Many websites, search engines, and online platforms track users’ online activity using methods such as cookies, IP address tracking, or browser fingerprinting. This valuable data makes up your unique digital profile, which may be used to show targeted ads or sold to third parties for various purposes. However, legitimate resources, such as online retailers and banks, rely on such information to red-flag transactions from unauthorized accounts or browsers known for suspicious or fraudulent activity.
In this article, we discuss a tool called antidetect browser, which is designed to bypass such browser fingerprinting. We’ll explore the techniques used by antidetect browsers, examine both their legitimate use cases and how cybercriminals exploit them for fraud as well as how organizations can fight against the illegal use of antidetect browsers.
What is an antidetect browser?
An antidetect browser (or an anti-detection browser) is a tool based on popular web browsers (often based on Chromium or Firefox) designed to conceal a user’s actual digital identity, making it almost impossible for websites to track and monitor you.
These specialized web browsers can be used to manipulate various browser fingerprint attributes such as mimicking devices, operating systems, plugins, time zones, locations, and more. Users can also create custom digital profiles, each with a unique fingerprint that is hard to link, offering multiple identities.
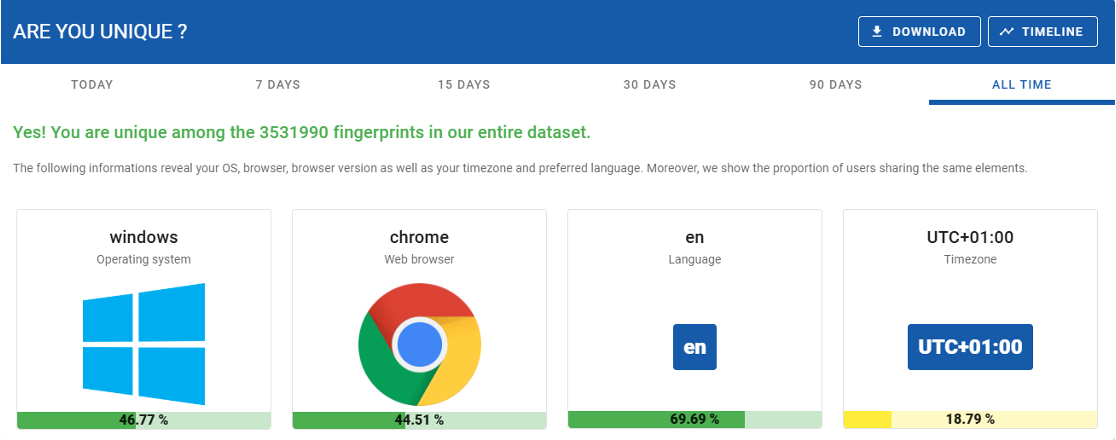
An example of browser fingerprint:
Antidetect browsers are used by both individuals and organizations. Digital marketing teams, SMM agencies, journalists, and cybersecurity professionals use them to manage multiple social media accounts or e-commerce profiles, safely share browser profiles with team members, access restricted websites, and more.
Even though the best antidetect browsers apps are advertised as innocent tools designed to help keep your privacy and (ironically) as a way to protect against cybercriminals, fraudsters can also benefit from them.
Banks, e-commerce sites, and other platforms typically monitor a user’s unique browser profile (their “fingerprint”) to spot suspicious behavior or unauthorized logins. Antidetect browsers undermine these defenses by altering that fingerprint, allowing threat actors to slip under the radar of anti-fraud systems. This means fraudsters can impersonate legitimate users or juggle dozens of accounts and avoid being detected by conventional device fingerprinting tools – a challenge for businesses working to prevent online fraud.
These tools also have legitimate applications (which we’ll discuss later). However, their ability to bypass ordinary tracking and fraud checks has made them a popular tool among fraudsters. Cybercriminals also develop proprietary antidetect browsers that are sold on the the dark web.
How do antidetect browsers work?
Antidetect browsers operate by intercepting and modifying the data that a normal browser would share with websites via JavaScript and other APIs. Antidetect browsers insert a layer that catches these queries and returns fake values in place of the real ones.
Here’s a breakdown of the techniques used by antidetect browsers:
- IP Address Spoofing
- Simply changing browser fingerprints isn’t enough if all activity originates from the same IP.
- Antidetect browsers route traffic through proxies, VPNs, or Tor to assign each browsing profile a different IP.
- Example: A user may assign one profile a U.S.-based residential proxy, while another appears to be from Europe or Asia.
- Profile Isolation (Multi-Account Management)
- Each browser profile acts as a separate digital identity with isolated cookies, cache, and local storage.
- Prevents tracking systems from linking multiple accounts to the same user.
- Example: Users can operate multiple accounts on the same platform (Facebook, Amazon, LinkedIn, Ebay or Gmail) without triggering suspicion checks.
- Cookie Management (Session Spoofing)
- Websites track users using cookies stored in the browser.
- Antidetect browsers store cookies separately for each profile, preventing cross-account detection.
- Fraudsters can import stolen cookies from breached accounts, allowing them to resume someone else’s session without logging in.
- Canvas Fingerprinting
- Websites use canvas fingerprinting to detect users by how their browser renders graphics.
- Antidetect browsers can randomly modify canvas outputs, preventing tracking systems from recognizing unique patterns.
- If a website uses canvas rendering to check a visitor’s device, an antidetect browser feeds back altered data to break tracking.
- WebRTC IP Leak Prevention
- WebRTC (Web Real-Time Communication) can expose a user’s true IP address, even when using a VPN or proxy.
- Antidetect browsers disable or spoof WebRTC leaks, ensuring a user’s real IP address never gets revealed.
- A cybercriminal using a VPN or proxy to appear from London could be exposed if WebRTC leaks their real IP from Russia.
- Modifying HTTP Headers & Requests
- Websites examine HTTP headers and request order to identify bot-like behavior.
- Antidetect browsers shuffle HTTP request sequences and modify headers to appear as a legitimate user.
- Fraudsters can imitate user traffic patterns, making bot activity harder to detect.
- Using Different Browser Profiles (Fingerprint Rotation)
- Some antidetect browsers allow users to rotate through multiple pre-configured fingerprints dynamically.
- This ensures that even if one identity is flagged, the next session appears as a completely different user.
- Users might cycle through ten different fingerprints per session, each appearing as a new, unrelated device.
Legitimate uses of antidetect browsers
Here are a few industries and scenarios where antidetect browsers serve a practical, legitimate purpose:
- Digital Marketing and Advertising: Marketing and advertising professionals often need to manage multiple accounts on Google, Facebook, or Instagram. These platforms usually limit one account per browser or enforce strict anti-multi-account policies. Antidetect browsers allow social media managers to run numerous client accounts or ad campaigns from one machine without getting flagged.
- E-commerce and Retail Management: Sellers on e-commerce marketplaces might use antidetect browsers to handle multiple storefronts or user accounts. This can be useful for legitimate reasons such as testing how their product listings appear to users in different regions (by switching profiles with different locations), or managing separate buyer accounts for market research. Web scraping for price comparisons can also be done more safely with antidetect browsers to avoid being blocked.
- Cybersecurity Testing and Research: Cybersecurity professionals and fraud analysts use antidetect browsers to simulate a fraudster’s behavior in a controlled environment. Penetration testers or red teamers might use these browsers to evade detection during an engagement when testing the resilience of a client’s fraud detection mechanisms. Researchers investigating the dark web and underground forums also use antidetect setups to protect their identity.
Privacy-conscious users, journalists, or activists often choose to use antidetect browsers to avoid invasive tracking or bypass online censorship. A journalist might use an antidetect browser to maintain separate online personas for sensitive investigations to avoid linking their research activities back to their real identity.
In these legitimate cases, the common theme is multi-account management and anonymity. The goal is to avoid linking or tracking, but not to commit fraud. Unfortunately, the same capabilities that benefit these use cases are exactly what attract cybercriminals.
How fraudsters leverage antidetect browsers
Threat actors combine the functionality of antidetect browsers with stolen credentials or banking details as a way to access compromised social media, email, or bank accounts without being detected by anti-fraud solutions.
Anti-detection apps enable threat actors to spoof dozens of web browser and hardware configurations (e.g., WebGL, Canvas, resolution, fonts, geolocation, IPs, browsing habits) in real time and create numerous profiles to mimic legitimate user behavior. Furthermore, some antidetect browsers can automate specific tasks or simulate human-like browsing behavior such as typing. Another function is collecting cookies on websites, which anti-fraud solutions identify as an attribute of an old and legitimate device.
Here’s how fraudsters use antidetect browsers against websites in various industries:
E-commerce
- Account Takeover (ATO): Threat actors use stolen credentials to access accounts, change shipping information, and make fraudulent purchases.
- Carding: Threat actors test stolen bank card information to make small purchases without attracting attention to themselves.
- Creating Fake Accounts: Threat actors set up many accounts to abuse promotional offers, leave bogus reviews, or resell limited-edition goods.
Gambling
- Bonus Abuse: Cybercriminals take advantage of sign-up offers or promotions across multiple accounts to “make” more money than legitimate users.
- Affiliate Fraud: Threat actors inflate referral traffic or conversions using numerous fake profiles that appear genuine.
- Match-Fixing: Fraudsters distribute bets based on fixed/rigged outcomes across dozens of accounts (each on different fingerprints) and cashes out a large combined reward.
Financial institutions
- Account Creation: Threat actors open fraudulent accounts for the purpose of laundering money or receiving funds transferred from compromised accounts.
- Fake Loan Applications: Fraudsters apply for loans and disappear with the money using fabricated identities created with antidetect browsers.
- Banking Session Hijacking: Fraudsters load stolen banking session cookies into antidetect browsers to replicate the victim’s device fingerprint and IP, then execute unauthorized transactions without detection.
How Group-IB Fraud Protection fights against the illegal use of antidetect browsers
Group-IB Fraud Protection team has been actively studying and countering antidetect browser techniques to help businesses stay a step ahead. Through a combination of fraud intelligence, device fingerprinting, and behavioral analysis, Group-IB provides tools to detect when a supposedly “legitimate” user is actually coming from an antidetect browser environment.
Here’s how our anti-fraud solution works:
- Group-IB Fraud Protection analysts reverse-engineer fraudulent antidetect browsers to identify their patterns and techniques. With this information in hand, we are able to unmask illegitimate traffic from antidetect browsers and protect our customers against them.
- Group-IB Fraud Protection’s Anomaly Detection feature examines browser fingerprints to detect any inconsistencies or unusual patterns that could indicate manipulation by an antidetect browser. This approach relies on data analysis and involves comparing fingerprints against known “normal” profiles.
- Group-IB’s Web Snippet (a code injected into the website) is used to force antidetect browsers to reveal the noise. It monitors multiple, varying Canvas fingerprints and identifies different types of noise, including dynamic, static, and text-based.
- Group-IB Fraud Protection also uses IP intelligence, scoring, VPN, and private and public proxy detection data to find out whether parts of various device fingerprints were spoofed or generated and what types of fraud tools were used.
As attested by Frost & Sullivan, Group-IB Fraud Protection platform is recognized as a leading anti-fraud solution within the industry. Our solution stands out from other offerings by being the only anti-fraud solution to contain all key functionalities, including bot detection, behavioral biometrics, explainable AI, and API security.
Learn more about how your organization can use Group-IB’s Fraud Protection to effectively combat advanced digital fraud.