Authorized Push Payment (APP) fraud presents a unique challenge: victims authorize the transactions themselves. Whether it’s an invoice scam, investment fraud, romance scheme, or a fake executive demanding urgent payment, the victim willingly initiates the transfer. By the time fraud teams spot the pattern, investigate, and confirm the fraud, the money has already moved through mule accounts and beyond recovery.
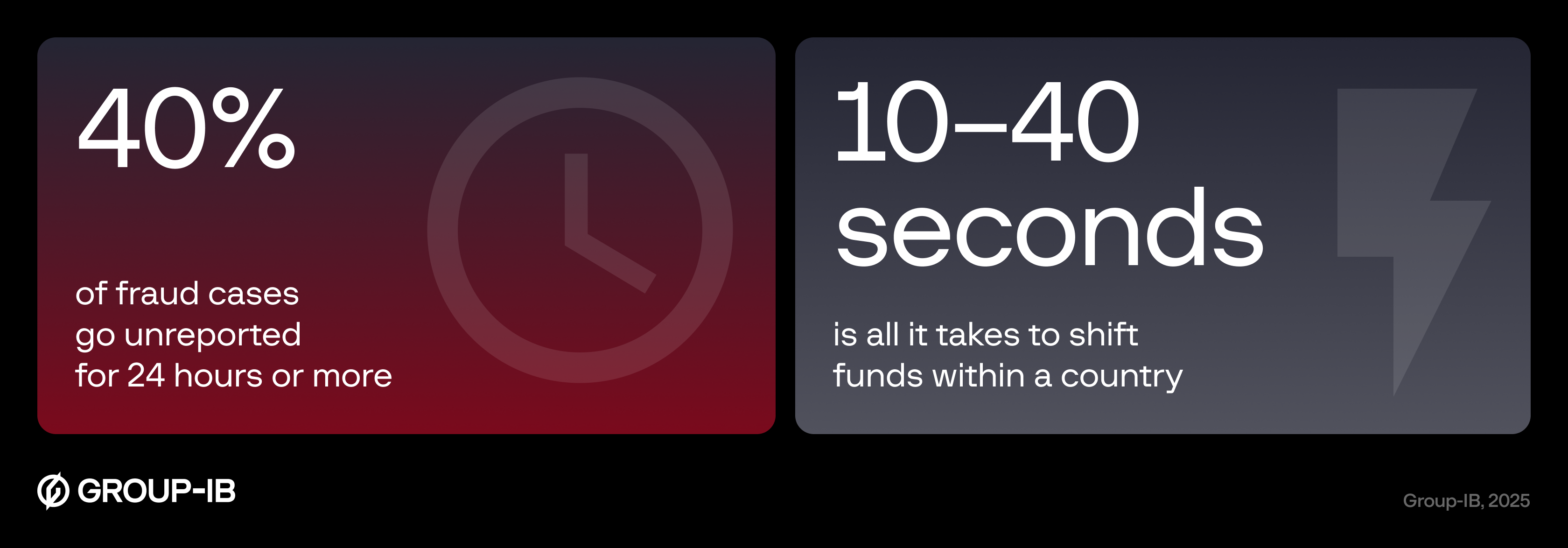
This window of vulnerability keeps shrinking. Real-time payment systems give criminals just 10–40 seconds to move funds out of reach. Yet despite consistent efforts to tighten controls, APP fraud continues to grow. Losses are expected to reach USD 7.6 billion by 2028. Meanwhile, regulators are increasing pressure on institutions to protect customers and ensure accountability. The UK Payment Systems Regulator, for instance, has introduced mandatory reimbursement for APP fraud victims. GDPR enforcement has also been severe, with a €225 million fine against WhatsApp for transparency failures and a $1.3 billion fine against Meta for EU data protection breaches.
Meeting the industry’s biggest demand: secure, real-time fraud prevention
For years, fraud and risk professionals across banking, telecom, e-commerce, and gaming have been calling for a way to share fraud intelligence securely and in real time, across institutions, sectors, and borders, while staying fully compliant with strict privacy regulations. That demand can now finally be met.
Group-IB’s Cyber Fraud Intelligence Platform provides the infrastructure that makes real-time, secure fraud intelligence sharing possible for the first time. Organizations can exchange risk signals instantly without exposing sensitive data, bridging the long-standing gap between speed and compliance – a challenge made even harder by the rise of instant payments and data protection frameworks such as GDPR.
Fraud prevention tools have evolved significantly in recent years. Account name verification services help catch basic impersonation attempts. Transaction monitoring systems flag unusual patterns. Multi-factor authentication confirms customer identity. Yet fraudsters adapt their social engineering tactics to account for these controls – providing plausible explanations for mismatches, staying within “normal” transaction limits, or simply convincing victims to authorize the payments themselves.
The fundamental limitation isn’t any single tool – it’s that these systems work in isolation. A bank’s fraud detection might flag an account receiving multiple inbound transfers, but it has no way to know if dozens of other victims at different banks are also sending money to that same mule account. By the time the fraud is confirmed and reported through traditional channels, the money has already moved through other institutions and the funds have been withdrawn, transferred abroad, or converted to cryptocurrency. At that stage, the funds are beyond recovery.
Institutions are caught between protecting customers and maintaining smooth payment experiences. Stopping every single unusual payment frustrates legitimate customers, but allowing suspicious transactions enables fraudsters to commit their crimes.
What’s more, data protection rules prevent early information sharing. Hashing methods do not meet GDPR pseudonymization standards because the data can still be traced back to individuals. The rollout of ISO 20022 makes this risk even greater as standardized payment fields are easier to match and re-identify. As a result, organizations are limited to sharing fraud information only after it has been confirmed, which means that every response is essentially a post-mortem.
Against this backdrop, is it even possible to predict and prevent fast-payment fraud under strict regulations across borders and multi-entity groups?
From reactive to proactive
Fraudsters typically spend 4-8 weeks preparing mule accounts before deploying them in attacks: building transaction histories, establishing patterns of legitimate activity, and warming up the accounts to avoid triggering basic fraud detection systems. Traditional fraud prevention only acts after confirmed losses, meaning this entire preparation phase goes undetected.
Cyber Fraud Intelligence Platform changes this timeline. By enabling participants to share suspicious signals – unusual account behaviors, suspicious device patterns, anomalous transaction velocities – already during the warm-up period, institutions can identify and neutralize mule networks weeks before they’re deployed in attacks.
Cyber Fraud Intelligence Platform is a sector-neutral solution designed for collaborative cyber fraud intelligence. It works across a variety of sectors, including banking, telecom, e-commerce, and gaming, by pseudonymizing identifiers and sharing risk signals without exposing customer data.
The enabler is Distributed Tokenization, Group-IB’s patented technology that converts sensitive identifiers into irreversible tokens. The tokens can be matched across institutions to identify shared risks in real time, without ever revealing any underlying customer data. Within milliseconds, an institution can verify whether other members of the network have also flagged the same account, device, or customer as suspicious. This correlation allows participants to act with confidence and stop fraud before funds are lost.
The first pilots have delivered measurable results. In one deployment, 46 banks and payment providers joined the platform. As active participation grew, monthly reports on fraudulent cards increased fivefold over six months (from 815 to 4,073), creating a rich, real-time database of high-risk accounts.
The network’s true power emerged when just two institutions – representing only 5% of participants – began performing real-time checks. These early adopters conducted approximately 180,000 checks daily, identifying and stopping between 300 and 400 transactions destined for mule accounts already reported by other participants. Based on conservative estimates, this activity prevents $10–15 million in fraud annually. With full participation from all 46 members, projected savings could reach $100–300 million per year from this single use case alone.
Why Distributed Tokenization outperforms current encryption protocols in the fight against fraud
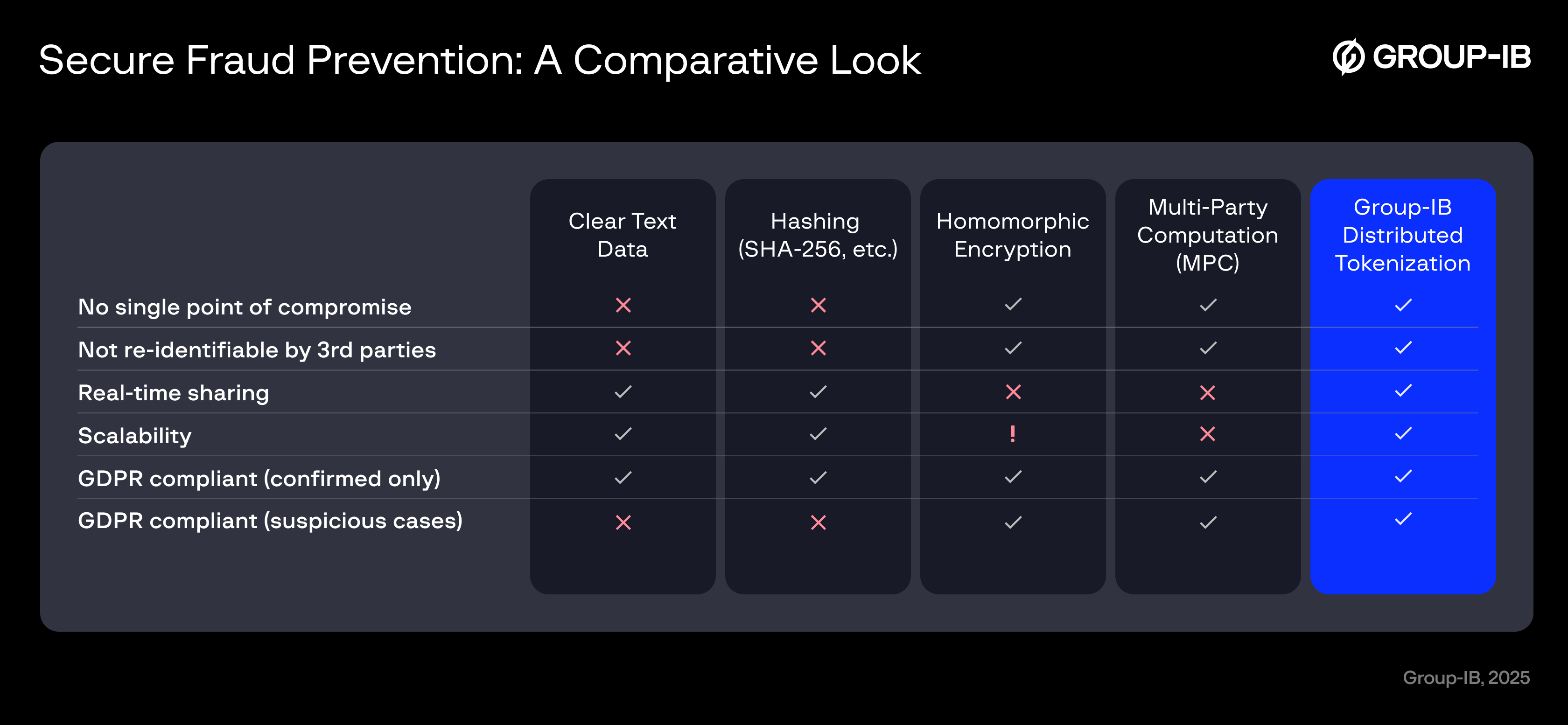
The platform’s Distributed Tokenization enables organizations to cross-check suspicious accounts in real time without exposing sensitive data. Each organization generates the same irreversible token for a given identifier, which allows fraud patterns to be identified across the network while raw information never leaves local systems. This ensures both collaboration and GDPR compliance, as verified by Bureau Veritas.
| Concern | Hashing | Group-IB Distributed Tokenization |
| Privacy | Deterministic; identical hashes can be linked or reversed | Patented multi-step salting and hashing produces irreversible tokens |
| Compliance | Fails GDPR pseudonymization standards; high risk of re-identification | Verified as GDPR-compliant by Bureau Veritas; “data protection by design” |
| Fraud sharing | Limits collaboration to confirmed fraud cases | Enables real-time sharing of suspicious signals across banks |
| Cross-border collaboration | Unsafe under ISO 20022 as data fields are predictable | Securely aggregates anonymized threat data across jurisdictions |
| Operational model | Siloed, institution-only detection | Supports organizations across many sectors, consortia, and regulators through neutral hubs |
Predictive intelligence across fraud scenarios
Predictive collaboration connects dots that are invisible in isolation:
Prevention of invoice and CEO fraud: When criminal organizations launch business email compromise campaigns, they often impersonate executives across several companies at the same time. Traditional systems might see one suspicious wire transfer request… Meanwhile, the collaborative network reveals dozens of similar “CEO” payment requests across different institutions to the same recipient accounts, predicting the full scope of the campaign and enabling preemptive protection for additional targets.
Detection and prediction of investment scams: Cryptocurrency and forex investment scams usually involve multiple victims sending money to the same fraudulent trading accounts. With the Cyber Fraud Intelligence Platform, this account can be cross-checked instantly against other banks’ signals. If multiple institutions have also flagged the recipient as suspicious, the account is identified as a likely mule. This shared intelligence allows banks to stop or delay transfers and, crucially, predict that more victims are likely to be targeted through the same account.
Intervention in romance scams: When criminals launch romance scam campaigns targeting hundreds of victims, the system identifies the coordinated nature of the attack as payment requests begin converging on fraudulent accounts. Instead of waiting for victims to file reports days later, the network predicts the next targets and how the timeline will unfold, enabling preemptive protection.
Detection of purchase scams: Fake marketplace and classified advertisement scams often involve the same fraudulent seller accounts receiving payments from multiple victims across different banks. The system predicts which new payment requests are likely to be part of ongoing scam operations and helps prevent additional victims from completing transfers.
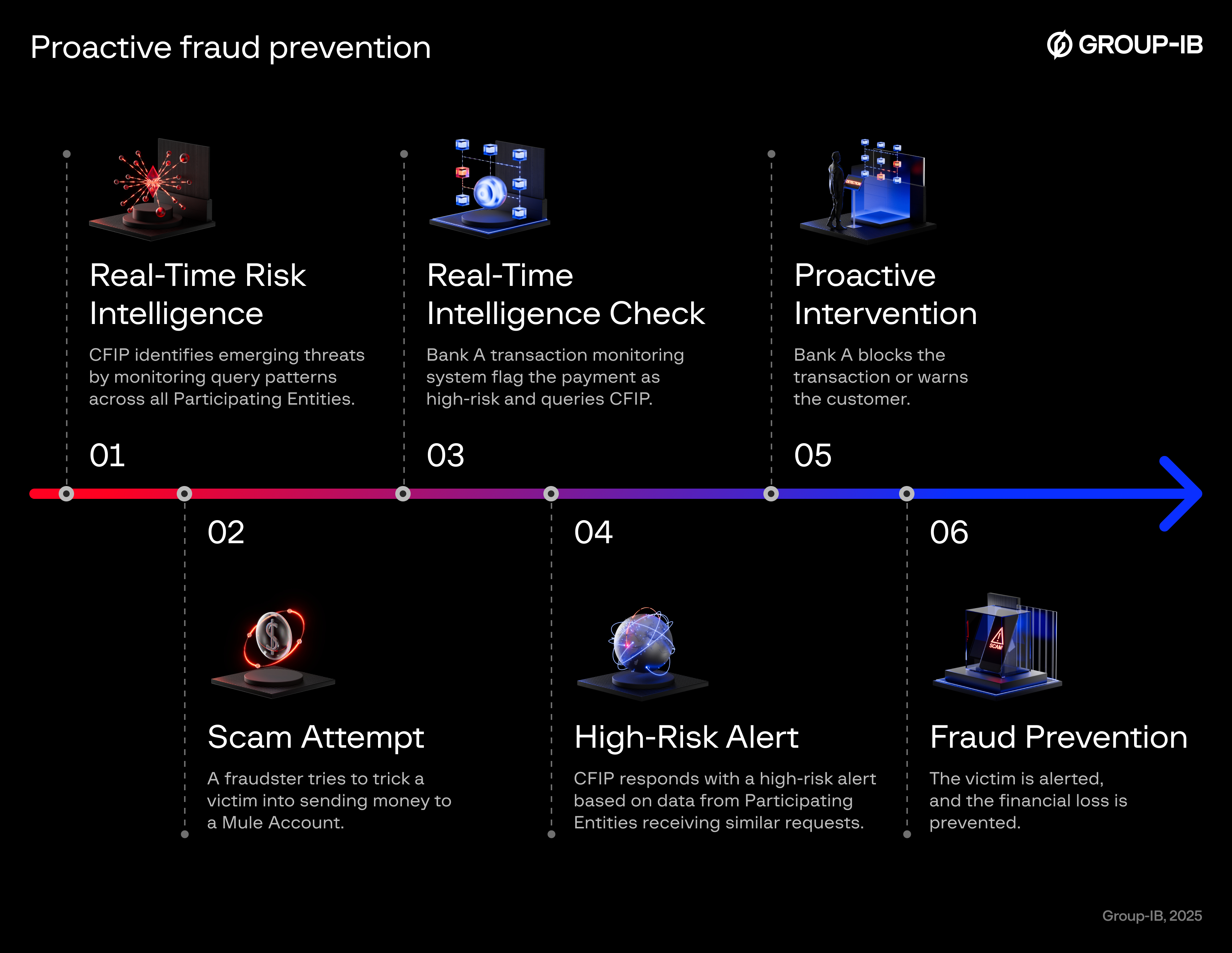
Identification of money mules: Mule networks are the backbone of APP fraud. Our platform analyzes suspicious signals across all participating entities (account activity, transaction velocity, device fingerprints) and matches them in real time. If Bank A sees unusual inflows into an account, it checks against the network. If Banks B and C report similar inflows, the system correlates the activity and flags the account as a potential mule node. The early warning allows institutions to block the transaction, warn their customers, or freeze accounts before they can be fully exploited.
The approach extends beyond payments to other critical areas, namely:
Loan application fraud: Cross-lender intelligence sharing makes it possible to predict fraudulent applications using synthetic identities or stolen credentials before approval decisions are made.
Prevention of account takeover: Behavioral patterns and device intelligence predict which accounts are likely to be compromised based on session data shared across institutions.
Detection of deepfake identities: Cross-institutional KYC intelligence identifies AI-generated fake identities during onboarding rather than after fraudulent activity has already begun.
Network effects across borders and sectors
The platform extends beyond the APP fraud and mule account scenarios described earlier. As the network’s size and diversity grows, so does the platform’s power. While individual institutions only see fragments of criminal operations, collaborative intelligence reveals the complete picture.
The platform’s architecture adapts to different regulatory environments, jurisdictions, and enterprise formats.
- Large banking groups can deploy it internally across subsidiaries to predict fraud patterns across global operations while maintaining data sovereignty compliance.
- Under consortium models, competing institutions can exchange predictive intelligence by cooperating through a neutral industry association, which hosts the platform on behalf of all participants.
- Regulatory authorities can host processing hubs under custodianship models, gaining systemic visibility into fraud flows without handling raw customer data.
- Cross-jurisdictional deployments are enabled by Distributed Tokenization, which ensures compliance under different privacy regimes.
The same model applies beyond banking. Telecommunications operators use it to predict and prevent SIM swapping attacks, e-commerce platforms use it to anticipate promotion abuse campaigns, and gaming companies use it to identify account farming operations before they can grow in scale. Each vertical contributes to – and benefits from – the predictive intelligence network.
Deploy in weeks, keep your stack
The Cyber Fraud Intelligence Platform is designed to integrate, not replace. Its microservice architecture and lightweight agents connect seamlessly with existing fraud prevention environments. Deployment takes weeks, not months, which means not having to deal with the long IT projects that typically slow adoption.
The approach is also vendor-agnostic. Institutions can continue using their existing monitoring and detection systems, while the Cyber Fraud Intelligence Platform enriches them with predictive intelligence from across the network. No vendor lock-in is introduced at any point and no large-scale replacement of current systems is required.
Once deployed, the same infrastructure supports new use cases without reintegration, which reduces future integration costs and ensures scalability. The platform is also ISO 20022-ready and designed with irreversible tokenization, which ensures longevity even as payment systems evolve.
Join the fight against fraud
Fraudsters are already exploiting artificial intelligence, fraud-as-a-service platforms, and global mule networks to scale their schemes. They collaborate across borders. Meanwhile, most institutions remain scattered and reactive.
The Cyber Fraud Intelligence Platform establishes a new standard: predicting and preventing fraud across sectors while protecting privacy and meeting regulatory demands. Each new participant strengthens the network, compounding its predictive power.
Participants gain the ability to recognize coordinated fraud campaigns in their earliest stages, become confident that privacy rules are respected, and strengthen customer trust by reducing the likelihood of large-scale scams. The network also creates a collective advantage: the intelligence that one participant contributes becomes protection for all. Early adopters gain immediate access to more than 60 live sources of Group-IB’s fraud and threat intelligence, which extends their visibility from day one.
You can also be part of the global network with Group-IB’s Cyber Fraud Intelligence Platform. Work together securely, stop fraud in real time, and stay compliant with the world’s toughest data protection standards.
Would you like to learn more about our Cyber Fraud Intelligence Platform?
Work together securely, stop fraud in real time, and stay compliant with the world’s toughest data protection standards.