Group-IB, a Singapore-based cybersecurity company that specializes in preventing cyberattacks, has detected a database containing over 460,000 payment card records uploaded to one of the most popular darknet cardshops on February 5. Over 98 percent of records were from the biggest Indian banks. The underground market value of the database is estimated at more than USD 4.2 million. The source of this batch currently remains unknown. Upon the discovery of this database, Group-IB has immediately informed the Indian Computer Emergency Response Team (CERT-In) about the sale of the payment records, so they could take necessary steps.
This is the second major upload of payment records related to Indian cardholders registered by Group-IB in the past several months. The first one was reported by Group-IB last October.
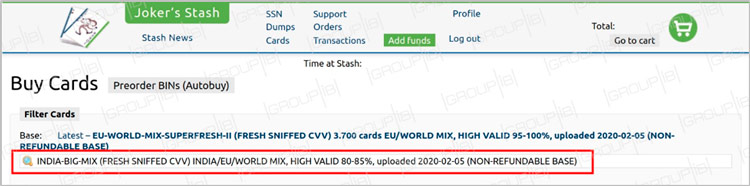
On February 5, a new database under the name “INDIA-BIG-MIX” (full name: [CC] INDIA-BIG-MIX (FRESH SNIFFED CVV) INDIA/EU/WORLD MIX, HIGH VALID 80-85%, uploaded 2020-02-05 (NON-REFUNDABLE BASE) went on sale on the Joker’s Stash one of the most popular underground cardshops.
Fig. 1″INDIA-BIG-MIX” database put up for sale on Joker’s Stash
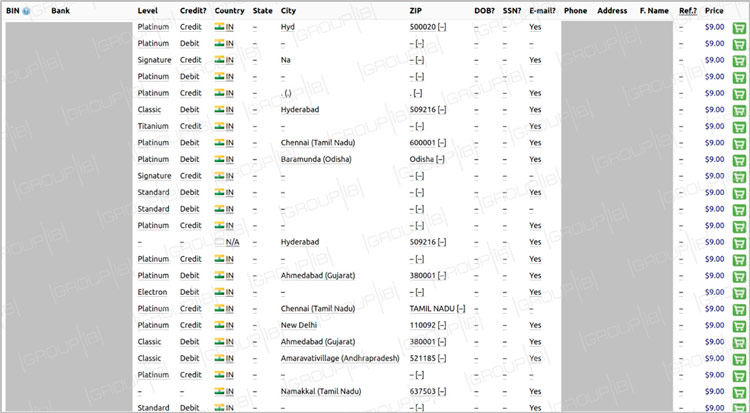
According to Group-IB Threat Intelligence team, the database, comprising 461,976 payment records, in particular, exposed card numbers, expiration dates, CVV/CVC codes and, in this case, some additional information such as cardholders’ full name, as well as their emails, phone numbers and addresses.
Fig. 2 Types of information contained in the database
All the cards from the database are being sold for $9 for piece, with the total underground market value of all the batch standing at $4,157,784. As of morning on February 6, 16 cards were sold out.
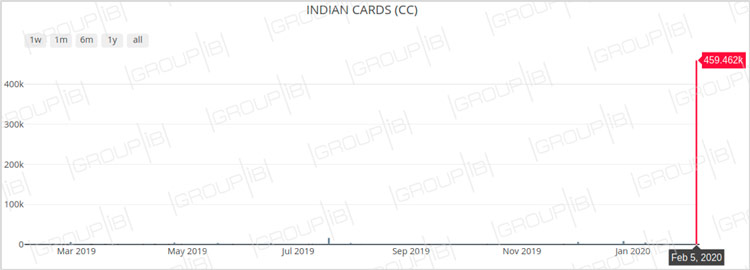
According to Group-IB Threat Intelligence team, this is the only big sale of Indian cards’ CC data detected for the past 12 months, since in the previous India case, card dumps the information contained in the card magnetic stripe were put up for sale. What distinguishes the new database from its predecessor is the fact that the cards were likely compromised online, this assumption is supported by the set of data offered for sale.
Fig. 3 Graph of sale of Indian bank cards CC data on underground cardshops
This is the second major leak of cards relating to Indian banks detected by Group-IB Threat Intelligence team in the past several months. In the current case, we are dealing with so-called fullz they have info on card number, expiration date, CVV/CVC, cardholder name as well as some extra personal info. Such type of data is likely to have been compromised online with the use of phishing, malware, or JS-sniffers while in the previous case, we dealt with card dumps (the information contained in the card magnetic stripe), which can be stolen through the compromise of offline POS terminals, for example. We have shared all the information discovered with our colleagues from CERT-In.

Head of Group-IB сybercrime research unit
On October 28, 2019, Group-IB Threat Intelligence team detected a huge database holding more than 1.3 million credit and debit card records of mostly Indian banks’ customers uploaded to Joker’s Stash. Group-IB experts determined that the underground market value of the database was estimated at more than $130 million. This became the biggest card database encapsulated in a single file ever uploaded on underground markets at once.
According to Group-IB’s “Hi-Tech Crime Trends 2019/2020” report, presented at CyberCrimeCon’19 in Singapore last November, the size of the carding market rose by 33 percent and totaled USD 879.7 million in H2 2018 H1 2019 year-on-year. The sale of CC data is also on rise today, having grown by 19 percent in the corresponding period.
One of the reasons behind the carding market boosting were the activities of JS-sniffers, which enable their operators to steal payment card data from ecommerce websites. This threat can hardly be underestimated: the APAC region has recently seen its first arrest of JS-sniffers’ operators, who stole payment card data with the help of GetBilling JS-sniffer family. The arrest came as a result of a joint operation of Group-IB with INTERPOL and Indonesian police.