Summary
Group-IB helped bring to justice members of Carberp, a hacker group responsible for large-scale attacks on remote banking systems. The group had operated an extensive botnet and infected more than 1.5 million computers. For the first time in cyber investigation history, the entire criminal chain was identified and arrested: the organizer managing the botnet, the operators carrying out fraudulent transactions, and the mules cashing out stolen funds.
Background
In 2011, cases of online banking fraud soared. The rapid increase was driven by two factors: advancements in malware designed to target banking systems and the emergence of more sophisticated criminal groups whose skills grew alongside their illicit earnings. Group-IB experts have referred to 2010 and 2011 as the “years of bank attacks,” noting that the number of bank-related incidents more than doubled in 2011 compared to 2010. Banking Trojans were involved in 92% of the cases. By December 2011, the largest botnet targeting banks (initially in Russia and later worldwide) had infected more than 1.5 million computers. This notorious botnet was known as Carberp.
In many ways, Carberp was a trailblazer on the cybercrime market. The group was among the first to extensively use specialized malware tailored to target common banking software (remote banking systems) for conducting large-scale fraud operations against major Russian banks. The Carberp Trojan was the first among banking malware to include Automatic Transfer System (ATS) features: automatic replacement of payment order details at the time when the document is signed and submitted and a fully automated process for creating and sending fraudulent payment orders using malware.
Group-IB specialists first encountered Carberp in late 2010, but it took two years and a great deal of effort to identify all the members of the group and help bring them to justice.
Behind the scenes
In spring 2012, Russian law enforcement conducted an operation to arrest one of Carberp’s leaders. Artem Artemov, Group-IB’s digital forensics expert, compared the operation to a scene from an action movie: “Suspended from ropes, special forces agents in black helmets and bulletproof vests came crashing through the 15th-floor window along with the broken frame. There were sounds of shattering glass and shouts of ‘On the floor!’. The suspect crawled on the floor in his underwear, screaming.”
Group-IB specialists watched the arrest like spectators, having completed their main work earlier. Once the criminals were detained, Group-IB forensic experts examined their computers and servers to establish links to the crimes.
Impact
In 2011, Carberp was one of the six most dangerous cybercriminal groups in Russia. The fact that they changed and updated their malware on a regular basis made them the number one threat for payment systems in the early 2010s. According to Group-IB, the group was one of the largest in terms of not only the scale of the thefts but also the total amount of money stolen. Group-IB’s investigation into the group’s botnet and servers, in cooperation with organizations from various countries (including the Netherlands and Canada), prevented further thefts from customers at more than one hundred banks around the world.
Storyline
Group-IB came across Carberp’s activities in November 2010. Substantial efforts were required to identify the organizer and his accomplices, however. The investigation was made more complicated by the frequent travels of the group’s organizer, who moved around the country and abroad. To add to the challenge, the malware was being used by multiple groups, with command-and-control servers dispersed across several countries. Nevertheless, by January 2011, our experts had identified the mastermind behind the group.
Group-IB experts believed that the organizer was the owner of the botnet used for infecting banking software and theft through online banking. Most of the other members focused on cashing out the stolen money. Besides financial theft, the group was also involved in conducting distributed denial-of-service (DDoS) attacks.
Carberp was the biggest botnet in Russia and other post-Soviet countries and it infected more than 1.5 million computers. The hackers used a banking Trojan to deplete bank accounts. They stole money from companies and their customers by intercepting login names, passwords and electronic keys.
How Carberp targeted accountants to steal millions
The Carberp Trojan was designed first and foremost to target companies who relied on remote banking systems to perform a huge number of financial transactions every day. Its initial victims were accountants and people working in financial departments, whose work and home computers became the focus of relentless attacks. At the height of its operations, Carberp managed to compromise up to 30,000 users per day.
In a strategic move to gain access to a large user base, Carberp breached websites often used by accountants as well as popular media platforms and major online retailers. These websites, already infected with exploit kits such as BlackHole, served as launch points for drive-by download attacks. When a visitor’s system was found to be vulnerable, the Carberp banking Trojan (Win32/Carberp or Win32/RDPdoor) was installed automatically, without the user’s knowledge.
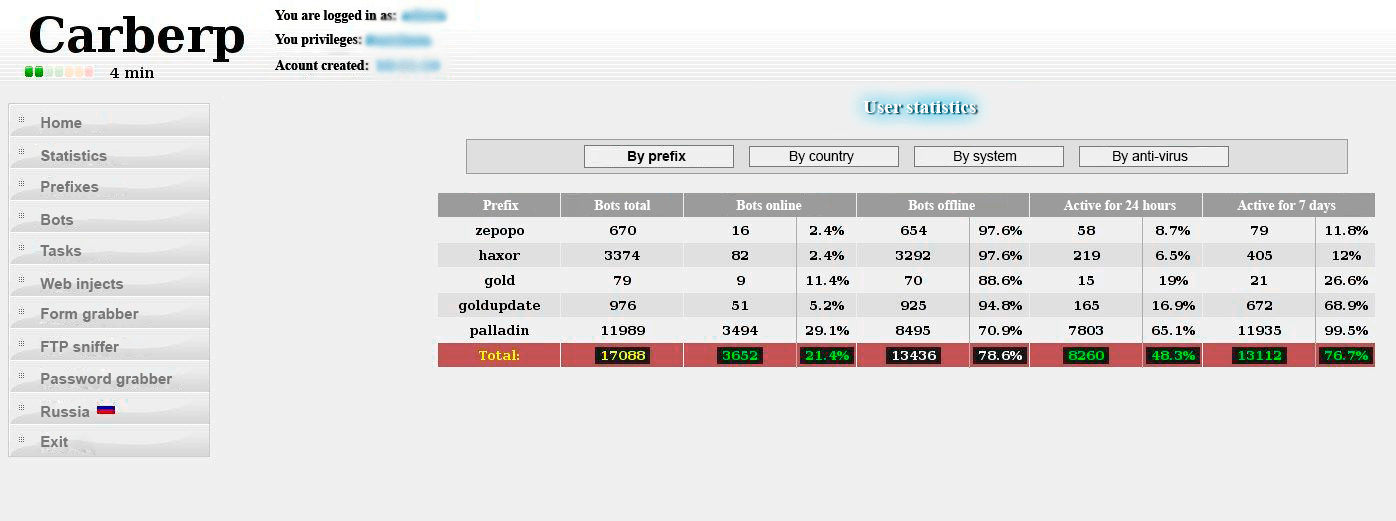
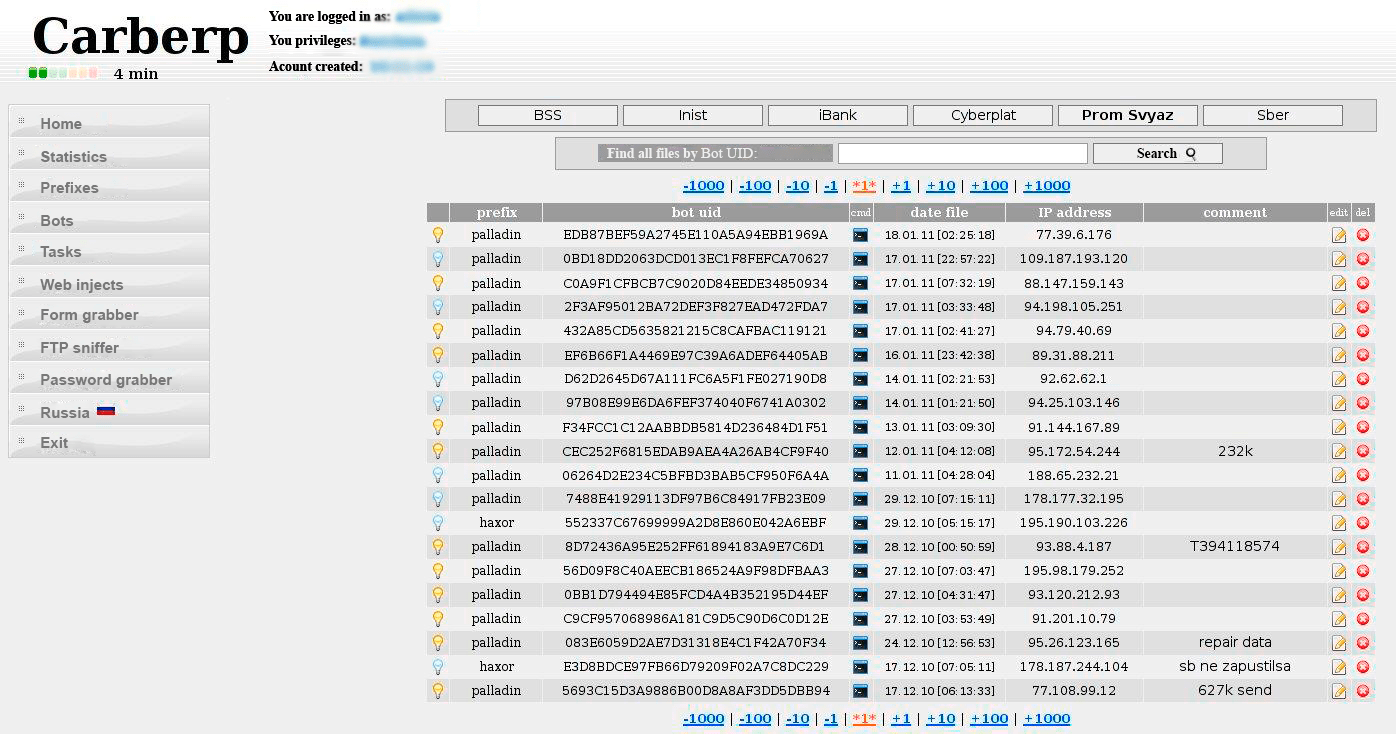
Figures 1-2. Carberp admin panel
After Carberp infiltrated a system, it would establish covert remote access and scan for client applications that provided access to remote banking system accounts. The Trojan would then copy electronic signature keys and capture screenshots to monitor the victim’s online banking activities.
Once the victim’s banking software and credentials were intercepted, the operator would craft fraudulent payment orders to transfer funds to pre-arranged accounts. The stolen funds were then laundered through bank cards registered to fake individuals or entities and eventually collected by money mules through ATMs.
Experts considered the Carberp malware to be highly effective — its continually evolving defenses made it difficult for many antivirus programs to detect it. Carberp members were equally adept at evading detection in the physical world. They even rented an office space in Moscow, posing as a legitimate tech firm. The office housed equipment that was used to connect to systems belonging to victims, along with bank cards and numerous forged documents.
Initially, Carberp targeted only Russian-speaking countries, breaking the unspoken rule among many cybercriminals to not target victims in Russia and former Soviet states. Around 70% of all Carberp infections were on computers in Russia and the CIS. The group later expanded its range to Western financial organizations, however, including in Turkey, the United Kingdom, Spain, the United States, and Italy.
In March 2012, a joint investigation involving law enforcement, the affected banks and Group-IB’s Cyber Investigators and Digital Forensics experts led to eight members of Carberp being arrested. During the operation, the police seized computers, mobile devices, fake bank cards, fake stamps, and over $250,000 in cash.
And justice for all
In April 2014, two organizers of the Carberp hacker group, which stole money from accounts belonging to over 1,000 Russian citizens and companies, were sentenced to five and eight years in prison. The criminals were two brothers from Moscow, aged 31 and 28 at the time they were sentenced. Interestingly, the younger brother had played the leading role. He had extensive criminal experience and there was already a warrant in his name for real estate fraud. The older brother was found guilty of theft and fraud only. Meanwhile, the younger brother was also convicted of forgery, production, and distribution of forged documents, in addition to theft and fraud.
Conclusion
Although all the members of Carberp were arrested, questions remained about the fate of the malware’s true creators — those who had developed and sold it on the underground market — as well as the owners of the affiliate networks that distributed the Trojan. As these individuals remained at large, new criminal groups emerged that used new modifications of Carberp. In the summer of 2012, Group-IB assisted law enforcement in arresting members of other criminal groups (Germes and Hodprot) that were using modified variants of Carberp.
Although Carberp malware remained on the market long after the botnet owners were arrested, the case set a powerful precedent and signaled to cybercriminals that online theft was no longer a safe and easy “income stream.” It showed that law enforcement and cybersecurity companies like Group-IB now had the tools to not only identify criminals but also gather sufficient evidence to prosecute them successfully. For a while, the investigation helped to reduce the number of cyberattacks in 2012 and stopped Carberp from expanding further.