The SMS scam that’s costing businesses millions
Imagine waking up to an alarming spike in SMS costs-hundreds of thousands of messages sent overnight. There’s no surge in new customers, no viral marketing campaign. Just a bill draining your budget. The culprit? A hidden cybercrime tactic known as SMS pumping fraud.
Much like a modern-day toll scam, fraudsters exploit SMS verification systems to inflate traffic, generating revenue while leaving businesses to foot the bill. This scheme has quietly siphoned millions from companies relying on SMS-based authentication, sign-ups, and notifications. But with the right strategies, businesses can detect and prevent SMS pumping.
What is SMS Pumping?
SMS Pumping, also known as artificial traffic inflation, is a type of fraud where attackers exploit SMS-based services, such as one-time passwords (OTPs) or notifications, to generate excessive message traffic using fake or automated phone numbers. This causes businesses to incur inflated costs, experience false engagement, and face disruptions in their operations. Fraudsters leverage this technique for financial gain or to strain application resources.
How does it usually work?
- A fraudster develops or uses an automated bot or low-skilled workforce to trigger actions such as fake account creation, OTP requests, or password resets. These bots or human bots mimic real user activity, often bypassing security measures through direct API calls.
- These actions trigger SMS messages, which are sent to phone numbers controlled by the fraudster, creating inflated traffic.
- The fraudster collaborates with a “rogue party,” often a corrupt telecom provider or intermediary with access to SMS routing infrastructure.
- The rogue party intercepts the inflated SMS traffic, typically avoiding message delivery to reduce costs. Instead, they route the traffic to numbers they control.
- The rogue party earns revenue by collecting funds from the inflated SMS traffic, benefiting from volume-based pricing or other arrangements.
How does it impact businesses?
For a business owner, SMS pumping can lead to several significant financial and operational problems:
- Increased Costs – The artificial inflation of SMS traffic can result in higher operational costs due to the excessive number of SMS messages being sent out, often leading to unexpected charges from SMS gateway providers.
- System Overload – The large volume of fake SMS requests can overload the application’s infrastructure, potentially causing delays, performance issues, or even complete service disruptions, affecting the user experience.
- Damage to Reputation – If users experience delays, errors, or outages due to the exploitation of the SMS system, the app’s reputation may suffer, leading to a loss of trust from customers and a decline in user engagement.
- Wasted Resources – Resources such as server capacity and customer support are wasted dealing with fake accounts and fraudulent activities, diverting attention from legitimate users and reducing operational efficiency.
Twitter’s costly battle against SMS pumping fraud
In late 2022, Elon Musk revealed that Twitter was losing around $60 million per year due to SMS pumping fraud. The activity was attributed to 390 telecom operators that allowed bot accounts to exploit Twitter’s two-factor authentication (2FA) system, generating fake SMS traffic to inflate their own revenue. As a response, Musk ordered Twitter to sever ties with telecon providers where over 10% of the SMS traffic appeared fraudulent, cutting off the source of the excessive costs.
Without proper monitoring, companies can face massive financial losses from fraudulent SMS traffic. Twitter’s case highlights the importance of proper traffic monitoring, implementing alternative authentication methods, like app-based verification, and using fraud analytics to detect unusual SMS patterns.
How SMS Pumping Fraud Exploited a KYC Onboarding Vulnerability
One real-world example of SMS pumping fraud was detected by Group-IB Fraud Protection when a customer experienced an unusual spike in new registrations. Upon investigation, it was revealed that attackers had created over 500 synthetic identities, which entered the Know Your Customer (KYC) process.
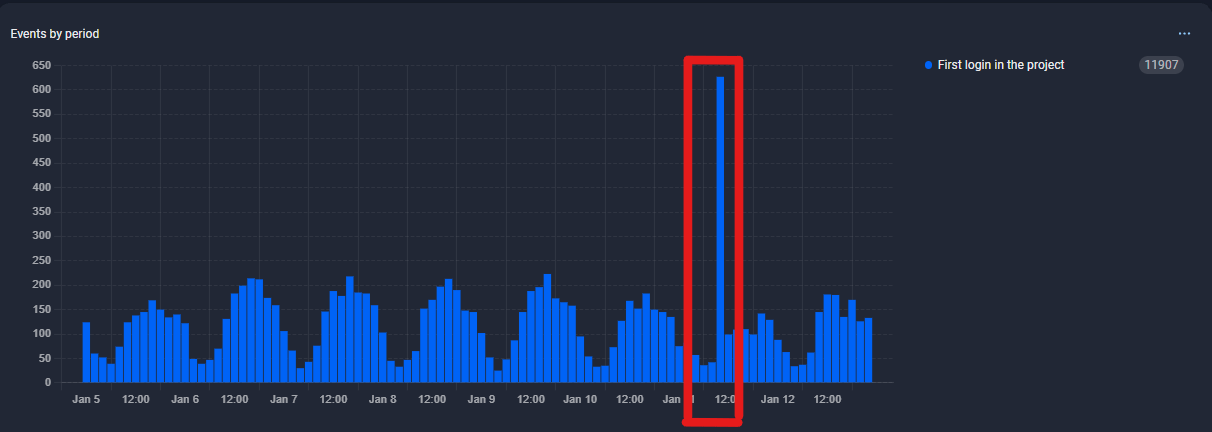
Figure 1. A screenshot showing a sudden surge of over 500 registration attempts in less than an hour
Although the company’s robust KYC measures prevented these fraudulent identities from being successfully onboarded, the attackers still achieved their goal—triggering phone verification SMS messages and exploiting a vulnerability in the onboarding process. This attack was uncovered because the fraudsters misconfigured their operation, generating a sudden surge of over 500 registration attempts in less than an hour. Typically, such fraudulent activity is distributed throughout the day to blend in with normal traffic. Even at an average A2P SMS cost of approximately €0.50 per fake identity, an attack of this scale—if sustained—could result in losses of up to €7,500 per month, with no revenue gained in return.
What is A2P SMS?
A2P (Application-to-Person) SMS refers to text messages that are sent from an application to an individual user. These messages serve various business and security purposes, such as One-Time Passwords (OTPs), authentication codes, transaction alerts, and sign-in notifications. Unlike person-to-person (P2P) SMS, A2P messages are typically automated and triggered by user interactions within an app.
Key Actors
The A2P SMS revenue flow involves several entities, each playing a role in message delivery and revenue distribution:
- App User – The recipient of the SMS, typically interacting with a web or mobile app.
- Web or Mobile App – The service provider that initiates the SMS request to verify user actions.
- SMS Hub Used by the App – The initial SMS aggregator responsible for routing messages to telecom networks.
- Transit SMS Hubs / Aggregators – Intermediary entities that relay SMS traffic across global telecom networks.
- Telecom Operator – The final entity responsible for delivering the message to the app user’s phone number.
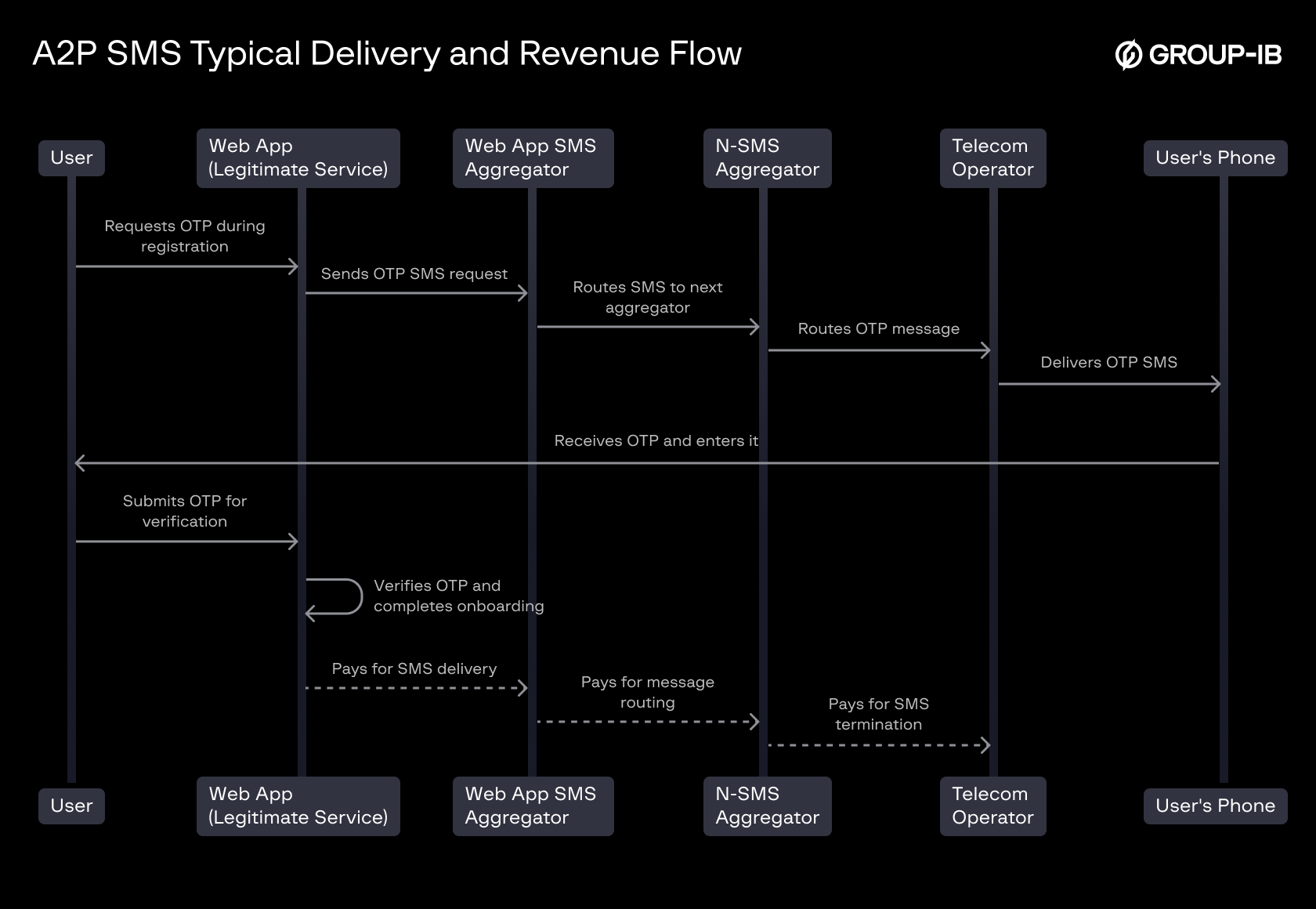
Figure 2. A2P SMS Typical Delivery and Revenue Flow
A2P SMS Revenue Flow
A defining characteristic of A2P SMS is that it is typically free for the end user—costs are absorbed by the entity that initiates the message, such as a business or online service. The revenue distribution follows these principles:
- Web or Mobile App Pays for SMS Delivery – The app contracts an SMS aggregator or provider to send A2P messages.
- Revenue is Distributed Across the Routing Chain – The SMS hub, along with any transit aggregators, take a share of the payment as the message progresses through the network.
- Final Beneficiary: Telecom Operator – The last entity in the chain, typically the mobile network operator, collects the remaining share of the SMS revenue for terminating the message to the user’s phone.
Fraudulent A2P SMS Flow (SMS Pumping)
Key Phases of SMS Pumping Fraud
Unlike legitimate A2P SMS delivery, fraudulent actors exploit the revenue model by artificially inflating SMS traffic. The fraud typically follows these four phases:
- Preparation – The fraudster registers multiple phone numbers, either through SIM farms, rogue telecom providers, or fake identities. These numbers are often concentrated in regions with high SMS termination fees.
- Execution – The fraudster (or an automated bot) triggers a high volume of OTP or verification SMS requests by abusing web or mobile apps that offer free SMS verification.
- Defense Evasion – The fraudster may use tactics such as human bots, direct API calls, and session spoofing to bypass rate limits and fraud detection systems.
- Monetization – The fraudulent traffic is routed through rogue SMS aggregators or telecom providers who manipulate delivery reports to claim revenue without actually delivering SMS messages to real end-users.
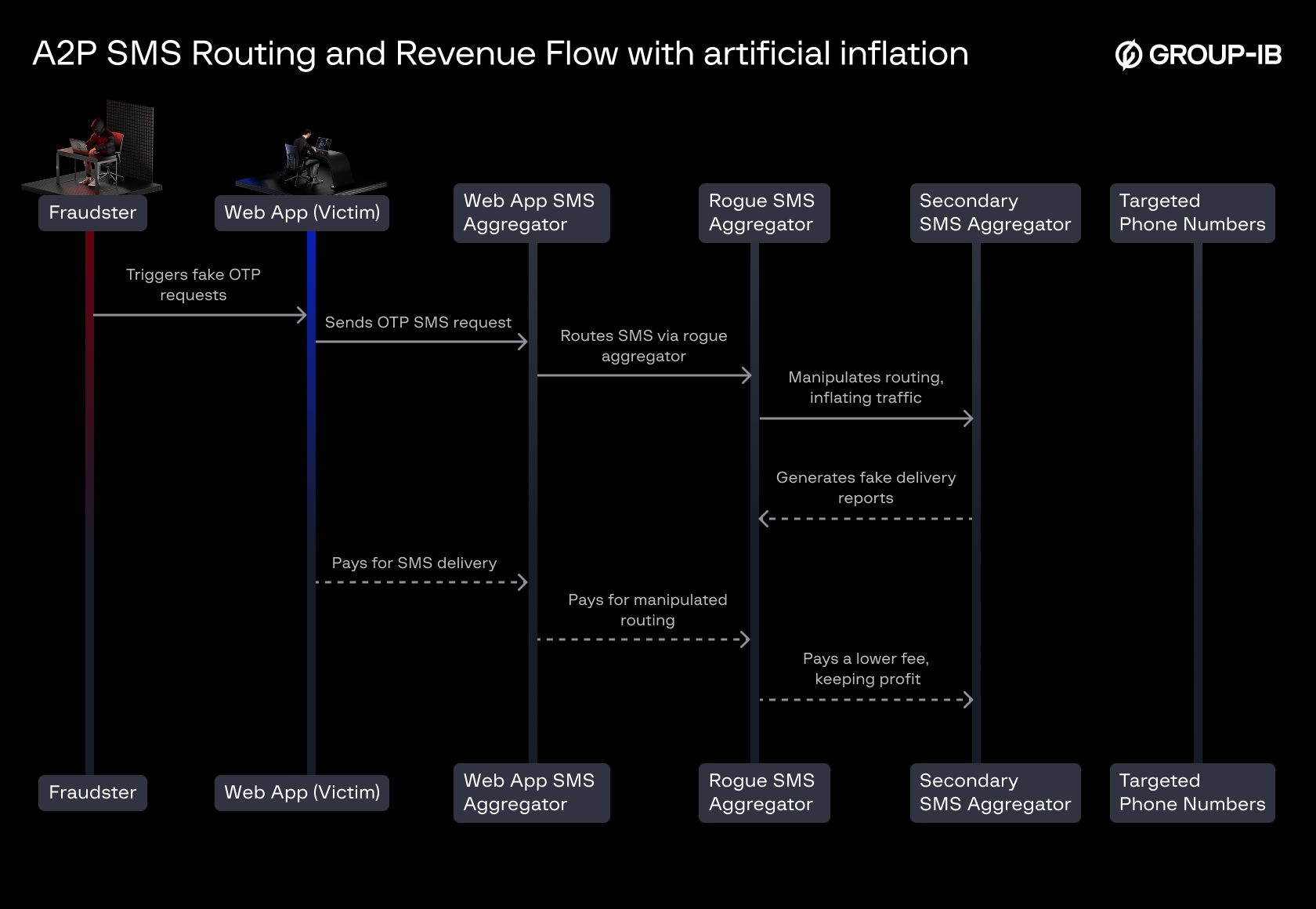
Figure 3. A2P SMS Routing and Revenue Flow with artificial inflation
How Fraudsters Monetize SMS Pumping
- Web or Mobile App Pays for SMS Delivery – Just like in the legitimate case, the app contracts an SMS aggregator to send messages.
- Rogue SMS Aggregator Inflates Traffic – Instead of routing messages efficiently, the rogue aggregator or transit hubs manipulate SMS traffic, generating artificially high volumes.
- Fake or Partial Delivery Reports – The rogue entity may claim successful message delivery without actually terminating the SMS, avoiding costs while still receiving revenue.
- Revenue Sharing in the Fraud Chain – The fraudulent parties split the profits, with each intermediary taking a portion before the remaining revenue reaches the rogue telecom provider.
How Are SMS Pumping Attacks Detected by Fraud Protection?
Risk Indicators Detected
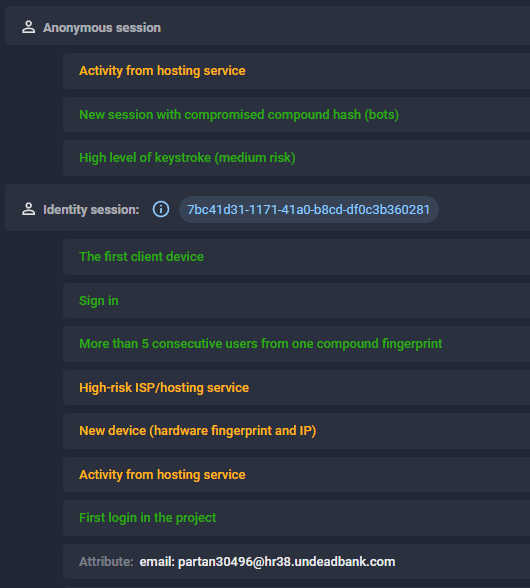
Figure 4. Web-app session captured by Fraud Protection during the SMS Pumping attack
- Unusual User Behavior Patterns – More than 500 fake accounts were created using the same hardware device fingerprint, indicating a coordinated attempt to automate account generation.
- Suspicious Hosting and ISP Activity – The traffic originated from known hosting services and high-risk ISPs, which are commonly associated with automated fraud operations rather than genuine users.
- Unnatural Keystroke Behavior – Some sessions exhibited extremely high levels of keystrokes, a pattern often linked to automated input emulation, suggesting bots or human-assisted automation.
- Massive Use of Disposable Emails – newly registered accounts used temporary or disposable email addresses, indicating an attempt to create fake identities at scale.
Typical Attack Visualization

Figure 5. Graph built based on the fake accounts created during the SMS Pumping attack
Graph Analysis of the involved entities just proves bot characteristics of the registrations:
- All identities are connected via the same fingerprint despite “One agent – one identity” approach (each session of the very next identity is initiated on the fresh agent with a newly assigned cookie);
- Limited number of IP networks in use
Sample Scenario Reproduction
- Automated or Human-Assisted Account Creation:
- The fraudster used an automated bot or a team of human bots to repeatedly initiate new registration attempts.
- Each session had a unique cookie, suggesting that the attackers deliberately refreshed browser sessions or used automation techniques to create a new session fingerprint while maintaining the same underlying hardware setup.
- The attack targeted the phone verification step, generating a high volume of SMS messages.
- Device and Network Spoofing:
- The system detected that multiple users (more than five) shared the same hardware fingerprint, indicating that the same device or virtual machine was being used across different registration attempts.
- The sessions originated from a hosting service, suggesting the use of cloud-based virtual machines, mobile emulators, or device farms.
- A high-risk ISP/hosting service was flagged, likely because it is known for bot traffic, anonymization, or large-scale automated requests.
- Suspicious User Behavior During Registration:
- A high level of keystroke activity (medium risk) suggests scripted or automated input for registration fields.
- A high level of keystroke activity (high risk) could indicate rapid, repetitive actions, possibly from automation tools or human-assisted input methods optimized for speed.
Fraud Protection identified an SMS Pumping attack where fraudsters systematically abused the registration process. While they attempted to appear as different users by resetting cookies or using incognito mode, the persistent hardware fingerprint exposed their activity. The use of hosting services, suspicious ISPs, and anomalyus keystroke patterns further confirmed the fraudulent nature of the traffic.
Financial Consequences
Increased Messaging Costs
- Likeliness: Very high
- Impact: High
Fraudsters inflate SMS traffic, leading to significantly higher costs for businesses that rely on per-message billing. If premium-rate numbers or inflated charges are involved, the cost can escalate quickly, causing financial strain.
Strained SMS Infrastructure and Service Disruptions
- Likeliness: High
- Impact: High
Fake SMS traffic can overwhelm the SMS infrastructure, causing service disruptions, delays, or system outages. These interruptions can require immediate fixes or infrastructure upgrades, leading to unexpected operational costs and negatively affecting user experience.
Lost Revenue from Customer Trust Erosion
- Likeliness: High
- Impact: High
If customers encounter issues like delays or failures in SMS verification, trust in the service may erode, leading to customer churn. This could result in significant revenue loss as users abandon the platform or stop engaging with the service.
Penalties and Charges from Telecom Providers
- Likeliness: Medium
- Impact: Medium
Telecom providers may impose penalties or additional charges for irregular SMS traffic, especially if the fraud causes the business to exceed agreed message volumes or breach terms of service. These penalties can add up over time and impact the business’s bottom line.
Brand Reputation Damage and Loss of Business Opportunities
- Likeliness: Medium
- Impact: High
Exposure of SMS Pumping fraud can severely damage a company’s reputation. Negative press and public exposure may cause a loss of business partnerships, decreased consumer trust, and a significant decline in new customer acquisition. Restoring a brand’s reputation often requires substantial marketing and PR efforts.
Conclusion
SMS Pumping fraud is a growing concern for businesses that rely on SMS services for phone number verification during sign-up, two-factor authentication (2FA), and other critical user communications. Services such as these are often targeted by fraudsters seeking to inflate traffic and exploit SMS billing systems, leading to significant financial and operational consequences.
The financial impact can be substantial, with businesses facing inflated messaging costs, fines from telecom providers, and revenue loss from customer churn due to service disruptions or delays in SMS delivery. The operational consequences are equally severe, as fake traffic can strain infrastructure, resulting in downtime and a poor user experience. Moreover, damage to brand reputation may lead to long-term losses in customer trust and future business opportunities.
To mitigate these risks, businesses must implement both proactive and reactive measures. Proactive measures include real-time monitoring of traffic, anomaly detection, and limiting the volume of SMS requests from suspicious sources. Reactive measures involve quickly identifying and responding to fraudulent activity by suspending or blocking suspicious accounts, investigating the source of fraud, and restoring any affected services. These steps are essential to safeguarding the integrity of business SMS services and minimizing potential damage from fraud.
Recommendations
SMS Traffic Anomaly Alerting
- Set up real-time monitoring and anomaly detection to flag unusual SMS traffic, such as spikes or patterns indicating fraud. Automated alerts should be configured to notify security teams instantly, enabling rapid response to mitigate financial losses.
Bot Protection
- Implement advanced anti-bot mechanisms, such as device fingerprinting, and behavior-based analysis, to ensure that only legitimate users interact with your SMS services. This helps block fraudulent bot traffic attempting to inflate SMS volumes.
API Protection Against Exploitation
- Safeguard your SMS APIs with rate limiting, IP whitelisting, and robust authentication methods like API keys or OAuth. These protections prevent unauthorized access and mitigate the risk of SMS API abuse, such as exploitation for SMS Pumping fraud.
Comprehensive Fraud Detection Rules
- Apply a set of fraud detection rules targeting disposable emails, suspicious IP addresses, velocity checks, and device fingerprinting. These rules help identify and block potentially fraudulent activity by recognizing patterns that deviate from legitimate user behavior.
Fraud Matrix
Protect digital identity and prevent fraud in real time

































