Introduction
Despite security measures implemented by telecom providers and regulatory bodies to prevent SIM swapping fraud, criminals continue to find new ways to exploit vulnerabilities. SIM swapping remains one of the most dangerous techniques in terms of its impact on victims. Such attacks not only lead to significant financial losses but can also result in the complete theft of personal data, accounts, and even unauthorized loan applications in the victim’s name.
In this blog, we’ll explore how this type of fraud persists in parts of the Middle East and what can be done to prevent it.
How SIM Swapping Fraud Happens?
SIM swapping fraud typically begins when the fraudster acquires sensitive information about the victim, such as their national ID, phone number, and card details. This information is often obtained through phishing websites that mimic legitimate services or via social engineering tactics.
Once armed with the necessary details, the fraudster initiates a request to swap or port out the victim’s SIM. This may involve converting the victim’s SIM to an eSIM with the same mobile network provider or porting the number to a different local telecom operator. These requests are often submitted through telecom provider mobile apps, enabling the process to be completed remotely.
In some regions, this process is safeguarded by a Government E-Verification Platform, which requires users to verify their identity before any SIM swap or port-out request is approved. Verification methods may include approving a login request or using biometric authentication.
To bypass these safeguards, fraudsters deceive victims into approving the verification request, often by posing as representatives of legitimate services—such as job applications or account updates. Once the victim unknowingly authorizes the request, the telecom provider deactivates the existing SIM and activates a new one under the fraudster’s control.
With control of the victim’s phone number, fraudsters can intercept SMS-based two-factor authentication (2FA) codes and carry out unauthorized transactions.
The following diagram (Figure 1) illustrates how a typical SIM swapping unfolds:

Figure 1: General scheme illustrating the SIM swapping fraud process.
Fraud cases and complaint description reports reveal three primary methods used in SIM swapping: phishing websites, social engineering, and hybrid approaches. Figure 2 shows the distribution of fraud cases by method, followed by timelines that showcase how each method was used in real-world scenarios, based on fraud case investigations gathered through Group-IB’s Fraud Protection system.

Figure 2: Distribution of SIM swapping fraud cases by method, along with real-world case timelines illustrating how phishing websites, social engineering, and hybrid approaches were used.
The Role of Phishing Websites in SIM Swapping Fraud
Phishing websites are the primary entry point for fraudsters in SIM swapping cases. These fraudulent sites closely mimic legitimate and reputable platforms, replicating its branding, design, and functionality to deceive victims into providing sensitive information.
Rather than creating random phishing sites, fraudsters exploit trends and high-demand services in a region. They analyze what users frequently search for and craft convincing fake websites to maximize engagement. Key industries targeted include:
- Car-Related Services – Fake platforms for vehicle inspections, insurance, and auto repairs.
- Hiring & Domestic Worker Services – Fraudulent websites offering short-term or hourly domestic worker hiring.
- Government & Official Services – Imitations of financial and regulatory institutions to steal authentication credentials.
- Other Niche Services – Phishing websites mimicking trusted brands in sectors like water purification or courier services.
By exploiting the trust users place in these services, fraudsters collect personal and financial details, facilitating SIM swaps and account takeovers.
Case Study: Phishing Network Targeting Insurance Customers
Group-IB’s investigation began with a phishing website that triggered multiple complaints from bank customers, reporting SIM deactivation after interacting with the site. What initially appeared to be an isolated incident quickly revealed a network of phishing domains impersonating well-known insurance providers. Figure 3 shows the interface of the fraudulent website.
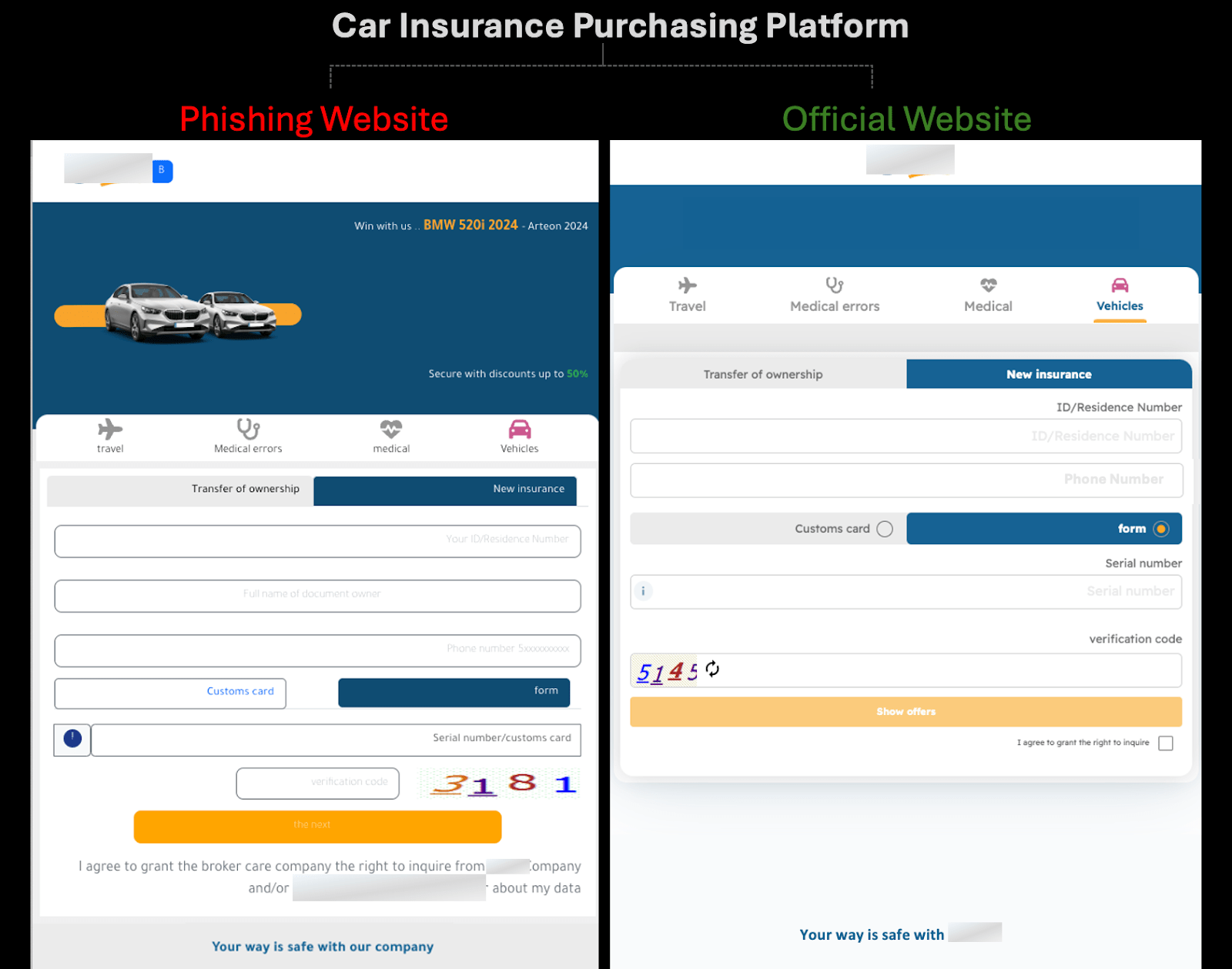
Figure 3: Example of a phishing site mimicking a legitimate car insurance service, linked to SIM swapping attacks.
Although the phishing website is now deactivated, traces of its remaining code provided clear indicators of malicious intent, as illustrated in Figure 4
Further investigation into becromeras[.]com using Group-IB’s Threat Intelligence revealed that it was linked to a larger phishing network. The domain was tied to the administrator email bednamasari@gmail[.]com, which appeared in the SOA records of over 80 associated domains. These domains shared the same IP address (209.124.66.11), identical nameservers, and were registered during November–December 2024 with one-year durations (see Figure 5).
![Figure 5: Graph network analysis revealing links between the phishing domain becromeras[.]com and a broader network of domains tied to bednamasari@gmail[.]com, sharing infrastructure like IP, nameservers, and registrar details.](https://www.group-ib.com/wp-content/uploads/unnamed5-min.png)
Figure 5: Graph network analysis revealing links between the phishing domain becromeras[.]com and a broader network of domains tied to bednamasari@gmail[.]com, sharing infrastructure like IP, nameservers, and registrar details.
A VirusTotal cross-check confirmed that 60% of the identified domains had already been flagged as phishing or suspicious. Upon analyzing their naming patterns and registration details, we found that many followed a bulk registration pattern, using typosquatting techniques to mimic well-known Gulf-region insurance brands. Examples of these phishing domains include:
- almiuttihada[.]com
- alwanttayah[.]com
- aldnorerra[.]com
- alwtonaieh[.]com
- teqgdaeers[.]site
In addition to direct impersonation, fraudsters also registered vague domain names (e.g., benomactos[.]site, braconsonara[.]net) to evade automated brand monitoring systems while still appearing credible to unsuspecting users.
This case demonstrates how phishing attacks extend beyond individual brands, targeting an entire industry sector, in this case insurance services. It underscores the need for industry-wide collaboration and proactive threat intelligence to detect and disrupt such operations early.
SIM Swap Fraud Indicators
In cases where a victim’s SIM was swapped to an eSIM, Group-IB’s Fraud Protection System detected the fraud through several indicators, as shown in Figure 6.

Figure 6: Group-IB’s Fraud Protection System detects SIM swapping in real-time when a victim’s account is accessed from a newly registered eSIM on an unfamiliar device with unusual geolocation changes.
Transaction Analysis: How Fraudsters Exploit Compromised SIMs
Once fraudsters gain control of a victim’s SIM, they exploit multiple entry points, including stolen card information and mobile banking apps, to conduct unauthorized transactions. They target fast, frictionless payment systems such as e-commerce platforms (3DS) and direct payments to merchants and digital wallets.
The appearance of transactions with Apple Pay and Android Pay (Android Payment App) shows that fraudsters were also able to perform point-of-sale (POS) transactions.
A key vulnerability lies in banking applications, where fraudsters swiftly transfer funds to mule accounts, as these transactions are often hard to reverse. RTGS (Real-Time Gross Settlement) is generally reserved for high-value transactions (over $5,332), unlike IPS (Instant Payment System) for lower amounts. Even utility payments are used to launder stolen money.
Figure 7 illustrates how SIM swapping opens multiple fraud channels, with mobile banking apps and stolen card information serving as primary access points.
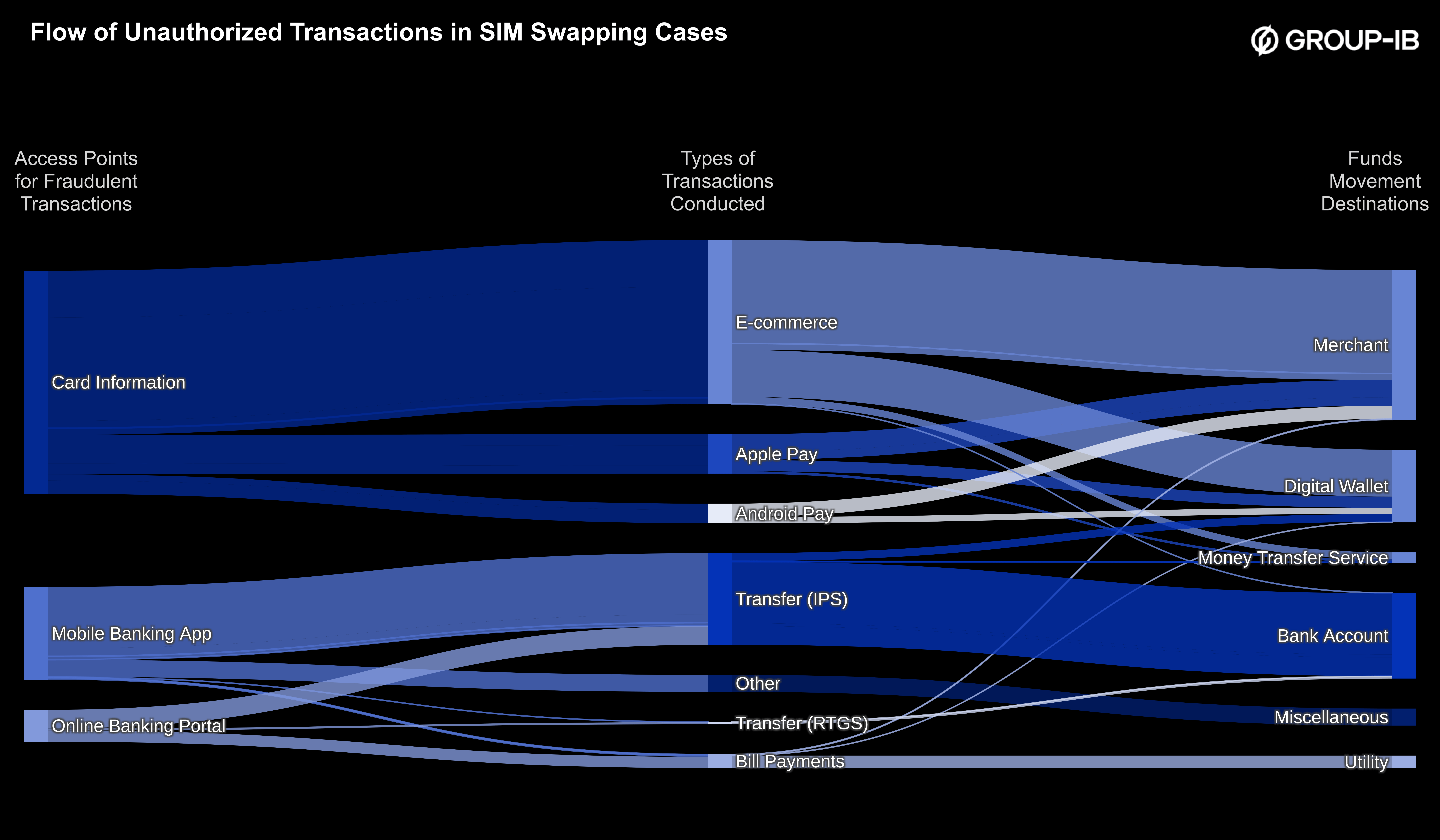
Figure 7: Flow of Unauthorized Transactions in SIM Swapping Cases, Detailing Access Points, Transaction Types, and Beneficiary Types.
Financial Losses
In 39% of reported fraud cases, multiple unauthorized transactions were conducted, while 61% resulted in total losses ranging from $270 to $5,400. Additionally, 15% of reported cases involved losses exceeding $5,400. These fraudulent flows often mimic legitimate transactions, making detection challenging without robust device data and behavioral analysis.
While most cases involve moderate losses, some incidents demonstrate the severe financial risks of SIM swap fraud. In one case, a fraudster used the victim’s national ID and compromised SIM to reset login credentials for their investment account, ultimately liquidating stocks worth over $160,000. This highlights how SIM swapping can lead to catastrophic financial losses.
Delays in Fraud Reporting
Fraud reporting delays refer to the time gap between when the first unauthorized transaction occurs and when the victim reports the fraud to the bank. Timely reporting is crucial in reducing losses and increasing the chances of recovering funds. As shown in Figure 8, while most victims report fraud on the same day, a significant portion delays action, increasing risk exposure.
Behavioral Shift in Internet Providers
An analysis of SIM swapping fraud cases revealed consistent shifts in Internet Service Providers (ISPs) before and during unauthorized access. In most cases, victims initially connected through their primary local provider, but fraudulent sessions originated from a different ISP within the same country, suggesting that attackers had performed a SIM port-out to take control of the victim’s number.
In other cases, unauthorized access to victims’ banking channels was traced to foreign ISPs in countries such as Jordan, Turkey, and Pakistan within a short period of time. This suggests that the fraudster, while abroad, was able to port out the victim’s SIM to another local provider in the victim’s home country before proceeding with unauthorized transactions.
Fraud Matrix
Group-IB’s Fraud Matrix provides an overview of the tactics and techniques used in SIM swapping fraud, as shown in Figure 9.

Figure 9: Fraud Matrix outlining the techniques used in SIM swapping fraud.
Conclusion
Despite continuous advancements by telecom providers and governments to prevent SIM swapping, fraudsters remain highly adaptive, rapidly evolving their tactics to bypass security measures. While eliminating fraud entirely is impossible, the goal is to make it as costly and difficult as possible for fraudsters.
Recommendations
Below are key insights and recommendations:
For Financial Institutions:
- Automatically freeze high-risk actions when a SIM swap event is detected and require additional identity verification.
- Treat failed fraud attempts as early indicators of reconnaissance attacks rather than isolated incidents.
- Complement historical analysis (what happened?) with predictive analytics to stay ahead of fraudsters who operate in real-time. Effective fraud prevention requires instant, API-driven intelligence that continuously adapts to emerging threats.
- Fraudsters can fake data but cannot mimic genuine user behavior. Therefore, relying solely on knowledge-based authentication (e.g., security questions) is no longer sufficient. Integrating device history, geolocation consistency, and behavioral analysis (typing speed, mouse movement, login habits, session behavior) is essential, and can be achieved through solutions like Group-IB Fraud Protection.
- Fraudsters share tactics and exploit gaps in banking systems as a network, yet financial institutions often work in silos. Real-time intelligence sharing between banks, merchants, and identity verification providers is essential to staying ahead of evolving fraud tactics.
For End Users:
- Replace SMS-based 2FA with authenticator apps like Google Authenticator or Duo to minimize the risk of SIM swap fraud.
- Stay alert for unexpected 2FA prompts or password reset messages. If you receive one without initiating it, assume someone is testing your account security and take immediate action.
































![Figure 4.2: User data was transmitted via an AJAX GET request to becromeras[.]com, an unrelated domain, exposing it in browser history and server logs. Figure 4.2: User data was transmitted via an AJAX GET request to becromeras[.]com, an unrelated domain, exposing it in browser history and server logs.](https://www.group-ib.com/wp-content/uploads/unnamed3-min.png)