workflows for better risk management, and ensuring seamless data flow between tools—preventing critical risk intelligence from getting lost in the void. An integrated security stack = a cohesive ecosystem = improved security function, better risk management and mitigation = an overall augmented security posture.
The first step is visibility and adversary intelligence, followed by detection and quick remediation. To build a robust cybersecurity system, it’s essential to partially or fully integrate log sources—including firewalls, servers, endpoints, and applications. These logs provide critical insights into activities across the network. However, too many log sources might also lead to irrelevant noise.
An effective analysis process cuts unnecessary highlights, focusing on important data to improve the threat landscape. Important data includes attributed alerts from XDR and AI-driven analysis, ensuring only high-value data is deciphered.
A fragmented security system leads to gaps in identifying threats, but too much connectivity is also a risk, allowing attackers to move freely within the network. It might sound counterintuitive, but segmentation (separating network areas) limits attackers’ lateral movement and should be part of the overall integration strategy. A properly integrated XDR can monitor segmented networks and correlate events without complete interconnectivity.
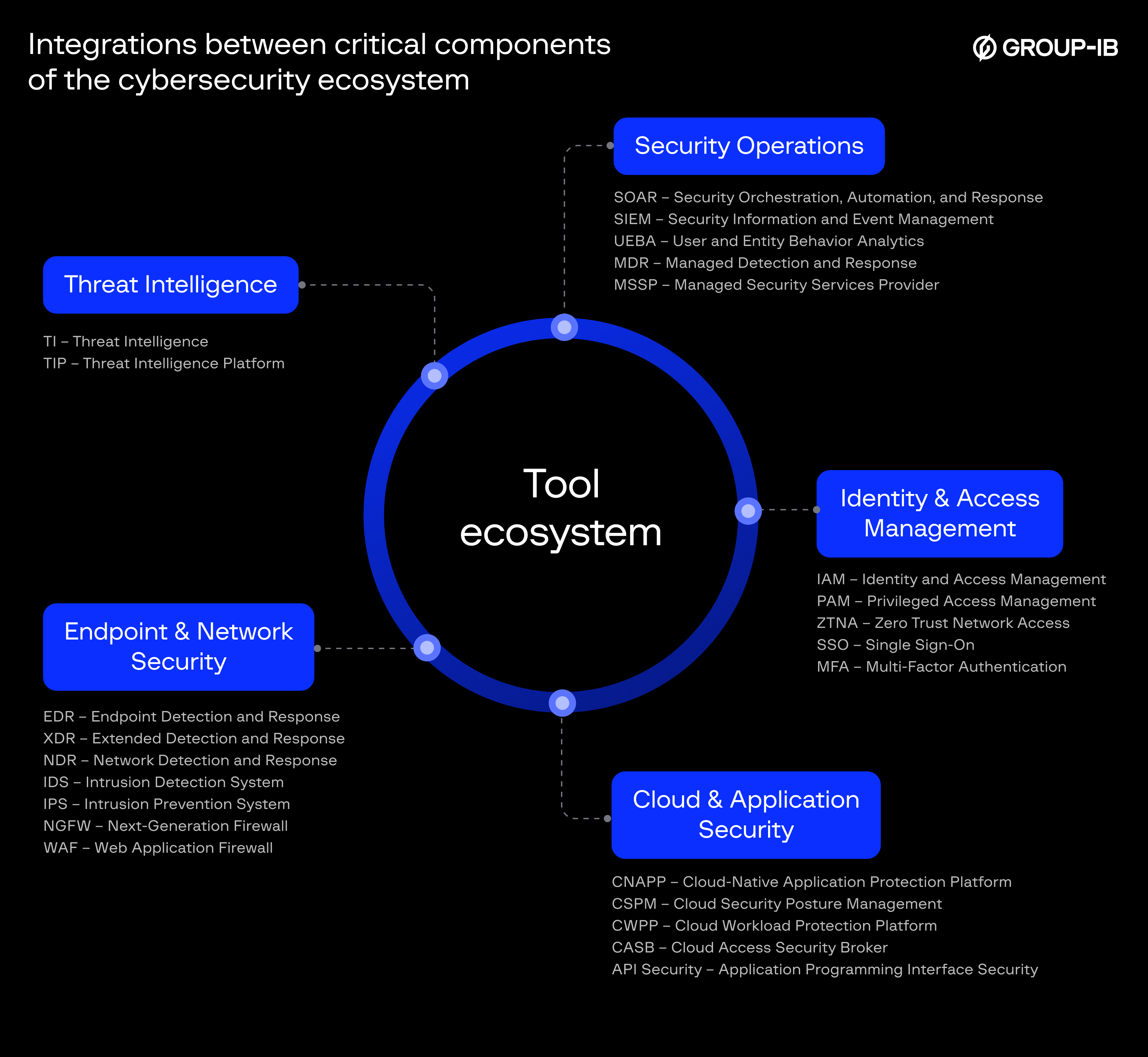
Image 1: Essential tools forming the cybersecurity ecosystem
While each security tool serves a critical purpose, the real challenge lies in making them work as one cohesive unit. Without proper integration, ingesting log sources, mapping the entire attack surface, correlating intelligence on assets, threat actors, and network anomalies, and automating initial remediation are all impossible.
Moreover, improper integrations aren’t just bottlenecks but active risks—creating potential exploit avenues through open ports, unpatched software, overly permissive access controls, and misconfigured databases, cloud systems, or APIs – expanding the attack surface further.
Addressing A Common Challenge In Cybersecurity Integrations: Misconfigurations
Infrastructure changes—cloud migrations, system upgrades, or new security tool integrations—can introduce misconfigurations if not handled properly. These misconfigurations may result from default settings, inconsistent security policies, or overlooked dependencies between systems.
A critical aspect of this is data misconfiguration — inconsistency in how data is stored, processed, or shared within an organization’s systems. According to IBM X-Force, data exposure due to misconfigurations accounted for 32% of breaches in 2023.
Cybersecurity systems rely on seamless data integration to provide comprehensive visibility and enable effective threat detection and response. However, misconfiguration in data handling can create inefficiencies and expose organizations to significant security gaps.
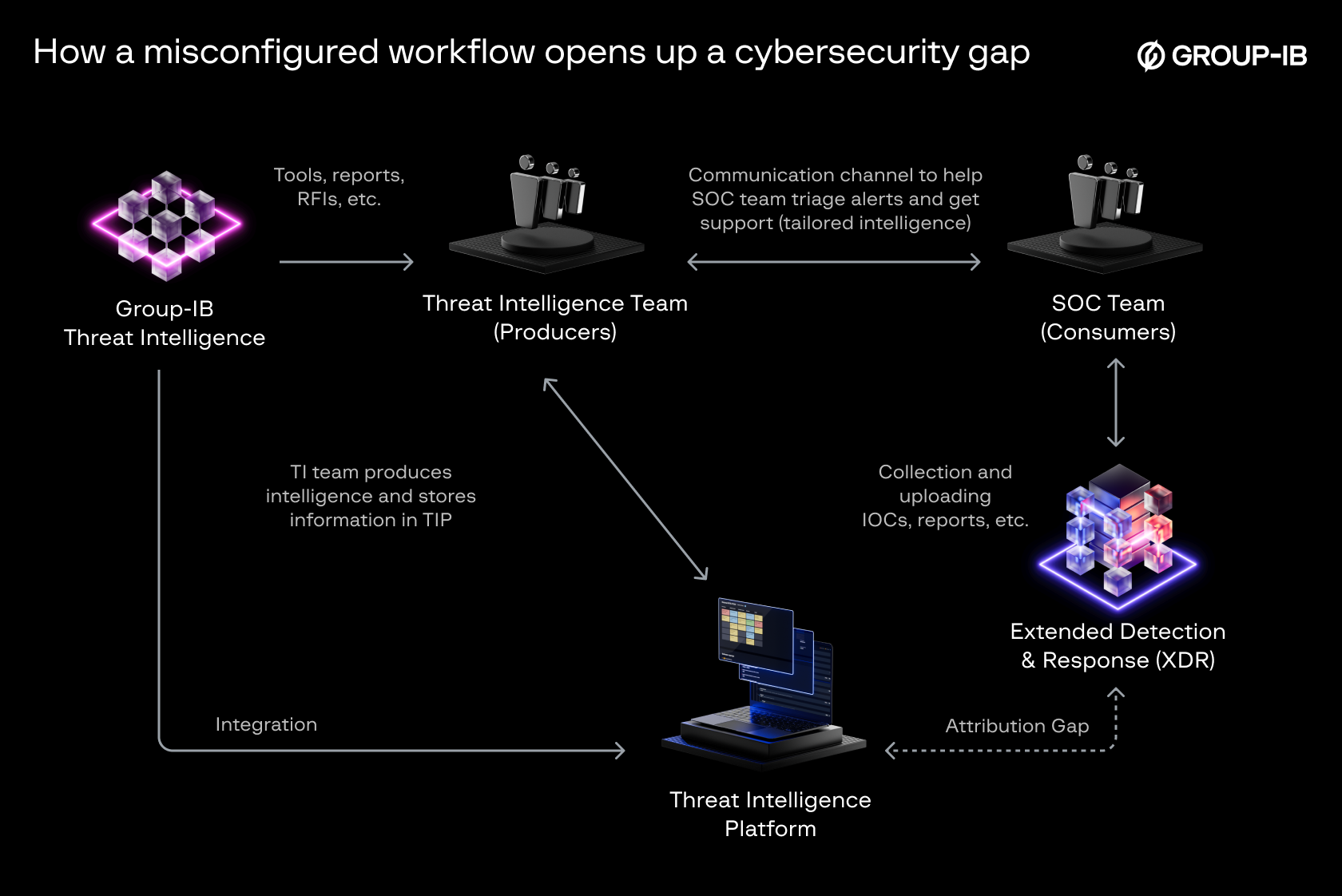
Image 2: Misconfiguration in a typical integration workflow
Scenario: A gap in actioning threat intelligence
Threat Intelligence Received
A Threat Intelligence vendor shares an IOC—a malicious IP associated with an APT Group called “X,” a known Advanced Persistent Threat actor. This IOC is tagged with relevant context, including:
- Indicator Type:IP
- Attribution: APT-X Group (Threat Actor)
- Threat Score: Critical
- Related Campaigns: Persistent, targeted attacks on financial institutions
Breakdown Of A Security Gap
Step 1: IOC is loaded into the Threat Intelligence Platform (TIP)
The Threat Intelligence Platform ingests the IOC and all its associated metadata, including attribution to APT-X Group.
Step 2: TIP-to-XDR Misconfiguration (Security Gap)
Due to a misconfiguration in the integration between the TIP and the XDR solution, the IOC is forwarded to the XDR without its attribution (Threat Actor label) and associated campaign context. Only the bare IOC remains in the XDR—a malicious IP address flagged as “high-risk” but with no further context.
Step 3: SOC Detection & Investigation
Several days later, the SOC analyst received an alert from the XDR indicating a malicious IP connection from an internal host. However, since the attribution information (APT-X Group) is missing, the analyst views it as an isolated event—a standard malicious IP alert.
Instead of treating it as part of an APT campaign, the analyst classifies it as a low or medium-priority incident and does not escalate it for deeper investigation.

Image 3: How a misconfigured workflow opens up a cybersecurity gap
Outcome: A Persistent, Undetected Breach
The APT actor remains undetected within the network, moving laterally and escalating privileges over several days until a significant breach occurs.
Potential Impact
Operational – Insecure infrastructure, security gaps, and exposed vulnerabilities.
Financial – Significant losses and reputational damage.
Increased Analyst Fatigue – Lack of attributions and context, no native integration, and unclear escalations.
Misconfigurations in threat intelligence tools create inefficiencies and expose organizations to significant security gaps. Without proper integration, data remains fragmented, limiting its effectiveness in detecting and responding to threats. This highlights the importance of a well-structured integration approach that ensures seamless data flow, minimizes human errors, and maximizes the value of intelligence-driven security operations.
Other Potential Scenarios Due To Inconsistent Integrations
To illustrate the scope and depth of other typical challenges, take a look at the categorized examples below. Each entry highlights a real-world integration issue, its operational consequence, and an example that security teams may already be experiencing – often without realizing the root cause is integration itself.This table isn’t meant to list every possible issue, but it serves as a possible mockup of what can (and does) go wrong when security tools fail to work together seamlessly.
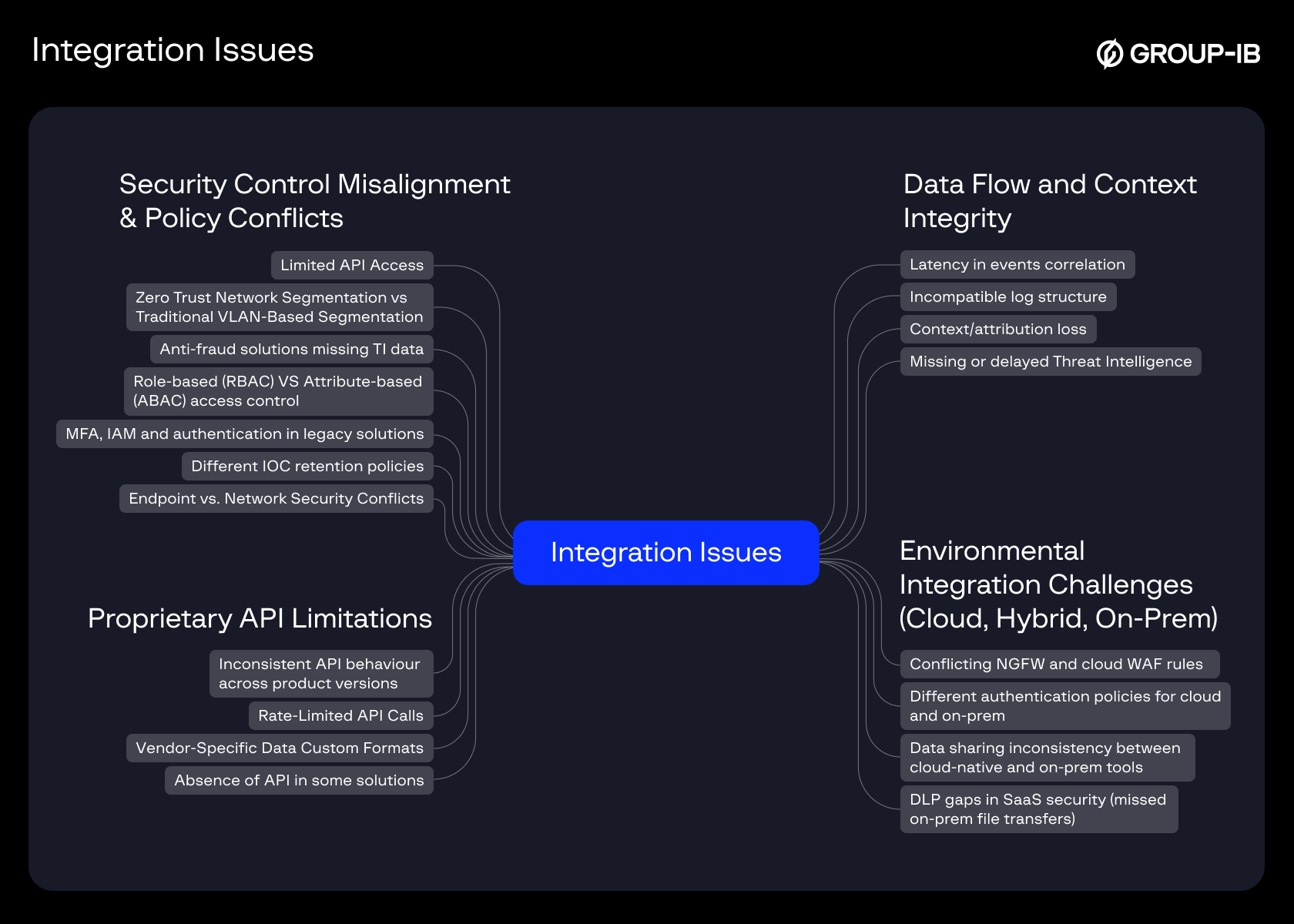
Image 4: Common integration issues
To illustrate the scope and depth of other typical challenges, take a look at the categorized examples below. Each entry highlights a real-world integration issue, its operational consequence, and an example that security teams may already be experiencing – often without realizing the root cause is integration itself.This table isn’t meant to list every possible issue, but it serves as a possible mockup of what can (and does) go wrong when security tools fail to work together seamlessly.
| Category | Potential Scenarios | Examples | Consequences |
| Data Flow & Context Integrity | Missing or delayed Threat Intelligence (TI) | TI feed updates every six hours; attackers rotate infrastructure hourly | Missed TI updates lead to outdated defenses |
| Context/attribution loss | APT tag missed from IOC when passing from Threat Intelligence Platform to Extended Detection & Response (XDR) | Threat actor attribution lost, misclassification of threats. | |
| Incompatible log structure | SIEM rejects improperly formatted JSON logs from endpoint tools | Critical logs are missing or unstructured, making IR slower | |
| Latency in event correlation | Cloud telemetry arrives 10 minutes late, breaking correlation with real-time EDR events | Delayed APT detection, SOC overload, increased SIEM costs | |
| Environmental Integration Challenges (Cloud, Hybrid, On-Prem) | Cloud VS On-prem Forensics | Cloud Incident Response (IR) auto-terminates the virtual machine, but SOC needs a full disk image | Incident response gaps due to forensic data mismatch |
| Conflicting NGFW and cloud WAF rules | WAF blocks traffic; FW on-prem allows the same vector | Firewall mismatches allow unintended access, expanding the attack surface | |
| Different authentication policies for cloud and on-prem | Cloud AD enforces MFA; on-prem AD accepts password-only logins | Cloud and on-prem authentication conflicts weaken IAM security | |
| Data sharing inconsistency b/w cloud-native and on-prem tools | Cloud logs not reaching on-prem SIEM | Limited visibility into cloud threats from on-prem SIEM | |
| DLP Gaps in SaaS Security (missed on-prem file transfers) | Dropbox upload via SMB not detected by cloud DLP | Failure to detect on-prem file transfers, leading to data leaks | |
| Security Control Misalignment & Policy Conflicts | Zero Trust Network Segmentation vs Traditional VLAN-Based Segmentation | Microsegmentation blocks east-west traffic; VLAN allows it | Attackers exploit inconsistent segmentation rules |
| Anti-fraud solutions missing TI data | Fraud TI feed not integrated with anti-fraud analytics platform | Gaps in fraud detection logic, leaving financial systems exposed | |
| Role-based (RBAC) VS attribute-based (ABAC) access control | ABAC rule grants broad access based on one attribute vs. tight RBAC | Access control mismatches create privilege escalation risks | |
| MFA, IAM, and authentication in legacy solutions | Okta policies differ from on-prem AD; gaps in user enforcement | Legacy authentication methods weaken Zero Trust efforts | |
| Different IOC retention policies | IOC TTL 30d in TIP, 90d in XDR – causes missed correlation | Discrepancies in threat detection | |
| Endpoint vs. Network Security Conflicts | EDR allows Chrome plugin; proxy blocks its traffic | EDR allows an application, but NGFW blocks its traffic, causing operational delays | |
| Limited API Access | SOAR cannot push block actions to third-party EDR | Inability to integrate key security tools due to API restrictions | |
| Proprietary API Limitations | Rate-Limited API Calls | Cloud security API allows only 100 calls/min by license | APIs throttled, preventing real-time security automation |
| Vendor-Specific Data Custom Formats | SIEM dev team must write a custom parser for proprietary XDR output | Custom formats require manual log transformation, increasing costs | |
| Absence of API in some solutions | Closed vendor system with no external data hooks | No option to integrate | |
| Inconsistent API behavior across product versions | API changes between v1 and v2 break SOAR playbooks | Breaks automation scripts and integrations during upgrades |
How To Avoid Misconfigurations From Change In Infrastructure?
Invest in a Security Posture Management System: Declarative environment control doesn’t eliminate misconfigurations on its own—but it helps define the desired state of security configurations across infrastructure and automatically enforces it. Combine this with continuous monitoring using SIEM and CSPM tools to detect and remediate misconfigurations in real-time.
Pre and Post-Deployment Security Validation & Testing: Before applying changes, verify system integrity in a sandbox environment. After implementing solutions, conduct regular audits, penetration testing, and security configuration reviews to identify misconfigurations that could expose threats.
Enforce Configuration Baselines: Follow security baselines mandated by regulations (e.g., CIS Benchmarks NIST guidelines) to ensure secure system integration by focusing on user authentication, system configurations, and network security settings.
Even when configurations are optimized, the end objective is to ensure that tools work seamlessly together. Integration is not just about connecting tools—it’s about building an “interoperable, communicating” ecosystem that provides comprehensive visibility, reduces noise, and maximizes the value of security data and resources. Achieving this requires careful planning and a strategic approach to avoid pitfalls like poor interoperability and fragmented data that misses critical threats.
To help you navigate this process, here are other key considerations when moving toward an integrated approach:
Your Current Security Stack: A clear analysis of your current security stack’s operational capacity and limitations—technologies, processes, and policies used to protect your digital assets, such as endpoint security tools, firewalls, and XDR. These tools should be able to communicate via APIs and standardized formats. Cybersecurity integrations aim to enhance protection, streamline workflows, and provide measurable benefits rather than adding unnecessary tools that cannot communicate effectively.
Integrated APIs & Automation: Modern cybersecurity operations rely on a steady flow of consistent, high-quality data across tools. Yet, disparate formats, siloed telemetry, and lack of standard APIs often lead to incomplete visibility, correlation failures, and alert fatigue.
With API-friendly, integration-oriented tools, organizations can maintain a consistent flow of data across environments – informing the entire ecosystem, automating routine tasks such as log tracking, patch management, correlating threats, vulnerability management. This ensures real-time detection and mitigation of emerging risks requiring limited manual oversight, allowing teams to focus on other critical tasks.
Security by Design in Integrations: When approaching integrated security solutions, keep the data triad in mind: confidentiality, integrity, and availability. Data must not be lost or left unsecured while in transmission or at rest within systems and tools. Interoperability and harmonization are factors, and so is ensuring that integrations do not leave you prone to breaches, unauthorized access, DoS attacks, and additional vulnerabilities.
Feedback Loop: An effective integrated approach continuously evaluates and scales depending on the evolving cyber threat landscape. Organizations should incorporate a threat intelligence feedback loop into their strategy according to the ingested data on changes in adversarial TTPs and real-time IOCs from multiple sources, which are then used to contextualize feeds and enrich threat alerts and retaliation measures. Another factor that hinders the process is the disconnect between teams.
For example, SOC analysts may be unaware of additional sandboxing or different tools available within the organization, and fraud teams may operate in isolation from cybersecurity teams, leading to gaps in intelligence exchange and response. These can result in communication inefficiencies on the client side. Therefore, security engineers must build a feedback mechanism for better inter-departmental communication, gap analysis, threat attribution, and scoring to enhance processes.
Integrate Cybersecurity Effectively With Group-IB
At Group-IB, our mission is to build a non-fragmented, interoperable security ecosystem that helps organizations stay ahead of threats without getting lost in complexity.
We actively partner with our customers and technology partners to fight cybercrime. That’s why we offer free integrations and do not limit our APIs to underscore our vision that cybersecurity should be a shared and collective endeavor, not a siloed effort. To know more about our approach to integrations, check out the page here: [Link]
To build a cybersecurity integration strategy for your cybersecurity and get your unaddressed queries answered that we might’ve missed, reach out to Group-IB experts here.

































