Introduction
Since May 2024, Group-IB analysts have detected a number of fake mobile applications disguised as trading platforms in various regions. All of these applications were developed for the Android platform using a single cross-platform development framework. One of the applications discovered was distributed through the official Google Play store, while a similar application targeting iOS devices was found shortly after. Unlike conventional mobile trojans such as the GoldPickaxe that Group-IB’s analysts first discovered in February 2024, these suspicious applications lacked the typical malicious features. Instead, cybercriminals created a facade of a legitimate trading platform to defraud its victims.
While these types of schemes, now widely known as pig butchering, are not new, the strategies and tactics used by cybercriminals continue to evolve.
Pig Butchering is a term used to describe a sophisticated and manipulative scam in which cybercriminals lure victims into fraudulent investment schemes, typically involving cryptocurrency or other financial instruments. The name of the scam refers to the practice of fattening a pig before slaughter, and symbolises how cybercriminals gain the victim’s trust and investment before making their move.
These scams often start with social engineering tactics, such as meeting someone on a dating app, social media platform, or through a cold call. Cybercriminals would typically spend weeks, or even months gaining the victim’s trust, often posing as a trading or investment advisor. Once the victim is sufficiently “fattened up”—meaning they’ve invested significant funds—the cybercriminals pull the rug out from under them, leaving them with nothing.
The scam often ends with the victim butchered of their initial investment, and in some cases also being pressured to pay additional fees or taxes, which are simply further attempts to extract money from them. This strategy is well explained from victims on specialised forums.
While the methodologies of pig butchering have been widely documented, Group-IB’s recent research has detected victims in the Asia-Pacific, European, and Middle East and Africa regions, the true extent of which could be much wider. In this research, we focus on the Pig Butchering campaign which targets Apple iOS users, including the Group-IB Fraud Matrix with categorised characteristics and tactics, as well as relevant Indicators of Compromise (IOCs).
Key findings
- Cybercriminals use fake trading applications to lure victims with the promise of financial gain.
- Individuals are lured by cybercriminals into funding bogus trading accounts, ultimately stealing their money.
- Cybercriminals initiate conversations with potential victims through dating applications, using social engineering tactics to gain their trust.
- Fraudulent applications have been discovered in Apple App Store and Google Play store.
- The fraudulent applications are built using the UniApp Framework.
- Various applications were discovered and have been classified under a single malware family dubbed by Group-IB as UniShadowTrade.
- Application provides multi-language support for English, Portuguese, Chinese and Hindi.
- Group-IB’s Threat Intelligence and Fraud Protection analysts have detected victims in the Asia-Pacific, European, Middle East and Africa regions, indicating the global reach of this scam.
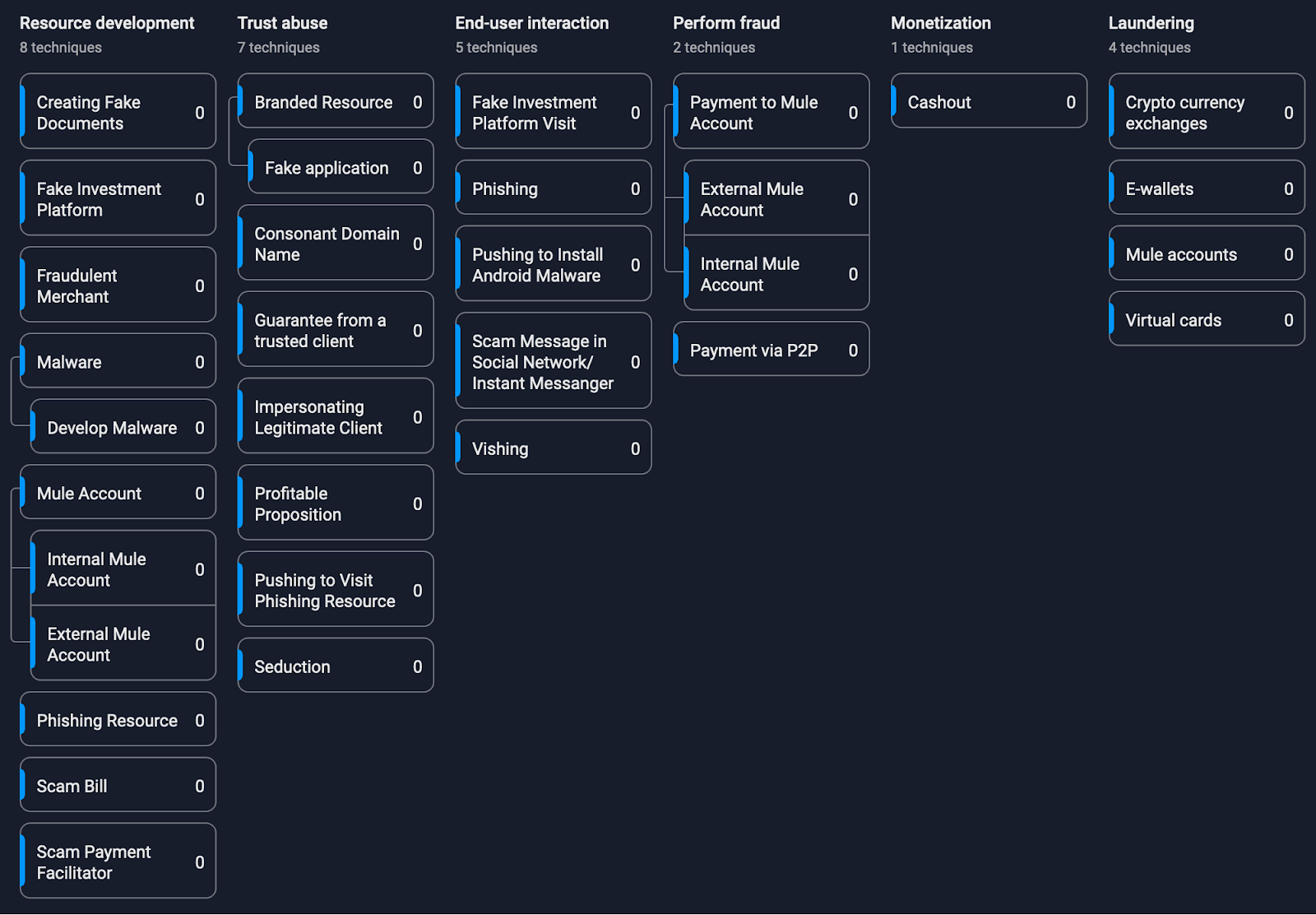
Infection chain
During the investigation, we were unable to determine the exact methods cybercriminals used to target potential victims. However, it is likely they relied on social engineering tactics via dating apps or social networks, as previously suggested.
We uncovered two distribution methods: initially, the cybercriminals successfully uploaded the fraudulent iOS application to the official Apple Store, exploiting the trust users have in the Apple ecosystem. This trust likely caused victims to let their guard down, making them more susceptible to the scam.

Figure 1. Illustration of the fraud application in the Apple App Store
The fraudulent app remained in the Apple App Store for several weeks before being removed. After its removal, the cybercriminals shifted to distributing the app through phishing websites, offering downloads for both Android and iOS. For iOS users, pressing the download button triggers the download of a .plist file, prompting iOS to ask for permission to install the application. However, after the download is complete, the application cannot be launched immediately. The victim is then instructed by the cybercriminals to manually trust the Enterprise developer profile. Once this step is completed, the fraudulent application becomes operational.
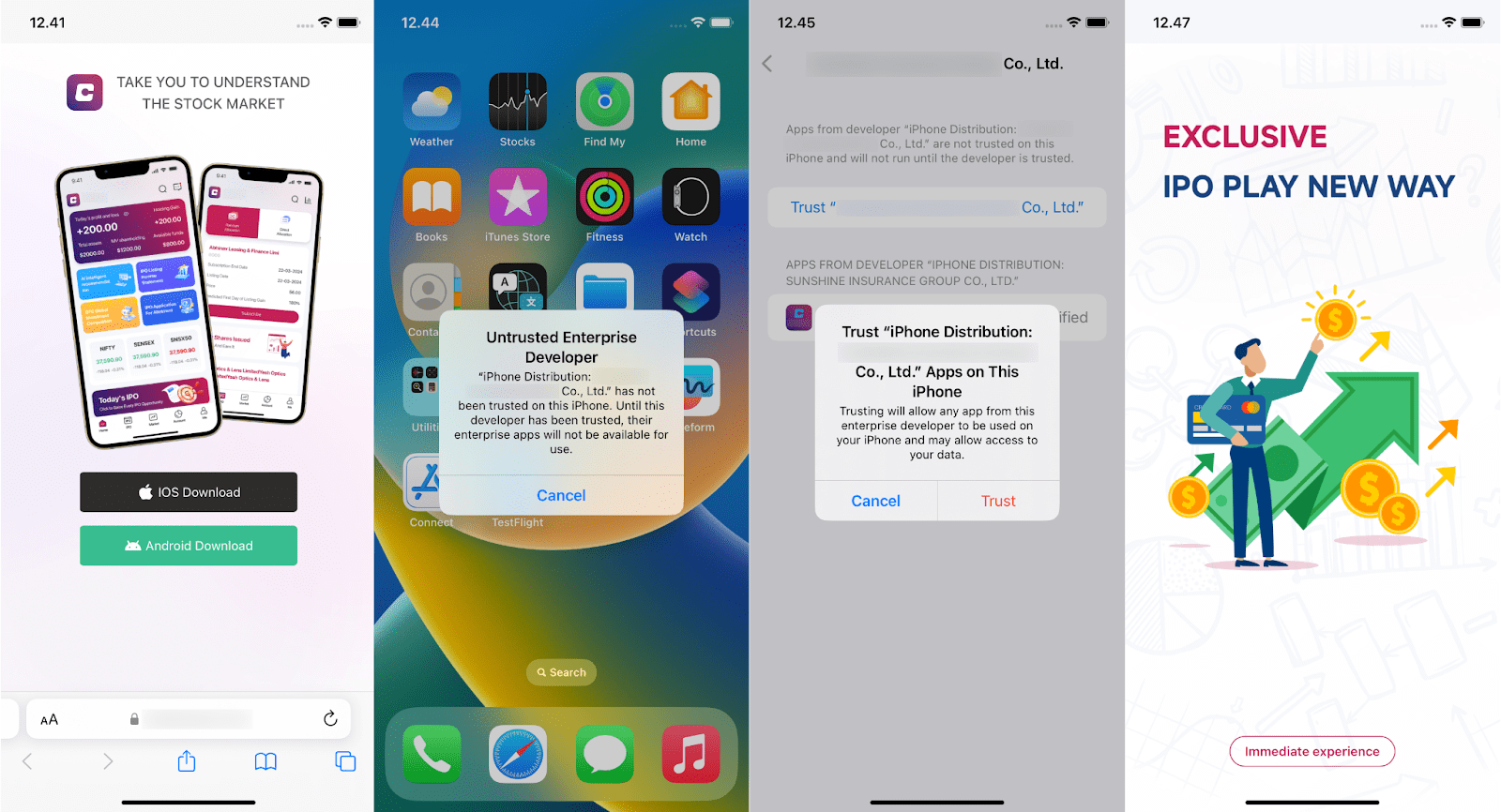
Figure 2. Example of a visit to a phishing website, the installation process and the opening of a fraudulent application
The application’s description claims that it is designed for algebraic mathematical formulas and 3D graphics volume area calculations. However, this is a faсade. Once the victim launches the app, they are met with a login page. To register within the application, the victim must enter an invitation code. This requirement suggests that the cybercriminals are not conducting a mass campaign, but are instead targeting specific individuals.

Figure 3. Example of the fraud application
Once a user registers with the fraudulent application, they are tricked into completing several steps. First, they are asked to upload identification documents, such as an ID card or passport. Next, the user is asked to provide personal information, followed by job-related details. After agreeing to the terms and conditions, and disclosures, they are instructed to fund their account. Once the deposit has been made, the cybercriminals take over and send further instructions, ultimately resulting in the theft of the victim’s funds.

Figure 4. The scheme is an illustration of the steps in a fraud scheme.
Technical details
There are minimal differences between the iOS and Android versions of the application, as the core functionality is web-based and delivered through a URL. The web application is built on the UniApp framework, which allows developers to create cross-platform applications using Vue.js. UniApp enables the development of applications that can run seamlessly on Android, iOS, and web browsers with a single codebase. By combining native components and web technologies, developers can write code once and deploy it across multiple platforms.
As mentioned previously, the application does not include functionality of classic mobile Trojan; its primary function is to open a Web View activity. According to the requirements, the application requests access to the photo gallery.
Before displaying the login page, the iOS application performs several checks. It checks the device model, as the application is only designed to run on mobile phones. First, it checks the current date and time. If the date is earlier than 22 July 2024, 00:00:00, the application launches a fake activity with formulas and graphics. We assume that this condition must bypass Apple’s checks before being published to the store. As we can see, this simple trick allows cybercriminals to upload their fraudulent application to the Apple Store.

Figure 5. Example of fake activity in fraud application
If all checks are successful, the application retrieves the address of the web application. The configuration is embedded at the end of the HTML page, enclosed in ## symbols. The configuration parameters are separated by commas. The second parameter specifies the address where the web application, including the login pages, is located. A sample configuration is shown below:

Figure 6. Example of configuration for fraud application
A point to highlight is that TermsFeed is an online service that provides customizable legal agreements like privacy policies, terms of service, and disclaimers for websites, mobile apps, and online businesses.
The string is parsed by the application, and stored in the local storage as a dictionary. Most of the parameters are responsible for how the web application is displayed on the phone. The parameters “2”, “3” “4” and “5” are applied in case a fraudulent web application will be launched inside the application.
|
Key |
Example |
Descriptions |
| 0 | 1 | Responsible for where the fraudulent web application will be opened. It will open as a web view within the application if the value is 1. If the value is set to 2, the web application will open in the web browser. |
| 1 | hXXps://www.REDACTED[.]com/h5 | The location of the web application to be displayed. |
| 2 | 1 | Response to the style of the status bar. If the value is greater than or equal to 1, UIStatusBarStyleDarkContent is used, otherwise UIStatusBarStyleLightContent is applied. |
| 3 | 1 | If the value is 1, overlap web-application under status bar. |
| 4 | 1 | If the value is 1, ignore the safe area where content can be placed without being obstructed by system elements such as the notch or home indicator. |
| 5 | 255,255,255 | Background colour of status bar (default: 255,255,255) |
| 6 | line[.]me,t[.]me | Open one of the messengers most likely to interact with victims |
The first discovered application, distributed through the Apple App Store, functions as a downloader, merely retrieving and displaying a web-app URL. In contrast, the second application, downloaded from phishing websites, already contains the web-app within its assets. We believe this approach was deliberate, since the first app was available in the official store, and the cybercriminals likely sought to minimise the risk of detection. As previously noted, the app posed as a tool for mathematical formulas, and including personal trading accounts within an iOS app would have raised immediate suspicion.
The web application is built using JavaScript and provides the full functionality of a trading account. Hints available in multiple languages English, Portuguese, Chinese and Hindi. It includes features such as account settings, forms for uploading bank cards and ID documents, transaction history, profit and loss, an IPO section, a list of available stocks, and more. When the web-app is opened within the mobile application, communication with the server is established via WebSocket, while in a web browser, the connection is secured through HTTPS.
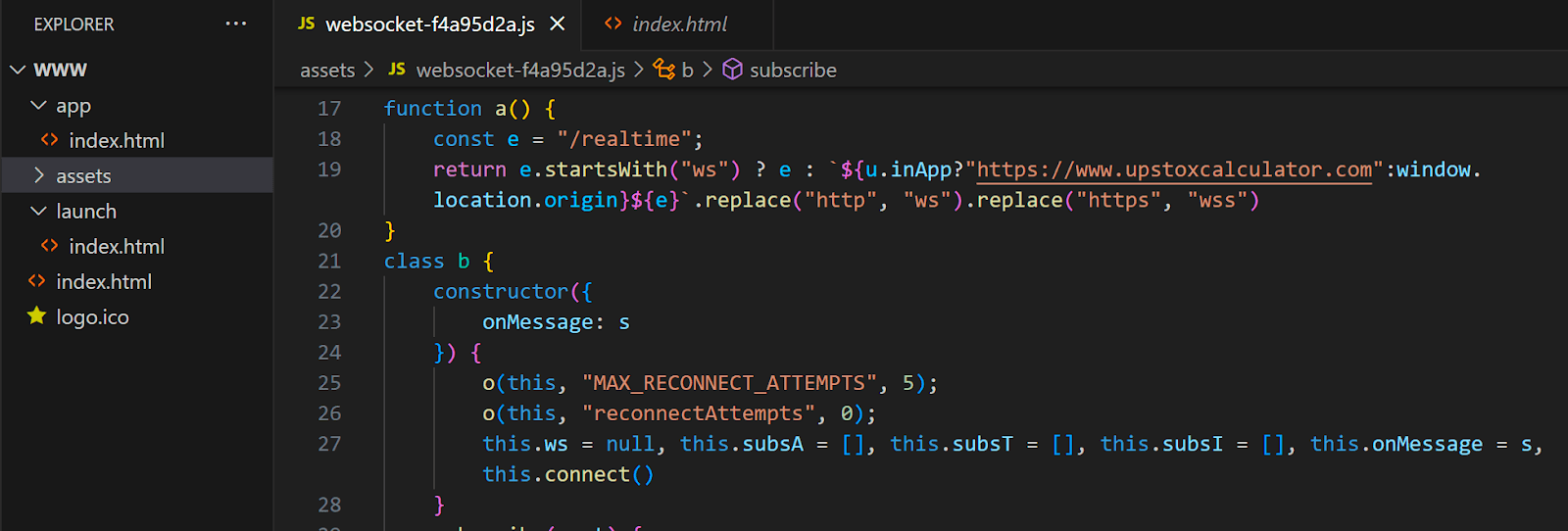
Figure 7. Example of a piece of JS code in the fraud application
To complete the scam, the victim is asked to fund their account. Once the deposit is made, the cybercriminals instruct the victim on which positions to buy. After a few seemingly successful trades, the victim is persuaded to invest more and more money. The account balance appears to grow rapidly. However, when the victim attempts to withdraw funds, they are unable to do so.
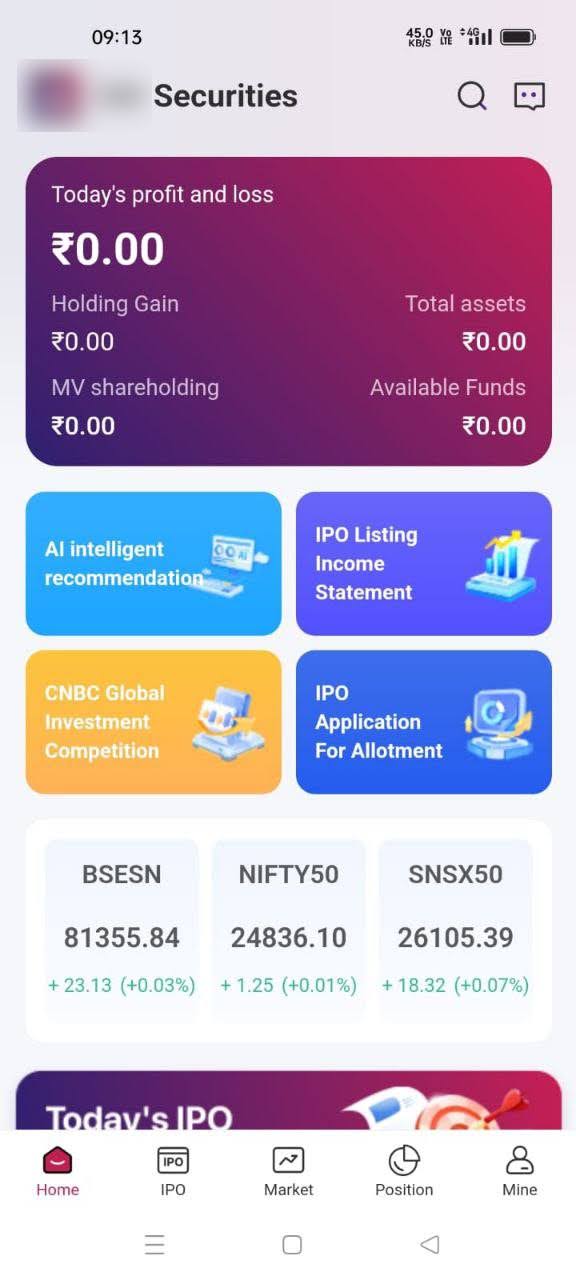
Figure 8. Example of fake trading terminal displayed to victim
More to Unfold
As mentioned above, our investigation began with an analysis of Android applications at the request of our client. The client reported that a user had been tricked into installing the application as part of a stock investment scam. During our research, we uncovered a list of similar fraudulent applications, one of which was available on the Google Play Store. These apps were designed to display stock-related news and articles, giving them a false sense of legitimacy. At the moment, the fraudulent application was removed from the store.
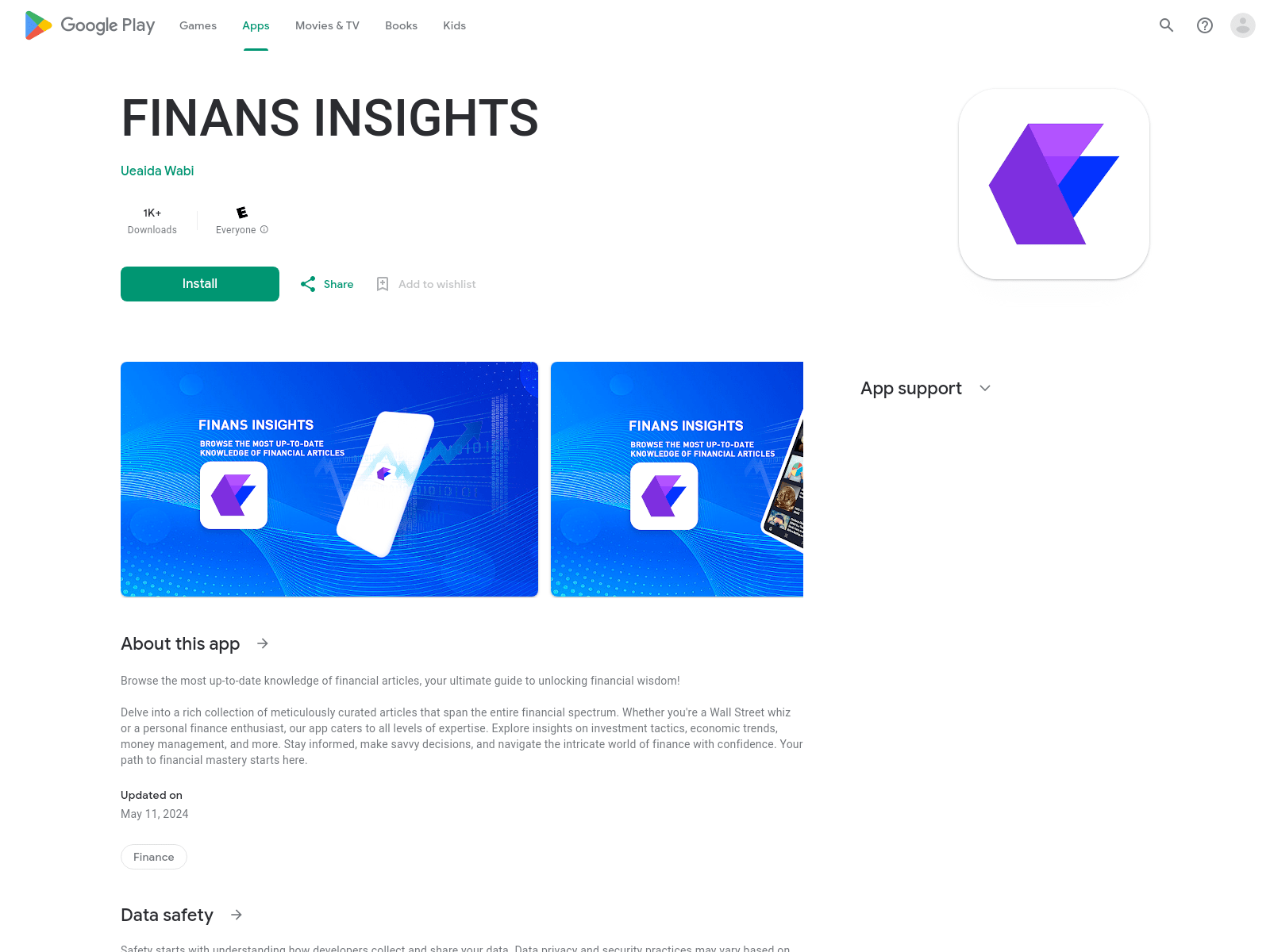
Figure 9. Illustration of the fraud application in the Google Play
All detected Android packages shared the same package names: com.finans.trader or com.finans.insights. These applications were built using the UniApp framework, with the core functionality implemented as JavaScript code. The applications are capable of mimicking various crypto and trading platforms. Below is a list of possible names they may impersonate, that was detected in application:
| FINANS INSIGHTS
AUR PRO biconomynft wxjtss Xzdl Deversi Fi Holloway Friendly stock GoldEX BLACK Fx6 Befongz Clueeio GOFX ZurichFX Limited Triltex AETO FX Aegis f-stock CHGS FX Ctrl FX Cortex Collins Dco Market LGFX Global Meifu Financial Mxfx Global |
Dongcai
Deus Decode Encounter Etofx Aipu Bestow Blue Whale COMEX MARKET Foxiv FREEDOM Fuex Funda Forex Future FX Corp FocusEX FXMX PRO Gampara GCCKC GDW GLFXM Goaxfx Brokers Gula Capital Ifxsix IGLON Novartis |
OTOFPR
Reputation Capital SBITRADEFX Sky Exchange SSJTCF Star Funds SUNDELL Superb Trading Taihe Limited TASSMAN Nax currency Transa Turbine trade Unisnow v5max WOB Markets WXJTSS XZDL Global Hengtuo Finance Heying Holloway Friendly GOFX-Rro Hota Coinbase Hota Crypto IMPERACE GOEX |
Yub Group Ltd
Bit exchange HYHLB Group Genting Maple-Six Capital GOFX-Pro7 Golden Peak CTRL INVESTMENTS COMEX GROUP Yuanxin lgfx Test Trade VisionTrade Fire Phoenix hengtuo ZZIT robin fair stock st6 Nax XTB Gms Kyros |
The samples discovered were designed to display a fraudulent trading application hosted on the domain api.fxbrokers[.]cc. This domain is part of a larger fraudulent infrastructure with many related domains registered under similar names, impersonating brokers and financial organisations. We would like to draw particular attention to gold-blockhain[.]cc, another domain associated with this scheme.
Next to this domain we found an Android package called com.ubsarov.ubsarovfx. Earlier in the article, we shared a message from one of the victims mentioning a fraudulent application called Ubsarov FX6. Although there was no direct evidence linking these cases, we believe that the discovered com.ubsarov.ubsarovfx application and others noted in this article is part of the same larger campaign tied to UOBE FX.
The UOBE FX fraud case involves a fake brokerage that operates under false pretences and deceptive tactics, primarily targeting victims through dating apps and other social engineering methods.
Group-IB Fraud Protection
Group-IB Fraud Protection telemetry reveals that installations have also been detected in the European regions, indicating that this threat is not limited to a specific region.
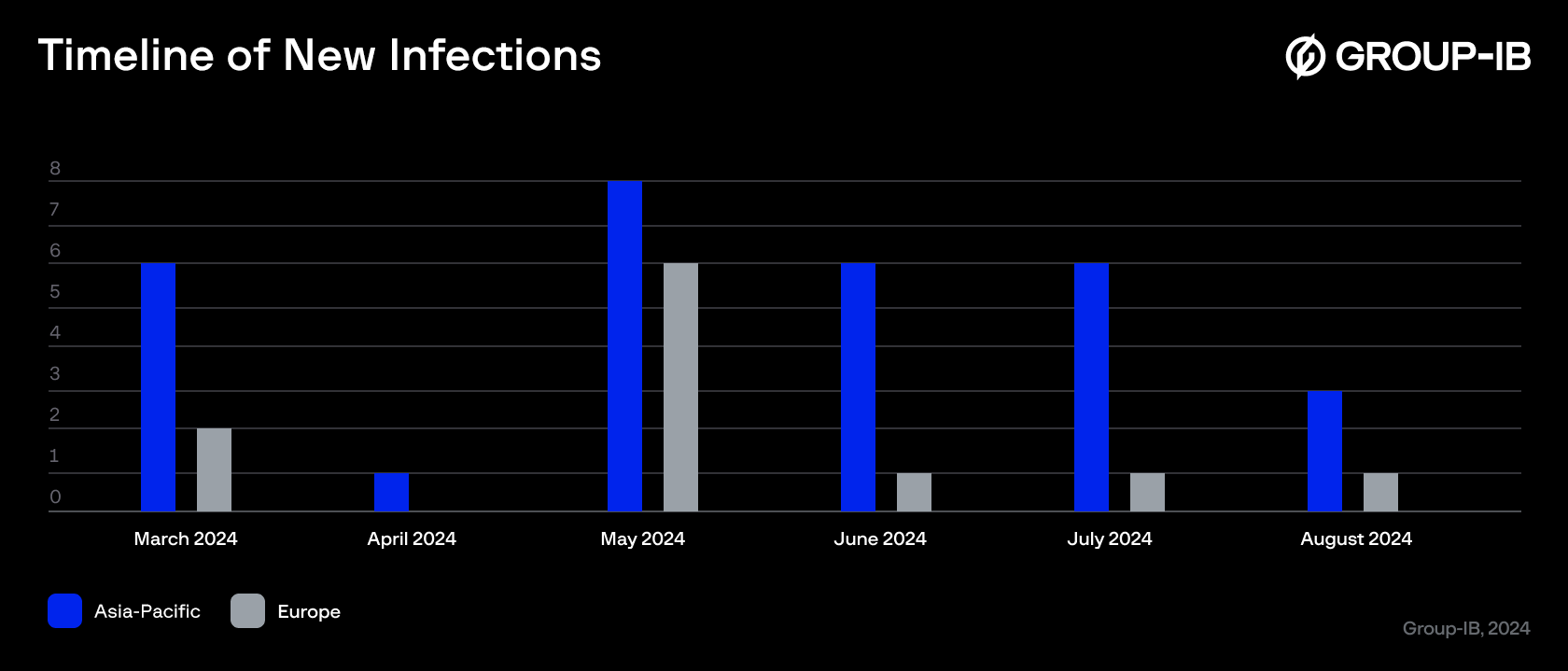
Figure 11. New infections timeline.
Source: Group-IB Fraud Protection
Group-IB Fraud Matrix
Conclusion
In summary, cybercriminals continue to use trusted platforms such as the Apple Store or Google Play to distribute malware disguised as legitimate applications, exploiting users’ trust in secure ecosystems. Victims are lured in with the promise of easy financial gains, only to find that they are unable to withdraw funds after making significant investments. The use of web-based applications further conceals the malicious activity and makes detection more difficult. This highlights the importance of vigilance and end-user education, even when dealing with seemingly trustworthy apps, and reinforces the need for continued review of app store submissions to prevent such scams from reaching unsuspecting victims.
Recommendations
For Financial Organizations
- Implement a user session monitoring system, such as Group-IB’s Fraud Protection, to detect the presence of malware and block suspicious sessions before any personal information is entered.
- Educate your customers about the dangers of mobile malware, including how to recognize fake websites, avoid malicious apps, and protect their passwords and personal data.
- Utilize a Digital Risk Protection platform to identify and mitigate the unauthorized use of your logos, trademarks, content, and design elements across the digital landscape.
- Ensuring a secure organization demands continuous vigilance. Employing a proprietary solution like Group-IB’s Threat Intelligence can bolster security by providing teams with the latest insights into emerging threats.
For End Users
- Be careful when opening links sent to your mobile device.
- Be wary of unsolicited messages from strangers on social media, dating apps or other platforms. Scammers often initiate contact with friendly conversations that gradually turn into investment opportunities.
- It’s important to conduct a comprehensive background check on any investment platform or job opportunity before committing to it. To make sure you’re dealing with a trustworthy entity, read reviews, check their website and social media presence, and verify their legitimacy.
- Only install applications from official websites. But if you’re asked to install an application from an official store, don’t let your guard down. Always check the publisher, application rating and user comments to make sure it’s legitimate.
- Don’t give out sensitive personal or financial information to anyone you meet online, especially if you haven’t met them in person.
- Stay up to date with the latest scam tactics. Learn how to spot potential scams
- Remember, if it seems too good to be true, it probably is.
Learn more about Group-IB's Fraud Protection Solution
Eliminate fraud across all digital channels in real time
IOCs
Files:
- e74392a807f0ad180c6a80aafd198b7ef4ad0581
- 0e2f85f1c7705e795ed9c2491ce628fac411fcfc
- 0179e333287fe6d87a76f4b4d90602f54e833379
- cfae03202181664723a2133fda7e74079b0e5f0e
- 34f93e7e4d74852c647978e3195a1de79eaba3ff
- 8b2fdbc0050b9840c404a49373d802586acc82ea
URLs:
- hXXps://www.upstoxcalculator[.]com
- hXXps://www.yupstocks[.]com/h5/#/login
- hXXps://a.gold-blockchain[.]cc/app/home/getH5