Introduction
The healthcare sector has undergone a massive digital transformation over the past decades. Patient information, medical services, and associated transactional processes are now more accessible and efficient for global patients through websites and applications.
The rapid expansion of data generated online — in both volume and frequency — has made storage, transmission, and analysis easier, but medical information available online needs to be subjected to strict cyber oversight and protection to avoid tampering, leaks, and other cyber threats.
To enable proactive cybersecurity, healthcare providers must continuously assess and monitor risk indicators, alerts, and other signals generated by their entire technology infrastructure to stop threats in real- time. Overlooking security blind spots can significantly weaken an organization’s security posture. Such was the case with one of the fastest-growing healthcare providers in Malaysia — who was blinded by the very challenge when a cyber threat escalated into a full-blown attack, prompting them to seek the expertise of a global cybersecurity service provider like Group-IB.
The Malaysian private healthcare provider operates with a high- responsibility mission to save lives, and any delays or disruptions could have catastrophic consequences — an outcome the healthcare provider was determined to avoid. The cyber threat delayed patient care, creating a critical and immediate need to act. Given its high-stakes mission, the provider responded quickly with the help of experts and compensated the threat actor to regain access to sensitive files.
Initial pain points:
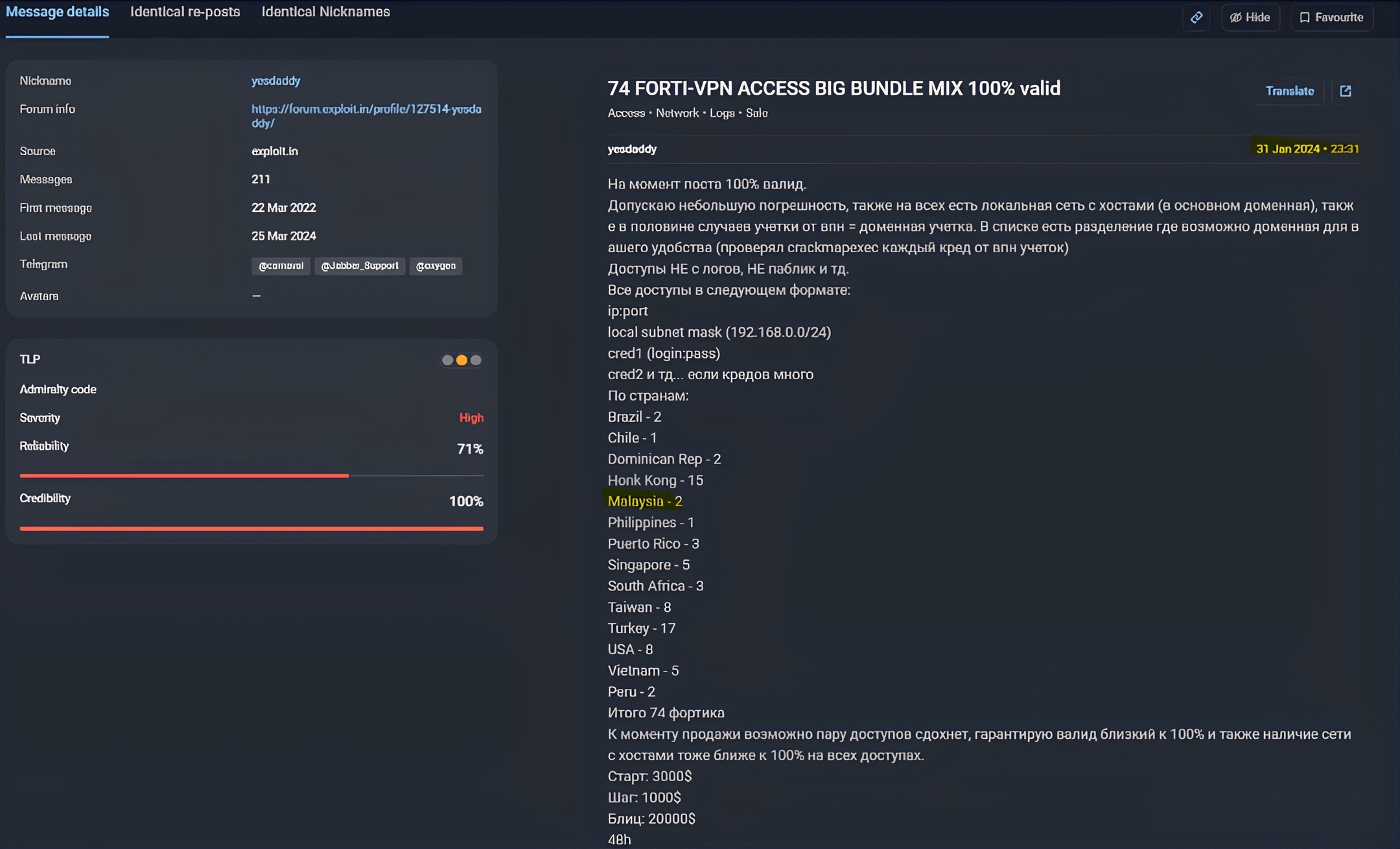
- A ransomware threat from a threat actor previously tracked and researched by Group-IB
- Limited context in Threat Intelligence, with no clear indicators of cyber threats, ultimately leaving the healthcare provider vulnerable to ransomware attacks
- Subpar risk advisory services
- Weak incident response strategy with no Plan of Action (POA) at the time of the attack, leading to delays in Mean Time to Recovery (MTTR) and inadequate support for takedowns
- The organization had a traditional and legacy security stack that lacked the necessary capabilities and visibility to defend against modern cyber threats
- Lack of visibility into current and emerging vulnerabilities in their network infrastructure, resulting in security gaps
- Insufficient critical insights to evaluate and improve the cybersecurity posture