Introduction
Since its emergence in 2017, the Ransomware-as-a-Service (RaaS) criminal enterprise has gained significant momentum. In 2023, Group-IB’s investigations revealed that the number of ads published on the dark web seeking affiliates for RaaS services had increased by 1.5 times compared to the previous year, highlighting its growing popularity and demand. Group-IB has been actively investigating and tracking ransomware groups, and the following is an illustration of a typical RaaS ecosystem.
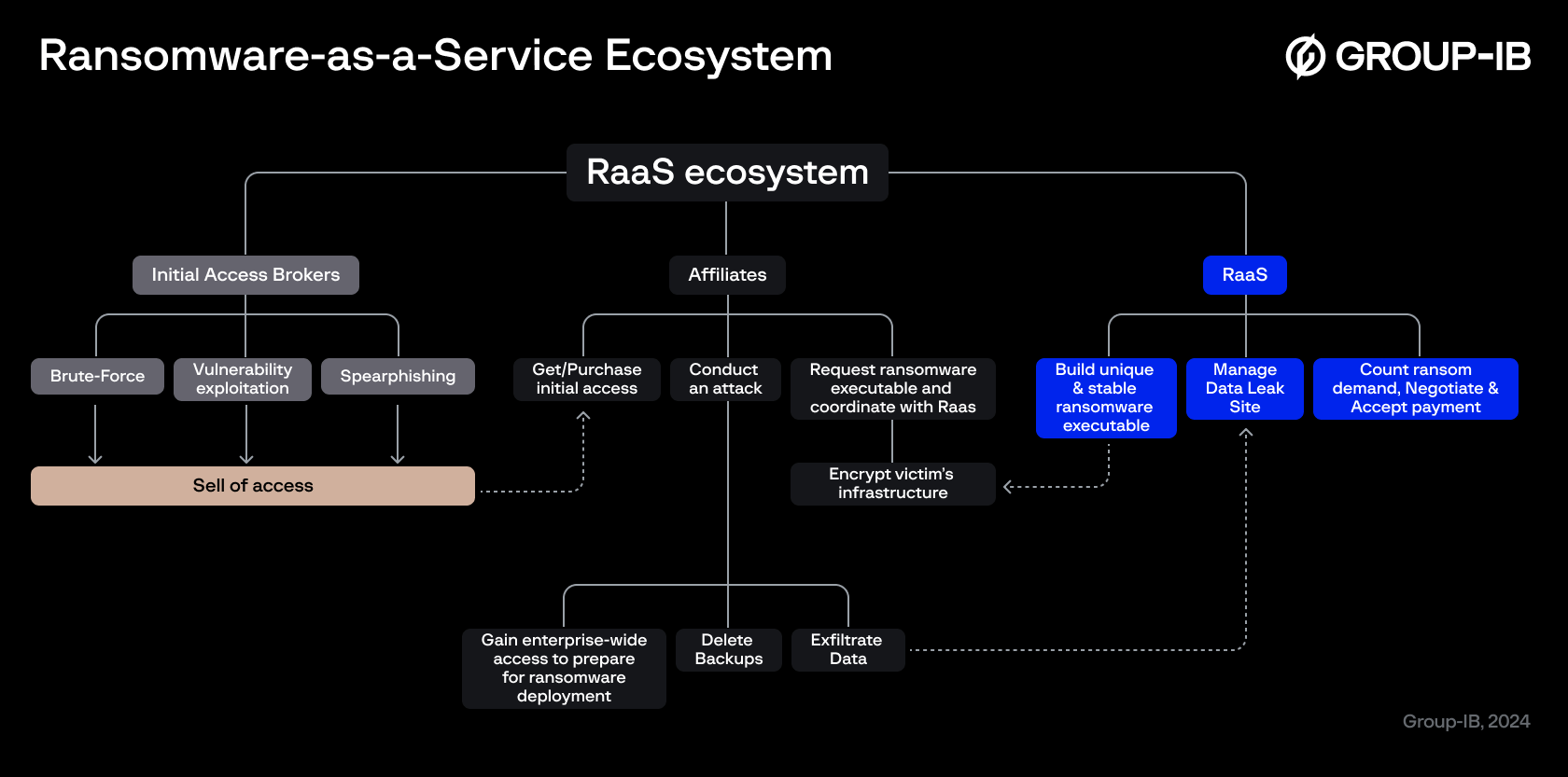
Figure 1. RaaS ecosystem review
Group-IB investigates the entire lifecycle of threat groups, including their establishment, syndicates, hiring and recruitment processes, promotions, partnerships, affiliates network, threat hunting on the infrastructure used to conduct the attacks, analyzing their tactics, techniques and procedures (TTPs), victimology and more.
Group-IB’s comprehensive visibility and insights into the threat groups is a culmination of extensive knowledge in the Cyber Threat Intelligence domain, case studies from Incident Response engagements, and Threat Hunting missions powered by Group-IB’s Managed Extended Detection and Response (MXDR) solution, and collaboration with the law enforcement agencies.
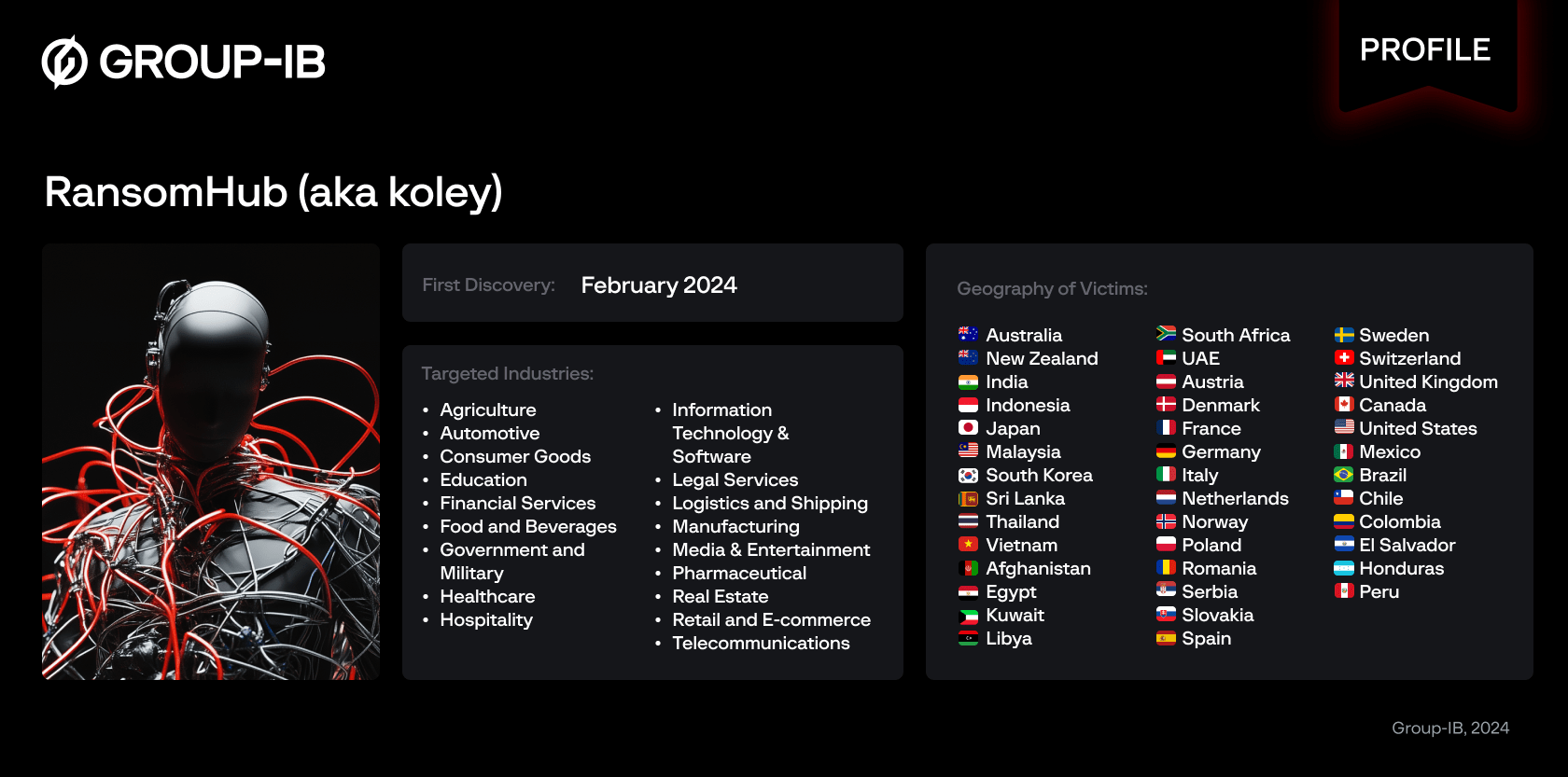
In this threat research, we present our findings on an emerging threat group known as the RansomHub, aggregating all available information about its activities from February 2, 2024, until today.
Key Discoveries in the Blog
- Launched its affiliate program in February 2024
- RansomHub has been observed to recruit former affiliates of Scattered Spider group, and allows affiliates to collaborate with other RaaS groups.
- RansomHub’s ransomware impacts Windows, Linux, and ESXi platforms, and can self-propagate within an internal network, which is capable of disabling network interfaces or entering Safe Mode on Windows systems before encryption.
- The most common entry point is a published RDP service on a public-facing Windows server without multi-factor authentication.
- Data is exfiltrated, archived and uploaded to remote file shares using utilities like rclone to Mega. Post-exfiltration, access tokens for Mega are revoked to obscure their tracks.
- Group-IB has observed large data transfers (exceeding 150 GB) in a single bulk, causing significant spikes in network traffic, which can be indicative of ongoing exfiltration activities.
Who may find this article interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat Intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams
- Law enforcement investigators
- Cyber Police Forces
A High Price to Pay
The RansomHub group practices the well-known double-extortion attacks by encrypting files on the victim’s network endpoints and exfiltrating sensitive data prior to the encryption. This strategy amplifies the damage and pressures victims to pay the ransom demand.
Analysis of its victimology confirms that RansomHub poses a significant threat to cybersecurity, as evidenced by their attack statistics. RansomHub most frequently attacks companies in the United States, the United Kingdom, Spain, France, and Italy, with less focus on the Latin-America (LATAM), Middle East and Africa (META) and Asia-Pacific (APAC) regions. This pattern aligns with the trends observed among similar RaaS groups. While RansomHub is not confined to a single industry and targets companies across various sectors, their primary targets are companies within the healthcare, finance, and government sectors.
RansomHub’s ransom demands are also noticeably high, rumored to be as steep as US$50-million in attacks on companies in Northern Africa. . However, their interest is usually aligned with publicly available financial information about the victim, as well as analysis of leaked data that often contains accounts balance details.
Group-IB’s Digital Forensics and Incident Response team has been involved in the investigation of several cybersecurity incidents where victims have fallen to RansomHub affiliates. These attacks typically lack sophistication, and the adversaries’ arsenal often consists of a set of dual-use tools for propagating over the victim’s network, as well as establishing a command-and-control over remote monitoring and management tools.
Summarizing the findings from our involvement in these incident investigations, we conclude that most of these companies were insufficiently prepared to detect and remediate an attack, and had common cybersecurity posture gaps in people, process and technology. To understand how to improve the cybersecurity posture, increase the ransomware attacks resilience, we highly recommend reading our Ransomware Readiness whitepaper.
Establishment
RansomHub announced its affiliate RaaS program in February 2024. On 2 February they first introduced themselves on RAMP dark-web forum via a user account with the nickname “koley”.

Figure 2. A screenshot of Group-IB’s Threat Intelligence Platform, which captured an announcement from RansomHub promoting their affiliate program
In their post, they sought to invite partners by offering them a fixed 90-10 payment split model, where 90% of every successful payment received from the victim goes to the affiliate, and 10% goes to the RansomHub.
Ticket
Affiliates who have joined our affiliate program to vouch for you. ID of any well-known forums, the longer the registration time or have a certain deal as well as reputation. Evidence of cooperation with other RaaS groups (including, but not limited to, screenshots of payments received or balances at the receiving address. The best and quickest way to join is to pay a deposit(Returned to you after first getting paid.)
As is common practice within the RaaS groups, RansomHub also developed their own data leak site (DLS) panel.
hxxp://ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd[.]onion/
Panel
Each panel uses a separate onion domain, and the panels can manage targets and chat rooms. The panel allows you to view the logs of target accesses and the last access time. The panel supports Offline auto-reply for one message The panel can create a private blog page, which can be very beneficial for proofing and negotiation.
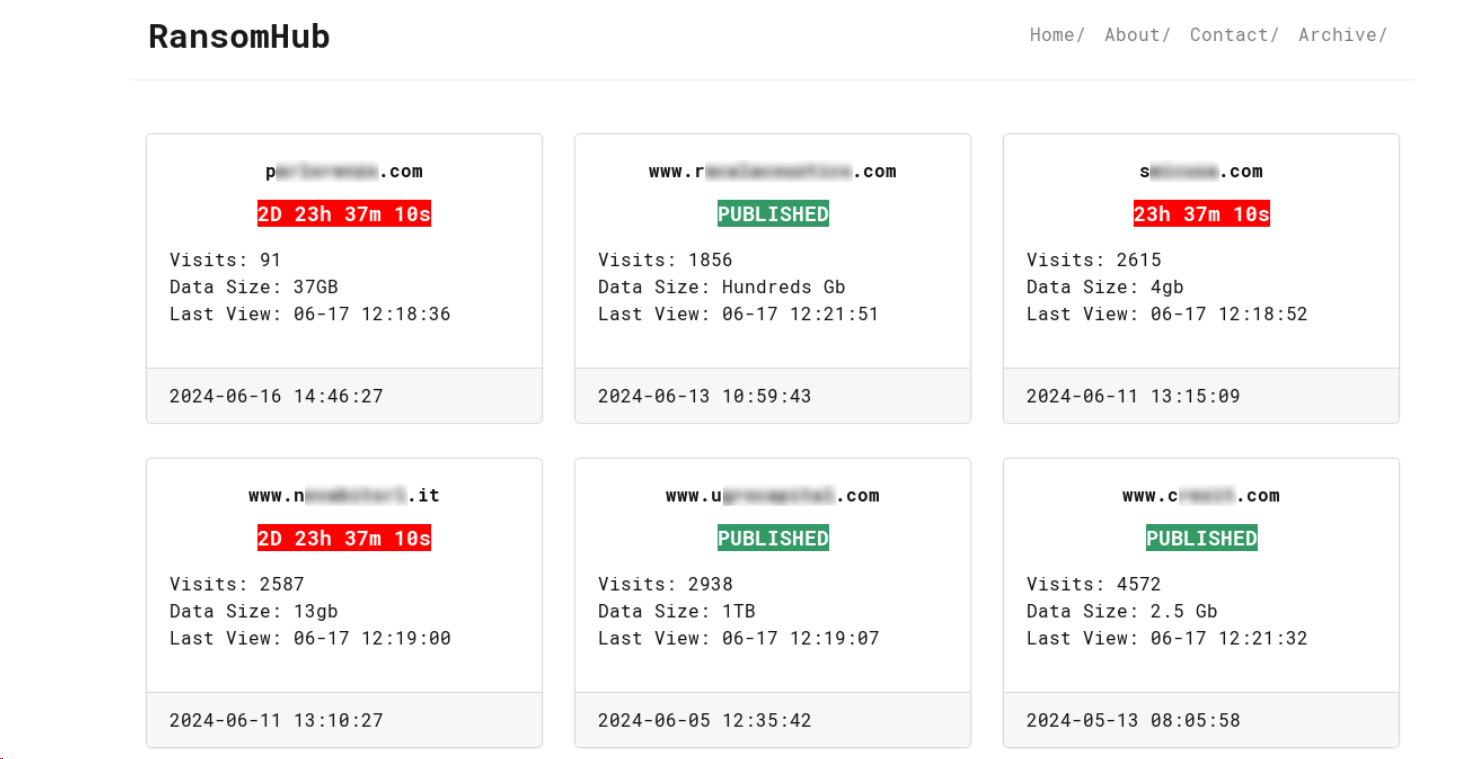
Figure 3. A screenshot of the RansomHub DLS
The RansomHub group also recruited numerous former Scattered Spider affiliates. Affiliates can cooperate with other RaaS, so long as they comply with the rules (below) that they do not initiate any attacks in the Commonwealth of Independent States (CIS) region, North Korea, China, Romania, and Cuba. Despite this, one of the known victims of the RansomHub was based in Romania.
Rules
We are not allowed to attack CIS as well as Cuba, North Korea and China. Accounts that add false targets or have no activity for a certain period of time will be banned. Repeated attacks on paid targets are not allowed, encryption of non-profit hospitals is not allowed but data ransom is allowed. After the target pays, you must fulfill all the terms and agreements promised in the negotiations, otherwise you will be banned. We do not forbid you to cooperate with other RaaS teams at the same time, but you can not disclose our panel address and account password. When we find more than one user logging in and do not explain the situation, we will ban your account.
Locker variants support Windows, Linux, ESXi across various architectures. The ransomware program developed by RansomHub is capable of self-propagating over an internal network, automatically spreading to reachable hosts with provided credentials. Moreover, it can disable the endpoint’s network interface before the encryption process or enter Safe Mode before encryption on Windows-based systems. As of the writing of this research, Group-IB confirms that encryption algorithm and key management implementation do not have any flaws that would allow cybersecurity teams to decrypt the data without obtaining the decryptor program.
Locker
The Locker is written in Golang. The asymmetric algorithm is based on x25519, and the encryption algorithm is adjusted in aes256 chacha20 xchacha20 according to the hardware support, so we have a very fast encryption speed. The Locker supports intranet propagation, Safe Mode encryption and disconnected encryption. The Locker supports Windows, Linux, ESXi and other arm mips architectures. The Locker is obfuscated using AST, built daily.
Victimology
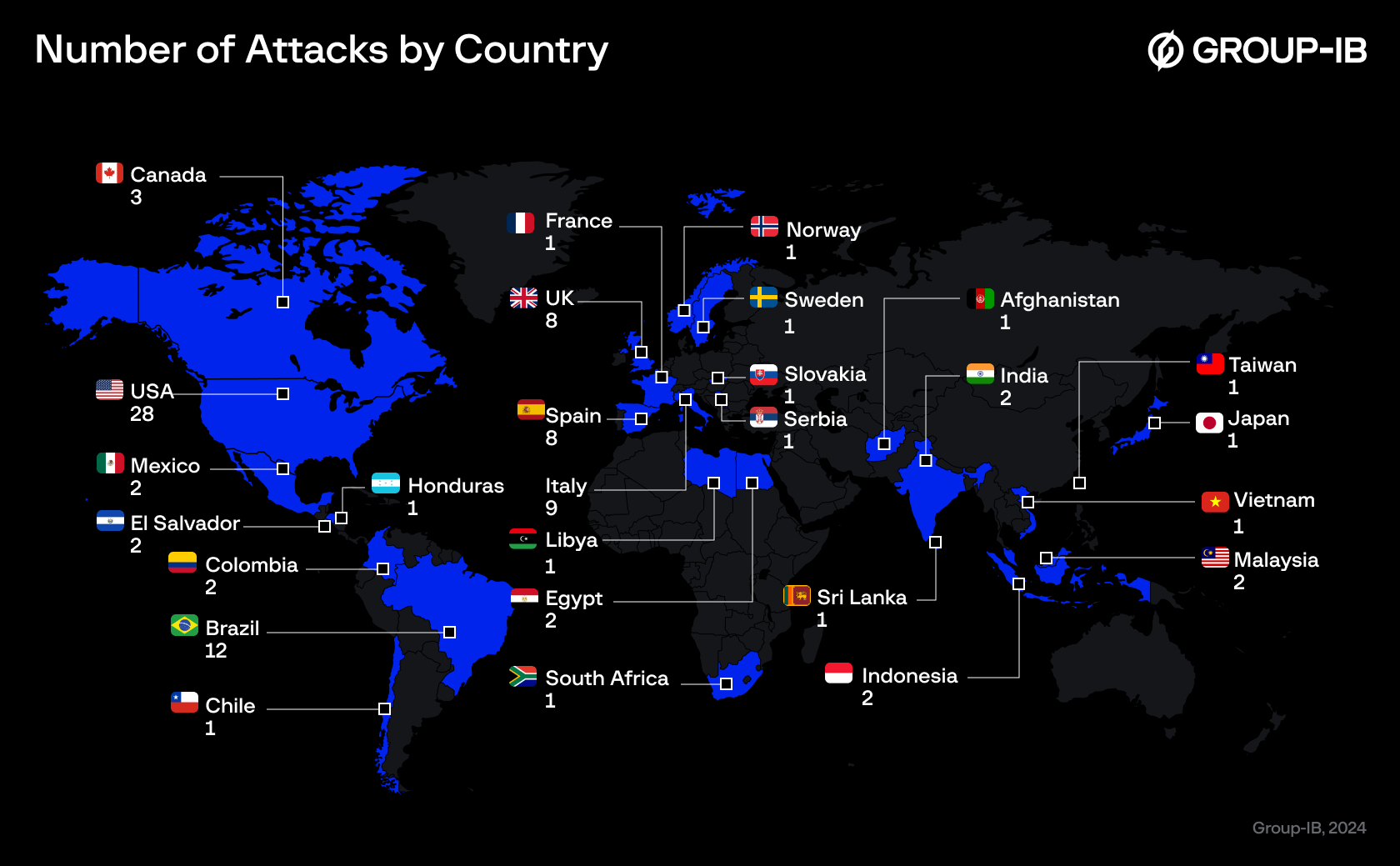
Figure 4. RansomHub DLS summary by country
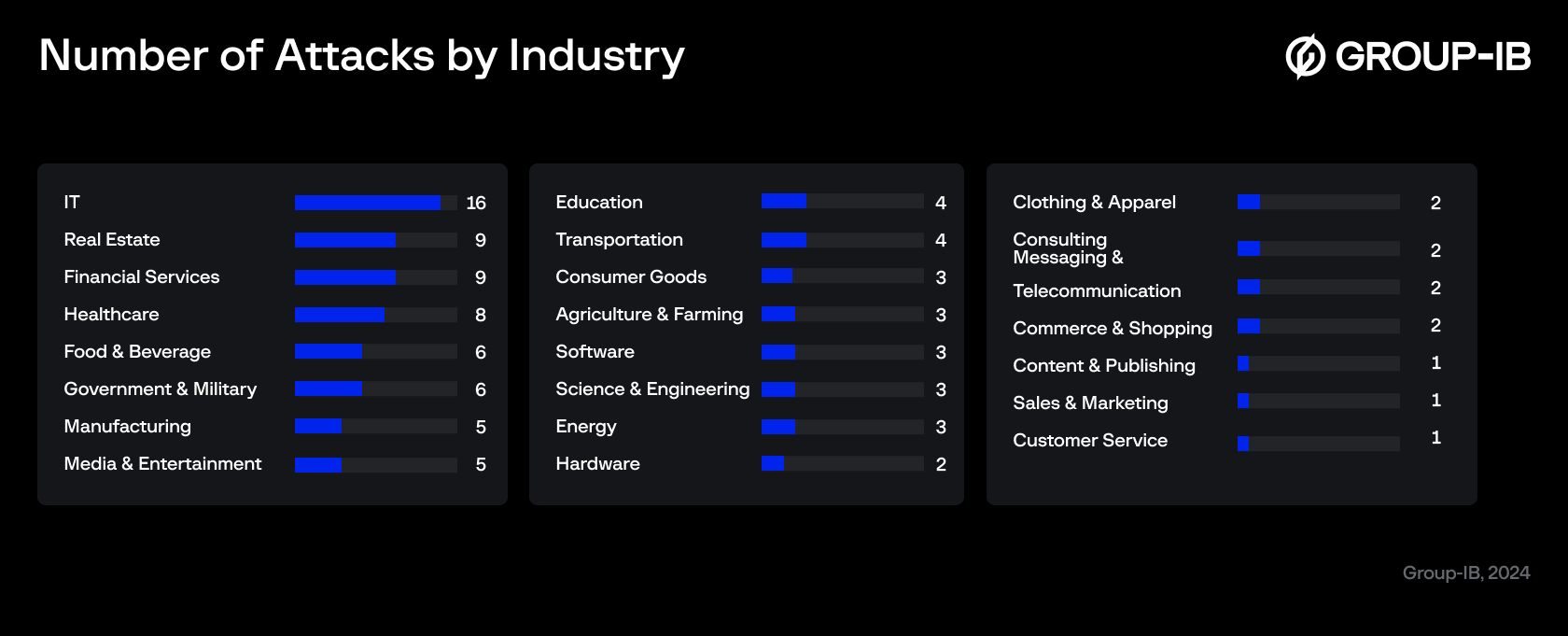
Figure 5. RansomHub DLS summary by industry
Attacks
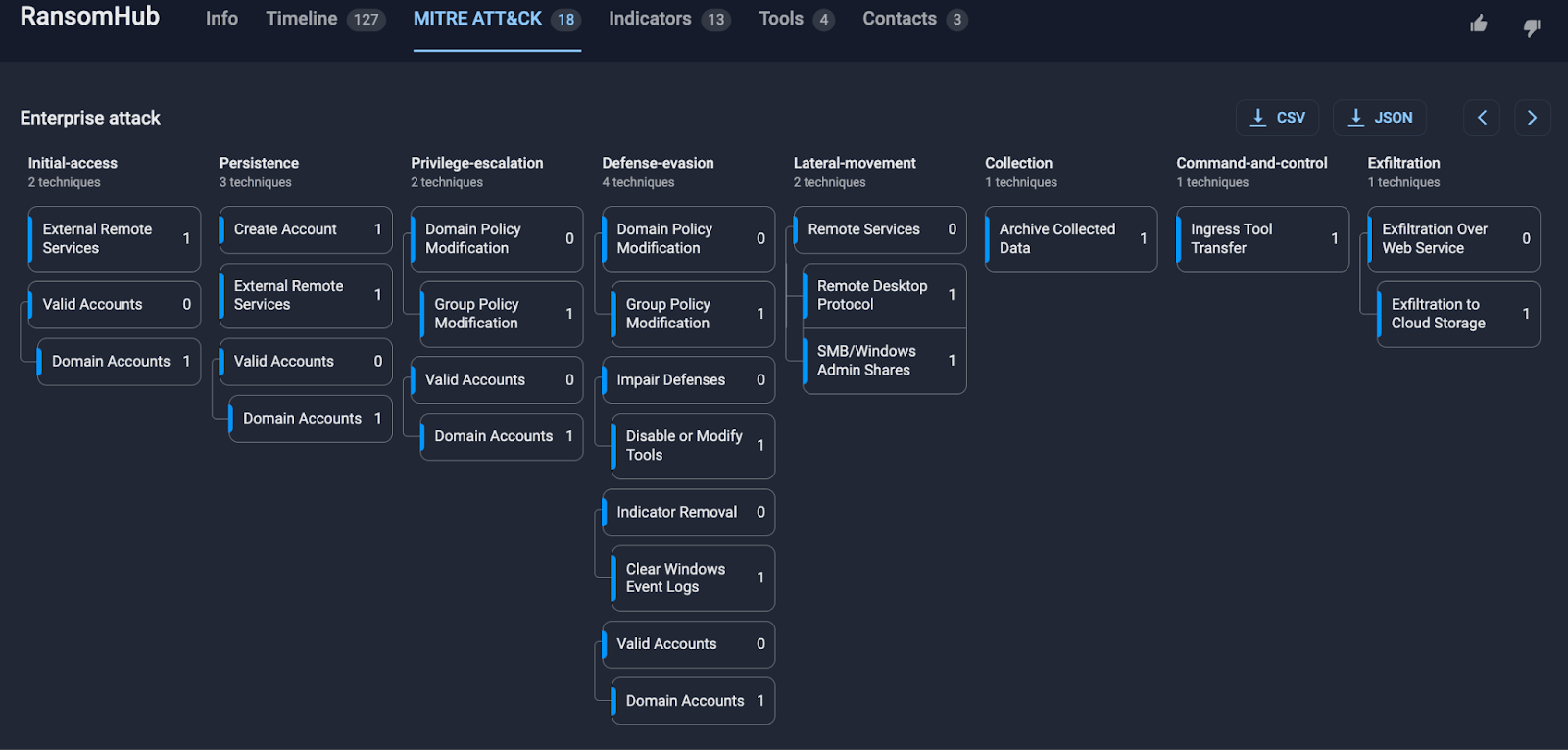
To illustrate the flow of an attack, we will use our Unified ransomware kill chain, mapping procedures to the MITRE ATT&CK ® matrix.
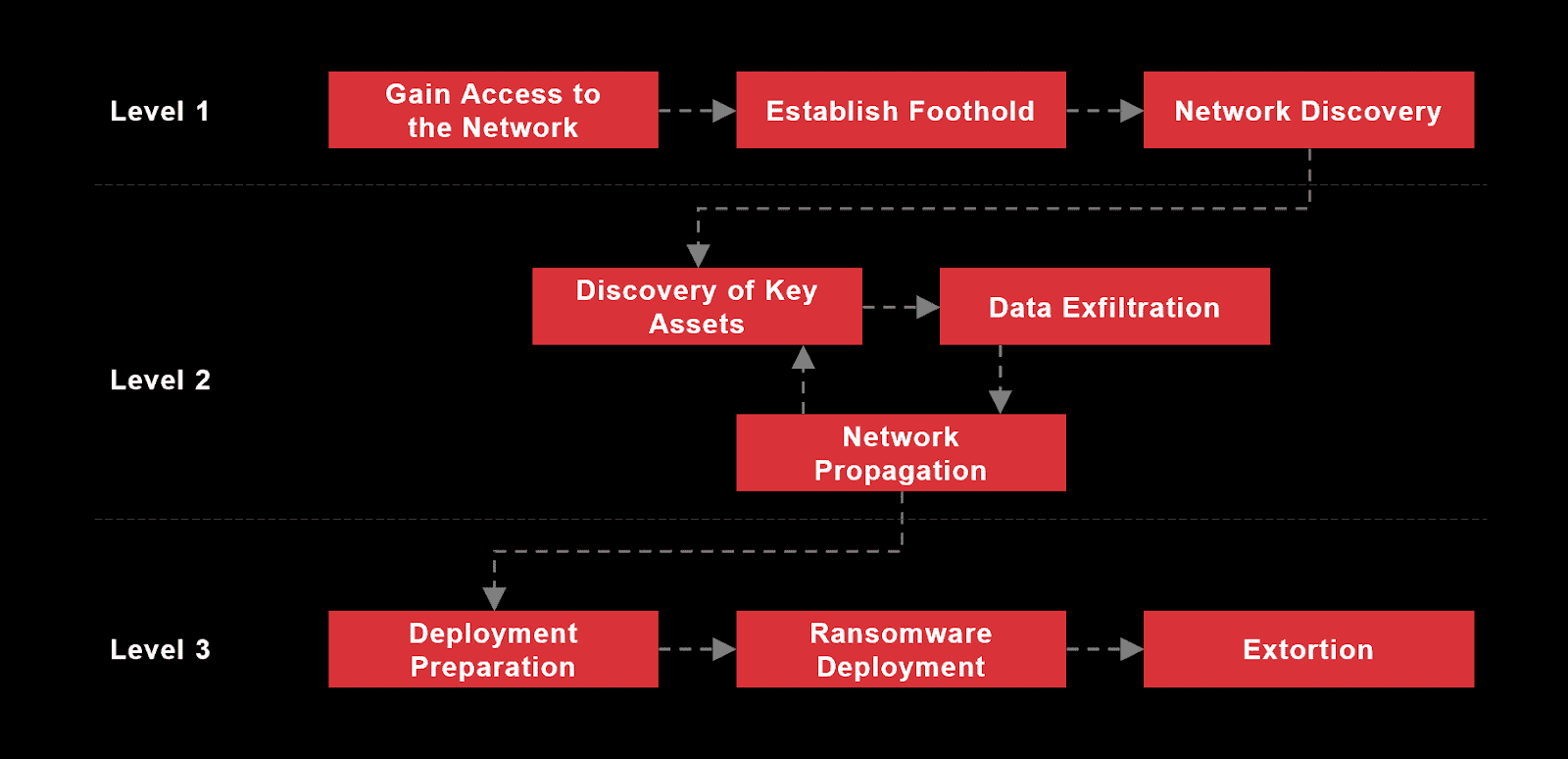
Figure 6. Group-IB’s Unified ransomware kill chain
Gaining Access to the Network
For initial access the affiliates usually purchase compromised valid domain accounts (T1078.002) from Initial Access Brokers (IABs) and external remote services (T1133). From the Incident Response cases Group-IB experts confirmed that accounts have been acquired via LummaC2 stealer. Keep in mind that there are dozens of initial access trojan families employed by IABs which we have described in detail in our annual High-Tech Cyber Crime threat report.
After purchasing the account, the affiliates would proceed with reconnaissance of the available external remote services.
In our observations from the investigations that we carried out, the most frequent entry point is a published remote desktop service (RDP) or RDP web access, deployed on a public-facing Microsoft Windows server without multi-factor authentication.
To establish the user session by connecting to the RDP service, attackers have been using various public Virtual Private Networks (VPNs) such as Windscribe, TOR nodes, and IP addresses of bad repute as illustrated below using Group-IB’s Graph analysis.
Establishing a Foothold
Notably, the attackers purchase access with sufficient privilege, which does not require significant efforts from them to remain stealthy. Consequently, having a valid account (T1078) and external remote services session, they usually proceed with their attacks without deploying other backdoors. In some cases, they have been employing AteraAgent and Splashtop remote monitoring and management tools (RMM) to establish redundant access to the victims’ networks.
Network discovery
By obtaining privileged access, the discovery process becomes simple and straightforward. The attackers leverage built-in Active Directory tools such as the Active Directory Users and Computers dsc.msc applet (T1018), in tandem with network service discovery (T1046). They use the Netscan dual-use tool, which is delivered via the lateral tool transfer technique (T1570) by copying the arsenal over the RDP buffer. This approach enables the attackers to successfully gather detailed information about the victim’s network and plan further breaches.
Key Assets Discovery
Diligently analyzing the outputs from the network discovery stage, the affiliates identify the crown jewels of their victims, typical of all ransomware attacks, such as data from file servers, financial data, and office documents.
Data Exfiltration
Before encryption, threat actors would archive data that was stored on the systems and upload them on a remote file share. To exfiltrate the data, they used rclone utility and uploaded it to Mega. Acknowledging the awareness of the threat actors, the attacks would then revoke access for the token used to upload data to Mega once the transfer is complete. Group-IB’s Digital Forensics and Incident Response experts have typically noticed large data transfers exceeding 150 GBs in one bulk transfer to a single resource, causing huge network traffic spikes.
Network Propagation
To propagate over the network, attackers employ Remote Desktop Protocol (T1021.001), SMB/Windows Admin Shares (T1021.002) using unpatched smbexec, along with other tools from Impacket collection, and PsExec from Microsoft SysInternals. The lateral tools transfer (T1570) technique is then used to deliver the attacker’s arsenal, as shown below.
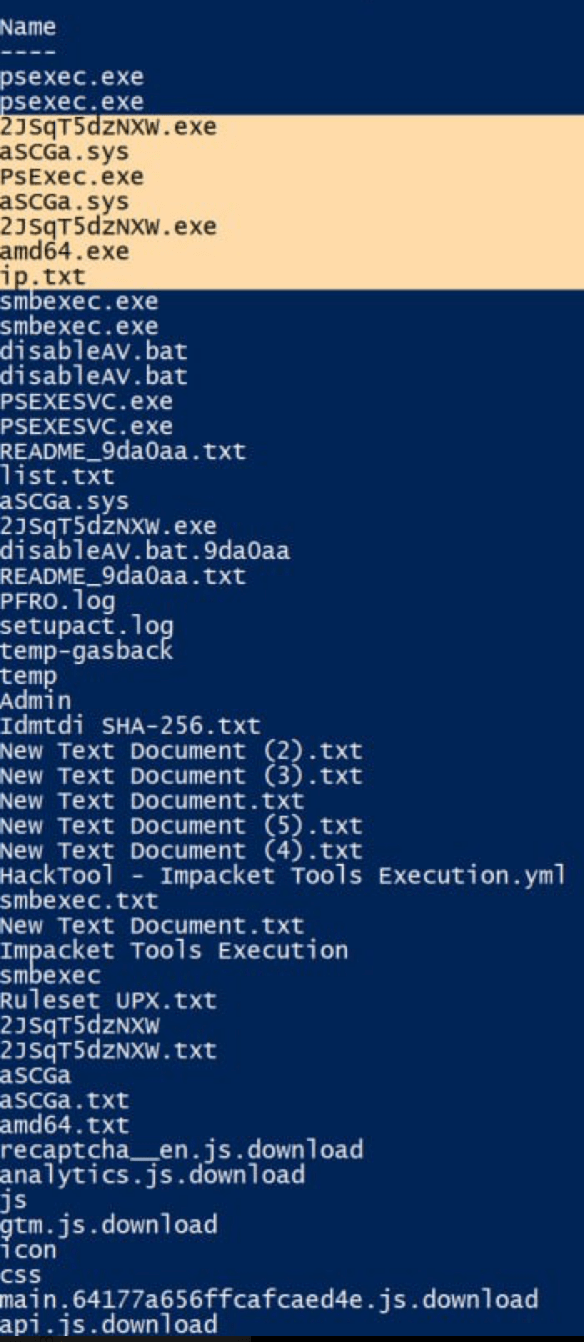
Figure 9. RansomHub affiliate’s arsenal
Deployment Preparation and Ransomware Deployment
The preparation for deployment is usually performed in the compilation of encryption targets’ internal IP addresses in the files like IP.txt. It contains the entries with 1 (one) IP address per line, which are later used as input for smbexec from Impacket framework or PsExec from Microsoft SysInternals tools. The execution command contains the launch of the ransomware file on every host with a predefined command line, as shown below.
amd64.exe -path C:\ -path D:\ -path E:\ -path F:\ -path G:\ -path J:\ -path K:\ -path M:\ -pass
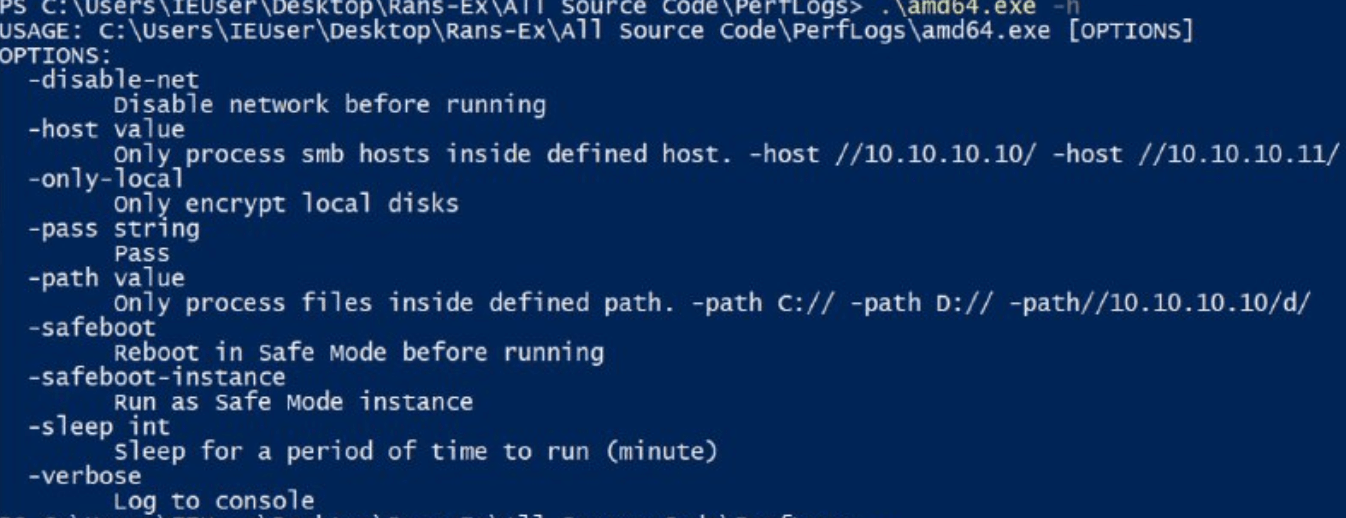
Figure 10. RansomHub locker execution options
disableAV.bat – a BAT file that was used to terminate the antivirus solution (T1562.001).
@echo off REM Copy files from the share to the local C:\temp folder copy "\\\temp\2JSqT5dzNXW.exe" "C:\temp" copy "\\ \temp\aSCGa.sys" "C:\temp" mkdir c:\temp REM Change directory to C:\temp cd /d C:\temp REM Run the copied .exe file start C:\temp\2JSqT5dzNXW.exe
And finally, any data that is encrypted using RansomHub Ransomware will have a random 6 character (CAP LTRS/Numbers) extension attached to the end of the encrypted data filename, and often leave files such as ransom notes with the name README_[random 6 char].txt. The following is a sample of a ransom note:
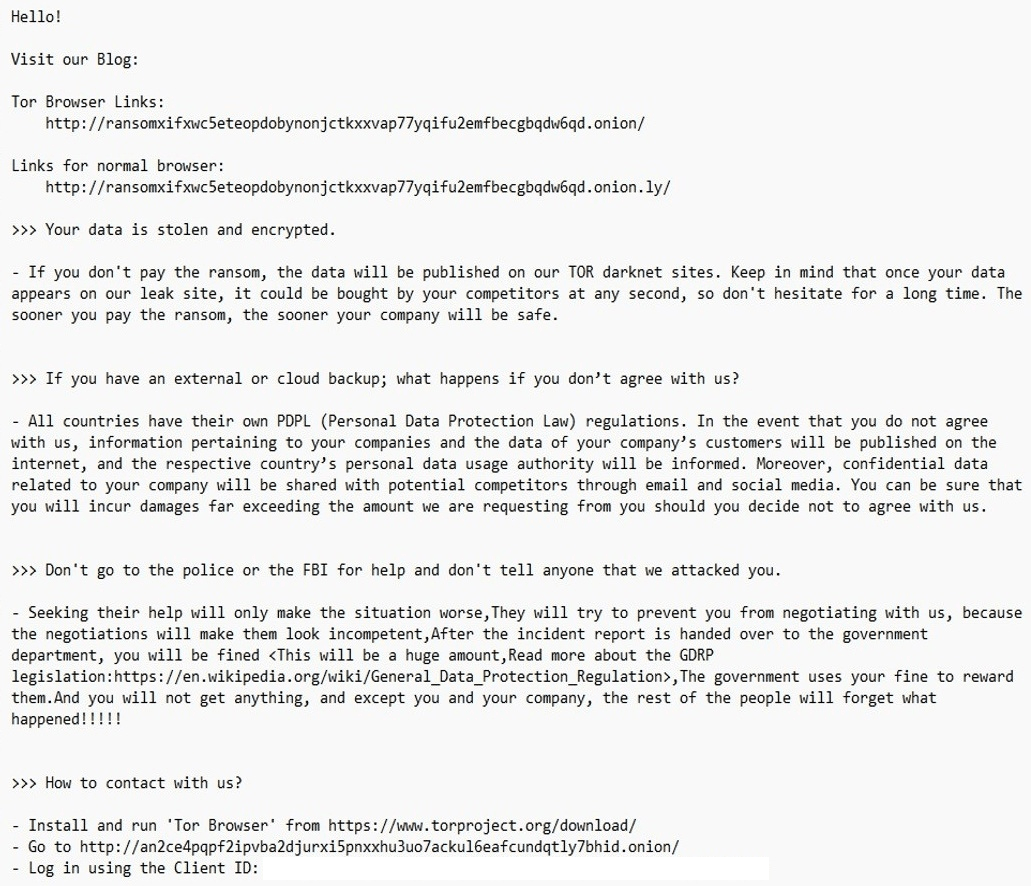
Figure 11. RansomHub ransom note file contents
Conclusion
RansomHub is a sophisticated ransomware group employing a double-extortion strategy by encrypting files and exfiltrating sensitive data to pressure victims into paying hefty ransoms. Targeting primarily the healthcare, finance, and government sectors in regions like the U.S., U.K., Spain, France, and Italy, RansomHub’s tactics include leveraging compromised domain accounts and public VPNs for initial access, followed by data exfiltration and extensive encryption processes. Their recent introduction of a RaaS affiliate program and use of high-demand ransom payments illustrate their evolving and aggressive approach.
To counter such threats, organizations must enhance cybersecurity measures, including strong access controls, vigilant network monitoring, and effective incident response strategies.
Recommendations
- Use an external attack surface management solution to discover any cyber threat exposures of assets, external remote services, user accounts compromised by initial access trojans.
- Enforce one-time password (OTP) based multi-factor authentication (MFA) for external remote services.
- Conduct regular ransomware readiness assessment to discover gaps in security controls, backup systems and sensitive data governance components being a crucial part of the cybersecurity resilience from ransomware attacks.
- Regular comprehensive data backup policies and processes are essential, as they minimize damage and help organizations prevent data loss in the event of a ransomware attack.
- Keep SLA for first response after receiving alerts from endpoint security controls.
- Do not add dual use tools to allowed lists. Monitor dual use tools usage based on EDR telemetry. Always consider events grouping before making a verdict such as: user session details (logon type), process tree, opened network connections, etc.
- Always monitor for significant network spikes to certain external resource, this might indicate the data leak. In most cases, the volume of exfiltrated data exceeded 300 GBs, which is relatively easy to spot from the netflow using network security controls.
- Conducting an annual technical audit or security assessment is not just a good practice, but it also provides an essential layer of protection. Governance of infrastructural integrity and digital hygiene processes is crucial.
- Organizations should leverage advanced analytics-based solutions to detect intrusions in real time, and Group-IB’s Managed Extended Detection and Response (Managed XDR) coupled with Threat Intelligence helps businesses gain insights into the unique Tactics, Techniques, and Procedures (TTPs) used by Advanced Persistent Threats (APTs) and other cybercriminal groups, while also enabling multi-layered cybersecurity (endpoint, email, web, and network) through automated threat detection and response.
- For businesses seeking to enhance their cybersecurity stance and boost resilience against ransomware attacks, we strongly recommend reviewing our Ransomware Readiness whitepaper.