Introduction
PDFs are ubiquitous in today’s digital world. We trust them for important documents, contracts, and records. But what if the seemingly official PDF wasn’t what it appeared to be? The reality is, PDF files can be manipulated, and forgery is more common than you might think.
Key discoveries in the blog
- Tampering of Digitally Signed PDF
- Discovering Annotations
- Metadata can be Misleading
- Analysis Limitations
Who may find this blog interesting:
- Cybersecurity analysts and corporate security teams
- Cyber investigators
- Digital Forensics Specialists
From Valid to Void: Signs Your PDF Was Altered After Signing
A digital signature provides three key assurances to a PDF document: integrity, authorship, and authenticity. Tools such as Adobe Acrobat Pro allow users to inspect the details of digital signatures and assess whether a document has been modified since it was signed.
When a digitally signed PDF is altered – for example, by opening it in Firefox and saving a new copy – the original signature becomes invalidated. In such cases, validating the signature using Adobe Acrobat will indicate that “there have been subsequent changes to the document.” Figure 1 below illustrates a document signed using DocuSign, with a warning that changes were made after the signature was applied.
Depending on the nature of the edits, the digital signature’s annotation section may contain additional details, such as what types of changes were introduced or which elements were modified.
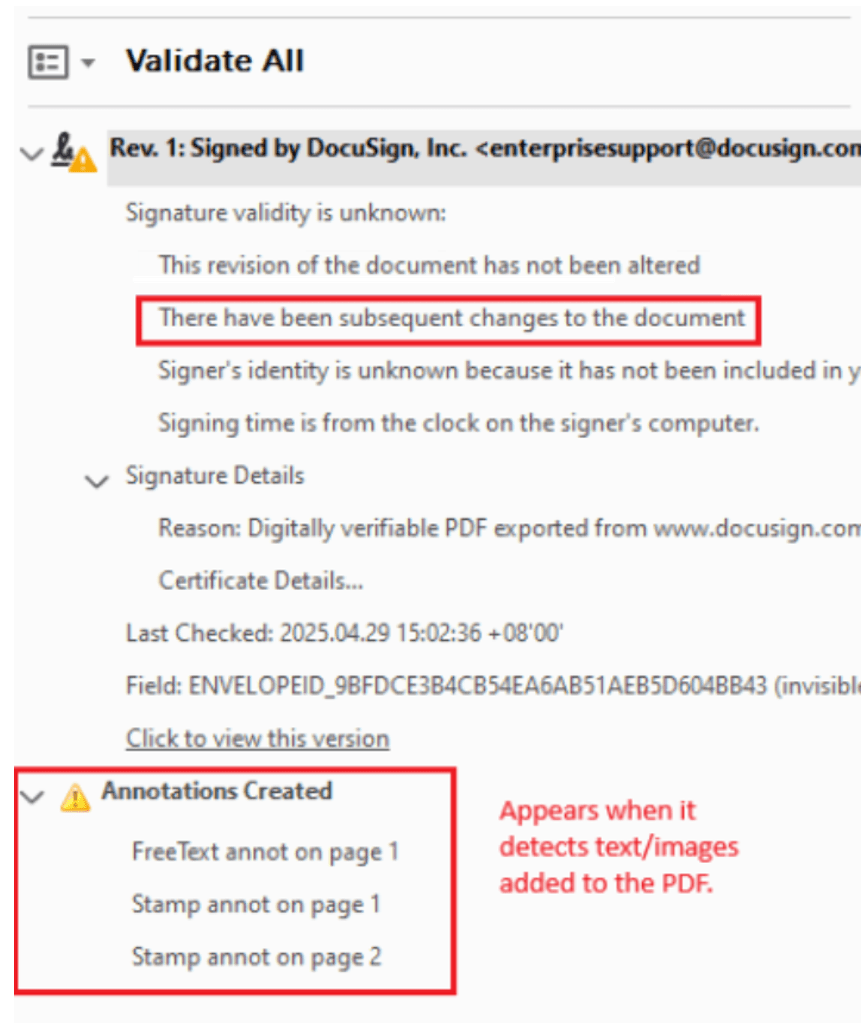
Figure 1. The structure of signature after modifications to the PDF document.
In many cases, a previous version of the document – prior to the modification – can still be accessed. Adobe Acrobat provides a “Click to view this version” link within the digital signature panel, which allows users to view the document as it existed at the time of signing. In the example shown in the following figure, the signature confirms that “The document has not been modified since this signature was applied,” indicating the document integrity of that earlier version.
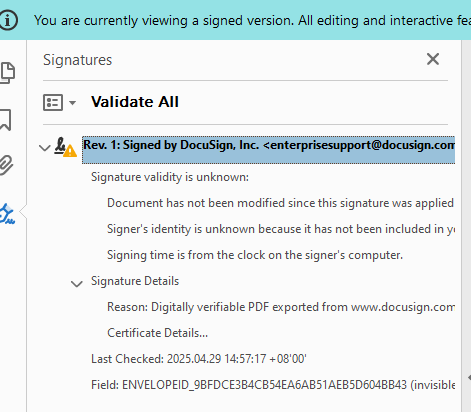
Figure 2. The structure of signature from the older (previous) version of the PDF document.
Because the earlier PDF displayed no modifications, whereas the version in Figure 1 reveals post-signature edits, the evidence indicates that the document was tampered with after signing.
Obscure Annotations
PDF files are composed of various objects, such as text and images. Using PDF editing tools, images can be inserted as overlays on top of existing content. To extract these objects, tools like PDF-Processing and Adobe Acrobat Pro are commonly used.
The PDF-Processing tool, in particular, is designed to recover previous versions of a PDF and automatically extract image objects (stamp annotations) from each version using the command: “./pdfprocessing.sh -f “/path/to/file.pdf” -p true”. This tool is especially useful when the PDF cannot be opened in editing mode via Adobe Acrobat or when multiple historical versions need to be analyzed for comparison.
In the example below, PDF-Processing successfully recovered three prior versions of the PDF in addition to the current one. The analysis revealed that two images present in the latest version were not found in the earlier versions, indicating they were added more recently.
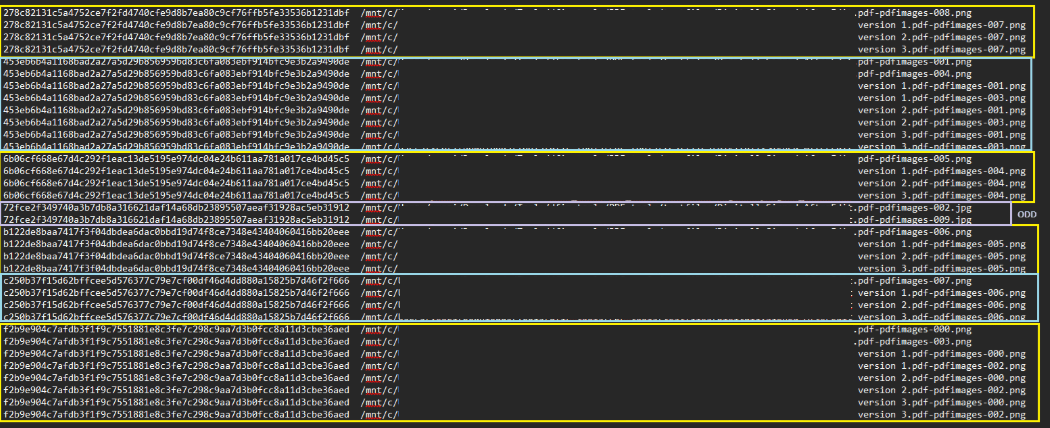
Figure 3. A screenshot indicating that images were previously included within the PDF document, and those subsequently added (within the purple box).
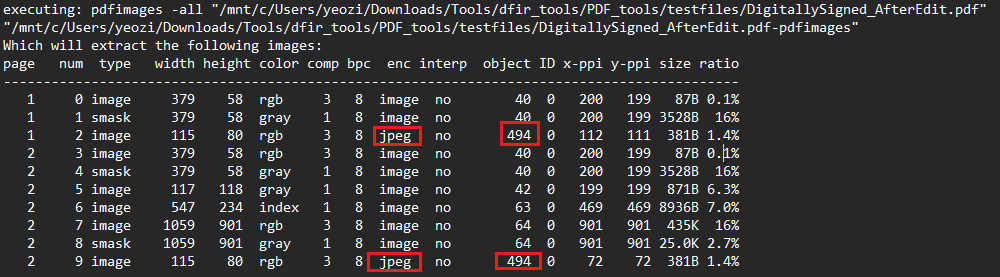
Figure 4. A screenshot with details of the PDF document where additional images were identified.
The pdfimages tool provides the page numbers where each extracted image is located. In this case, reviewing the extracted images revealed two white rectangles, likely used to obscure content on pages 1 and 2 of the PDF.

Figure 5. The two extra images identified on the PDF document.
If the PDF is unsigned, it can be opened in Adobe Acrobat Pro editing mode, allowing the objects on each page to be examined individually. In this case, one of the white rectangles appeared to have another object positioned beneath it. By moving objects within the editable view, it is possible to reveal hidden content that may have been obscured by overlays.
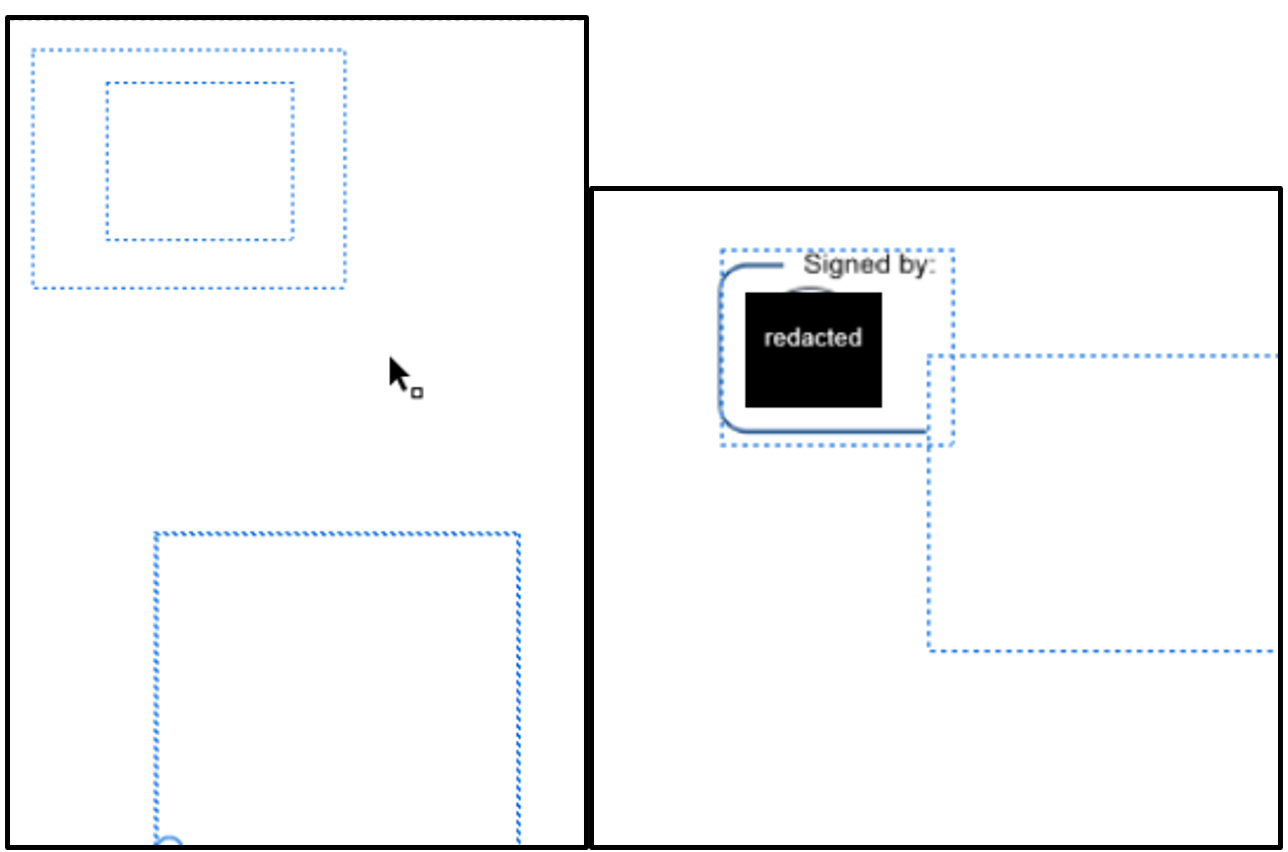
Figure 6. Stamp annotations viewed in editing mode.
When content is obscured using a white Ink annotation (Scribble) and then overwritten with a Text annotation, both elements are treated as separate objects within the PDF. In Adobe Acrobat DC, switching to editing mode allows these objects to be individually selected and moved. Doing so can reveal the underlying content that was originally concealed by the annotations.

Figure 7. Ink and text annotations viewed in the editing mode of Adobe Acrobat DC.
Adding text using a PDF editor may also introduce inconsistencies in font style, size, or spacing, which can serve as indicators of tampering. However, discrepancies can only be identified if a previous version of the PDF is available for comparison. A noticeable difference in fonts between the original and modified content may suggest that additional text was later inserted into the document.
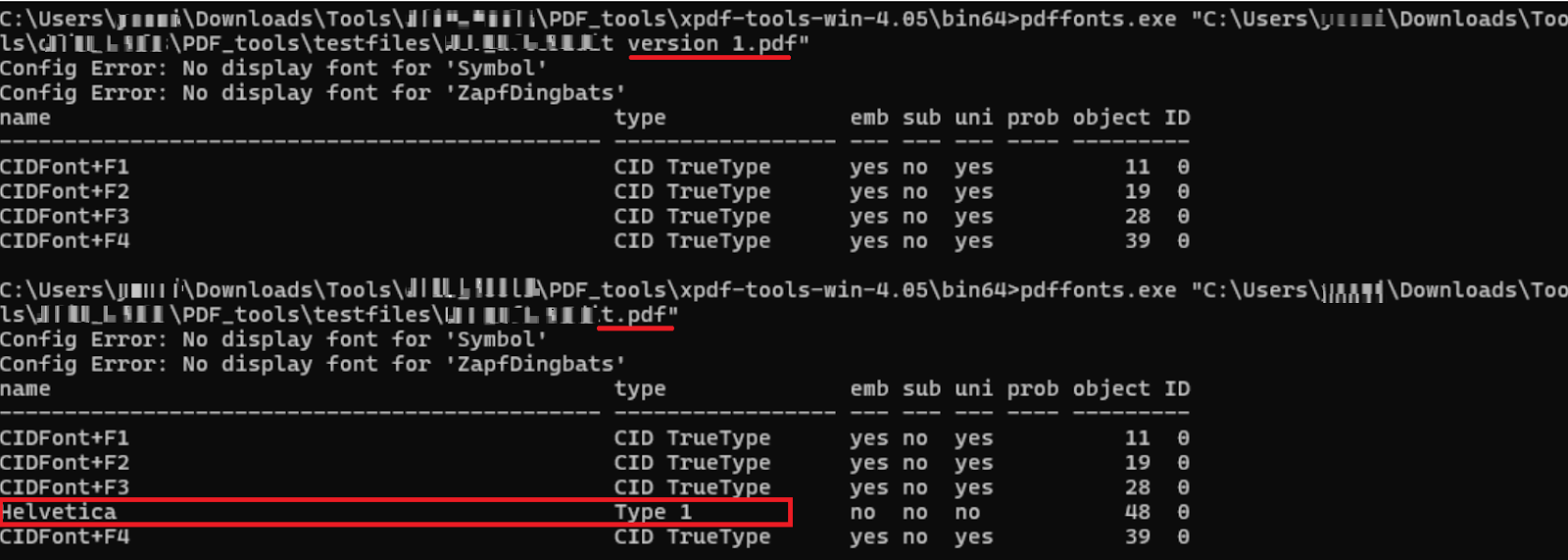
Figure 8. Comparison of fonts used between two versions of the PDF document.
Metadata: A Misleading Clue?
Metadata alone is often not a reliable indicator of whether a PDF has been edited or tampered with. For instance, when a user simply downloads a PDF, the file’s modification timestamp is automatically updated to reflect the time of download – regardless of whether any changes were made. While actual edits will also alter the modification time, this overlap makes the timestamp an unreliable piece of evidence on its own.
Additionally, editing a PDF using common tools does not always alter the creator or producer fields in the metadata. In some cases, it has been observed that even after modifications are made using different PDF editors, the original metadata values remain unchanged.
If the author or producer fields do change, it might suggest possible tampering – but without access to the original, unmodified version for comparison, it’s difficult to draw definitive conclusions.
Limitations: When Forgery is Hard to Detect
Despite the availability of various tools and techniques to uncover tampering in digital documents, significant limitations still exist – especially when certain safeguards are absent. One of the most common challenges occurs when a PDF is unsigned and has been edited directly using applications like Microsoft Word or Adobe Acrobat.
In such cases, if the file lacks embedded version history or if no original version is available for comparison, it becomes extremely difficult to determine whether any alterations have taken place. Without a reliable baseline, identifying discrepancies, removed content, or subtle modifications is nearly impossible.
This highlights the importance of digital signatures and document management systems, which not only establish trust and accountability but also provide verifiable evidence of a document’s integrity over time.
Conclusion
When a PDF file is neither password-protected nor digitally signed, a PDF file offers little assurance regarding its authenticity or integrity. At its core, such a file is merely a collection of digital objects – fonts, images, metadata, and text – any of which can be altered without leaving clear traces.
From a technical standpoint, the most critical element for ensuring document integrity is the digital signature. A valid digital signature not only verifies the document’s authenticity and authorship but also provides strong evidence that its content has not been altered.
When in doubt – and if it is feasible – always verify the document directly with the source or originator to confirm its accuracy and legitimacy. This simple step can often clarify uncertainties that technical analysis alone cannot resolve.
Fortunately, the PDF format supports both digital signatures and basic integrity or confidentiality mechanisms, such as PDF lock to prevent alteration and password protection from unauthorized access. However, without these protections in place, a PDF remains a mutable and easily manipulated file – offering little to no evidentiary value.
Recommendations
To ensure the authenticity and security of important PDF documents, consider the following best practices:
- Use digital signatures on all critical PDF files to establish legal validity and integrity. Disable editing rights on the PDF to prevent further modifications after signing.
- Password-protect PDFs, and share the password through a separate communication channel (e.g., a phone call, text, or a different email).
- If in doubt, always contact the source to verify the document’s authenticity before trusting or acting on its contents.
Frequently Asked Questions (FAQ)
Can a PDF be forged or tampered with?
Yes. Despite appearing trustworthy, PDF files can be manipulated using editing tools. These edits can include inserted images, modified text, or obscured content. Without safeguards like digital signatures, such tampering may go unnoticed.
What is a digital signature in a PDF and why is it important?
A digital signature authenticates a PDF by ensuring its:
- Integrity: The content hasn’t been changed since signing.
- Authorship: The signer’s identity is verified.
- Authenticity: The document is confirmed to be original.
If a signed PDF is modified, the signature becomes invalid, flagging potential tampering.
How can I tell if a digitally signed PDF has been altered?
You can use tools like Adobe Acrobat Pro to inspect the signature. If the document was changed after signing, Adobe will show a warning like “There have been subsequent changes to the document.”
Can I see what a PDF looked like before it was modified?
Yes. Tools such as Adobe Acrobat lets you view the version of the PDF at the time of signing. Use the digital signature panel and click “View this version” to compare it against the current version.
How can hidden changes or annotations be detected in a PDF?
Tools like PDF-Processing and pdfimages can uncover:
- Stamp annotations
- Overlay images
- Ink or text annotations used to obscure content
These tools can extract image objects and reveal edits that may be invisible in normal viewing mode.
Is metadata a reliable way to detect PDF tampering?
Not always. Metadata like modification time, author, or producer fields can be misleading:
- Simply downloading a file can alter the timestamp.
- Some editors don’t update metadata when making changes.
- Metadata alone is not definitive proof of tampering.
What tools are commonly used for PDF forensic analysis?
There are many tools that can be used to conduct analysis on a PDF file. Some tools mentioned in the blog are:
- Adobe Acrobat Pro – for signature inspection and editing mode.
- PDF-Processing tool – to extract versions and embedded images.
- pdfimages – to identify and locate images in the document.

































