Since RaaS was first identified in 2012 with the Reveton ransomware strain, it has made it easier for criminals that lack the technical expertise to launch high-impact attacks by using ready-made tools developed by more skilled operators.
RaaS affiliates are a major source of concern for businesses and organizations, as they have contributed to the proliferation of ransomware attacks in recent years. In fact, Group-IB’s investigations in 2024 revealed a 44% increase in dark web ads seeking affiliates for RaaS services compared to 2023.
In this article, we dive into what RaaS is, how it works, its history and evolution, its global impact on organizations, strategies to prevent ransomware attacks, and trends for 2025 and beyond.
What is Ransomware as a Service (RaaS)?
Ransomware-as-a-Service, or RaaS, is a “subscription-based” cybercrime in which ransomware creators lease or sell their malware to affiliates who then use it to execute attacks.
Hackers are able to profit from extortion without having to develop the malware themselves, while ransomware developers can increase their profits by reaching victims they might never have found on their own. Consequently, what started as a niche tactic has now grown into a full-blown industry with dedicated leak sites (DLS), sophisticated affiliate networks, and evolving extortion techniques.
Think of RaaS as a malicious variation of software as a service (SaaS). RaaS kits are available on the dark web and work much like legitimate SaaS products; complete with 24/7 support, bundled offers, user reviews, and forums. These kits are accessible and affordable, costing anywhere from a few hundred to several thousand dollars a month.
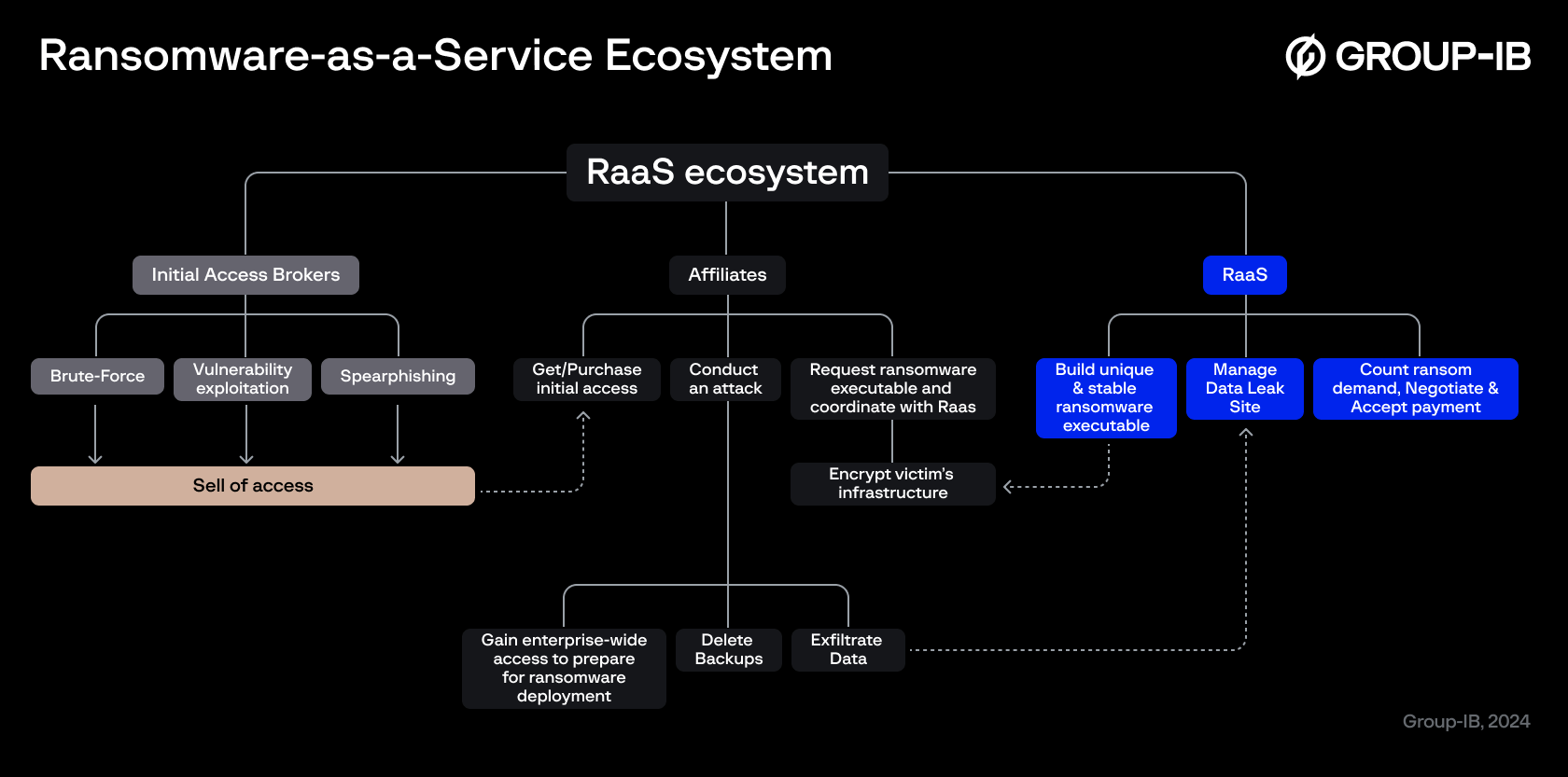
Group-IB has been actively investigating and tracking ransomware groups, and the following is an illustration of a typical RaaS ecosystem.
How does Ransomware-as-a-Service work?
RaaS operates on the dark web, where malware developers — also called RaaS providers or RaaS groups —provide ransomware tools, infrastructure, and related services to cybercriminals (also known as RaaS affiliates).
In order to better distribute their malware, these developers carry out affiliate programs (an increasingly popular trend) where they can expand their reach and carry out more attacks than they could on their own.
Here’s how a typical ransomware-as-a-service affiliate program works:
- Once the malware is developed, the multi-end user infrastructure is created which includes command-and-control servers, payment portals, and other necessary components.
- The RaaS group may advertise their services on popular dark web forums and may also run affiliate advertisements for interested attackers or groups to sign up and receive access to the RaaS tools and infrastructure. Special underground platforms make ransomware attacks more accessible to a wider range of cybercriminals as they don’t need to write their own code for the malware — it can be completely ordered.
- A Ransomware-as-a-Service affiliate program may include different levels of membership, with different fees and commissions for the affiliate. Each new affiliate is given a custom exploit code to deploy the ransomware attack.
- RaaS affiliates present victims with these links, through phishing attempts, social engineering tactics, etc. When a link is clicked, victims are taken to the exploit site where the ransomware is downloaded. The affiliate in turn earns a commission on any ransom payment made by the victim, and a part of the payment also goes to the RaaS operator and distributor.
- Ransomware operators usually first publish a small amount of data to show the scope of the attack and promise to delete the data after the ransom is paid. The affiliate in turn earns a commission on any ransom payment made by the victim, and a part of the payment also goes to the RaaS operator and distributor.
- Upon payment, the attackers are supposed to provide a decryption tool to unlock the files. If the victim refuses to pay by the deadline, the attackers typically publish the stolen data on their leak site. However, there have been cases where the links that lead to compromised files located on servers used by other hackers remain available even after the demand is met.
- Successful affiliates will often repeat the process on new victims, reusing the RaaS platform for multiple attacks. They may share tactics on criminal forums or with the core operators to improve the “product.” The RaaS operators, on their side, continually update the ransomware code (to evade antivirus, add features, etc.), handle the backend infrastructure (like maintaining the Tor sites, payment wallets, and sometimes a decryptor helpdesk), and recruit more affiliates via darknet forums.
Although this is how RaaS is usually carried out, ransomware groups are increasing the stakes by demanding higher ransoms and reinventing their approaches. An example is the double extortion technique, where data is both encrypted and threatened with public release. The gangs – Snatch and Maze were the first to use the double extortion technique. The technique involves both encrypting the victim’s data and publishing it on a Dedicated Leak Site (DLS).
This profit-sharing “franchise” model has proven highly effective and scalable, which is why dozens of RaaS affiliate programs exist today, ranging from big names like LockBit to emerging groups like RansomHub. This approach means that even if one affiliate is caught or one sub-group shuts down, the Ransomware-as-a-Service operation as a whole continues with others – making it a resilient threat model.
Group-IB monitors hundreds of ransomware groups, analyzing their malware, extortion tactics, and tools. We have collected ransom notes from the most active ransomware groups in 2024 to help you stay vigilant and prepare for potential threats.
A growing threat: Ransomware-as-a-service statistics
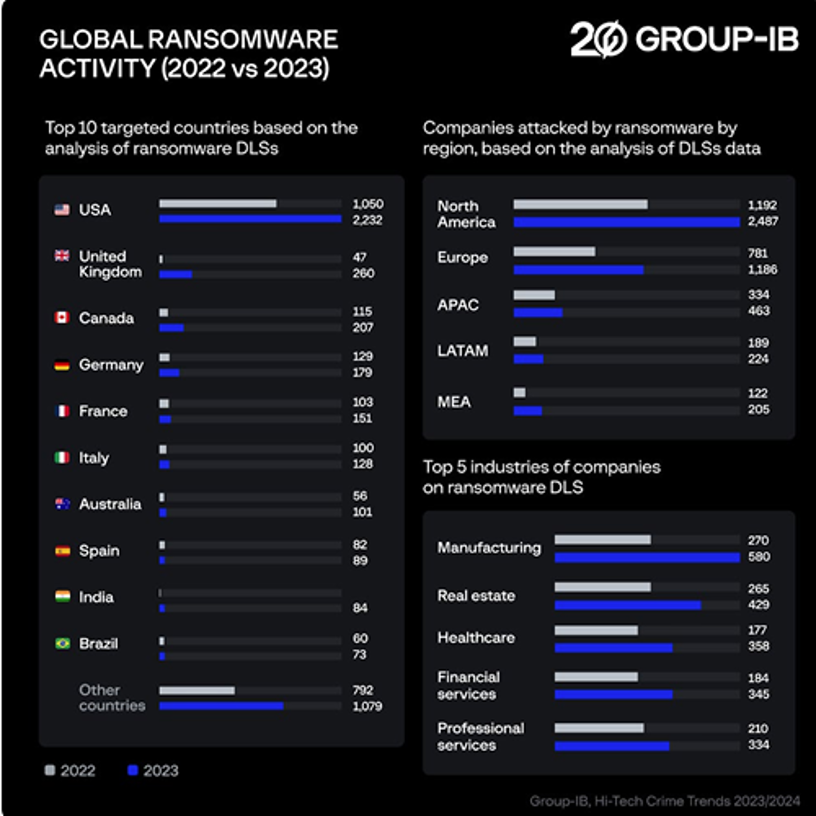
To identify trends in ransomware attacks, Group-IB experts have been analyzing DLSs where attackers publish stolen data when victims refuse to pay.
Global RaaS statistics reveal alarming figures, showing that ransomware attacks have surged across different countries and industries. Our analysis in 2023 found that 83% of ransomware cases involved data exfiltration. We also found a staggering 74% increase in ransomware attacks compared to 2022, totaling 4,583 attacks published on DLSs.
Our latest data shows that ransomware incidents increased by 10% globally in 2024 compared to the previous year. In 2024 alone, 5,066 ransomware incidents resulted in data leaks on Dedicated Leak Sites (DLS), a stark indicator of how many victims fell prey to RaaS extortion.
It’s worth noting that the total number of ransomware attacks worldwide is likely to be much larger, with instances of organizations paying the ransom or those deciding not to go ahead with their threat of publishing data on a DLS.
The following is a list of the top five ransomware groups by number of attacks globally in 2024. While LockBit carried out the most attacks, RansomHub was most active consistently throughout the year.
| RaaS Group | Number of attacks |
|---|---|
| LockBit | 673 |
| RansomHub | 548 |
| Play | 348 |
| Akira | 333 |
| Hunters International | 233 |
For the latest Ransomware-as-a-Service statistics, download Group-IB High-Tech Crime Trends Report 2025 which covers emerging cyber threats, tactics, and their impact on global security.
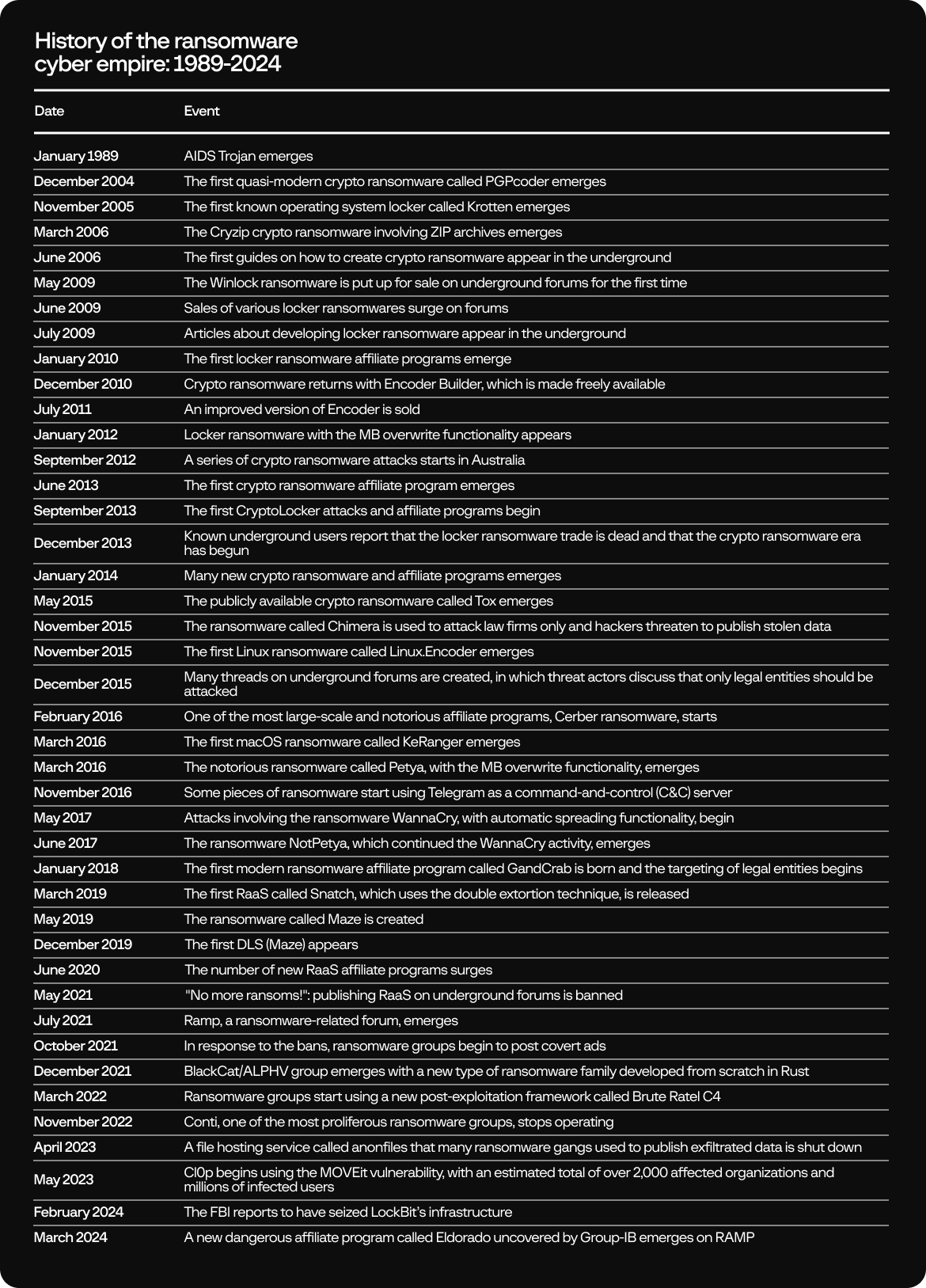
History of RaaS
Towards the end of the 2000s, threat actors decided to adopt a simpler approach: blocking certain operating system functionalities and demanding a ransom. This marked the beginning of the WinLock era, which brought forth a phenomenon known today as “ransomware as a service” (RaaS).
The year 2010 saw the appearance of malware developers who realized that developing, improving, and distributing Trojans all at the same time is challenging, so they started paying third parties for traffic generation and malware downloads to victim machines. To optimize their activity, they created the first affiliate program prototypes, which all modern RaaS model services later adopted and improved upon.
The evolution of RaaS with a definitive timeline is described below:
-
- April 2024: Japanese optics manufacturer Hoya was hit by the Hunters International Ransomware-as-a-Service group. Production systems and ordering platforms were disrupted, and attackers claimed to have stolen ~1.7 million files (~2 TB of data). A $10 million ransom demand was issued via the gang’s leak site.
-
- May 2024: Ascension (one of the largest U.S. healthcare networks) suffered a ransomware attack by the Black Basta RaaS group, forcing hospitals to divert ambulances and revert to manual processes.Despite a global law enforcement takedown of its infrastructure just months prior, the LockBit 3.0 RaaS gang launched 176 attacks in May 2024 alone, accounting for 37% of all recorded ransomware incidents that month – an astounding 665% increase from the previous month. This surge underscored the resilience of the RaaS model, as LockBit’s affiliates quickly resumed operations post-disruption.
- June 2024: A ransomware group believed to be Qilin (a Russian RaaS gang) targeted Synnovis, a UK pathology services provider for major London hospitals, with a $50 million ransom demand. The attack affected critical blood transfusion services, underscoring the threat to healthcare infrastructure and essential medical services.A new RaaS player called Cicada3301 emerged. Between June and October 2024, Cicada3301 leaked stolen data from 30 victim organizations via its dark web leak site, with the majority of victims in the US and UK. Group-IB investigators recently gained access to the Cicada3301 ransomware affiliate panel, revealing insights into the RaaS group’s operations as it gained traction.An Indonesian data center was compromised by a major ransomware attack causing outages in government services and immigration systems. The threat actor, Brain Cipher, published the decryptor for free after initially demanding a ransom of $8 million. Brain Cipher ransom notes were found in connection with LockBit malware samples. Attacks with similar ransom notes were carried out in July 2024 under the name RebornRansomware.
- July 2024: The City of Columbus, Ohio, was targeted by the Rhysida ransomware group resulting in the personal information of over 500,000 current and former residents being compromised. The attack further highlights the potential for large scale government data breaches with consequences for residents.
-
- August 2024: Beverage producer Stoli Group (maker of Stolichnaya vodka) suffered a crippling ransomware attack. The company’s ERP and accounting systems failed, forcing all internal processes into manual mode. Unable to issue financial reports or service a $78 million debt due to the IT outage, Stoli’s subsidiaries ultimately filed for bankruptcy in December 2024. This incident showed how RaaS attacks can directly lead to severe financial distress or insolvency for businesses. No ransomware gang has taken credit.
-
- October 2024: Japanese electronics giant Casio announced unauthorized access to its network in October. The Underground RaaS group (linked to the Russia-based RomCom cybercrime group) claimed responsibility, leaking confidential data (including R&D documents, employee personal info, legal and financial records) on its site. Notably, Casio stated it did not pay any ransom and was able to restore most services by early 2025 – highlighting that some victims are choosing recovery and disclosure over ransom payment.
-
- November 2024: An atypical target, Italian Serie A football club Bologna FC, fell victim to ransomware in November. The RansomHub RaaS gang claimed the attack, and when the club refused to pay, RansomHub leaked a trove of stolen data. Leaked files reportedly included sponsorship and transfer contracts, the club’s entire financial history, player medical records, personnel data, and even confidential fan information. The incident demonstrated RaaS groups are expanding their targets beyond traditional industries.
- December 2024: The highest monthly volume of global ransomware attacks ever recorded occurred in December 2024. Artivion, a global supplier of cardiac surgery tissue and equipment, disclosed a ransomware attack had compromised its IT infrastructure. Some systems were encrypted and data stolen, causing “disruptions to order and shipping processes” for life-saving medical supplies. While no ransomware group has claimed responsibility for the Artivion breach, the attack highlights ongoing RaaS threats to the healthcare supply chain, not just hospitals.
Our recent article, “RansomHub Never Sleeps Episode 1: The evolution of modern ransomware” explores how ransomware has evolved into a sophisticated cyber threat, with groups like RansomHub leading the charge. Learn more about their adaptability, TTPs, and the rise of Ransomware-as-a-Service in this first-of-three-part trilogy.
Impact of Ransomware-as-a-Service on businesses and individuals

In 2024, manufacturing, real estate, professional services, and healthcare were frequently targeted worldwide.
Ransomware-as-a-Service attacks cause multifaceted harm to businesses and individuals – combining the worst aspects of cyber extortion and data breaches, with consequences ranging from financial loss to public safety.
On top of massive ransom payment figures, lost productivity and the recovery time required to get IT systems running and back to normal operating levels are significant expenses incurred by organizations in the aftermath of a ransomware attack.
As 83% of ransomware cases involve data exfiltration, organizations must treat them not only as malware incidents but as major data breaches. Confidential data – customer information, intellectual property, financial records – can be leaked publicly if a ransom isn’t paid, or sometimes even if it is. Moreover, leaked personal data from a ransomware attack can lead to identity theft or fraud against individuals down the line.
For businesses seeking to enhance their cybersecurity stance and boost resilience against ransomware attacks, we highly recommend reviewing our Ransomware Readiness whitepaper.
Forecasts for RaaS: 2024 and beyond
Since the Cryptolocker ransomware emerged about a decade ago, ransomware operators have grown from small hacker groups to entire corporations.
Ransomware-as-a-Service owners will continue to focus on developing ransomware, creating and optimizing control panels, and laundering money while outsourcing attack-related activities via RaaS affiliates.
However, the exit scams carried out by ALPHV and NoEscape have undermined confidence among ransomware operators, leading to uncertainty within the RaaS community.
We may witness several key trends for 2025 and beyond:
- RaaS dark web ads: in 2024, Group-IB specialists identified 39 ads for RaaS programs on dark web forums – a 44% rise in underground RaaS recruitment efforts compared to 2023, demonstrating the industrialization of cyber extortion.
- Centralization: According to Group-IB High-Tech Crime Trends 2025 report, there were 5,066 attacks that were published on DLSs in 2024, an increase of 10% compared to 2023, during which 4,583 attacks were published. This points to a growing centralization of the RaaS industry within larger, more organized groups that are able to launch greater numbers of attacks.
- Key threat actors: In 2024, Lockbit (with 673 successful attacks), RansomHub, and Play were the most active ransomware groups globally, and they will continue to improve their malware and infiltration techniques. Black Basta became the top ransomware actor in Europe in December while RansomHub and Akira kept their positions as the second and fourth most active ransomware groups in Europe.
- Top geography and industry targets: Most ransomware attacks target US companies, and the trend is likely to continue with manufacturing and real estate sectors considered as top targets. There is also growing concern of an increase in attacks targeting healthcare, critical infrastructure, and governmental entities, as these sectors may be perceived as vulnerable and high-impact targets.
- Diversification in extortion methods: Some RaaS groups may even move away from double extortion to extortion-only attacks, leading to the rise of new ransomware and extortion tactics in 2025, as cybercriminals seek to evade legal scrutiny. Furthermore, the LockBit Ransomware group announced in December 2024 its LockBit 4.0 update and a new affiliate program to be released in February 2025, demonstrating the strengthening of ransomware operational infrastructure and tactics.
- Higher financial stakes: According to data collected by Group-IB, a common strategy used by ransomware actors is to demand ransoms not exceeding 5–10% of the victim’s annual revenue. However, recent high-profile cases, such as the $75 million ransom paid to Dark Angel in 2024, indicate more aggressive tactics with higher ransom payment figures expected in 2025 and beyond.
- RAMP will continue to be the main public community for ransomware gangs. Approximately 60% of new RaaS programs between 2022 and 2023 were advertised on this forum.
- Leaked code and tools: The Ransomware-as-a-Service ecosystem often feeds on leaked source code. When ransomware source code or builders leak (whether via insider leaks or law enforcement releasing keys), it spawns new variants. For instance, the 2022 leak of LockBit 3.0’s builder enabled various copycats to create their own versions and carry out new attacks. Similarly, when Conti’s source code was leaked in 2022, multiple new ransomware strains (like MeowCorp, etc.) emerged from that codebase. Going forward, any leak of a major ransomware’s code could accelerate the rise of new RaaS groups. However, these leaks also allow security researchers to study and develop decryptors for older variants.
- Misuse of artificial intelligence: RaaS gangs are reportedly experimenting with AI to enhance their attacks – for example, using AI tools to craft more convincing phishing lures or even deepfake voices of CEOs to trick employees (a terrifying possibility for social engineering). We might see some ransomware attacks assisted by AI-driven reconnaissance or automated targeting. On a positive note, cybercrime defenders are also employing AI for anomaly detection and leveraging global threat intelligence to predict ransomware campaigns. Learn more about key issues, challenges, and opportunities in the intersection of AI and cybersecurity in our Cybersecurity X AI e-guide.
Legal and law enforcement actions against RaaS
The adoption of the UN Cybercrime Convention in December 2024 represents a landmark step in global efforts to combat cybercrimes, especially Ransomware-as-a-Service attacks.
International collaboration against ransomware, such as the Counter Ransomware Initiative, reinforces global law enforcement efforts to combat ransomware and enhance coordinated responses. The arrests of individuals associated with groups such as Scattered Spider in 2024 emphasizes the importance of this global crackdown.
In 2024, a joint operation by INTERPOL and AFRIPOL, Operation Serengeti, in 2024 resulted in 1,006 suspects arrested in cybercriminal activities across Africa. Operation Synergia II brought together 95 countries to target the entire spectrum of cybercrime infrastructure, including ransomware servers, resulting in dozens of seizures and arrests worldwide. The scale of such operations is unprecedented – 22,000 malicious servers taken down in one sweep.
While many ransomware operators remain in countries without extradition (making arrests challenging), these actions demonstrate that affiliates and unwary operators can be identified and caught. There’s also increased intelligence sharing between cybersecurity companies and law enforcement with Group-IB contributing to eight major law enforcement operations in 2024.
However, the resilience of the Ransomware-as-a-Service threat combined with the emergence of new groups suggests that the threat is likely to evolve in 2025 and beyond. RaaS threat actors are adaptive; when core infrastructure is taken down, affiliates scatter to other programs or lay low until a new variant emerges. We’ve seen gangs fake shutdowns (BlackCat), rebrand under new names, or shift operations to new jurisdictions.
The ongoing challenge for law enforcement is to maintain pressure through coordinated international action, even as RaaS groups find new ways to hide. More importantly, organizations at risk are urged to report ransomware incidents and not quietly pay criminals, because every bit of information can help investigations to dismantle these RaaS networks.
How to prevent Ransomware attacks?
Preventing a ransomware attack is far preferable to dealing with one. Given the growing RaaS threat, organizations should adopt a multi-layered defense strategy.
Here’s how:
- Enable comprehensive protection: Stakeholders need to review/revamp their information security infrastructure and enable multiple-layered defense capabilities.
- Integrate advanced information security abilities: Leverage an advanced, real-time threat detection and response technology that comprehensively covers your infrastructure and assets. Group-IB Managed Extended Detection and Response (MXDR) identifies ransomware indicators across your managed endpoints, email, web, and network, issuing automated responses while your team analyzes further mitigation actions.
- Employee training: educate your employees about the risks pertaining to the organization’s network, assets, devices, and infrastructure. The human factor has always been one of the greatest vulnerabilities. Organizations can prevent employees from making mistakes with regular training and safety awareness checks.
- Control vulnerabilities: do not turn a blind eye to the possible vulnerabilities. Checking your infrastructure annually with a technical audit performance is not only a good habit, but also adds a much-needed protection layer. Infrastructure integrity needs to be monitored repeatedly.
- Never pay the ransom: The main rule in case of an attack, and if your data is confiscated by the offender, is to not pay the ransom. Even if one attacker gives your data back, the other will know about your gullibility and readiness to pay, leading to a possible increase in the number of attacks. Having an Incident Response Retainer ensures your business is best prepared if ransomware strikes. With experienced professionals by your side, you can enable a swift and effective response to mitigate damage, collect forensic evidence, and recover data.
Despite ransomware attacks increasing rapidly, there have been substantial overlaps in the TTPs used by attackers. Businesses can leverage Group-IB’s MITRE ATT&CK® matrix, to analyze the threat actor activity and get expert-approved security recommendations.
Conclusion
The history of Ransomware-as-a-Service shows a cybercrime environment that thrives on the sharing, reusing, and rebranding of tools and source codes, fueling a robust underground market where high-profile victims, infamous groups, and substantial sums of money play central roles.
RaaS groups may continue to grow in sophistication, particularly with the influence of generative AI platforms, which will undoubtedly present a significant challenge for security researchers and cybersecurity firms for years to come. While some RaaS gang takedowns have offered hope, new groups and tactics quickly replace them, keeping organizations and law enforcement on high alert.
Therefore, organizations are encouraged to adopt a proactive, intelligence-driven strategy against ransomware attacks by enabling threat intelligence, security analysis, and penetration testing. These measures will identify vulnerabilities in your infrastructure and possible attack vectors to help avert malicious threats.
Get in touch with Group-IB experts today to secure your business with a full range of ransomware resilience solutions.