Intelligence.
Action. Defense:
Intelligence (CTI)
risk-intelligent
another
world, insights-packed resource with insights on

Building a CTI function from scratch

Maturing existing
capabilities

Scaling operations across teams and regions
What You'll
Learn
types of intelligence

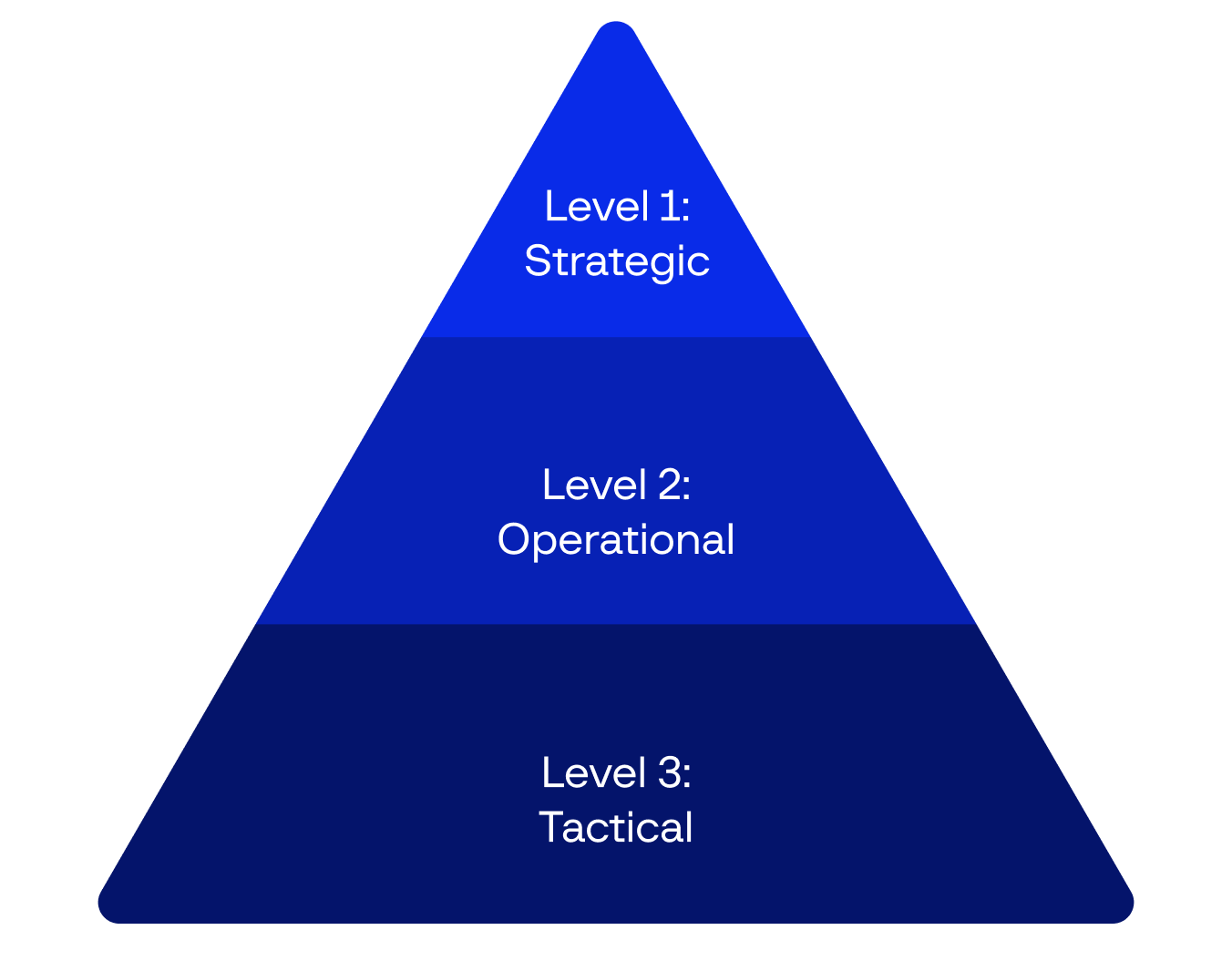
components

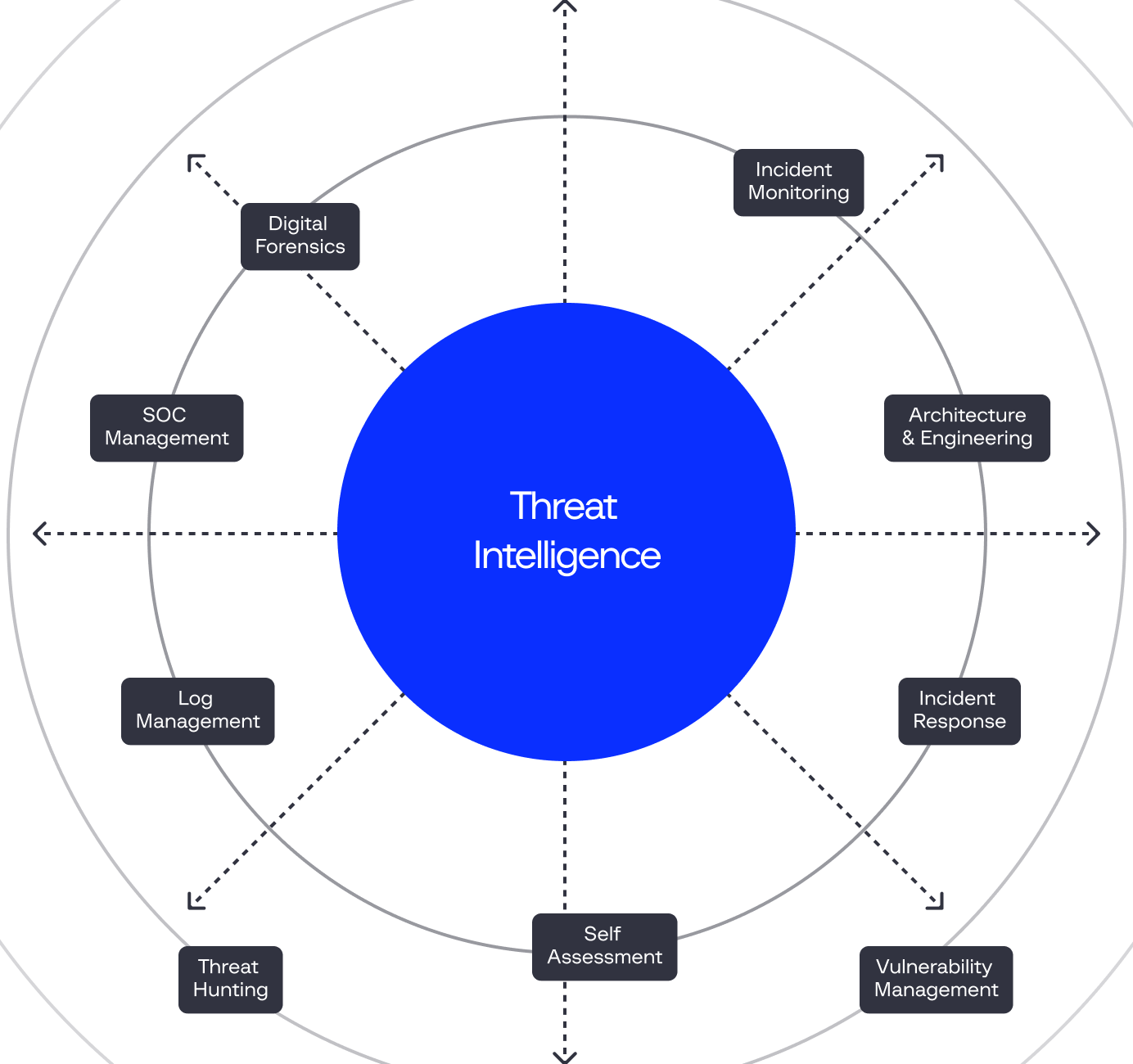
intelligence lifecycle


operation, and optimization
workflow


Intelligence at a glance
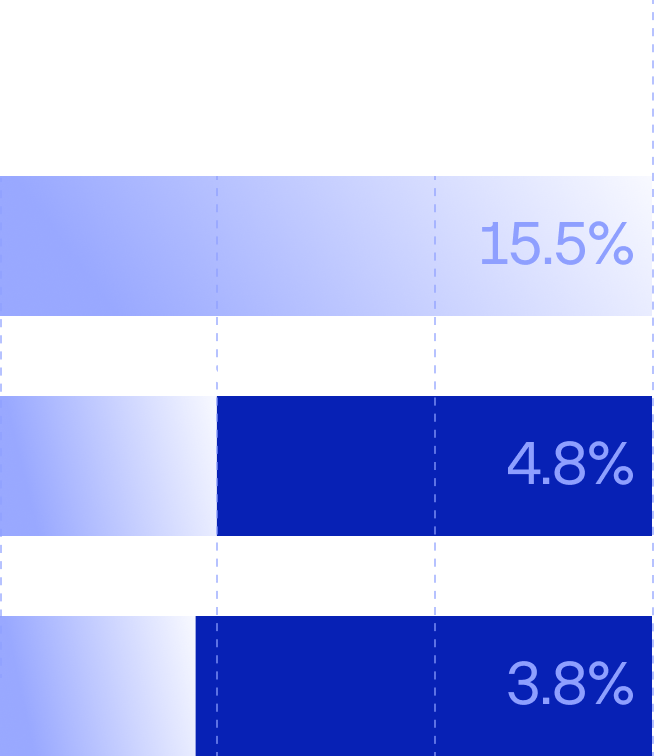
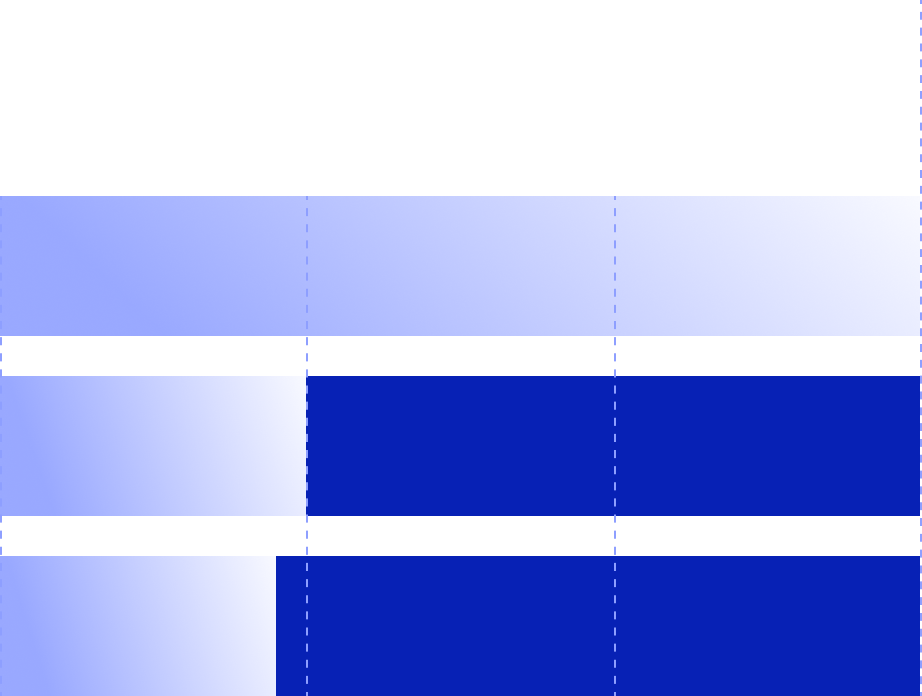
Geopolitical conflicts drive attack spikes.
surged by

of cybercrime
Threat groups
Ransomware-as-a-Service groups
Threat Intelligence

& Intelligence Outputs
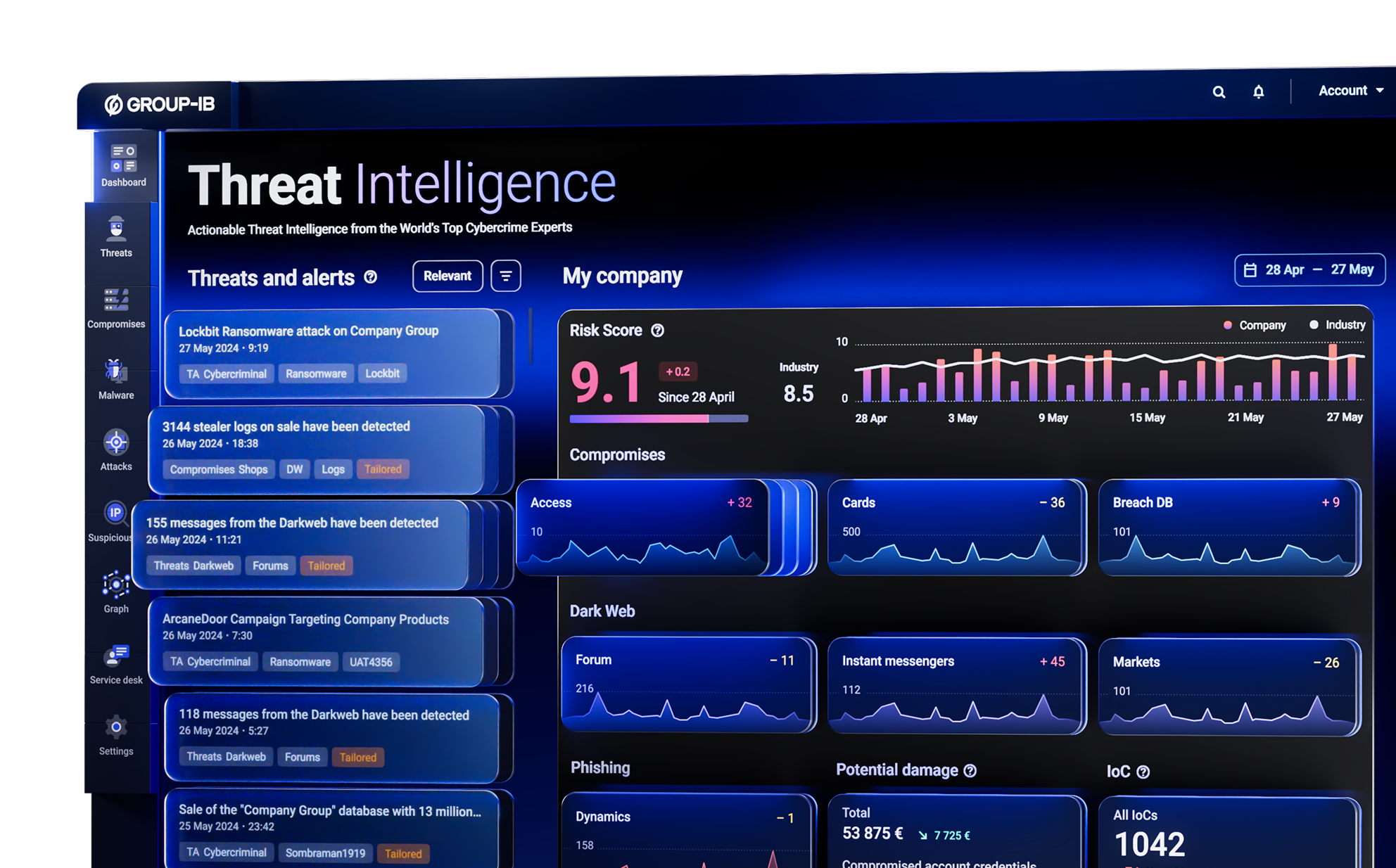
& Expertise
Intelligence

and Intelligence Infrastructure
Resistance Centers

Building intelligence-driven defense

Meeting compliance requirements

Justifying CTI investments

intelligence

IOC mapping

centric approach

and support


and prioritisation


24x7 threat intelligence
foundation

actionable insights, forecasts and recommendations
























