
Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.


For cyber criminals, email gateway is an ideal attack vector because they can bypass traditional email security systems with relative ease, putting organizations at serious risk. Once a single corporate email account is breached, the entire organization is vulnerable. That’s why secure email gateways are a crucial defense for locking cybercriminals out of your system.
As cyberattacks become increasingly sophisticated, your organization needs to implement email security best practices for protecting email accounts and preventing damaging data breaches, financial losses, and legal risks.
Group-IB Business Email Protection leverages patented technologies and industry-leading threat intelligence to detect, block, and analyze all email-borne attacks, from spam and phishing attempts to malware delivery and business email compromise (BEC) attacks.
Business Email Protection provides an advanced feature set that supplements legacy email security systems and the built–in security controls offered by third-party email providers.

Inspect over 290 different file formats to ensure all attachments are safe. Check all links, including obfuscated and redirected links with Group-IB Business Email Protection

Recursively analyze suspicious URLs, attachments, and objects that can change state over time to discover hidden threats that other solutions miss

Outfox sophisticated malware designed to recognize sandboxes by using a customizable detonation platform that replicates your real environment

Reverse engineer malware to understand who might be targeting your organization and how to be prepared for what might be coming next

Cross-check detonation reports with Group-IB’s intelligence library to attribute attacks to specific threat actors or malware families

Get to full deployment quickly and easily with a SaaS corporate email protection solution that secures email whether it’s hosted internally or with a 3rd party provider
Instantly test your current defenses with Group-IB’s free and automated email security assessment tool.
Stop phishing attacks that attempt to trick users into downloading malware or providing credentials
Ensure all email attachments are secure and check all links sent via email to block any malicious or fraudulent sites

Protect your organization from BEC and the resulting fraud damages with intelligence-driven technology
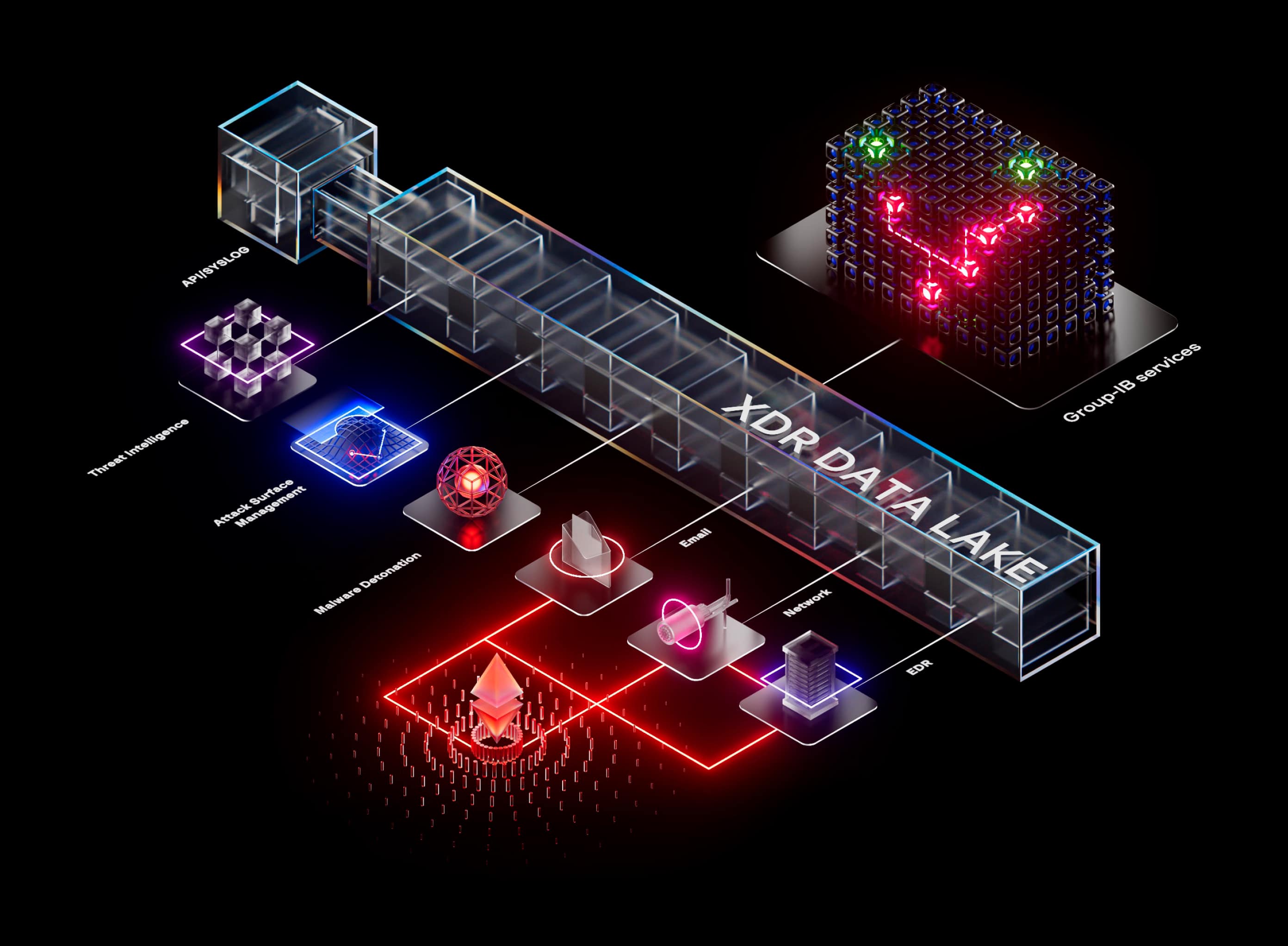
Group-IB Business Email Protection is one component for our Managed XDR solution, which identifies threats in real-time to enable immediate response actions. Protect your infrastructure, servers, network, and endpoints with Managed XDR.
Graph
Business email protection encompasses a set of security solutions designed to secure organizational email systems against threats such as phishing, malware, and unauthorized access. Key components of email protection include email encryption, spam filters, anti-phishing tools, malware protection, authentication protocols, and more. These tools and practices help safeguard data and networks while enabling compliant email communications.
Email is the central part of communication in an organization, making it an attractive attack surface for cybercriminals. As many users continually fall for email scams, information technology officers must leverage a layered approach using multiple defenses for robust business email security and to stay ahead of evolving criminal tricks. The following are common attacks that compromise email security for businesses.
Fraud: Implementing strong enterprise email security measures can help avoid email fraud schemes targeting individuals and organizations. Through sophisticated deceptive tactics, fraudsters craft emails to manipulate recipients into detrimental actions. Criminals impersonate trusted authority figures and exploit human psychological weaknesses to make urgent demands.
Malware: Emails are often an ideal channel that cybercriminals use to take control of an organization’s system by sending URLs or malicious links as malware to infiltrate and access sensitive data. The costly result is damaging a system, encrypting other essential files, and demanding a ransom to restore, which can halt operations. Installing antivirus software on your employees’ devices helps protect the company’s email system and data from malicious attachments and links.
Phishing: Most business email security breaches are the result of a phishing attack. Through phishing emails, employees click links and download infectious attachments, enabling cybercriminals to steal credentials that facilitate deep network intrusions.
Email interception: With email interception, criminals gain unauthorized access to a personal or business email account, allowing them to impersonate the owner. They then spy on messages, read sensitive information, or collect confidential data and business plans, financial information, intellectual property, and personal details.
Account takeover: Without proper email security for businesses, hackers gain unauthorized access to email accounts through stolen credentials obtained from the dark web, password cracking, malware, and other forms of compromised email security. The motivation is typically financial gains, obtaining valuable private data for misuse, and leveraging compromised accounts to anonymously spread their cybercrimes for profit.
Use Group-IB’s simple self-assessment tool to identify potential weaknesses in your current email security.
Most cloud-based email solutions use sandboxes with generic images, traffic routes, usernames and other parameters that are trivial for attackers to circumvent. Business Email Protection utilizes highly customizable virtual machines that appear to attackers to be real environments. Group-IB Business Email Protection solution also reanalyzes objects that may change their state over time, blocking them if they become malicious.
Business Email Protection can be set up in minutes; a cloud tenant is set up automatically after your trial request is approved. Integration is very simple and implemented as a gateway solution. Simply configure your domain name and Business Email Protection will start providing protection the moment DNS records are updated.
To further improve detection and response, Group-IB supports API-level integration between Business Email Protection and popular productivity tools like G-Suite and Office 365.
To provide flexibility Business Email Protection can be deployed in the cloud or on-premises to provide security for email services hosted in any location.
To deliver cutting-edge email protection in accordance with local regulations, Group-IB Business Email Protection is available in four different regions:
Business Email Protection is a full-featured corporate email security solution that includes following protection tracks:
Group-IB Business Email Protection uses:
Today’s work dynamics are shifting, requiring businesses to make infrastructural adjustments conducive to remote work. When it comes to enabling protection, it is often not a question of choosing between the alternatives - on-prem protection, cloud email protection, or sourcing it to a 3rd party vendor: but concurrently adopting all to ensure maximum flexibility and efficiency.
Email remains the number #1 attack vector for modern businesses. Therefore, having an email gateway with anti-phishing and anti-spam email protection isn’t enough. Choose an advanced business email protection solution against impersonation attempts, malicious URLs, ransomware, and other targeted attacks.
Ensure your security is well-rounded with Group-IB’s Business Email Protection – an intelligence-driven solution that can be SaaS, self-hosted in the cloud, or hosted in a fully isolated, on-prem installation, and fully deployed in just a matter of hours!
In addition to its features, Business Email Protection is an essential component of Group-IB’s next-gen, comprehensive security solution – Managed XDR, which is designed to enable multi-layered protection on all fronts – endpoints, servers, cloud workloads, emails, and networks.
Also, explore our fraud prevention solution and digital risk protection service, and learn more about our unified cybersecurity platform for a multi-pronged approach to security.