High-Tech Crime
Trends Report 2025
Available in English, Spanish, German, Italian, French, Arabic languages

Introduction
In 2025, the world of cybercrime continues to evolve at an unprecedented pace. Group-IB’s annual report delves into the most critical high-tech crime trends, offering a comprehensive analysis of emerging threats, tactics, and their impact on global security.
Welcome Video


The Group-IB Annual High-Tech
Crime Trends Report 2025
Crime Trends Report 2025
About this Report
Advanced Persistent Threats
Top targets:
Government
Manufacturing
Financial services
Trend:
Geopolitical conflicts drive attack spikes.
Geopolitical conflicts drive attack spikes.
15.5%
4.8%
3.8%
APT activity
surged by
surged by
58%
Dark Web
& Data Breaches
& Data Breaches
Corporate access sales increased by 15%
6.4 billion
records leaked in 2024
Phishing
& Scams
& Scams
Top targets: Logistics, travel, internet services, finance, and telecom
80,000+

22%
phishing websites
detected in 2024
detected in 2024
200,000+

22%
fraudulent resources
uncovered
uncovered

Hacktivism
Main targets:
India
Ukraine
Israel
300+
hacktivist groups launched
cyberattacks
hacktivist groups launched
cyberattacks
AI-Powered
Cyberattacks
Cyberattacks
Telegram deepfake
services up 40%
services up 40%
Ransomware
& Data Leaks
& Data Leaks
Ransomware attacks increased by 10%
5,000
attacks published on Dedicated Leak Sites (DLS) in 2024
Key Cyber Threats
01
Advanced Persistent Threats
State-sponsored attackers exploit geopolitical tensions to infiltrate government, finance, IT, and manufacturing sectors, seeking strategic and economic advantages.

02
Hacktivism
Politically motivated cyberattacks escalate, targeting nations involved in geopolitical conflicts, with India, Israel, and Ukraine being primary hotspots.

03
Data Leaks
Massive data breaches expose billions of user records, including emails, passwords, and phone numbers, fueling cybercrime and identity theft.

04
Scams
Online fraud skyrockets, with cybercriminals exploiting high-demand sectors like travel, logistics, and finance through sophisticated scam schemes.

05
Phishing
Phishing attacks surge, with fake websites and deceptive messages targeting industries like logistics, travel, and internet services.

06
Ransomware and Dedicated Leak Sites
Ransomware operations continue to expand, fueled by underground markets offering Ransomware-as-a-Service (RaaS) and leak sites exposing stolen data.

07
Initial Access Brokers
Cybercriminals sell unauthorized access to corporate networks, enabling data theft, espionage, and large-scale cyberattacks across multiple regions.

08
Compromised Hosts
Stolen credentials from infected devices provide cybercriminals with backdoor access to corporate systems, facilitating ransomware, APT campaigns, and fraud.

Advanced
Persistent Threats

Introduction
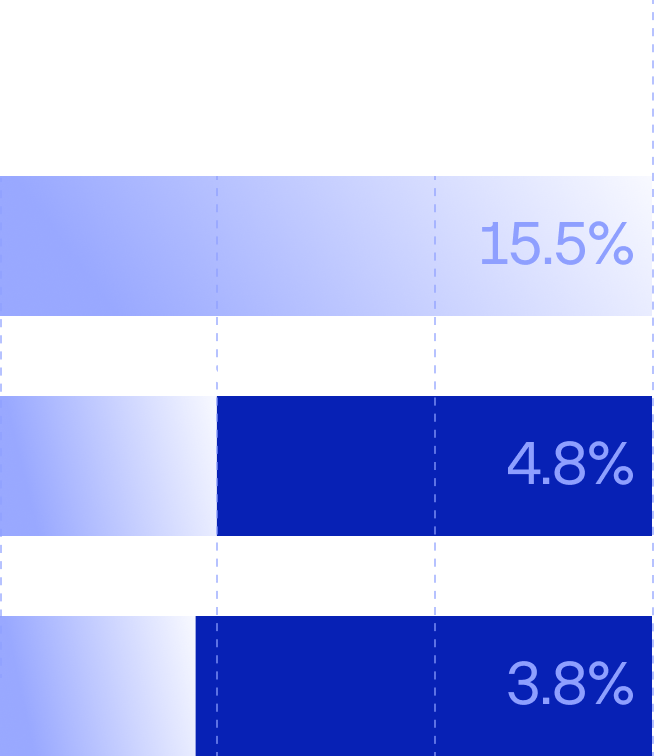
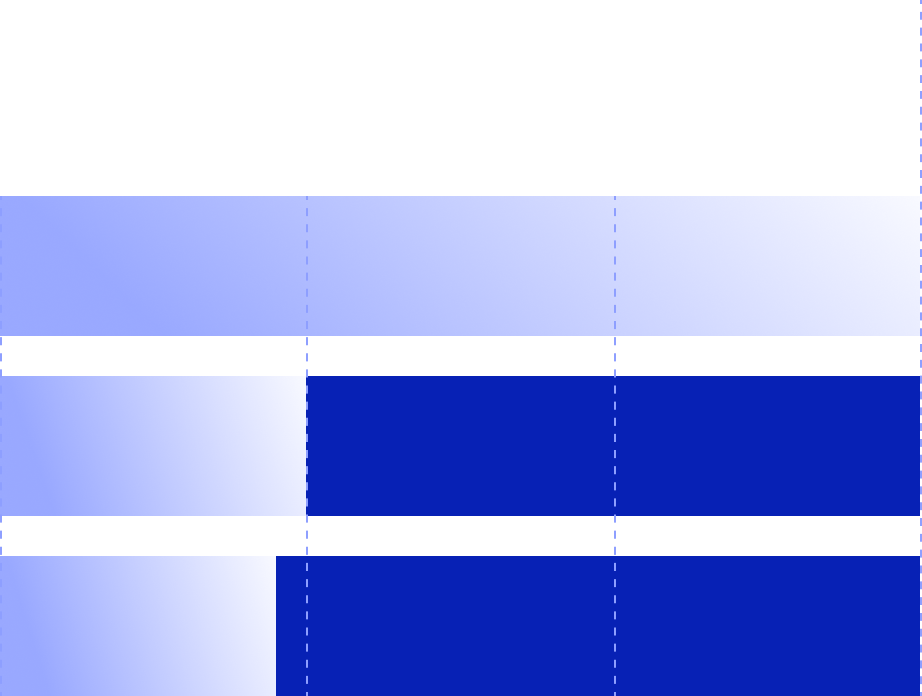
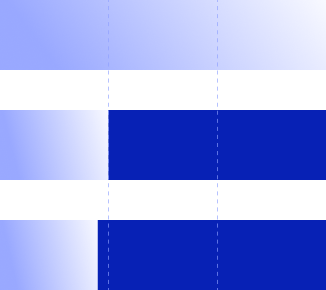
In 2024, Group-IB's Threat Intelligence team detected 828 APT cyberattacks, a 58% rise from 2023, driven by geopolitical conflicts in Europe and the Middle East. State-sponsored actors targeted government (15.5%), manufacturing (4.8%), finance (3.8%), IT (3.5%), and science (2.3%) sectors for strategic, economic, and technological advantages.
Global: Distribution of cyberattacks conducted
by APTs by region in 2024
by APTs by region in 2024
Global: Top jurisdictions targeted by APTs in
2024
2024
Global: Top 10 industries targeted by APTs in
2024
2024
Hacktivism

Introduction
Hacktivist groups, driven by political agendas, target nations involved in conflicts like Israel-Palestine and Russia-Ukraine, as well as their allies. India has become a prime target due to regional tensions and its ties with Israel, facing attacks from pro-Palestinian groups while Indian hacktivists retaliate against pro-Palestinian organizations.
Global: Distribution of hacktivist attacks by
region in 2024
region in 2024
Global: Top jurisdictions targeted by hacktivists
in 2024
in 2024
Global: Top 10 industries targeted by
hacktivists in 2024
hacktivists in 2024
Data Leaks

Introduction
In 2024, 1,107 instances of data leaks were detected globally, compromising over 6.4 billion user data strings. The leaked data, particularly email addresses, phone numbers, and passwords, poses significant risks as it can be exploited for various attacks. Of the leaked data, more than 6.5 billion entries included email addresses (2.5 billion unique), nearly 456 million leaks involved passwords (161 million unique), and over 3.3 billion entries contained phone numbers (631 million unique).
Global: Leaks by data type sold on the dark
web in 2024
web in 2024
Global: Top 10 jurisdictions with reported data
leaks in 2024
leaks in 2024
Global: Top 10 industries impacted by data
leaks in 2024
leaks in 2024
Scams

Introduction
In 2024, Group-IB detected over 200,000 fraudulent resources, a 22% rise from 2023. The travel industry was hit hardest, followed by energy, financial services, logistics, and telecoms. Scams like Classiscam targeted logistics, emphasizing sector vulnerabilities during peak demand periods.
Global: Top 10 industries where scam
resources were detected in 2024
resources were detected in 2024
Phishing

Introduction
In 2024, Group-IB detected over 80,000 phishing websites, a 22% increase from the previous year. The logistics, travel, and internet services sectors were the most targeted, accounting for 25.3%, 20.4%, and 16.4% of phishing websites, respectively.
Global: Top industries targeted by phishing
attacks in 2024
attacks in 2024
Ransomware
and Dedicated Leak
Sites

Introduction
Ransomware has become a global threat, evolving into a complex underground industry with Ransomware-as-a-Service (RaaS), leak sites, and initial access brokers. In 2024, Group-IB identified 39 RaaS ads and a 44% rise in affiliate offers. Dedicated leak sites saw 5,066 attacks, a 10% increase from 2023.
Global: Distribution of ransomware attacks by
region in 2024
region in 2024
Global: Top 10 ransomware groups by number
of attacks in 2024
of attacks in 2024
Global: Top industries targeted by ransomware
groups in 2024
groups in 2024
Initial Access
Brokers

Introduction
In 2024, Group-IB detected 3,055 instances of access for sale, a 15% increase from 2023. North America saw a significant rise of 43%, while Europe and Latin America saw increases of 32% and 41%, respectively. The Asia-Pacific and Middle East & Africa regions saw stable numbers. The top IAB sellers identified were SGL (146 instances), Kot Ucheniy (91), and sandocan (81).
Global: Instances of corporate access
detected and sold on the dark web by region in
2024
detected and sold on the dark web by region in
2024
Global: Top 10 jurisdictions targeted by initial
access brokers in 2024
access brokers in 2024
Compromised
Hosts

Introduction
In 2024, cybercriminals increasingly exploited Underground Clouds of Logs (UCLs) to gain access to compromised hosts, using stolen credentials from infected devices to infiltrate corporate networks. Information-stealer malware played a critical role, providing attackers with valid login data for internal systems, remote services, and cloud platforms. These compromised hosts became prime entry points for ransomware operations, APT campaigns, and large-scale fraud, reinforcing the need for stronger endpoint security and credential protection measures.
Global: Top 10 jurisdictions by number of
compromised hosts observed
compromised hosts observed
Global: Top 5 stealers by number of
compromised hosts in 2024
compromised hosts in 2024
Download
the entire report
the entire report

Download the entire report
Available in English, Spanish, German, Italian, French, Arabic languages.

Choose your language and download the report
























