Background
In the mid 2010s, experts observed a rising trend where mobile Trojans gained rapid momentum and took on features of PC malware. Mobile malware was adopted by various types of cybercriminals, from professional, organized groups to dark web forum newbies with varying levels of experience in criminal activities in general. The least experienced cybercriminals relied on toolsets and technical support offered by underground vendors.
Threat actors targeted Android with mobile malware more and more often due to its widespread use (85% of device users) and the popularity of mobile banking in Russia. Most Android devices became infected when users downloaded apps from unofficial websites, although threat actors managed to also place Trojans on official app stores or bundle them with legitimate apps. Group-IB experts reported a three-fold increase in mobile malware incidents and 10 new hacker groups using mobile malware in 2015 alone.
The Cron hacker group, one of the most active players at the time, managed to access bank accounts belonging to Android users on a massive scale. At the height of their operations, the hackers infected 3,500 mobile devices per day. In total, the gang compromised over one million devices. Their large-scale campaigns drew the attention of Group-IB researchers and law enforcement agencies, prompting an investigation into the group’s activities.
Behind the scenes
The threat actors would attempt to steal money from 50 to 60 clients of different banks every day. An average theft was about $100. According to Group-IB’s investigators, Cron stole more than $800,000 in total.
Impact
In November 2016, law enforcement arrested 16 members of the Cron group, with help from Group-IB. The last active members were apprehended in April 2017 and there have been no attacks or thefts by the group since. The collaborative efforts between the police and Group-IB helped disrupt the group’s operations and prevented its expansion on a global scale.
Storyline
Group-IB first learnt about Cron in March 2015, when the criminal gang was spreading Cron Bot malware disguised as Viber and Google Play apps. Back then, Group-IB’s Threat Intelligence began tracking a new cybercriminal group distributing Android malware samples (“viber.apk”, “Google-Play.apk”, “Google_Play.apk”) on underground forums. Group-IB experts named the group Cron after what the hackers called their own malware. Cron targeted customers of 50 Russian banks, and all of their SMS banking services were under threat while Cron was active.
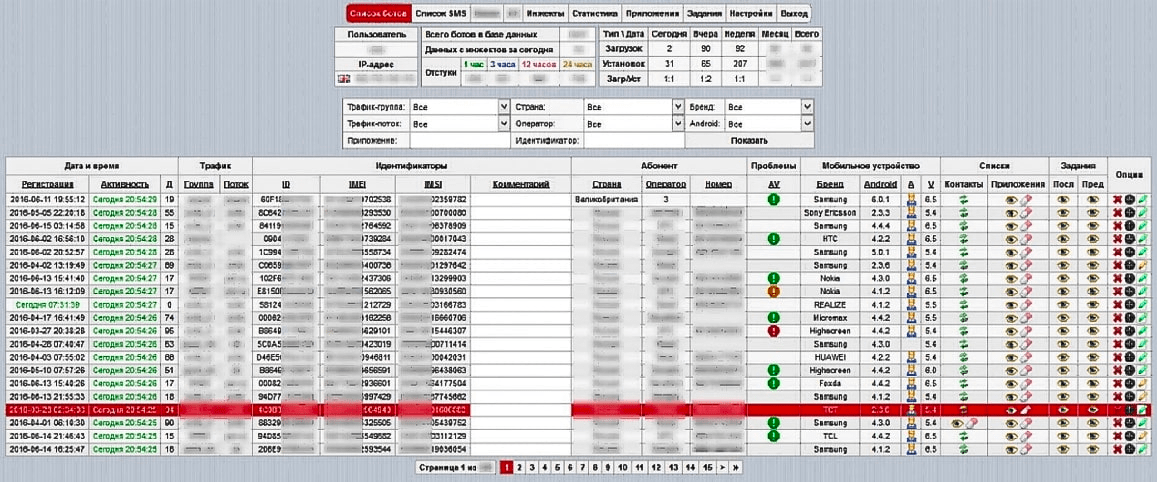
Figure 1. Screenshot of Cron Bot panel indicating more than 50,000 bot installations
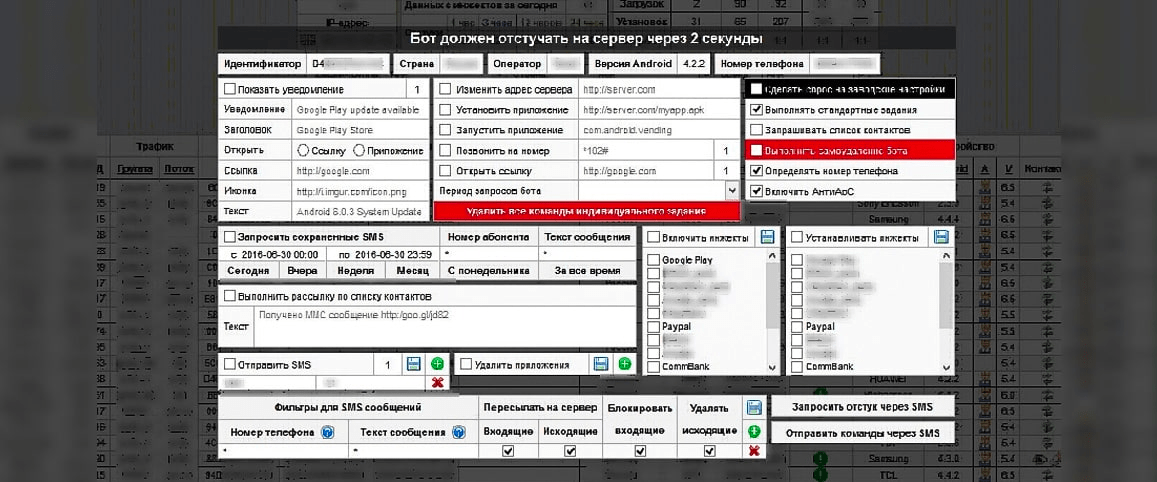
Figure 2. Screenshot of the panel showing daily Cron Bot installations
At the time, hackers no longer needed to know how to write a virus to be able to steal money from online banking users. Ready-to-use malware was available for purchase or rent on dark web forums. The Cron organizers had already been convicted of various non-digital crimes before they engaged in hacker attacks. As was the trend during that time, organized criminal groups were becoming increasingly involved in cybercrimes that promised “easy money”.
Cron’s attack scheme
The group’s approach was simple: after a victim’s phone was infected, the Trojan would automatically transfer money from the user’s bank account to a money mule account. To cash out the stolen money, the hackers opened more than 6,000 bank accounts.
The group used two vectors to compromise victims:
- Spam SMS messages with a link to a website infected with the banking Trojan. The Cron gang used a social engineering technique to inform recipients that their ads or photos had been shared on a website. The message usually said “Your ad has been posted on the website…”, or “Your photos have been posted here.” The threat actors shared links to a website that tricked the victims into downloading and installing malicious apps.
- Weaponized applications. Victims would often unknowingly install Cron malware on their phone by downloading fake applications masked as legitimate ones. The Trojan was spread by being made to look like applications such as Navitel, Framaroot, Pornhub, and Avito.
Once a victim had downloaded and installed a fake app on their device, the app would add itself to the auto-start and would send SMS messages to the phone numbers specified by the criminals, forward SMS messages received by the victim to C&C servers, and intercept SMS messages containing confirmation codes sent by the bank to verify transactions. Using these features, the malware could intercept 2FA messages sent to the users to authorize fraudulent transactions conducted by the threat actors.
A turning point in the investigation occurred in April 2016, when the Group-IB team discovered an ad about leasing a mobile Trojan called Cron Bot on an underground forum. The malware claimed to offer various options (which was reminiscent of PC Trojans) and promised the possibility to intercept SMS messages and calls, send USSD requests, and perform web injections. Group-IB experts suspected that the group was recruiting a new member because according to the ad author, they were willing to provide the Trojan to one person only. At the time, the group already had various individuals performing the roles of organizers, operators, “cryptors”, “traffers” and money mules.
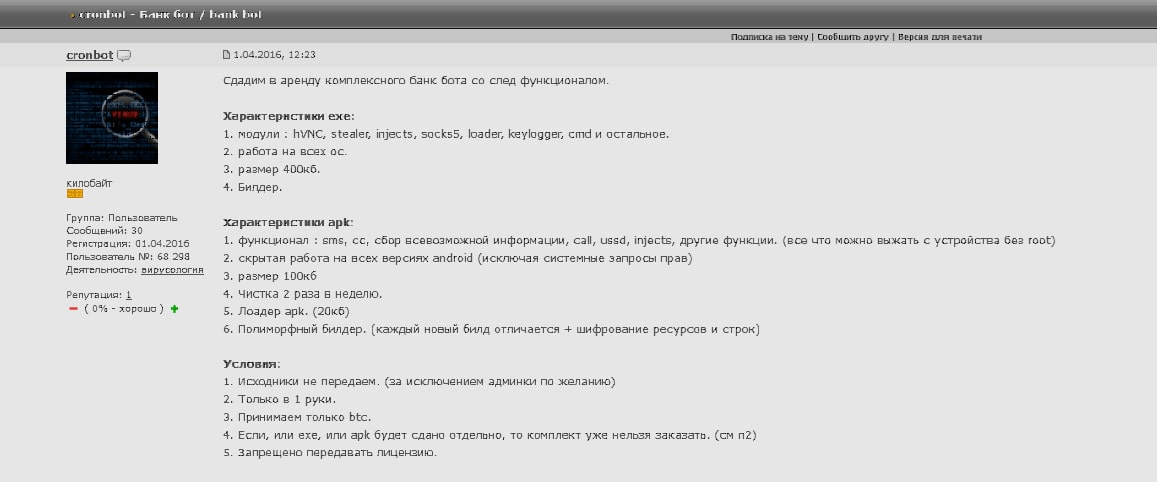
Figure 3. Forum ad about Cron Bot for lease
Translation:
We are offering to rent out a comprehensive bank bot with the following functionalities:
Exe characteristics:
- Has several modules: hVNC, stealer, injects, SOCKS5, loader, keylogger, cmd and more
- Works on every OS
- Has a file size of 400 KB
- Comes with a builder
APK characteristics:
- Functionality includes SMS hijacking, CC grabbing, all kinds of information gathering, call forwarding, USSD grab, overlay screens and other functions — all that you can squeeze from the device without root-level access
- Covert work on all versions of Android (excluding system privilege queries)
- APK size of 100 KB
- Cleanup two times per week
- APK loader (20 KB)
- A polymorphic builder to ensure every new build is different, plus encryption of resources and strings
Terms:
- The source code is not provided (except for the admin panel).
- The offer is limited to one person.
- Payment is accepted only in BTC.
- If any file is rented separately, the combination of both cannot be rented (see point 2)
- The license may not be transferred to third parties.
Plans for international expansion
Following successful campaigns in Russia, Cron decided to expand worldwide. To do so, in June 2016 the gang rented access to a more powerful mobile banking Trojan, Tiny.z (aka MarsElite), which was offered for $2,000 per month on underground forums. This universal tool could attack Android devices belonging to the customers of both Russian and international banks. The figures below show the Tiny.z admin panel, indicating the date and time of bot registration, web injections, the total number of bots, types and identifiers of compromised devices, etc.
Our analysis of the botnet control panel revealed that this was the same panel as the one used by the Russian criminal group called “404” that targeted clients of banks all over the world. It would seem that after a “404” member named Foxxx was arrested in 2015, Cron modified the malware.
The authors tailored the malware to be used for attacks on banks in the United Kingdom, Germany, France, the USA, Turkey, Singapore, Australia, and others. The Trojan scanned the victim’s phone for banking applications and displayed a universal window with the banking app’s icon and name retrieved from Google Play that prompted the user to enter their personal data.
Cron planned to start their international expansion with attacks targeting banks in France. They developed special web injections for the following French financial institutions: Credit Agricole, Assurance Banque, Banque Populaire, BNP Paribas, Boursorama, Caisse d’Epargne, Societe Generale, and LCL.
And justice for all
The group’s criminal plans were foiled, however. By November 2016, Russian law enforcement with support from Group-IB had identified all members of the group and collected digital evidence of the crimes they had committed. On November 22, 2016, the police conducted a large-scale operation in six Russian regions: 16 Cron members were arrested for computer fraud. During the raids, the authorities seized computers, bank cards, and SIM cards used by the criminal gang. The group’s last active member was caught in early April 2017 in St. Petersburg.
Conclusion
In the mid-2010s, hackers used Russia as a testing ground for their malware, with plans to expand globally later on. PC Trojans disappeared from the market but were soon replaced by even more dangerous Trojans for mobile phones and tablets. According to 2015 year-end results, online banking users lost over $1 million in attacks involving Android Trojans. Cron was the largest mobile malware gang operating in Russia at the time. As part of our fight against Android botnets, Group-IB’s investigation efforts helped to stop Cron campaigns in Russia and prevented them from affecting banking users worldwide.