Get 24/7 incident response assistance from our global team
- APAC: +65 3159 4398
- EU & NA: +31 20 890 55 59
- MEA: +971 4 540 6400
- LATAM: +56 2 275 473 79
Get 24/7 incident response assistance from our global team
Please review the following rules before submitting your application:
1. Our main objective is to foster a community of like-minded individuals dedicated to combatting cybercrime and who have never engaged in Blackhat activities.
2. All applications must include research or a research draft. You can find content criteria in the blog. Please provide a link to your research or research draft using the form below.

Join over 500 million users already empowered by Group-IB’s fraud protection solution
across banking, payment, and e-commerce applications.
Our online fraud protection platform uses global fraud intelligence, device fingerprinting,
and behavioral analysis to detect even the most sophisticated forms of fraud.

$1.026 trln stolen by fraudsters in 2023, which is 1.05% of the global GDP
In 2022, bots represented 47% of internet traffic, 30.2% of it was malicious
Fraudsters exploit AI's capabilities in social engineering, data analysis, automation, and content generation to craft sophisticated scams and bypass security measures
With Group-IB Fraud Protection service, you’ll have a powerful ally to ensure fraud never makes it past your front door.

Protect your business and stay ahead of new tactics with advanced detection across your digital channels.

Block a wide range of fraud attempts and identify risk patterns early with automated threat response.

Keep genuine user interactions smooth and secure with adaptive risk scoring while reducing false positives.

Leverage the automated defense systems to combat AI-driven attack frameworks.
Lower fraud losses and operational costs. View the Total Economic Impact™ (TEI) of Group-IB Fraud Protection platform for a client migrating from a legacy anti-fraud solution.
Create unique device fingerprints based on a combination of both constant (hardware) and variable (software) parameters
Utilize canvas and WebGL fingerprinting techniques to generate highly distinctive browser fingerprints for accurate device tracking
Connect multiple device IDs to a single physical device, even across browser updates and changes in device configurations
Utilize a broader range of device and network parameters to provide enhanced short-term device identification, even in challenging scenarios such as virtual machine usage
Apply device fingerprints in the Graph section to identify connections between devices and user accounts, uncovering suspicious patterns and potential fraud rings

Unambiguously identify devices across web and mobile platforms
Benefit from the technological network feature: global cross-country and cross-client hunting technology offers the option to share worldwide the information on the devices previously flagged as fraudulent
Facilitate your investigation processes: the Graph technology for better visualization of global device connections and the true scale of any scheme you face
Streamline user authentification and authorizations across devices and SIM cards
Minimize false positives to ensure the seamless flow
Avoid degrading the overall user experience

More than 11 types of sensors analyzed
Web and mobile application protection

Collect data from both web and mobile applications, including mouse movements, keystrokes, screen touches, and sensor data
Create unique behavioral profiles for each user, encompassing digital interaction patterns, access preferences, and device usage
Compare user behavior against median profiles generated for similar user groups or segments to identify potential outliers and suspicious patterns
Continuous coverage of all digital channels - webpage or mobile apps, user enter logins and passwords

Legitimize user sessions to minimize the number of false positive
Detect deviations from established baselines, such as unusual mouse movements, atypical keyboard input speeds, or abnormal session durations
Utilize sophisticated machine learning models to analyze user behavior and detect anomalies, including those indicative of remote access, Trojans (malware) or bot activity
Trigger real-time alerts and risk scores based on detected behavioral anomalies, enabling immediate actions to safeguard user accounts
30% of cost reduction compared to legacy vendors (according to forrester*)

Multilayered analysis of a wide array of criteria and scoring
Independently create conditions for responding to newly identified cases of fraud
Benefit from our all-team friendly no-code solution
Modify rules and adapt them to your current needs
Intuitive interface for all teams even non-technical ones

Setting up your own workspace and change rules as soon as your need it
Defend your users from social engineering (information theft, caller ID spoofing, buyer fraud, or banking scams etc.)
Enrich your anti-scam systems
Protect the personal and sensitive data of your users with flexible configuration and call timeline analysis

Visualize the true scale of the scheme you face
Make your reporting easier and more comprehensible
Detect links and connections between accounts and devices so as not to miss a thing
Uncover malicious activity, VPN usage, and server information
Evaluate IP, ISP, and subnet risk levels for informed decision-making
Get detailed information on geolocation, ISP, and network attributes
Easily integrate with your existing systems using JSON format via API
Utilize IP addresses, GPS, and cellular data to determine user location with remarkable accuracy, even combating VPNs and hosting services
Employ geohashing algorithms to identify and monitor suspicious regions, pinpointing fraud hotspots down to specific buildings or city blocks
Track and visualize device locations in real-time within the Fraud Protection Admin Panel, enabling immediate action on suspicious activities
Configure sophisticated geolocation-based rules to detect anomalies, such as rapid location changes, multi-accounting from a single location, or activity from high-risk areas
Create and manage blocklists of known fraudulent locations, actively preventing fraudulent activity from these regions
Identify deliberate blocking or alteration of JavaScript APIs used for browser fingerprinting
Detect the use of noise injection techniques employed by antidetect browsers to distort canvas fingerprints
Leverage machine learning models to flag unusual combinations of device parameters, browser versions, and geographic locations
Identify inconsistencies in reported WebGL capabilities, video card information, and User-Agent strings to pinpoint attempts at browser spoofing
Generate dynamic risk scores based on detected anomalies and inconsistencies, empowering fraud teams to take swift action
Detect changes in IMEI, IMSI, and ICCID to identify unauthorized SIM card or eSIM profile changes.
Utilize Cloud ID technology to authenticate user devices, even across device and SIM changes, streamlining legitimate access
Identify anomalies in user behavior, such as new device logins or unusual navigation patterns, to flag potential account takeovers
Trigger alerts and risk scores upon suspicious activity, enabling immediate intervention to prevent unauthorized access and fraudulent transactions
Defend against both traditional SIM swapping and emerging eSIM-related fraud threats
Set of additional layers of protection
Nurture of your fraud intel and anti-scams systems
Provide clear explanations for each risk score, highlighting the key factors and events contributing to the assessment
Explain the specific rules and thresholds triggered, allowing for easy comprehension and auditability of fraud detection processes
Empower fraud analysts to review and understand AI-driven decisions, fostering trust and collaboration between human expertise and machine intelligence


Centers strategically located in key regions, housing analysts with deep knowledge of local fraud landscapes and trends
Leverage nuanced understanding of regional cyberattack patterns to reduce false positives, improving operational efficiency
Offer clients tailored advice on emerging threats and vulnerabilities based on regional insights, enabling them to implement preventative measures
Adapt solutions to specific regional challenges, enhancing fraud detection accuracy and reducing financial losses
Foster partnerships with local law enforcement and industry stakeholders to strengthen collective cyber defenses and disrupt fraud operations
Constantly get threat intelligence insights to fine-tune your security measures
Use the Group-IB Threat Intelligence solution to identify and block known fraudsters, compromised credentials, and other threats in real-time
Follow the global threat trends and stay vigilant
Aggregate and correlate threat data from diverse sources, including open-source intelligence, dark web monitoring, and internal incident response data
Utilize machine learning and behavioral analytics to detect patterns, anomalies, and hidden connections across vast datasets
Combine AI-driven insights with the expertise of seasoned fraud analysts to investigate complex cases and identify emerging threats
Identify and address vulnerabilities before fraud occurs, empowering businesses to stay one step ahead of cybercriminals
Detect and respond to fraudulent activity in real time, minimizing financial losses and protecting customer trust
Research centres in all key regions
Proprietary Group-IB innovations involved

Detect mule accounts through device fingerprinting, unusual device usage, and anomalous activity patterns
Uncover complex mule networks by linking accounts with devices or global IDs associated with known mule activity
Trigger alerts and risk scores for suspicious accounts, enabling timely investigation and intervention
Leverage machine learning models and behavioral analytics to identify subtle mule behavior patterns
Create and manage blocklists of known mule devices and identities to actively prevent fraudulent transactions

Research centres in all key regions

Proprietary Group-IB innovations involved

Identify suspicious behavior patterns, such as the changing of default SMS applications or enabling of accessibility services
Record and analyze user sessions to detect in-progress attacks, including phishing attempts
Leverage a combination of rules to identify both the presence of malicious software and the telltale actions they perform
Create and manage blocklists of known malicious applications and suspicious behaviors to prevent future attack
Detect known malware and trojans by analyzing application attributes, including installation sources, package hashes, requested permissions, and installation dates
Detect RAT activity through abnormal device settings, screen sharing indicators, and suspicious remote access sessions
Record and analyze user sessions to identify active RAT connections and potential data exfiltration
Identify and flag the installation of known RAT software or applications with suspicious permission requests
Link RAT activity with other suspicious events, such as phishing attempts or changes in default applications
Create and manage blocklists of known RAT software and associated behaviors to prevent future unauthorized access attempts
Research centres in all key regions

Proprietary Group-IB innovations involved

Replace easily manipulated biometric-only logins with BioConfirm’s device-bound dynamic linking, ensuring high-risk transactions and account changes are only approved by the real user.
BioConfirm works by combining two strong factors – biometric inherence (Face/Fingerprint) and trusted device possession – backed by cryptographic tokens that no fraudster can see, spoof, or intercept. This creates real-time, user-controlled approvals that not only strengthen compliance but also block fraud methods by design.

 Group-IB Fraud Protection
Group-IB Fraud ProtectionOften prioritize identifying suspicious activities, leading to a higher rate of false positives by flagging legitimate user actions as potentially fraudulent due to their focus on anomalies. It causes inconvenience for legitimate users, pollutes their experience, and wastes valuable resources
 Group-IB Fraud Protection
Group-IB Fraud ProtectionGroup-IB Fraud Protection takes a different approach, prioritizing user authentication before delving into fraud detection. This user-centric prioritization significantly reduces false positives.
Vendors not embracing cyber-fraud fusion risk falling behind due to their limited scope, siloed operations, reactive measures, inability to adapt to evolving threats, and failure to meet customer expectations for comprehensive fraud and cybersecurity solutions
 Group-IB Fraud Protection
Group-IB Fraud ProtectionGroup-IB leads in cyber-fraud fusion and has integrated the cyber-fraud kill chain framework, demonstrating a proactive approach to comprehensive fraud prevention. This equips clients with a multi-layered fraud protection service against increasingly sophisticated online threats
While AI enhances fraud detection capabilities, relying solely on it means vendors often overlook the nuanced expertise of human analysts
 Group-IB Fraud Protection
Group-IB Fraud ProtectionOur fraud detection systems leverage artificial intelligence (AI), but we also value human expertise. That's why we assign a dedicated Fraud Analyst to each client. These analysts have the experience to interpret fraud patterns, investigate suspicious activities, and provide personalized guidance for comprehensive fraud prevention
Fraud providers without local fraud analysts face limitations in combating region-specific fraud due to a lack of cultural and linguistic understanding, missed red flags, and an inability to gather real-time intelligence about emerging fraud trends and schemes
 Group-IB Fraud Protection
Group-IB Fraud ProtectionGroup-IB's regional Digital Crime Resistance Centers establish a local presence with in-depth knowledge of cultural nuances, language, and client behaviors within a region. This allows for a better understanding of local fraud tactics and behaviors, leading to accurate identification of fraudulent activities
Many vendors often prioritize revenue over providing adequate client support and resources, which can hinder their ability to effectively combat fraud
 Group-IB Fraud Protection
Group-IB Fraud ProtectionGroup-IB’s fraud protection service has been recognized as a market leader by major market analysts, including Gartner, Frost & Sullivan, Kuppingercole, and Forrester. Our platform has lowered the rate of false positives by 20% and enabled 10% to 20% more fraud attempts to be detected and prevented. It also improved customer experience, reducing the need for one-time passwords by 30%.
Frost & Sullivan recently cited Group-IB Fraud Protection as a leading solution within the industry. Source: "Fraud Detection & Prevention Market: Solutions Differentiation, Global, 2022"
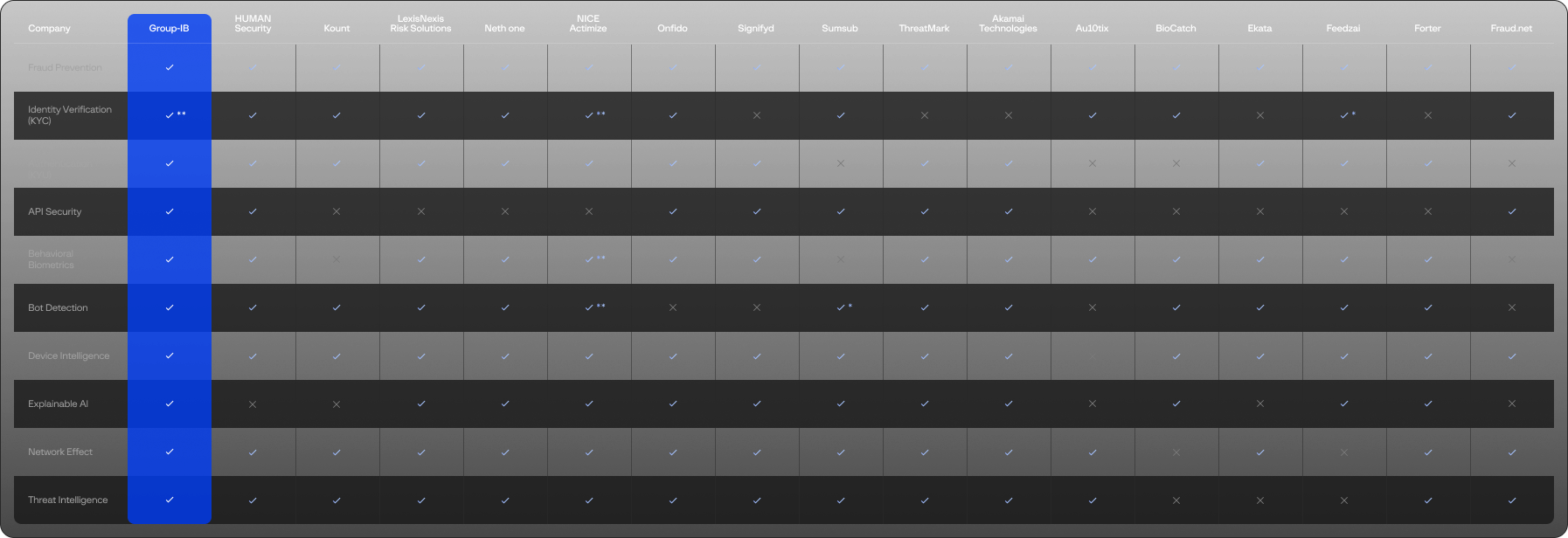

Fraud Protection is a set of tools and services that help organizations detect, identify, prevent damage and protect from digital fraud; it comprises both fraud prevention and fraud detection strategies. Fraud Protection services are used to protect the digital identity of users, block bot activity and prevent fraud. Fraud Protection helps reduce fraud losses and improve user experience in automated customer systems.
Group-IB Fraud Protection allows you to detect the following types of fraud: social engineering attacks (phishing sites, email scams etc.), account takeover fraud, payment fraud, malicious bot attacks, web injections, mobile trojans, malware-related and credit frauds etc.
No, our solution only processes hashed or encrypted user IDs and session IDs that cannot be associated with an individual.
Group-IB adopts a serious approach to enforcing personal data protection in accordance with the EU General Data Protection Regulation (GDPR).
As part of complying with GDPR requirements, Group-IB takes the necessary organizational and technical measures to develop, maintain, and provide the Fraud Protection solution.
The legitimate interests of a controller (in accordance with Article 6 and Recital 47 EU GDPR) provide a legal basis for the processing of data subjects’ personal data while using the Fraud Protection solution.
To protect your website(s), you simply need to add our Web Snippet to your site. The Web Snippet is a client module that is built into the protected application, and from the moment the first page of the application is loaded, it transmits indicators of compromise, the behavioral characteristics of the user, and the environment in which the application is running to the server-side of the Fraud Protection.
To protect your mobile application(s), you simply need to add our SDK to your mobile application. Integrating the Mobile SDK into a mobile application does not require changing the application’s logic.
The Mobile SDK is a client module built into the protected mobile application. From the moment the application is loaded, it transmits indicators of compromise, the behavioral characteristics of the user, and the environment in which the application is running to the server-side of the Fraud Protection platform.
The Mobile SDK does not transfer sensitive banking information, Personal Identifiable Information, or other confidential data. The contents and type of transferred data can be set by the customer independently when integrating the SDK into the mobile application.
The Fraud Protection solution can integrate into any Risk Management Platform that uses API. We can provide Pull and Push mode APIs.