Falcon. Act 1
Background
In 2020, business email compromise (BEC) emerged as the top cybercrime reported to the FBI, according to victim complaints. With confirmed losses amounting to a staggering $1.8 billion, BEC accounted for 37% of all cybercrime-related financial losses — overtaking even ransomware in its impact.
BEC is a type of email phishing attack that relies on social engineering. When sent as part of BEC, phishing emails either target specific people within an organization or are sent out as a mass email. They are often disguised as money transfer requests, HR-communications or business proposals and they are used to steal confidential data.
In 2020–2021, one of the most notorious BEC groups named TMT was identified and dismantled with support from Group-IB experts. Originally from Nigeria, the TMT gang’s activities spanned a vast scale, compromising approximately 500,000 government entities and private companies across more than 150 countries. Investigating this group presented several unique challenges:
- The group operated a highly organized criminal enterprise and used an array of tools and deceptive techniques to evade detection
- Their methods of monetizing their campaigns were deliberately obscured
- The investigation focused on technically skilled organizers rather than easily identifiable support roles like money mules
Impact
As a Gateway partner, Group-IB shared its findings with INTERPOL, which initiated a joint operation named “Falcon.” In collaboration with police forces in Nigeria and in member countries where the victims were located, INTERPOL gathered the necessary evidence to enable the Nigerian authorities to proceed with the arrests.
In November 2020, the three BEC gang members identified with the help of the Group-IB Investigations and CERT-GIB teams were arrested in Lagos by the Nigerian cybercrime police unit. The data discovered on the devices of the arrested TMT members confirmed their involvement in the criminal scheme and identified stolen data from at least 50,000 victims.
Storyline
In 2017, the CERT-GIB team detected a surge in emails impersonating various brands, often containing widespread malware in their attachments. The purpose behind the emails was initially unclear. Nevertheless, Group-IB promptly notified the affected brand owners and helped take down fraudulent domains and command-and-control (C2) servers linked to the malicious campaigns.
A clearer picture began to emerge when Group-IB analysts categorized emails based on patterns. By analyzing email headers, we discovered that the group relied on email automation tools like Gammadyne Mailer and Turbo-Mailer to distribute their phishing emails. They also used MailChimp to track whether recipients opened messages.
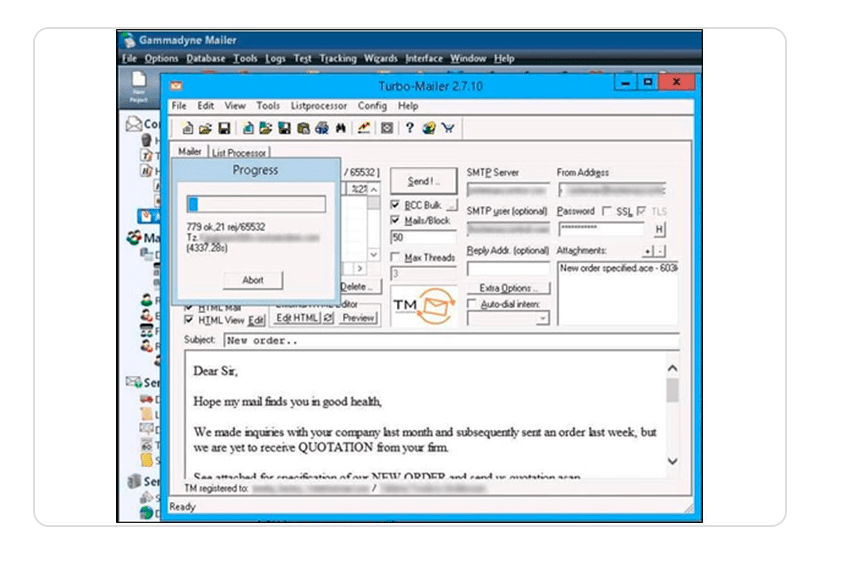
Figure 1. Gammadyne Mailer and Turbo-Mailer used by cybercriminals
In the “X-Originating-IP” field of the analyzed emails, we identified Nigerian IP addresses without any VPN usage. This led us to suspect that a group of Nigerian fraudsters might be behind the attacks.
To strengthen our hypothesis, we conducted additional correlation based on the email addresses used in the campaigns. Further evidence linking the operation to Nigeria emerged when we discovered several command-and-control (C2) servers hosted there.
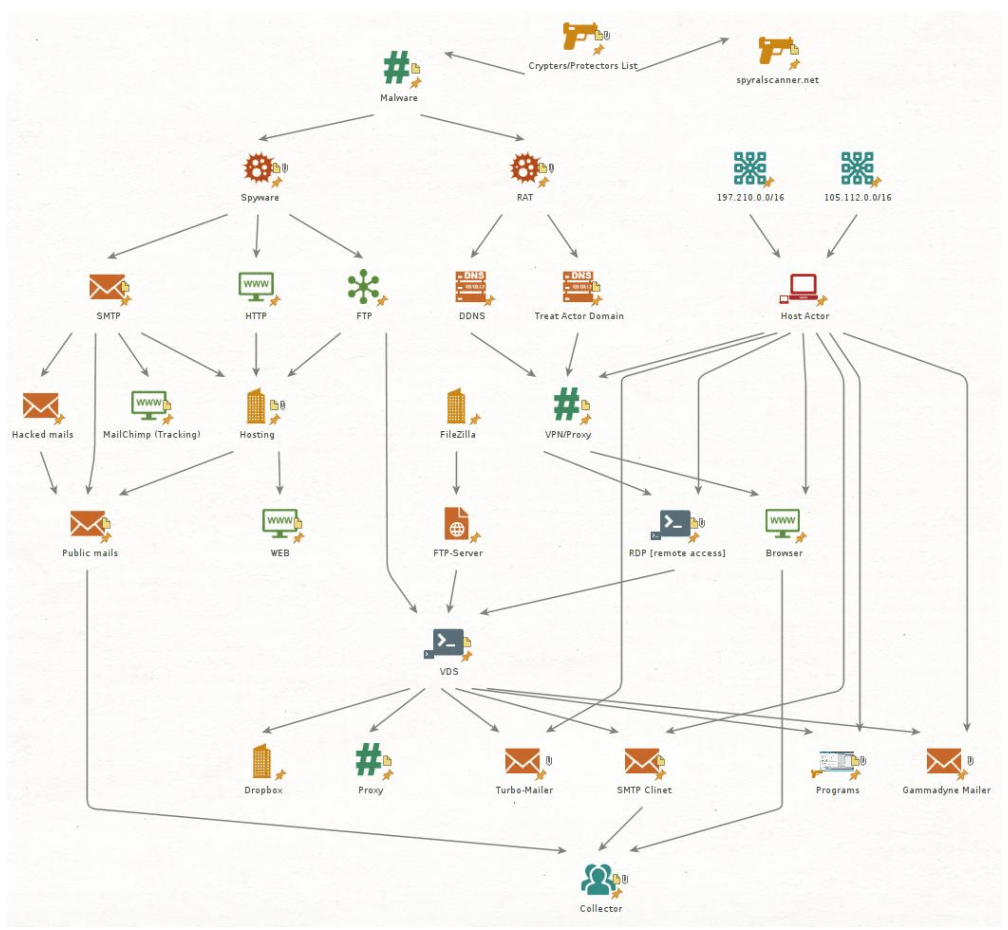
Figure 2. Attackers’ infrastructure
The threat actor behind the campaign was identified and codenamed by Group-IB as “TMT gang”. The name was derived from the username used by one of the gang’s leaders, which contained the letters “TMT”. The gang used well-crafted emails impersonating legitimate companies to conduct mass email phishing campaigns and distribute popular malware strains. They made their emails look like purchasing orders, product inquiries, and COVID-19 aid schemes.
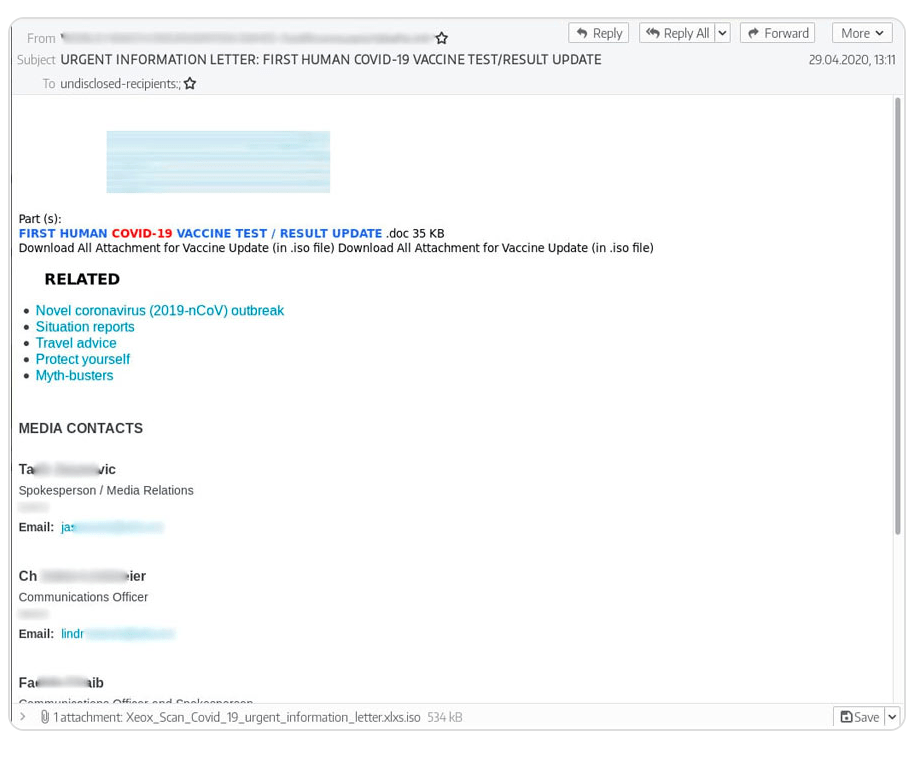
Figure 3. Sample of TMT’s phishing email made to look like a message about COVID-19-related aid
The cybercriminals also used email accounts compromised in advance to push a new series of phishing attempts. The discovered email samples, detected and analyzed by Group-IB Managed XDR, were written in English, Russian, Spanish, and other languages, depending on the scammer’s target list.
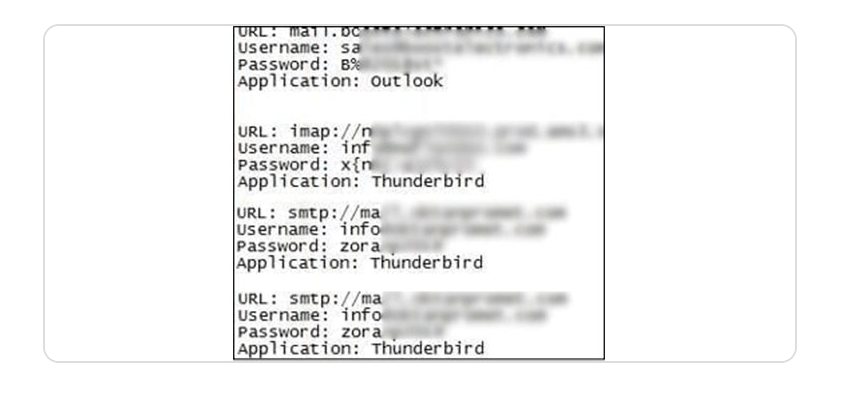
Figure 4. Example of compromised data from the cybercriminals’ logs
Malware features
Group-IB analysts identified various types of malware attached to phishing emails sent by TMT. A key characteristic of the malware samples was their stealer functionality. Their primary purpose was to extract and copy saved credentials from infected systems. This included authentication data from browsers, email, and FTP clients. The stolen credentials were then sent to predefined email addresses controlled by the attackers, enabling unauthorized access to victims’ accounts and systems.
The group relied exclusively on a variety of publicly available spyware and Remote Access Trojans (RATs), including AgentTesla, Lokibot, AzoRult, Pony, and NetWire. The malware families, widely used by many threat actor groups, were acquired from public forums.
To evade detection and tracking by common security tools, TMT used public crypters to obfuscate the malware code. The technique altered the malware’s signature, allowing it to bypass email security systems and anti-virus solutions. Once deployed, the malware communicated with the attackers’ command-and-control (C&C) servers using common protocols like SMTP, FTP, and HTTP.
| Spyware | RAT/Backdoor | Crypter/Protector |
| AgentTesla | Remcos | Spartan Crypter |
| AveMaria | HWorm (Houdini) | Cyanx Sharp |
| HawkEye | Adwind | The Old Phantom Crypter |
| Phoenix Keylogger | Warzone RAT | DarkEyE Protector |
| Origin Keylogger | NetWire | CypherIT |
| Loki | NanoCore | Cassandra Crypter |
| 404 Keylogger | ConfuserEx | |
| AzoRult | CloudEyE Protector | |
| ViottoKeylogger | ASPIRE CRYPT | |
| Pony | Atilla Crypter | |
| Toretto Exploit Software |
Figure 5. List of tools used by TMT
The gang’s primary objective was to compromise mailboxes. Once they had gained access, they either used the mailboxes for their own schemes or sold them to other criminals. Such an approach is a key component of business email compromise (BEC) schemes. Additionally, some Group-IB customers confirmed that they had experienced BEC attacks that matched the patterns used by TMT, which solidified our conclusions even more. Throughout their operations, the gang members managed to infect organizations around the world, including in the US, the UK, Singapore, Japan, and even back home in Nigeria, according to Group-IB data.
Investigation details
Some of the email addresses used by the fraudsters in the malware samples were directly linked to their personal email accounts. This connection led Group-IB to the Facebook profiles of Nigerian individuals. Upon closer analysis, we discovered that many of them were based in Lagos, had a technical education, and were either friends or acquaintances. More than 10 identified individuals had studied at the same university and appeared in photographs together.
Further investigation and enrichment of their profiles revealed their activity on dark web forums, where they had created threads discussing phishing attacks. By analyzing the details of their phishing kits and comparing them with email content, we discovered that one of the group members had developed the phishing kit and even offered it as a service to other fraudsters.
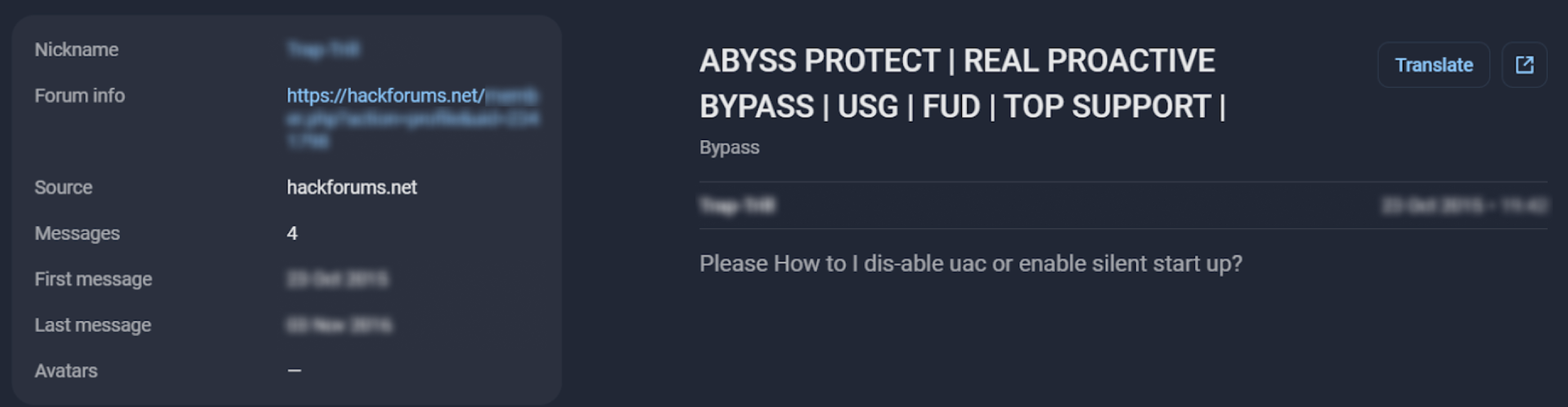
Figure 6. Post of a TMT gang member on a dark web forum
The phishing kit’s distinctive pattern enabled Group-IB specialists to uncover the scope of its usage. Our research showed that more than 50 brands were targeted and abused using phishing pages built with this kit.
And justice for some
In November 2020, Group-IB’s APAC Cyber Investigations Team supported a cross-border anti-cybercrime effort that involved INTERPOL’s Cybercrime Directorate and the Nigerian police force and resulted in the arrest of three individuals in Lagos. The BEC gang members, with the initials “OC” (32 y.o.), “IO” (34 y.o.), and “OI” (35 y.o.), were identified with the help of Group-IB’s Cyber Investigations and CERT-GIB teams. The data discovered on the devices of the arrested TMT members confirmed their involvement in the criminal scheme and identified stolen data from at least 50,000 victims.

Figure 7. An arrest photo related to Operation Falcon I, courtesy of INTERPOL
Based on the infrastructure and techniques that the attackers use, Group-IB was also able to establish that the gang was divided into subgroups and that a number of individuals were able to escape. Our findings about other suspected gang members, whom Group-IB was able to track down, were shared with INTERPOL’s Cybercrime Directorate. The investigation was to be continued…
Falcon. Act 2
In December 2021, Group-IB supported the INTERPOL-led cooperative effort involving INTERPOL Global Financial Crime Task Force, Nigerian law enforcement agencies, a range of INTERPOL expert teams and its private partners. As a result of a ten-day operation called Falcon II, eleven alleged members of a prolific cybercrime network known for business email compromise attacks were arrested. Many of the suspects were thought to belong to the TMT gang, whose members had remained at large after the first operation.
Behind the scenes
Group-IB’s APAC Investigations Team contributed to the operation by sharing information about the threat actors, having identified the attackers’ infrastructure, collected digital traces they left behind, and assembled data relating to their identities.
Group-IB also expanded the investigation’s evidence base by reverse engineering the samples of malware used by the cybercriminals and conducting a digital forensics analysis of the files contained on the devices seized from the suspects.
Impact
Falcon I had led to the arrest of three TMT members. However, this prompted the remaining members to intensify their activities in retaliation. The group updated their phishing kits to route compromised data through Telegram bots, making their operations more challenging to trace.
In a bold move, the threat actors also attempted to compromise Group-IB staff by impersonating top management and targeting employee emails. Despite their efforts, Group-IB’s cybersecurity solutions and staff awareness thwarted these attempts.
Falcon II, which took place in December 2021, marked a significant decline in the group’s activities, particularly in specific regions. Although not all members were identified and apprehended, the operation sent a clear message: justice is closing in.
Storyline
As part of the ten-day Operation Falcon II, ten Nigeria Force Police officers were deployed from the Abuja headquarters to Lagos and Asaba to arrest suspects identified earlier with intelligence provided by INTERPOL.
Field operations were preceded by an intelligence exchange and analysis phase, where Nigerian law enforcement used INTERPOL’s secure global police communications network to work with police forces across the world also investigating email-borne scams linked to Nigeria.
INTERPOL’s General Secretariat supported field operations 24/7, extracting and analyzing data contained in the laptops and mobile phones seized by NPF during the arrests.
This preliminary analysis indicated that the suspects’ collective involvement in BEC criminal schemes may be associated with more than 50,000 targets. One of the arrested suspects had more than 800,000 potential victim domain credentials stored on his laptop.
Another suspect had been monitoring conversations between 16 companies and their clients and diverting funds to the SilverTerrier gang whenever a company was about to make a transaction.
Another individual was suspected to have taken part in BEC crime across a wide range of West African countries including Gambia, Ghana, and Nigeria.
With BEC attacks having both cyber and financial aspects, as part of Operation Falcon II financial “pathfinder countries” belonging to INTERPOL’s Global Financial Crime Taskforce (IGFCTF) including Nigeria worked together on cross-border financial investigations linked to the operation.
The IGFCTF therefore initiated the coordination of further action against SilverTerrier bank accounts and ensured that intelligence about the domain credentials of potential victims was shared with member countries so that further fraud activities could be prevented.
And justice for all
As a result of ten-day operation Falcon II, eleven alleged members of a prolific cybercrime network known for Business Email Compromise (BEC) were arrested by officers of the NPF Cybercrime Police Unit and INTERPOL’s National Central Bureau (NCB) in Nigeria. Many of the suspects were thought to be members of the TMT gang that have harmed thousands of companies worldwide. The final blow to this case came with the arrest of the TMT gang leader in May 2022 as part of Operation Delilah.

Figure 8. An arrest photo related to Operation Falcon II, courtesy of INTERPOL
Partnership is key
Both operations came under Project Gateway, which encourages law enforcement and private sector partnerships to generate threat intelligence from multiple sources and helps police authorities prevent and investigate attacks in a timely manner. Through INTERPOL’s Gateway initiative, Group-IB and other private partners informed the investigation by sharing information about TMT threat actors and analyzing data to situate the group’s structure within the broader organized crime syndicate. They also provided valuable technical expertise and consultancy to support INTERPOL’s teams.
The two cross-border operations demonstrated that only effective collaboration between private sector cybersecurity companies and international law enforcement can bring the most elusive cybercriminals to justice. It also helped to overcome regulatory differences across countries, which usually impede the exchange of threat intelligence data.


























