Introduction
Cybersecurity risk management is a constantly moving target. With the hyperscaling threat landscape and emerging risks, cybersecurity is booming to become more than a half-trillion dollar industry by 2032. Despite increasing investments, the risks do not decrease, and the CISO is responsible for managing them.
CISOs are majorly involved in defining and overseeing the organization’s risk reduction strategy. However, depending on the organization’s structure, role dynamics, and industry, this function is often shared with the Chief Risk Officer (CRO) — especially in financial services and large enterprises — the Chief Information Officer (CIO) in government sectors, or the Data Privacy Officer (DPO) in data-centric industries. While these leaders typically operate with separate budgets, they collaborate on cybersecurity initiatives.
That said, for C-level executives, risk management isn’t just about putting out fires as they arise. It’s about strategically overseeing operations that ensure business longevity, building resilience against evolving threats, and maintaining control over an increasingly complex digital landscape. Tasks of such gravitas demand that you get the fundamentals right — and that’s exactly what we’ll help you do in this blog.
CISOs, cyber risk management require you to be risk Intelligent – But what does that mean?
Today, cybersecurity leadership is about proactiveness, not mere survival. The “We’ll contain the risk when it presents itself” approach only exposes a lack of foresight, strategy, and accountability—critical for securing stakeholder trust and aligning security with business objectives.
With 82% of CISOs now reporting directly to the CEO, bridging the gap between technical risk, business impact, and decision-making is much required. Strong communication skills, business acumen, and regulatory expertise are no longer optional—they are expected—and these aren’t the only concerns on a CISO’s plate.
Some of these are building defense mechanisms against AI-driven attack vectors, third-party risks, vendor ecosystems, supply chain attacks, insider threats, and evolving compliance requirements—all while ensuring real-time risk aggregation, analysis, and management—has become a ground expectation of cybersecurity leadership.
At the same time, for CISOs, security priorities today also include:
- Leveraging automation, integration, and real-time monitoring for better oversight, reduced redundancies, and streamlined risk management.
- Enhancing security posture by improving the ability to prevent, detect, and remediate critical risks through integrated systems and processes.
- Seamlessly integrating security functions into different departments’ workflows, ensuring risk awareness is embedded across the organization.
- Disseminating risk information organization-wide to foster a strong security culture.
- Improving strategic flexibility—protect existing assets while enabling secure innovation.
- Providing a confident front to leadership—help the board, C-suite, and key stakeholders understand, monitor, and manage IT risks effectively.
- Maintaining a centralized IT risk repository—integrate, document, and manage IT risk requirements in a single, accessible system.
- Empowering the organization with self-assessment programs—drive a structured approach to audits, risk assessments, and continuous mitigation improvements.
As organizations’ risk portfolios grow, the responsibilities mount. However, effective risk management comes down to strategic analysis, prioritization, a boots-on-the-ground recovery plan, clear ownership, and company-wide collaboration. Let’s see how you can approach each.
How Do CISOs Define Risks Through Data?
Today’s threat landscape rapidly evolves, forcing businesses to make urgent security changes. Managing risk effectively requires continuous, relevant, validated data streams across hybrid, cloud, and legacy environments.
Data security typically revolves around three key pillars:
- Identity – Who are you dealing with? (Customers, employees, suppliers, partners)
- Assets – What are you protecting? (Systems, data, third-party risks)
- Change – When are security events occurring? (Network activity, configuration updates, threat movements)
To gain comprehensive visibility, businesses must leverage multiple intelligence + departmental sources. More on this in the next section →
Aggregating Risk Data for Analysis
Looking at risks solely through a technology lens creates a tunnel vision, leading leaders straight into unaddressed security gaps that could have costly business consequences. Every business function generates some level of risk, which must be identified, aggregated, and addressed.
Aggregating risk data helps organizations understand their overall exposure—at an enterprise level or within a new product, project, function, or department. This, in turn, enables CISOs to prioritize risks, enhance communication, and make informed response decisions.
One key source for risk data aggregation is a Cyber Threat Intelligence (CTI) solution. CTI helps businesses monitor threat actors and their TTPs, actively exploited vulnerabilities, and leaked Indicators of Compromise (IoCs) from underground and commercial sources. However, CTI becomes even more powerful when integrated with other security solutions, such as Endpoint Detection and Response (EDR) and Digital Risk Protection (DRP), to identify brand impersonation, credential leaks, and insider threats.
A strategic approach to risk aggregation combines CTI, business context (finance, HR, security teams), and regulatory compliance data (audit findings, compliance reports, and regulatory filings). By consolidating this data into a centralized risk intelligence system, organizations can enhance cyber exposure visibility for:
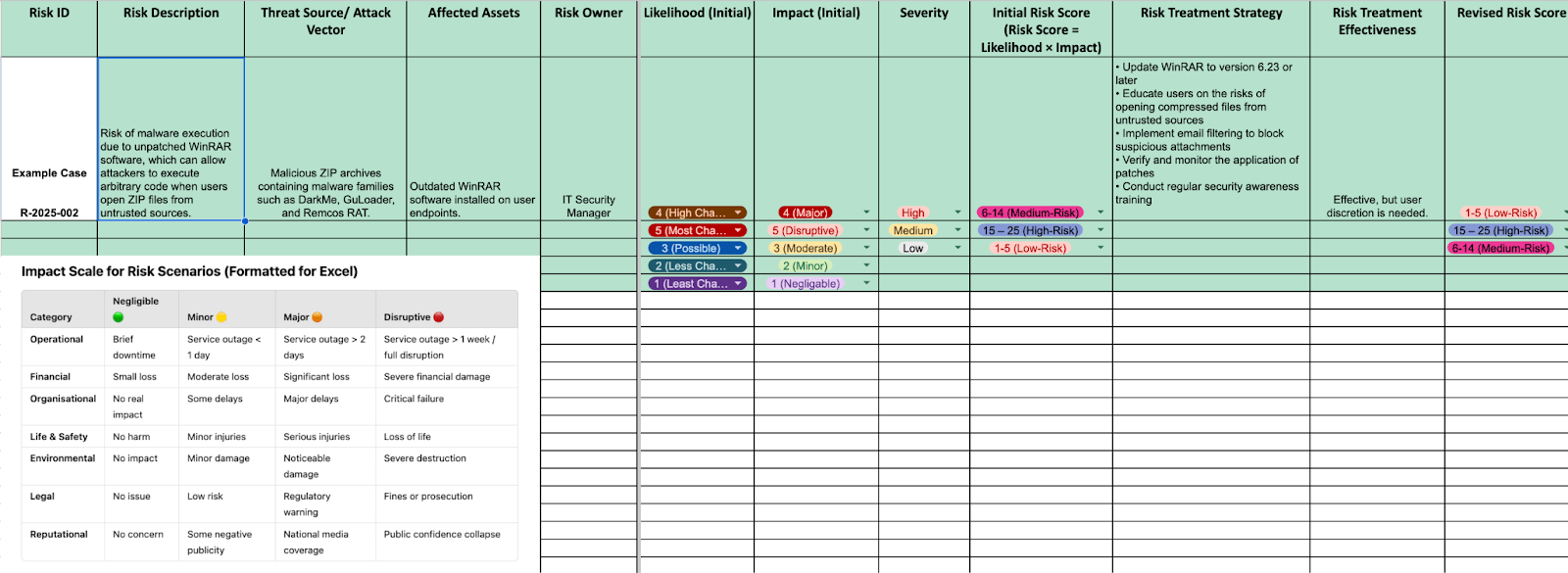
- Quantifying risk, and prioritize mitigation efforts (via a Risk Register for structured documentation).
Note: In a risk register, the focus is on assets first—such as hardware, applications, and documents—before identifying associated risks and vulnerabilities. Vulnerabilities are typically handled separately within a vulnerability management program rather than being the primary entry in a risk register.
Get your own editable copy of the template
- Threat landscape analysis to identify emerging risks (through centralized dashboards and heatmaps tailored to industry-specific TTPs and risk trends).
- Proactive response planning based on real-time intelligence (continuous updates on threat actor activity and vulnerabilities).
Impediments to Inadequate/ Incomplete Risk Analysis
Inadequate Asset Inventory AnalysisFor cyber risk management, CISOs must first gain a comprehensive understanding of the infrastructure they’re defending. Asset inventorying is crucial and should be a continuously updated layer across security, business, and IT systems, offering a complete view of all technology assets. This approach enables seamless orchestration of key vulnerability management, compliance reporting, and incident response workflows.
Risk Register used as an end-all meansIndexing every risk in the register is a great way to log risks, but prioritization and information-sharing can become challenging. While it serves as a single source of truth for a company’s risk portfolio, it can also be a liability if it falls into the wrong hands. Manual threat tracking is essential, leveraging real-time asset logging, scanning, risk scoring, and automated patching can cut through the clutter, making the traditional risk register feel outdated. These solutions don’t just document risks—they fix them immediately.
Risk Communication is ComplexIt is difficult to speak and understand the language of risks. It isn’t always straightforward, and many security professionals struggle to differentiate between threats, vulnerabilities, and actual risks, leading to misjudgment in security priorities. A threat actor’s tactics, techniques, and procedures (TTPs) don’t just result in a single security caveat. For example, using phishing techniques to implant malware that obfuscates security systems and retrieves confidential information is not a risk but a method of attack. The actual risks can be translated into:
Too Many Risks to ManageJustifying the likelihood and impact of all current and anticipated risks is practically impossible. No risk register can capture every risk and its estimated impact with 100% certainty, making prioritization challenging.
Inconsistent & Incomplete Data for Decision-MakingHistorical risk data and imperfect event reporting mean organizations lack full visibility into past breaches and threats, leading to gaps in risk assessment and incomplete analysis.
Evolving & Persistent ThreatsAdversaries are highly adaptive and continually refine their TTPs, making static defenses obsolete and requiring real-time intelligence updates to maintain relevance. |
Risk Assessment
While each assessed risk is documented in the risk register and assigned a threshold to determine whether it should be accepted, prioritized, or mitigated, CISOs must also consider the business impact. Understanding which risks pose the greatest threat to critical assets is key.
Risks should be categorized into critical, high, medium, or low to guide decision-making effectively. The following things need to be cleared in precedence to a risk assessment.
Risk Definition: Risk is the potential for loss, damage, or disruption due to the exploitation of a network vulnerability. In cybersecurity and business contexts, risk represents the likelihood of an event occurring and its impact on assets, people, operations, or reputation.
Risk Statement: A structured way to describe risk that typically includes the source of risk (threat, vulnerability, or gap), the event or condition that may lead to an undesirable outcome, and the repercussions of that event occurring.
Example Risk Statement: Due to open user privileges and a lack of identity access management (source), there is a risk of malicious or accidental data exfiltration (event), which could result in operational disruption, regulatory penalties, and loss of intellectual property (consequence).
How is risk measured? Risk is measured using qualitative or quantitative approaches, which are supported by certain models to score risk under event loss frequency and magnitude. But when it comes to the leadership, rather than overwhelming them with technical scores or models, CISOs should identify high-level risk scenarios that reflect these principles.
The risks and impact should be clear and simple, based initially on
Confidentiality – Can sensitive data be exposed?
Integrity – Can information or systems be tampered with?
Availability – Can services or data be disrupted?
Some organizations also consider Non-Repudiation—ensuring actions or transactions cannot be denied later—a key element.
The details of risk measurement—such as particular control failures, system dependencies, or exposed vulnerabilities—are typically owned and managed by business process owners who understand their operational impact. They can pitch in to refine risk criteria, translate technical insights into objective insights, and show the mitigation processes to management for improved security.
Management must also actively collaborate to understand the risks and participate in their assessment, acceptance, and treatment. If resources allow, engaging a third-party vendor can enhance the risk assessment process.
Risk Framework Dependencies
Risk assessments are typically based on industry-recognized methodologies such as NIST (National Institute of Standards and Technology) or ISO standards like ISO27001, which is the backbone for most risk management and data privacy laws, e.g., GDPR, in-country data privacy laws.
Some also include project management because managing risk is a project for each department. This approach is commonly used for compliance-driven risk assessments, incident response enrichment, risk evaluations, and security control architecture and implementation. Teams use methodologies like PMBOK (Project Management Body of Knowledge) or agile frameworks to ensure documented and structured execution. Although it is a continuous project, it is not a one-time event.
While these frameworks help meet compliance requirements or follow a risk-based approach (e.g., FAIR), they directly influence security decisions, risk prioritization, resourcing, and budgeting. However, an effective risk management strategy should extend beyond mere compliance.
There are many frameworks to choose from, each with its own strengths. A compliance-based approach often starts with a framework like NIST CSF, operating under the assumption that implementing more controls reduces risk. While widely accepted for structuring cyber risk management programs, this approach primarily measures compliance—not actual risk reduction.
Compliance frameworks do not assess the effectiveness of cybersecurity controls or help prioritize their deployment. This is where the FAIR (Factor Analysis of Information Risk) framework does chime in, making it a valuable complement to compliance-driven models. FAIR enables organizations to quantify risk, evaluate control effectiveness, and make data-driven security decisions—capabilities that compliance frameworks alone do not provide.
Ultimately, CISOs must balance both approaches—leveraging compliance frameworks to meet regulatory requirements while using risk quantification models to drive strategic security decisions. To do this effectively, they must answer key questions:
- Impact: How much damage could this risk cause?
- Likelihood: How probable is it that this will happen?
- Velocity: How quickly would it escalate if ignored?
- Preparedness: Do we have the ability to mitigate or respond effectively?
Risk Prioritization: (The Governance, Risk, and Compliance (GRC)-Approach)
Scanning your environment for vulnerabilities can present hundreds of alerts, including false positives, demanding immediate attention. But is giving your time equally to all vulnerabilities a cost- and time-effective strategy? No, you need to prioritize. Overseeing, prioritizing, and monitoring key deliverables within the agreed-upon timelines of the remediation programs is essential.
Risk prioritization and scoring help separate critical issues from irrelevant noise or an unending stream of alerts. A targeted approach can identify 10–15 high-priority risks or critical risk scenarios with calibrated loss magnitude assessments, incorporating key contributing factors such as whether a system is internet-facing or not, the system’s value/liability characteristics (e.g., whether it is identified as critical by the team or contains highly sensitive data), historical data, and adjusted risk assessment as new intelligence is derived.
Addressing critical risks first can help reduce risk exposure and the likelihood of risks turning into actual incidents. In formal risk management practices, prioritization is typically based on:
Risk = Threat x Vulnerability x Asset Value
(Asset Value = Confidentiality x Integrity x Availability (CIA)) and (Risk Level = (Probability x Impact x Asset Value
An organization is scanning its network for vulnerabilities and identifies the following:
GRC-Based Prioritization:
Result: Vulnerability B receives higher priority in remediation despite having a lower severity on paper.
For additional context with the prioritization decision, the following factors can also be added: Asset Severity: How critical is the system affected? Is it an internet-facing asset or deep within the internal network? Does it contain sensitive data (e.g., customer PII, financial records)?
Threat likelihood in context
Results from Prioritization:
|
Why not CVSS-based prioritization? While GRC frameworks focus on broad risk exposure and support board-level decisions, CVSS is designed to analyze the technical aspects of vulnerabilities. It helps security and IT teams prioritize patching, manage remediation workflows, and score vulnerabilities based on exploitability and severity from a technical standpoint.
Risk Response & Recovery
Despite constantly improving risk containment and management processes, risks cannot be 100% predicted or avoided. While preventing cyber risks is essential, an equally (if not more) effective incident response plan must be in place, ensuring security leaders are ready to fight back.
Being proactive gives you an edge, and CISOs are encouraged to lead their own tabletop exercises to identify gaps in their incident response plans and strengthen their skill sets.
During a security incident, people look to leaders for strategic guidance, reassurance and assuaging, and decisive action. Therefore, CISOs must be well-prepared with a contingency plan and have the tools and expertise to minimize damage, minimize disruption, and restore business operations efficiently. This includes
- A structured incident response and recovery plan, leveraging automated initial responses to intrusions and conducting thorough digital forensics.
- Understanding the attack vector, entry points, network activity, and adversary tactics (TTPs) helps enhance future remediation efforts.
- Strengthening security systems with refined detection rules and logic ensures similar attacks can be identified and mitigated early.
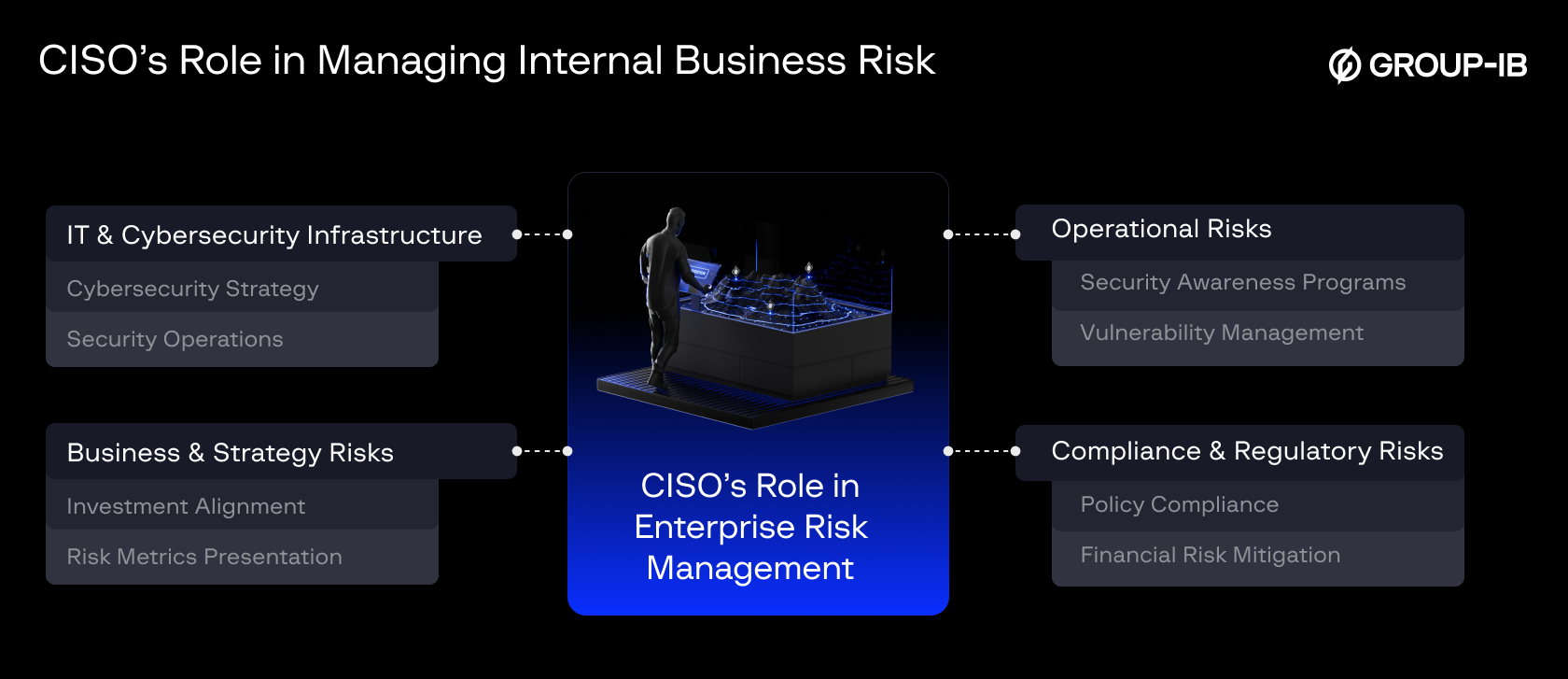
Risk Ownership: Is Everything CISO’s Liability?
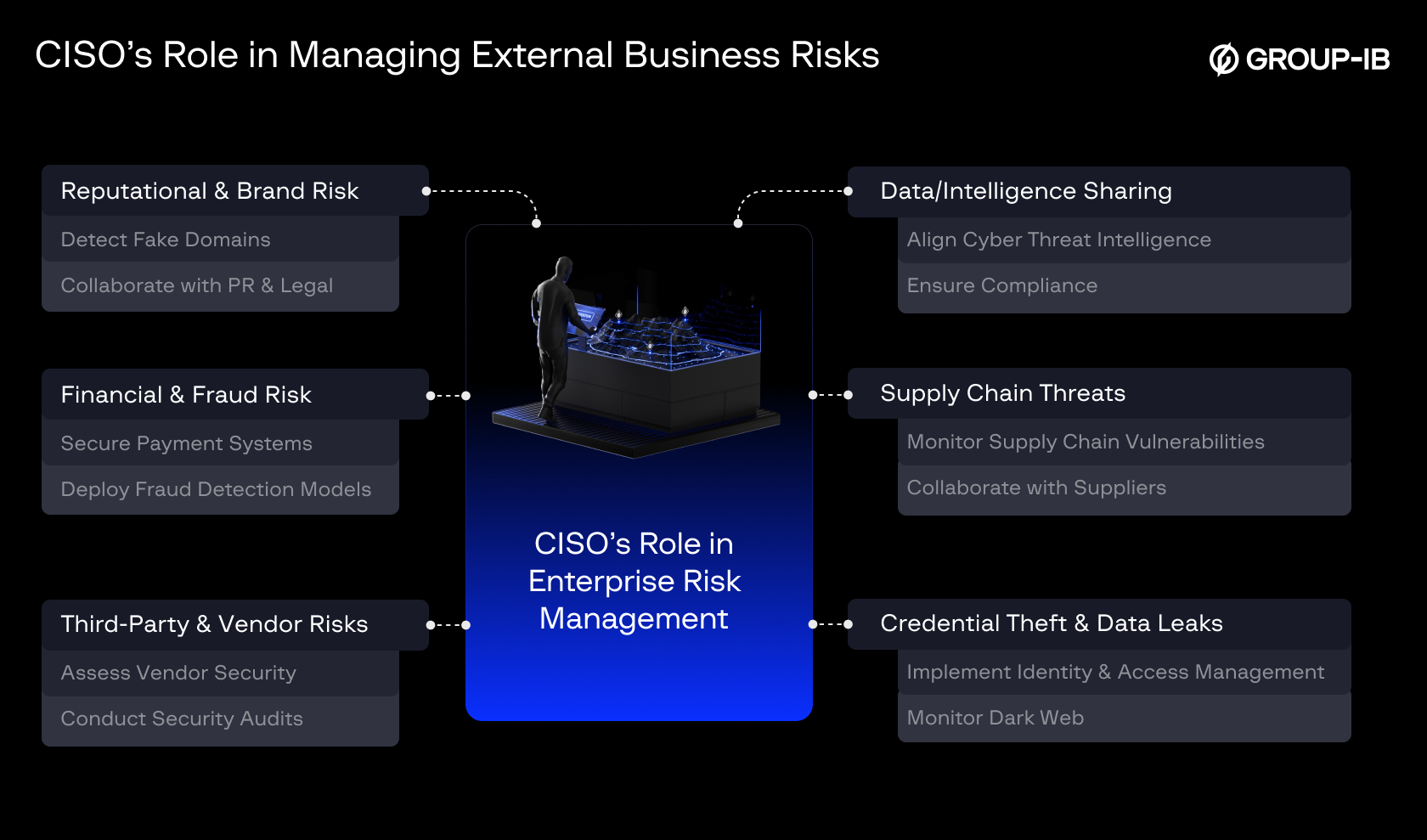
Today, CISOs are (indirectly) responsible for broader risk management beyond just IT, infrastructure, and security risks. While a CISO’s responsibility bifurcation might differ in different organizations, their advisory, oversight, and alignment on the business impact of risks are crucial. That includes finance, reputation, expansion, governance, compliance, and more risks.
But with the growing risk portfolio encompassing not just extensive IT gaps but also the overarching business, it is impractical for one role to handle all of it or have a single perspective of the entire cybersecurity domain. Here is where collaboration and delegation lead to a strengthened posture. A true partnership between CISOs, CIOs, CROs, and other leaders needs to emerge.
Identifying a risk does not mean owning it. Since risks originate from different departments, they should be assigned to individuals best positioned to influence and manage them—CISOs are not always the primary owners.
CISOs Communicating Risks To The Management
100% of security leaders are expected to communicate cybersecurity and technology risks, yet CISOs and business leaders often speak different languages. Identifying risks isn’t enough—you need to articulate them in a way that enables informed decision-making. Translating security risks into business impact remains one of the biggest challenges.
Speaking about technical metrics—such as the number of security events, intrusion attempts, vulnerabilities patched, MTTR, MTTC, and MTTD—often leaves boards confused. They are accustomed to objectives, numbers, and targets tied to business outcomes —operational risks, financial impact, regulatory exposure, and shareholder confidence.
As for the officially implied requirements, the U.S. Securities and Exchange Commission (SEC: https://www.sec.gov) requires companies to disclose some key information on cybersecurity that is also useful for the board to know.
Business Meets Security: Framing Cyber Risk for The Leadership
To get executive buy-in, CISOs must communicate risk in terms of the risks being managed, the controls in place for mitigation, and the operational and financial impact on the business. CISO budget decisions must also directly address the most relevant threats to the business, clearly showing measurable risk reduction and how certain measures align with organizational priorities.
Control inconsistencies and cybercriminals aren’t risks—what they lead to are real risks. This shift in mindset strengthens risk management and prioritization, ensuring leadership understands what truly matters. When measuring risk, take a risk-based approach focusing on loss event scenarios, not just security gaps.
❌ Incorrect problem statement: “A ransomware attack could encrypt our data.”
Correct statement: “A ransomware incident could lead to data leaks that can compromise our clients’ information. It disrupts business operations for 5+ days, impacting revenue streams and critical services.”
❌Incorrect problem statement: “We have vulnerabilities in our cloud infrastructure.”
Correct statement: “Unauthorized access to our cloud environment could lead to data exfiltration, resulting in regulatory fines and loss of customer trust.”
❌ Incorrect problem statement: “We’re experiencing heightened bot activity on our website, making us vulnerable to a DDoS attack.”
Correct statement: “A DDoS attack on our customer-facing website could cause service disruption for 48+ hours, leading to % revenue loss, SLA breaches, and reputational damage.”
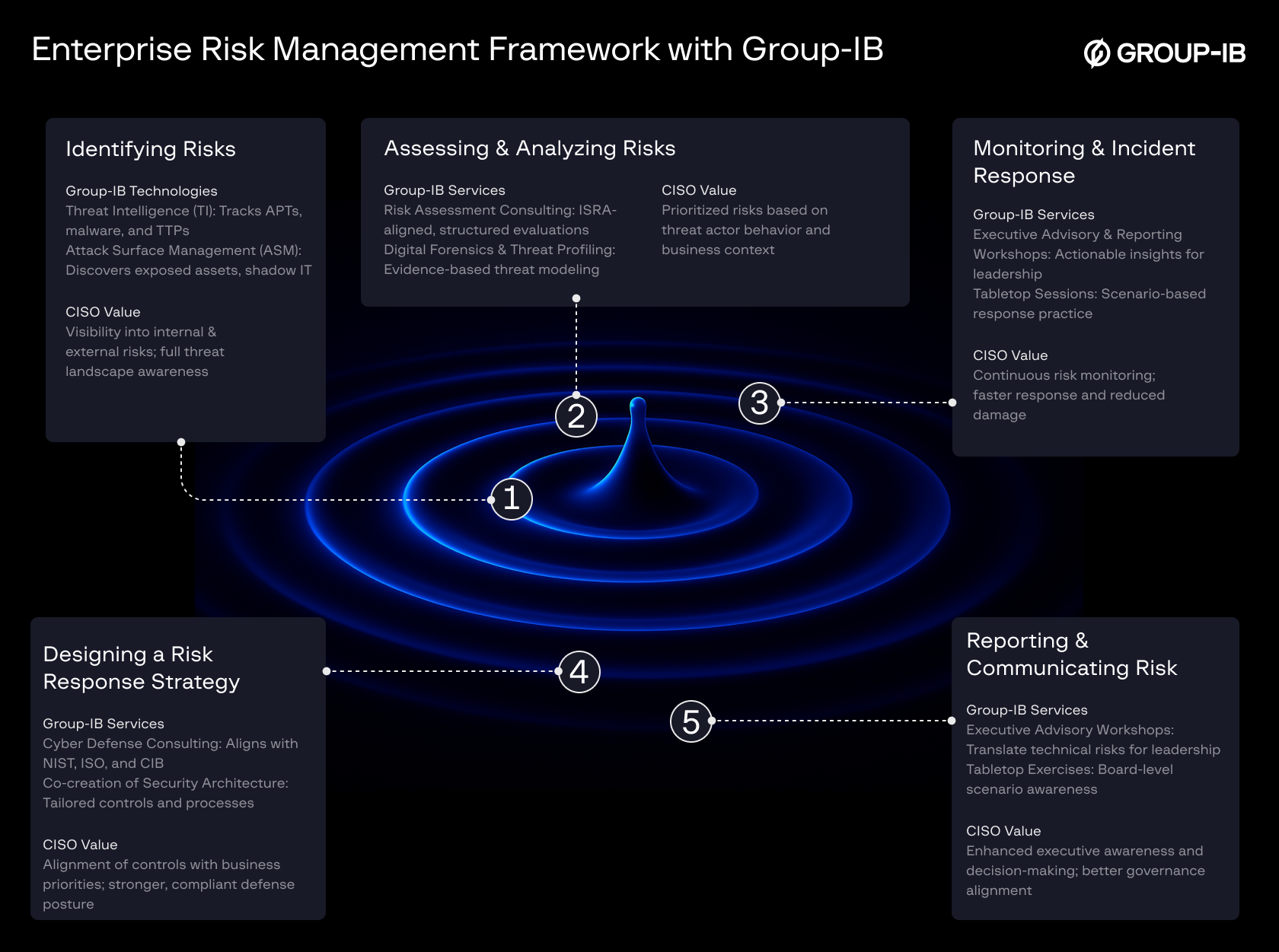
Handle Enterprise Risk Management like a CISO with Group-IB
A CISO’s role is part technical and part business—a treacherous line but highly empowering and rewarding if done right. For business leaders, who often don’t grasp the severity of a threat unless it has a cost equivalent attached, a CISO must translate cybersecurity risks into financial and operational impact.
The skills needed are extensive, and having a truly blended cybersecurity and business partner like Group-IB provides critical leverage to help you excel as a CISO.
A CISO must bridge the gap between cybersecurity operations and Enterprise Risk Management (ERM) by leveraging products and services to enhance risk assessment and mitigation. Group-IB’s solutions, such as Cyber Threat Intelligence (CTI), provide enriched risk insights by feeding intelligence into ERM processes, and Attack Surface Management (ASM) helps monitor, score, and manage external risks. Meanwhile, our services, like Cyber Defense Consulting, help organizations align cybersecurity frameworks with business risk management strategies, ensuring a stronger and proactive security posture.
With our constant and holistic support, you can establish a robust security function, drive effective risk management, create business value, strengthen cybersecurity culture, and effectively communicate the importance of your initiatives to leadership — report both incremental and long-term improvements to auditors and stakeholders with confidence. Get in touch to begin a strong partnership today.