Case Background
Over the years, Group-IB has supported and led crime-nabbing operations worldwide that have brought nefarious perpetrators to justice – helping businesses, law enforcement, and citizens recover from financial damage, restore law and order, and regain much-needed peace of mind.
One prominent investigation led us to identify and takedown a malware kingpin who once dominated the exploit kit sales market, with 40% of infections attributed to his tools. The name behind two such exploit kits—BlackHole and Cool Exploit Kits—was Paunch.
Paunch, a cybercriminal hiding in plain sight, masqueraded as an advertising and tourism manager. By day, the 27-year-old was a law-abiding citizen. However, he was also the mastermind behind some cybercrime businesses, offering infamous exploit toolkits, anti-virus simulators, and crypting services.
Group-IB’s Digital Forensics and Incident Response (DFIR) and Cyber Investigations teams played a major role in assisting the police in investigating and suppressing the criminal activities of the Russian hacker, who remained virtually hidden for a long time. Through their efforts, they managed to identify and track his infrastructure, partners, and clients. This case marked the first successful prosecution of such a cybercriminal in the country. On October 4, 2013, our experts’ efforts led to his arrest.
Group-IB’s team laid out the complete profile of the accused malware author, including several of his pictures and how he amassed over 1,000 customers and generated a staggering $50,000 per month from his illegal activities.
Behind the scenes
The analysis of underground forums and exploit kits created by Paunch revealed critical details about the exploits’ target vulnerabilities, the buyers of these exploit kits, and more. Additionally, he had more than 1000 contacts of clients and partners in his Jabber.
The case didn’t end with Paunch; during a later stage of the investigation, some of his partners and major clients, including Germes, Pioneer, ADV, Velles, and others, were also arrested.
Impact
Paunch’s confidence in evading detection for his cybercrimes grew stronger each year, starting in 2010 when he got his first exploit kit buyer. However, his assumptions were shattered in 2013 when he was arrested in October along with a dozen other individuals involved in selling, developing, and profiting from the crimeware package. This was the first case in Russian law enforcement practice when an exploit kit developer was arrested as a theft accomplice.
The conclusion of the investigation brought their operations to a permanent halt, including the use of BlackHole and CoolKit, which were perhaps the driving forces behind an explosion of cyber fraud in those years. The damage caused by their activities amounted to 2.3 million USD, as 40% of infections detected worldwide were carried out using Paunch tools.
Numerous threat actors utilized his exploit kit to deliver malware onto victims’ devices silently. It facilitated the delivery of banking malware, various downloaders, and other types of trojans. The arrest of this threat actor changed the landscape significantly because threat actors lost an effective tool for delivering malware. They consequently shifted from drive-by techniques to spam campaigns.
Additionally, Paunch’s arrest directly reduced demand from other cybercriminals who relied on hacking legitimate websites to redirect victims to the exploit kit landing page, where exploitation and subsequent infections occurred.
Storyline
Online assets, networks, endpoints, devices, and data servers – everything that a business views as opportunities for growth can become the means for cybercriminals to infiltrate, depending on the availability of exploits.
Exploit kits are a means of launching many cyber threats. They are potent tools for automated attacks that leverage compromised sites to divert web traffic, scan for vulnerable browser-based applications, and deploy malware.
Paunch didn’t just create and sell these exploit kits; he continuously innovated them to obfuscate detection and make them more potent tools for cyber destruction. In 2010, Paunch officially got the BlackHole exploit kit’s first sale and then quickly gained popularity among cybercriminals, which helped spread his malicious programs far and wide.
BlackHole exploited vulnerabilities in web browsers, particularly zero-day vulnerabilities for which no patch had been released, as Paunch’s weapon of choice. Compromised websites and email spam were the primary delivery methods for BlackHole’s malicious payloads.
The BlackHole Exploit Kit was available for rent on the seller’s server for $500 per month, or the software itself could be rented for installation on one’s own server for $700 for three months. Additionally, dedicated support was provided at an additional cost for some key clients.
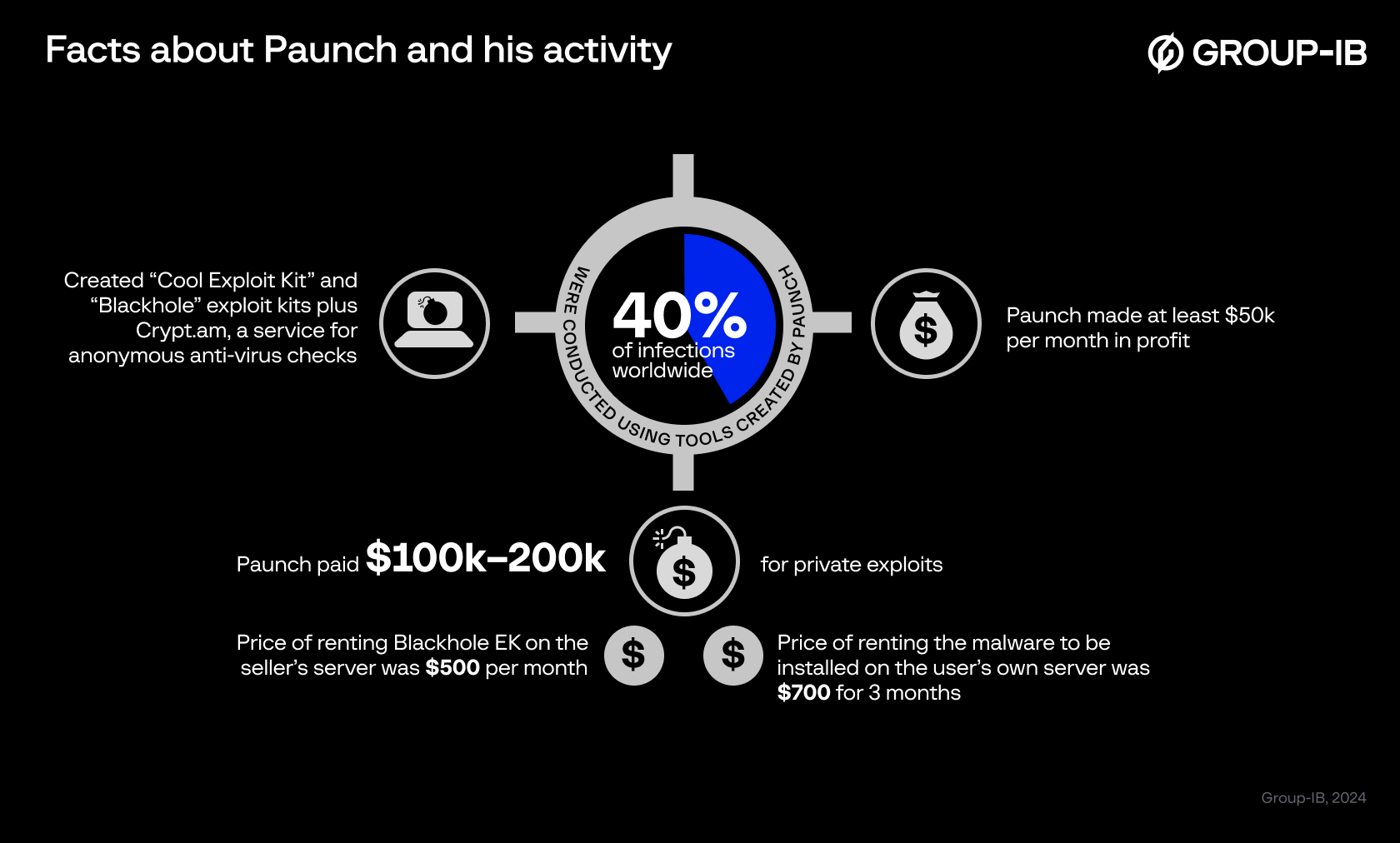
Image 3. Paunch profile infographics
Group-IB’s Cyber Investigators also revealed that Paunch had over 1000 customers, earning him a staggering $50,000 monthly. This substantial income enabled him to afford luxuries such as a white Porsche Cayenne, symbolizing his illegal wealth.

Image 2,3: Paunch’s official photos at the time of the arrest
Paunch's criminal activities may have started with BlackHole, but didn’t end there…
He also specialized in supporting the online service Crypt.am, which automatically obfuscated malware source codes. In other words, Crypt.am protects malware from detection by antivirus programs. The unlimited tariff price for this service was $50 per month, without any limit on the number of “protected” malicious software.
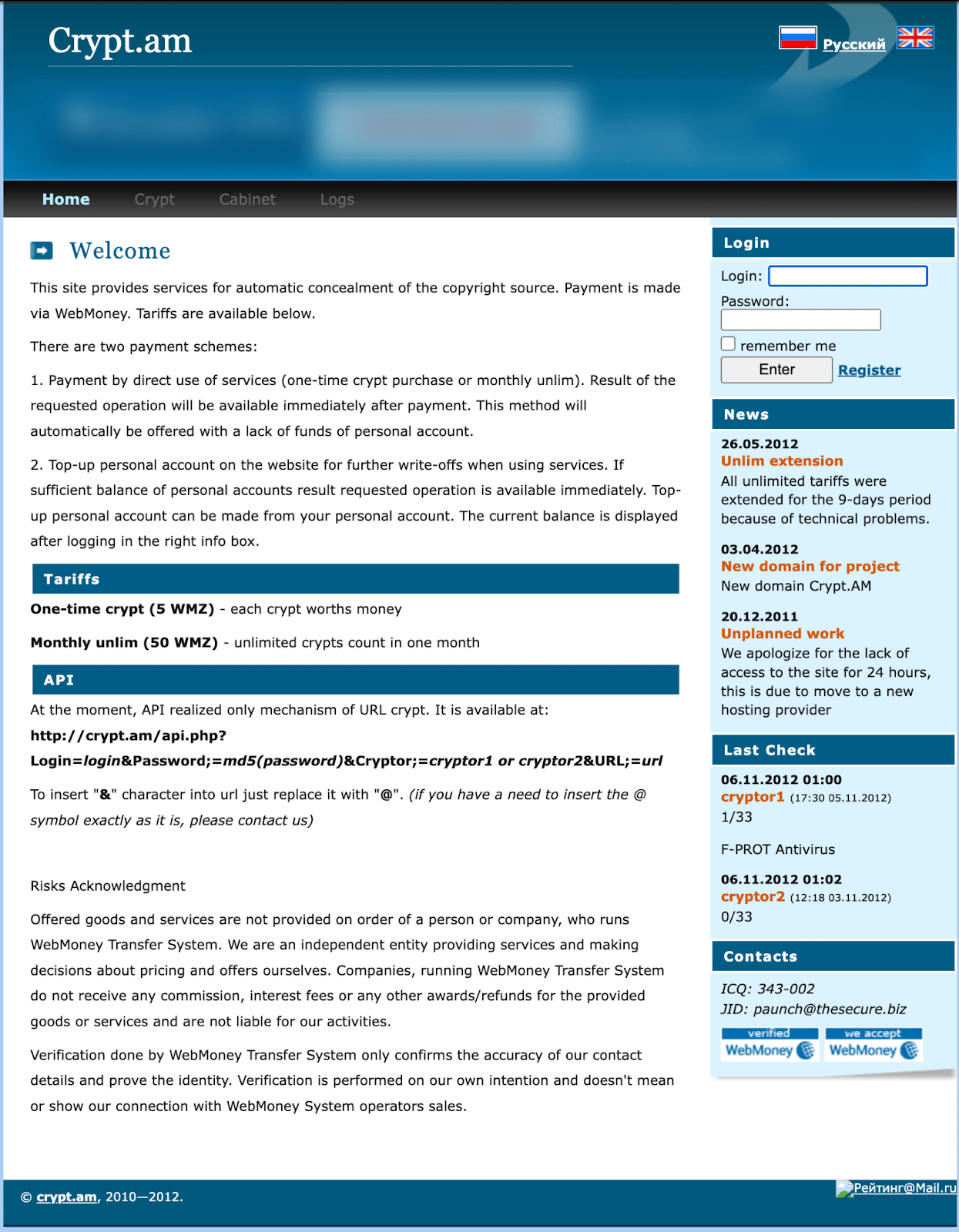
Image 4: Original screenshot of the underground site from Hi-Tech Crime Trends 2014
Over the years, the BlackHole Exploit Kit became increasingly popular among cybercriminals and was used to steal from bank customers worldwide.
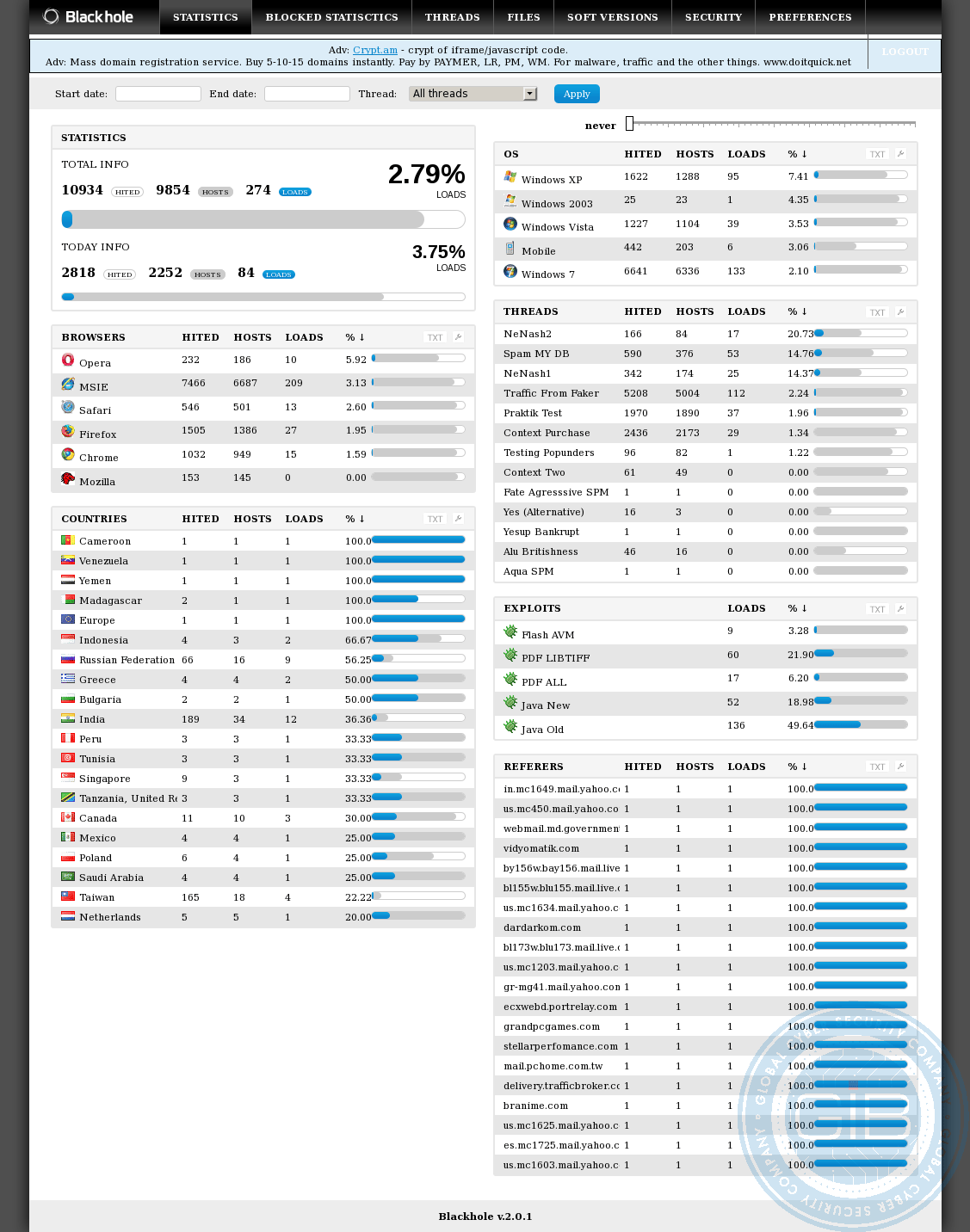
Image 5: BlackHole statistics page, version 2.0.1
Need a more potent exploit kit? Pay a higher price
Paunch collaborated with several other cybercriminals to purchase new exploits and security vulnerabilities to enhance BlackHole’s success. These efforts funded a pricier ($10,000/month) and more exclusive exploit pack called the “Cool Exploit Kit.” This new exploit kit aimed to improve the quality of exploiting vulnerabilities, thereby increasing the number of malicious programs installed on victims’ computers.
Cool Exploit Kit was rented out for a higher price and unavailable to beginner hackers. According to estimates by various antivirus companies, the sale of BlackHole and Cool Exploit Kits accounted for about 40% of the total market.
A fellow cybercriminal, spreading the word for Paunch
Paunch’s strong ally in boosting his sales was a known fraudster, ‘J.P.MORGAN’, who helped him acquire new exploits. On various hacker forums, J.P.MORGAN posted ads expressing interest in buying browsers with zero-day vulnerabilities. However, he provided his Jabber contact address as gugusik@thesecure.biz – the same address used by Paunch. The original budget for the purchase of exploits was $100,000 but was later increased to $200,000. Attempts were made to contact well-known brokers actively working with government agencies to acquire new exploits.
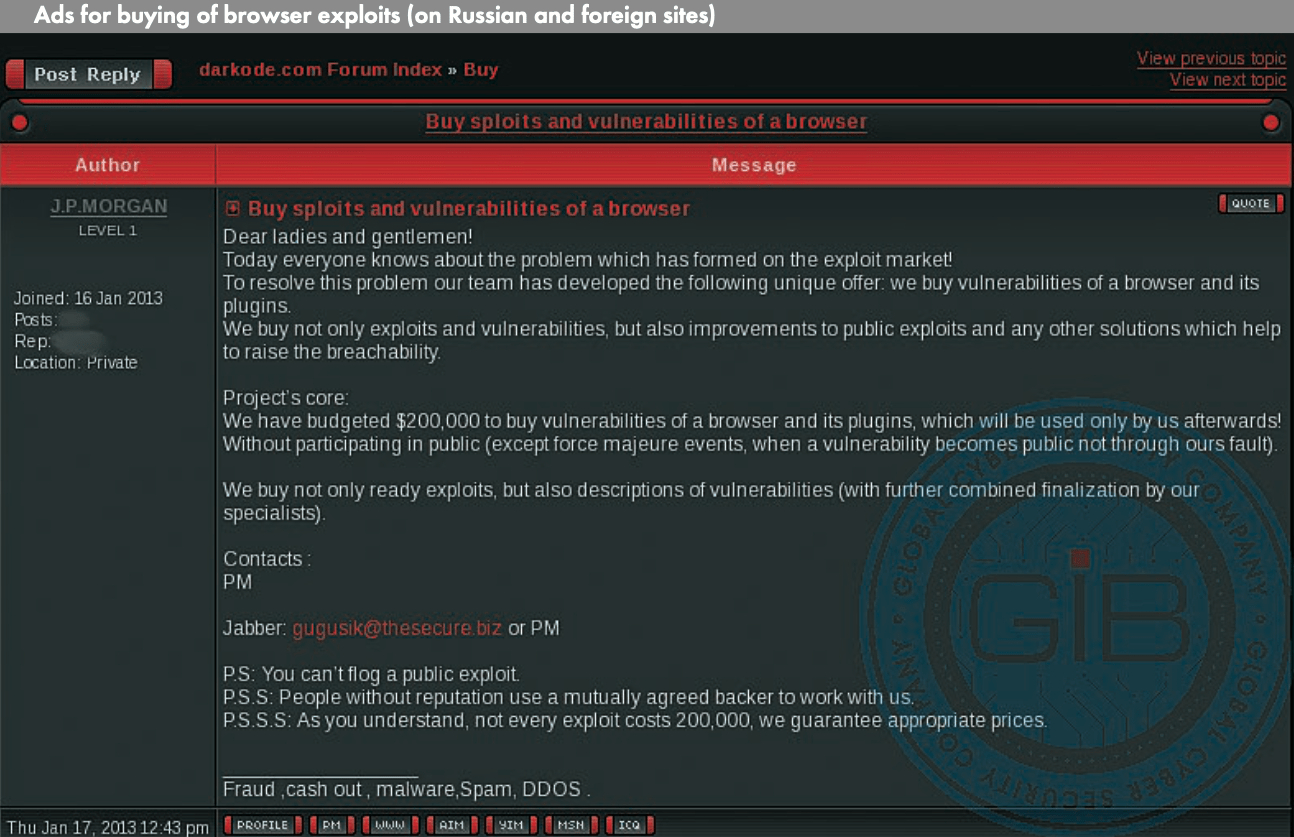
Image 6: An advertisement on one of the hacker forums displaying the new price for selling exploit kits.
Putting Paunch’s face behind these illicit activities
Group-IB’s Cyber Investigators played a significant role in exposing Paunch’s intricate cyberwarfare operations, arsenal, and his network of buyers and allies. They also mapped his exploit kits, the purchase of newer exploit kit frameworks, and other malicious services he offered.
Through conducting several Incident Response operations when banking trojans were used to steal money from corporate bank accounts, our experts observed that the BlackHole Exploit Kit was predominantly used.
We further discovered a method to track malicious infrastructure, including landing pages, traffic management systems, and admin panels used by different clients. Collaborating with law enforcement, Group-IB traced the operations and identified those responsible for exploit development, infrastructure support, and client relationship management.
Simultaneously, Group-IB analyzed Paunch’s activity on dark web forums, messages, support, and clients to gather more information. Upon identifying the individual behind the nickname Paunch, law enforcement initiated operations on the ground.
Group-IB’s DFIR (Digital Forensics and Incident Response) experts were involved in search and seizure operations to preserve evidence during this activity. Working alongside law enforcement, they awaited his return to his hometown for several days, as he had suddenly moved out of town. Upon his return, law enforcement took control of the situation, leading to its righteous conclusion—Paunch’s arrest, which was executed early in the morning.
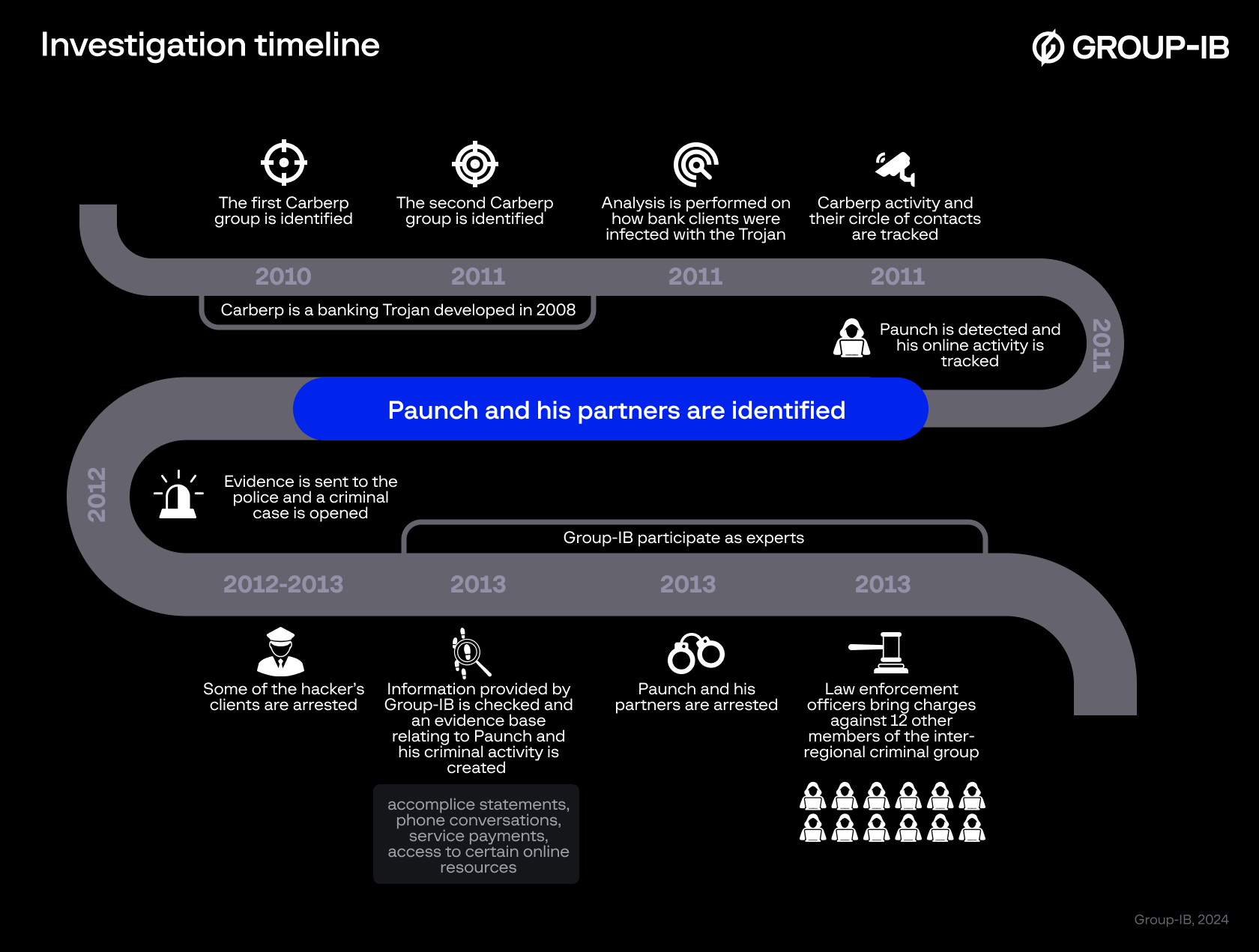
Image 7. Investigation timeline
And justice for all…
Apart from Paunch, the police also charged 12 more members of an interregional criminal group, which included well-known cyber criminals such as Germes, Pioneer, ADV, Velles, and others.
These cybercriminals were charged with forming and participating in a criminal organization to commit serious crimes. Membership in such an organization is punishable by 5 to 10 years in prison. The total damage caused by this group of criminals is estimated at 2.3 million USD.
Conclusion
With over 1400+ cybercrime investigations supported or led by Group-IB, our experts have been a force behind taking down some of the most notorious criminals plaguing the cyber world. Paunch, the mastermind behind BlackHole and Cool Exploit Kit, was a significant arrest due to his tools’ massive impact in propelling cyber fraud. Almost every report on malware activity between 2010 and 2013 mentioned these exploit kits prominently.
Paunch’s arrest is not just a victory—it’s a warning to others that law enforcement can reach them. These investigations require time, effort, and cooperation, but they demonstrate that no cybercriminal is beyond the law’s reach when authorities and cybercrime fighters work together.

























