Summary
Group-IB’s High-Tech Crime Investigations team played a key role in dismantling a sophisticated cybercriminal network that used a Remote Access Trojan (RAT) for Android to steal over USD 25 million. The Trojan was made to look like legitimate apps and enabled the gang to harvest banking credentials and personal information from victims in Singapore and Hong Kong. After months of investigating, Group-IB uncovered the infrastructure behind the phishing campaigns, which ultimately helped law enforcement in arresting the members of the syndicate.
Background
In early 2023, a wave of phishing scams targeting mobile users began sweeping across Southeast Asia. The scams involved distributing a Remote Access Trojan (RAT) for Android, which was hidden within fake mobile apps. The RAT made it possible for cybercriminals to control infected devices, steal sensitive information, and conduct fraudulent transactions.
The phishing campaigns were intricately designed. The threat actors set up phishing websites that imitated popular online platforms, retail shops, and even an anti-scam center. Abusing popular brands and masquerading Android Trojans as legitimate apps has been a notable trend among cybercriminals in recent years.
Behind the scenes
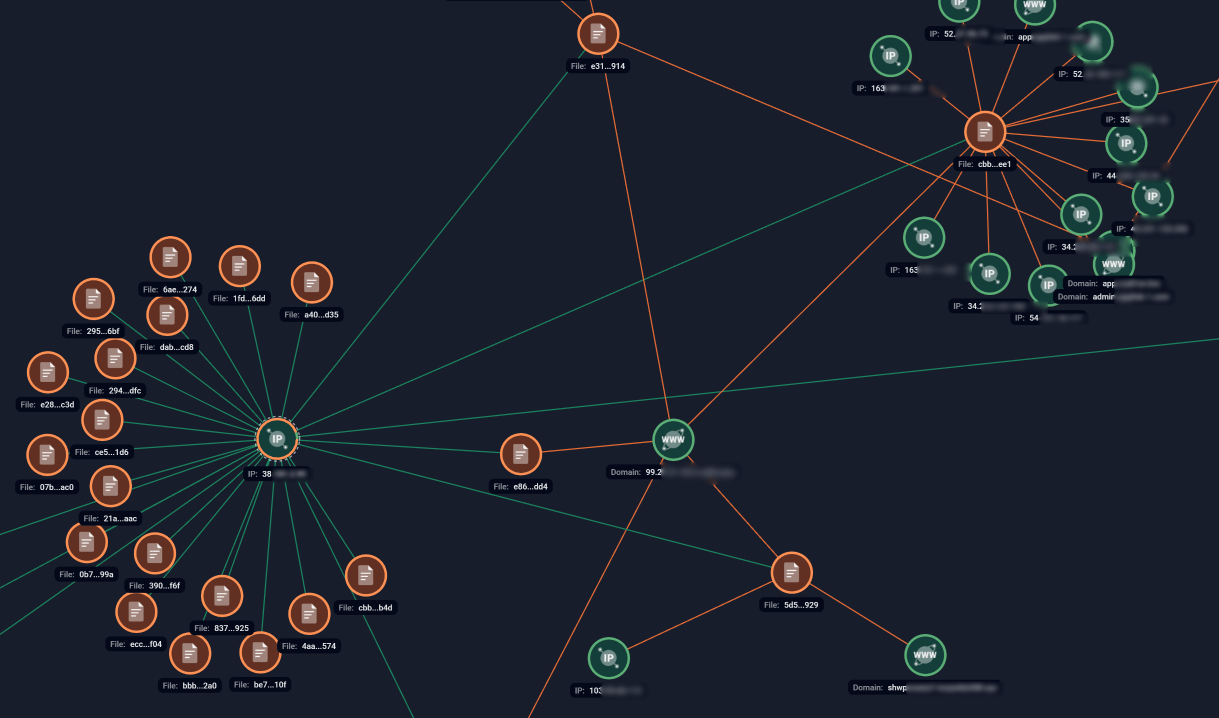
Group-IB’s High-Tech Crime Investigation team began analyzing the RAT campaigns in mid-2023. Our team found that the cybercriminal syndicate had used more than 250 phishing websites to distribute fake Android apps across Southeast Asia. Group-IB’s investigation revealed that the malware was being offered as part of a malware-as-a-service (MaaS) scheme, allowing other cybercriminal groups to purchase and deploy the RAT as part of their own attacks.
Using its patented Graph technology, Group-IB uncovered the network infrastructure behind the RAT operations in Singapore and Hong Kong. The investigation revealed over 100 command-and-control (C2) servers, which were used to manage the malware and coordinate attacks. By mapping connections between the C2 servers, Group-IB identified key figures within the syndicate who were responsible for distributing the malware and coordinating the phishing campaigns.
Impact
More than 4,000 people fell victim to the fraud. Singapore alone recorded nearly 2,000 cases in 2023, with losses amounting to over USD 25 million. The Group-IB Investigation team’s meticulous work helped build a complete picture of the attack infrastructure, leading to the arrest of 16 cybercriminals in Malaysia and Hong Kong and several malware operators in Taiwan. The efforts helped prevent further losses and reduce the scale of fraud across the region.
Storyline
The Singapore campaign with Android Trojans garnered increasing attention in May 2023. Group-IB’s High-Tech Crime Investigation team was quickly brought on board and carried out a thorough analysis of the campaign. The investigation revealed that the Remote Access Trojan (RAT) used in the attacks was based on a code that had been leaked in 2020. This updated version of the Trojan was promoted by the threat actor, initially on underground forums and later via Telegram. Group-IB further uncovered that there were at least 10 different brands abused by the threat actors, including several online shopping platforms, an anti-scam center, a pet grooming salon, a dumpling shop, among others.
When potential victims visited the fraudulent websites, they were prompted to download malicious apps under the pretext of making a payment or placing an order. The victims unknowingly granted extensive permissions to these apps, allowing the attackers to control their devices remotely. The RAT enabled the attackers to record keystrokes, capture screenshots, intercept one-time passwords (OTPs) sent by banks to verify transactions, and track the real-time geolocation of the devices. The malware operated silently in the background and could persist even after a device reboot. Using the stolen information, the cybercriminals made fraudulent transactions on the victims’ bank accounts, leading to significant financial losses.
Featured investigation details
As Group-IB analyzed dozens of Android RAT samples from the Singapore and Hong Kong phishing campaigns, they identified numerous phishing websites impersonating well-known brands, including online shopping platforms and local businesses.
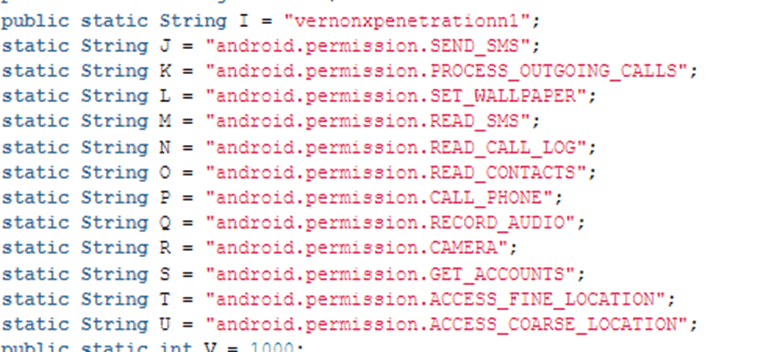
The list of permissions requested by a malware sample on the infected Android device is presented below:
Operators of the scheme also lured victims into enabling Accessibility Service permissions on their devices. Together with other permissions granted to a malicious application, the malware allowed cybercriminals to gain a total remote control of the device including geo location tracking and keylogger functions.
One of the phishing websites involved in the scheme was made to look like a large furniture store, as shown below:
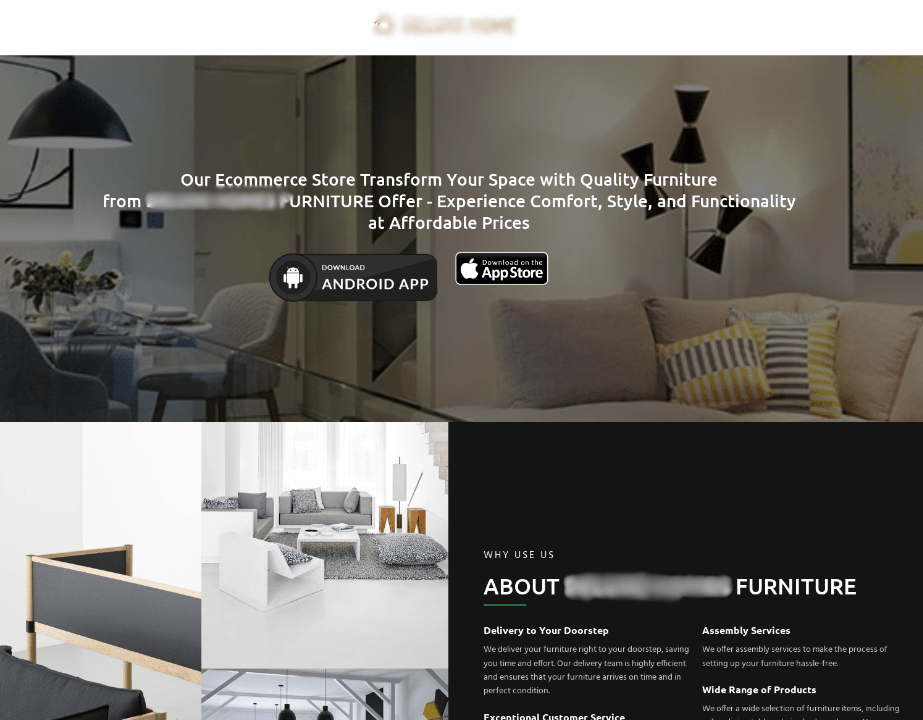
Figure 2. Phishing page made to look like the furniture online store
During the investigation, Group-IB experts discovered that the phishing websites were administered through the admin panel with a Chinese interface.
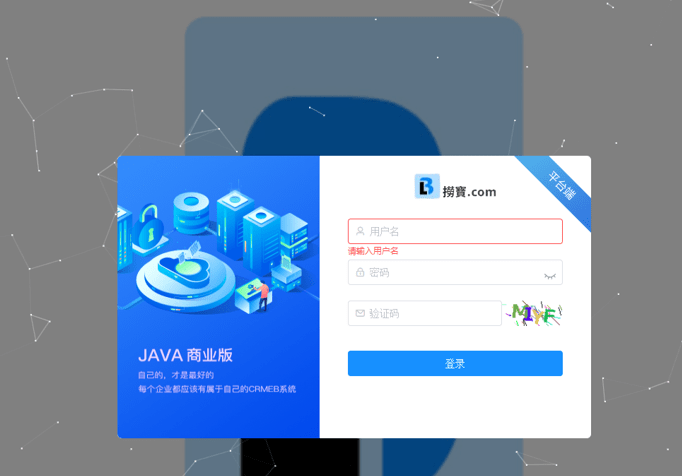
Figure 3. Example of a CRMEB admin login page for a phishing website
Further analysis of the command-and-control (C2) infrastructure revealed a password field in Chinese, which led us to the conclusion that Chinese-speaking threat actors were most likely behind the campaign.
The evidence gathered by Group-IB was handed over to law enforcement agencies, which was crucial to identifying and arresting key members of the group and dismantling their infrastructure.
And justice for all
In June 2024, the Singapore Police Force (SPF), the Hong Kong Police Force (HKPF), and the Royal Malaysia Police (RMP) announced a joint operation. Hong Kong Police Force named it Operation DISTANTHILL. Working closely with Group-IB, the law enforcement agencies identified at least 260 variants of the Remote Access Trojan (RAT) stored on command-and-control (C2) servers across Hong Kong and other Southeast Asian countries, all linked to the syndicate.
During the operation, the HKPF arrested 10 men and 4 women, aged 19 to 61, on charges of conspiracy to commit fraud and money laundering. Between June 12 and 13, 2024, two men aged 26 and 47 were arrested in Malaysia in a joint cross-border operation led by the SPF, with the support of the HKPF and the RMP. They are believed to be the primary masterminds behind the attacks and administrators of more than 50 C2 servers. One of the suspects faces a prison term of up to seven years, a fine of USD 50,000, or both, while the other might receive a penalty of up to USD 500,000, a prison term of up to 10 years, or both.
As part of the operation, Taiwanese police arrested four individuals who were operating a fake customer service center in Kaohsiung City, Taiwan. This campaign involved distributing malicious apps to unsuspecting customers and conducting unauthorized transactions from their bank accounts. The police seized a total of $1.33 million in both money and cryptocurrency from the suspects.
Conclusion
The success of Operation DISTANTHILL was a milestone in the battle against cybercrime in Southeast Asia. Group-IB’s advanced expertise and investigative tools, combined with its in-depth analysis of phishing campaigns and malware infrastructure, were instrumental in dismantling the cybercriminal syndicate. Carried out in close collaboration with law enforcement agencies, the operation not only brought the perpetrators to justice but also mitigated further financial losses.
As malware-as-a-service (MaaS) becomes more and more popular and as RAT malware continues to evolve, criminal buyers across the globe are likely to exploit such tools, potentially causing even greater damage. This evolving threat landscape calls for a vigilant, proactive approach from both users and organizations.
In such circumstances, the importance of a close collaboration between private cybersecurity firms and law enforcement agencies cannot be overstated. Group-IB remains steadfast in its commitment to combating cybercrime and will continue to strengthen partnerships, monitor and neutralize emerging threats, and strive to ensure a safer digital environment for society as a whole.