Introduction
Electronic payments surely bring convenient, time-saving, and seamless transactions, but what one might see as a three-click simple process involves a whole other level of complex infrastructure to make one transaction happen. It is a multi-component process involving website/ application interfaces, payment gateways, processors, and networks behind the scenes – each can have exposures that cybercriminals could exploit, putting your businesses’ and your customers’ faith in the entire system to the test.
This emphasizes the importance of maintaining robust security measures across all e-payment and financial services, starting from the first line of infrastructure code, especially when cyber adversaries are increasingly motivated to exploit any vulnerabilities for potential intrusions and attacks.
It is standard practice to segregate development and testing environments from production ones. In the case of Fawry, this isolation was even physical due to its high-security, high-reliability systems. However, despite that, cybercriminals might still find ways to intrude into your testing environment, potentially causing disruptions.
Such was an impasse experienced by Egypt’s largest e-payment service provider – Fawry. LockBit (2023’s most prominent ransomware-as-a- service group with 1,079 posts on its DLS (24% of the annual total as per Hi-Tech Crime Trends Report 23/24) tapped into their data inventory to exfiltrate information, encrypt files, and demand ransom.
Beyond mitigating the crisis, there were associated situational challenges. As a $2 billion company, Fawry was extra cautious in ensuring unhindered and continued operations. Group-IB not only assisted Fawry in navigating through this difficult period but also provided tangible support in helping the company gauge the crisis deeply and share credible communication about its impact on its extensive user base.
Comprehensive investigation and analysis of Fawry’s cybersecurity infrastructure
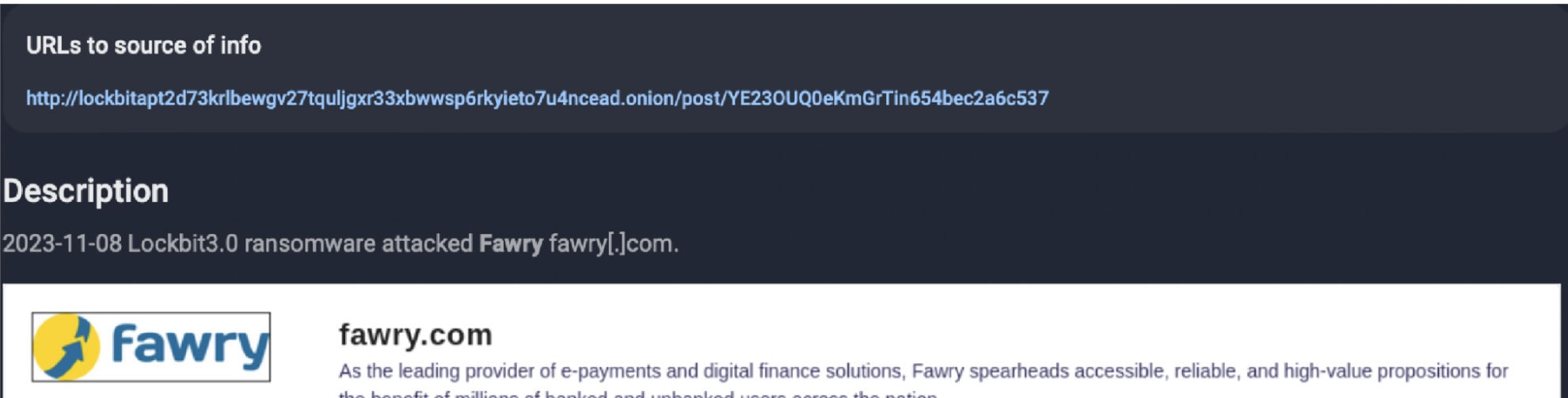
The investigation and threat interdiction began after a post was published on the Lockbit threat cluster on their Data Leak Site (hereinafter – DLS) on November 8th, 2023.