Who may find this post interesting
Vulnerability management teams, risk managers, SOC analysts, CTI analysts
Available in Group-IB Threat Intelligence
Defeat threats efficiently and identify attackers proactively with a revolutionary cyber threat intelligence platform by Group-IB
Introduction
Love it or hate it, AI in cybersecurity is no longer hype or hypothetical. You can either harness its power or deal with the consequences. Attackers are already using AI to launch faster and more convincing phishing campaigns, generate deepfake videos, and exploit vulnerabilities at scale. Meanwhile, defenders are bogged down by slow, manual workflows and debating the risks of AI while cybercriminals charge ahead, in an industry where seconds matter. We’ve been there and we know what’s at stake.
To stay ahead, security teams need AI-driven tools that detect threats in real time, identify anomalies before they can escalate, and automate responses. Such tools streamline routine tasks, which allows experts to focus on more complex and critical issues. As AI assistants evolve, they will have the potential to make security operations dramatically more effective. Given that AI systems and their extensive access are prime targets for exploitation, however, a “security by design” approach is essential.
At Group-IB, we’re always looking for more innovative ways to help our customers address the most difficult issues. Bearing all the above in mind, today we’re happy to introduce our AI Assistant designed to make your work life easier. Our tool will change how you and your team interact with threat intelligence without compromising privacy: no more sifting through countless reports, managing multi-step filters, or waiting on slow manual processes. Just real-time, relevant, structured, and context-rich responses to your plain-language questions in seconds.
Manual threat intelligence: an uphill battle
Every security team has the same problem: too much data and not enough time and workforce to process it. Analysts spend hours sorting through intelligence, cross-referencing sources and reports, and manually piecing together information just to answer simple yet critical questions. Under the circumstances, specialists get burnt out and are left feeling frustrated and overloaded.
A SOC analyst trying to verify a suspicious file has to jump from one malware repository to the next, research known IoCs, and scan internal logs. A threat hunter tracking APT activity in their region has to manually compile recent attack patterns, review multiple sources, and cross-check findings before even starting an analysis.
Group-IB AI Assistant changes all that by converging one of the industry’s largest threat intelligence databases with AI to help you make decisions quicker. Now, instead of navigating rigid search functions or static dashboards, analysts can simply ask questions such as: What are the latest TTPs used by this threat actor? Which vulnerabilities are currently being exploited in financial attacks? Instead of spending half the day gathering intelligence, they get precise answers instantly.
How the assistant works
Traditional RAG (Retrieval-Augmented Generation) systems retrieve relevant documents based on vector embeddings and provide them to a language model for answer generation. Group-IB AI Assistant goes beyond this approach. Instead of relying solely on vector searches, AI Assistant first reformulates user inputs into independent queries. It then determines the most relevant data sources — whether vulnerabilities, malware reports, threat actor profiles, or attack statistics — and identifies key elements like indicators, dates, and country-specific incidents.
For greater accuracy, AI Assistant prioritizes direct keyword detection for IP addresses, domains, and malware names. It also applies context-based ranking to highlight the most significant attacks, prioritizing incidents that carry greater risks. By correlating intelligence dynamically, the tool goes beyond simple document retrieval, giving analysts deeper insights with minimal effort.
The interface available within the Group-IB TI dashboard is a prompt, similar to a search engine input, which allows the user to ask questions in natural language and receive responses formatted as text, tables, and links to source documents. The chatbot has access to key sections of Group-IB’s Threat Intelligence and responds to all the related queries. Users can ask questions such as: Which countries did LockBit target the most? When did LockBit emerge? What is SpyMax malware? For deeper intelligence, AI Assistant can provide detailed insights into malware arsenal, MITRE ATT&CK® techniques, and the most common attack methods within a specific timeframe.
Analysts can also request intelligence about major cyber incidents from the past year or retrieve specific information relating to critical vulnerabilities like CVE-2023-47246. If a question falls outside the scope of Group-IB Threat Intelligence, the system will redirect the query or filter results to prevent hallucinations or misleading recommendations.
In addition to general intelligence, the chatbot delivers customized responses based on tailored reports exclusive to specific customers. For example, 12 reports may be available, but the chatbot will provide answers based on only eight of them as the remaining four contain sensitive, client-specific insights. This ensures that organizations receive the most relevant intelligence while protecting their confidential information.
Secure by design
Not all AI-powered security tools are created equal. Some vendors rely on commercial models like OpenAI or Google Gemini, meaning every query you make leaves your environment, gets stored externally, and is potentially used to train an external AI.
Group-IB uses a different strategy. Our AI Assistant runs on Llama 3.3, one of the most widely used open-source and pre-tuned models, which eliminates the need for external training and ensures that AI Assistant operates securely without internet access.
Because AI Assistant operates entirely within Group-IB’s secure infrastructure, there’s no external data sharing, no risk of customer queries being used for AI training, and no reliance on third-party vendors. Every request remains private, secure, and built on real threat intelligence.
We don’t use search queries to train external AI models, but AI Assistant isn’t just a static tool — it evolves continuously based on user interactions. The Group-IB team analyzes user feedback (such as thumbs-down responses) to manually refine responses and improve accuracy. This ensures that AI Assistant adapts to real-world cybersecurity needs while maintaining strict data privacy.
Use cases at your fingertips
Let’s explore how AI Assistant streamlines key intelligence tasks for security teams.
Use case 1: Identifying the most common attack techniques
Security analysts must understand which attack techniques have been used most often over the past year. Instead of manually searching through reports, they can ask AI Assistant:
“What attack techniques were used most often in 2024?”
AI Assistant instantly retrieves a structured list of techniques mapped to the MITRE ATT&CK® framework. The client can narrow the request down by specifying the industry, region, country, threat actor and attack type. This allows the team to quickly identify the most relevant threats and adjust defenses accordingly.
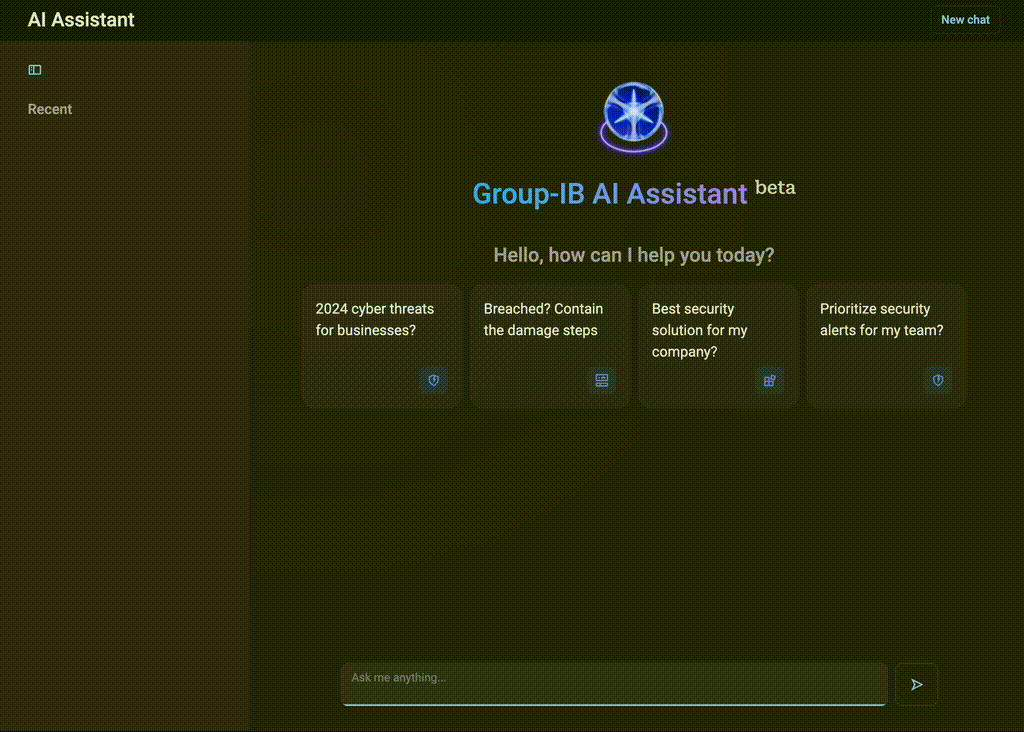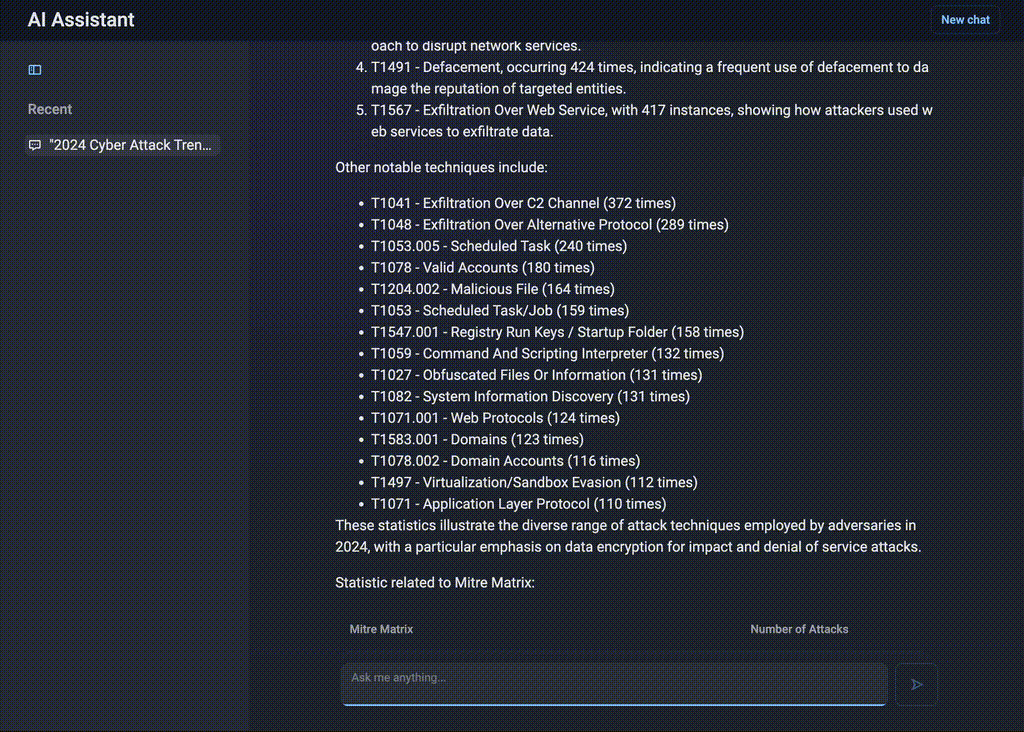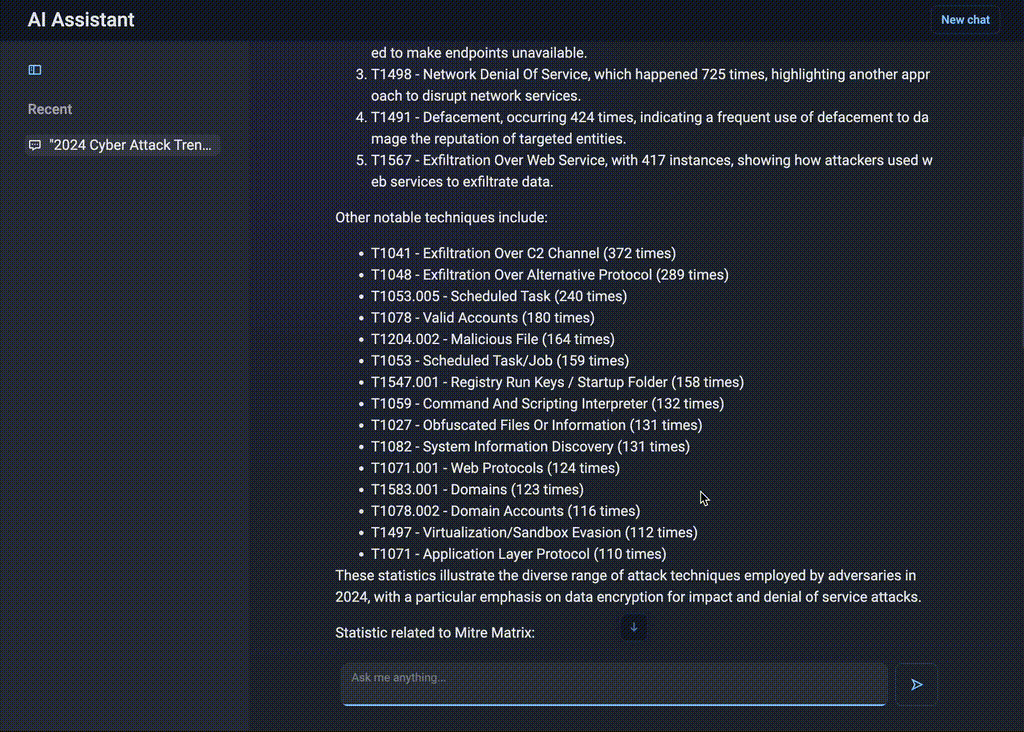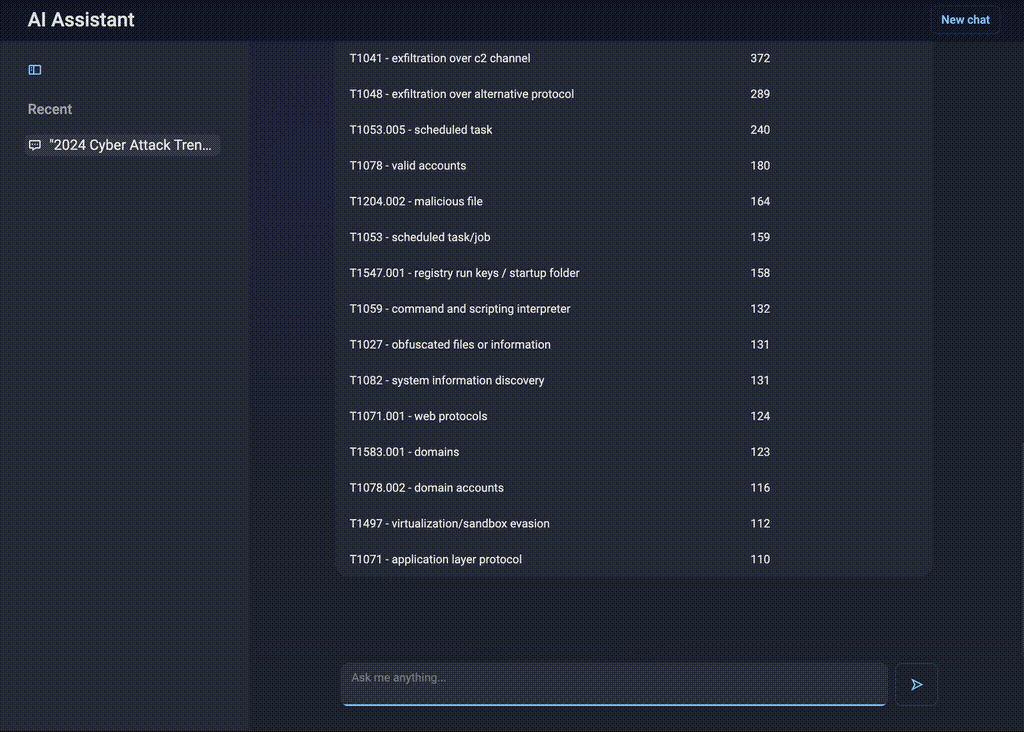
Figure 1. AI-driven statistical insights
What are the advantages over manual filtering?
For requests related to attack techniques, a security analyst would need to set date filters, sift through over 800 techniques (as shown below), cross-reference multiple intelligence sources, and manually compile findings into a structured report.
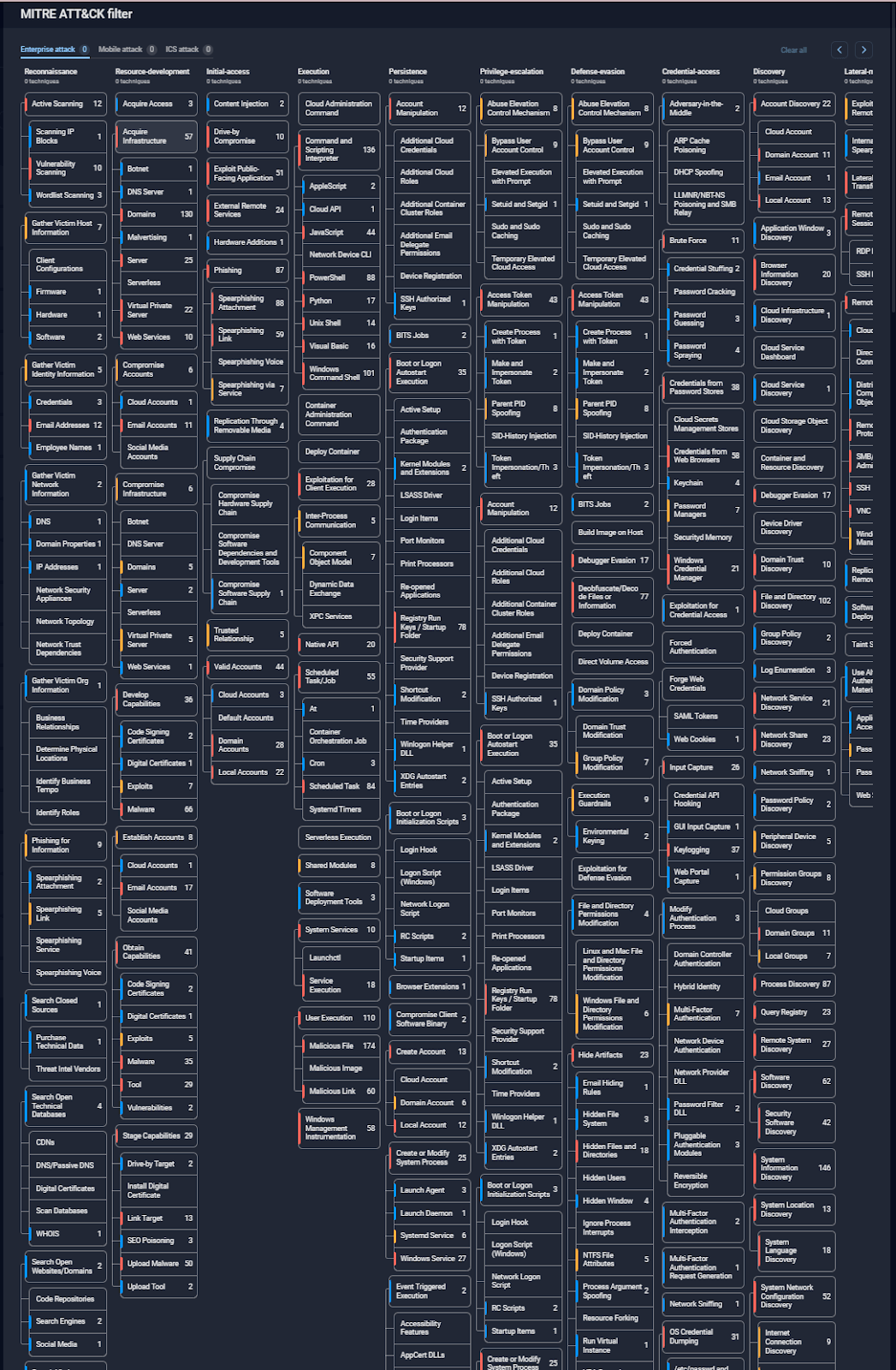
Figure 2. MITRE ATT&CK® matrix for cyber threats in 2024
Use case 2: Pinpointing the most critical vulnerabilities
Vulnerability management teams face an overwhelming volume of CVEs every year, which makes prioritization critical. If an analyst needs to identify the most dangerous vulnerabilities affecting their organization’s tech stack, they would ask AI Assistant:
“What were the most critical vulnerabilities in 2024?”
AI Assistant will then provide a ranked list of vulnerabilities with active exploits in the wild, based on real-world incidents. The analyst will also receive links to technical reports with remediation steps, which enables the security team to mitigate the highest-priority risks immediately.
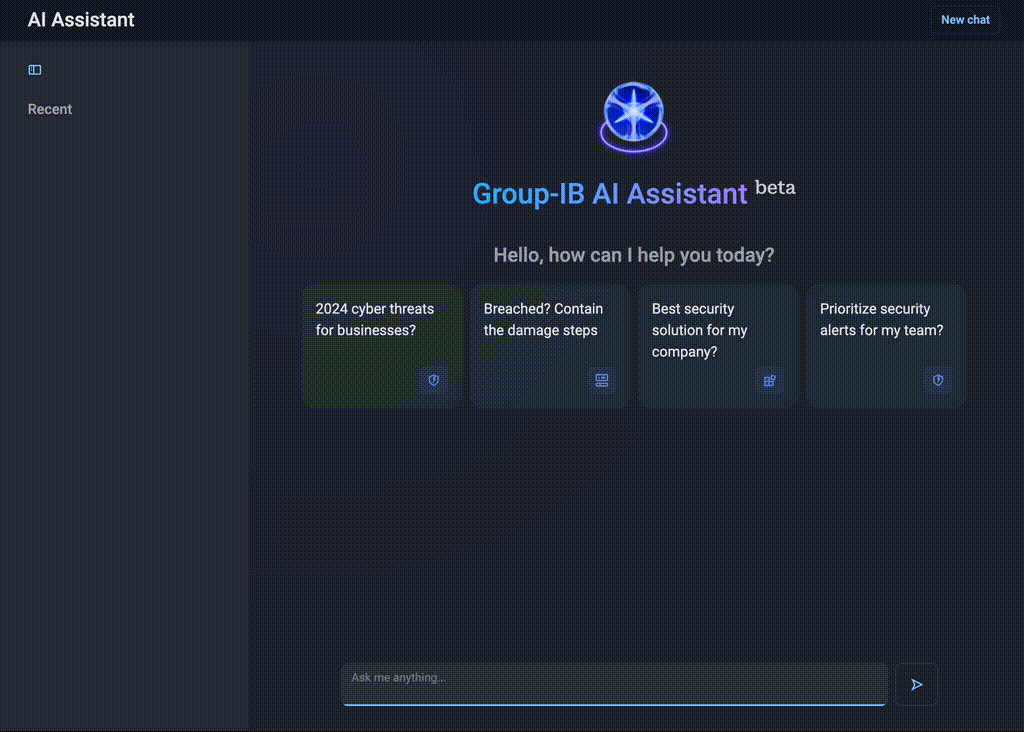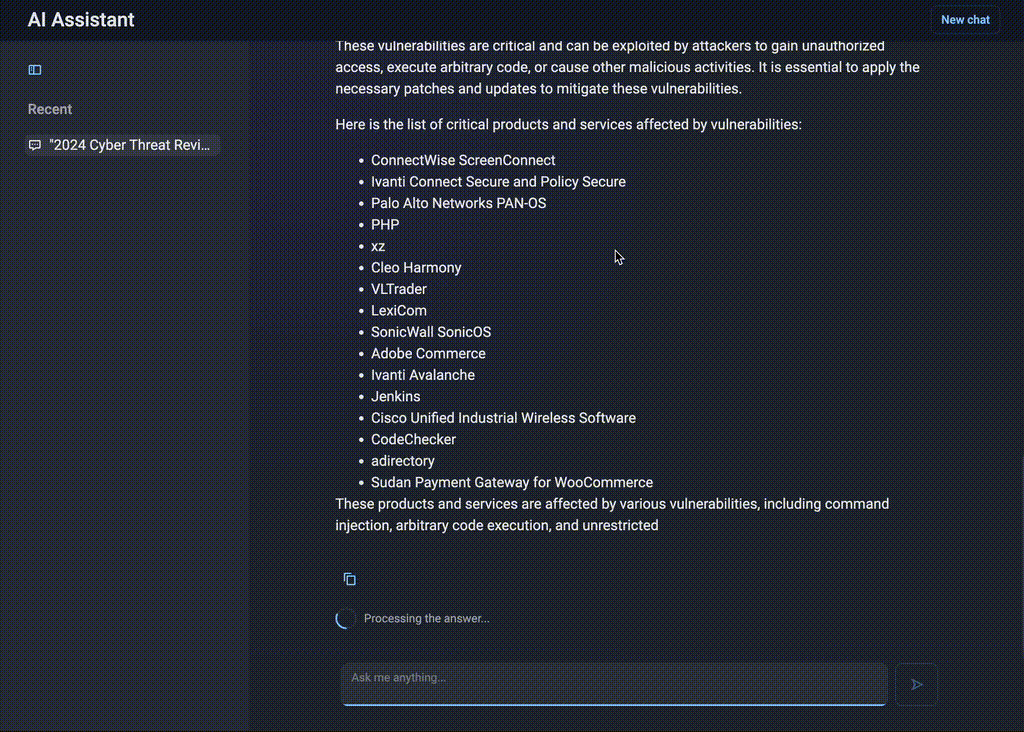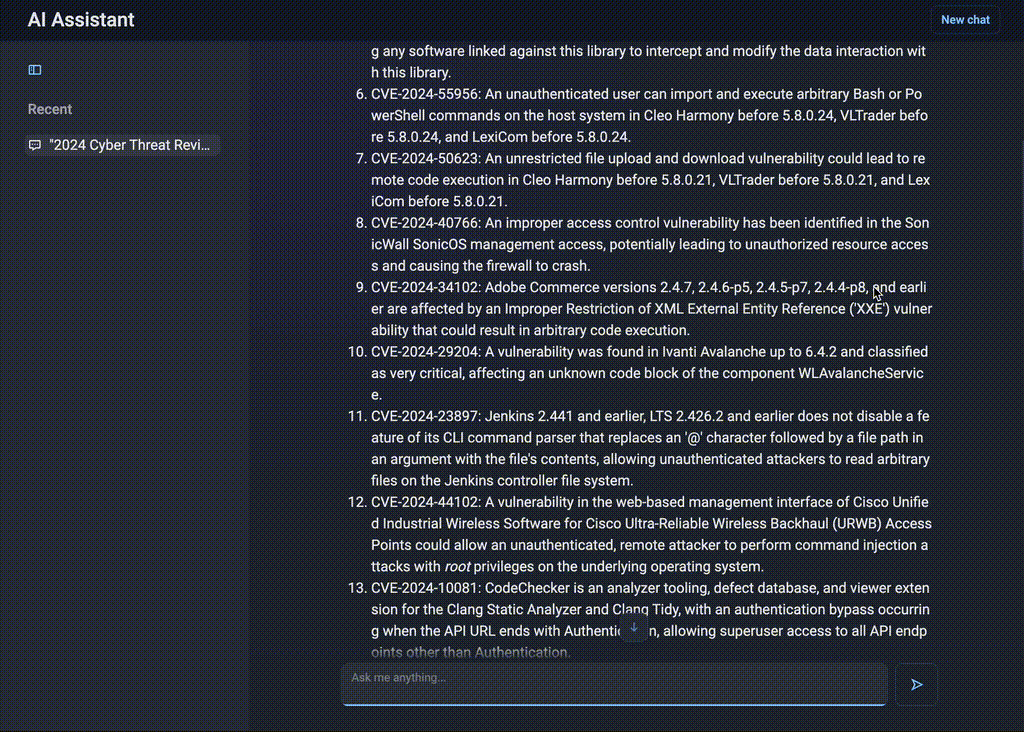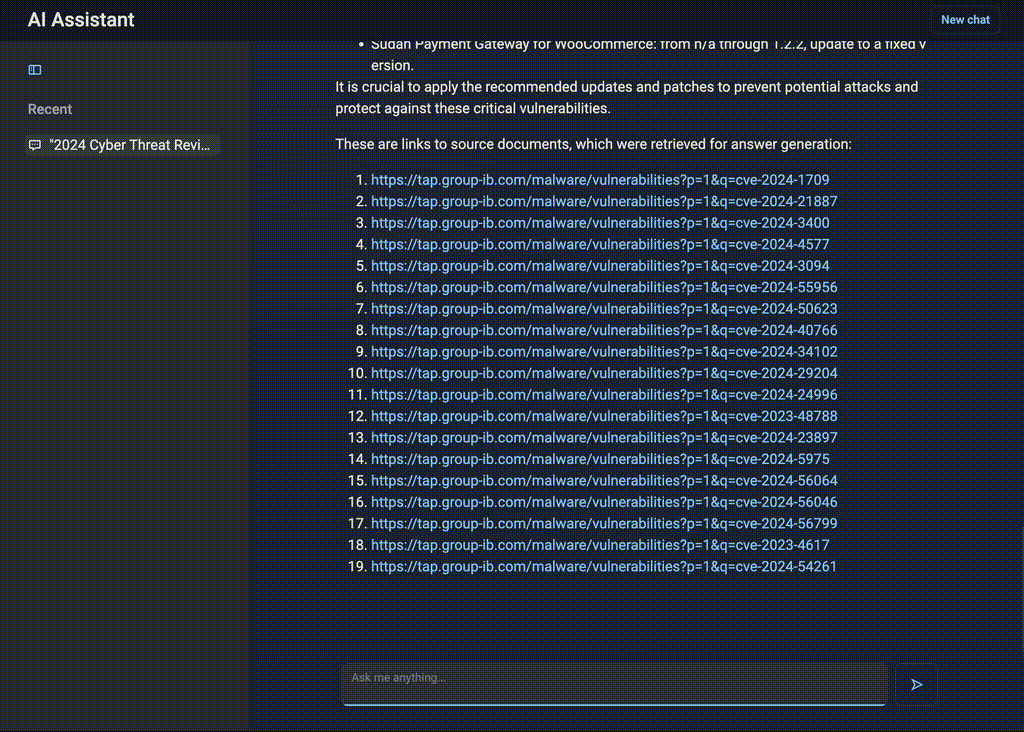
Figure 3. Integrating statistics and search across multiple sources
What are the advantages over manual filtering?
Filtering vulnerabilities by date helps narrow the scope, but no existing filter consolidates all reports containing relevant CVEs into a single, prioritized view. Even if such a filter existed, security teams would still need to manually sift through individual reports, extract key insights, and compile statistics.
Use case 3: Investigating an active exploit
If a new vulnerability — say CVE-2024-1709 — is identified as one of the most critical in the previous query (Figure 4), the security team needs immediate insights into who used this vulnerability in the wild and how. Instead of manually searching for reports, they can ask AI Assistant:
“Show me attacks linked to CVE-2024-1709 in table form with details about threat actors, attack dates, and descriptions.”
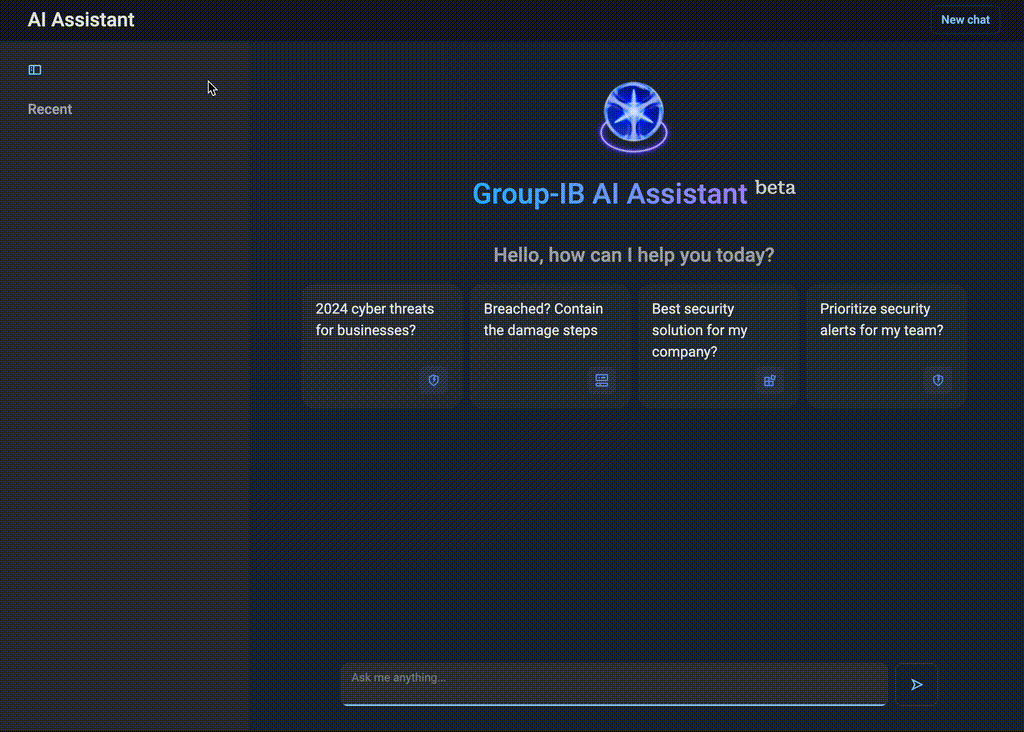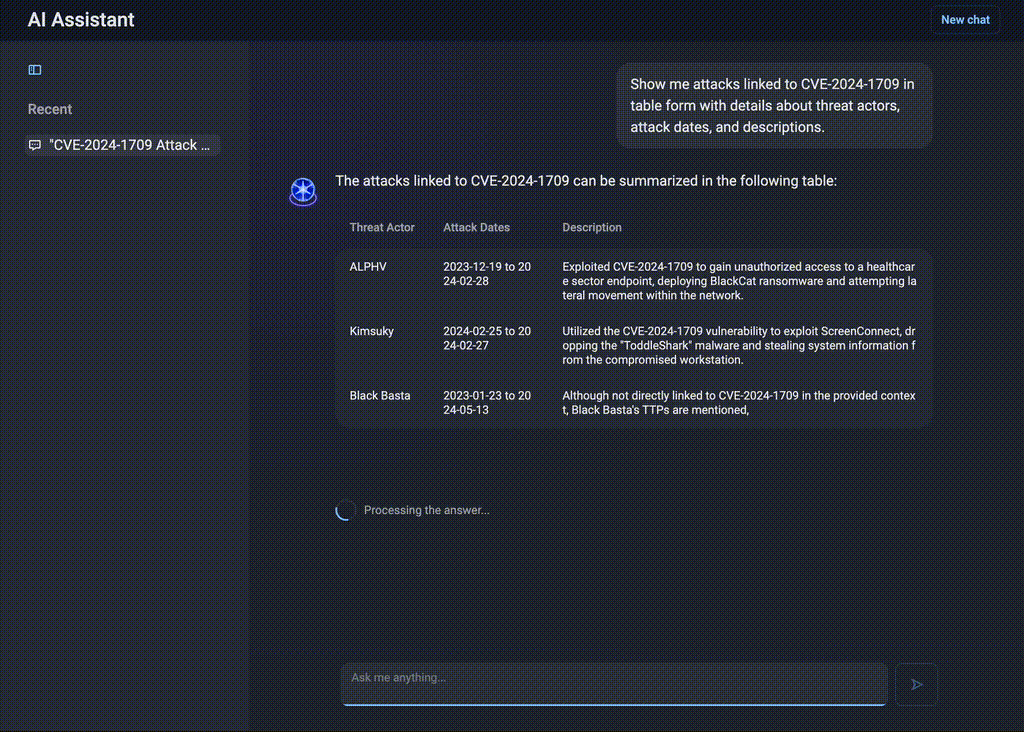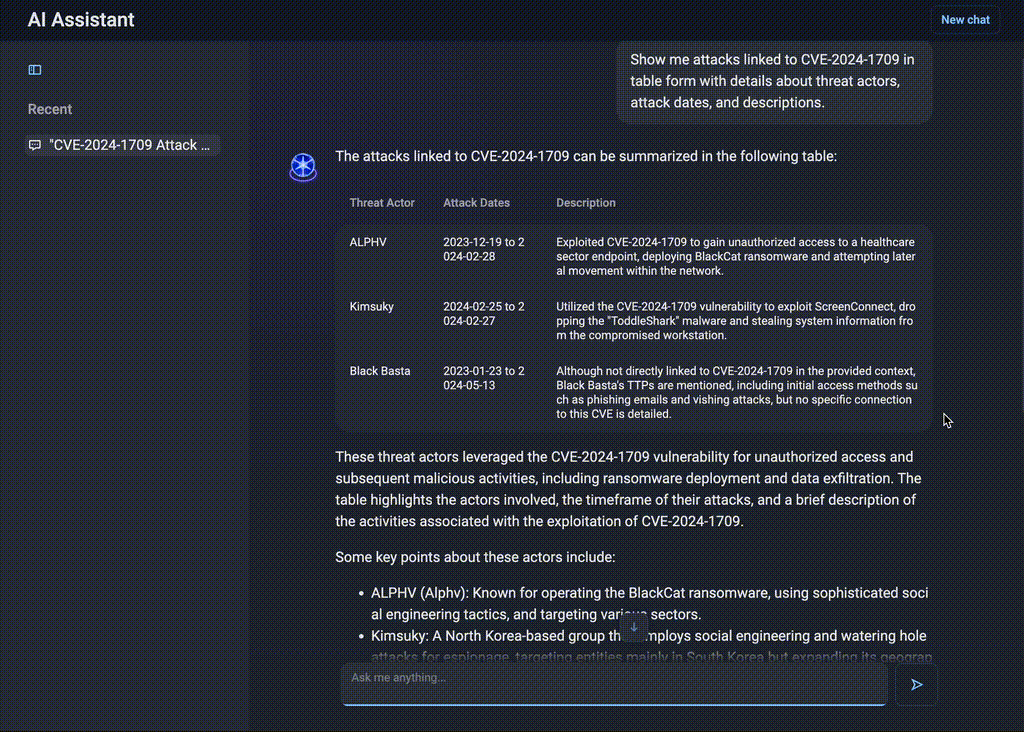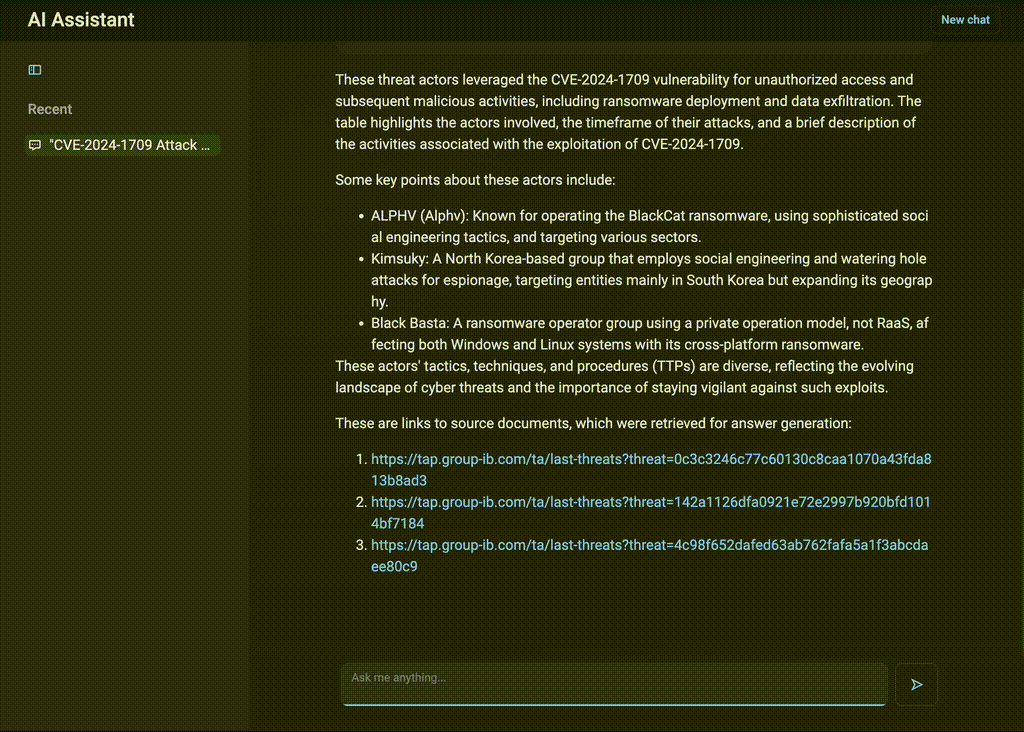
Figure 4. Structured responses by AI Assistant
AI Assistant delivers a structured dataset, listing threat actors exploiting the CVE, attack timelines, and technical details. This allows the team to assess the risk level and take proactive defensive steps.
What are the advantages over manual filtering?
Even with a date filter and an additional CVE filter, analysts would still need to manually go through multiple reports, extract key insights, and compile a summary. After that, they’d have to cross-check the CVE in the “Vulnerabilities” section to gather detailed information (as shown in the screenshot below). Such a process would be time-consuming and prone to oversights.
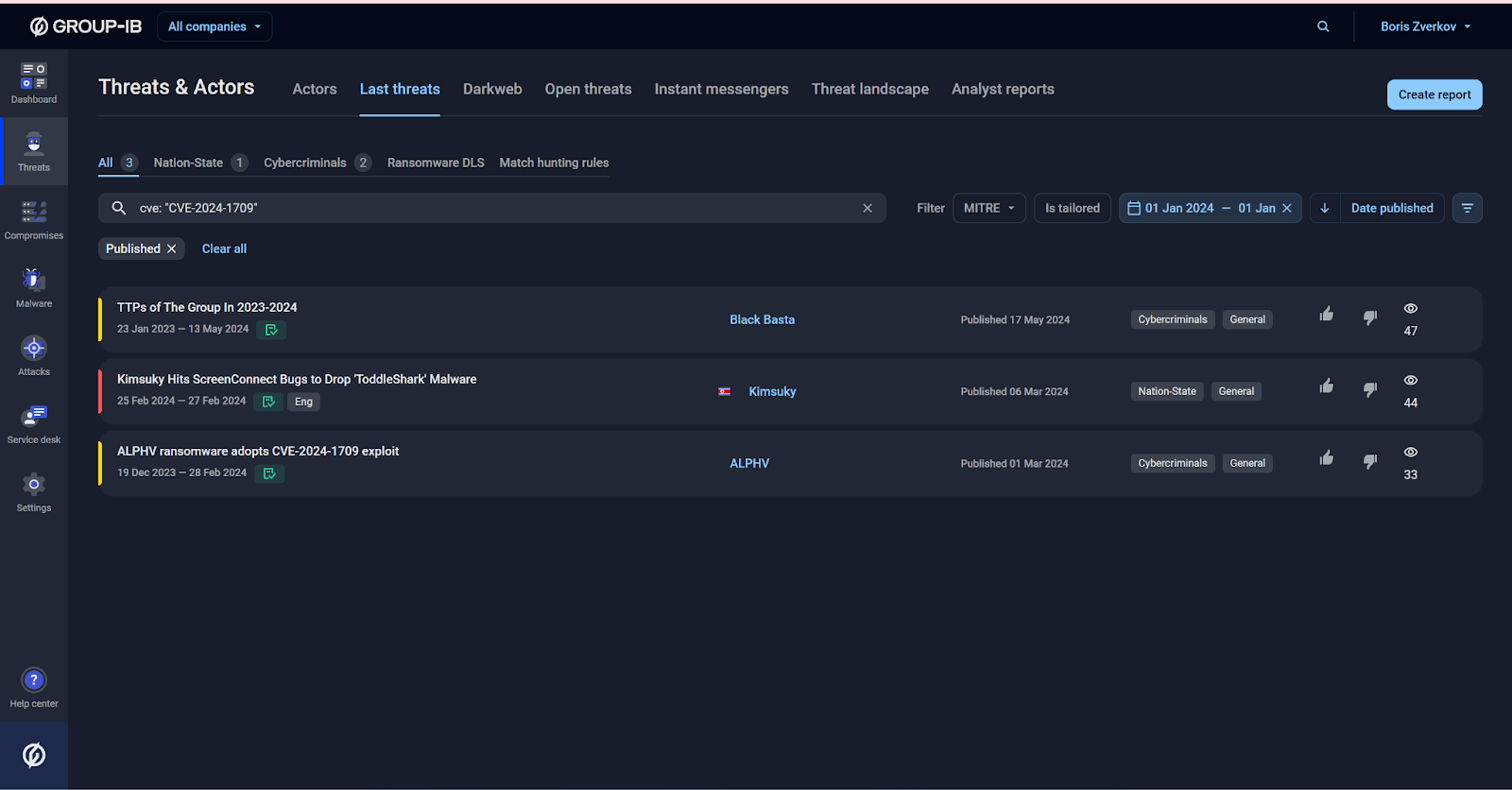
Figure 5. Manual search results for reports involving CVE-2024-1709
Use case 4: Investigating emerging threat groups
A CISO might come across a mention of a new threat actor targeting their industry — say Black Basta — but have no background information and need more intel fast. These ad-hoc, high-priority requests often take much time and pull the security team from ongoing investigations to dig through multiple sources. Instead, they can ask AI Assistant:
“Who is Black Basta and what attacks have they carried out?”
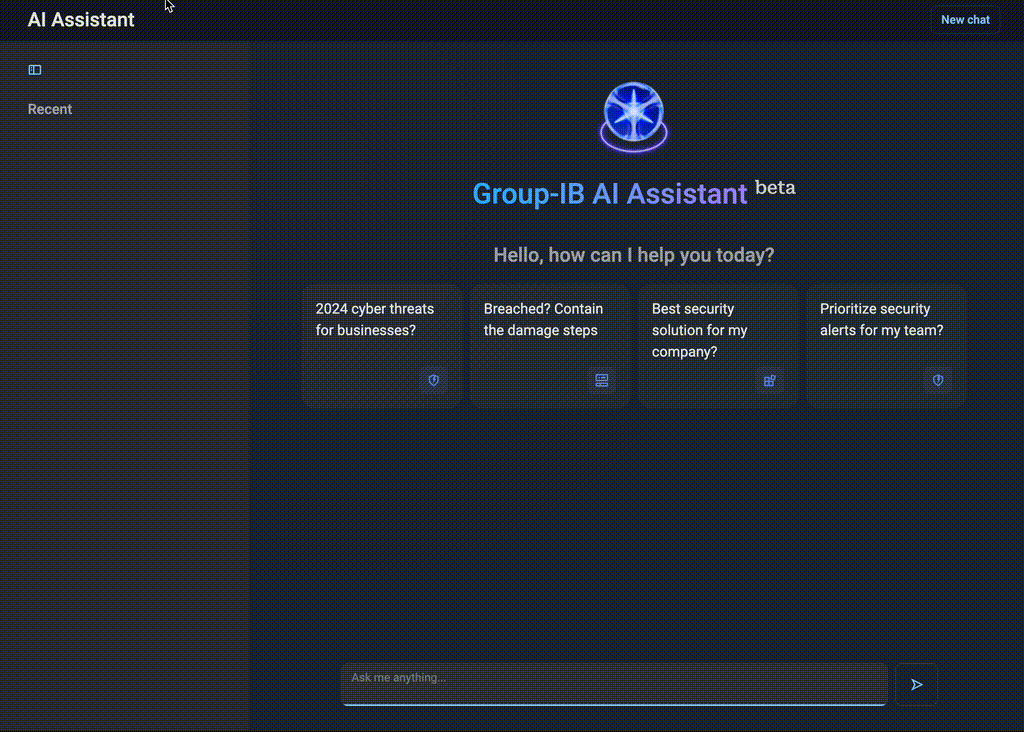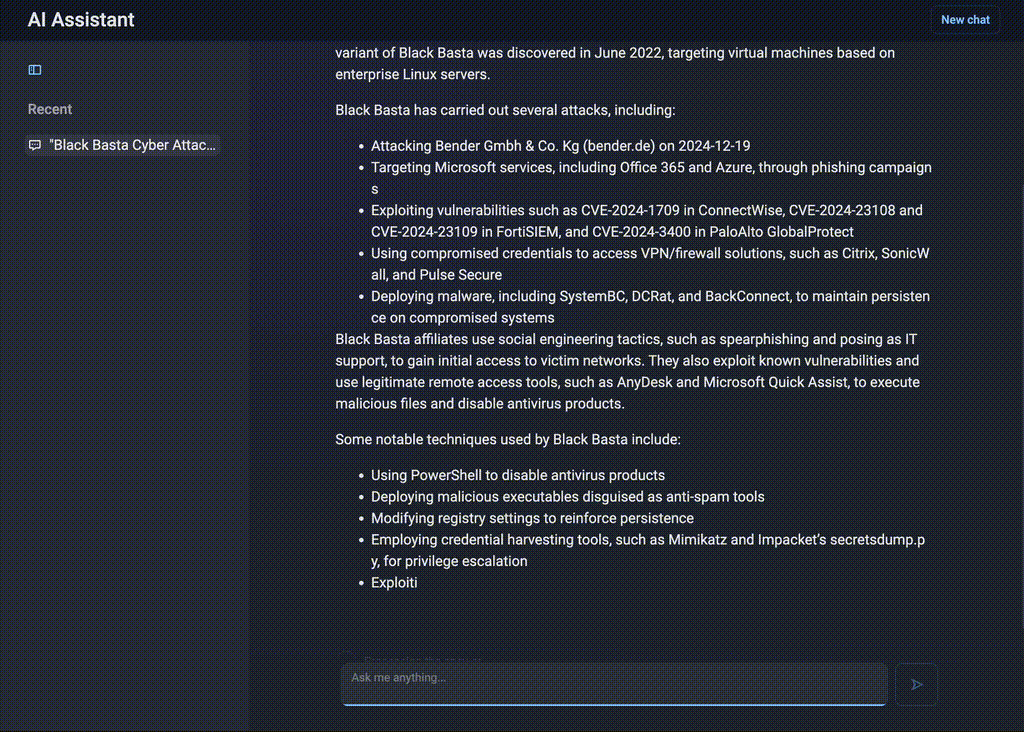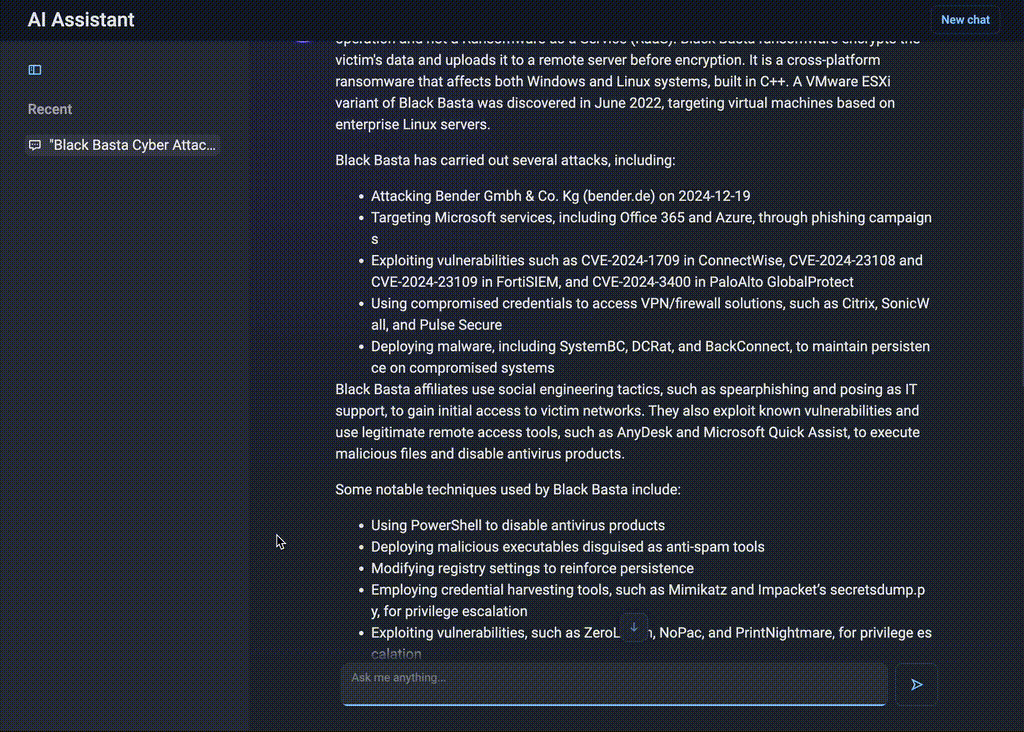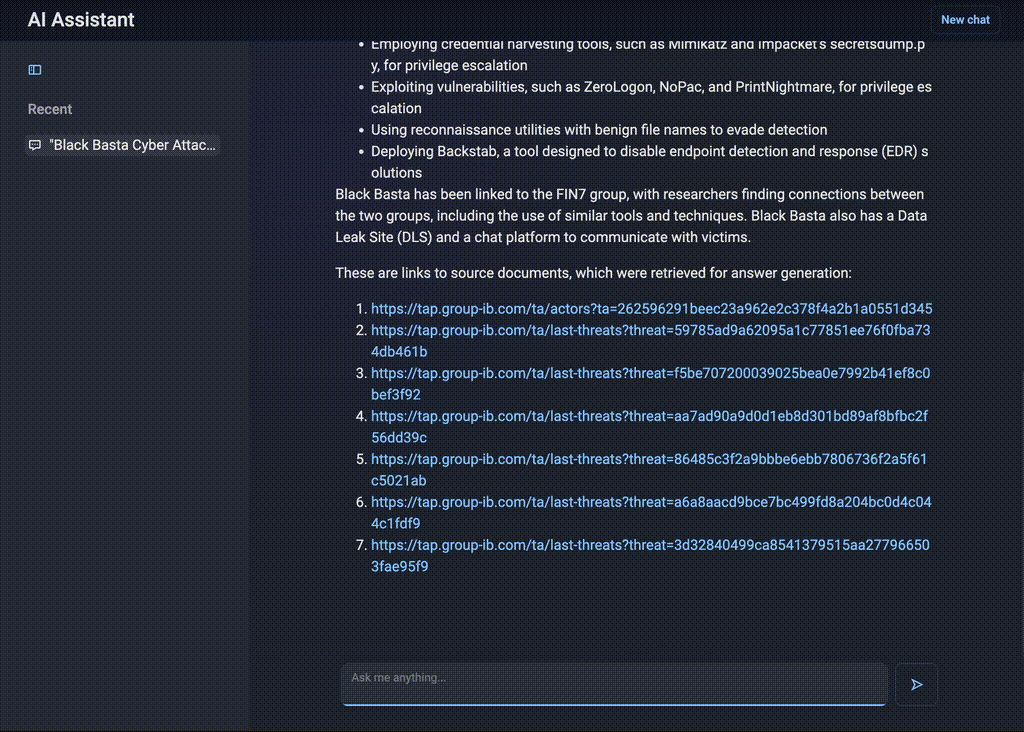
Figure 6. Intelligent summarization by AI Assistant
AI Assistant can instantly compile a profile of the group, detailing its origins, attack methods, and past campaigns. Analysts receive links to further reports and an overview of the group’s latest activities in seconds, which ensures that they stay ahead of emerging threats without disrupting their workflow.
What are the advantages over manual filtering?
Manually gathering intelligence on Black Basta would require analyzing the threat actor’s profile page along with information from the first and last attacks in the timeline. This would involve searching through several reports, identifying relevant incidents, and compiling key details.
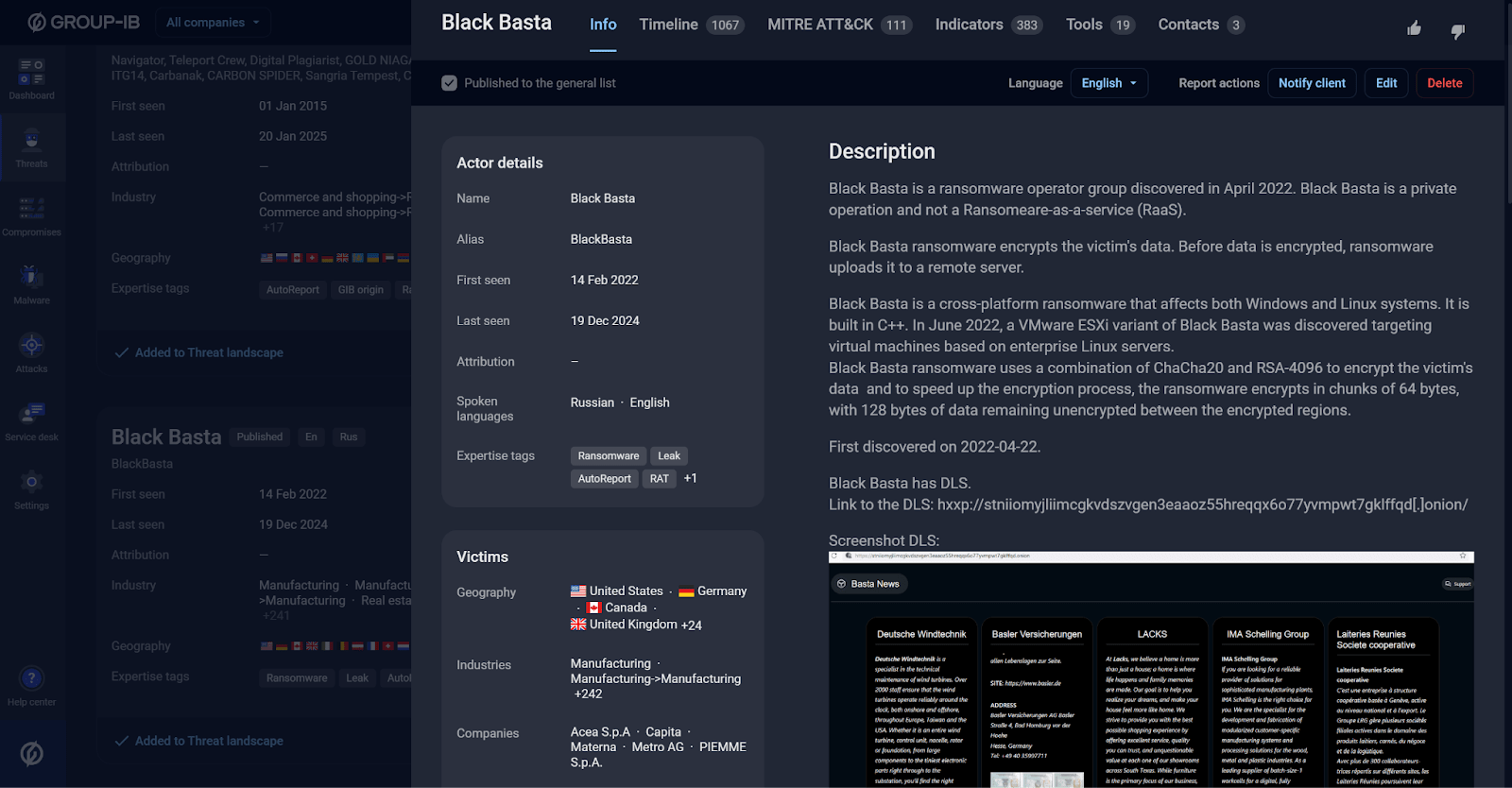
Figure 7. Black Basta actor profile in the TI interface
Use case 5: Monitoring major cyberattacks in 2025
Security leaders must stay informed about high-impact or unique cyberattacks involving new techniques that have affected their industry. A SOC team lead can ask AI Assistant:
“What were the most significant cyberattacks in 2025?”
Figure 8. Analytical capabilities of AI Assistant
AI Assistant will retrieve real-time intelligence about major incidents, attack vectors, and tools. The team can therefore stay ahead of attack evolution and adjust their security measures accordingly.
What are the advantages over manual filtering?
Such a search would require adding an expertise tag filter alongside a date filter, but even then there would be no direct way to filter by attack severity. Analysts would need to review reports manually to assess the impact of each attack.
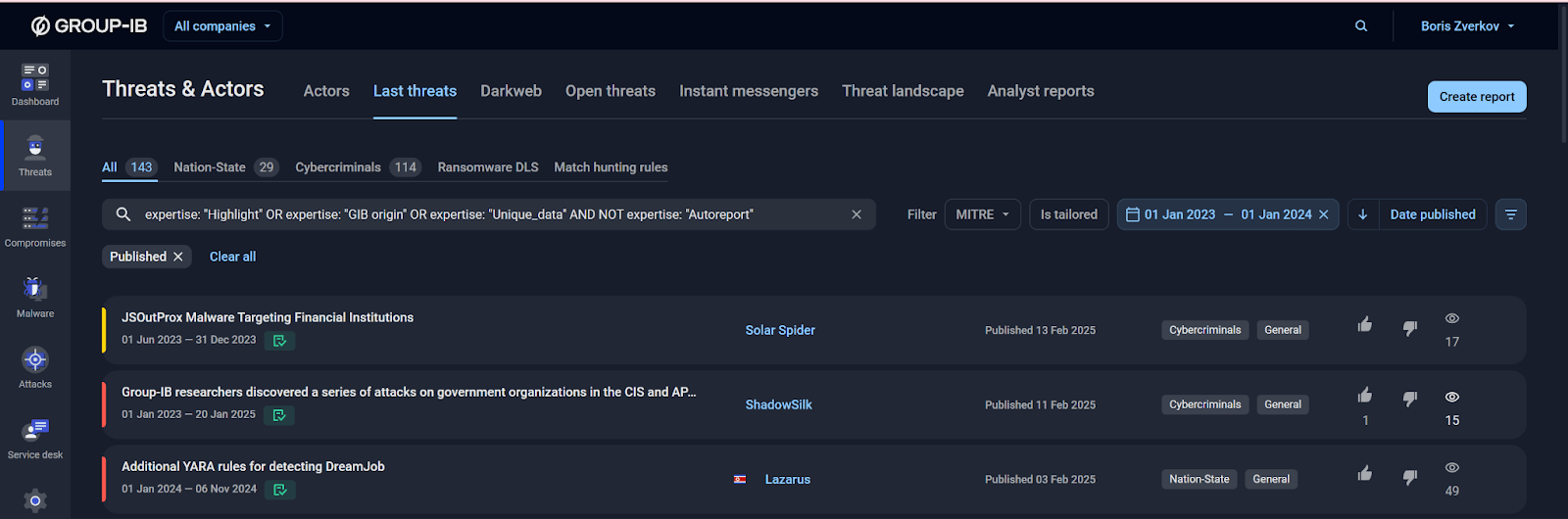
Figure 9. Approach for retrieving critical reports in the TI interface
Use case 6: A CTI team in a local bank
For financial institutions especially, monitoring targeted threats is critical. Imagine a cyber threat intelligence team at a major Thai bank that must monitor regional threats, identify targeted attacks on the financial sector, and provide timely updates to executives. Instead of manually filtering threat reports, an analyst can ask AI Assistant:
“What were the latest cyberattacks carried out against banks in Thailand?”
AI Assistant will summarize all attacks on Thai financial institutions, map them to the MITRE ATT&CK® framework, and classify them by type.
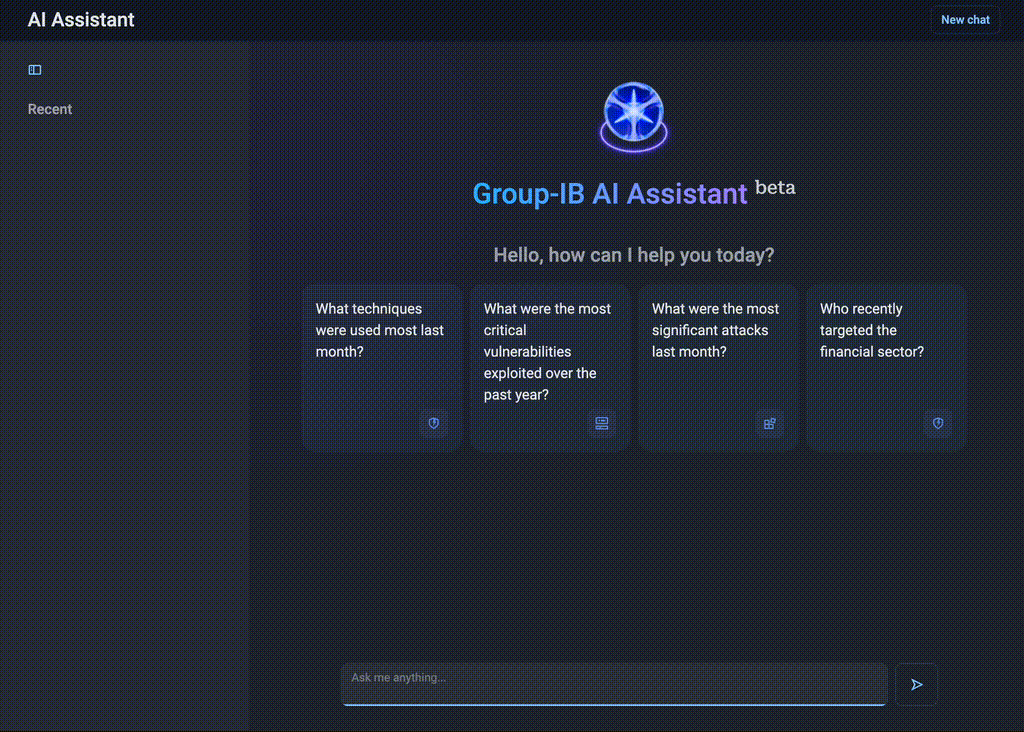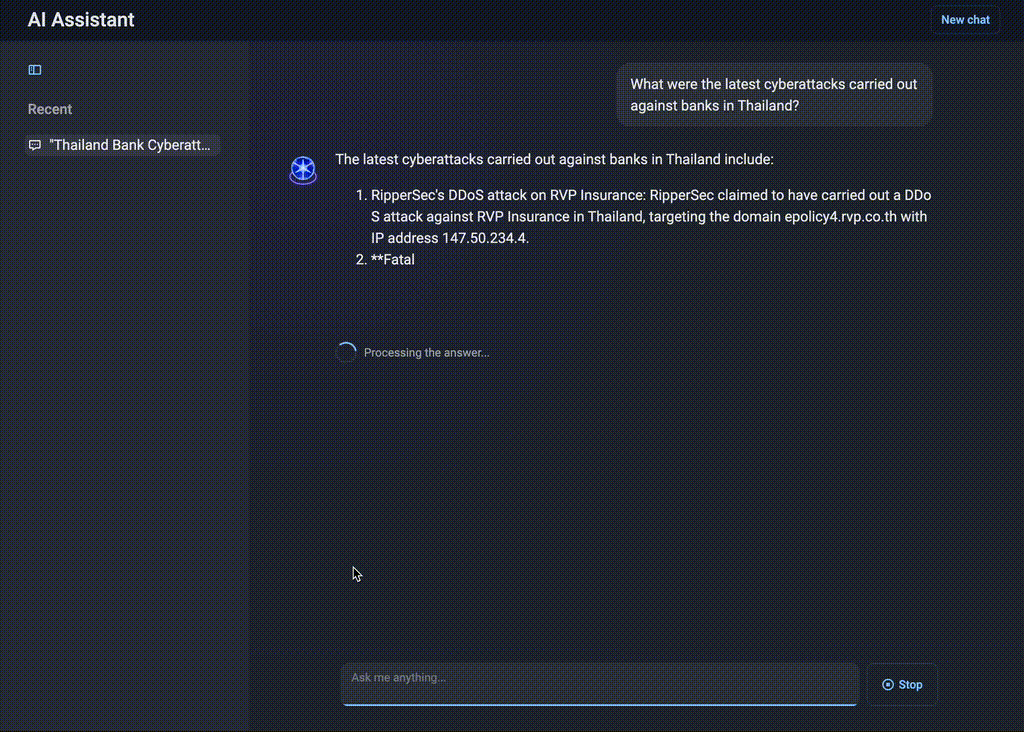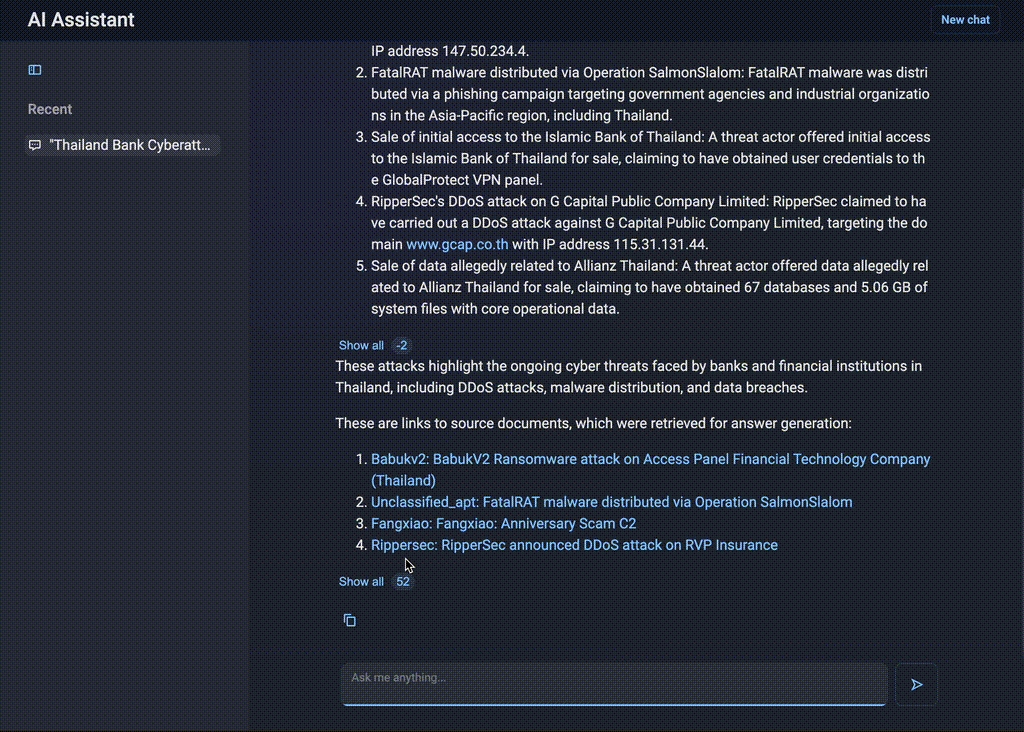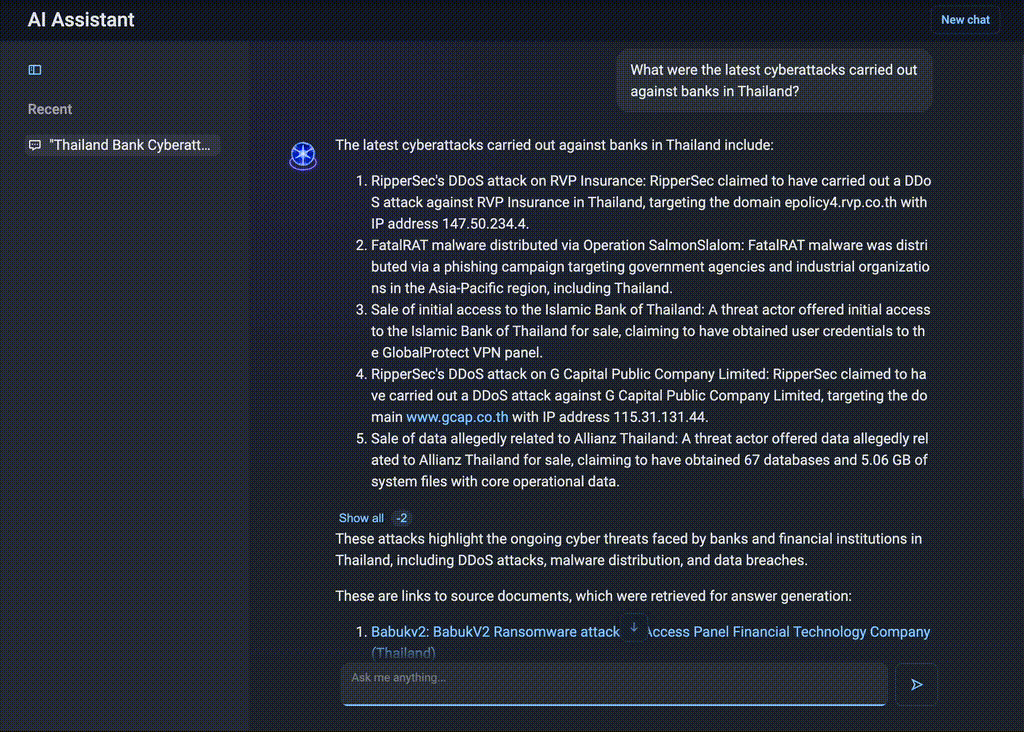
Figure 10. AI Assistant’s insights on attacks targeting the Thai banking sector
Even if the bank itself was not attacked recently, the team would need intelligence relating to common attack techniques, exploited vulnerabilities, and active threat groups operating in the financial sector. By understanding the tactics, techniques, and procedures used against other financial institutions in the region, the team can assess whether their own infrastructure is vulnerable to similar threats. This includes identifying gaps in defenses, ensuring protection against the most prevalent attack types, and strengthening monitoring efforts in areas that could be initial entry points for an attack.
Would you like to learn more about Group-IB AI Assistant?
Conclusion
Our AI Assistant doesn’t replace human expertise but enhances it. Although human oversight remains critical, AI Assistant significantly speeds up threat analysis, streamlines workflows, and improves efficiency. What’s more, it’s free for our Threat Intelligence customers because we believe every organization should have access to efficient, AI-driven security tools. By leveraging an open-source model, we eliminate costly licensing fees, which helps to avoid the expenses proprietary models usually impose.
AI is already embedded across Group-IB products, and we are continuously refining its application. AI Assistant is currently available in beta, giving all Group-IB Threat Intelligence customers early access to its powerful capabilities. In the near future, it will be integrated into even more products, scaling effortlessly without affecting performance or cost.
In cybersecurity, AI isn’t just a trend — it’s an operational necessity. Group-IB AI Assistant bridges the gap between experience levels, making high-quality threat intelligence accessible to junior analysts while dramatically improving efficiency for seasoned professionals at every stage of their work, whenever they need cyber intelligence. By handling routine tasks and providing rapid initial assessments, it turns hours of work into seconds, addresses the cybersecurity talent shortage, and synthesizes vast amounts of threat data, enabling quicker and more informed decisions.


































