What is the Underground Cloud of Logs (UCL)?
For a relatively small fee, UCL services allow less-skilled threat actors to access confidential information, thus helping them skip the initial stages of an attack.
For the first time, UCL services were noticed in the second half of 2018 and since then their popularity has been growing every year. At the moment of writing, 103 UCLs were discovered during the investigation made with Group-IB Threat Intelligence tools. 33 of those clouds are actively operating and large flows of stolen data are transferred through them every day.
A combination of two interconnected factors has made UCLs a raging service nowadays:
- great amount of stolen data, gained by expanding hacking community,
- demand for simplicity coming from novices and beginners.
How is sensitive data shared on UCLs?
As the underground cloud of logs is an emerging means of buying and selling data in underground forums, all organizations are at risk of data exfiltration. Threat actors have private cloud-based platforms in which they host the cloud of logs. The logs are made available to the interested party through data analysis and extraction tools.
The underlying purpose of UCL is the implementation of a system that can facilitate the exchange of access to the logs for money. Telegram is the most convenient place where such deals can be made. This is the reason why Telegram became the main distribution platform for UCLs.
The difference between UCLs is in the quality of Telegram channel administration, the format in which logs are presented, and the update frequency. The most important features that UCL owners provide for their audience are authorization methods, automated payment tools, and advanced subscription plans, which can be set up with bots.
There are two ways of how logs are distributed:
- direct download archive file with logs from telegram channel,
- or link to some file sharing service, like mega-nz.
The average channel performs weekly new log uploads.
Types of data stored in the UCLs?
In computer science, a log file is defined as a file that stores records about events that occurred in an operating system or other software installed on a PC/device. The purpose of UCL users is to get specific information from these unsorted data arrays. Types of data made available are listed in the table below.
| Type of data | Malicious action | Services Examples |
| Accounts of corporate applications and VPN services | Initial access to the victim’s company network. | VPN-RDP, Citrix, GlobalProtect, Pulse Secure, Fortinet, RDWeb, Cisco, SonicWall |
| Crypto wallets, banking, and payment systems account | Money theft and fraud | PayPal and personal banking account information |
| Social media, marketplace, and gaming platforms accounts and IM sessions | Blackmailing and scamming | Amazon, eBay, BestBuy, and Steam |
As UCLs gain more prominence, the possibility of sensitive data being accessed by multiple threat actors to use it for nefarious purposes has increased significantly.
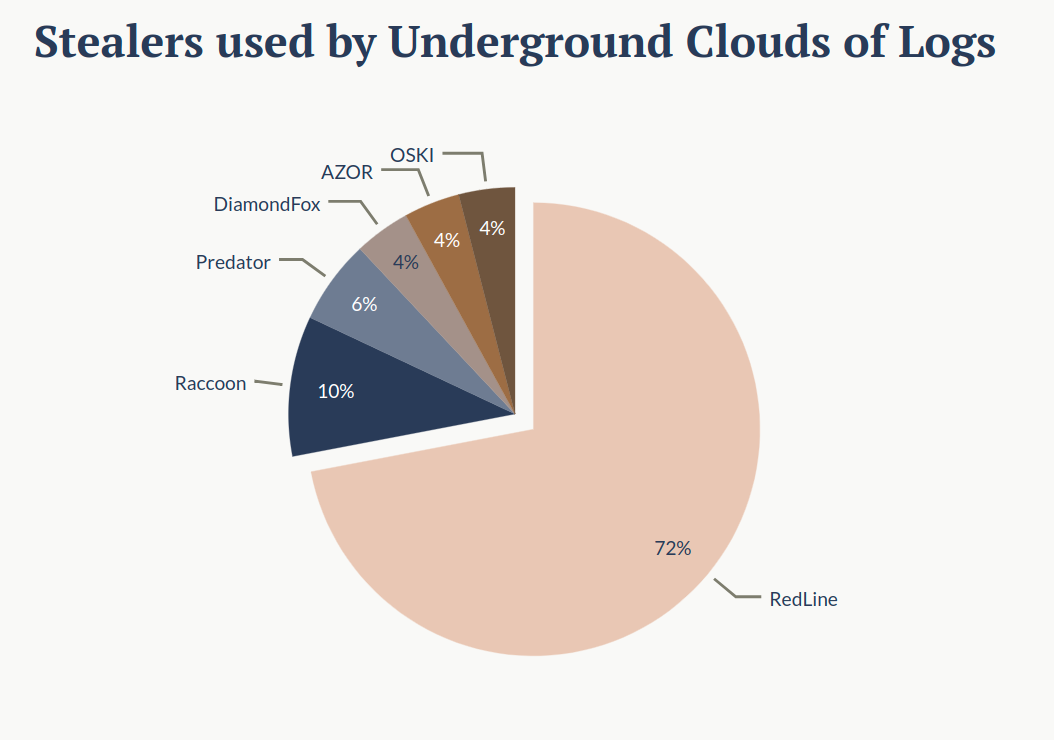
Sources of data in the UCLs: owners of the clouds of logs use all the available data that can be found on the dark web to expand their services. However, a dominant source for UCLs is the stealers.
A stealer is a type of Trojan software used for stealing sensitive data and making it accessible to the attacker through stealer logs. Sensitive information from the victim’s computer – visited domains, usernames, saved passwords, autofill forms, cookies and sometimes even files and desktop screenshots can be accessed through stealer logs.
The popularity of stealers among UCLs
What are the UCLs used for?
Credentials for crypto wallets and bank accounts are the most sensitive form of data obtained from logs. Even if multi-factor authentication acts as a defense wall in protecting bank account credentials, there isn’t a stern defense system in place for crypto wallet credentials.
Complex data made available in the UCLs are access to corporate accounts and VPN services. The scale of UCL development provides ransomware gangs with a real possibility to just buy access to clouds of logs and get credentials of organizations they want to exploit instead of trying to steal them on their own.
Other types of credentials, such as social networks and gaming platforms accounts can also be made available in the UCLs, which can be used for account promotion or scum purposes. However, such data is rarely of any interest to skilled hackers.
UCLs: Marketing gimmicks and raging prices
UCL owners are increasingly leveraging it as a monetization model for great gains. At times, the data sold holds little to no value as UCL owners buy logs from resellers and build clouds around them to sell out-of-date logs again.
Such manipulations become possible due to the low average level of technical knowledge among the target audience of UCL users. It mostly consists of young, incompetent, low-level cybercriminals. Threat actors who buy access to these datasets also vary in their specializations. This is also reflected in the marketing campaigns that some of the cloud owners advertise, loosely naming their clouds such as WALL STREET CLOUD, Wayne Cloud, Peaky Blinders Cloud, PerseCloud, etc.
Despite that, stealing information as massively as UCLs owners do, requires infrastructure: malware, servers, phishing pages, user traffic, etc. Sustaining it costs a lot of resources. The threat intelligence community needs to understand the danger that UCLs possess and develop means to control them.
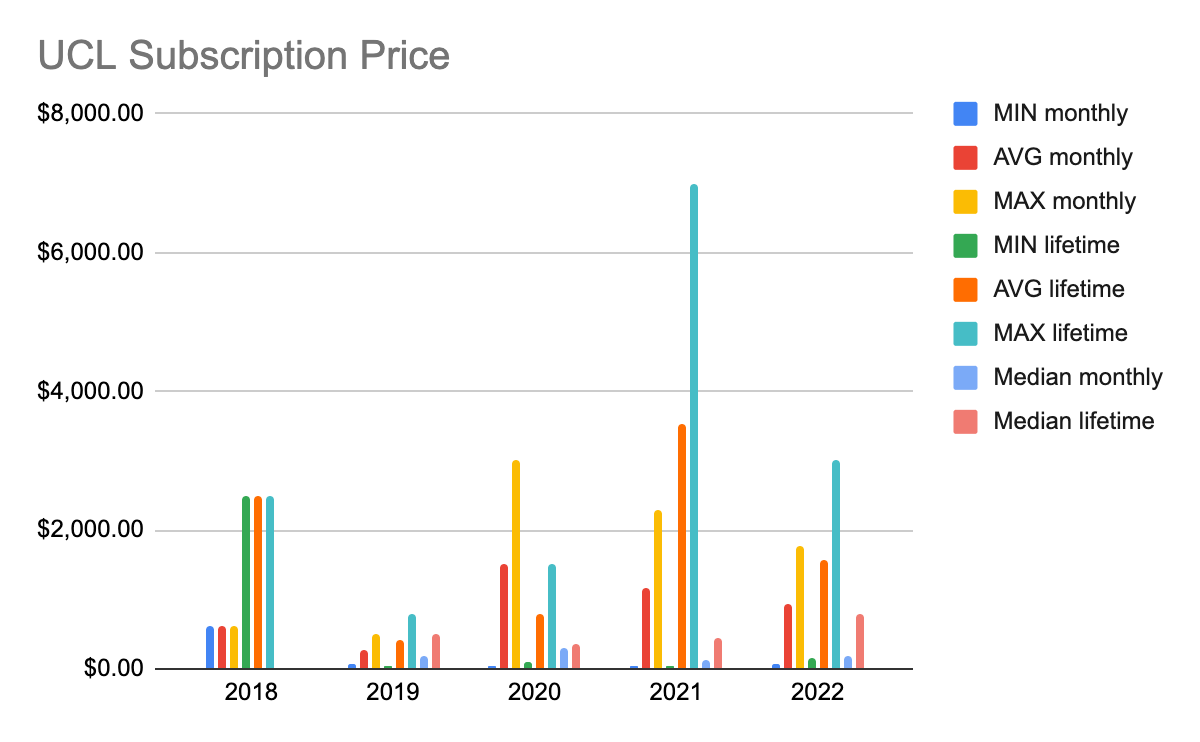
Prices for UCLs: to understand clouds of logs market trends, here’s a comparison of prices for subscriptions on access to UCLs (starting from 2018):
In the chart below, one can see the percentage of specific stealers predominantly used by cloud owners –
How can Group-IB help organizations protect their data?
As the underground business of selling access to the cloud of logs grows, organizations are at a higher risk of intrusions into their networks and data compromises for further attacks. Therefore, an early defense is the best offense. Group-IB’s Threat Intelligence helps organizations gain proactive and real-time visibility into their compromised accounts, to further enable protection.
The platform constantly monitors the dark web and underground forums for leaked credentials and once found, relevant takedown measures are taken. The Group-IB Threat Intelligence platform also offers convenient tools for investigating vast infrastructures and pinpointing bottlenecks of companies’ security systems:
- Searching through all possible Trojan implementations and finding IoC and TTS of real attacks in a matter of minutes and without any risk.
- Monitoring up-to-date reports about the latest attacks presented in the business industry.
Learn more about Group-IB’s proprietary Threat Intelligence here.