Introduction
Phishing remains one of the most persistent and adaptive threats in cybersecurity. It is common and widespread for cybercriminals to impersonate reputable IT companies in phishing campaigns, exploiting the trust these brands have built and thus targeting both affected companies and their customers. What began as simple social engineering has matured into a complex criminal economy with defined roles, scalable tools, and rapid monetization. Through its continuous monitoring of underground ecosystems, Group-IB’s Threat Intelligence and Investigations team recently uncovered a sophisticated phishing framework that illustrates this evolution in striking detail.
The analyzed kit was engineered to impersonate the Italian IT and web services provider Aruba S.p.A., a company deeply embedded in Italy’s digital infrastructure and serving more than 5.4 million customers. Such a target offers significant payoff: compromising a single account can expose critical business assets, from hosted websites to domain controls and email environments.
Group-IB researchers dissected the phishing kit and found it to be more than a cloned web page — it is a fully automated, multi-stage platform designed for efficiency and stealth. It employs CAPTCHA filtering to evade security scans, pre-fills victim data to increase credibility, and uses Telegram bots to exfiltrate stolen credentials and payment information. Every function serves a single goal: industrial-scale credential theft.
This discovery highlights a broader trend in the underground economy — the rise of phishing-as-a-service (PhaaS). These kits are built, sold, and even supported like legitimate software products. Their availability drastically lowers the technical barrier to entry, enabling less skilled actors to launch convincing campaigns at scale. The automation observed in this particular kit exemplifies how phishing has become systematized — faster to deploy, harder to detect, and easier to replicate.
By tracing the kit’s architecture and Telegram infrastructure, Group-IB analysts have documented how today’s phishing operators mirror legitimate SaaS businesses in structure and scale. This industrialization transforms phishing from a series of isolated scams into a sustained, automated supply chain. Understanding this shift is crucial for defenders who must now contend not with individuals, but with an ecosystem that behaves like an agile enterprise.
Key discoveries
- Spear-phishing lures sent to Aruba customers, warning of expiring services or failed payments
- Pre-filled login URLs embedding the victim’s email address for realism
- The phishing kit is built for efficiency and evasion. It is a complete, multi-stage application designed to guide a victim through a full data harvesting process
- Telegram chats are used as exfiltration channels, used to exfiltrate the payment details data
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware and fraud protection analysts
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement and cybercrime units
Group-IB Threat Intelligence Portal:
Group-IB customers can access our Threat Intelligence portal for more information about phishing campaigns.
Attack Scheme Overview
The attack usually begins with a classic spear-phishing lure. Victims receive an email designed to create a sense of urgency, such as a warning about an expiring service or a failed payment—tactics that Aruba itself warns its customers about. The email contains a link to one of many phishing pages that meticulously mimic the official Aruba.it webmail login portal.
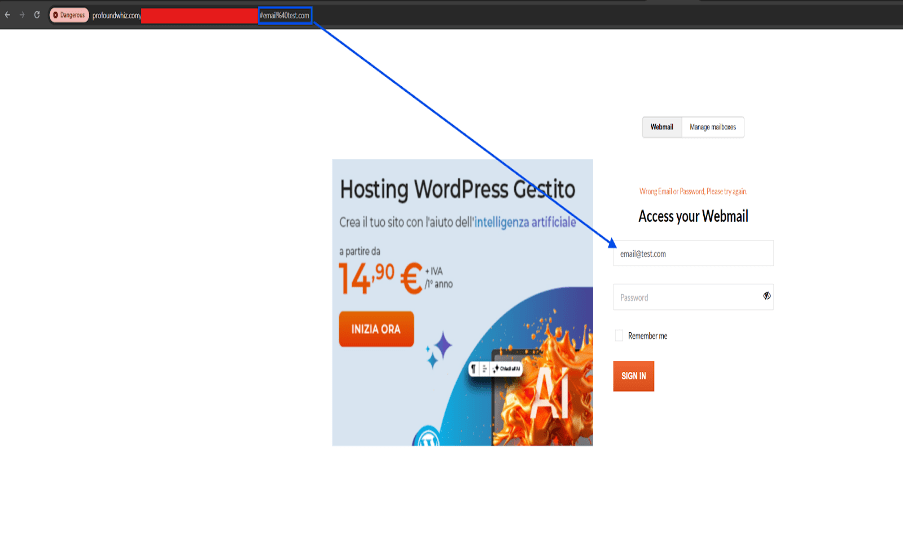
The phishing page mimics the official Aruba.it webmail login portal.
The analysis of this particular phishing kit highlighted the use of pre-filled login URLs which include the victim’s email address as a parameter. When the victim clicks the link, the page loads up automatically populating the email field in the login form, creating a convincing illusion of legitimacy that lowers the user’s guard and makes them more likely to enter their sensitive data. Once the data is submitted, it is exfiltrated to the attacker and the victim is redirected to the legitimate Aruba.it website to minimize suspicion.
Furthermore, the phishing kit analysis uncovered a meticulously orchestrated four-stage process designed to systematically strip a victim of their credentials and financial data.
Stage 1: Evasion & Access
The attack sequence starts with a CAPTCHA challenge, which serves as the kit’s first line of defense. This filter is designed to weed out analysis by security bots and scanners, increasing the likelihood that the malicious page is only delivered to a human target.
Stage 2: Credential Theft.
After solving the CAPTCHA, the victim is redirected to a high-fidelity replica of the Aruba.it customer login page. The victim enters their username and password, which are immediately exfiltrated to the attacker.
Stage 3: Financial Data Harvesting
To lower suspicion, the victim is then presented with a fake payment page for a small, plausible fee (e.g., €4.37), often under the pretext of a service renewal or validation. This page is designed to steal the victim’s full credit card details: name, card number, expiration date, and CVV.
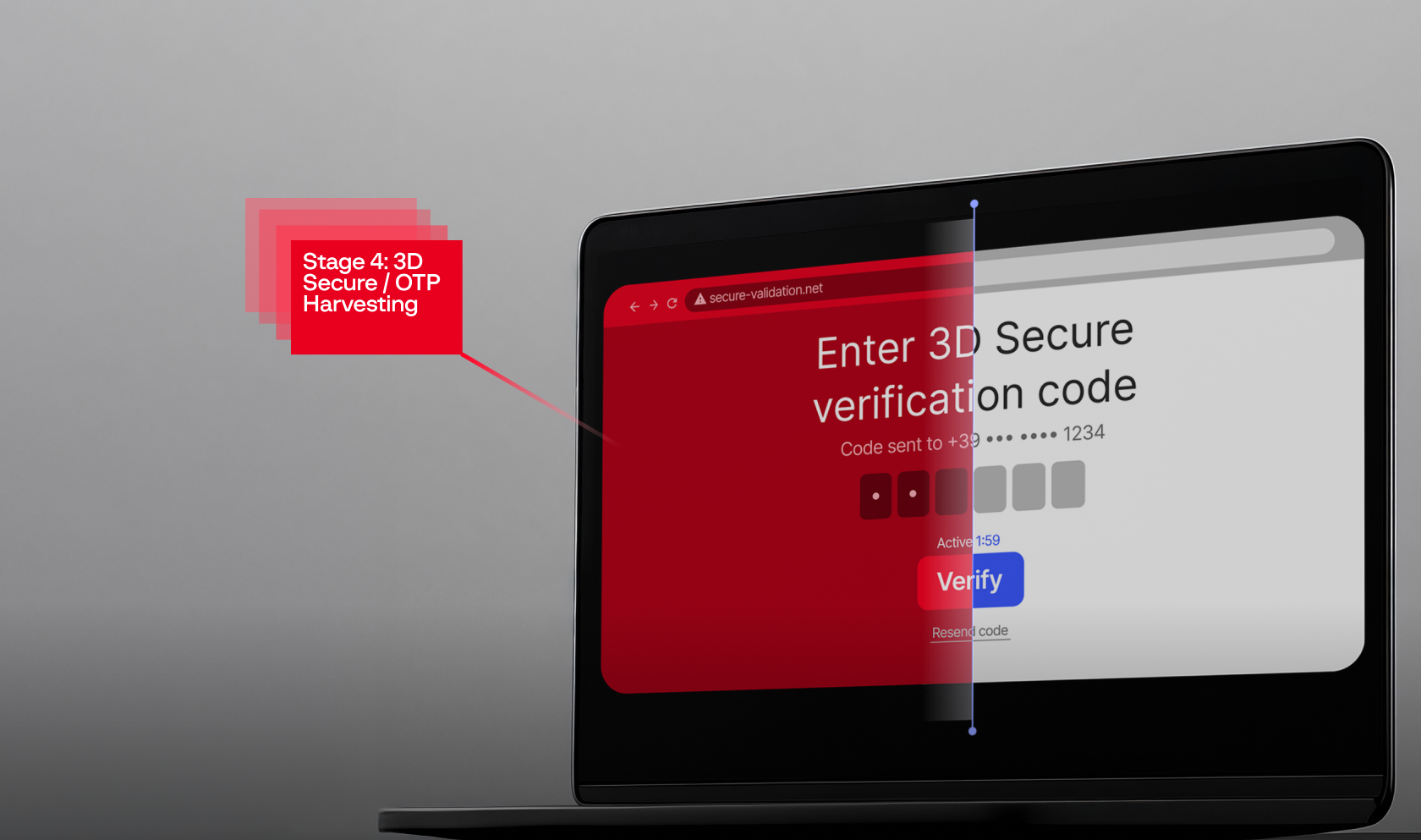
Stage 4: 3D Secure / OTP Harvesting
Immediately after submitting their card details, the victim is taken to a fake 3D Secure / OTP verification page. The page prompts them to enter the one-time password sent to their phone by their bank. This final piece of information is captured and sent to the attacker, giving them everything needed to authorize fraudulent transactions in real-time. The victim is then redirected to a loading screen before being sent to the legitimate Aruba.it website, leaving them unaware of the theft.
Analysis of the Phishing Kit
The phishing kit is a comprehensive framework built for efficiency and evasion. Rather than being a single page, it is a complete, multi-stage application designed to guide a victim through a full data harvesting process.
The process begins with an anti-bot gateway that filters out automated security tools, ensuring the core phishing pages are only shown to potential human victims.
Once a user passes this check, they enter the main application, which contains separate, high-fidelity templates for each stage of the attack: the initial credential login, the financial data form, and the final OTP interception page.
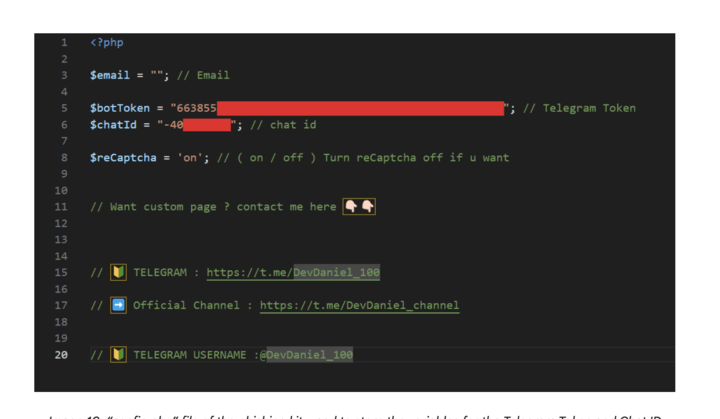
When a victim submits their information at any stage, the data is sent to the attacker through multiple channels simultaneously. The primary method is a direct message to a pre-configured Telegram chat, providing the attacker with instant notification. As a backup, the data is also saved on a local log file on the attacker’s machine running the kit.
Our analysis also uncovered a second Telegram exfiltration channel, hardcoded within the kit’s client-side code. This channel is apparently used to exfiltrate the payment details data, as the parameters are different from the one shown in the screen below. However, in case the exfiltration to this Telegram channel fails, the one shown below will be used as fallback or backup.
While there are kits targeting Aruba.it, which can both be rudimentary and more “supported”, they are part of a dangerous, layered criminal ecosystem that lowers the barrier to entry for phishing attacks.
The Telegram Ecosystem
Telegram is the central nervous system for this entire operation. As seen in many other cases, It functions as a full-service platform for cybercrime, often hosting every stage of the attack lifecycle. In the case of the kit analyzed, we were able to identify numerous Telegram chats dedicated to the Aruba campaign.
These Telegram entities are used for:
- Distribution and Sales: Announcing, promoting, and selling phishing kits. In the screenshot below, taken from our Threat Intelligence Platform, the kit analyzed in this article was distributed by the actual developer for free in at least one Telegram channel.
- Community and Support: Creating spaces for criminals to exchange tools, techniques, and support.
- Exfiltration bots: Using bots as endpoints for exfiltrated data. This method is stealthier than some other types of traditional infrastructures, as the traffic blends in with normal messaging activity.
Conclusion
The phishing kit analyzed by Group-IB exemplifies the industrialization of online deception. What once required technical expertise can now be executed at scale through pre-built, automated frameworks. These operations function like illicit SaaS businesses–modular, subscription-based, and supported through Telegram communities.
The evolution underscores a critical truth: phishing is no longer a static or low-skilled threat. It is a dynamic, market-driven ecosystem that continues to innovate. Each new kit accelerates the cycle of attack, lowering barriers to entry and expanding the global reach of cyber fraud.
Phishing may be one of the oldest forms of cybercrime, but in its current industrial form, it represents a new frontier of automation and deception – one that demands intelligence-driven, collaborative defense.
Recommendations
The multi-stage nature of this kit and its ability to intercept OTPs highlight the limitations of traditional security advice. A more robust, multi-layered defense — with both parties (organizations/service providers and end users) committed to security — is required to counter this threat.
For Organizations and Service Providers
- Implement technological solutions like a Secure Email Gateway (SEG) to filter malicious content and inspect URLs. Enforce email authentication standards like SPF, DKIM, and DMARC.
- Actively monitor for impersonating domains and phishing sites, proactively requesting their takedown. Provide a dedicated page for users to report abuse.
- Use a zero-trust approach to make sure that any connection is not taken for granted. Always double check everything and continuously monitor all the traffic. Send notifications or request approval on multiple separate channels when any (critical) operation is requested. Make payments by redirecting to the banks’ official websites for multi-factor authentication/authorization (like 3DS or app verification, etc…) and do not host all on your infrastructure.
For End Users
- Be skeptical of any email that uses any social engineering techniques, like creating urgency or fear. Always verify the sender and hover over links to check the destination URL before clicking. Remember that an HTTPS lock icon does not guarantee a site is legitimate as a high number of phishing sites use it nowadays.
- If you receive a suspicious email from Providers, avoid using any links in it. Instead, open a new browser window and manually log in into your account. Look for new notifications or try to find the same information provided in the email (i.e. invoices to pay). Providers (as Aruba) are generally committed to supporting their customers by offering support through specific channels, such as dedicated website pages, and customer assistance services—through which users can obtain accurate information and report suspicious activities, including potential phishing attempts.
- Even though some phishing kits are capable of bypassing it, it is very important to enable multi-factor authentication on your critical accounts. Where available, prioritize passkeys over SMS or app-based OTPs to neutralize the threat of OTP theft. Use a password manager to ensure you have a unique, strong password for every site.
Indicators of Compromise (IOCs)
Network IOCs
| Domain | IP |
| serdegogozedeytid[.]bulkypay[.]xyz | 23[.]239[.]109[.]118 |
| serdegogozedeytidtelerstore[.]marina[.]am | 192[.]250[.]229[.]24 |
| scarecrow[.]metalseed[.]you2[.]pl | 109[.]95[.]159[.]70 |
| wordpress-1512889-5811853[.]cloudwaysapps[.]com | 45[.]77[.]157[.]140 |
| firsijdaeeuetevcbcsj[.]cfolks[.]pl | 185[.]208[.]164[.]121 |
| arb-app[.]nero-network[.]eu | 185[.]25[.]23[.]155 |
| srv229641[.]hoster-test[.]ru | 31[.]28[.]24[.]131 |
Telegram IOC’s