Introduction
Let’s revisit the Qilin ransomware group, which recently drew considerable attention due to an attack on the healthcare sector. The highest ransom demand they issued was $50 million during their assault on Synnovis, a pathology services provider. This attack had profound impacts on several key NHS hospitals in London.
First identified in July 2022, Qilin has rapidly gained notoriety by launching its Ransomware-as-a-Service (RaaS) operations on underground forums as of February 2023. Originally evolving from the Agenda ransomware, which was developed in the Go programming language, Qilin has since been redeveloped using Rust, reflecting a shift towards more robust and efficient malware construction techniques.
Qilin, also known as Agenda Ransomware, has been particularly active and successful in its operations, having compromised over 150 organizations across 25 countries and spanning a diverse array of industries. Our previous research has shed light on various aspects of this group, from the intricacies of Qilin’s admin panel to the network of partners that facilitate their operations. For those interested in a deeper understanding of these elements, we’ve provided insights into Qilin’s administrative strategies here and their collaborative tactics here.
In this blog, we aim to unpack the sophisticated techniques and procedures employed by Qilin, insights we’ve gathered through meticulous efforts by our Threat Intelligence and Digital Forensics and Incident Response (DFIR) teams in recent incident responses.
This analysis will be particularly insightful for SOC analysts, DFIR specialists, Threat Intelligence experts, and threat hunters, providing you with the necessary knowledge to understand and possibly mitigate the threats posed by this formidable ransomware operator.
Initial Access
T1133 External Remote Services
Threat actor exploits well-known vulnerabilities in Fortinet devices. In some cases, organizations use firewall clusters running on different software versions; sometimes, one of these versions is vulnerable.
The threat actor may also move laterally from a FortiGate Firewall, via its SSL VPN service, to the Failover server.
Additionally, there are indications of brute force attempts targeting VPN devices prior to the incident. However, because the attackers systematically clear the logs, it is difficult to definitively determine the success of these attempts.
T1190 Exploit Public-Facing Application
Another tactic involves leveraging the CVE-2023-27532 vulnerability found in internet-facing Veeam Backup & Replication software. Successfully exploiting this vulnerability enables attackers to access encrypted credentials from the configuration database.
Execution
T1204.002 – User Execution: Malicious File
A threat actor deploys a copy of the ransomware into the folder C:\temp, naming it w.exe—a common practice. Execution of the ransomware necessitates specifying a password as an argument. This password, when hashed using SHA-256, must match the hash sum outlined in the ransomware’s configuration data. Additionally, other optional arguments can be included to activate various features.
Privilege Escalation
T1078.002 Valid Accounts: Domain Accounts
There are two proofs of concept available on GitHub by Horizon3 and sfewer-r7 that demonstrate how to exploit CVE-2023-27532 and access the backup server. However, there is no confirmed evidence that Qilin operators have utilized these exploits:
T1134 Access Token Manipulation
Upon execution, the ransomware seeks to elevate its privileges to the SYSTEM level. It accomplishes this by using an embedded Mimikatz module to steal the user token from a process such as lsass.exe, winlogon.exe, or wininit.exe. The ransomware then uses this stolen token to launch a new process under the security context of the acquired token.
Then, it also resolves symbolic links from a remote object to remote and local objects:
- fsutil behavior set SymlinkEvaluation R2R:1
- fsutil behaviour set SymlinkEvaluation R2L:1
Defense Evasion
T1070 Indicator Removal
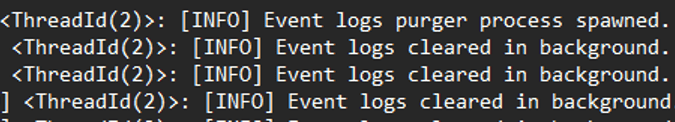
The ransomware first deletes all system logs before initiating data encryption. After completing the encryption, it removed all system events, erasing any traces of the malicious activities conducted by the threat actor on the host, including the clearing of Windows PowerShell and Windows System logs.
To delete evidence of malicious activity, upon completing all tasks, it periodically cleans the Windows Event Logs in a separate thread using the following command:
"powershell" $logs = Get-WinEvent -ListLog * | Where-Object {$_.RecordCount} | Select-Object -ExpandProperty LogName ; ForEach ( $l in $logs | Sort | Get-Unique ) {[System.Diagnostics.Eventing.Reader.EventLogSession]::GlobalSession.ClearLog($l)}T1562.001 Impair Defenses: Disable or Modify Tools
The threat actor can specify a list of substrings and regular expressions for process names to be terminated, as well as for the names of services to be stopped or denied, within the Qilin configuration file.
| Parameter | Description |
| process_black_list | List of substrings of the names of the processes to be terminated |
| win_services_black_list | List of substrings and regular expressions of names of stopped and denied services |
Discovery
T1087.002 Account Discovery: Domain Account
The ransomware employs a brief PowerShell script to compile a list of hosts connected to the domain.
"powershell" -Command "Import-Module ActiveDirectory ; Get-ADComputer -Filter * | Select-Object -ExpandProperty DNSHostName"
If the initial attempt fails, it proceeds to install the RSAT-AD-PowerShell module using another PowerShell script.
"powershell" -Command "ServerManagerCmd.exe -i RSAT-AD-PowerShell ; Install-WindowsFeature RSAT-AD-PowerShell ; Add-WindowsCapability -Online -Name 'RSAT.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0'"
Following the installation, it makes a second attempt to gather the list of connected domain hosts.
Lateral Movement
T1021.001 Remote Services: Remote Desktop Protocol
The adversary exploited CVE-2023-27532 to extract credentials, which were then used to access the backup server via the Remote Desktop Protocol (RDP).
T1021.002 Remote Services: SMB/Windows Admin Shares
The Qilin ransomware is capable of self-propagation across a local network, functioning as a network worm when the –spread command line argument is specified. It achieves this through an embedded version of Sysinternals PsExec (version 2.43) stored within the ransomware’s code.
After deploying a copy of PsExec to the %Temp% directory under a randomly generated name, the ransomware performs a swift reconnaissance of the domain. It then executes PsExec to establish connections with each host identified within the domain, using the specified command.
%Temp%\<PSEXEC_NAME>.exe -accepteula \\<HOST_IP> -c -f -h -d <LOCKER_PATH> <LOCKER_ARGS> --spread-process
If any user account is specified in the configuration data, the PsExec utility is executed explicating the user credentials:
%Temp%\<PSEXEC_NAME>.exe -accepteula \\<HOST_IP> -u <USER_NAME> -p <PASSWORD> -c -f -h -d <LOCKER_PATH> <LOCKER_ARGS> --spread-process
| PSEXEC_NAME | name generated for PsExec |
| HOST_IP | host IP address |
| USER_NAME | the username |
| PASSWORD | the password |
| LOCKER_PATH | the ransomware folder path |
| LOCKER_ARGS | command line arguments set to launch the ransomware |
To be able to spread itself, the ransomware sets the value 65535 of the MaxMpxCt registry parameter to increase the number of outstanding network requests for each client.
Qilin malware also has the capability to carry out self-distribution using VMware vCenter, typically with the command:
–spread-vcenter
Impact
T1490 Inhibit System Recovery
In the backup management console, threat actors carry out the following manual actions:
- Delete tape backups
- Disable scheduled backup jobs
- Delete backup jobs
Malware starts the VSS service and deletes shadow copies of partitions by executing the following commands:
net start vss wmic service where name='vss' call ChangeStartMode Manual vssadmin.exe Delete Shadows /all /quiet net stop vss wmic service where name='vss' call ChangeStartMode Disabled
T1486 Data Encrypted for Impact
During its operation, the ransomware encrypts specific local files as defined in the attacker’s configuration file, along with all data in network shared resources.
The malware begins by encrypting all data on the host and any attached drives, including network shares.
File encryption is performed in multiple streams and the data encryption can be performed using stream algorithms AES-256 CTR or ChaCha20. If there is hardware support for AES (AES-NI), the encryption is performed using AES-256 CTR, otherwise – ChaCha20.
Encryption of AES-256 CTR / ChaCha20 keys and nonce codes is performed using the RSA-4096 public key specified within the configuration data.
The data block with the encrypted key, nonce and encryption parameters is added to the end of the encrypted file.
Files can be encrypted in multiple passes (Multipass mode), and be encrypted three times, using «fast», «per cent» and «normal» encryption modes.
After completing the encryption, the ransomware cleans up free disk space with the command:
cipher /w:”X:\”
where X identifies the disk.
The malware logs details of the execution process, including the status of each encryption:
T1529 System Shutdown/Reboot
The ransomware initiated a reboot of the backup server after encrypting the data, thereby hindering recovery efforts. Additionally, the threat actor rebooted VPN servers.
Malware command line parameters
| Parameter | Description |
| –password <PASS> | Specify a password to run the ransomware. The SHA-256 hash sum of the password must match the hash sum specified in the configuration data |
| –paths <PATHS>… | Encrypt files at specified paths |
| –ips <IPS>… | Encrypt hosts with specified IP addresses |
| –exclude <EXCLUDE>… | Exclude specified hosts when self-propagating |
| –timer <SECS> | Set the waiting time in seconds before encryption and other actions are performed |
| –no-sandbox | Do not detect running in a virtual machine |
| –no-escalate | Do not implement privilege escalation |
| –impersonate <ACCOUNT> | Use the specified account for impersonation |
| –safe | Reboot in safe mode to encrypt files in safe mode |
| –no-local | Do not encrypt files on the local system |
| –no-domain | Do not encrypt files on domain hosts |
| –no-network | Do not encrypt files on network shares |
| –no-ef | Do not use the file extension filter |
| –no-ff | Do not use a filename filter |
| –no-df | Do not use the directory name filter |
| –no-proc | Do not terminate processes |
| –no-services | Do not stop system services |
| –no-vm | Do not stop virtual machines |
| –kill-cluster | Stop clusters using a script PowerShell:
“powershell” -Command “Stop-Cluster -Force” |
| –no-extension | Do not add an extension to encrypted files |
| –no-wallpaper | Do not set the desktop wallpaper |
| –no-note | Do not create text files with ransom demands |
| –no-delete | Do not delete folders |
| –no-destruct | Do not delete yourself when you are finished |
| –no-zero | Do not perform free space cleanup of host disks using the command:
cipher /w:”X:\” |
| –print-image | Print the image |
| –print-delay | Delay before printing |
| –force | |
| –debug | Enable debugging mode |
| –spread | Perform self-distribution. The PsExec utility version 2.43 from Sysinternals is used for self-distribution |
| –spread-vcenter | Carry out self-distribution with the use of vCenter |
| –escalated | Tell the program that it is running with elevated privileges |
| –parent-sid <SID> | Pass the SID of the user of the parent process to the program |
| –spread-process | To indicate to the program that it is running in self-distribution mode |
Conclusion
In conclusion, the Qilin ransomware represents a formidable threat in the cybersecurity landscape, demonstrating flexibility in its deployment through Ransomware-as-a-Service (RaaS) partnerships. The techniques employed by different operators can vary significantly, making it a continually evolving challenge for security defenses. We are committed to closely monitoring the development of this malware and the emerging tactics it employs to circumvent security measures. For comprehensive updates and in-depth analysis, information on Qilin malware and its RaaS ecosystem is continually updated within the Group-IB Threat Intelligence platform.
Supercharge cybersecurity with Group-IB Threat Intelligence platform
Maximize known and unlock hidden values of cyber threat intelligence