In the wake of increasing ransomware attacks, do security leaders strongly believe that their organization is secure enough, especially when cyber threats are only growing in sophistication?
Group-IB’s Hi-Tech Crime Trends 2022/2023 Report recently revealed that the impact of ransomware attacks will continue to grow in 2023 and beyond, with trends such as the Ransomware-as-a-Service market (RaaS), the publication of stolen data on dedicated leak sites (DLS), and an increase in affiliate programs shaping this trajectory.
In this blog, we aim to provide a detailed breakdown of the ransomware group – Qilin (aka Agenda ransomware). This group, discovered in August 2022, has been targeting companies in critical sectors with ransomware written in the Rust* and Go languages* (Golang).
Group-IB’s Threat Intelligence team infiltrated the Qilin ransomware group in March 2023 and now can reveal inside information about this RaaS program. The blog provides recommendations on how to prevent Qilin’s attacks and will be useful for threat intelligence experts, threat hunters, and corporate cybersecurity teams.
At Group-IB, our ongoing commitment to fighting cybercrime drives us to continue detecting and analyzing Qilin and other ransomware groups’ methods, tools, and tactics. We are committed to maintaining a proactive stance, enabling us to anticipate threats and keep organizations worldwide informed and protected.
Key Findings
- Qilin’s targets are primarily critical sector companies.
- Between July’22 and May’23, Qilin posted 12 victims on their DLS.
- Group-IB analyzed Qilin’s admin panel and revealed information about the affiliates’ payment structure and the inner workings of the program.
- Qilin ransomware group has an affiliate panel divided into sections such as Targets, Blogs, Stuffers, News, Payments, and FAQs to manage and coordinate its network of affiliates.
- Group-IB Threat Intelligence team Identified Qilin’s recruiting posts on the underground forums.
Note:
Rust* A cross-platform programming language used by Qilin along with other nefarious ransomware gangs such as Hive, Blackcat, Luna, etc. Threat actors are increasingly using the programming language as it is more difficult to analyze and has a lower detection rate by antivirus engines.
Golang* A cross-platform programming language used by Qilin and several other threat actors, which is widely popular for its versatility as it eliminates the need to rewrite the malware code for different operating systems.
What is Qilin Ransomware?
Qilin is a Ransomware-as-a-Service affiliate program that now uses a Rust-based ransomware to target its victims. Many Qilin ransomware attacks are customized for each victim to maximize their impact. To do this, the threat actors can leverage such tactics as changing the filename extensions of encrypted files and terminating specific processes and services.
The Rust variant is especially effective for ransomware attacks as, apart from its evasion-prone and hard-to-decipher qualities, it also makes it easier to customize malware to Windows, Linux, and other OS. It is important to note that the Qilin ransomware group has the ability to generate samples for both Windows and ESXi versions.
Qilin advertises the ransomware on the dark web. It has a proprietary DLS that contains unique company IDs and leaked account details, according to observations by Group-IB Threat Intelligence experts.
Operators of Qilin utilize a double extortion technique, i.e., they exfiltrate a victim’s sensitive data in addition to encrypting it. They then demand payment for a decryptor and the non-release of stolen data even after the ransom is paid. Qilin ransomware has various encryption modes; all of which are controlled by the operator.
Qilin Ransomware Attack Lifecycle
A comprehensive understanding of the Qilin ransomware attack lifecycle is essential for mounting effective defenses. This lifecycle can be broken down into several distinct phases:
- Initial Access: Attackers gain entry through various methods, including phishing, exploiting vulnerabilities, and using compromised credentials.
- Establishing a Foothold: Once inside, the operators perform lateral movement and reconnaissance to identify critical assets and assess the network environment.
- Payload Delivery: At this stage, the ransomware payload is executed. Qilin ransomware online campaigns often involve a mix of automation and manual intervention to maximize impact.
- Encryption Phase: The malware encrypts files using robust algorithms, often leaving behind ransom notes detailing payment instructions.
- Ransom Demand: Sometimes, the primary reason for paying the ransom is to prevent the leaked data from being exposed and to protect the company’s reputation, ensuring the attack remains undisclosed. As a result, cybercriminals usually refrain from immediately announcing the attack on their platforms, instead waiting for ransom negotiations to begin.
- Data Exfiltration: Data exfiltration is almost always a core objective. Most modern ransomware operations are double-extortion schemes, where attackers exfiltrate data before encryption to increase leverage during ransom negotiations and maximize pressure on the victim.
Enable Ransomware Protection and Response
Discover Group-IB’s Incident Response core capabilities to approach ransomware attacks with strategic agility.
Behind the Scenes: Qilin Ransomware Operator
Based on previous studies into the ransomware group’s attacks, we know that Qilin targets its victims through phishing emails that contain malicious links to gain a foothold in the victim’s network and exfiltrate sensitive data.
Once Qilin completes initial access, they typically move laterally across the victim’s infrastructure, searching for essential data to encrypt.
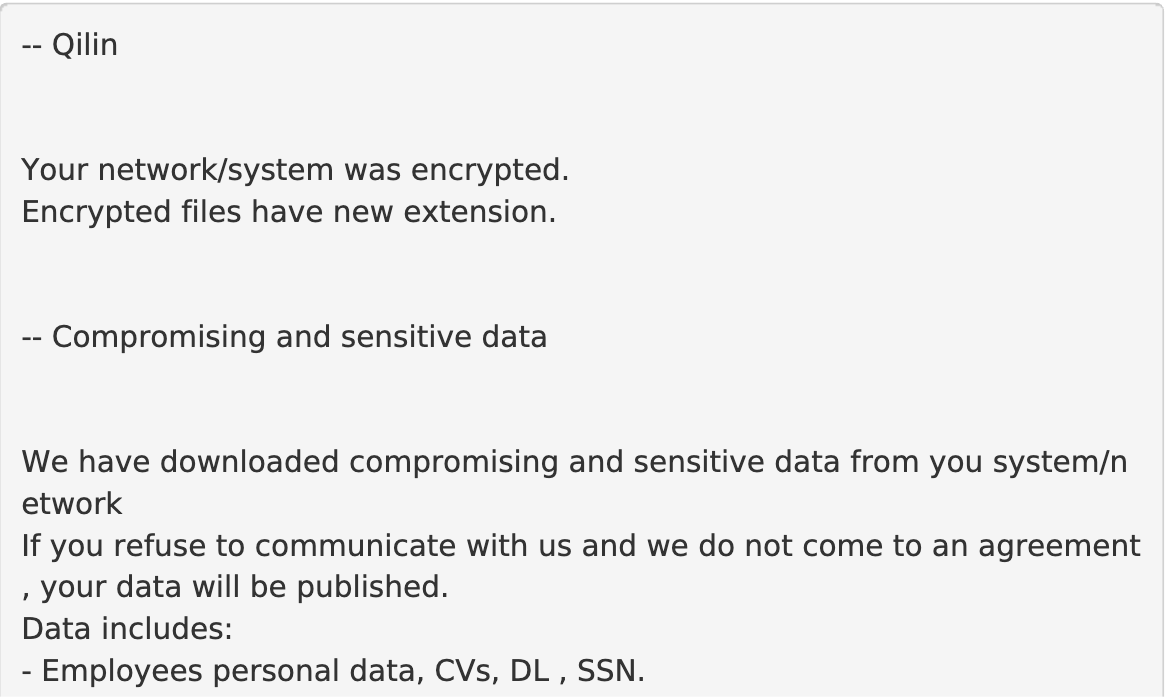
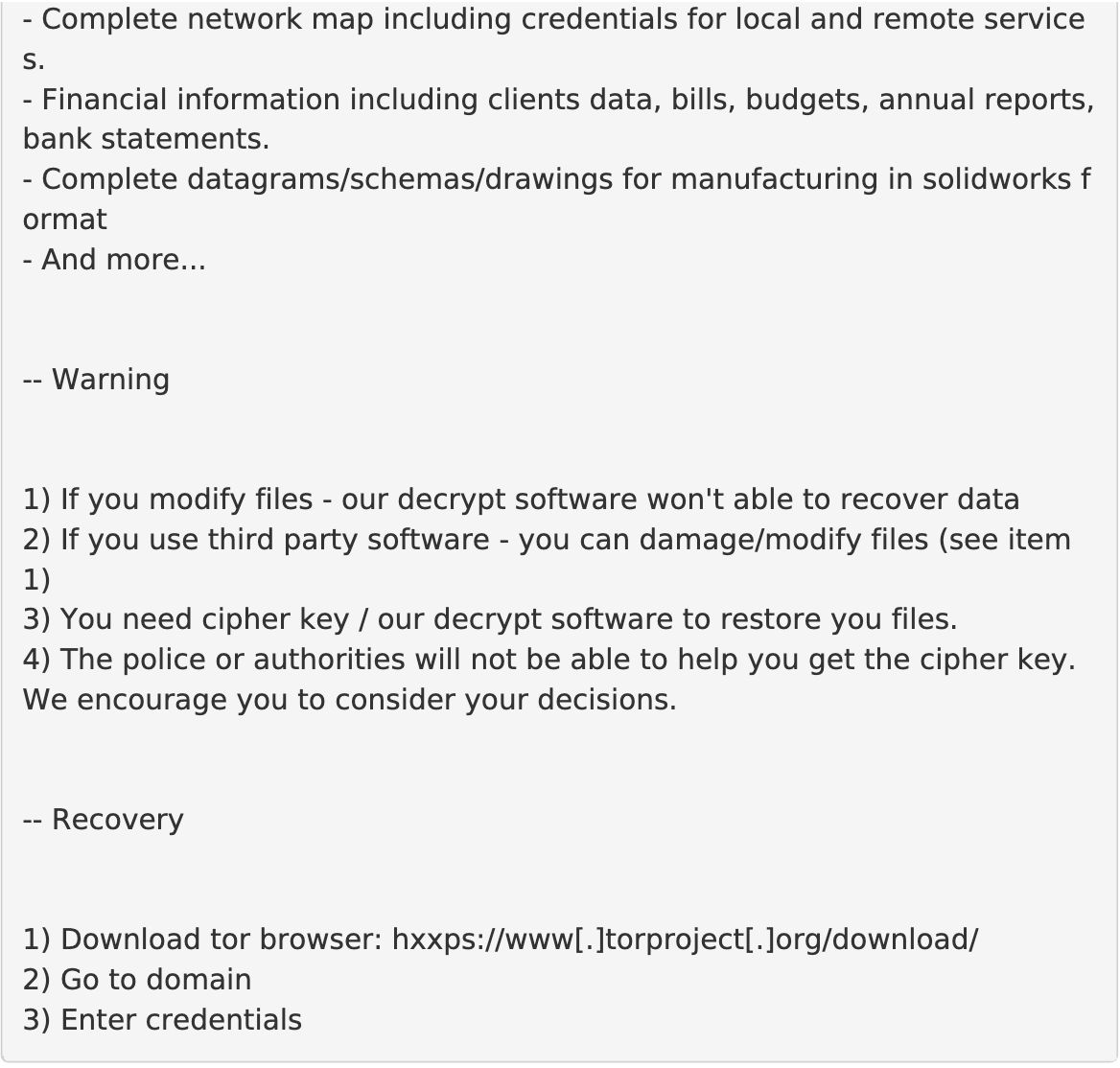
During the encryption process, the actors place a ransom note (Figure 1) in each infected directory of the system, which provides instructions on how to purchase the decryption key.
They may also attempt to reboot systems in normal mode and stop server-specific processes to make it harder for the victim to recover their data. If the ransomware operator is successful in encrypting a victim’s files, it uses a double extortion technique as a means to increase its potential revenue.
Qilin ransomware activities also include posting its victim’s data on the group’s DLS. When analyzed by Group-IB researchers in May 2023, Qilin’s DLS contained data from 12 companies, from the following countries:
- Australia
- Brazil
- Canada (2 victims)
- Colombia
- France
- Netherlands
- Serbia
- United Kingdom
- Japan
- The United States (2 victims)
The distribution of Qilin’s victims posted on their DLS is shown on the map below:

Figure 2: Leaked data on Qilin’s DLS. Source: Group-IB Threat Intelligence
Analysis of Qilin’s admin panel
In March 2023, Group-IB specialists observed that Qilin operates under the RaaS model and provides its affiliates with an administrative panel to manage the attacks more effectively.

Figure 3: Screenshot of Qilin’s affiliate panel. Source: Group-IB Threat Intelligence
Having infiltrated Qilin, Group-IB Threat Intelligence researchers were able to analyze the inner workings of the affiliate program and all sections of Qilin’s admin panel. The affiliates’ panel of the Qilin ransomware group is divided into the following sections:
Section 1: Targets
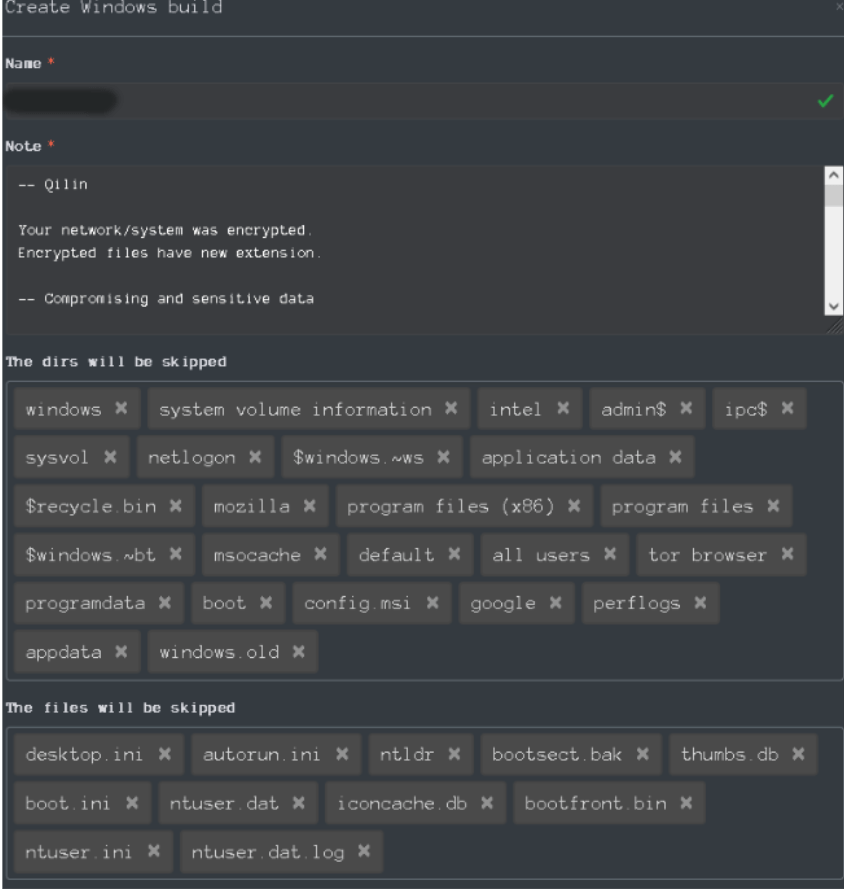
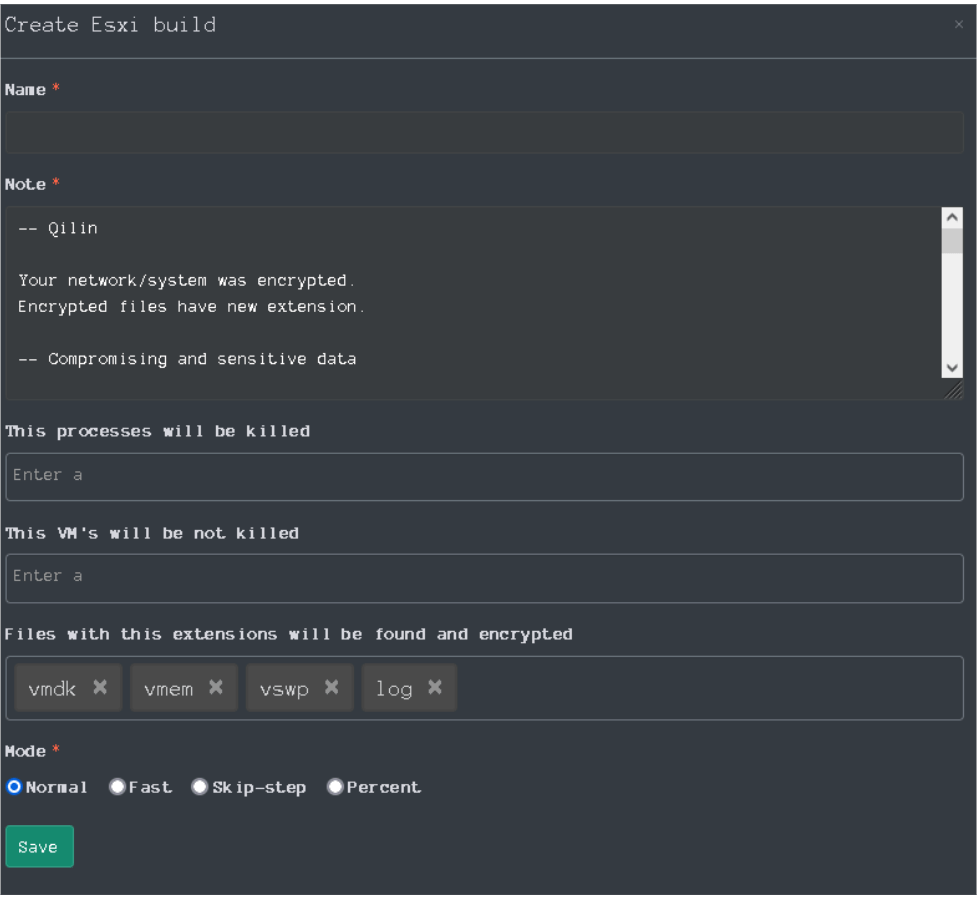
The section named Targets contains information about attacked companies, the size of the ransom, etc. Also, this section allows affiliates to build samples of Qilin ransomware with various settings.
When an affiliate creates a target, they can configure a sample of Qilin ransomware using a builder. The following details can also be configured:
- name of the company
- ransom amount
- waiting period for ransom payment
- timezone of the company
- information about the company’s revenue from the Zoominfo website
- announcement
- description of the attacked company

Figure 4: Information under the ‘Target’ section of the panel. Source: Group-IB Threat Intelligence
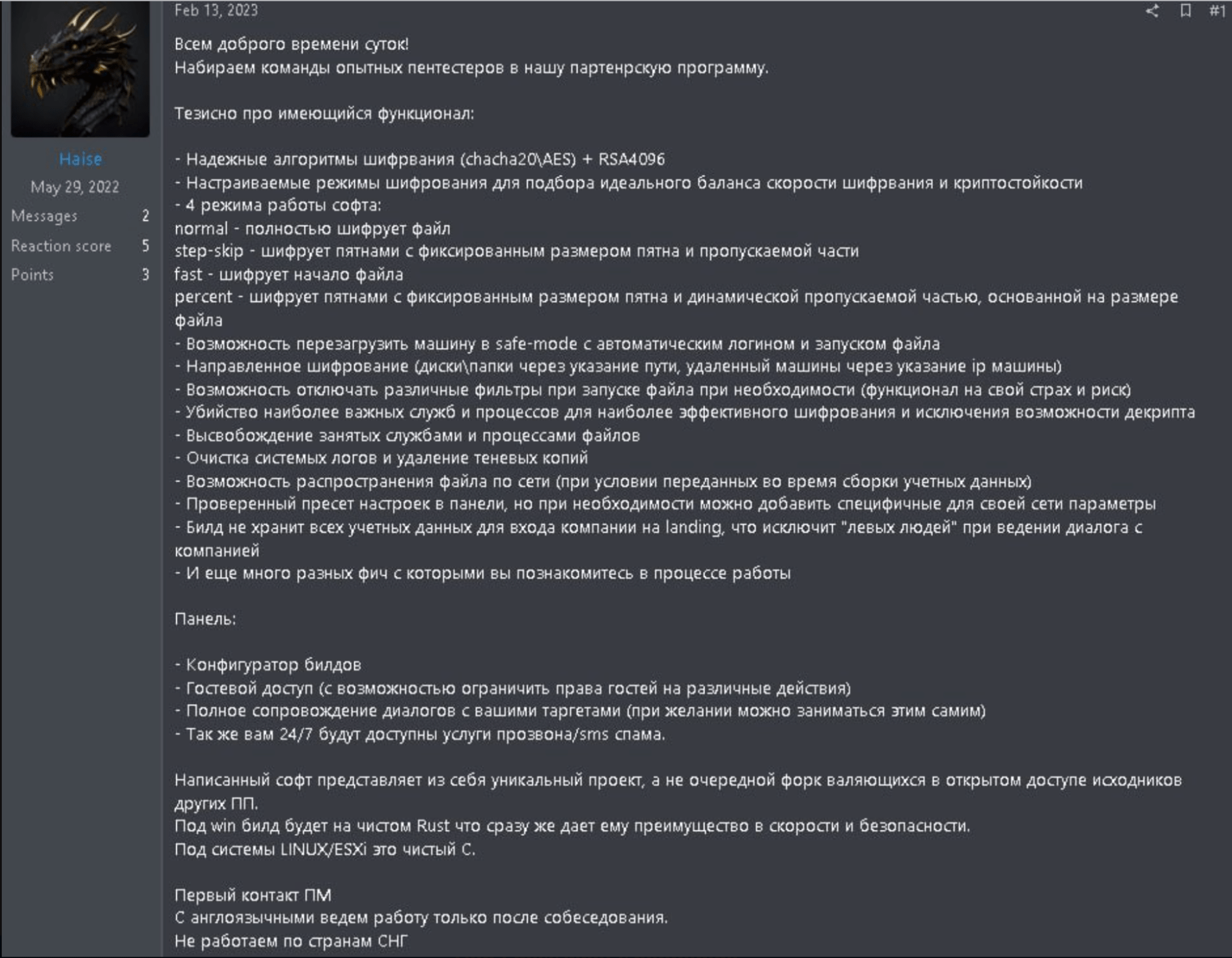
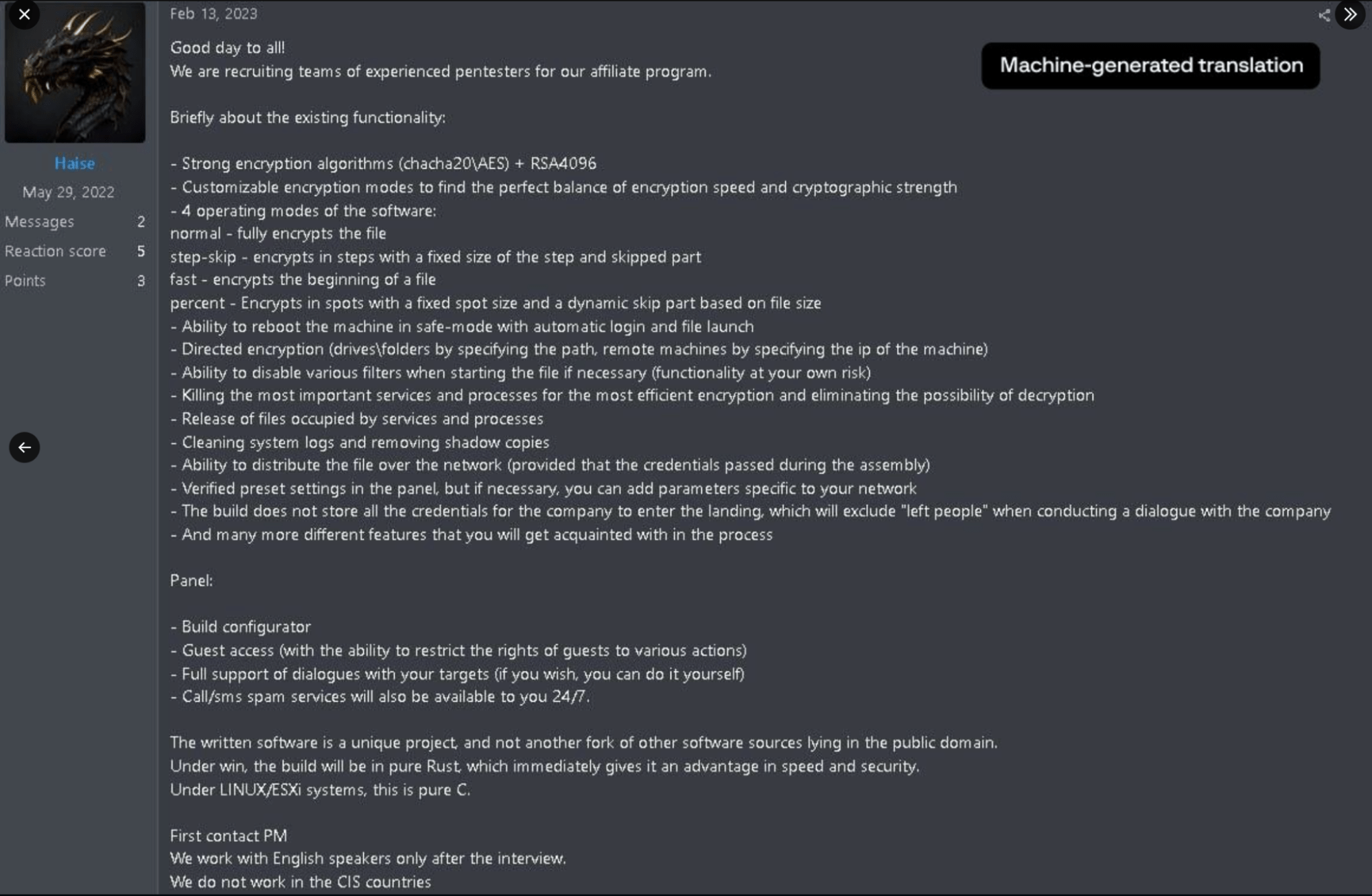
Group-IB’s Threat Intelligence team was able to get information about Qilin’s payment structure as a result of entering a private conversation with one of the users (Haise) on Tox (an open-end messaging app that offers end-to-end encryption), who was identified on the underground forum RAMP. According to the information provided by the owner of the Qilin RaaS program, for payments totaling $3M or less, affiliates earned 80% of the payment; for payments of more than $3M, they earned 85% of the payment.
Group-IB’s threat analysts came across an original screenshot of a post by a “recruiter” from Qilin to hire affiliates and advertise their RaaS on an underground forum. The post is written in Russian and mentions that the group “does not work in CIS countries.”
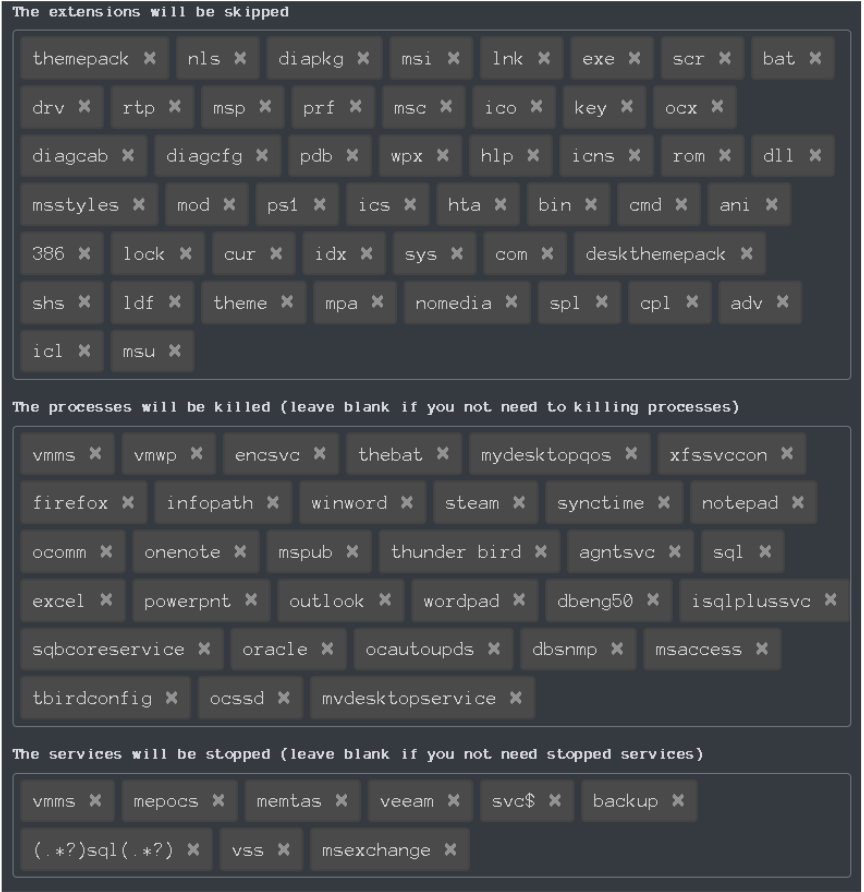
In this section, the intruders can also configure the following
- Content of the ransom note
- The directories that will be skipped
- The files that will be skipped
- The extensions that will be skipped
- The processes that will be killed
- The services that will be stopped
- Login credentials of accounts
- Safe mode excluded hosts
- Mode of encrypting
- Extensions that will be encrypted
- List of virtual machines (VMs) that will be not killed/shut down
Section 2: Blogs
Under this section, affiliates can also create and edit blog posts that contain information about attacked companies that have not paid the ransom.

Figure 7: Screenshot of the Blogs section of the panel. Source: Group-IB Threat Intelligence
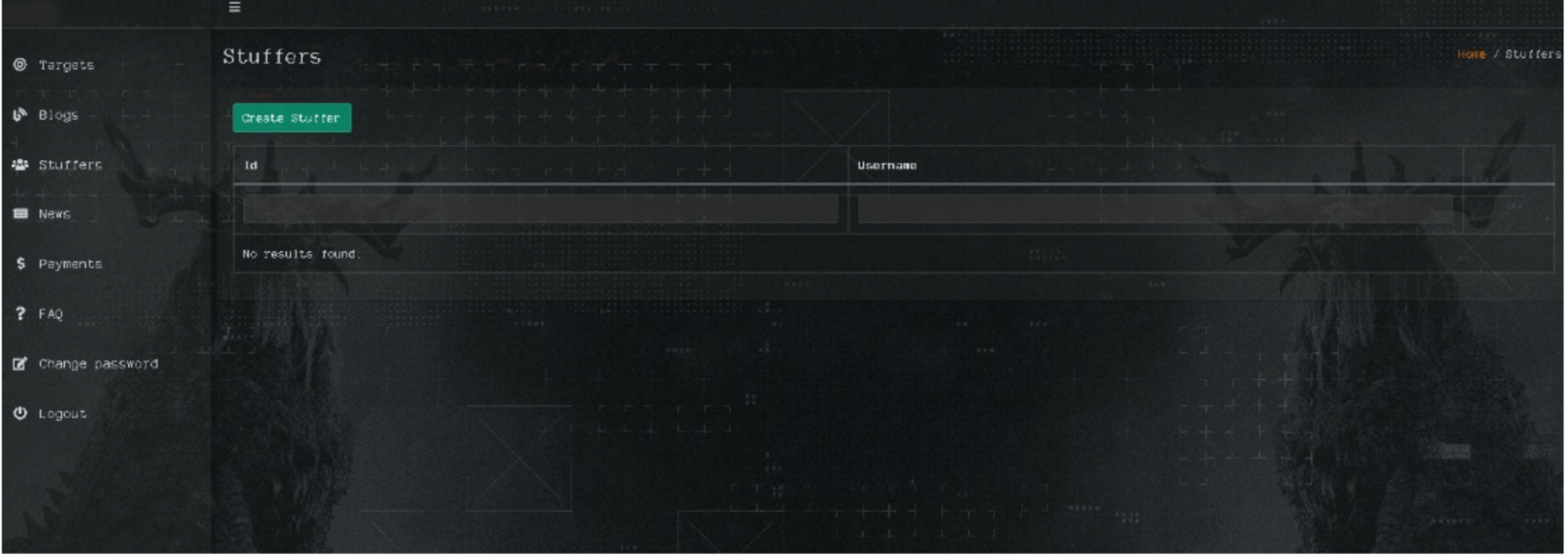
Section 3: Stuffers
The Stuffers section allows intruders to create accounts for members of their team by entering their nicknames, login credentials, and passwords. Additionally, they can control if their team members can witness all of their attacks, build ransomware samples, or gain access to the chats with victims.
Section 4: News
In the News section, Qilin ransomware operators post updates related to their ransomware partnership. However, no published posts are under this section at the moment of reporting (April 2023).
Section 5: Payments
The Payments block contains information about the balance of affiliate wallets, transactions, and fees to the ransomware group. In this section, affiliates can withdraw the ransom money.

Figure 9: Information under the Payments section of the panel. Source: Group-IB Threat Intelligence
Section 6: FAQs
The affiliates also have access to support and documentation in the FAQ section, which details the type of infections, how to use the malware, additional information about the targets, and more.

Figure 10: Information under the FAQs section of the panel. Source: Group-IB Threat Intelligence
Detect and defend against Qilin ransomware
Although Qilin ransomware gained notoriety for targeting critical sector companies, they are a threat to organizations across all verticals. Moreover, the ransomware operator’s affiliate program is not only adding new members to its network, but it is weaponizing them with upgraded tools, techniques, and even service delivery.
That being said, it is absolutely essential that businesses take concrete steps now to keep their mission-critical operations and data completely secured. Here’s how:
- Add layers of security: multi-factor authentication (MFA) and credential-based access solutions help businesses secure their critical assets and high-risk users, making it harder for the attackers to be successful.
- Have a “backup” strategy: data backup processes should be conducted on a regular basis, as they help organizations avoid data loss following ransomware attacks and help their business reduce damages.
- Qilin relies on spear phishing to get access to their victims’ networks. We recommend Group-IB’s Business Email Protection, which is able to counter these threats effectively.
- Leverage an advanced malware detonation solution: Qilin is an emerging ransomware group that is migrating its ransomware code to Rust, which is harder to detect by antivirus engines. Organizations should leverage AI-infused, advanced analytics-based solutions to detect intrusions in real time. Learn how Group-IB’s Managed XDR, coupled with Threat Intelligence helps businesses:
- gain visibility into the unique TTPs of APTs and other threat groups to enable them to pivot their security strategies.
- enable multi-layered cybersecurity (endpoint, email, web, and network) through automated threat detection and response capabilities.
- Patch it up: the longer a vulnerability remains unpatched, the greater the risk of exploitation by cybercriminals. Security patches should, therefore, be prioritized. Organizations also need to set up a process to regularly review and apply patches as they become available.
- Employee training: educate your employees about the risks pertaining to the organization’s network, assets, devices, and infrastructure. The human factor remains one of the greatest cybersecurity vulnerabilities. Organizations should conduct training programs and security drills to help employees identify and report the tell-tale signs of cybercrime (e.g. phishing emails).
- Control vulnerabilities: do not turn a blind eye to emerging vulnerabilities. Checking your infrastructure annually with a technical audit or security assessment is not only a good habit but also adds a much-needed protection layer. Infrastructural integrity and digital hygiene processes need to be monitored repeatedly.
- Never pay the ransom: in 97% of ransomware attack cases, it is impossible to regain access to data without decryption software. Group-IB Incident Response experts do not recommend rushing to pay ransoms demanded by threat actors. Rule number one in the event of an attack – don’t pay the ransom.
Cybercriminals are financially motivated and they are driven to make you pay more. Even if one attacker gives your data back, the other will know about your gullibility and readiness to pay, all leading to an increase in the number of attempted attacks on your company. If you have become a victim of a ransomware attack, the best step you can take is to contact incident response experts as soon as possible.
Frequently Asked Questions
1. How does Qilin ransomware gain access to a network?
Qilin ransomware typically infiltrates networks through multiple initial access vectors, including phishing emails, exploitation of unpatched vulnerabilities, and compromised remote access solutions.
They often include VPN appliances (e.g., Fortinet), RDWeb interfaces, and other remote desktop technologies. Affiliates frequently leverage misconfigured or exposed services, combining social engineering tactics with automated scanning tools to identify weak points and scale their intrusions.
2. What makes Qilin ransomware different from other ransomware strains?
Unlike some ransomware groups that avoid specific sectors, Qilin doesn’t discriminate. They target various industries, focusing on healthcare as one of their primary verticals.
3 Which industries are most targeted by Qilin ransomware?
Industries with critical operations, such as healthcare, financial services, and energy, are often the primary targets. These sectors are attractive due to the high potential for disruption and the willingness of organizations to pay ransoms to restore operations.
4. Can Qilin ransomware be decrypted without paying the ransom?
Generally, decrypting Qilin ransomware without the key provided by the attackers is extremely challenging. However, organizations may recover data through comprehensive backups or by employing specialized decryption tools, although these tools are often limited in effectiveness.
5. What steps can organizations take to prevent Qilin ransomware attacks?
Prevention requires a layered approach, including regular system updates, employee training, robust backup solutions, network segmentation, and the deployment of advanced threat detection technologies.
6. What tools and technologies help detect and defend against Qilin ransomware?
Cutting-edge solutions such as Endpoint Detection and Response (EDR) systems, behavior analysis tools, and AI-driven security platforms are critical. Additionally, an appropriate cybersecurity audit and continuous monitoring can help identify vulnerabilities before they are exploited.
Any question about our products and services, or pricing?
Keep your mission-critical data and operations completely secured from Qilin, and all other ransomware types with Group-IB’s complete stack of next-gen solutions.