The increasing popularity of real estate frauds
Real estate scams are growing in popularity due to the trust people place in online listings and the urgency often involved in securing a home. With the expansion of digital platforms for property searches, users are overlooking essential verification steps in their rush to close a deal, making them easy targets.
Scammers usually target specific groups like expatriates or people relocating to new cities, as they tend to be less familiar with local practices and may skip critical background checks. The ease of online transactions, the anonymity provided by messaging apps, and the quick transfer of funds make it easier for fraudsters to exploit their victims.
According to Group-IB’s analysis, the median financial loss per case of this fraud scheme type in the Middle East is 3,064 USD. Given the average number of reports and the large user bases of financial institutions in the region, annual losses from such schemes could reach millions of dollars per institution. This emphasizes the critical importance of robust fraud prevention measures.
Similar trends are observed globally, including the U.S. In 2023, 54% of real estate professionals in the U.S. reported encountering at least one attempt of seller impersonation fraud in the past 6 months, with 77% noting an increase in similar cases. These findings highlight the global relevance of combating real estate scams and the growing need for stronger preventive measures.
How do real estate frauds work in the Middle East?
The analysis of components of any fraudulent scheme typically begins with a detailed review of complaints from defrauded clients. Below are examples of complaints from actual bank customers. Group-IB analysts investigate such complaints in collaboration with the anti-fraud departments of financial organizations to develop effective countermeasures.
Customer complaints: victims of real estate frauds
Example 1: A user discovered a rental advertisement on a well-known rental listing platform and reached out to the person who published the listing. After communication, the user receives a rental contract through the legitimate real estate (regulatory) platform. After transferring the initial payment, the scammer asked for additional funds but stopped responding when the user declined to pay more.
Example 2: A user contacted the fraudster through a well-known rental listing platform while searching for an apartment. Communication took place via WhatsApp, where the fraudster sent the location of the property. Then a user received a contract via the real estate platform. After agreeing to the contract, transferring the payment, and trying to move into the apartment, it became evident that the owner was someone else, revealing that it was a scam.
Group-IB’s Fraud Protection analysts researched how fraudsters operate to scam people and steal money.
Fraud workflow
As evident from the described complaints, this scheme involves different components such as Ad Platform, Rental Registration Platform, and Mule Bank Account.
Below are the definitions of each component, along with a step-by-step interaction diagram.
Victim: The person searching for a property to rent, who ultimately becomes the target of the fraud;
Fraudster: The scammer who creates fake property listings and manipulates victims to transfer money;
Ad Platform: A popular online platform where property listings are posted (can be local or international platforms);
Rental registration platform: The government system for documenting and managing rental agreements;
Mule Bank Account: A bank account used by the fraudster to receive and withdraw the stolen money.
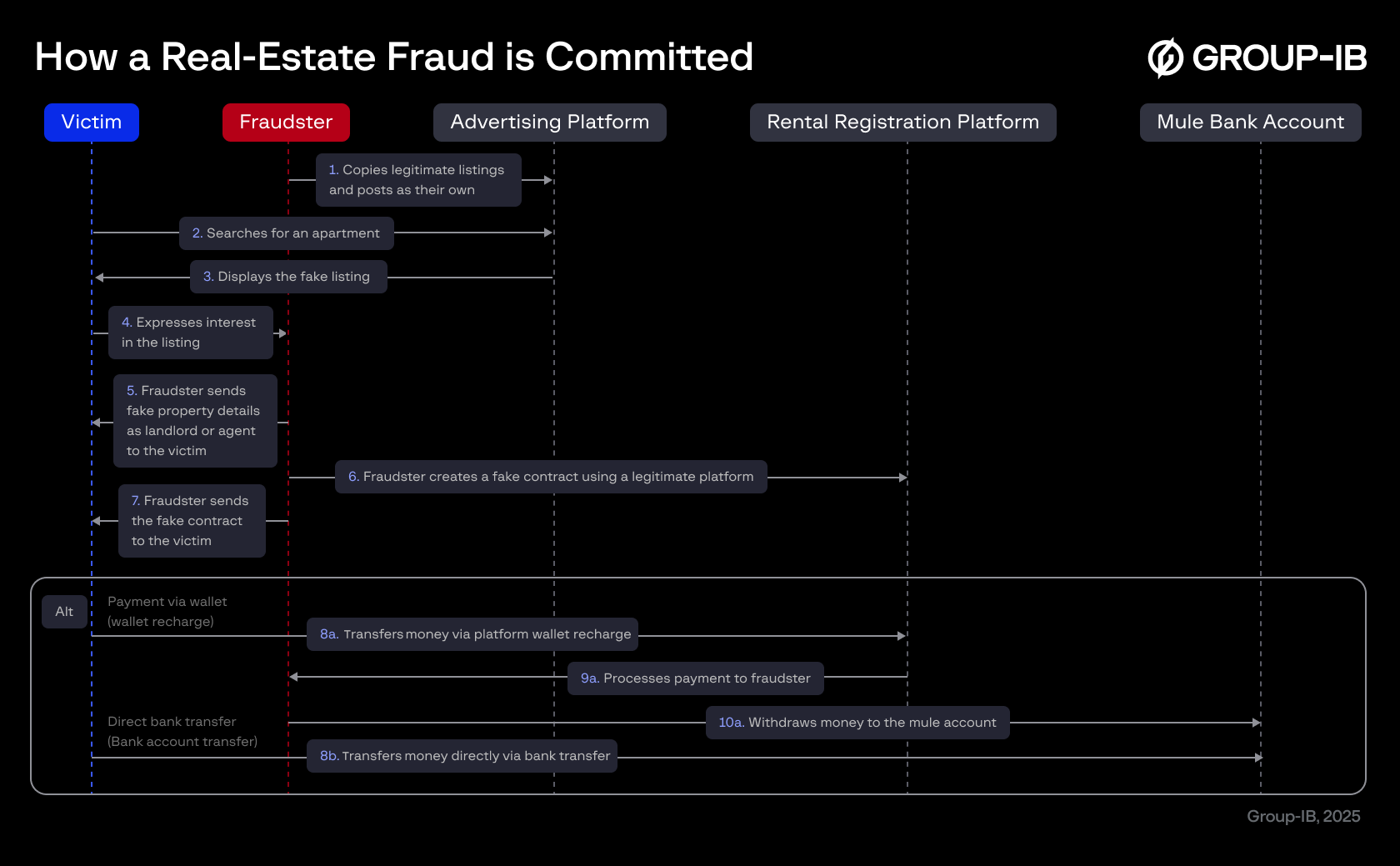
Figure 1. Flowchart of how fraudsters carry out a real-estate scam.
The scheme begins with the fraudster finding a suitable advertisement on a platform (most often related to apartment rentals), copying it, and publishing it under their name. The victim, finding the advertisement (typically offering better conditions than the market average), gets in touch with the fraudster. Communication can occur via the platform’s messenger or a third-party application (most commonly WhatsApp).
During the conversation, the fraudster persuades the victim of their reliability, sending additional photos (previously downloaded from the original advertisement) and providing a fabricated property agreement. A key step in the scheme is to create and send a rental contract using a legitimate platform (Step 6). This step involves a synthetically created or hacked account on the property registration platform and is a crucial factor in establishing trust with the victim.
Subsequent steps in the scheme are directly related to the victim making a payment. The scheme generally includes at least two of the most common scenarios:
- Replenishment of an electronic wallet linked to the fraudster’s account on the rental registration platform. This scenario is the safest for the fraudster, as funds are transferred to a mule account via an intermediary account (e-wallet belongs to the registration platform). This allows scammers to avoid immediate account suspension if suspicious activity is detected by the bank recipient or if the victim files a fraud complaint immediately, but it requires additional actions.
- Direct transfer to the mule account. This method is easier because it involves fewer steps but is riskier since the account is more likely to get blocked.
Based on the described steps and components, this scheme can be characterized as authorized push payment fraud with elements of impersonation. However, this definition does not fully reflect the scheme’s unique features. To provide a comprehensive description of fraudulent schemes using common techniques and tactics, Group-IB specialists apply a dedicated framework known as the Group-IB Fraud Matrix.
Fraud Matrix
Group-IB’s Fraud Matrix helps outline the specific tactics and techniques used during the execution of the scheme. For the current real estate scam, the configuration of the Fraud Matrix represents the following scheme.
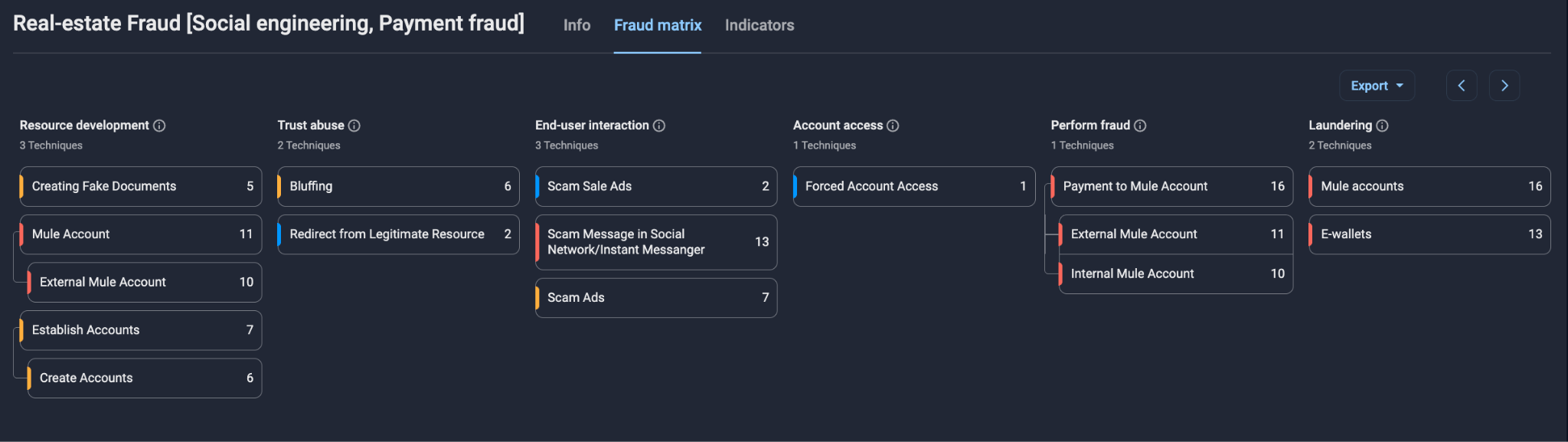
Figure 2. Group-IB’s Fraud Matrix outlining the tactics and techniques used during the execution of the scheme.
Since the described scheme relies on the victim’s actions on their device, it often bypasses traditional methods of detecting suspicious activity, such as identifying new devices, unusual locations, or irregular network behavior. Effective countermeasures should focus on analyzing and monitoring mule accounts to trace and block fraudulent activity, leveraging advanced tools.
Revealing mule networks in real estate scams
A money mule is someone who transfers or moves illegally acquired money on behalf of someone else. Criminals recruit money mules to help launder money they receive from online scams, fraud, and other crimes. Identifying mule networks is crucial for revealing fraud schemes and preventing further financial crimes. These networks facilitate the laundering and movement of stolen money from victims, making it more difficult to trace its origins.
Using the Fraud Protection solution, Group-IB analysts uncovered multiple mule networks across the Middle East. The solution leverages advanced tools to detect mule behavior by analyzing key indicators, such as:
- Technical Indicators: Identifying signs such as multiple accounts on the same device, using anonymization tools (e.g., VPNs, cloning apps, or GPS spoofing programs), activity originating from high-risk locations, and network analysis.
- Behavioral Indicators: Analyzing user behavior, including repeated activity patterns, unusual interaction sequences, and atypical ways of using an application or website.
- Relationship Indicators: Connections between accounts based on different technical parameters such as networks, locations, and unique device identifiers.
Thus, the identification of mule networks involves using various technical parameters. One of them is information about the device’s geolocation. In analytics, the geohashing method is often used for efficient geodata processing. The geohash method represents geographic locations as short strings, providing a quick and efficient way to compare nearby locations and identify clusters of suspicious activity.
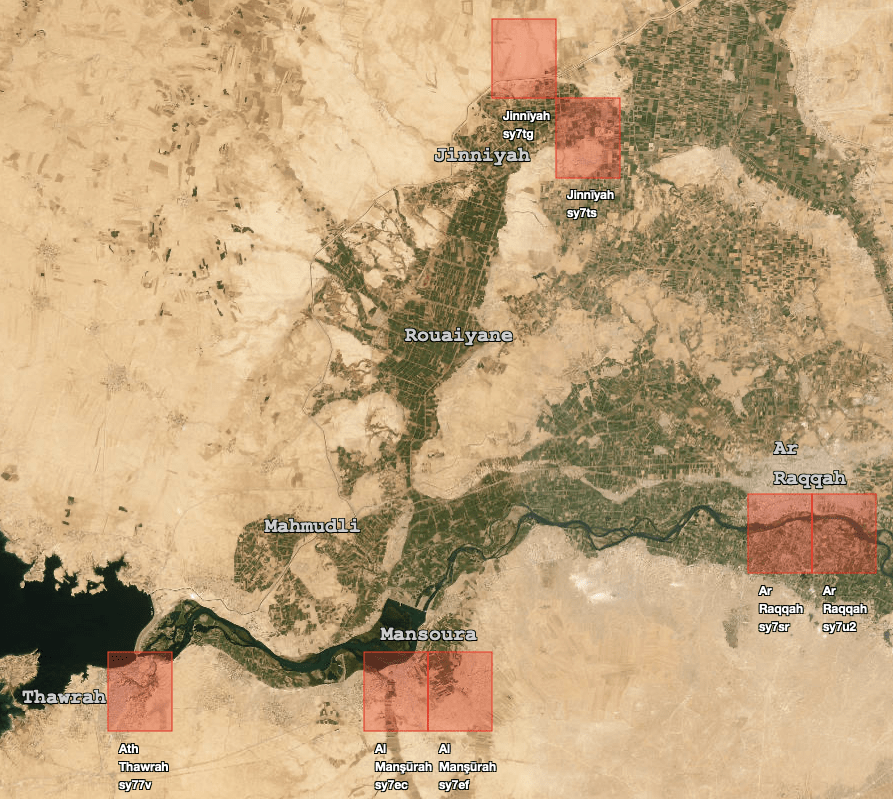
Figure 3. The map shows approximate locations in Syria where suspicious activities related to real estate scams have been identified.
In this blog, geohashes with a precision of 4.89 km x 4.89 km (precision level 5, e.g., sy7sr) are used for demonstration purposes. In analytical work, the utilized geohash precision varies depending on the task: some require exact coordinates with meter-level accuracy, while others focus on larger areas.
Activity from highlighted locations was traced to devices linked to mule accounts that received fraudulent funds from real estate scams. Additionally, suspicious activity in some identified areas was confirmed through customer complaints about account takeover schemes and further linked to suspicious hosting subnets originating from Iraq.
Close collaboration with financial institutions across the Middle East enabled Group-IB analysts to conduct cross-analyses, uncover potential networks, and facilitate intelligence sharing among clients.
This expertise empowers the Group-IB Fraud Protection team to quickly identify emerging fraud techniques and implement preventive measures to protect its clients from malicious activities.
Mule accounts used IP addresses associated with confirmed scammers. Although those addresses originate from legitimate Internet Service Providers (ISPs), listing them helped reveal a fraud network. IPs played a significant role in identifying other unconfirmed accounts that may be linked to fraudulent activities.
Suspicious IP addresses either originate from outside the country or belong to hosting services. As these IPs presented a serious threat, analysts extracted them for further investigation using Fraud Protection graph network analysis.
Fraud Protection graph network analysis shows the relationships between confirmed fraud accounts and other potentially malicious accounts through different parameters. The device type, number of nodes around a confirmed account, and distance of the nodes to the confirmed account determine the severity of the threat that each device/account signifies.
Devices directly related to a confirmed fraud account are blocklisted, and all other accounts associated with blocklisted devices are considered potential mules.
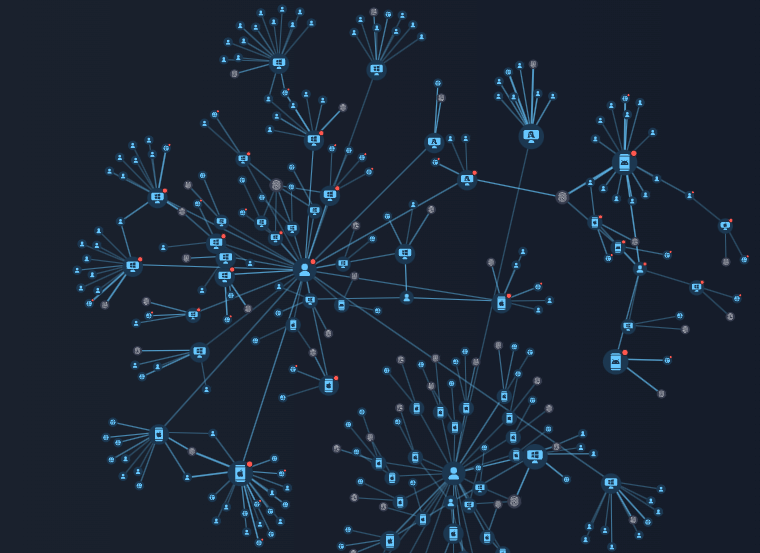
Figure 4. FP graph network analysis shows the relationships between the confirmed fraud accounts and other potentially malicious accounts through device links.
Graph network analysis enables effective disruption of fraud networks by identifying high-risk accounts and devices. By blocklisting confirmed connections and tracing associated accounts, the system proactively minimizes threats and strengthens fraud prevention efforts.
The analysis demonstrates that combating mule accounts is a complex challenge requiring a multi-faceted approach. Early detection and prevention at the account creation stage are critical to halting fraudulent activities before they escalate. Proactive relationship analysis reveals connections between suspicious accounts and devices, while geo and network analysis helps identify high-risk locations and suspicious traffic patterns. Behavioral pattern analysis, including repeated activity sequences and unusual usage of applications, adds an extra layer of protection.
Impact on organizations and individuals
Real estate scams significantly impact both organizations and individuals by exploiting trust and psychological manipulation. These schemes are designed to deceive people, targeting their trust and decision making.
For Group-IB Fraud Protection customers: Please access our Fraud Protection Intelligence portal for a more detailed report and tailored recommendations.
For individuals (end users):
- Financial losses
Victims often face significant financial losses from fraudulent schemes. Payments for rentals or deposits are typically unrecoverable once the scammer disappears or the fake agreement is exposed. - Identity theft
Beyond financial losses, fraudsters may collect sensitive personal information, such as copies of IDs or bank details, which can later be used in cybercrimes or sold on the black market.
For organizations (rental registration platform and financial institutions):
- Operational challenges
- Rental registration platforms: Exploiting legitimate systems to create fake rental contracts directly undermines the platform’s credibility and operational security. This also increases the workload on compliance teams, as every suspicious case requires investigation.
- Financial institutions: Mule accounts used to process stolen funds pose additional risks. Financial institutions must detect suspicious activities while managing the growing number of fraud-related cases.
- Reputation and trust
Fraud incidents associated with legitimate platforms undermine user trust. Perceived security lapses can lead to reputational risks, reduced customer confidence, and long-term credibility challenges. - Compliance implications
Although penalties and fines are rare, organizations may face increased regulatory scrutiny if fraud cases expose process gaps. This can lead to higher costs for auditing and strengthening existing systems.
Despite the challenges of detecting and preventing such schemes, many organizations in the Middle East are actively countering these cases. The key factor in combating these schemes is the implementation of strong fraud monitoring systems and building collaboration between stakeholders.
Recommendations
Recommendations for end users
- Verify property ownership
Before proceeding with any transaction, ensure that the person you are dealing with is the legitimate owner of the property. Request official ownership documents issued by the government and verify their authenticity. - Understand local procedures
Familiarize yourself with standard real estate processes, including identity verification, legal lease agreements, and common payment practices. This knowledge can help you identify warning signs, such as demands for upfront payments or unusual terms. - Visit the property in person
Whenever possible, inspect the property in person to validate its existence and ownership. Speaking with neighbors or local residents can also help verify the legitimacy of the property and its owner. - Avoid impulsive decisions
Fraudsters often manipulate victims using psychological tactics like the fear of missing out. Take time to conduct a proper investigation of the market before making any payments or commitments.
Recommendations for regulatory platforms and financial institutions
- Educate users on best security practices
Proactively educate users on safeguarding themselves from fraudulent activities. Address common risks, such as fake listings, account theft, and social engineering tactics. - Collaborate to enhance real estate fraud prevention
Financial institutions and real estate companies collect valuable intelligence from scam complaints and incident reports. Sharing this data—including fraud patterns, suspicious accounts or devices, and tactics—can greatly enhance security and fraud prevention efforts. For instance, Fraud Protection’s Global ID technology allows for the detection of fraudulent devices across various partner institutions, providing a collaborative and effective approach to dismantling fraudulent networks. - Monitor and analyze traffic
Fraudsters frequently use external platforms, like social media, to drive traffic to fake listings. Platforms should track URLs and referrer domains to identify fraudulent sources. - Implement advanced account and device monitoring
A robust monitoring system should include the following capabilities:- Device-based analysis: Track account creation patterns per device to detect multi-accounting.
- Behavioral analysis: Monitor unusual activity or dormant accounts linked to fraud.
- Account profiling: Analyze account age and activity frequency for inconsistencies.
- Blocklist integration: Maintain updated blocklists to prevent mule accounts from operating.
- Cross-platform intelligence: Leverage shared data across platforms to uncover larger fraud networks.
- Investigate fraud networks
Conduct a deeper analysis of accounts involved in fraudulent activities by:- Examining the relationships between accounts, devices, ISPs, and IPs.
- Identifying device characteristics and geolocations used in fraudulent schemes to build targeted counter-strategies.
- Tracking IP addresses and subnets associated with suspicious activity to block further threats.
- Prevent social engineering exploitation
Organizations should deploy systems capable of detecting active phone or video calls during user sessions, issuing warnings, or terminating suspicious interactions.