Background
After the fall of the Cron gang in late 2016, the group dubbed TipTop by Group-IB became one of the largest and most dangerous ones on the Russian cybercrime market. Using Android Trojans, the cybercriminals infected over 800,000 smartphones and created a giant botnet. Their ultimate goal was to steal money from payment cards. The group stole between USD 1,500 and 10,500 on a daily basis. Victims were identified in several Russian regions.
TipTop spread their malware by disguising it as popular mobile apps. Downloading such an app would prompt the download of the Trojan, which gave the hackers access to the victim’s mobile banking services.
The group members were ultimately arrested as a result of a coordinated operation between Russian law enforcement and Group-IB.
Behind the scenes
Group-IB first came across TipTop’s activities in 2015, but the members were active until 2019. The group used many different tools and money withdrawal schemes, which made it difficult for law enforcement and cybersecurity experts to attribute attacks to them. At different points in time, the group’s command-and-control (C&C) servers and websites used to infect the devices were located in Germany, USA, and Ukraine.
Impact
In the mid-2010s, Android Trojans targeting banking customers became more widespread. In some periods, Group-IB experts identified new Android Trojans every month. Almost all the authors of these Trojans were Russian-speaking hackers.
By the end of 2019, such Trojans were becoming less active. Compared to PC Trojans, Android Trojans disappeared more slowly; however, the number of new ones was significantly lower than those that had fallen out of use.
Due to stricter legislation and intensified efforts to fight against this type of threat in Russia (including arrests of key botnet masterminds), cybercriminals found it increasingly less profitable to attack victims in the CIS region and eventually shifted their focus to other countries. Group-IB played a crucial role in reducing this threat in Russia by bringing major actors such as TipTop to justice.
Storyline
TipTop was active between 2015 and 2019. The group targeted customers of the top ten Russian banks that used Android smartphones. The hackers delivered malware to devices via fake mobile apps disguised as banking apps, messengers, Adobe’s graphic design application, and a fake Google Play store app. The hackers placed links to the fake apps either on rogue websites they had designed themselves or on legitimate web resources they had compromised. To increase the number of potential victims, the cybercriminals promoted these websites in search engines by purchasing ads for the keyword “mobile bank”. When users tried to download one of the fake apps, an Android banking Trojan was installed on their device.
The group started their activities with the Hqwar Android banking Trojan (also known as Agent.BID). In this case, the Trojan was made to look like dating apps, the Google Play store, and even Minecraft. Once installed, the app (with the generic name “Install”) would “fail” during installation and then disappear from the home screen. In reality, it continued to operate covertly.
The Trojan could send SMS messages, access the user’s contact list, perform USSD requests, make calls, redirect calls, and even hide incoming calls and messages. It could also steal credit card data and block the device or its screen.
The group parsed SMS messages from victims to gather information about their bank accounts and balances. By sending USSD requests, they obtained details about the victim’s mobile account balances. They exploited mobile banking commands and the auto-reply features to transfer money from the victim’s account to their own. They also used web injects tailored to various banks in order to compromise online banking login credentials and steal money, and deployed phishing dialogues to capture banking card data.
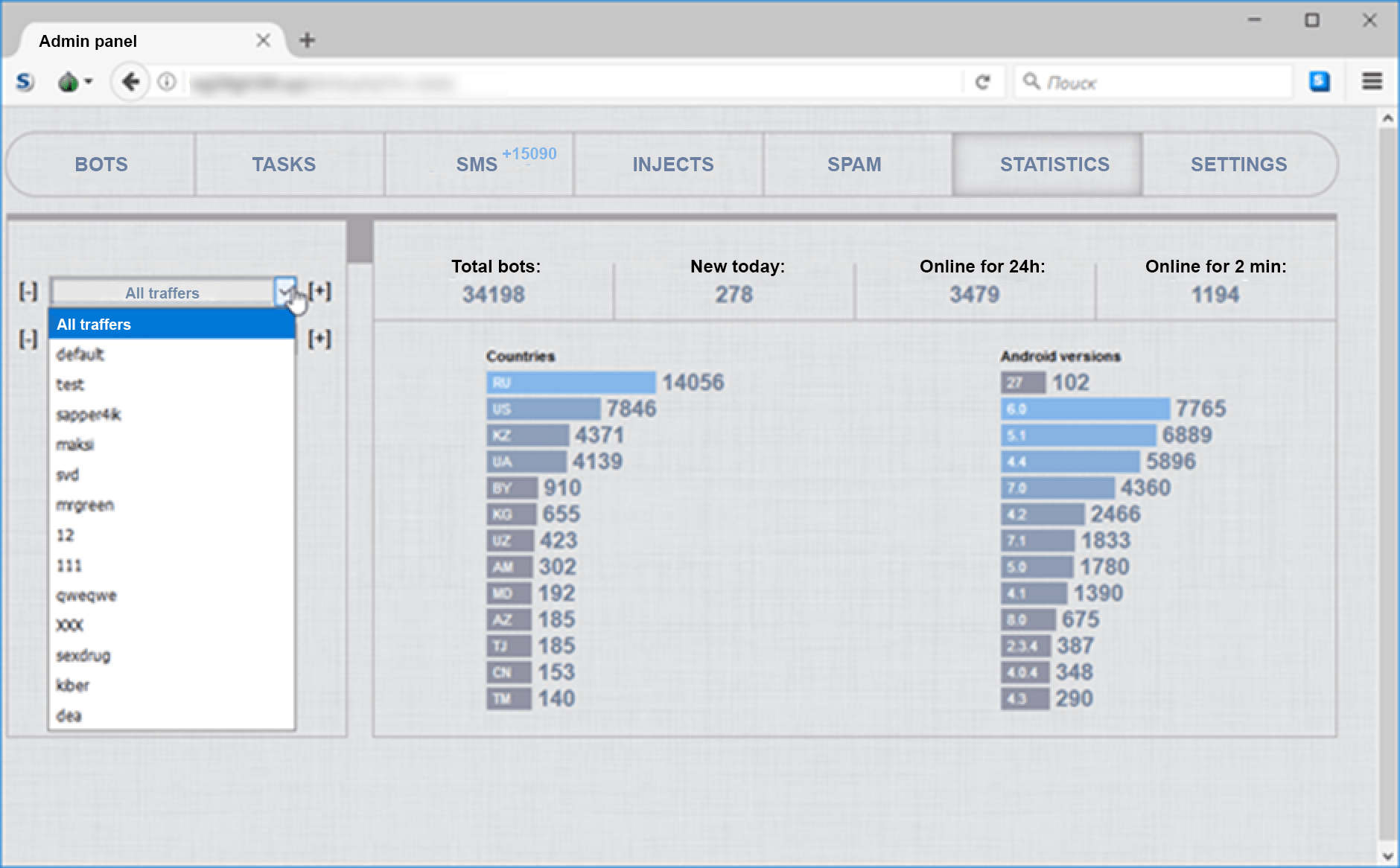
Figure 1. Hqwar control panel
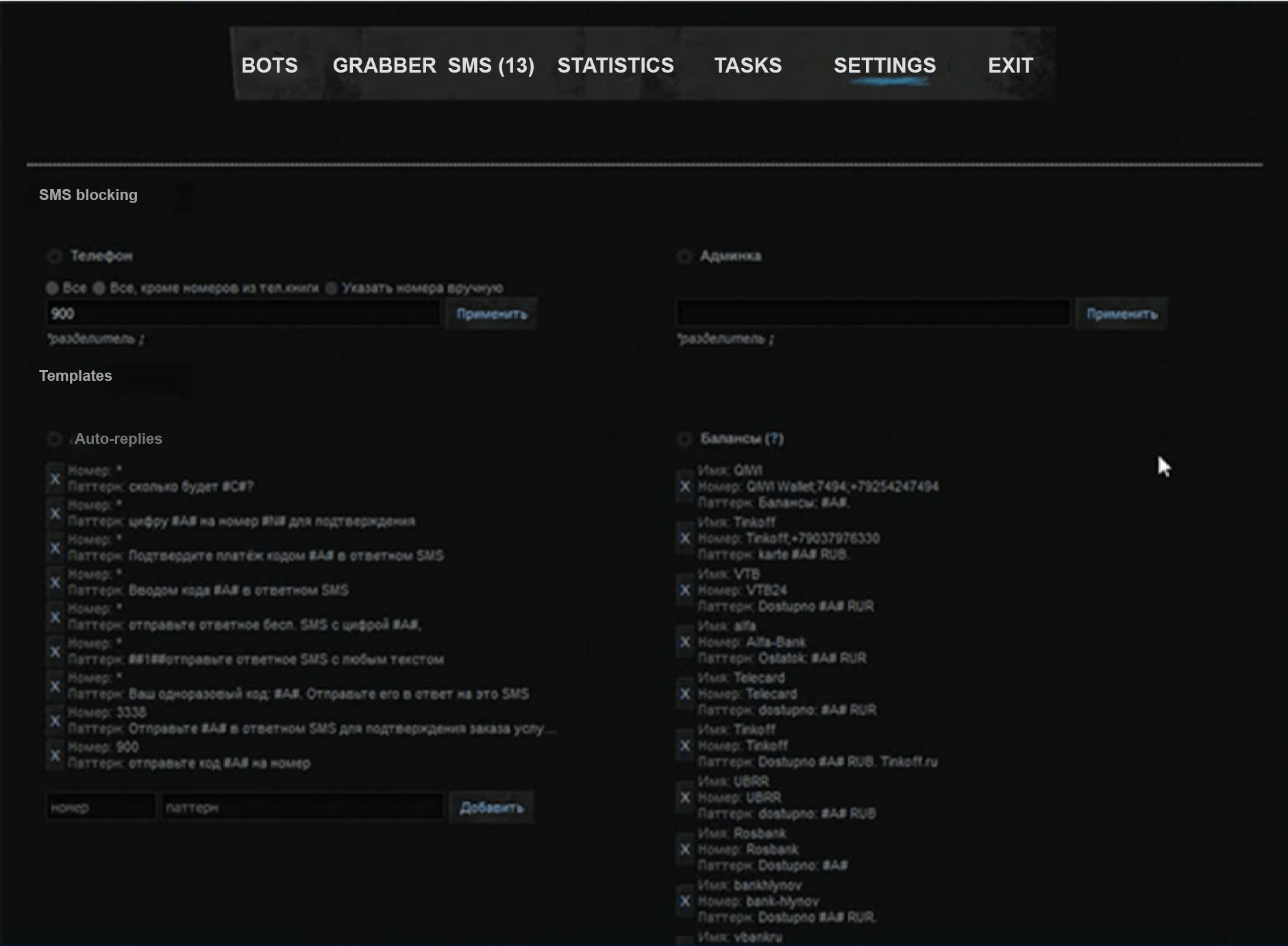
Figure 2. Hqwar (updated version) control panel
The group tried various tools and money withdrawal schemes, which made it difficult to attribute attacks to them. In 2015, the hackers used the Hqwar (aka Agent.BID) Android Trojan to infect customers of Russian banks. In 2016, they started using the Honli Trojan, and in February 2016 they adopted an upgraded version of it, which anti-virus systems tracked as Asacub.g.
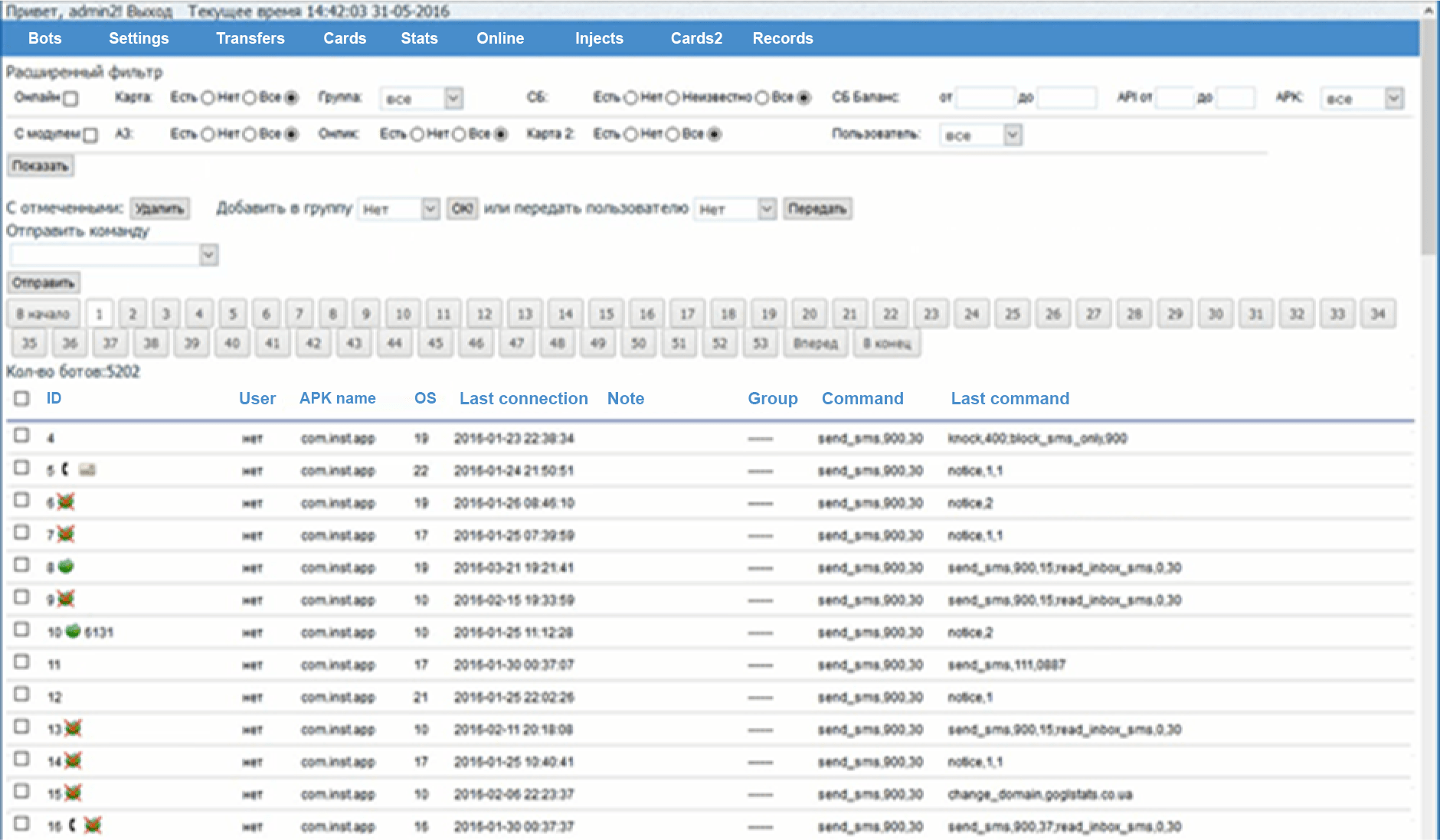
Figure 3. Honli control panel
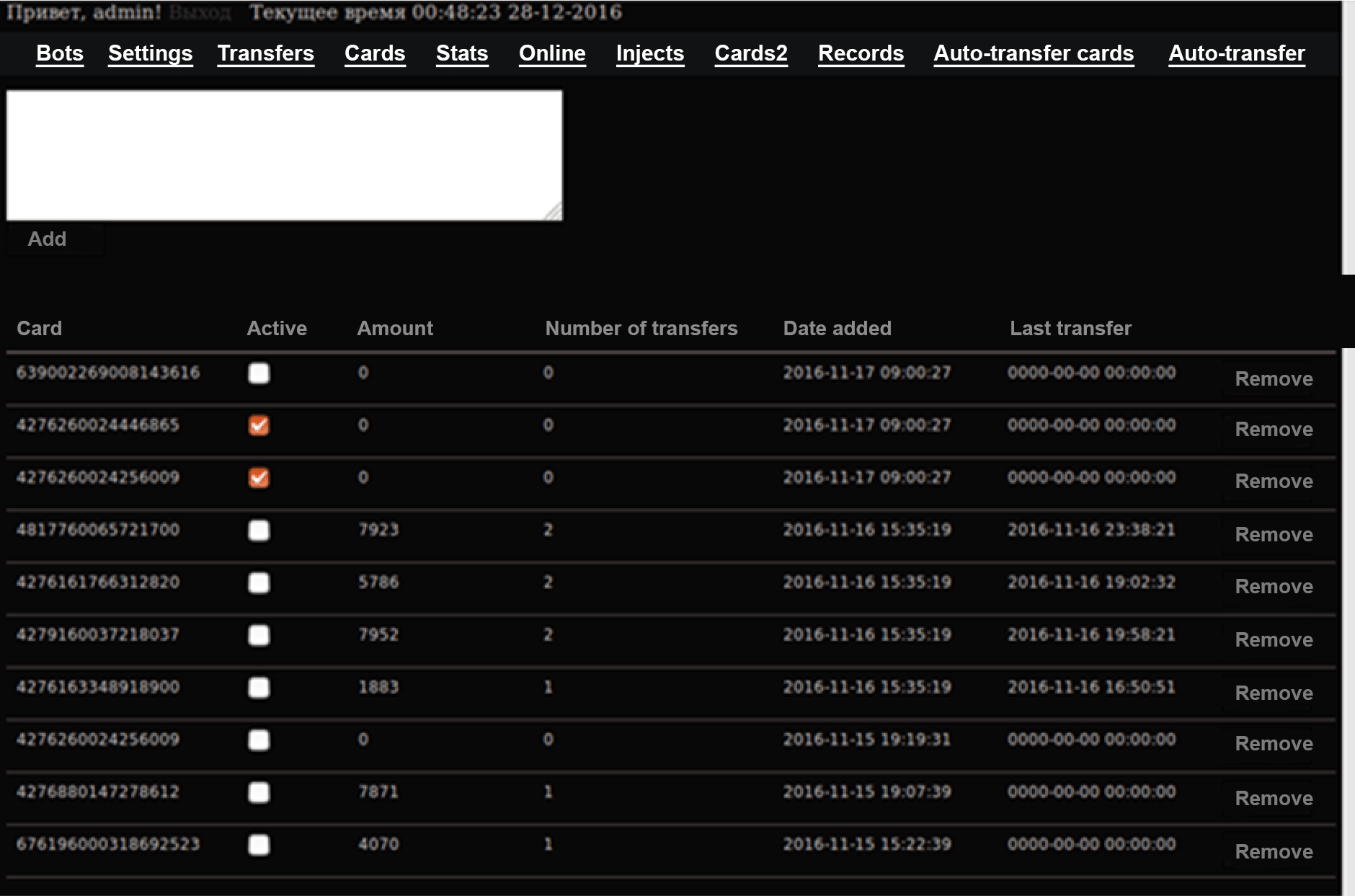
Figure 4. Asacub.g control panel
In the same year, the group tried infecting smartphones with Cron, a Trojan developed by their predecessors, which had given its name to that group.
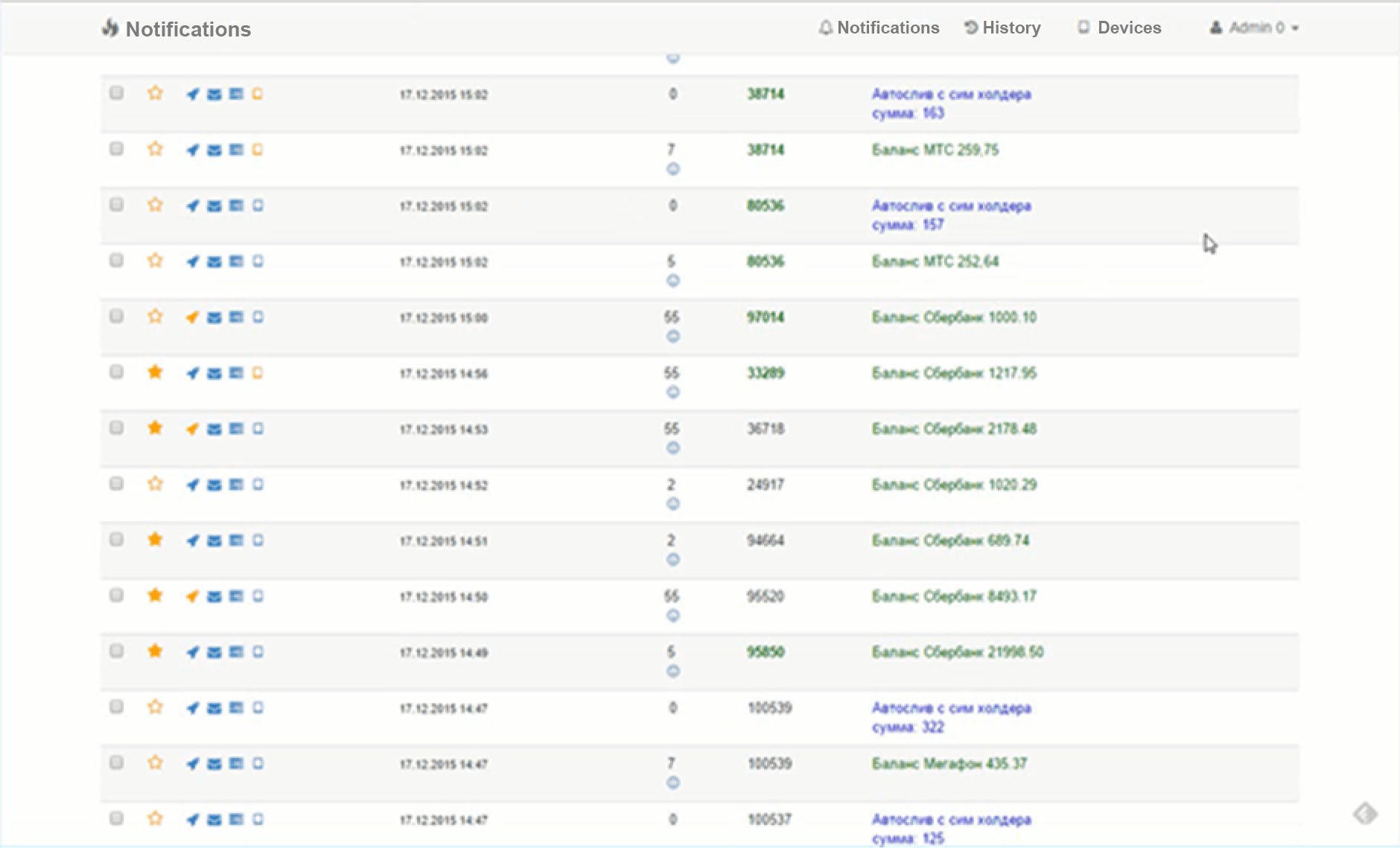
Figure 5. Cron control panel
During the same period, TipTop used the CatsElite (MarsElite) Trojan. The admin panel below shows information such as the date and time of bot registration, web injections, apps installed, the total number of bots, telecoms operators, and types and identifiers of compromised devices.
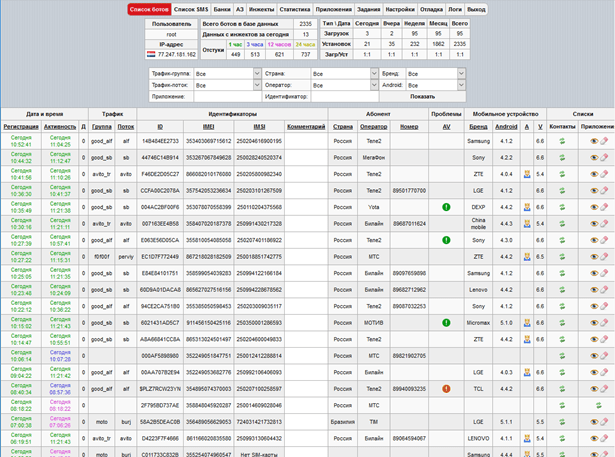
Figure 6. CatsElite (MarsElite) control panel
In April 2017, they returned to Hqware (Agent.BID) but also used LokiBot and an upgraded version of the old Marcher (Rahunok) Trojan.
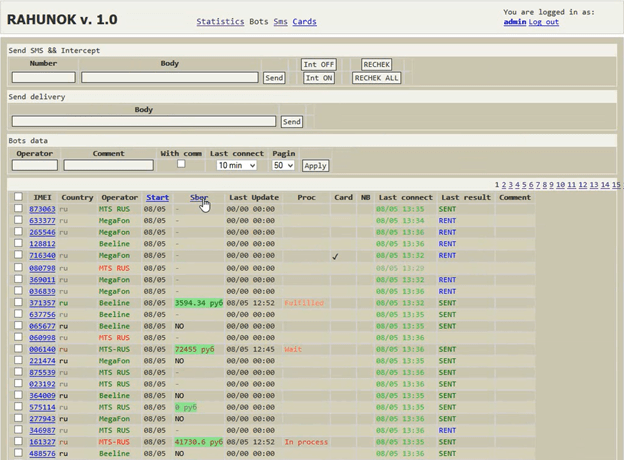
Figure 7. Rahunok control panel
All mobile Trojans used by the hackers could intercept and read SMS messages, record phone calls and send USSD requests, but their main goal was to steal payment card details by using phishing windows and web fakes designed to trick users into entering their credentials for online banking accounts.
And justice for all
During the investigation, with help from Group-IB, the police identified one of the TipTop members as a 31-year-old man from Krasnoyarsk, Russia, as well as other group members.
In early 2019, a series of police operations took place in various locations, leading to the arrest of the TipTop members and the search of their homes. During the search, the police seized their computers, hard drives, flash drives, phones, and SIM cards. The suspect from Krasnoyarsk was identified as one of TipTop’s “cash-out specialists,” responsible for siphoning money from victims and transferring it to the main TipTop accounts. This hacker confessed to laundering money stolen from banking clients through Bitcoin. He revealed that he had collaborated with a partner via a messaging app from 2016 to 2018 but had ceased working with them after 2018 due to “personal differences.”
The police opened a criminal case for the сreation, use and dissemination of harmful computer programs. The suspect from Krasnoyarsk was convicted in 2019 and received a two-year suspended sentence. Other members of TipTop were also prosecuted under Russian law.
Conclusion
Group-IB’s long-term efforts helped to ultimately stop one of the most successful malware groups of its time, TipTop, which had used various botnets between 2015 and 2019. Group-IB’s contribution helped to level off the Android Trojan market in Russia after several years of growth. Other similar threat actors using Android malware continued to gain momentum on the world stage, however.


























