Key Takeaways
- Hacktivist activity spiked by 46% above baseline on June 13, but has since dropped by approximately 70% from its peak.
- Analysis of social networks behavior shows eight key channels consistently amplify hacktivist content within 0-15 minutes.
- 16% of content was forwarded or amplified, while 84% was original, reflecting broad decentralized participation.
- The campaign follows a classic hacktivist cycle: an explosive launch → a brief plateau→ a secondary surge in response to geopolitical development → and a rapid decline.
- Looking ahead, activity is likely expected to shift toward short, reactive bursts tied to future geopolitical events rather than sustained campaigns.
Critical Operational Threats
- Iranian-nexus threat actors weaponized Israeli emergency alert systems, sending fake warnings about ammonia leaks and terror attacks to lure civilians from shelters during active missile attacks.
- Regional GPS spoofing incidents affected maritime and aviation navigation across multiple countries (Israel, Iran, Lebanon and GCC).
- Exploitation of exposed Israeli IP cameras provided real-time battle damage assessment and intelligence gathering for potential future targeting.
- Iranian cryptocurrency exchange Nobitex suffered a data breach, exposing internal data and source code.
Introduction
In light of the ongoing escalation in the Middle East, Group-IB Threat Intelligence unit has been closely monitoring cyber activity across the full spectrum of threat actors involved in the conflict—ranging from state-nexus operations to hacktivist networks.
While hacktivist groups have generated significant noise through perception warfare and harassment campaigns, the first week of intensified hostilities has also revealed the presence of more sophisticated cyber operations with direct operational impact.
These include electronic warfare activities such as GPS spoofing affecting regional navigation systems, the exploitation of internet-connected cameras for intelligence gathering, and the manipulation of emergency alert systems aimed at endangering civilians.
This report analyzes both the broader hacktivist ecosystem and the critical, advanced operations that pose immediate risks to regional security and civilian safety. It also provides actionable recommendations for organizations seeking to enhance their resilience against these evolving threats.
Cyber Escalation : Week 1 Summary
Between June 13-20, Group-IB researchers observed over 250 claimed hacktivist attacks, including DDoS attacks, data leaks, and website defacements. These attacks primarily targeted the government, media, financial services, education, transportation, IT, telecommunications and energy sectors, which were the most frequently affected based on claimed incidents.
In line with previously observed tactics, most hacktivist groups attempted to generate attention by focusing on generating visibility by repurposing data from older breaches, often presenting recycled material as evidence of new attacks.
Credible to High-Impact Incidents
Separate from these hacktivist attacks, Group-IB researchers also observed several credible cyber incidents occurring during the escalation that demonstrated significant operational impact. Unlike the largely symbolic hacktivist activities, these incidents affected critical infrastructure, caused documented service disruptions, and required operational responses from affected organizations.
Nobitex Hack
On June 18, the threat actor Predatory Sparrow claimed responsibility for compromising Nobitex, a prominent Iranian cryptocurrency exchange. The group threatened to release the platform’s source code and internal data within 24 hours. In their statement, Predatory Sparrow accused Nobitex of acting as a financial conduit for the Iranian regime, facilitating sanctions evasion and terrorism financing.

Figure 1: Predatory Sparrow announcement on Twitter regarding the Nobitex attack on June 18
Blockchain analysis indicated that approximately $90 million appeared to be “burned” by the actor. Burning refers to sending cryptocurrency to addresses that are provably unspendable, effectively removing those tokens from circulation permanently.
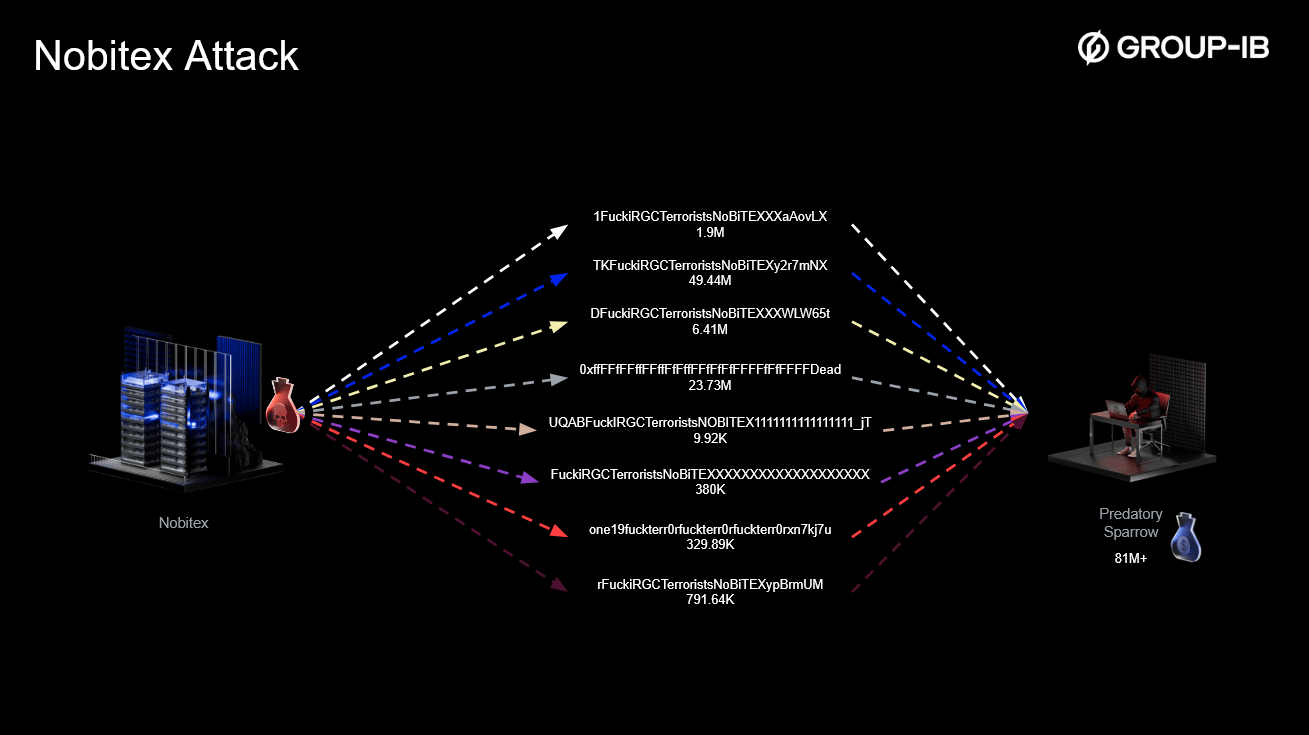
Figure 2: Cryptocurrency flows from Nobitex to burn addresses generated and sent to by Predatory Sparrow
Nobitex initially responded by stating that only hot wallets were affected, and that no customer funds were compromised. However, the threat actor escalated the attack the following day, releasing Nobitex’s complete source code— consisting of over 5,000 directories and 20,000 files— along with more than 25 internal documentation screenshots, further intensifying the reputational and operational impact of the breach.
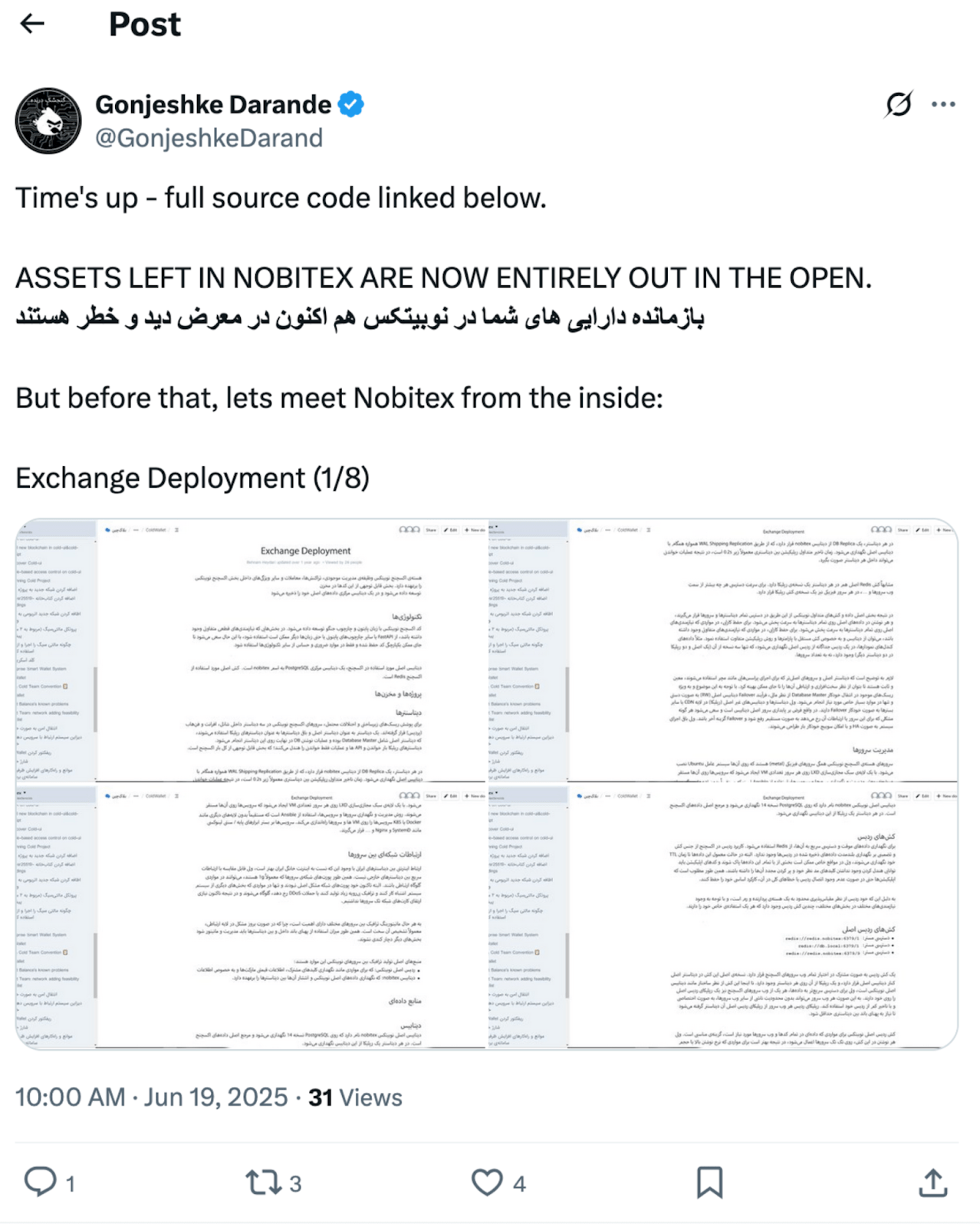
Figure 3: Predatory Sparrow tweet announcing the leak of Nobitex internal data and source code on June 19
The leaked materials exposed critical infrastructure blueprints, security protocols, wallet management code, multi-blockchain implementations, KYC processes, and integrations with Iranian financial institutions. This highly detailed breach effectively provided a complete operational blueprint of the exchange’s operations.
GPS Spoofing Incidents Across the Region
Electronic interference and GPS spoofing activities have intensified in parallel with the Israel-Iran conflict, disturbing maritime, aviation, and GPS-dependent technologies across the Middle East.
Maritime Sector: Vessel Disruption in the Gulf and Eastern Mediterranean
On June 16, the United Kingdom Maritime Trade Operations (UKMTO) issued an advisory warning of “electronic interference” in the Gulf and Strait of Hormuz following multiple reports from vessels operating in the area. According to Windward data, an average of 972 ships per day experienced GPS jamming between June 15-18, with interference peaking at 1,155 vessels on June 16.
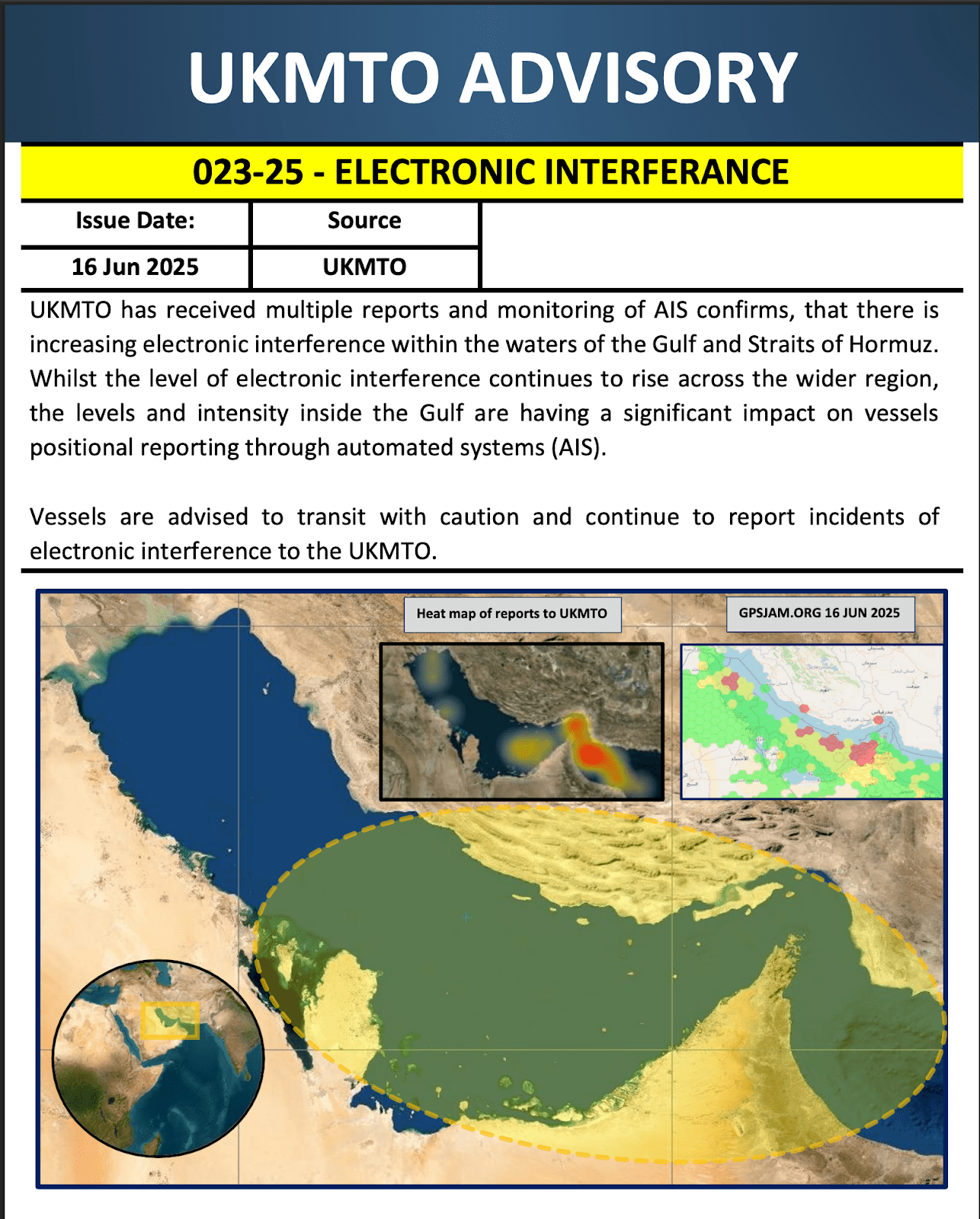
Figure 4: UKMTO advisory from June 16 warning maritime operators of GPS spoofing in the region
GPS spoofing incidents have been documented from June 14-20, with erratic positional reporting observed off the coasts of Haifa, Israel, Iran, and Lebanon.
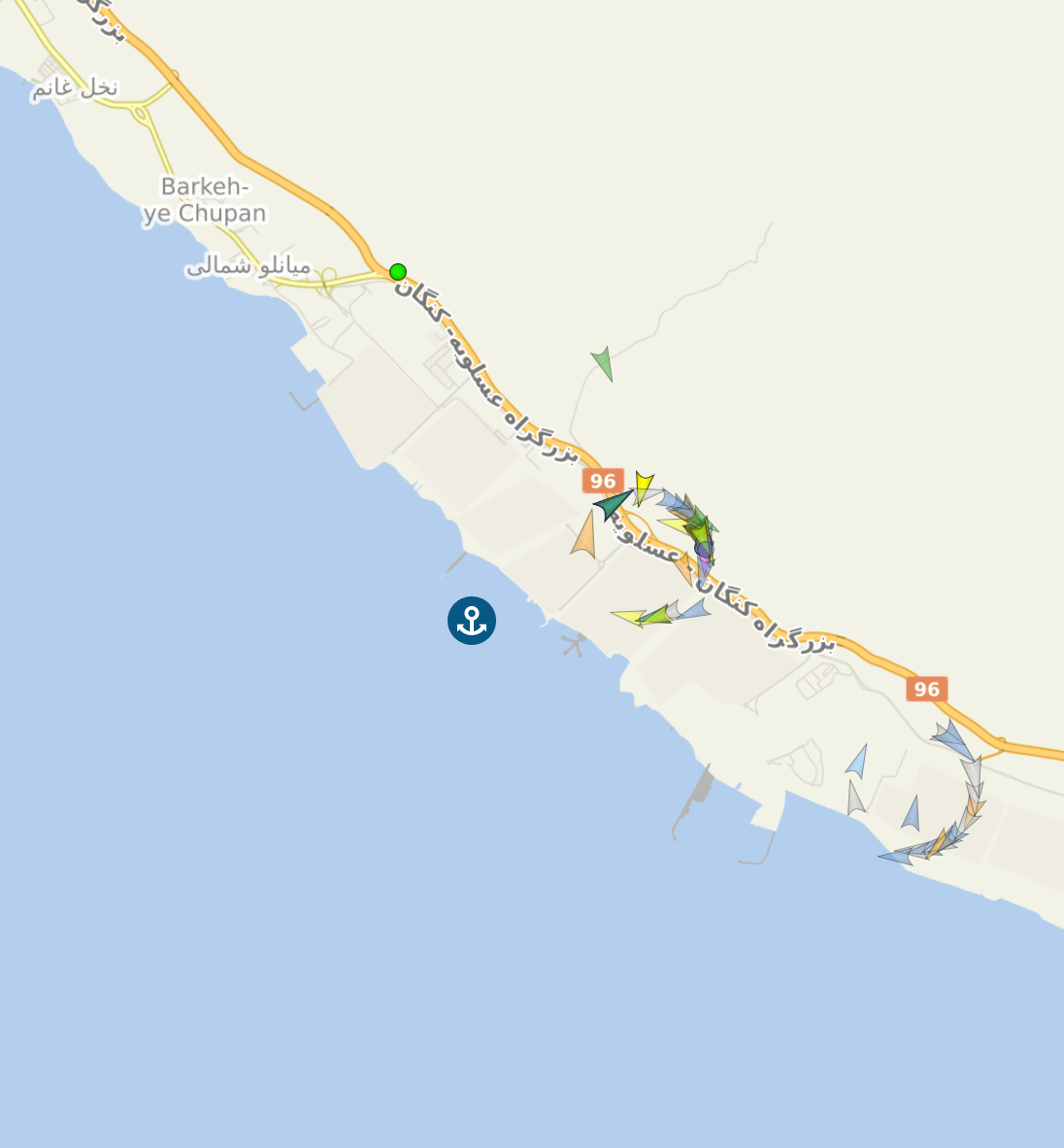
Figure 5: Automatic Identification System (AIS) data showing ‘ghost ships’ with incorrect positioning around Port of Tombak, Iran on June 20 (Credit: VesselFinder)
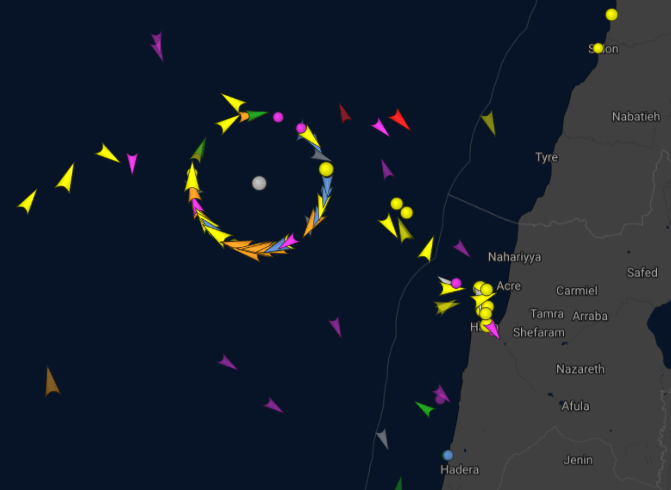
Figure 6: Automatic Identification System (AIS) data showing ‘ghost ships’ with incorrect positioning around Israel and Lebanon on June 20 (Credit: VesselFinder)
Aviation Sector: Confirmed Interference and Spoofing Impacting Flight Safety
According to IATA data, GPS signal loss events increased by 220% between 2021 and 2024, with officials citing geopolitical tensions as the driving factor. The current conflict period exemplified this trend, with widespread GPS interference affecting civilian aviation across the Eastern Med and Gulf regions.
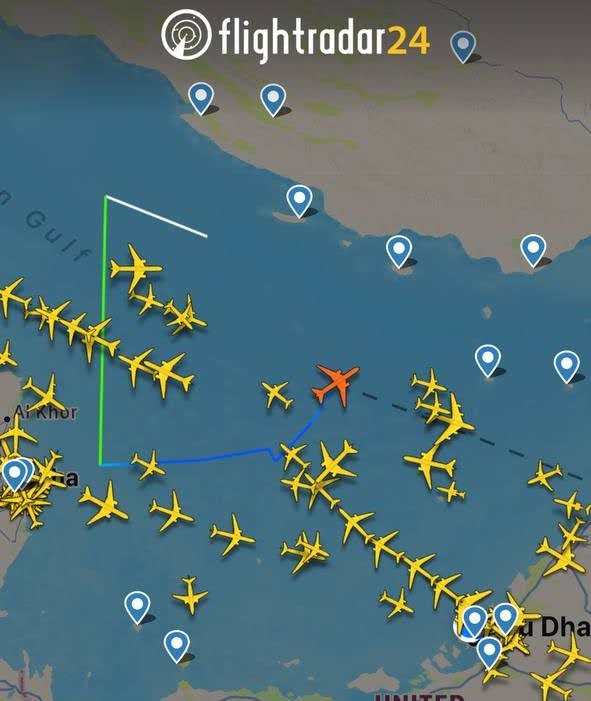
Figure 7: Automatic Dependent Surveillance–Broadcast (ADS-B) data showing erratic aircraft positional-reporting over the Gulf on June 20 (Credit: Flightradar24)
Automatic Terminal Information Service (ATIS) and Aircraft Communications Addressing and Reporting System (ACARS) communications confirm ongoing spoofing activity impacting both maritime traffic and aircraft navigation systems. Some airports in the Gulf explicitly warn pilots of jamming, while others caution them to expect interference. The European Union Aviation Safety Agency (EASA) has issued multiple safety advisories documenting GPS interference & loss of navigation affecting flights in the eastern Mediterranean. Below is an example of such messages:

Figure 8: EASA ACARS message sent to aircraft entering Eastern Med
Regional aviation notices have included standing NOTAMs warning operators in the region of the expected GNSS interference since late May. Additionally, more than 150 GPS interference warnings were documented on public aviation tracking websites like AvDelphi and Airframes.io between June 14-21 for aircraft operating in the Gulf.
Digital Disinformation: Fake Alerts, Camera Exploitations
False SMS Alerts Target Israeli Residents
On June 16, multiple news agencies and official sources reported that residents across Israel received fake SMS messages impersonating official emergency authorities.
The messages appeared to come from “OREFAlert”, the national alert system, and falsely instructed citizens to remain outside of shelters until further notice, citing a fabricated “possible terror attack within shelters”.
Additional false alerts claimed fuel shortages in Israel, with other messages warning of a gas leak, instructing residents to “leave Haifa” and allegedly containing a phishing link.
Official authorities have issued warnings against these messages on the 15th and 16th of June, 2025 as shown on the below figure.
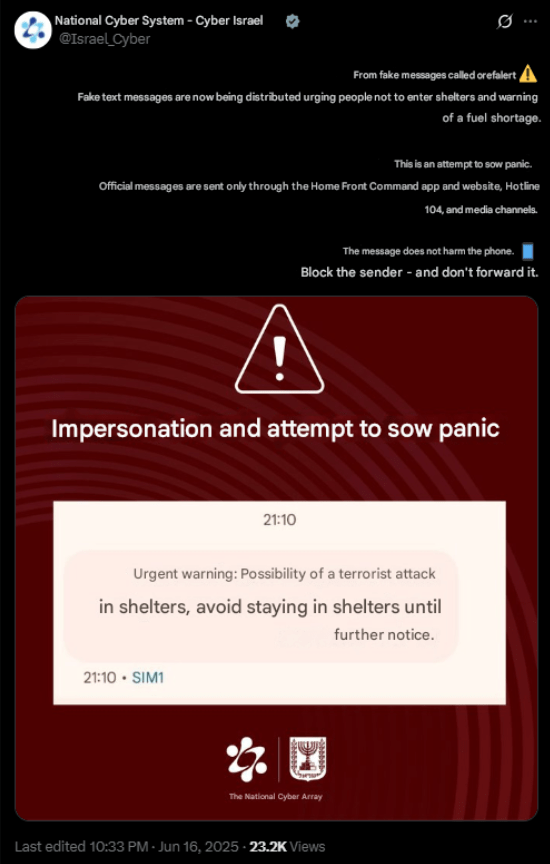
Figure 9: Israel National Cyber Directorate’s warning against fake SMS messages (Credit: X @Israel_Cyber)
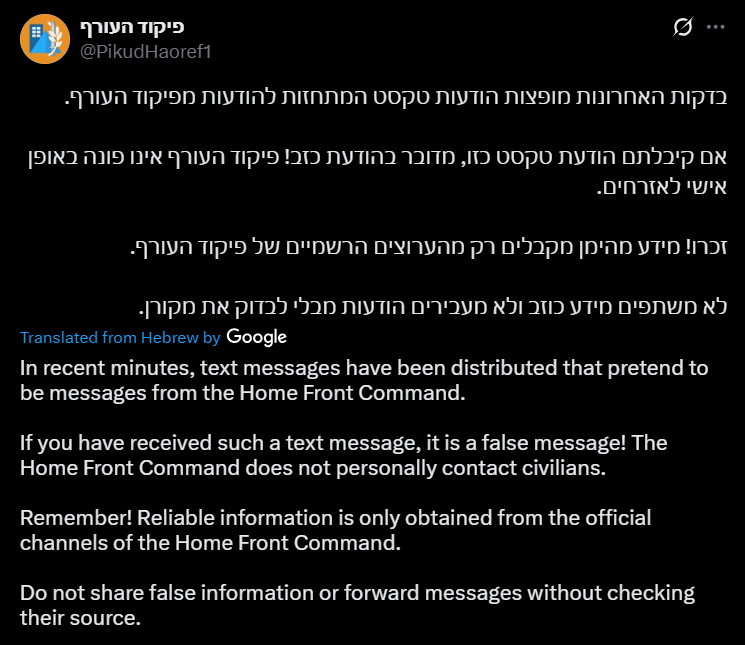
Figure 10: Israel Home Front Command’s warning against fake SMS messages (Credit: X @PikudHaoref1)
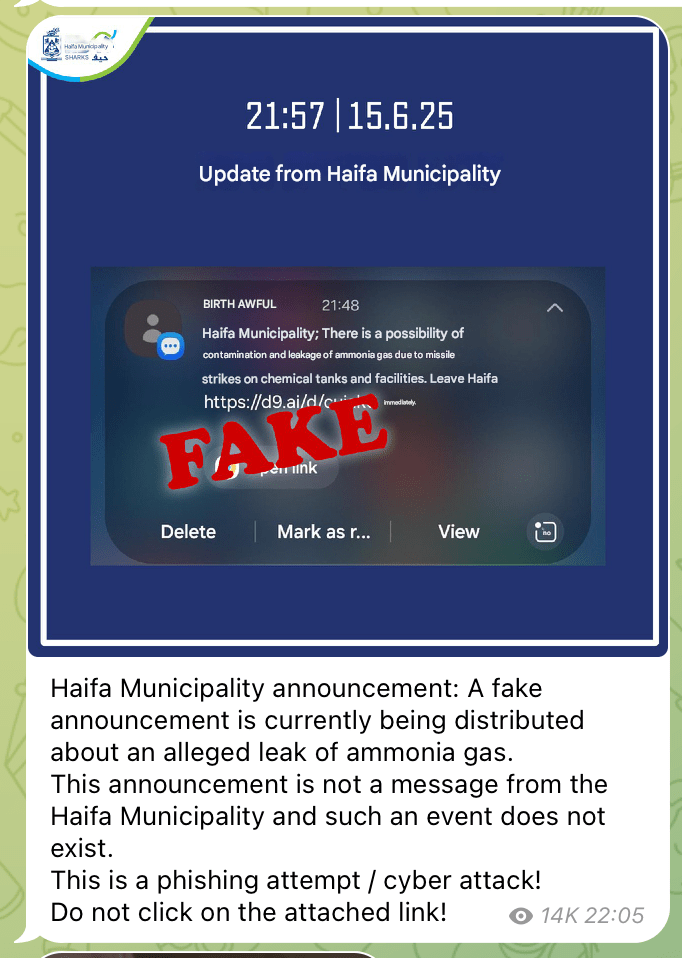
Figure 11: Haifa Municipality warning against fake SMS messages (Credit: Telegram @haifamuni)
Exploitation of Israeli IP Cameras for Strike Assessment
On June 20, Bloomberg reported statements from former Israel National Cyber Directorate (INCD) Deputy Director Rafael Franco, warning of Iranian-linked cyber actors attempting to access IP cameras across Israel. The intent, he explained, was to gather post-strike imagery and assess missile accuracy following recent attacks on Tel-Aviv.
This technique continues a well-established pattern seen in past conflicts. For example, Hamas reportedly accessed thousands of security cameras on the periphery of Gaza before and after the October 7 attacks.
Group-IB research highlights that over 30,000 unsecured cameras remain exposed locally, with pro-Iranian channels circulating access information consistent with methods seen in previous conflicts.
Interestingly, these open feeds are not only leveraged by malicious actors. Open-source analysts and others have used these feeds for real-time conflict monitoring, demonstrating their significant intelligence value to multiple parties. Such feeds are livestreamed on platforms such as Twitch and YouTube as demonstrated in the screenshot below (figure 12).
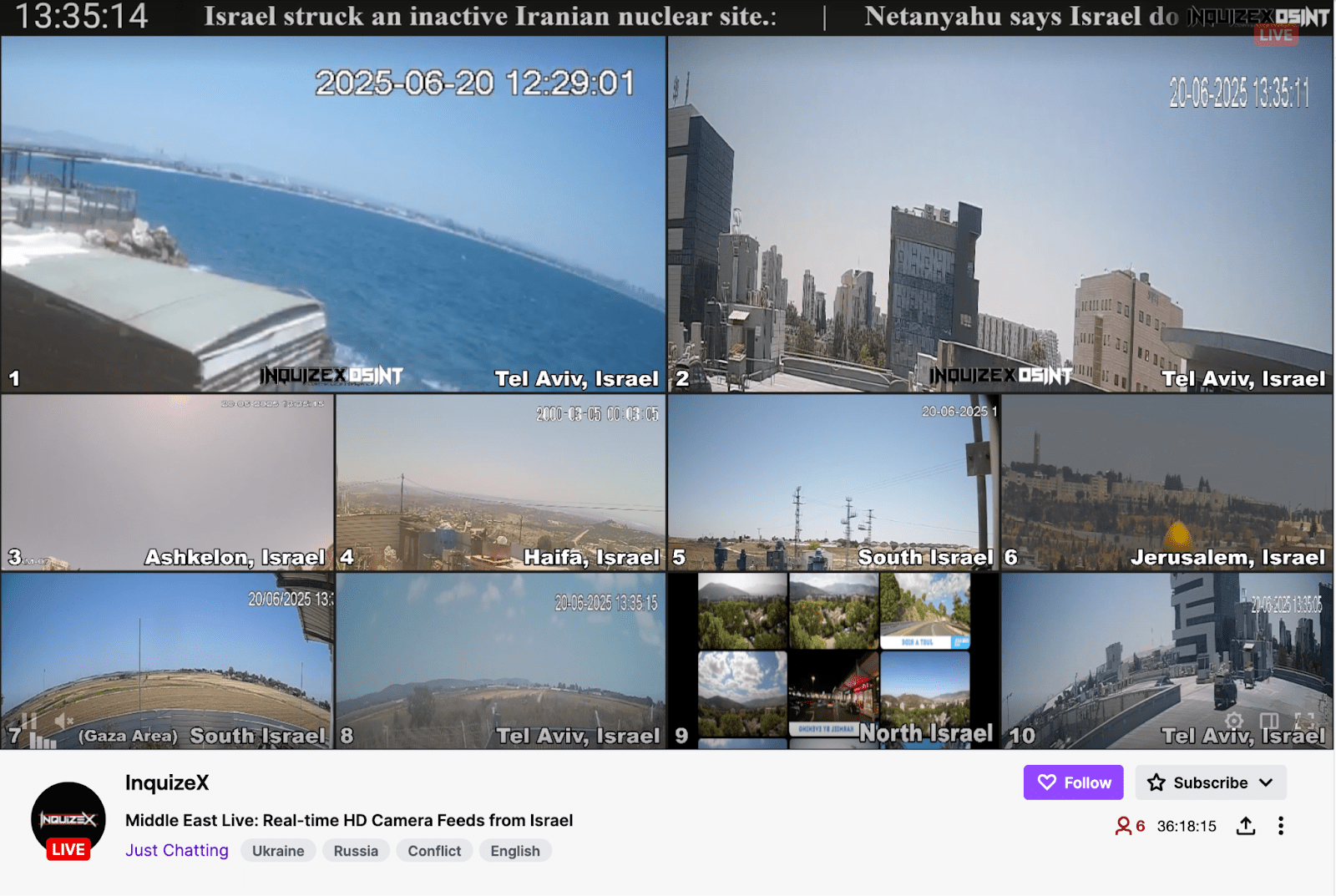
Figure 12: Twitch livestream showing Israeli CCTV feeds, broadcast by an OSINT researcher on June 20, 2025. (Screenshot captured by Group-IB via publicly accessible Twitch stream.)
While this isn’t a novel tactic, this represents one of the few instances where a victim country has officially acknowledged these attacks at this scale.
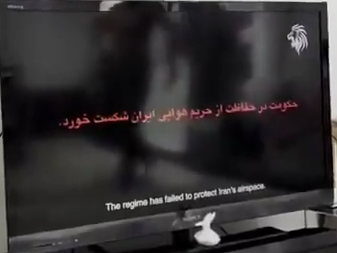
IRIB Stream Disruption
On June 18, Iran’s state broadcaster IRIB TV stream was hijacked to display pro-Israeli and anti-Iranian government imagery, including footage from the 2022 “Woman, Life, Freedom” protests. The broadcast also featured the logo for Operation Rising Lion. IRIB acknowledged the incident and attributed responsibility to Israel, while Israeli officials have reportedly denied involvement.
This incident follows a previous hijacking during the 2022 protests, when IRIB’s web stream was compromised by a hacktivist group called “Adalat Ali,” which broadcast similar content for several hours.
Hacktivist Attacks
Following the escalation of the conflict on June 13, hacktivist groups rapidly mobilized across multiple platforms including Telegram, and broader social media. These loosely coordinated networks primarily engaged in website defacements and distributed denial-of-service (DDoS) attacks, leveraging community size and social media amplification to maximize perceived impact despite limited technical sophistication.
Activity and Temporal Analysis
In the seven days following June 13, Telegram-based hacktivist activity increased significantly, with daily output rising 46% above baseline levels. A single mega-channel now accounts for over 30% of total message reach. Analysis of posting rhythms and the creation of new channels in a short time span suggests a coordinated activation effort rather than organic or spontaneous activity.
Daily Message Volume
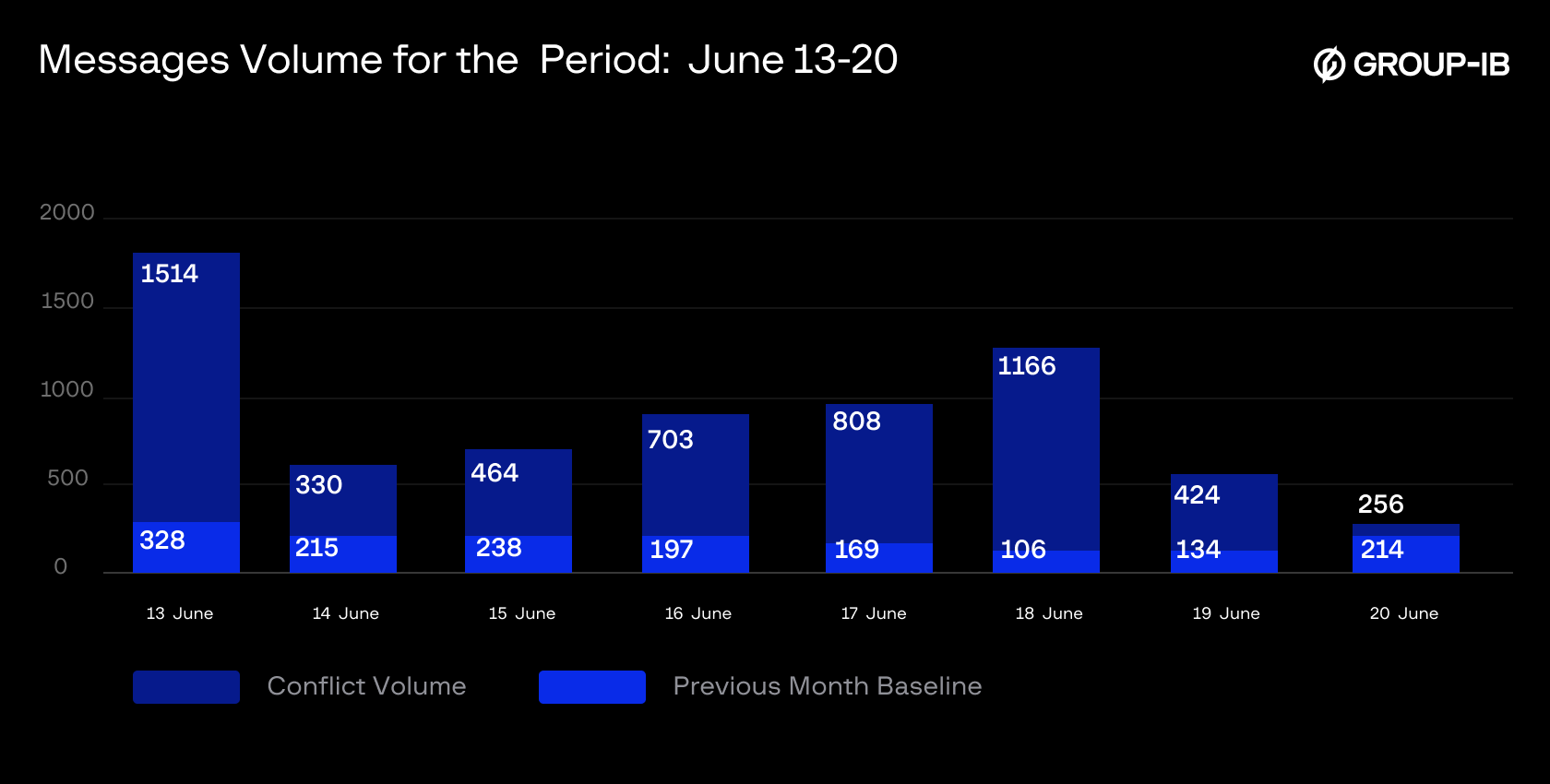
Figure 14: Daily message volume across hacktivist channels, between June 13-20, 2025
Following the initial conflict escalation, hacktivists’ messaging volume surged from fewer than 100 messages on June 12 to over 1500 messages on June 13 — a spike consistent with the start of the conflict.
The operation tempo followed a classic hacktivist wave pattern: an explosive launch, brief stabilization (June 14-17 averaging 576 messages daily), a secondary surge on June 18, followed by a consistent rapid decline.
Summary of the channel dynamics
- Primary surge (June 13): 1,514 messages.
- Brief stabilization (June 14-17): average of 576 messages per day.
- Secondary surge (June 18): 1,166 messages.
- Post-surge decline: A consistent drop in message volume, now down by ~70% from the peak.
Notably, if June 13’s surge is excluded, activity levels never return to that initial momentum. Even the June 18 spike recovered only ~75% of launch-day volume, indicating a waning narrative trajectory. Group-IB assesses that future activity will likely consist of short, reactive bursts, aligned with geopolitical flashpoints, rather than a sustained, coordinated campaign.
Channel Network Analysis
- The most referenced channel was DieNet, quoted 79 times across other Telegram channels.
- Approximately 16.16% of content was forwarded (amplified from other sources), while the remaining 83.84% was original content—suggesting broad, decentralized participation.
- More than 5,800 messages in total were recorded across observed hacktivist channels between June 13-20.
- Analysis of message forwards during the conflict period reveals a distinct bimodal pattern in timing behavior. The majority of forwards fall into two categories: immediate response (26% within 0-15 minutes) and delayed (50% after 12+ hours). The middle timeframes show significantly lower activity—only 8.5% of forwards occur within 15-60 minutes, and just 15.3% within 1-12 hours combined. The relatively low activity in intermediate timeframes (15 minutes to 12 hours) suggests forwarding behavior clusters around immediate response and delayed discovery, rather than consistent ongoing sharing throughout the day.
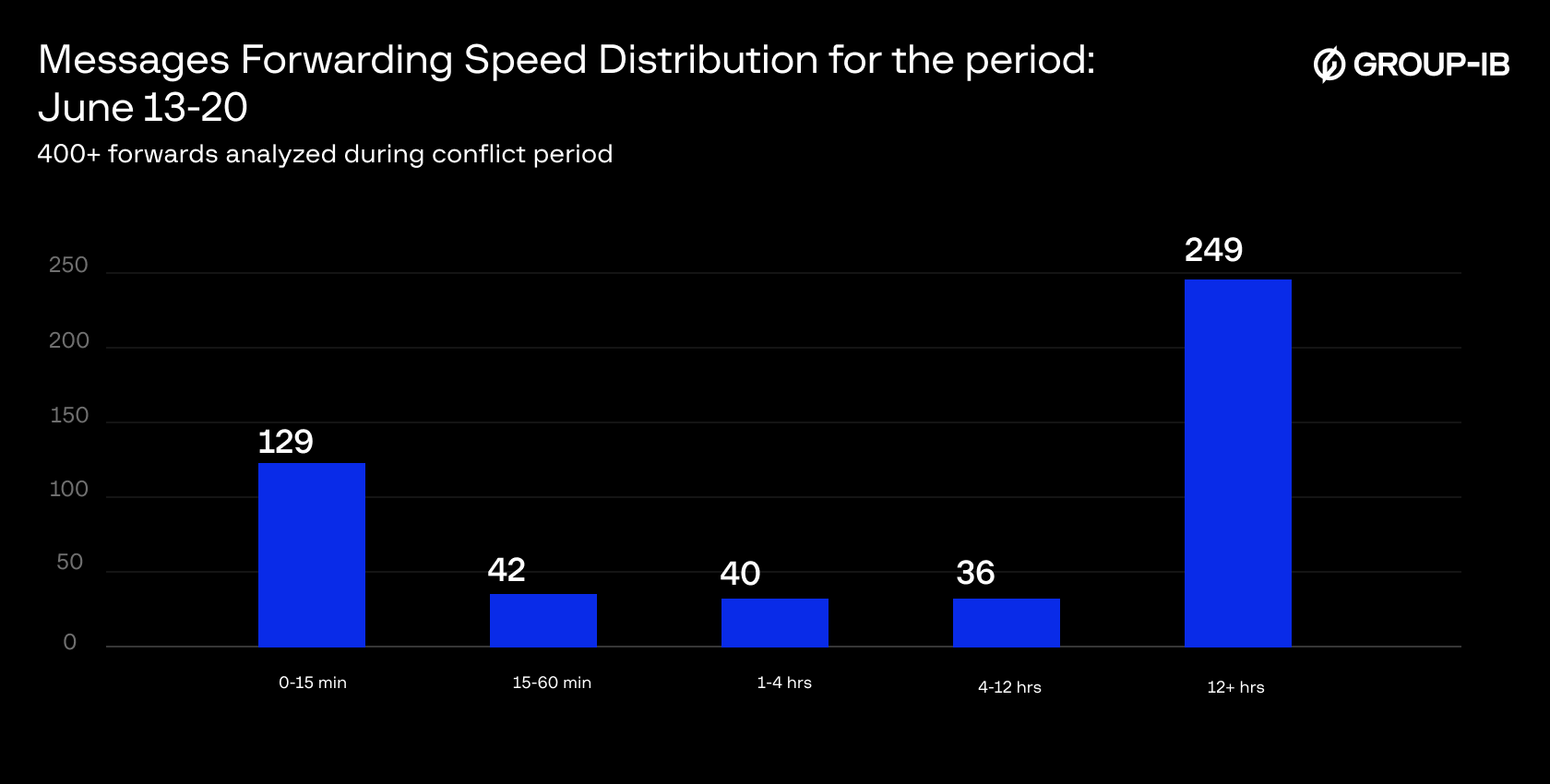
Figure 15: Hour-of-Day Activity of Monitored Hacktivist Channels, June 13-20
Hour-of-Day Activity
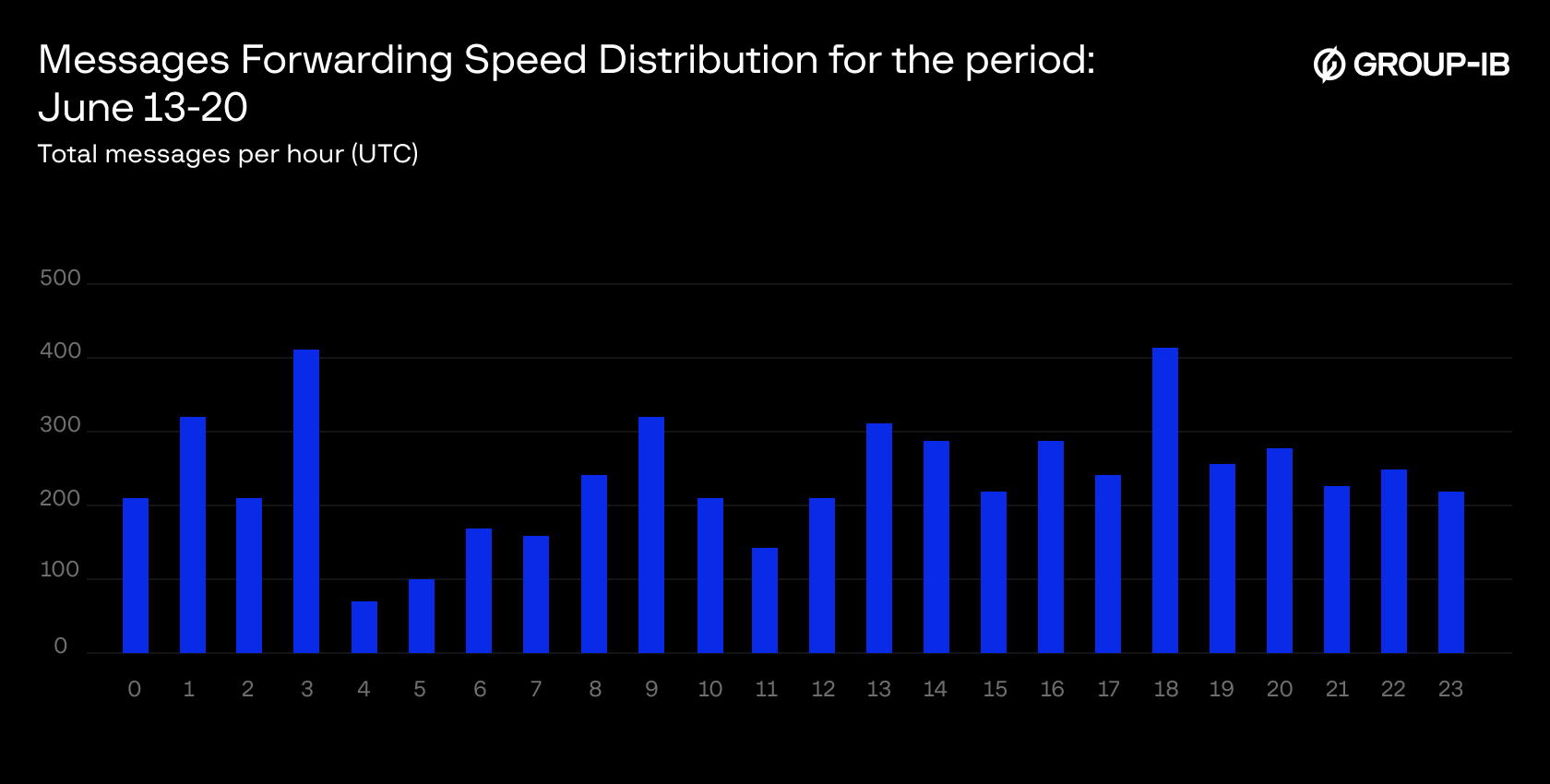
Figure 16: Hour-of-Day Activity of Monitored Hacktivist Channels, June 13-20
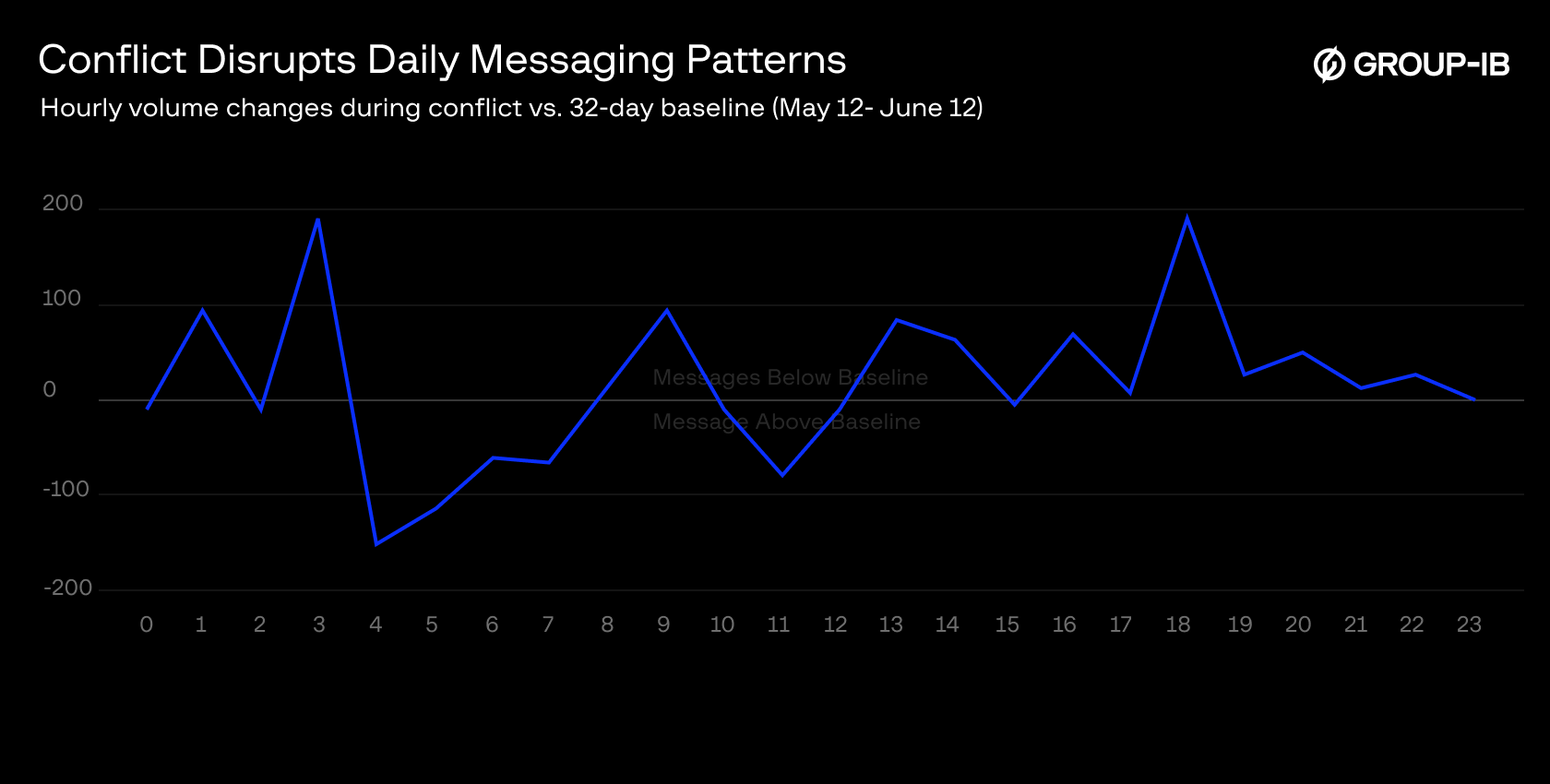
Figure 17: Change in active hours during the baseline period (May 12 – June 12) vs. conflict period (June 13-20)
During the first week of the conflict (June 13-20), hacktivist channel activity patterns shifted dramatically compared to baseline (May 12 – June 12):
- Early morning activity surged 74.5% compared to the baseline,
- Afternoon/evening peak of the baseline activity collapsed during the conflict week, with a 47% decrease,
- Activity during 04:00-07:00 UTC remained consistently low in both periods
A noticeable drop in activity between 04:00–07:00 UTC suggests the presence of human-operated posting cycles, rather than fully automated distribution. This rhythm aligns with regional work/rest hours and supports the assessment that, despite some automation, manual curation remains central to the campaign’s content dissemination.
Exaggerated or False Claims
As seen in previous conflicts, hacktivist groups have generated significant noise around alleged cyber attacks and data breaches. However, most claims lack credible evidence and appear attended more for harassment and perception management rather than operational impact. The following examples illustrate the typical patterns for exaggerated or fabricated incidents.
False Claim: Compromise of Egyptian Universities
Shadow Unit is an Arabic-speaking hacktivist group which appeared on Telegram on September 28, 2024 and has since gained approximately 1,240 followers. Initially, the group demonstrated opportunistic targeting behavior, claiming responsibility for website defacements and alleged data leaks. There was little evidence of a strategic operational motive or targeting patterns. In October 2024, the group shifted its focus to include Israel in its messaging, calling on other hacktivist teams to launch coordinated cyberattacks.
Figure 18: “Shadow Unit” Telegram profile
Following recent regional developments in June 2025, Shadow Unit began claiming responsibility for DDoS attacks and data leaks against both Israel and Egypt.
On June 17, the hacktivist group claimed to have compromised the credentials of 12,000 faculty members and students of “prominent Egyptian universities” (figure 19).
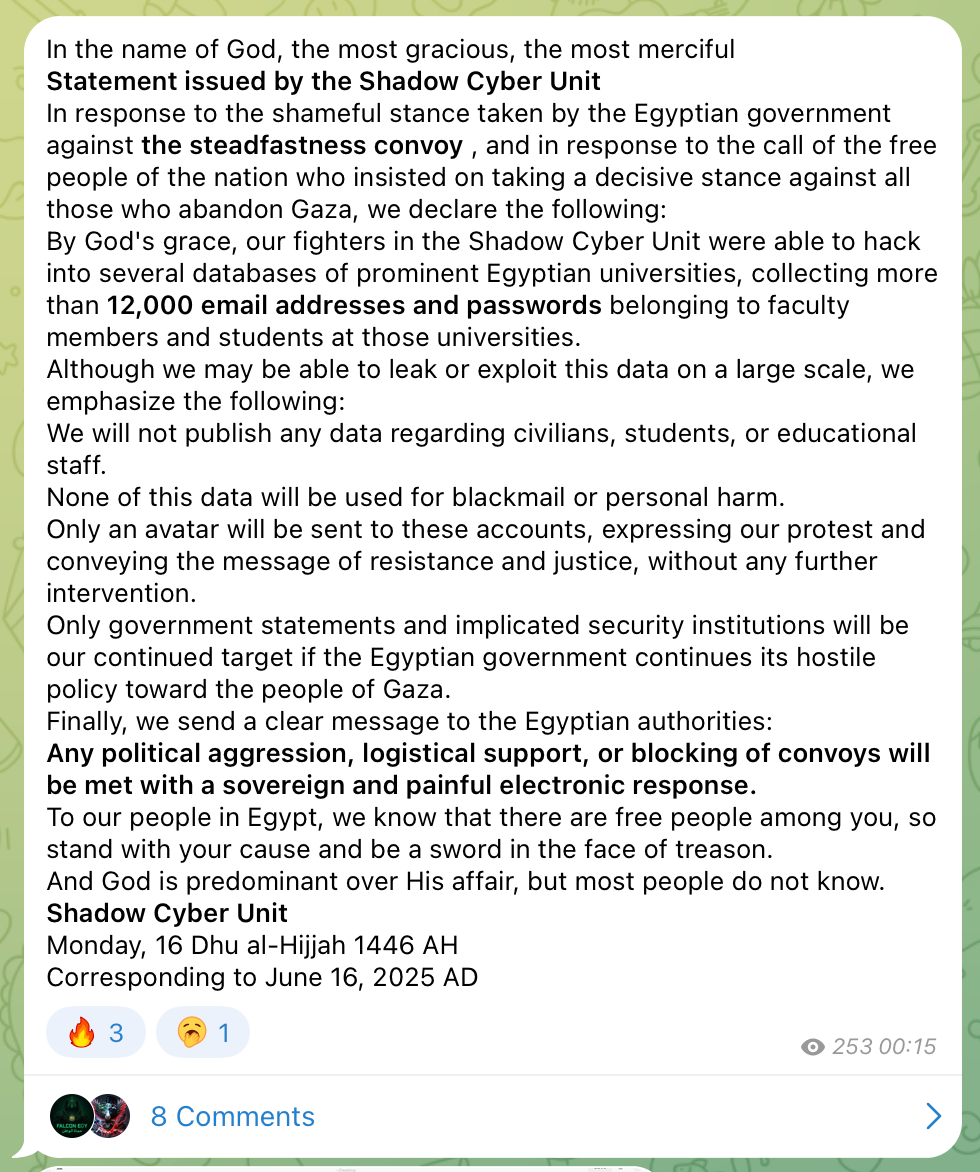
Figure 19: Statement by Shadow Unit posted on June 17th, (credit: Shadow Unit’s Telegram Channel)
While the group did not mention specific targets, Shadow Unit posted an image showing the allegedly compromised credentials as shown below.

Figure 20: Fabricated screenshot from Shadow Unit claiming Egyptian university student credentials breach (Credit: Shadow Unit’s Telegram channel)
Group-IB specialists analyzed Shadow Unit’s claim, and assessed it to be not credible, based on several factors. Historically, breaches and data leaks claims made by hacktivist groups are frequently found to consist of recycled data from previous breaches, stealer logs or combolists.
Combolists are files containing large volumes of login:password entries, commonly shared through illicit channels including Telegram and dark web forums. These compilations typically contain a mix of old, recycled, or entirely fabricated credentials rather than newly compromised data.
Using Group-IB’s Threat Intelligence platform, analysts confirmed that the credentials claimed by Shadow Unit were sourced from previously known combolist files, with no indication of a recent compromise.
Recycled Data Mispresented as SAP Israel Leak
RuskiNet is a hacktivist group first observed in February 2025 on X (formerly Twitter). Over four months of activity, the group has claimed responsibility for cyberattacks targeting organizations in Russia, the United States, Poland, Nigeria, Algeria, Turkey, India and Israel.
Their claims span DDoS attacks, website defacements, and alleged data leaks across more than 16 industry sectors.
Figure 21: “RuskiNet” X profile
Group-IB analysts have been monitoring RuskiNet since its emergence, and assess the group to be of low reliability based on data leaks claimed on their social media presence and dark web forums, which bear low credibility.
Figure 22: X Post by RuskiNet mentioning an affiliated user; “YK3”
On June 13, a RuskiNet-affiliated user operating under the alias “YK3” on the DarkForums marketplace claimed to have leaked data belonging to 38,000 employees of SAP Israel.

Figure 23: RuskiNet-affiliate; “YK3” claiming a leak of 38,000 Israeli SAP employees’ data
While the dataset included entries referencing SAP Israel, Group-IB analysts identified numerous matches with a previously known data leak from October 2023, originally associated with an Israeli digital payments platform.
Recommendations for Organizations
To mitigate the risks posed by recent regional cyber escalations in the Middle East region, Group-IB recommends actionable measures:
- DDoS Attacks
- Use Group-IB’s Threat Intelligence to stay updated on hacktivist groups’ tactics, techniques and procedures (TTPs), upcoming campaign attacks and IP infrastructure.
- Our tailored threat intelligence provides organizations with context-specific threat landscape and relevant risks, customized reporting, and early warnings—moving beyond generic alerts to improve response time and mitigation efficiency.
- Many threat actors employ automated DDoS tools to execute their attacks. These tools often utilize predefined lists of proxy addresses. These lists are collected, regularly updated, and provided by Threat Intelligence systems. Additionally, some attackers conceal their real IP addresses using standard methods like VPNs, proxies, or TOR. Group-IB’s Threat Intelligence also collects this information and can enhance lists of suspicious IP addresses to facilitate the process of blocking incoming malicious traffic.
- Enable anti-DDoS protection and ensure it’s active. Diversify providers: use multiple ISPs or cloud providers to ensure redundancy. If one is attacked, you can fall back on others.
- Upstream filtering: Work with ISPs that offer malicious traffic filtering to block malicious traffic before it reaches your network.
- Scale resources: Auto-scale resources to absorb traffic spikes, especially using cloud services that provide auto-scaling.
- Rate limiting: Cap the number of requests a user can send in a certain time frame.
- Bot protection: If you are facing an L7 DDoS attack on web apps and the current provider has issues, ensure your organization has bot protection in place.
- Geofencing: Block non-region-related IP access for critical applications in the active face of an attack.
- Use blacklisting and whitelisting.
- Save logs during DDoS attacks: Technical information about the attack can significantly improve your detection and prevention capabilities after an in-depth analysis. Furthermore, it offers valuable insights for further investigation.
- Defacements
- Regular Backups: Store backups both on-site and off-site to ensure you can quickly restore your website after a defacement.
- Update CMS: Make sure that your Content Management System (CMS) is not accessible from the internet and is regularly updated to the latest version. Update all plugins, themes, and extensions. Outdated plugins can be a common vector for attacks.
- Regularly update web-server backend software to prevent exploitation with common CVEs.
- Web Application Firewall (WAF): Configure a WAF to inspect incoming traffic, block malicious requests and attempts to exploit vulnerabilities.
- Start searching for your publicly facing shadow IT assets to uncover potential vulnerabilities that can be exploited by threat actors. We recommend solutions such as Attack Surface Management.
- Limit shadow IT: Limit your exposure by disabling unnecessary services that are not in use and do not use default URLs for login or admin panels.
- Restrict CMS access: The emergence of underground markets has simplified the attack process for potential intruders, including hacktivists. These illegal marketplaces provide pre-compromised CMS access or web shells, removing the need for attackers to breach these systems themselves. Use Threat Intelligence platforms to obtain information about any unauthorized access that may be up for sale. It can preempt potential threat activities, neutralizing risks before other malicious actors purchase and exploit this access.
- Implement geofencing during the active phase of an attack.
- Data leaks
- Use Group-IB Threat Intelligence to monitor for compromised corporate credentials of your employees. Make sure your employees’ passwords are regularly updated and that they do not reuse old passwords.
- Strengthen your password policy. Make sure your employees’ passwords are regularly updated and that they do not reuse old or same passwords. Companies should not only establish strong password policies but also regularly update them to stay ahead of evolving threats and security best practices. Employee training and enforcement of these policies are equally important to ensure compliance and data security.