Background
OPERA1ER, also known as DESKTOP-GROUP, Common Raven, and NXSMS, operated as a financially motivated cybercriminal syndicate. The group’s attacks relied on highly targeted spear phishing campaigns. Its members often impersonated financial regulators, tax authorities, and bank employees. Using stolen credentials, they gained access to enterprise VPNs and banking back-office systems. They then moved through internal infrastructures, escalated privileges, and executed fraudulent transactions, funneling stolen funds through mule account networks before withdrawing cash via ATMs and mobile payment platforms.
The group was active between 2018 and 2022 and mainly targeted financial institutions, mobile banking services, and telecom providers. Most attacks took place in Africa, with confirmed incidents in Ivory Coast, Mali, Burkina Faso, Cameroon, Gabon, Niger, Nigeria, Senegal, Sierra Leone, Uganda, Togo, and Benin. Beyond Africa, OPERA1ER extended its operations to South Asia and Latin America, targeting banks in Bangladesh, Paraguay, and Argentina. The cybercriminals communicated mainly in French, though English and Russian were also sometimes used.
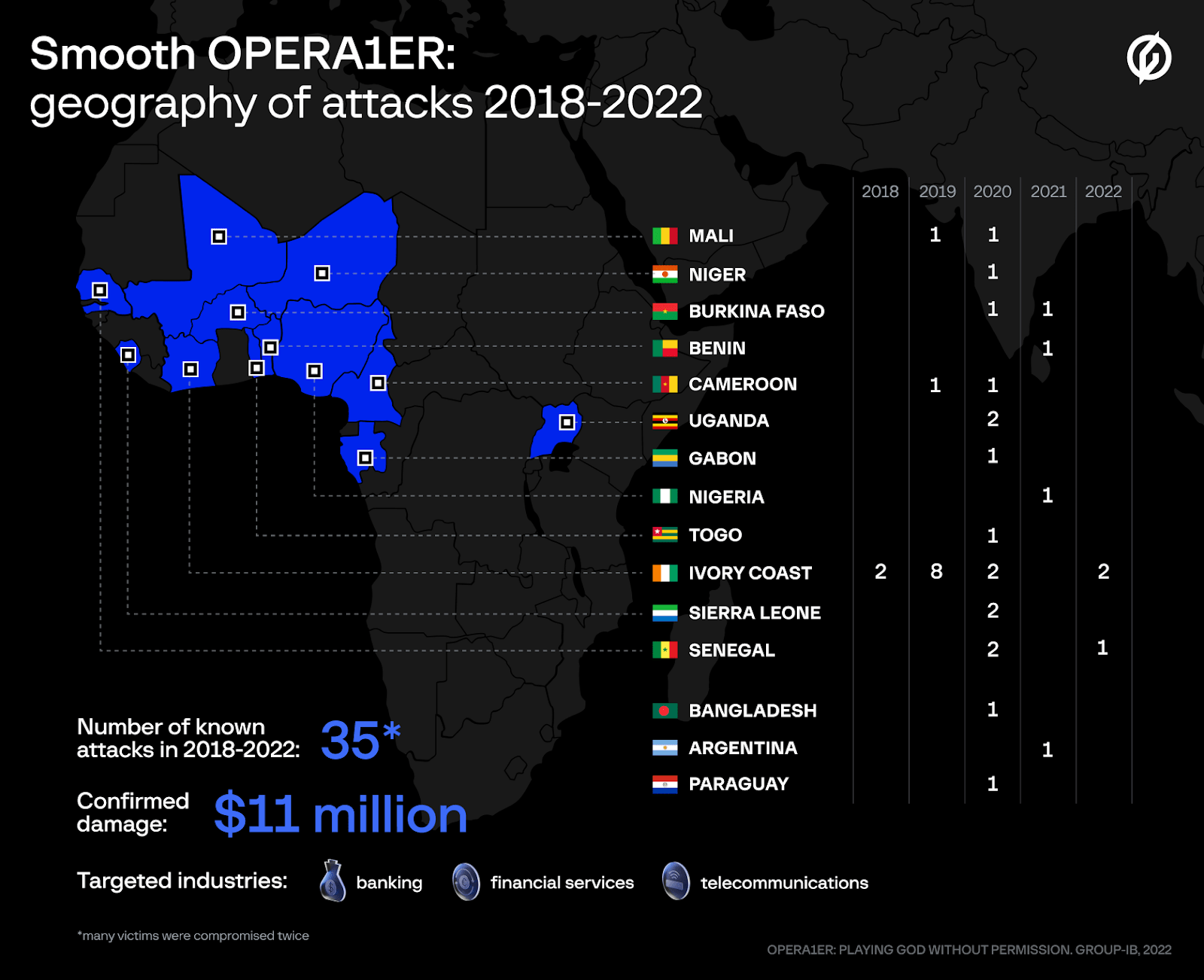
Figure 1. Geography of OPERA1ER attacks
Despite its operational discipline, OPERA1ER made critical errors that ultimately led to its downfall. Investigators at Group-IB were able to link elements of the group’s infrastructure to specific individuals, providing law enforcement with the intelligence needed to take action.
Behind the scenes
The story began in 2019, when Orange-CERT-CC detected an extensive phishing campaign that targeted banks and financial institutions in Africa. Following this, they reached out to Group-IB’s Threat Intelligence unit in May 2020, suggesting to join efforts and address the attacks, unaware that our researchers had been tracking the group (and had named it OPERA1ER) since the second half of 2019. The results of our joint investigation were published in OPERA1ER: Playing God without permission.
Impact
The intelligence provided by Group-IB helped all the players involved (INTERPOL, AFRIPOL, the Direction de L’information et des Traces Technologiques (DITT), Orange-CERT-CC, and Group-IB itself) coordinate a series of actions that ultimately disrupted OPERA1ER’s operations. The information gathered led to the arrest of a key member of the syndicate, significantly weakening the group’s ability to keep carrying out criminal activities.
Storyline
In 2019, Orange-CERT-CC detected a large-scale phishing campaign targeting financial institutions across Africa. The phishing emails were made to look like official communications from government agencies, financial regulators, and tax authorities. They contained malicious attachments or links that, when opened, deployed Remote Access Trojans (RATs) and password sniffers onto devices.
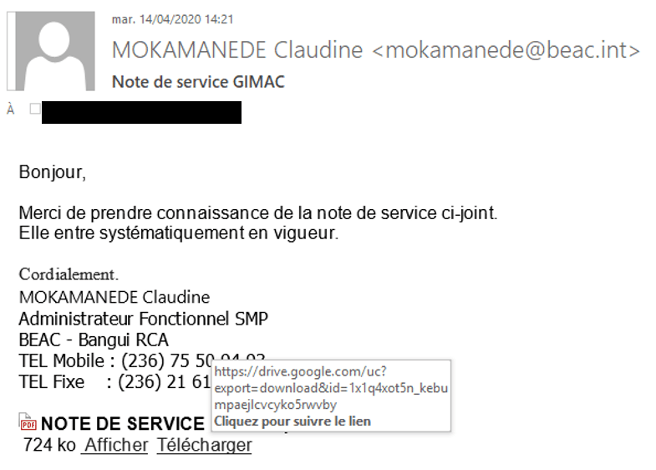
Figure 2. Phishing email with a link to Google Drive
One of the first confirmed incidents involved a financial institution that reported suspicious banking transactions occurring over the weekend. Analysts quickly identified abnormal money withdrawals from ATMs and traced them back to unauthorized access within the organization’s internal infrastructure. Further forensic investigation revealed that the cybercriminals had taken control of computers used by payment gateway operators. The attackers leveraged stolen credentials to escalate privileges within the system, gaining administrator access to domain controllers and banking back-office systems.
As the investigation expanded, security teams uncovered additional incidents where OPERA1ER had attempted to infiltrate financial institutions across many African countries. By mid-2019, despite the efforts made by the affected organizations to reinforce their defenses, the group managed to regain access to previously compromised networks, attempting to carry out further fraudulent operations.
By mid-2020, Orange-CERT-CC sought help from Group-IB’s Threat Intelligence Team, unaware that Group-IB had already been monitoring a financially motivated cybercriminal group using similar tactics. The investigation revealed that the same threat actors were behind multiple incidents. Group-IB had been tracking their activity since late 2019 and had already linked them to a pattern of fraud targeting banks in Africa, South Asia, and Latin America. Group-IB codenamed the cybercriminals OPERA1ER, after an email account they often used to register domains.
How OPERA1ER operated
What set OPERA1ER apart from other cybercriminal groups was their ability to execute high-impact attacks using basic tools. Unlike sophisticated threat actors who develop custom malware, OPERA1ER relied on open-source hacking programs, Remote Access Trojans (RATs), and penetration testing frameworks such as Metasploit and Cobalt Strike. They were effective not because of any advanced technical capabilities but rather meticulous reconnaissance, precise targeting, and long-term persistence within compromised networks.
Once inside a bank’s network, OPERA1ER exfiltrated emails and internal documents to use them in subsequent phishing attacks. The gang harvested credentials, escalated privileges, and moved laterally using Mimikatz, BloodHound, and PowerSploit. The threat actors compromised payment processing systems, mobile banking platforms, and even SWIFT messaging interfaces in at least two banks, making it possible to execute fraudulent transactions on a massive scale.
Forensic analysis revealed that OPERA1ER often spent months inside an organization’s infrastructure, meticulously studying internal financial systems before launching an attack. In some cases, they remained undetected for up to a year, carefully planning fraudulent transactions that would be difficult to trace. They took the time to study internal documentation so that they could better prepare for the cashing-out stage as most of OPERA1ER’s victims used a complex digital money platform.
The platform has a three-tiered architecture involving distinct accounts to allow for different types of operations. To compromise such systems, OPERA1ER required specific knowledge about key people involved in the processes, the protection mechanisms in place, and the links between back-end platform operations and cash withdrawals. The group could have obtained this information directly from insiders, or they could have obtained it themselves by slowly inching their way into the targeted systems.
The shift toward mobile money fraud became one of OPERA1ER’s most profitable ventures. Digital payment systems in Africa and South Asia had security gaps that made them vulnerable to exploitation. In some countries, as much as 27% of salaries were paid via mobile money, which made such platforms a lucrative target. OPERA1ER exploited these weaknesses by stealing the credentials of mobile money operators, transferring funds to mule accounts and cashing out through ATM withdrawals and international transfers.
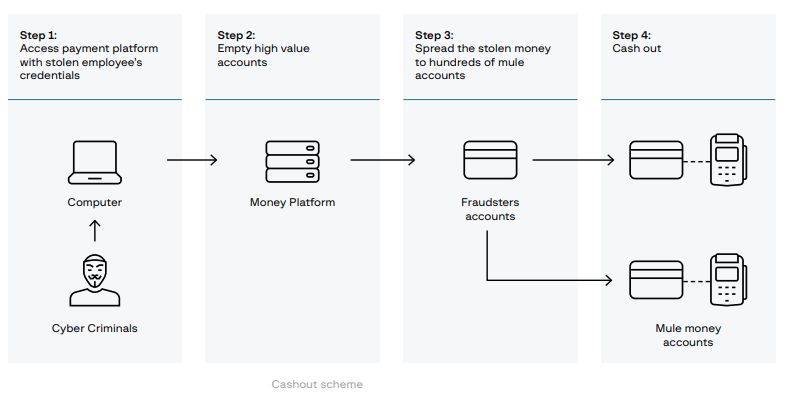
Figure 3. OPERA1ER cashout scheme
The breakthrough
As OPERA1ER continued expanding its operations, Group-IB’s Threat Intelligence Team intensified efforts to track the group’s infrastructure. By mid-2021, investigators had mapped OPERA1ER’s network using our proprietary Graph, identifying key domains, VPN relay points, and compromised servers.
A crucial discovery was that OPERA1ER used the same naming conventions when registering malicious domains, email addresses, and VPN services. Analysts cross-referenced domain registration data, WHOIS records, and SSL certificates, which revealed digital footprints linked to the syndicate’s core members.
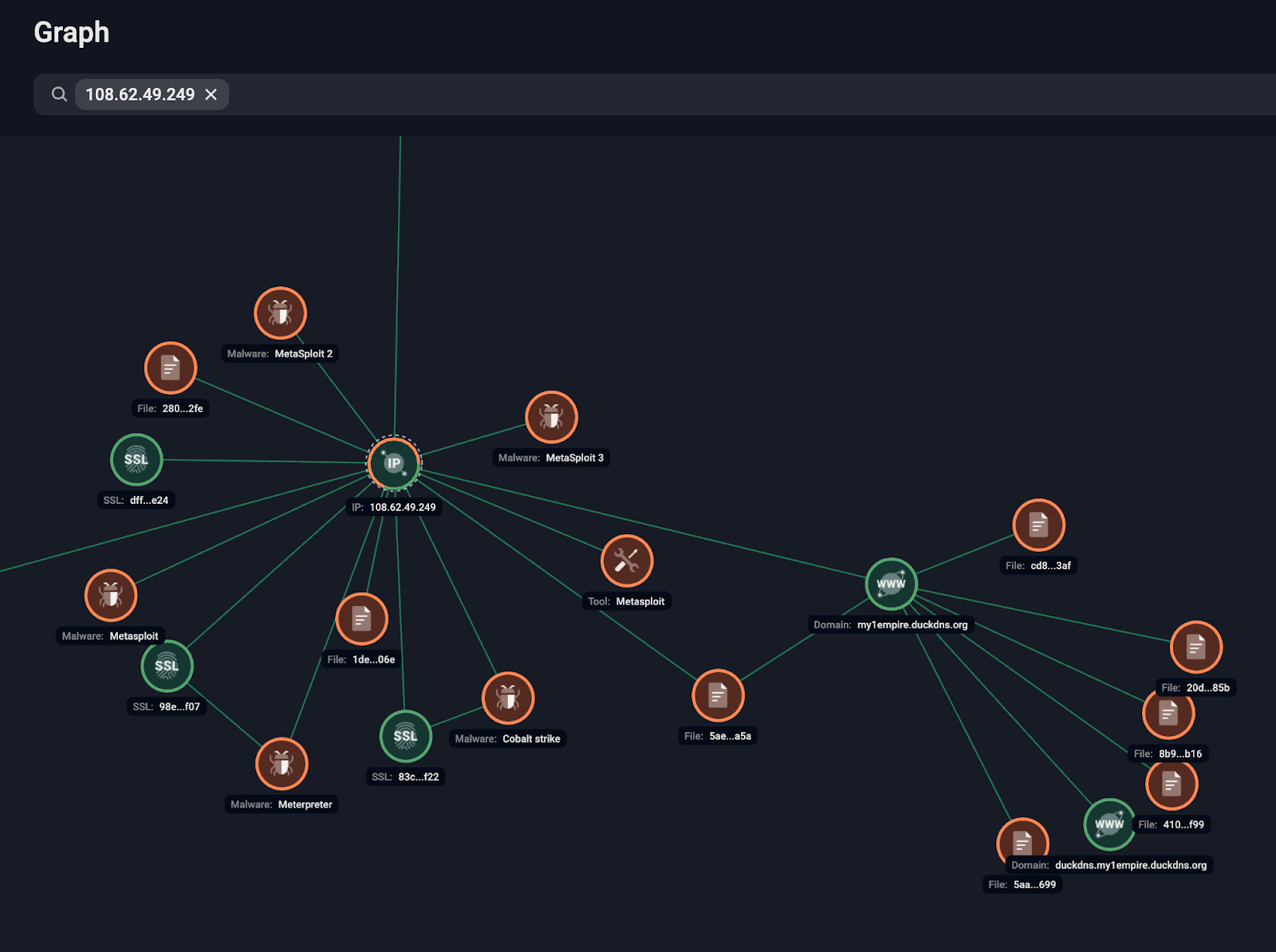
Figure 4. Group-IB Graph helped reveal that adversary C&Cs hosted both Metasploit and Cobalt Strike frameworks
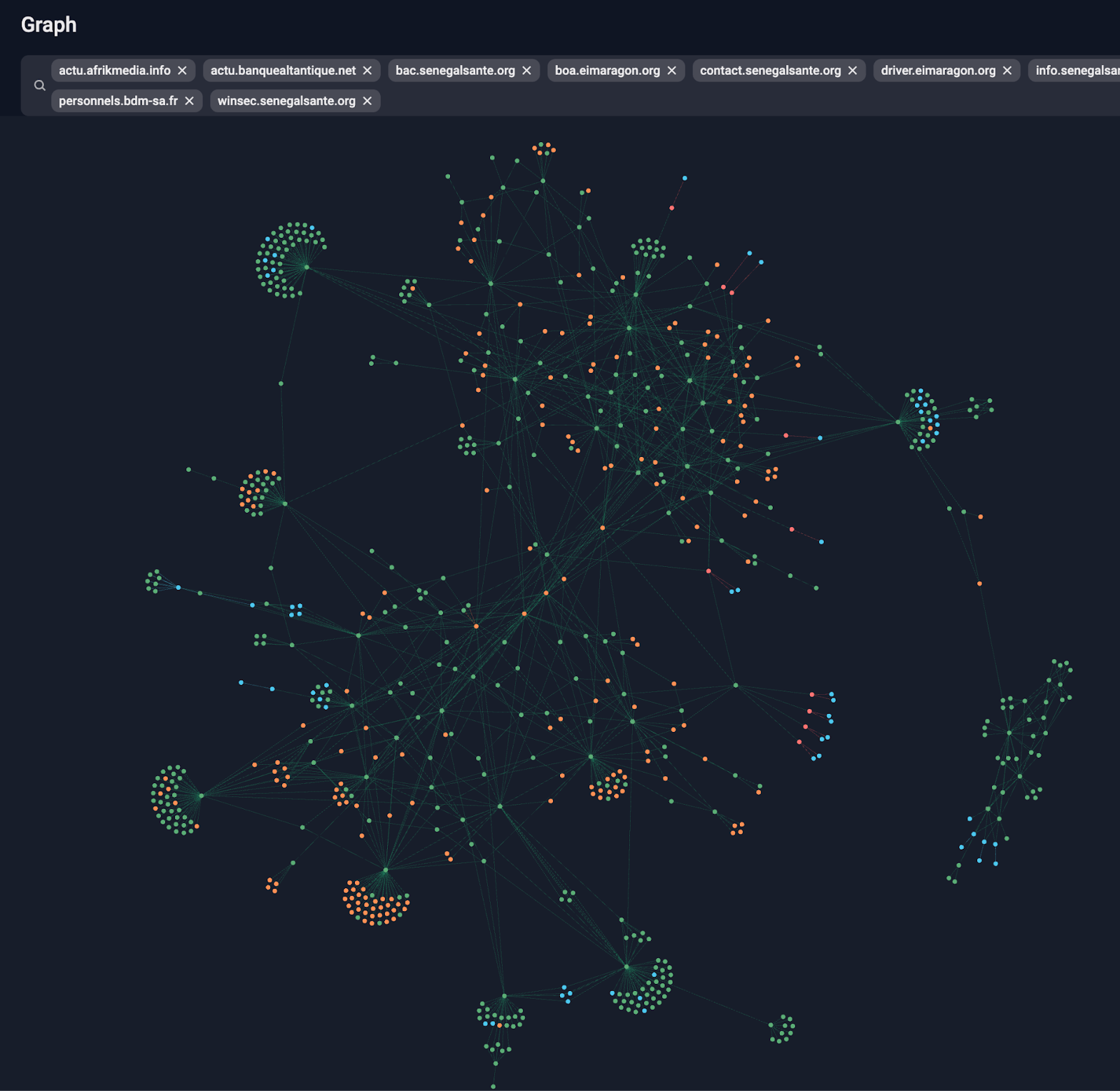
Figure 5. Group-IB Graph made connections between various servers used by OPERA1ER
Further investigation uncovered overlaps between OPERA1ER’s criminal activities and the personal online presence of its members. Some email addresses used for malicious domain registrations were also tied to social media accounts, underground hacking forums, and leaked credential databases. Analysts uncovered identical forum posts across several dark web marketplaces where OPERA1ER members discussed malware deployment, credential theft, and fraud techniques.
And justice for some…
In early 2023, the intelligence gathered by Group-IB, Orange-CERT-CC, and INTERPOL provided the foundations for Operation NERVONE, a multinational crackdown on OPERA1ER. The operation was coordinated by AFRIPOL, INTERPOL, and the Direction de L’Information et des Traces Technologiques (DITT).
After months of monitoring, the various authorities carried out a series of coordinated raids. In July 2023, INTERPOL announced that a key OPERA1ER member had been arrested in Côte d’Ivoire, which marked a major milestone in the fight against financial cybercrime. The arrest disrupted OPERA1ER’s ability to conduct large-scale fraud operations and dealt a serious blow to the group’s infrastructure.
Conclusion
Operation Nervone showed how advanced cyber intelligence and international cooperation can dismantle even the most resilient cybercriminal networks. OPERA1ER’s success was largely due to the use of open-source hacking tools and an in-depth understanding of financial transaction systems, but their downfall came from careless operational security mistakes that allowed investigators to track them.
As cybercrime continues to evolve, mobile money fraud, VPN abuse, and credential theft remain pressing concerns for financial institutions. The intelligence gathered during this operation has provided new tools and strategies for tracking similar threat actors in the future. Group-IB remains committed to supporting global cybersecurity efforts and ensuring that threat actors like OPERA1ER no longer operate unchecked.


























