Introduction
If you envision the dark web as a shadowy realm where cybercriminals orchestrate nefarious activities under the cover of anonymity, you’re not far from the truth. However, the dark web isn’t just as unreachable as you’d think—you likely interact with it more often than you realize. Given this reality, both businesses and individuals must ask: What are the chances that your sensitive, confidential information is present on the dark web, ready for adversaries to exploit and profit from?
The dark web is a hub for the sale of stolen data and personal information. Over 15 billion stolen credentials were discovered in the first half of 2022. Stolen credit card data can be purchased for as little as $25.
Unique dark web insights impacting regions and industries (by Group-IB experts)
🛡️ Group-IB’s Threat Intelligence team identified 101,134 stealer-infected devices with saved ChatGPT credentials found within the logs of info-stealing malware traded on dark web marketplaces.
🛡️ Database leaks became a major issue in 2023, with many compromised datasets sold or published on dark web forums.
🛡️ Group-IB discovered various info-stealer malware information on the dark web, enabling unauthorized data leaks and money withdrawals.
🛡️ Since mid-2023, four GPT-style LLM tools designed for cybercriminal activity have gained traction on dark web forums.
🛡️ From 2022 to 2023, Group-IB identified 27 ads for Ransomware-as-a-Service (RaaS) programs on dark web forums. Cybercriminals often recruit partners by posting ads on these forums, including contact details for private messengers like Tox, Jabber, and Session.
🛡️ Group-IB’s ads analysis from 2022 to 2023 revealed 2,675 instances of corporate access for sale on the dark web in 2023.
🛡️ As threat actors restrict their use of the dark web for several reasons, breachforums.is. is still a favored underground forum for threat actors.
Learn more in Hi-Tech Crime Trends 23/24 Report
The growing threats press businesses to remain vigilant by regularly scouring the dark web for illegal brand mentions, sensitive information leaks, and other potential attacks. Continuous dark web monitoring is crucial for identifying these risks in time. Start by identifying your most valuable social points of presence, key personnel, and critical assets. Consider the potential damage to your organization if these high-value accounts were compromised or impersonated.
What exactly is the dark web, and can you access it?
The dark web can be broken down into two basic categories: structured and unstructured content. The Internet consists of several layers of accessibility:
- Surface Web (Clear Web): This is the easily accessible part of the internet that search engines can index.
- Deep Web: This part is not indexed by search engines and is generally inaccessible through standard means.
- Dark Web: A subset of the deep web, the dark web requires specific browsing technology, such as the Tor browser, for access.
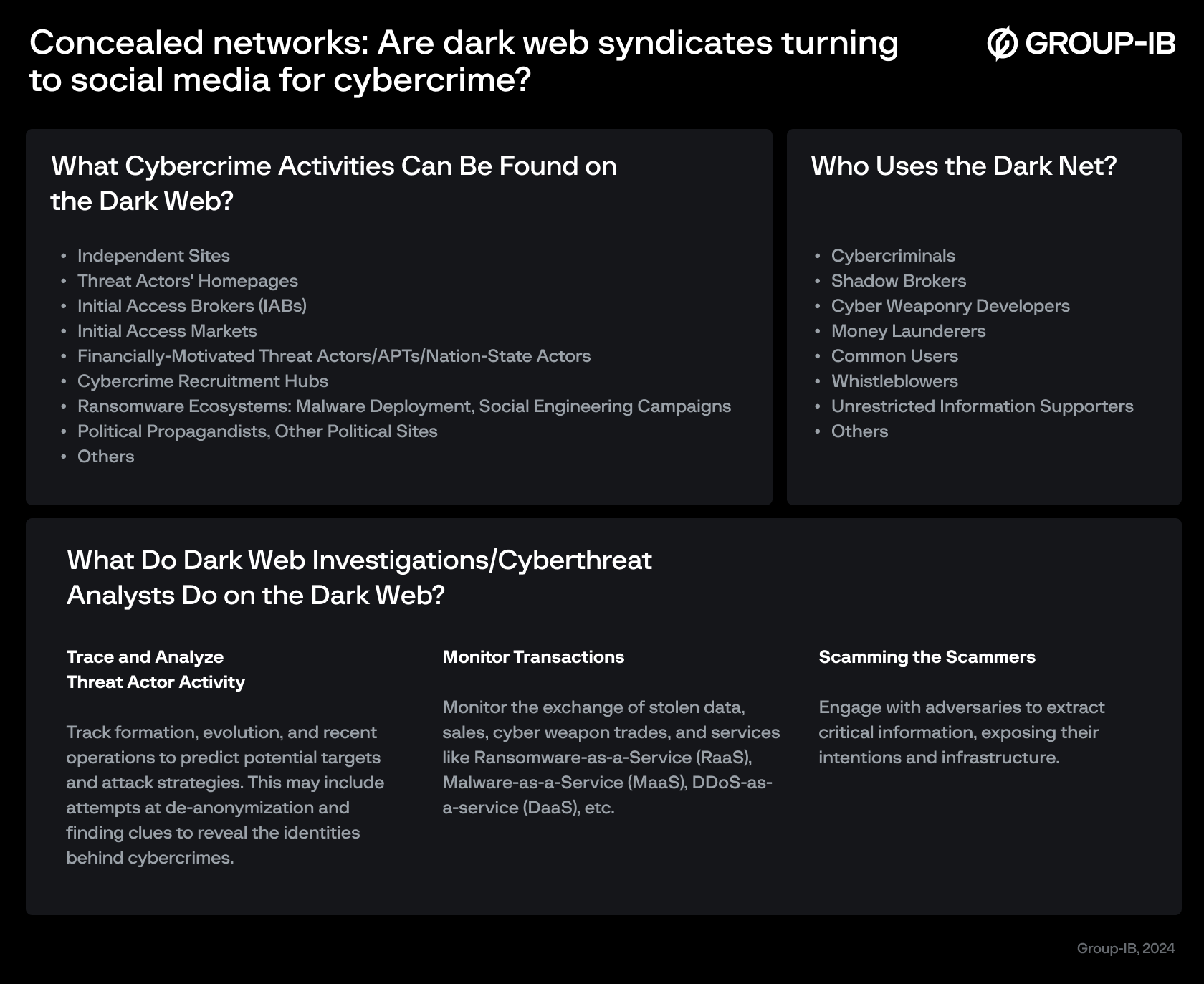
Figure 1: Dark Web cybercriminal activity mapping
The dark web serves as a breeding ground for various cyber threats, including emerging vulnerabilities, exploit and hacking tools, phishing, social engineering, espionage, ransomware, malware, and related services. It also facilitates personal attacks, data breaches, credential leaks, money laundering, and cryptocurrency transactions. The dark web market is estimated to reach a staggering $1.3 billion by 2028 at a CAGR of 22.3%.
The business risks of accessing the dark web
Accessing and browsing the dark web is simple but not without risks for businesses. While it’s a valuable source of data and intelligence for cybersecurity professionals, the dangers—such as malware, phishing attacks, and untrusted network threats—make it risky without proper precautions. It’s advisable to use virtualization or a sandbox when running Tor to protect your systems, as Tor guard and exit nodes can inject malware or monitor your activity. Even encrypted content is not completely safe. For safer dark web monitoring, consider working with cybersecurity experts who can use advanced tools to mask digital fingerprints, allowing secure access to Tor and I2P networks without compromising your infrastructure.
How do dark web investigators retrieve information on concealed crimes and criminals?
Dark web investigations go beyond merely scouring the untraceable, non-indexed parts of the web to gather information that could potentially be exploited for crimes. They require established techniques, tools, and methods to identify criminals in the dark web—including underground markets, discussion forums, and more—to collect digital evidence that can be analyzed, processed, and shared with authorities and law enforcement to disrupt illicit operations. Some methods adopted by Group-IB’s team of dark web investigators include:
Manual analysis and tools: Investigating threat actors involves manual analysis and specialized tools. Open-source and commercial tools help investigators analyze data posted by threat actors, such as nicknames, contact details, language use, and writing style. This information is crucial for understanding adversaries and validating gathered intelligence.
During manual analysis, investigators also need to ensure that breaches are legitimate. Some leaks, purported to be new, may consist of previously released data, making due diligence essential. Also, many attackers today use multiple accounts on underground forums to hide their activities better. To determine the goal of an attack and proceed with its further probe, one has to know the adversary.
Group-IB Threat Intelligence: Group-IB collects threat intelligence data from various sources, a large amount from the dark web. They structure their dark web findings in a way that reduces noise and makes it easy to navigate. Threat intelligence is categorized into campaign reports labeled industries, countries, vulnerabilities, tools, and techniques. These reports are used to build threat actor profiles, allowing for deeper analysis of techniques, tools, and frequency of use.
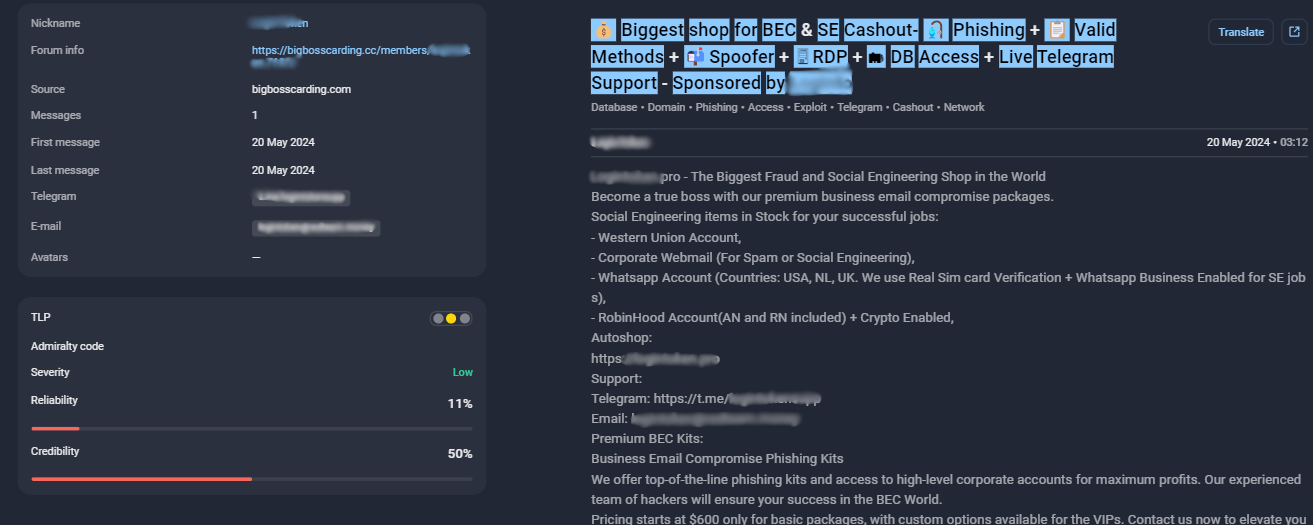
Figure 2: Decoding cybercriminal activity, tactics, and techniques using Group-IB Threat Intelligence
Semantic analysis: Group-IB investigators use machine learning algorithms to automate cyber investigations and analyze dark web content, building correlations between various posts in underground forums. Natural Language Processing (NLP) algorithms are employed to reveal multiple accounts belonging to the same individual or group based on the semantics of their messages.
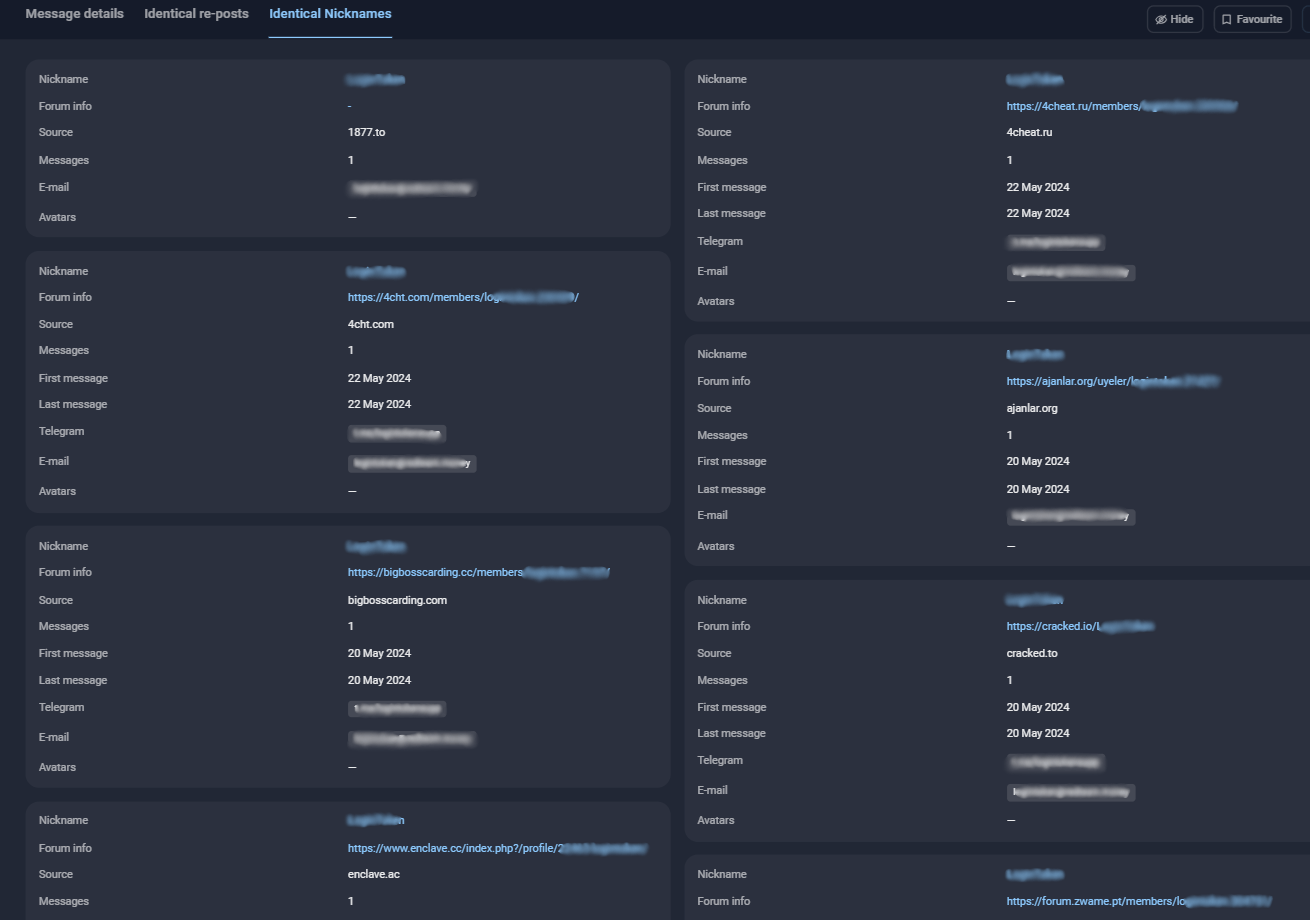
Figure 3: Decoding cybercriminal dark web identities and activities using Group-IB Threat Intelligence
Social Engineering (Uno-Reverse): Fraud-risk domain experts often act as decoys by creating profiles and establishing a presence on various forums and marketplaces. By carefully building credible personas, they gain the trust of adversaries and gather crucial information, all while maintaining anonymity and securing communications.
Tracking dark web activities and investigator interests: Threat actors commonly use dark web forums to publish or sell leaked data, seek out partners in crime, or purchase compromised credentials to facilitate illegal activities. Investigators focus on extracting all available information about these threat actors through their dark web activity, including tracking aliases, contact information, language patterns, and writing style.
Social media monitoring: Social media platforms provide crucial insights often unnoticed, including emerging threats, existing criminal networks, and new trends or tactics cybercriminals use. By monitoring social media, investigators can:
- Identify emerging threats: Detect early traces of new criminal activities or trends before fully developing.
- Analyze criminal networks: Uncover and map connections between individuals and groups involved in illegal activities.
- Track dark web references: Monitor and analyze links or mentions of dark web sites and marketplaces; identify active platforms and track their operations.
- Identify and profile threat actors through digital traces: Investigate individuals and groups by tracking their digital traces. Exploit threat actors’ tendency to overshare and their lack of operational security (OpSec), which can reveal personal information. Use this data to debunk their operations and build comprehensive threat profiles.
Social media monitoring should become an active brand protection component for businesses. It greatly supports traditional investigative techniques while uncovering insights hidden in plain sight.
Adversaries are increasingly resorting to social media platforms to avoid prying eyes on the dark web
As law enforcement ramps up monitoring and seizing dark web forums, many threat actors are migrating to social media platforms such as Facebook, X (formerly Twitter), TikTok, Telegram, and more.
They often create multiple accounts with variations of the same username to avoid suspension. TikTok, in particular, has become a popular platform for sharing short videos about hacking activities or hacktivism propaganda. While criminals on the dark web believe they are invisible, Group-IB’s Threat Intelligence can unmask them. As monitoring of the dark web increases, adversaries are shifting to more discreet communication methods, often utilizing social media channels to evade detection, extend their reach, and bring their services to a wider audience.
Discussing the surge in illicit activities, let’s take the example of the EU, where Pavel Durov, CEO and co-founder of Telegram, was under scrutiny for the platform’s hands-off moderation and easy access, allowing illegal activities to thrive. These activities include the distribution of child sexual abuse material, drug sales, malicious hacking tools, fraud, and money laundering. Additionally, three other charges involve providing cryptology tools without proper declarations to French authorities. (Learn more on how Telegram enables cybercriminal communities to thrive and exploit security caveats within the messaging app to perpetrate crime).
Cyril Boussiron, Group-IB’s Sales Account Manager in the EU region, recently shared valuable insights during a webinar for cybersecurity enthusiasts and professionals about the growing trend of cybercriminals turning to social media. He stated:
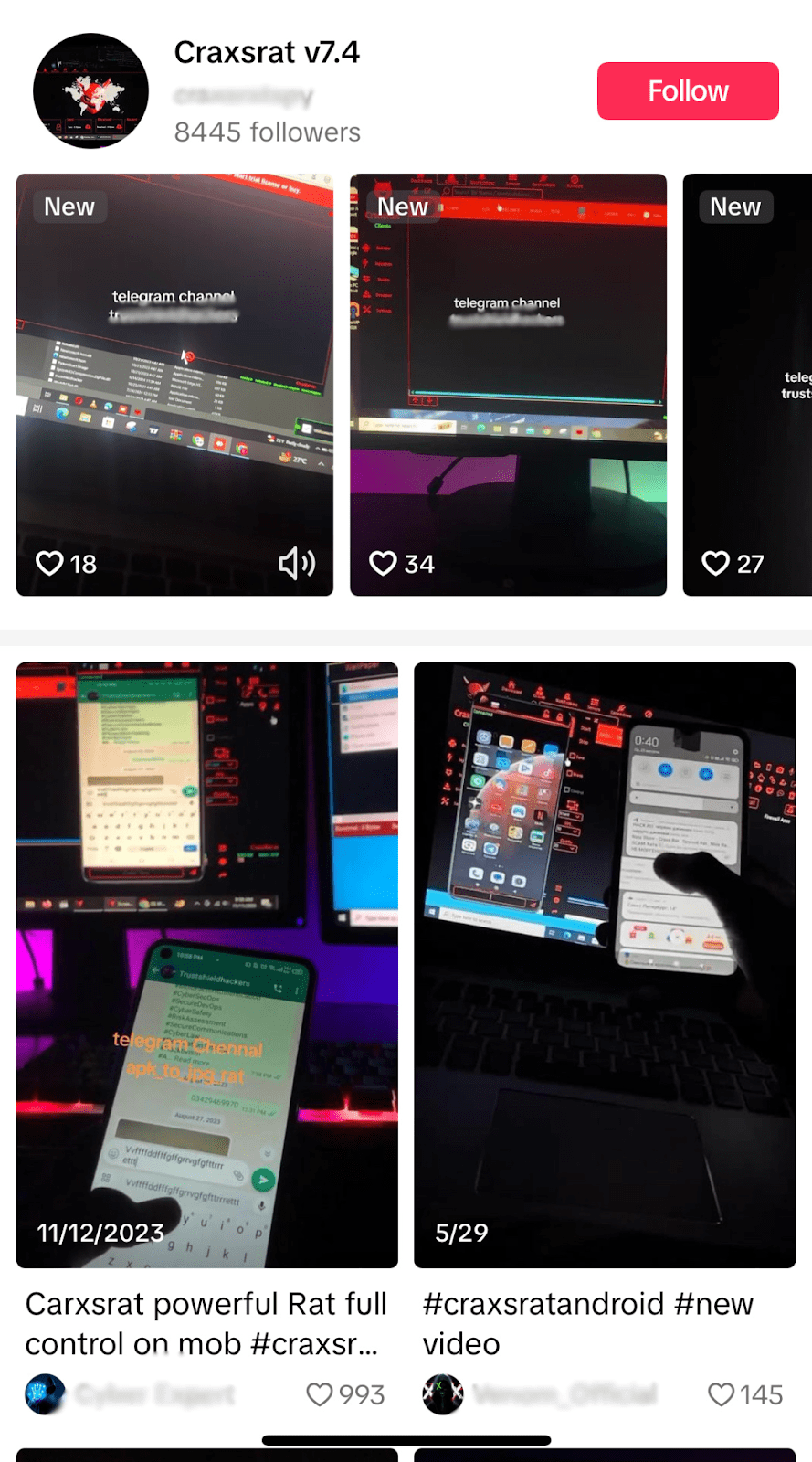
Figure 4: Pictures of social media campaigns associated with CraxsRATmalware
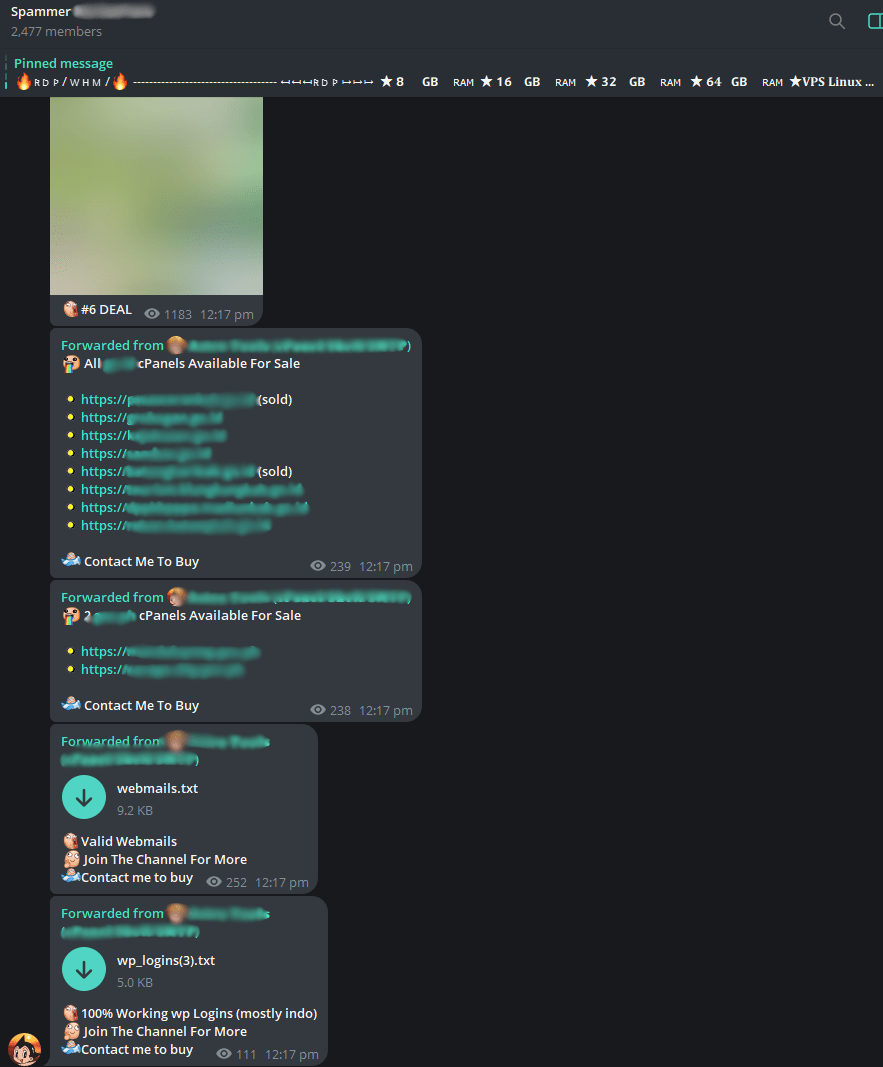
Figure 5: Exploitation tools advertisement on communication channels
A recent six-month global study by a criminology expert from the University of Surrey in the UK found that cybercriminals exploiting popular social media platforms generated nearly $3.25 billion in earnings over the past year.
Cybercriminals leverage social media platforms in several ways to market and sell their services and tools:
- Malware distribution: Cybercriminals distribute malware through deceptive links, malicious ads, and phishing scams, tricking users into downloading harmful software. Info-stealing malware, specifically designed to collect and exfiltrate sensitive information from infected systems, has been widely distributed through social media, as highlighted in the Hi-Tech Crime Trends 23/24 report.
Another important occurrence was the discovery of MacStealer, a recently identified type of macOS-based stealer malware that controls operations on an infected device via Telegram. The stealer extracts data such as documents, browser cookies, and login credentials, then transmits this information to the listed Telegram channel
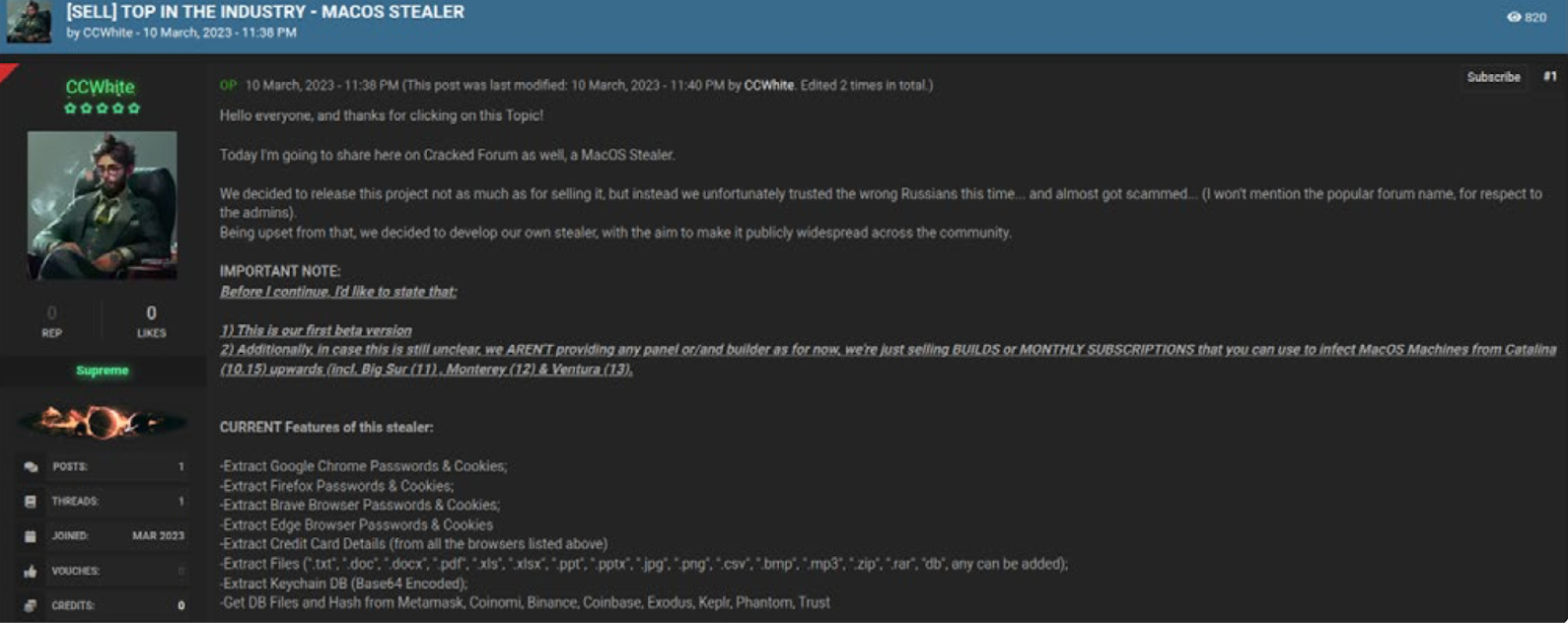
Figure 6: Ad by a threat actor on the dark web
- Toolkits and exploits: They advertise and sell toolkits and exploits, including software designed to exploit vulnerabilities, through forums, groups, or direct messages.
- Malware/Ransomware-as-a-Service (MaaS/RaaS): Cybercriminals market malware and hacking tools, including ransomware, spyware, and trojans, as services through social media channels.
- Data exploitation: Stolen data, such as personal details and credentials, is bought and sold on social media, with specialized groups and pages acting as marketplaces for this information.
- Full-service packages: Comprehensive packages are provided, including malware, exploit tools, and additional resources. These packages include step-by-step tutorials and technical support to help buyers use the tools effectively.
- Personalized attacks: They use social media to gather information for targeted attacks, crafting personalized phishing schemes and malicious activities for specific individuals or organizations.
Recent social media operations: Group-IB’s key insights
VietCredCare Incident
Recently, Group-IB identified and investigated a significant cyber threat known as VietCredCare. Here’s a brief overview of the operation:
Picture this: an employee at a prominent Vietnamese bank was targeted via a local messaging app with a link leading to a malicious .zip file. This file compromised sensitive web browser information. This was the underlying intent behind the operation. Our Threat Intelligence team thoroughly analyzed the threat, leading to the identification of VietCredCare, an information-stealing malware with operations starting from August 2022. The malware primarily affects 44 of Vietnam’s 63 provinces, including major cities like Hanoi, Ho Chi Minh City, and Da Nang.
Key findings were that VietCredCare focuses on session cookies and Facebook credentials, particularly those used for managing advertisements.
Cybercriminals could acquire a botnet from VietCredCare’s developers or use the source code independently. Each purchaser received a dedicated Telegram bot channel for data exfiltration and communication with the malware creators, and over 20 such channels were uncovered.
Classiscam Operations
In 2023, Group-IB reported that the Classiscam botnet had scammed users out of over $60 million between H1 2021 and H1 2023.
ResumeLooters Attack
From November to December 2023, ResumeLooters exploited SQL injection and Cross-Site Scripting (XSS) vulnerabilities to breach at least 65 websites. This attack resulted in the theft of over 2 million unique email addresses and other job-seeker information. Group-IB has informed the affected parties to mitigate further damage.
FakeBoss Scheme
Previously, Group-IB identified the FakeBoss scheme, where attackers impersonate senior leadership to extort funds or confidential information via messaging platforms such as Telegram and WhatsApp, and also included preliminary precautions such as avoiding engaging with suspicious accounts or transmitting any information to them and verifying the authenticity of accounts before initiating any communication.
Conclusion
The vast, evolving, and fragmented dark web requires more effective approaches to tracking and minimizing threats. Tracking transactions and activities in black marketplaces requires advanced techniques. The unpredictable dark web—where old sites are taken down and new ones appear daily—demands strong digital evidence for forensic agencies to overcome obstacles and apprehend criminals.
International borders, cybercriminals’ unpredictable nature, and the lack of expertise to excavate dark web traces further complicate investigations. Therefore, advanced tools such as Group-IB’s Threat Intelligence and professional experts are crucial in tackling forensic challenges, uncovering hidden threats, and safeguarding organizations, people, and the greater community.
Cybercriminal social media communities and channels: Don’t get caught in the trap! 🚫
Cybercriminals are masters at exploiting social media, turning it into a playground for their illicit activities. They use these platforms to spread malware, sell stolen data, and recruit accomplices. But don’t be fooled—engaging with or sharing their content can put your business and employees at serious risk.
- Monitor and manage the network to prevent unauthorized access and attacks.
- Smartphones have become a prime target for cybercriminals exploiting social media platforms. Implement robust mobile security solutions to secure corporate or personal devices and applications.
- Regularly monitor social media channels for suspicious activity or threats to your organization. Enable it now.
- Conduct periodic investigations into the dark web to identify potential threats and data leaks.
- Understand the scale of illicit activities on the dark web. This insight will inform resourcing and investigative efforts.
- Gain visibility into unauthorized brand mentions, content exploitation, and counterfeiting attempts on dark web marketplaces.
- Investigate cybercriminal individuals and groups by leveraging usernames, aliases, and historical activity data to build a comprehensive threat profile.
Don't wait for the situation to escalate!
If you suspect a cybercriminal is targeting your business, employees, or network, schedule an investigation with our experts today.